| File name: | FwCustom Driver.exe |
| Full analysis: | https://app.any.run/tasks/e932ecd6-088e-42d6-a193-81d284031de3 |
| Verdict: | Malicious activity |
| Analysis date: | December 20, 2020, 20:12:43 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows |
| MD5: | D4983A06051B0774EB951E1E9A51E1B5 |
| SHA1: | 9D748D068442F2B5AAE091CD7C0DD8EEAA68DE21 |
| SHA256: | 4A8A70D55A86A4950958F4449542F81EF2CE761BBC3DD86D012C4BAF922F5538 |
| SSDEEP: | 393216:3BmT6Bp1pMTwbWR2HPNQymjOZ7hzrSmza:IS+eWR2HFQymjOZ5vm |
MALICIOUS
Loads dropped or rewritten executable
- FwCustom Driver.exe (PID: 2344)
- Redragon Kumara.exe (PID: 1536)
Drops executable file immediately after starts
- FwCustom Driver.exe (PID: 2344)
Application was dropped or rewritten from another process
- ISBEW64.exe (PID: 596)
- Redragon Kumara.exe (PID: 1536)
SUSPICIOUS
Executable content was dropped or overwritten
- FwCustom Driver.exe (PID: 2344)
Drops a file that was compiled in debug mode
- FwCustom Driver.exe (PID: 2344)
Executed via COM
- DllHost.exe (PID: 1740)
- DllHost.exe (PID: 1204)
Executed as Windows Service
- vssvc.exe (PID: 1768)
Searches for installed software
- DllHost.exe (PID: 1740)
- FwCustom Driver.exe (PID: 2344)
Drops a file with too old compile date
- FwCustom Driver.exe (PID: 2344)
Creates a directory in Program Files
- FwCustom Driver.exe (PID: 2344)
Creates files in the program directory
- FwCustom Driver.exe (PID: 2344)
Creates a software uninstall entry
- FwCustom Driver.exe (PID: 2344)
INFO
Low-level read access rights to disk partition
- vssvc.exe (PID: 1768)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .ax | | | DirectShow filter (36.7) |
|---|---|---|
| .exe | | | Win32 EXE PECompact compressed (v2.x) (10.7) |
| .exe | | | InstallShield setup (7.8) |
| .exe | | | Win32 EXE PECompact compressed (generic) (7.5) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2008:05:10 05:39:06+02:00 |
| PEType: | PE32 |
| LinkerVersion: | 6 |
| CodeSize: | 294912 |
| InitializedDataSize: | 106496 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x21ee4 |
| OSVersion: | 4 |
| ImageVersion: | - |
| SubsystemVersion: | 4 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 15.0.0.498 |
| ProductVersionNumber: | 15.0.0.0 |
| FileFlagsMask: | 0x003f |
| FileFlags: | (none) |
| FileOS: | Windows NT 32-bit |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | English (U.S.) |
| CharacterSet: | Unicode |
| CompanyName: | Acresso Software Inc. |
| FileDescription: | Setup.exe |
| FileVersion: | 15.0.498 |
| InternalName: | Setup |
| OriginalFileName: | Setup.exe |
| LegalCopyright: | Copyright (C) 2008 Acresso Software Inc. and/or InstallShield Co. Inc. All Rights Reserved. |
| ProductName: | InstallShield |
| ProductVersion: | 15 |
| InternalBuildNumber: | 77018 |
Summary
| Architecture: | IMAGE_FILE_MACHINE_I386 |
|---|---|
| Subsystem: | IMAGE_SUBSYSTEM_WINDOWS_GUI |
| Compilation Date: | 10-May-2008 03:39:06 |
| Detected languages: |
|
| CompanyName: | Acresso Software Inc. |
| FileDescription: | Setup.exe |
| FileVersion: | 15.0.498 |
| InternalName: | Setup |
| OriginalFilename: | Setup.exe |
| LegalCopyright: | Copyright (C) 2008 Acresso Software Inc. and/or InstallShield Co. Inc. All Rights Reserved. |
| ProductName: | InstallShield |
| ProductVersion: | 15.0 |
| Internal Build Number: | 77018 |
DOS Header
| Magic number: | MZ |
|---|---|
| Bytes on last page of file: | 0x0090 |
| Pages in file: | 0x0003 |
| Relocations: | 0x0000 |
| Size of header: | 0x0004 |
| Min extra paragraphs: | 0x0000 |
| Max extra paragraphs: | 0xFFFF |
| Initial SS value: | 0x0000 |
| Initial SP value: | 0x00B8 |
| Checksum: | 0x0000 |
| Initial IP value: | 0x0000 |
| Initial CS value: | 0x0000 |
| Overlay number: | 0x0000 |
| OEM identifier: | 0x0000 |
| OEM information: | 0x0000 |
| Address of NE header: | 0x00000108 |
PE Headers
| Signature: | PE |
|---|---|
| Machine: | IMAGE_FILE_MACHINE_I386 |
| Number of sections: | 4 |
| Time date stamp: | 10-May-2008 03:39:06 |
| Pointer to Symbol Table: | 0x00000000 |
| Number of symbols: | 0 |
| Size of Optional Header: | 0x00E0 |
| Characteristics: |
|
Sections
Name | Virtual Address | Virtual Size | Raw Size | Charateristics | Entropy |
|---|---|---|---|---|---|
.text | 0x00001000 | 0x00047052 | 0x00048000 | IMAGE_SCN_CNT_CODE, IMAGE_SCN_MEM_EXECUTE, IMAGE_SCN_MEM_READ | 6.55825 |
.rdata | 0x00049000 | 0x00009D98 | 0x0000A000 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ | 4.60456 |
.data | 0x00053000 | 0x0000726C | 0x00006000 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ, IMAGE_SCN_MEM_WRITE | 3.08275 |
.rsrc | 0x0005B000 | 0x0000978C | 0x0000A000 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ | 5.30828 |
Resources
Title | Entropy | Size | Codepage | Language | Type |
|---|---|---|---|---|---|
1 | 5.03019 | 895 | Latin 1 / Western European | UNKNOWN | RT_MANIFEST |
2 | 3.35099 | 4264 | Latin 1 / Western European | UNKNOWN | RT_ICON |
3 | 3.33005 | 2440 | Latin 1 / Western European | UNKNOWN | RT_ICON |
4 | 3.47791 | 1128 | Latin 1 / Western European | UNKNOWN | RT_ICON |
5 | 6.18448 | 2216 | Latin 1 / Western European | UNKNOWN | RT_ICON |
6 | 4.85842 | 1384 | Latin 1 / Western European | UNKNOWN | RT_ICON |
7 | 5.57777 | 9640 | Latin 1 / Western European | UNKNOWN | RT_ICON |
8 | 5.81004 | 4264 | Latin 1 / Western European | UNKNOWN | RT_ICON |
9 | 6.06596 | 1128 | Latin 1 / Western European | UNKNOWN | RT_ICON |
100 | 2.62308 | 62 | Latin 1 / Western European | UNKNOWN | RT_GROUP_ICON |
Imports
ADVAPI32.dll |
COMCTL32.dll |
GDI32.dll |
KERNEL32.dll |
LZ32.dll |
OLEAUT32.dll |
RPCRT4.dll |
SHELL32.dll |
USER32.dll |
VERSION.dll |
Total processes
46
Monitored processes
7
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 596 | C:\Users\admin\AppData\Local\Temp\{245AD37A-4B37-482A-8156-639BB4A76FC6}\ISBEW64.exe {EFB7539B-24F3-46B6-AF6E-3B021B51EFEF}:{C64E4306-A1E0-4C0A-8259-7341D0BA01C0} | C:\Users\admin\AppData\Local\Temp\{245AD37A-4B37-482A-8156-639BB4A76FC6}\ISBEW64.exe | — | FwCustom Driver.exe | |||||||||||
User: admin Company: Acresso Software Inc. Integrity Level: HIGH Description: InstallShield (R) 64-bit Setup Engine Exit code: 0 Version: 15.0.498 Modules
| |||||||||||||||
| 1204 | C:\Windows\system32\DllHost.exe /Processid:{F32D97DF-E3E5-4CB9-9E3E-0EB5B4E49801} | C:\Windows\system32\DllHost.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: COM Surrogate Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
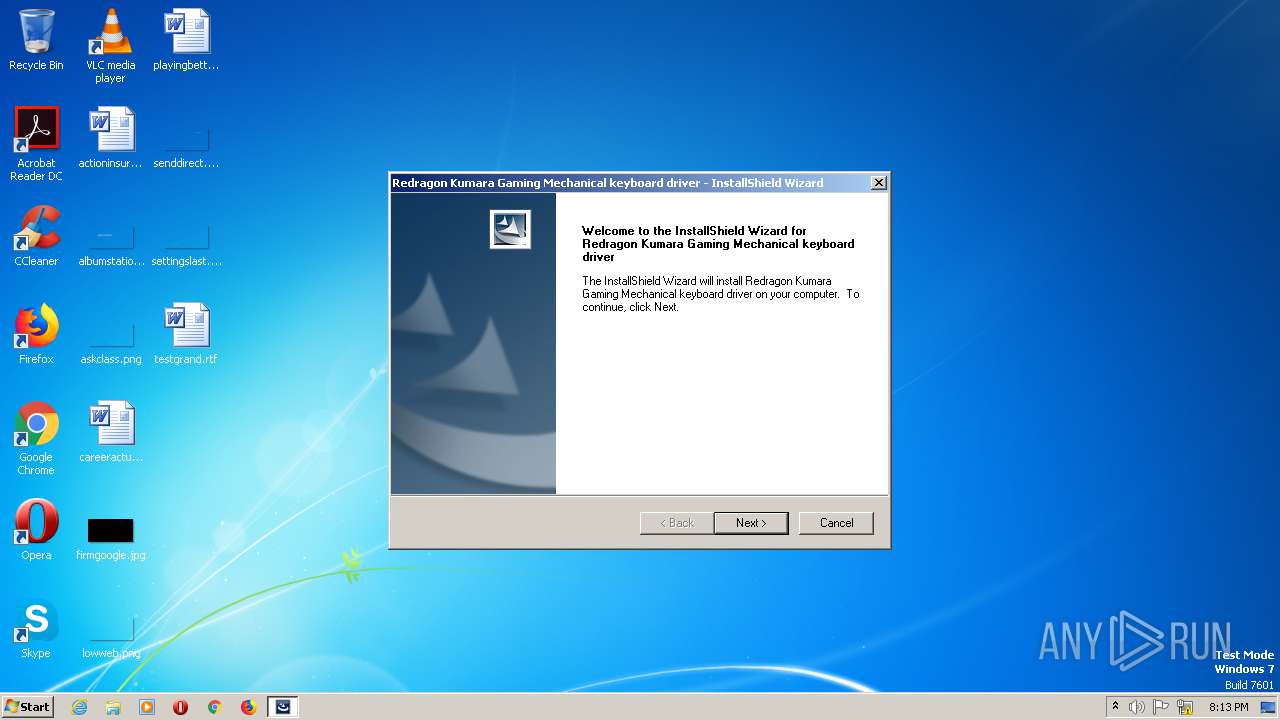
| 1536 | "C:\Program Files (x86)\Redragon Kumara Gaming Mechanical keyboard driver\Redragon Kumara.exe" /Start | C:\Program Files (x86)\Redragon Kumara Gaming Mechanical keyboard driver\Redragon Kumara.exe | — | FwCustom Driver.exe | |||||||||||
User: admin Company: 0 Integrity Level: HIGH Description: FwCustom Exit code: 0 Version: 1, 0, 0, 0 Modules
| |||||||||||||||
| 1740 | C:\Windows\system32\DllHost.exe /Processid:{F32D97DF-E3E5-4CB9-9E3E-0EB5B4E49801} | C:\Windows\system32\DllHost.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: COM Surrogate Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1768 | C:\Windows\system32\vssvc.exe | C:\Windows\system32\vssvc.exe | — | services.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Microsoft® Volume Shadow Copy Service Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2300 | "C:\Users\admin\AppData\Local\Temp\FwCustom Driver.exe" | C:\Users\admin\AppData\Local\Temp\FwCustom Driver.exe | — | explorer.exe | |||||||||||
User: admin Company: Acresso Software Inc. Integrity Level: MEDIUM Description: Setup.exe Exit code: 3221226540 Version: 15.0.498 Modules
| |||||||||||||||
| 2344 | "C:\Users\admin\AppData\Local\Temp\FwCustom Driver.exe" | C:\Users\admin\AppData\Local\Temp\FwCustom Driver.exe | explorer.exe | ||||||||||||
User: admin Company: Acresso Software Inc. Integrity Level: HIGH Description: Setup.exe Exit code: 0 Version: 15.0.498 Modules
| |||||||||||||||
Total events
425
Read events
266
Write events
159
Delete events
0
Modification events
| (PID) Process: | (1740) DllHost.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\services\VSS\Diag\SPP |
| Operation: | write | Name: | SppCreate (Enter) |
Value: 480000000000000068F273890CD7D601CC0600000C0A0000D00700000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (2344) FwCustom Driver.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\services\VSS\Diag\SystemRestore |
| Operation: | write | Name: | SrCreateRp (Enter) |
Value: 400000000000000068F273890CD7D60128090000FC050000D5070000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (1740) DllHost.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\SPP |
| Operation: | write | Name: | LastIndex |
Value: 50 | |||
| (PID) Process: | (1740) DllHost.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\services\VSS\Diag\SPP |
| Operation: | write | Name: | SppGatherWriterMetadata (Enter) |
Value: 4800000000000000A83DC0890CD7D601CC0600000C0A0000D30700000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (1740) DllHost.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\services\VSS\Diag\VssapiPublisher |
| Operation: | write | Name: | IDENTIFY (Enter) |
Value: 480000000000000002A0C2890CD7D601CC06000094090000E803000001000000000000000000000084BED75078283E44A45E91B1651606AB00000000000000000000000000000000 | |||
| (PID) Process: | (1768) vssvc.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\services\VSS\Diag\ASR Writer |
| Operation: | write | Name: | IDENTIFY (Enter) |
Value: 4800000000000000D2B2D5890CD7D601E8060000A00B0000E80300000100000001000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (1768) vssvc.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\services\VSS\Diag\Registry Writer |
| Operation: | write | Name: | IDENTIFY (Enter) |
Value: 4800000000000000D2B2D5890CD7D601E8060000C0090000E80300000100000001000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (1768) vssvc.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\services\VSS\Diag\COM+ REGDB Writer |
| Operation: | write | Name: | IDENTIFY (Enter) |
Value: 4800000000000000D2B2D5890CD7D601E806000040090000E80300000100000001000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (1768) vssvc.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\services\VSS\Diag\Shadow Copy Optimization Writer |
| Operation: | write | Name: | IDENTIFY (Enter) |
Value: 4800000000000000D2B2D5890CD7D601E8060000D00B0000E80300000100000001000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (1768) vssvc.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\services\VSS\Diag\COM+ REGDB Writer |
| Operation: | write | Name: | IDENTIFY (Leave) |
Value: 4800000000000000949EE1890CD7D601E806000040090000E80300000000000001000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
Executable files
13
Suspicious files
13
Text files
93
Unknown types
3
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2344 | FwCustom Driver.exe | C:\Users\admin\AppData\Local\Temp\{245AD37A-4B37-482A-8156-639BB4A76FC6}\{12F382E1-63D4-4B94-BD32-5F845E74FC79}\setudd07.rra | — | |
MD5:— | SHA256:— | |||
| 2344 | FwCustom Driver.exe | C:\Users\admin\AppData\Local\Temp\{245AD37A-4B37-482A-8156-639BB4A76FC6}\{12F382E1-63D4-4B94-BD32-5F845E74FC79}\licedd07.rra | — | |
MD5:— | SHA256:— | |||
| 2344 | FwCustom Driver.exe | C:\Users\admin\AppData\Local\Temp\{245AD37A-4B37-482A-8156-639BB4A76FC6}\coredd07.rra | — | |
MD5:— | SHA256:— | |||
| 2344 | FwCustom Driver.exe | C:\Users\admin\AppData\Local\Temp\{245AD37A-4B37-482A-8156-639BB4A76FC6}\dotndd16.rra | — | |
MD5:— | SHA256:— | |||
| 2344 | FwCustom Driver.exe | C:\Users\admin\AppData\Local\Temp\{245AD37A-4B37-482A-8156-639BB4A76FC6}\{12F382E1-63D4-4B94-BD32-5F845E74FC79}\Fontdd16.rra | — | |
MD5:— | SHA256:— | |||
| 2344 | FwCustom Driver.exe | C:\Users\admin\AppData\Local\Temp\{245AD37A-4B37-482A-8156-639BB4A76FC6}\{12F382E1-63D4-4B94-BD32-5F845E74FC79}\DIFxdd16.rra | — | |
MD5:— | SHA256:— | |||
| 2344 | FwCustom Driver.exe | C:\Users\admin\AppData\Local\Temp\{245AD37A-4B37-482A-8156-639BB4A76FC6}\{12F382E1-63D4-4B94-BD32-5F845E74FC79}\VASDdd16.rra | — | |
MD5:— | SHA256:— | |||
| 2344 | FwCustom Driver.exe | C:\Users\admin\AppData\Local\Temp\{245AD37A-4B37-482A-8156-639BB4A76FC6}\ISBEdd26.rra | — | |
MD5:— | SHA256:— | |||
| 2344 | FwCustom Driver.exe | C:\Users\admin\AppData\Local\Temp\{245AD37A-4B37-482A-8156-639BB4A76FC6}\{12F382E1-63D4-4B94-BD32-5F845E74FC79}\Stridd26.rra | — | |
MD5:— | SHA256:— | |||
| 2344 | FwCustom Driver.exe | C:\Users\admin\AppData\Local\Temp\{245AD37A-4B37-482A-8156-639BB4A76FC6}\{12F382E1-63D4-4B94-BD32-5F845E74FC79}\isrtdd26.rra | — | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
2
TCP/UDP connections
6
DNS requests
11
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
— | — | GET | 200 | 52.109.76.68:80 | http://office14client.microsoft.com/config14?UILCID=1033&CLCID=1033&ILCID=1033&HelpLCID=1033&App={C0AC079D-A84B-4CBD-8DBA-F1BB44146899}&build=14.0.5128 | IE | xml | 1.99 Kb | whitelisted |
— | — | GET | 200 | 34.107.221.82:80 | http://detectportal.firefox.com/success.txt | US | text | 8 b | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
— | — | 34.107.221.82:80 | detectportal.firefox.com | — | US | whitelisted |
— | — | 52.109.76.68:80 | office14client.microsoft.com | Microsoft Corporation | IE | suspicious |
— | — | 54.149.138.154:443 | push.services.mozilla.com | Amazon.com, Inc. | US | unknown |
— | — | 52.109.120.29:443 | rr.office.microsoft.com | Microsoft Corporation | HK | whitelisted |
— | — | 44.238.41.205:443 | location.services.mozilla.com | University of California, San Diego | US | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
detectportal.firefox.com |
| whitelisted |
prod.detectportal.prod.cloudops.mozgcp.net |
| whitelisted |
location.services.mozilla.com |
| whitelisted |
locprod2-elb-us-west-2.prod.mozaws.net |
| whitelisted |
push.services.mozilla.com |
| whitelisted |
autopush.prod.mozaws.net |
| whitelisted |
office14client.microsoft.com |
| whitelisted |
rr.office.microsoft.com |
| whitelisted |