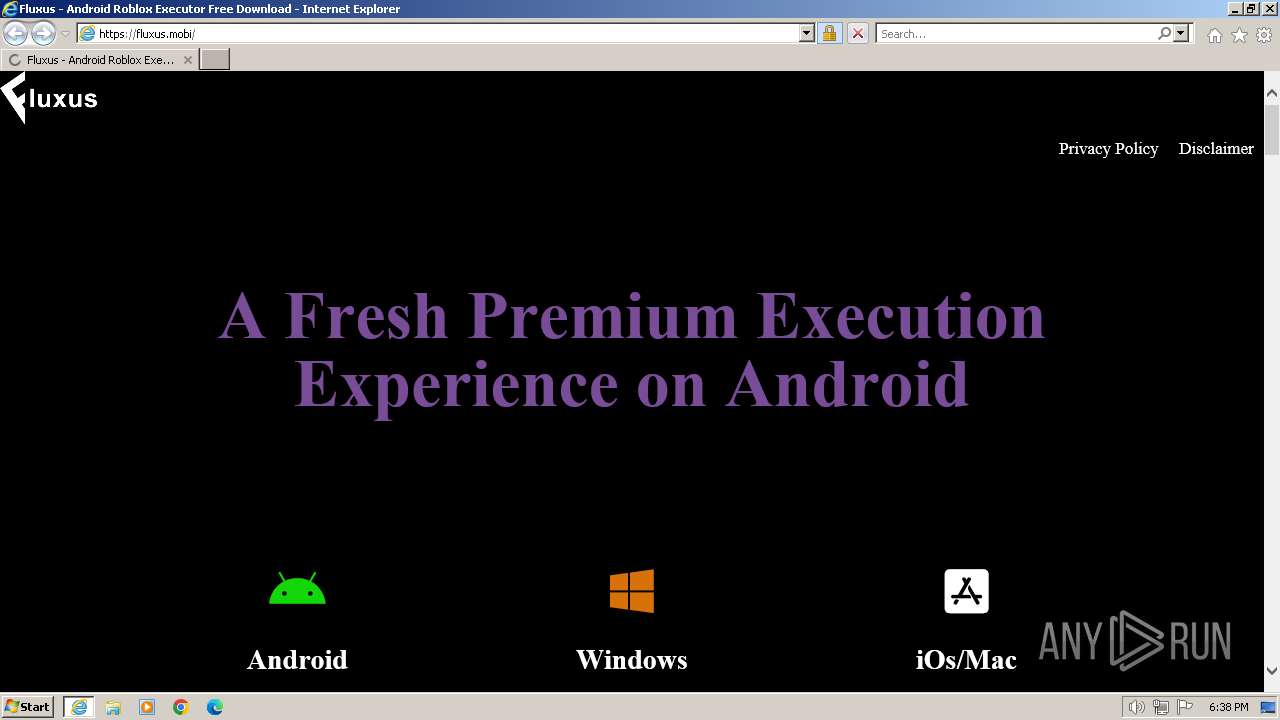
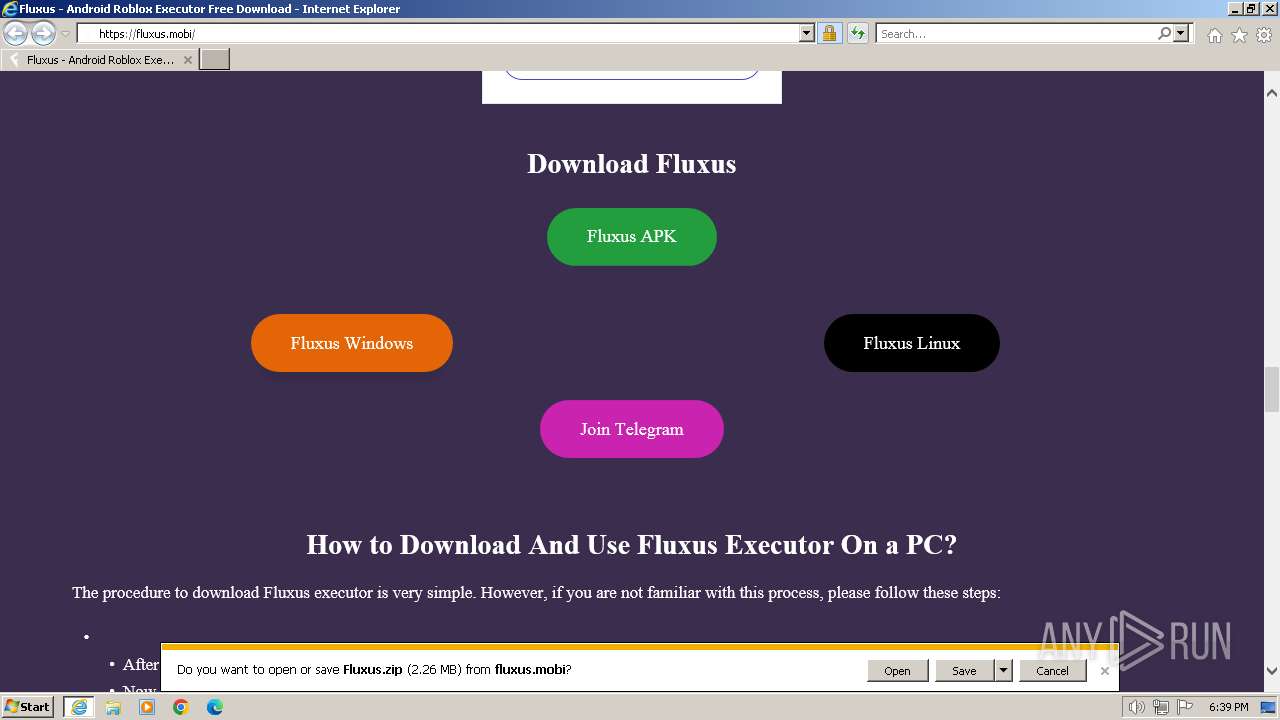
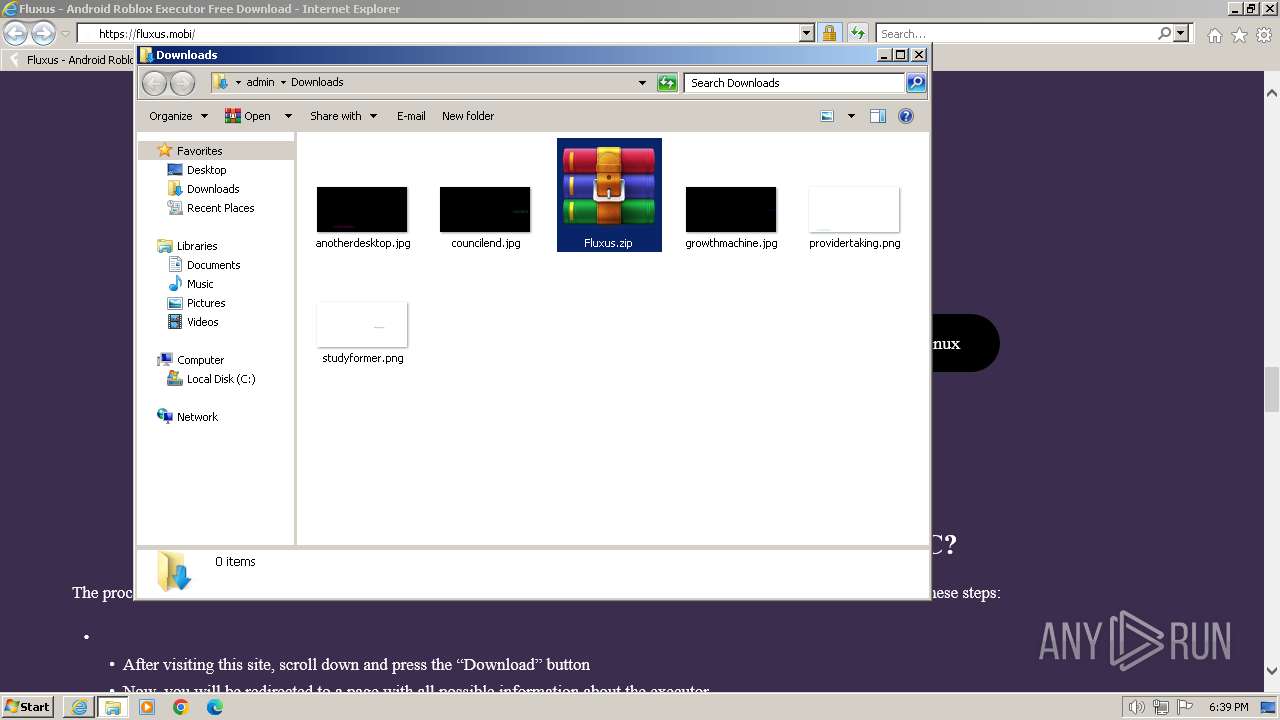
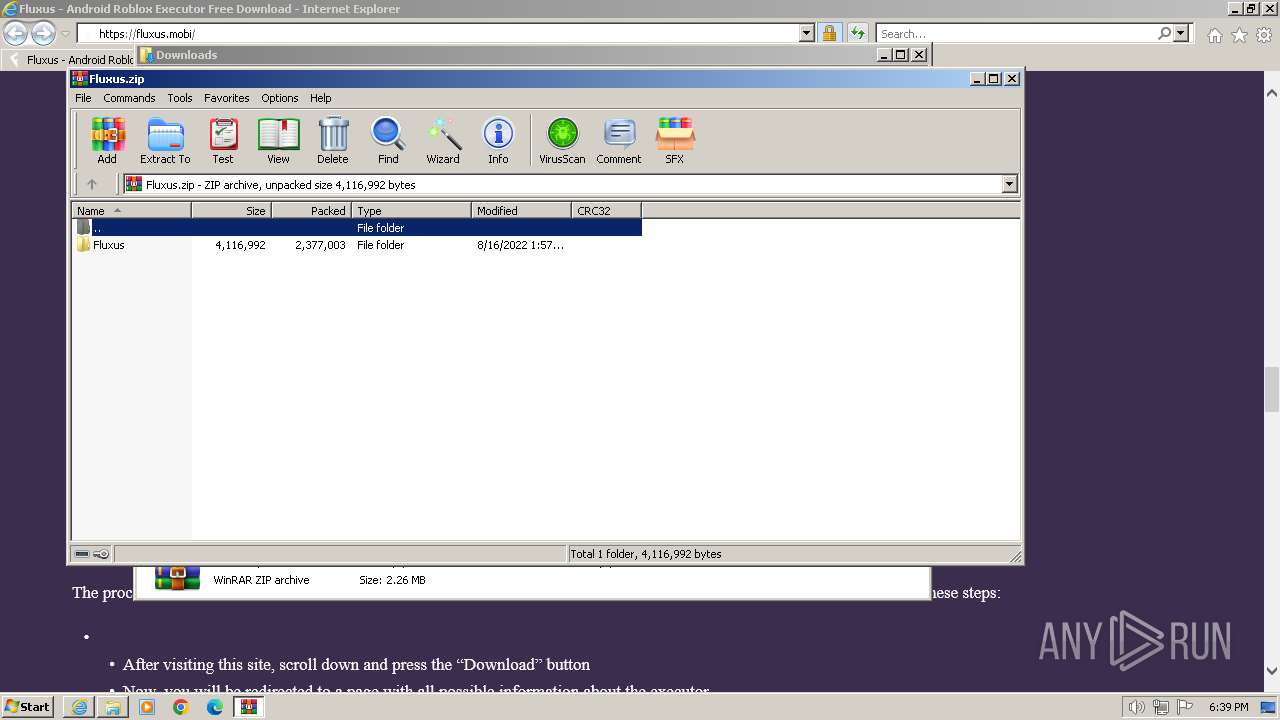
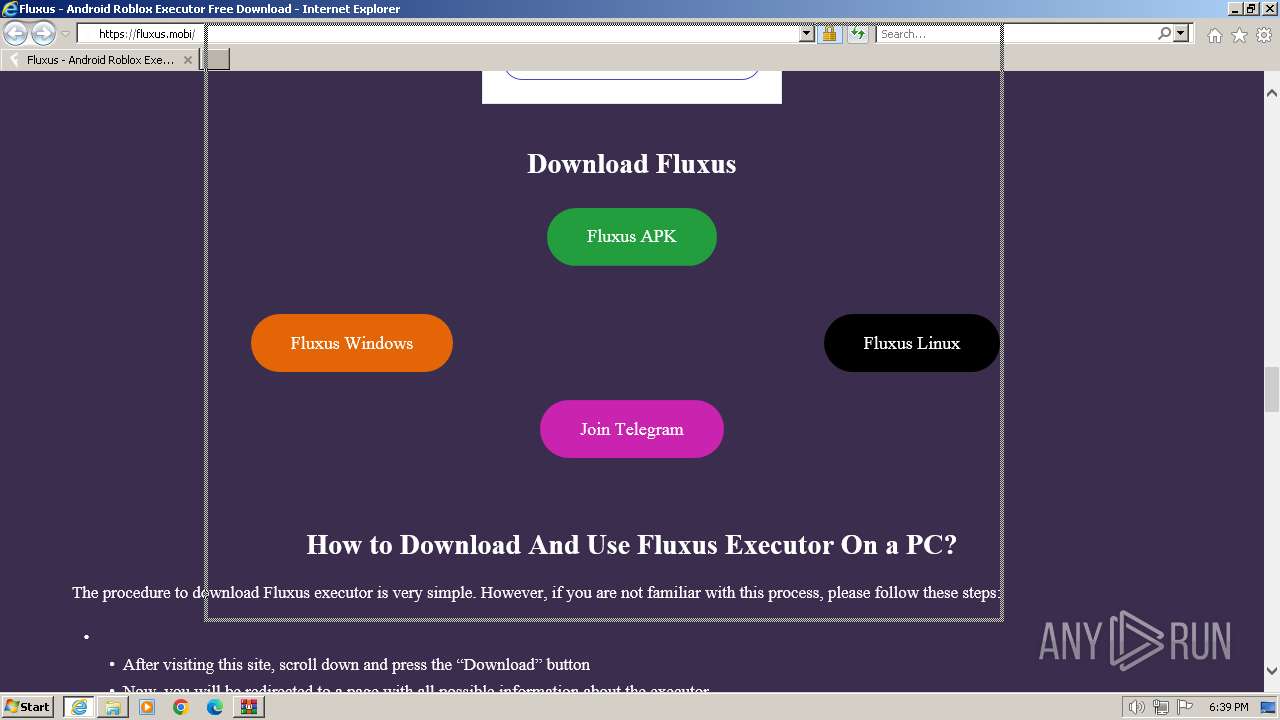
| URL: | https://fluxus.mobi/ |
| Full analysis: | https://app.any.run/tasks/546b151a-47fc-430a-92ef-5e6bddada8f8 |
| Verdict: | Malicious activity |
| Analysis date: | March 08, 2024, 18:38:16 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MD5: | 433E5C984A9BC0DD6134B052001D802A |
| SHA1: | 428BAF2E6FF960E7584CD327B9C136C3BC4A2901 |
| SHA256: | 4A89533B4816EDD6283C78D25D6EEAE5F7A4E2AAFCD7D34C739D5694B3C85951 |
| SSDEEP: | 3:N8UdX3sK:223sK |
MALICIOUS
No malicious indicators.SUSPICIOUS
Reads the Internet Settings
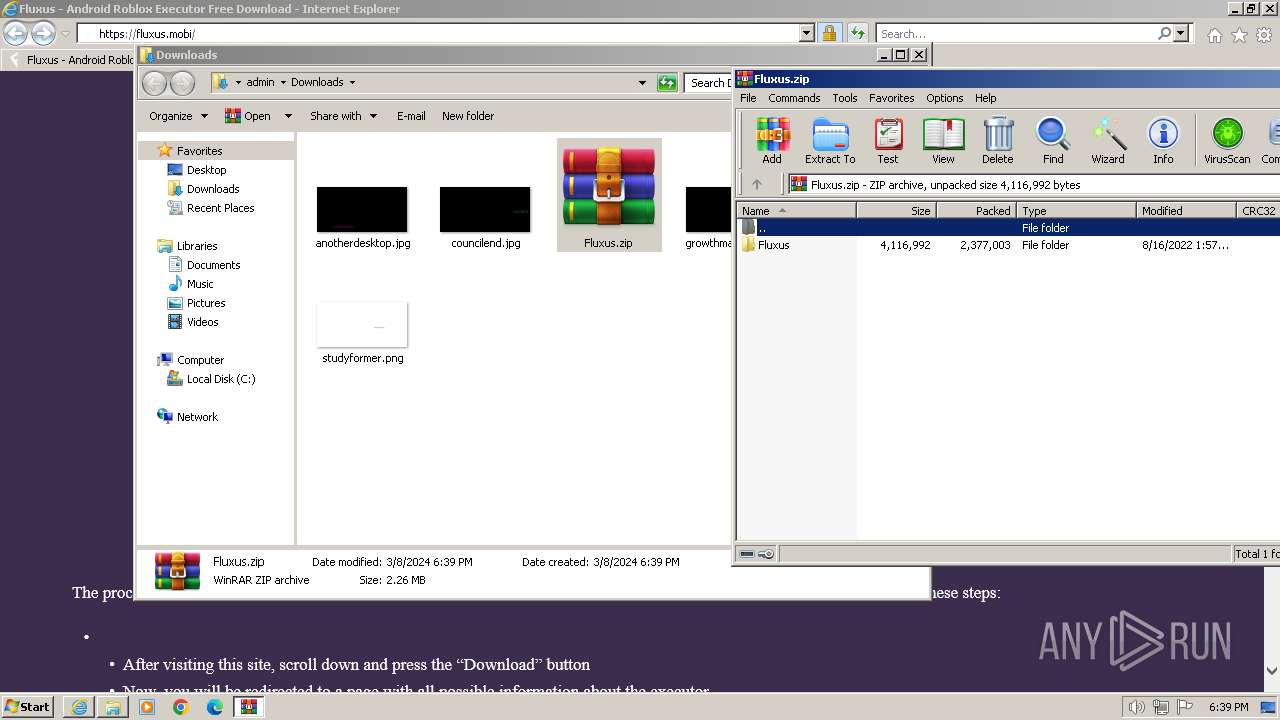
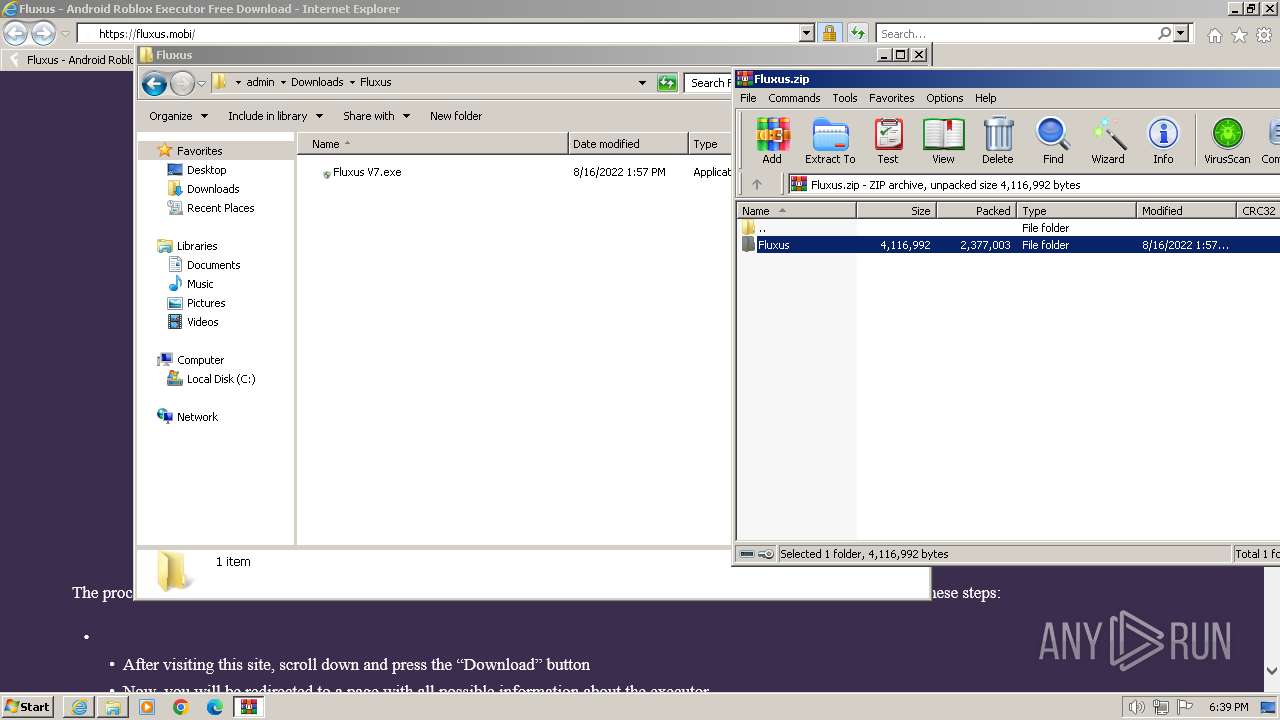
- Fluxus V7.exe (PID: 3976)
- Fluxus V7.exe (PID: 3620)
INFO
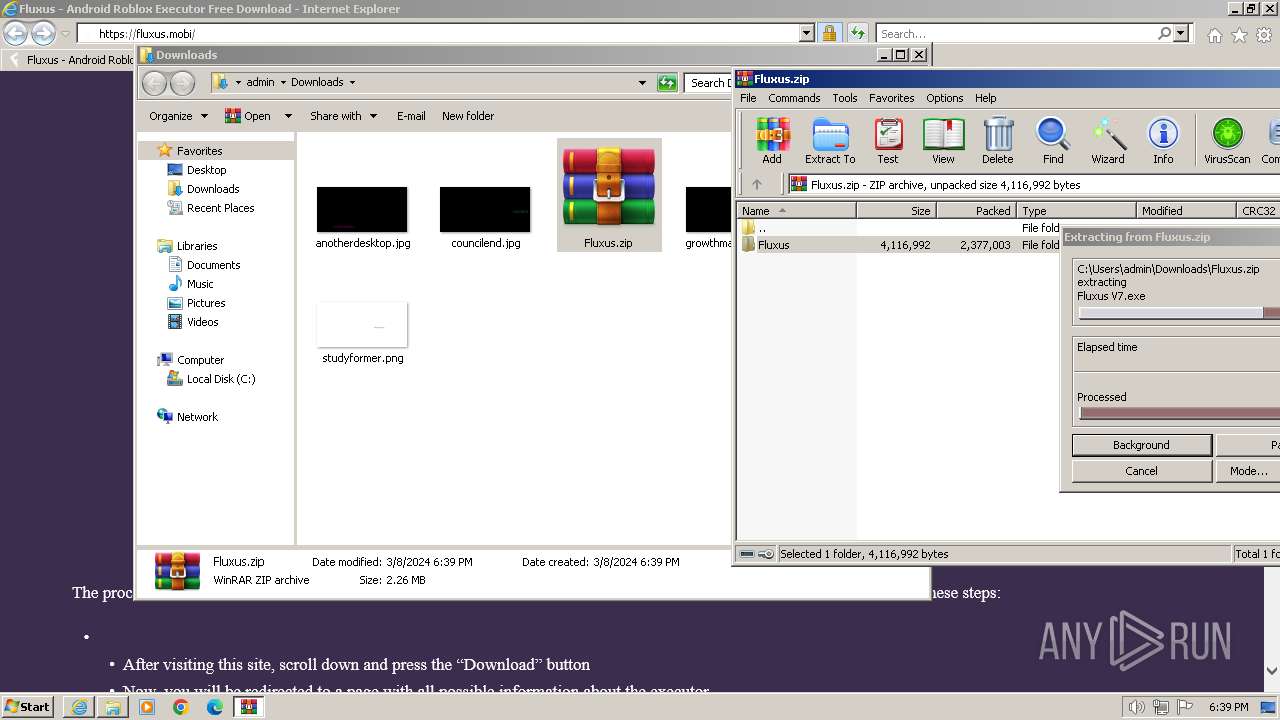
Executable content was dropped or overwritten
- WinRAR.exe (PID: 2000)
Modifies the phishing filter of IE
- iexplore.exe (PID: 3536)
Drops the executable file immediately after the start
- WinRAR.exe (PID: 2000)
Application launched itself
- iexplore.exe (PID: 3536)
The process uses the downloaded file
- iexplore.exe (PID: 3536)
- WinRAR.exe (PID: 2000)
Manual execution by a user
- Fluxus V7.exe (PID: 680)
- WinRAR.exe (PID: 2000)
- Fluxus V7.exe (PID: 3976)
- Fluxus V7.exe (PID: 3620)
Checks supported languages
- Fluxus V7.exe (PID: 3976)
- Fluxus V7.exe (PID: 3620)
Reads the machine GUID from the registry
- Fluxus V7.exe (PID: 3976)
- Fluxus V7.exe (PID: 3620)
Reads Environment values
- Fluxus V7.exe (PID: 3976)
- Fluxus V7.exe (PID: 3620)
Reads the computer name
- Fluxus V7.exe (PID: 3976)
- Fluxus V7.exe (PID: 3620)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
53
Monitored processes
6
Malicious processes
0
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
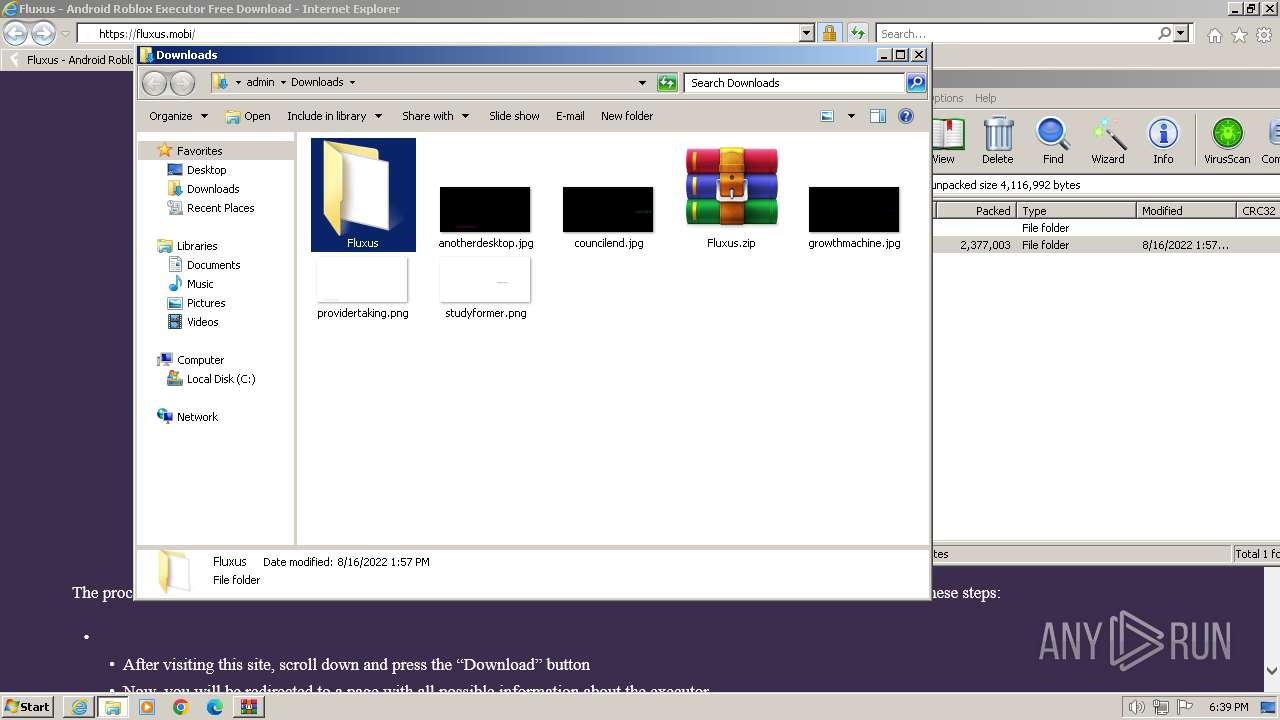
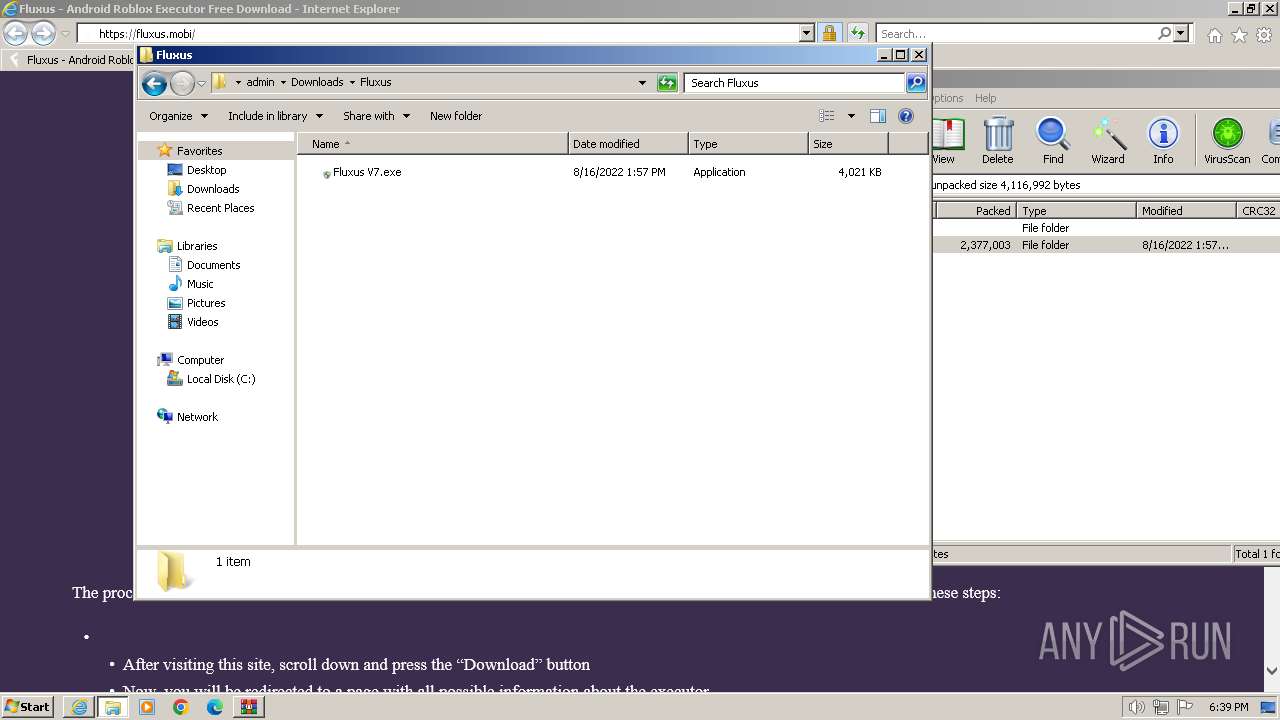
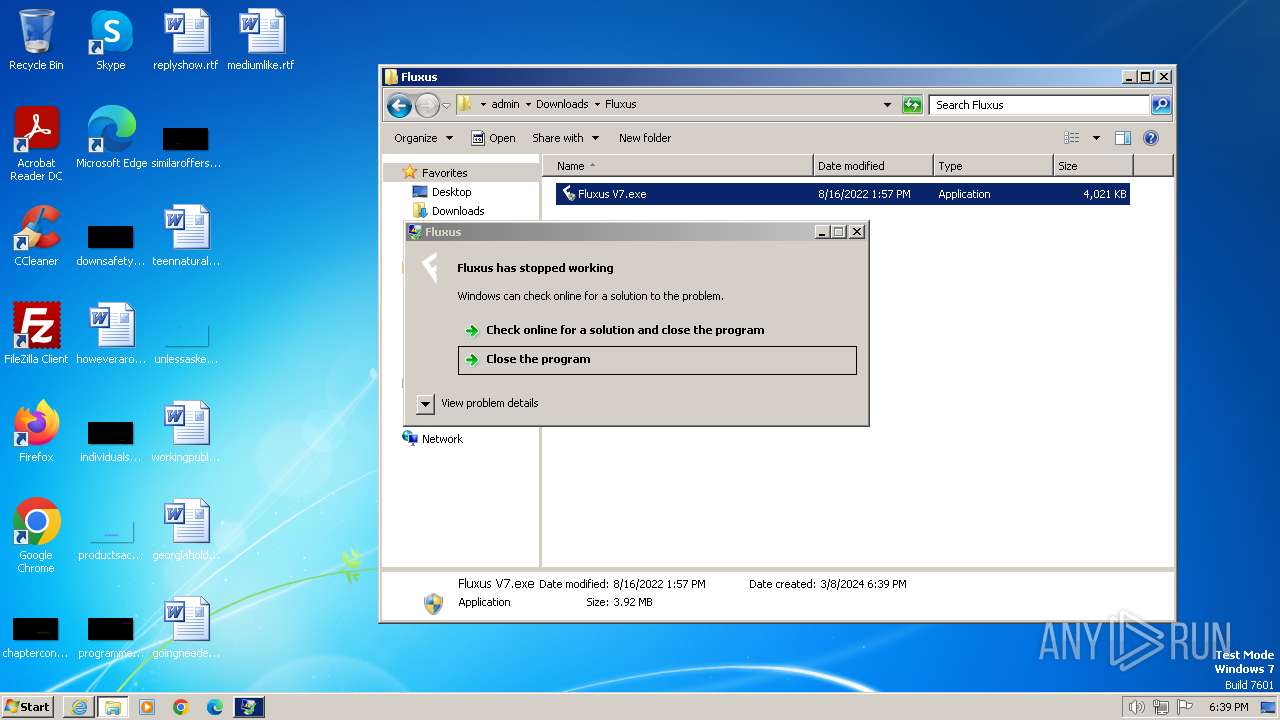
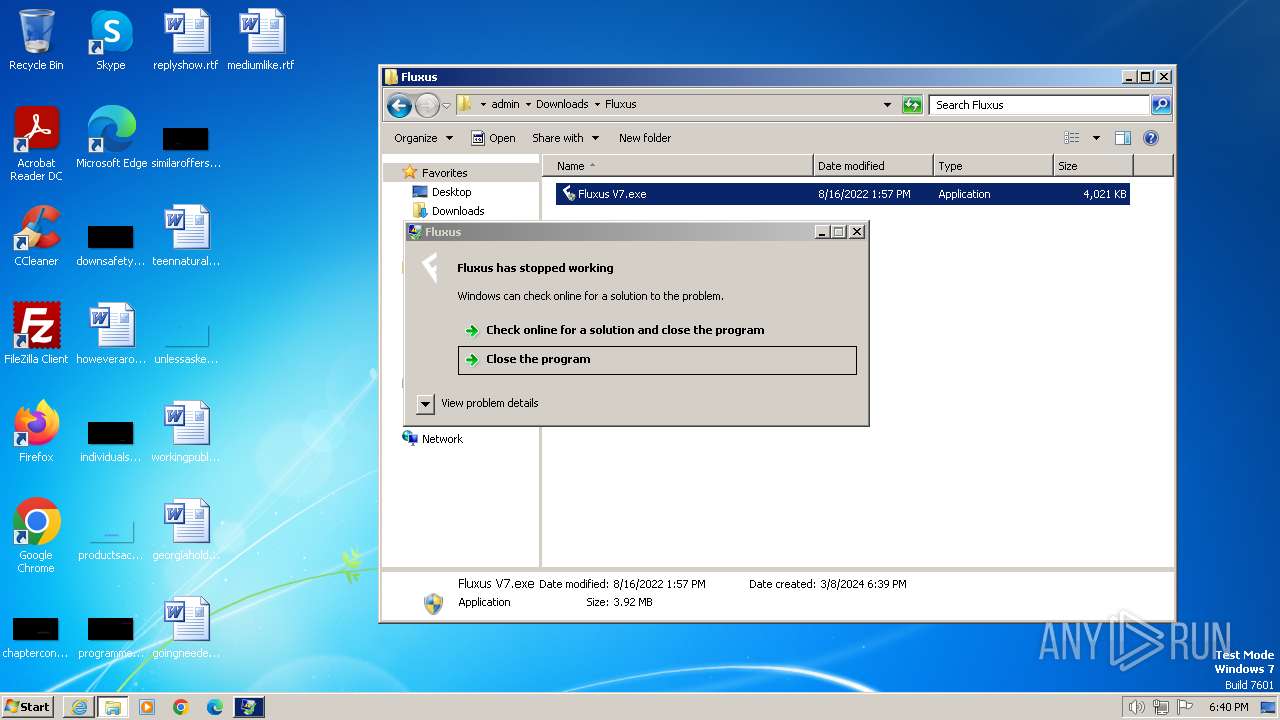
| 680 | "C:\Users\admin\Downloads\Fluxus\Fluxus V7.exe" | C:\Users\admin\Downloads\Fluxus\Fluxus V7.exe | — | explorer.exe | |||||||||||
User: admin Company: Fluxteam Integrity Level: MEDIUM Description: Fluxus Exit code: 3221226540 Version: 1.0.0.0 Modules
| |||||||||||||||
| 2000 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\Downloads\Fluxus.zip" | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.91.0 Modules
| |||||||||||||||
| 3536 | "C:\Program Files\Internet Explorer\iexplore.exe" "https://fluxus.mobi/" | C:\Program Files\Internet Explorer\iexplore.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Internet Explorer Exit code: 0 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
| 3620 | "C:\Users\admin\Downloads\Fluxus\Fluxus V7.exe" | C:\Users\admin\Downloads\Fluxus\Fluxus V7.exe | explorer.exe | ||||||||||||
User: admin Company: Fluxteam Integrity Level: HIGH Description: Fluxus Exit code: 3762504530 Version: 1.0.0.0 Modules
| |||||||||||||||
| 3732 | "C:\Program Files\Internet Explorer\iexplore.exe" SCODEF:3536 CREDAT:267521 /prefetch:2 | C:\Program Files\Internet Explorer\iexplore.exe | iexplore.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Internet Explorer Exit code: 0 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
| 3976 | "C:\Users\admin\Downloads\Fluxus\Fluxus V7.exe" | C:\Users\admin\Downloads\Fluxus\Fluxus V7.exe | explorer.exe | ||||||||||||
User: admin Company: Fluxteam Integrity Level: HIGH Description: Fluxus Exit code: 3762504530 Version: 1.0.0.0 Modules
| |||||||||||||||
Total events
30 637
Read events
30 437
Write events
162
Delete events
38
Modification events
| (PID) Process: | (3536) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPDaysSinceLastAutoMigration |
Value: 1 | |||
| (PID) Process: | (3536) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPLastLaunchLowDateTime |
Value: | |||
| (PID) Process: | (3536) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPLastLaunchHighDateTime |
Value: 31093127 | |||
| (PID) Process: | (3536) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\UrlBlockManager |
| Operation: | write | Name: | NextCheckForUpdateLowDateTime |
Value: | |||
| (PID) Process: | (3536) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\UrlBlockManager |
| Operation: | write | Name: | NextCheckForUpdateHighDateTime |
Value: 31093127 | |||
| (PID) Process: | (3536) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Content |
| Operation: | write | Name: | CachePrefix |
Value: | |||
| (PID) Process: | (3536) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (3536) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
| (PID) Process: | (3536) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\Main |
| Operation: | write | Name: | CompatibilityFlags |
Value: 0 | |||
| (PID) Process: | (3536) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
Executable files
1
Suspicious files
31
Text files
95
Unknown types
18
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3732 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\24BD96D5497F70B3F510A6B53CD43F3E_3A89246FB90C5EE6620004F1AE0EB0EA | binary | |
MD5:49A28DD8A906537E83E1D59B1232C1D6 | SHA256:9F944C25319C8FBF027AE03FD2CB719E82CD1CE775E9CE3AC06B63A0B9ABB0B9 | |||
| 3732 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\DY534W2X\widget-icon-box.min[1].css | text | |
MD5:F4219864DEDF59BDA19430A5D855F8FF | SHA256:70038873428CC0E3B92E5E7E74CD241AFD5B322FF98765CA2DB09B3F19925610 | |||
| 3732 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\57C8EDB95DF3F0AD4EE2DC2B8CFD4157 | binary | |
MD5:70F5973CF998C31937D83A4B09A4538F | SHA256:32E0514DA0BEE10D7F9B2A5440039BDFE0C85711EBBB8A2CA985E25F8FCE5853 | |||
| 3732 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\DY534W2X\header.min[1].css | text | |
MD5:3E4ABAA77D9CEC962A9367CD0482D170 | SHA256:E776A7F761E5975D81C3D8A5ECE5139FC9AC0DD13E3C494A941CF34C7A426EF8 | |||
| 3732 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\24BD96D5497F70B3F510A6B53CD43F3E_3A89246FB90C5EE6620004F1AE0EB0EA | binary | |
MD5:C3818B612D208953849775D66B053395 | SHA256:10BB002F4992DE8D387656AE2FABCFCAE310FF43B3AB2F1E6BA8D18A86299A20 | |||
| 3732 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\MFAQUS6V\375RQGMT.htm | html | |
MD5:F1631D70C2C7174C25BC29CA2239BA36 | SHA256:1EC33DE6DB884C8FA5531A0064DD708215BAB9583205B2CE37D97CEFA1EED6C2 | |||
| 3732 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\DY534W2X\global.min[1].css | text | |
MD5:73C090A651FDE16284EEAEA977FD19E1 | SHA256:9D8ED4CA489C25F4E040740A80AFD25EDE9F9E6B56F4BF0FDE73779599AC9791 | |||
| 3732 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\5IWPIAR9\frontend-lite.min[1].css | text | |
MD5:788883FA142B0B5FDB6C795072AC213F | SHA256:3C9EF71CB1059C3B6059B62872BB1CB9EAEA460B73ECD5431A8B3FE719A131D7 | |||
| 3732 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\MFAQUS6V\post-10[1].css | text | |
MD5:F9A5B6BD788CD2046989A0650A867173 | SHA256:CC0513BCB40B3DB5EB71F0E0716B351040F47AAE3671507CBFC88C72041BB8E6 | |||
| 3732 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\CAF4703619713E3F18D8A9D5D88D6288_F2DAF19C1F776537105D08FC8D978464 | binary | |
MD5:8202A1CD02E7D69597995CABBE881A12 | SHA256:58F381C3A0A0ACE6321DA22E40BD44A597BD98B9C9390AB9258426B5CF75A7A5 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
22
TCP/UDP connections
73
DNS requests
29
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
3732 | iexplore.exe | GET | 304 | 2.16.197.214:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?5b0325f31ae0f9b6 | unknown | — | — | unknown |
3732 | iexplore.exe | GET | 304 | 2.16.197.214:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?545e1839169dd0e6 | unknown | — | — | unknown |
3732 | iexplore.exe | GET | 200 | 142.250.185.195:80 | http://ocsp.pki.goog/gtsr1/ME4wTDBKMEgwRjAJBgUrDgMCGgUABBQwkcLWD4LqGJ7bE7B1XZsEbmfwUAQU5K8rJnEaK0gnhS9SZizv8IkTcT4CDQIDvFCjJ1PwkYAi7fE%3D | unknown | binary | 724 b | unknown |
3732 | iexplore.exe | GET | 200 | 142.250.185.195:80 | http://ocsp.pki.goog/gtsr1/ME4wTDBKMEgwRjAJBgUrDgMCGgUABBQwkcLWD4LqGJ7bE7B1XZsEbmfwUAQU5K8rJnEaK0gnhS9SZizv8IkTcT4CDQIDvFNZazTHGPUBUGY%3D | unknown | binary | 724 b | unknown |
3732 | iexplore.exe | GET | 200 | 142.250.185.195:80 | http://ocsp.pki.goog/gts1c3/MFIwUDBOMEwwSjAJBgUrDgMCGgUABBTHLnmK3f9hNLO67UdCuLvGwCQHYwQUinR%2Fr4XN7pXNPZzQ4kYU83E1HScCEQC%2BP0iGO7o7nQoIudW3BwdU | unknown | binary | 472 b | unknown |
3732 | iexplore.exe | GET | 200 | 142.250.185.195:80 | http://ocsp.pki.goog/gsr1/MFEwTzBNMEswSTAJBgUrDgMCGgUABBS3V7W2nAf4FiMTjpDJKg6%2BMgGqMQQUYHtmGkUNl8qJUC99BM00qP%2F8%2FUsCEHe9DWzbNvka6iEPxPBY0w0%3D | unknown | binary | 1.41 Kb | unknown |
3732 | iexplore.exe | GET | 200 | 142.250.185.195:80 | http://ocsp.pki.goog/gts1c3/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTHLnmK3f9hNLO67UdCuLvGwCQHYwQUinR%2Fr4XN7pXNPZzQ4kYU83E1HScCEH6FWuT3fbHwEAPEHSB2q%2B0%3D | unknown | binary | 471 b | unknown |
— | — | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTBL0V27RVZ7LBduom%2FnYB45SPUEwQU5Z1ZMIJHWMys%2BghUNoZ7OrUETfACEAo3h2ReX7SMIk79G%2B0UDDw%3D | unknown | binary | 1.47 Kb | unknown |
3732 | iexplore.exe | GET | 200 | 2.20.21.213:80 | http://x1.c.lencr.org/ | unknown | binary | 717 b | unknown |
— | — | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAzlnDD9eoNTLi0BRrMy%2BWU%3D | unknown | binary | 314 b | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | unknown |
3732 | iexplore.exe | 188.114.97.3:443 | fluxus.mobi | CLOUDFLARENET | NL | unknown |
3732 | iexplore.exe | 2.16.197.214:80 | ctldl.windowsupdate.com | Akamai International B.V. | BR | unknown |
3536 | iexplore.exe | 2.16.197.71:443 | www.bing.com | Akamai International B.V. | BR | unknown |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
3732 | iexplore.exe | 142.250.185.195:80 | ocsp.pki.goog | GOOGLE | US | whitelisted |
3732 | iexplore.exe | 142.250.186.170:443 | fonts.googleapis.com | GOOGLE | US | whitelisted |
3732 | iexplore.exe | 216.58.206.40:443 | www.googletagmanager.com | GOOGLE | US | unknown |
3732 | iexplore.exe | 216.58.206.34:443 | pagead2.googlesyndication.com | GOOGLE | US | unknown |
3732 | iexplore.exe | 104.20.67.115:443 | s10.histats.com | CLOUDFLARENET | — | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
fluxus.mobi |
| unknown |
ctldl.windowsupdate.com |
| whitelisted |
api.bing.com |
| whitelisted |
www.bing.com |
| whitelisted |
ocsp.pki.goog |
| whitelisted |
fonts.googleapis.com |
| whitelisted |
www.googletagmanager.com |
| whitelisted |
pagead2.googlesyndication.com |
| whitelisted |
s10.histats.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |