| File name: | MrsMajor3.0.exe |
| Full analysis: | https://app.any.run/tasks/017509fd-067e-4729-a636-72e2e559c1d9 |
| Verdict: | Malicious activity |
| Analysis date: | January 20, 2025, 15:42:36 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Indicators: | |
| MIME: | application/vnd.microsoft.portable-executable |
| File info: | PE32+ executable (GUI) x86-64, for MS Windows, 6 sections |
| MD5: | 35A27D088CD5BE278629FAE37D464182 |
| SHA1: | D5A291FADEAD1F2A0CF35082012FE6F4BF22A3AB |
| SHA256: | 4A75F2DB1DBD3C1218BB9994B7E1C690C4EDD4E0C1A675DE8D2A127611173E69 |
| SSDEEP: | 6144:Th3idhONY259BH1DzJ5PzVNtGgc+F9TBd096cTKAsLEbqqbd+VWM8AHiKn9SlXNA:Th3iXPw9Tc6kVXMHHLEf8l7 |
MALICIOUS
Creates a new registry key or changes the value of an existing one (SCRIPT)
- wscript.exe (PID: 5568)
SUSPICIOUS
Executable content was dropped or overwritten
- MrsMajor3.0.exe (PID: 2072)
- eulascr.exe (PID: 2676)
Reads security settings of Internet Explorer
- MrsMajor3.0.exe (PID: 2072)
- eulascr.exe (PID: 2676)
Runs shell command (SCRIPT)
- wscript.exe (PID: 5568)
Reads the date of Windows installation
- eulascr.exe (PID: 2676)
- MrsMajor3.0.exe (PID: 2072)
Runs WScript without displaying logo
- wscript.exe (PID: 5568)
The process executes VB scripts
- MrsMajor3.0.exe (PID: 2072)
The process executes via Task Scheduler
- PLUGScheduler.exe (PID: 2712)
INFO
The sample compiled with english language support
- MrsMajor3.0.exe (PID: 2072)
Reads the computer name
- MrsMajor3.0.exe (PID: 2072)
- eulascr.exe (PID: 2676)
- PLUGScheduler.exe (PID: 2712)
Checks supported languages
- MrsMajor3.0.exe (PID: 2072)
- eulascr.exe (PID: 2676)
Checks proxy server information
- eulascr.exe (PID: 2676)
Reads the software policy settings
- eulascr.exe (PID: 2676)
The process uses the downloaded file
- eulascr.exe (PID: 2676)
- MrsMajor3.0.exe (PID: 2072)
Create files in a temporary directory
- MrsMajor3.0.exe (PID: 2072)
- eulascr.exe (PID: 2676)
Reads the machine GUID from the registry
- eulascr.exe (PID: 2676)
Process checks computer location settings
- MrsMajor3.0.exe (PID: 2072)
- eulascr.exe (PID: 2676)
Disables trace logs
- eulascr.exe (PID: 2676)
Reads Environment values
- eulascr.exe (PID: 2676)
Creates files in the program directory
- PLUGScheduler.exe (PID: 2712)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win64 Executable (generic) (87.2) |
|---|---|---|
| .exe | | | Generic Win/DOS Executable (6.3) |
| .exe | | | DOS Executable Generic (6.3) |
EXIF
EXE
| MachineType: | AMD AMD64 |
|---|---|
| TimeStamp: | 2018:02:01 20:47:38+00:00 |
| ImageFileCharacteristics: | No relocs, Executable, No line numbers, No symbols, Large address aware |
| PEType: | PE32+ |
| LinkerVersion: | 2.5 |
| CodeSize: | 86528 |
| InitializedDataSize: | 303104 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x1000 |
| OSVersion: | 4 |
| ImageVersion: | - |
| SubsystemVersion: | 5.2 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 3.0.0.0 |
| ProductVersionNumber: | 3.0.0.0 |
| FileFlagsMask: | 0x003f |
| FileFlags: | Debug, Pre-release, Private build |
| FileOS: | Windows 16-bit |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | English (U.S.) |
| CharacterSet: | Windows, Latin1 |
| FileVersion: | 3.0.0.0 |
| ProductVersion: | 3.0.0.0 |
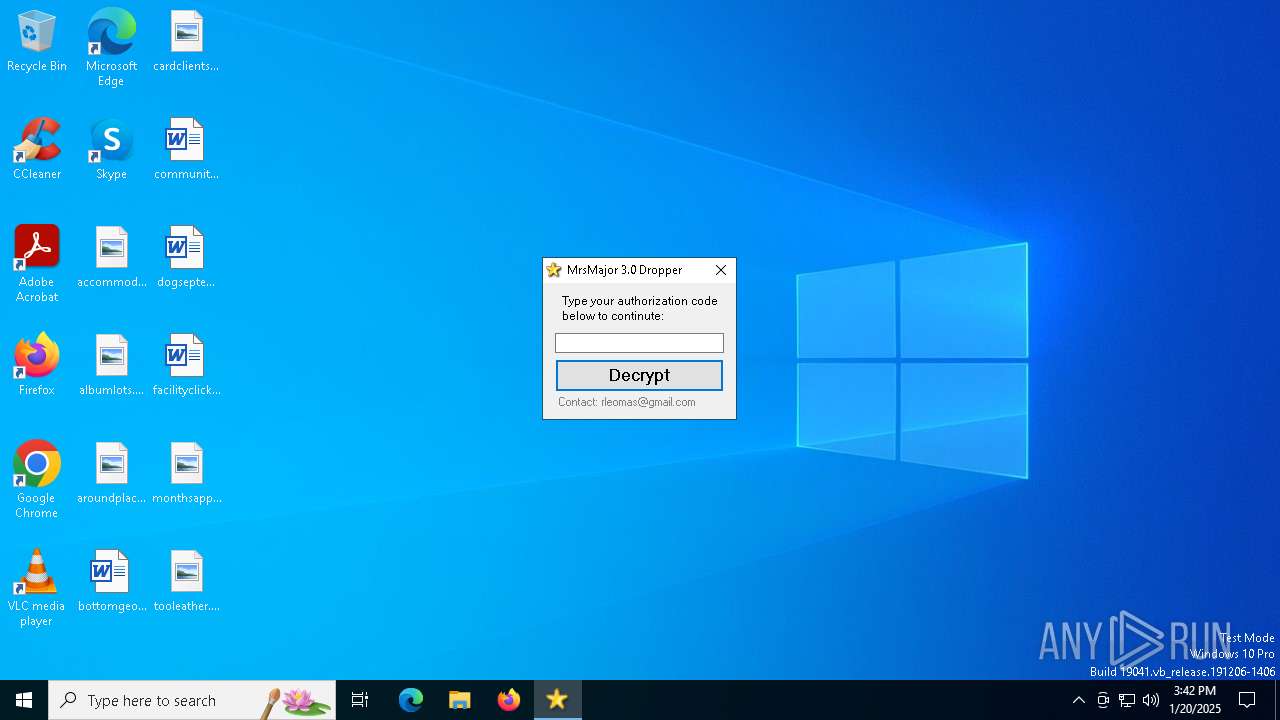
| ProductName: | MrsMajor |
| OriginalFileName: | MrsMajor3.0.exe |
| InternalName: | MrsMajor3.0 |
| FileDescription: | Watch out |
| CompanyName: | Mnc 2020 |
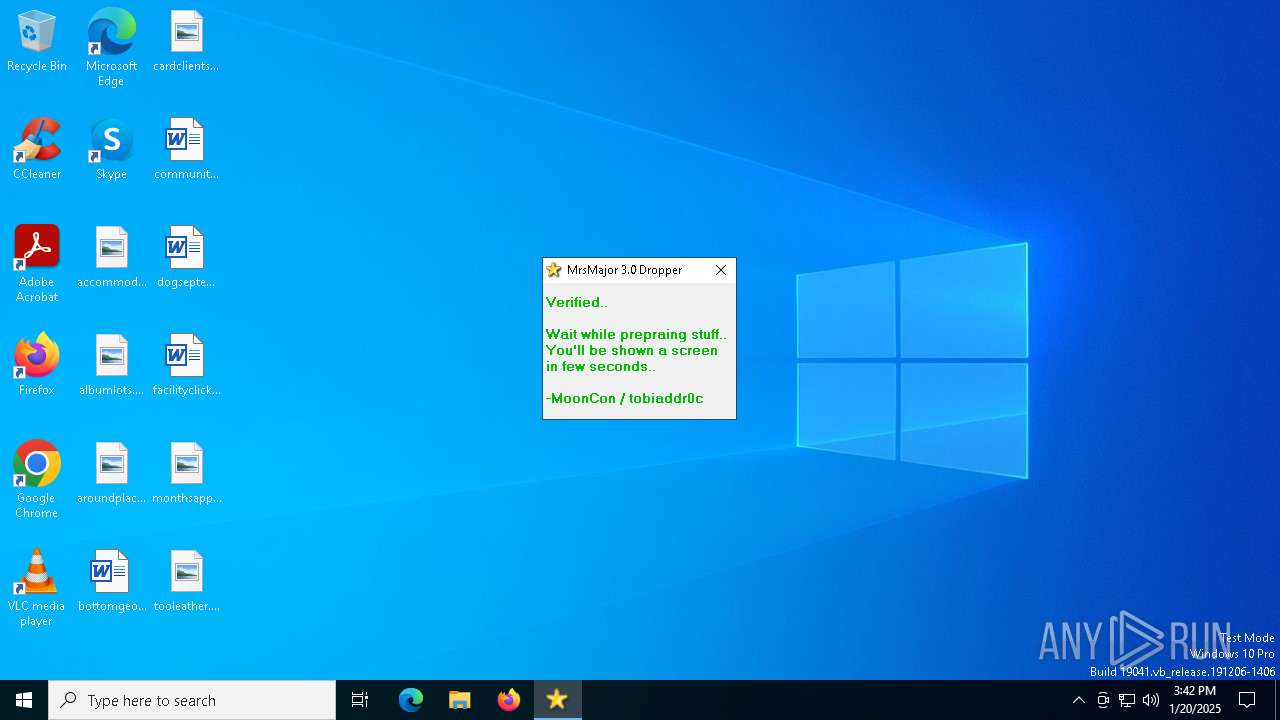
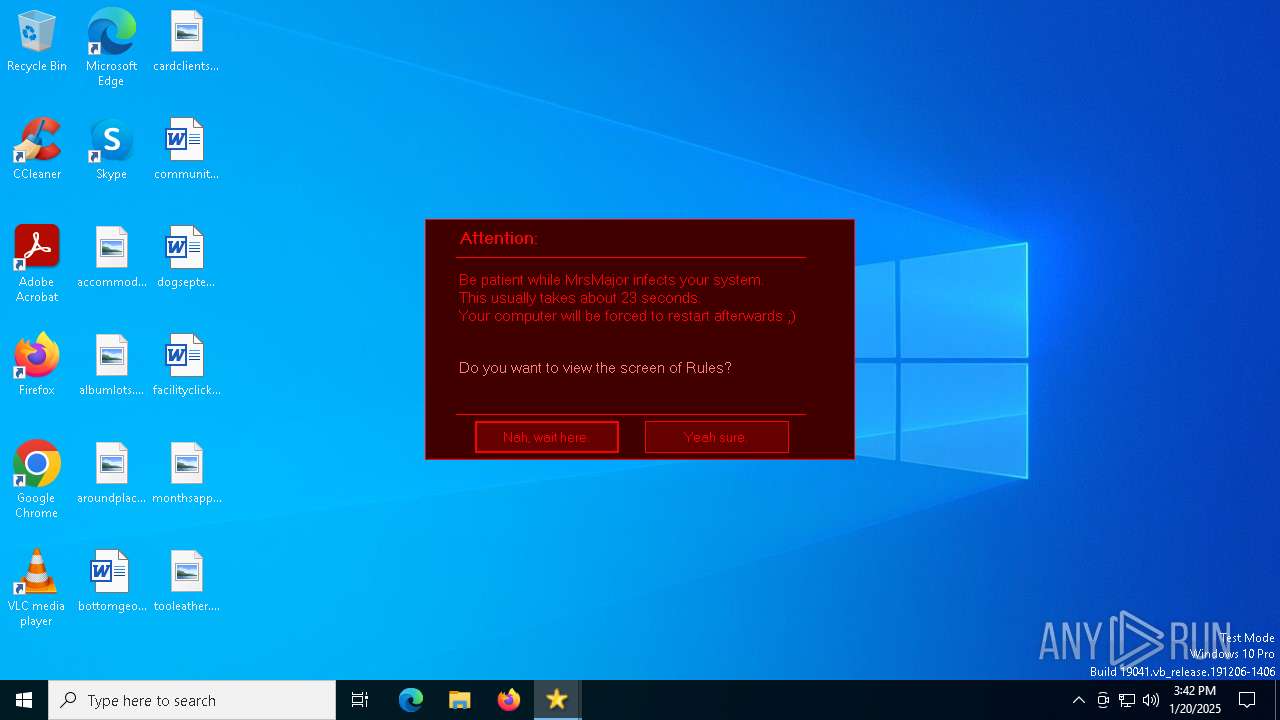
| LegalCopyright: | Elektro Berkay / MoonCon / Tobiaddr0c |
Total processes
269
Monitored processes
5
Malicious processes
2
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 936 | "C:\Users\admin\AppData\Local\Temp\MrsMajor3.0.exe" | C:\Users\admin\AppData\Local\Temp\MrsMajor3.0.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 3221226540 Modules
| |||||||||||||||
| 2072 | "C:\Users\admin\AppData\Local\Temp\MrsMajor3.0.exe" | C:\Users\admin\AppData\Local\Temp\MrsMajor3.0.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
| 2676 | "C:\Users\admin\AppData\Local\Temp\66BC.tmp\eulascr.exe" | C:\Users\admin\AppData\Local\Temp\66BC.tmp\eulascr.exe | wscript.exe | ||||||||||||
User: admin Integrity Level: HIGH Description: mmdropper Exit code: 1073807364 Version: 1.0.7321.42228 Modules
| |||||||||||||||
| 2712 | "C:\Program Files\RUXIM\PLUGscheduler.exe" | C:\Program Files\RUXIM\PLUGScheduler.exe | — | svchost.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows Update LifeCycle Component Scheduler Exit code: 0 Version: 10.0.19041.3623 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5568 | "C:\WINDOWS\system32\wscript.exe" C:\Users\admin\AppData\Local\Temp\66BC.tmp\66BD.tmp\66BE.vbs //Nologo | C:\Windows\System32\wscript.exe | — | MrsMajor3.0.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Microsoft ® Windows Based Script Host Exit code: 0 Version: 5.812.10240.16384 Modules
| |||||||||||||||
Total events
3 082
Read events
3 067
Write events
15
Delete events
0
Modification events
| (PID) Process: | (5568) wscript.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Policies\System |
| Operation: | write | Name: | ConsentPromptBehaviorAdmin |
Value: 0 | |||
| (PID) Process: | (2676) eulascr.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\eulascr_RASAPI32 |
| Operation: | write | Name: | EnableFileTracing |
Value: 0 | |||
| (PID) Process: | (2676) eulascr.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\eulascr_RASAPI32 |
| Operation: | write | Name: | EnableAutoFileTracing |
Value: 0 | |||
| (PID) Process: | (2676) eulascr.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\eulascr_RASAPI32 |
| Operation: | write | Name: | EnableConsoleTracing |
Value: 0 | |||
| (PID) Process: | (2676) eulascr.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\eulascr_RASAPI32 |
| Operation: | write | Name: | FileTracingMask |
Value: | |||
| (PID) Process: | (2676) eulascr.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\eulascr_RASAPI32 |
| Operation: | write | Name: | ConsoleTracingMask |
Value: | |||
| (PID) Process: | (2676) eulascr.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\eulascr_RASAPI32 |
| Operation: | write | Name: | MaxFileSize |
Value: 1048576 | |||
| (PID) Process: | (2676) eulascr.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\eulascr_RASAPI32 |
| Operation: | write | Name: | FileDirectory |
Value: %windir%\tracing | |||
| (PID) Process: | (2676) eulascr.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\eulascr_RASMANCS |
| Operation: | write | Name: | EnableFileTracing |
Value: 0 | |||
| (PID) Process: | (2676) eulascr.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\eulascr_RASMANCS |
| Operation: | write | Name: | EnableAutoFileTracing |
Value: 0 | |||
Executable files
3
Suspicious files
41
Text files
2
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2676 | eulascr.exe | C:\Users\admin\AppData\Local\Temp\5a530dfd-bc51-4992-a05d-f09d41a331d4\AgileDotNetRT64.dll | executable | |
MD5:42B2C266E49A3ACD346B91E3B0E638C0 | SHA256:ADEED015F06EFA363D504A18ACB671B1DB4B20B23664A55C9BC28AEF3283CA29 | |||
| 2072 | MrsMajor3.0.exe | C:\Users\admin\AppData\Local\Temp\66BC.tmp\AgileDotNet.VMRuntime.dll | executable | |
MD5:266373FADD81120BAEAE3504E1654A5A | SHA256:0798779DC944BA73C5A9CE4B8781D79F5DD7B5F49E4E8EF75020DE665BAD8CCB | |||
| 2072 | MrsMajor3.0.exe | C:\Users\admin\AppData\Local\Temp\66BC.tmp\66BD.tmp\66BE.vbs | binary | |
MD5:3B8696ECBB737AAD2A763C4EAF62C247 | SHA256:CE95F7EEA8B303BC23CFD6E41748AD4E7B5E0F0F1D3BDF390EADB1E354915569 | |||
| 2712 | PLUGScheduler.exe | C:\ProgramData\PLUG\Logs\RUXIMLog.037.etl | binary | |
MD5:A23907B6FDD47DCABFDFD7CF2FCD7671 | SHA256:0C9C33FE9E984A2E5A70EBA51F36B9929A86199E424AF2F8080E1267B87DC970 | |||
| 2712 | PLUGScheduler.exe | C:\ProgramData\PLUG\Logs\RUXIMLog.033.etl | binary | |
MD5:B53B2070E686FFB1FBC8B06994E7C8D7 | SHA256:A3ABD06F4E40CB700B1908AB6BCD2E27455E13EF076E0BF2345BB2FA369EF802 | |||
| 2676 | eulascr.exe | C:\Users\admin\WinManagementLIB.MSI | text | |
MD5:804823057912FAD0670C6EE060D56AA2 | SHA256:02633ED987F60305B83A886FC4F7DE876D91CD616BFE01F611659352433F8175 | |||
| 2712 | PLUGScheduler.exe | C:\ProgramData\PLUG\Logs\RUXIMLog.036.etl | binary | |
MD5:FED961067F664B5381B65A534B7AB728 | SHA256:652F31A8284AE812D1D9D24192BC800976BF74C240591C6AC443A28C4709FB7C | |||
| 2072 | MrsMajor3.0.exe | C:\Users\admin\AppData\Local\Temp\66BC.tmp\eulascr.exe | executable | |
MD5:8B1C352450E480D9320FCE5E6F2C8713 | SHA256:2C343174231B55E463CA044D19D47BD5842793C15954583EB340BFD95628516E | |||
| 2676 | eulascr.exe | C:\Users\admin\AppData\Local\Temp\66BC.tmp\winfool.exe | html | |
MD5:A11ADE174A72DC881796B28EA55F8F9E | SHA256:6C8F3A6076D60F6EC40206A79821FB99A738A3CEDBDA76E42757D38CF05EDC3F | |||
| 2712 | PLUGScheduler.exe | C:\ProgramData\PLUG\Logs\RUXIMLog.042.etl | binary | |
MD5:868E79A00A8204448B2FFC4F4D5C08EA | SHA256:148FE324431CB4C826BCF0436147D946AC389A877732612CF40629048B8517DC | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
10
TCP/UDP connections
67
DNS requests
34
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
4712 | MoUsoCoreWorker.exe | GET | 200 | 2.19.11.105:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
4712 | MoUsoCoreWorker.exe | GET | 200 | 23.37.237.227:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 23.37.237.227:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
5064 | SearchApp.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
6940 | SIHClient.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
1176 | svchost.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
6552 | backgroundTaskHost.exe | GET | 200 | 2.23.77.188:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAUZZSZEml49Gjh0j13P68w%3D | unknown | — | — | whitelisted |
6940 | SIHClient.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
4404 | svchost.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
4136 | backgroundTaskHost.exe | GET | 200 | 2.23.77.188:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAUZZSZEml49Gjh0j13P68w%3D | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
— | — | 4.231.128.59:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4712 | MoUsoCoreWorker.exe | 2.19.11.105:80 | crl.microsoft.com | Elisa Oyj | NL | whitelisted |
4712 | MoUsoCoreWorker.exe | 23.37.237.227:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
— | — | 23.37.237.227:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
3568 | svchost.exe | 4.231.128.59:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
5064 | SearchApp.exe | 2.16.204.153:443 | www.bing.com | Akamai International B.V. | DE | whitelisted |
5064 | SearchApp.exe | 2.17.190.73:80 | ocsp.digicert.com | AKAMAI-AS | DE | whitelisted |
3976 | svchost.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
3568 | svchost.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
google.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
www.bing.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
settings-win.data.microsoft.com |
| whitelisted |
drive.google.com |
| whitelisted |
drive.usercontent.google.com |
| whitelisted |
login.live.com |
| whitelisted |
go.microsoft.com |
| whitelisted |