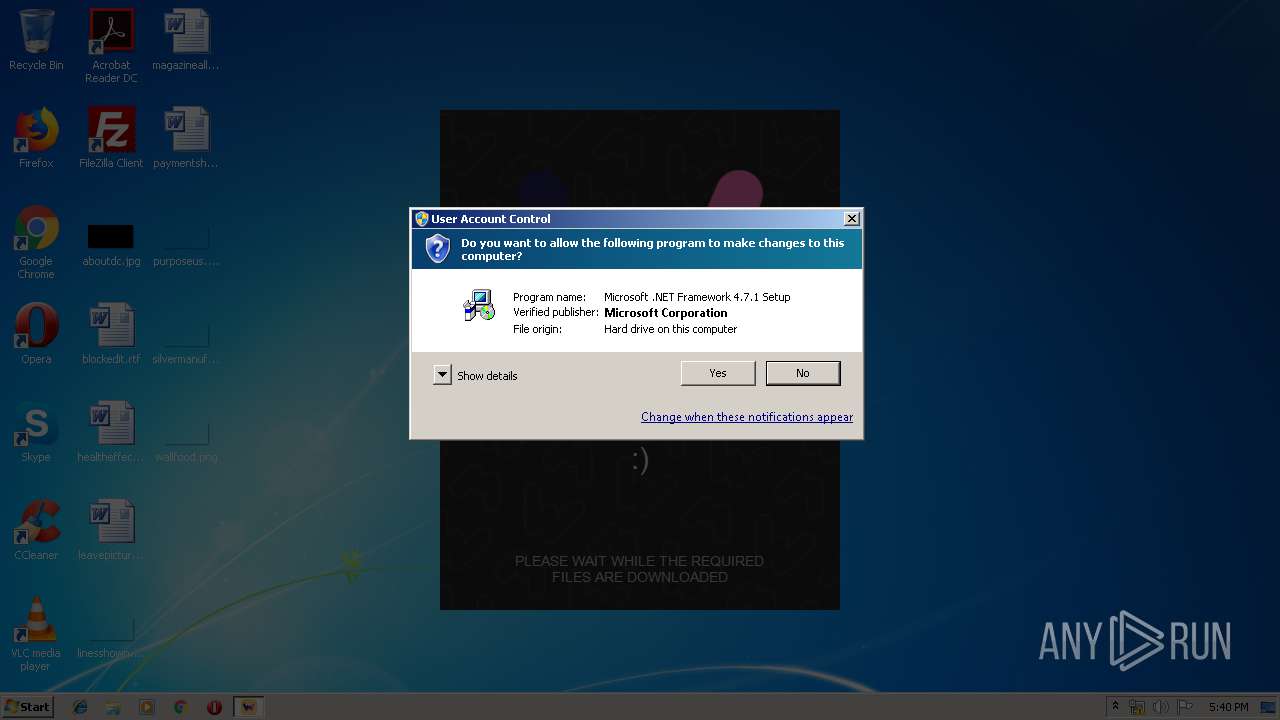
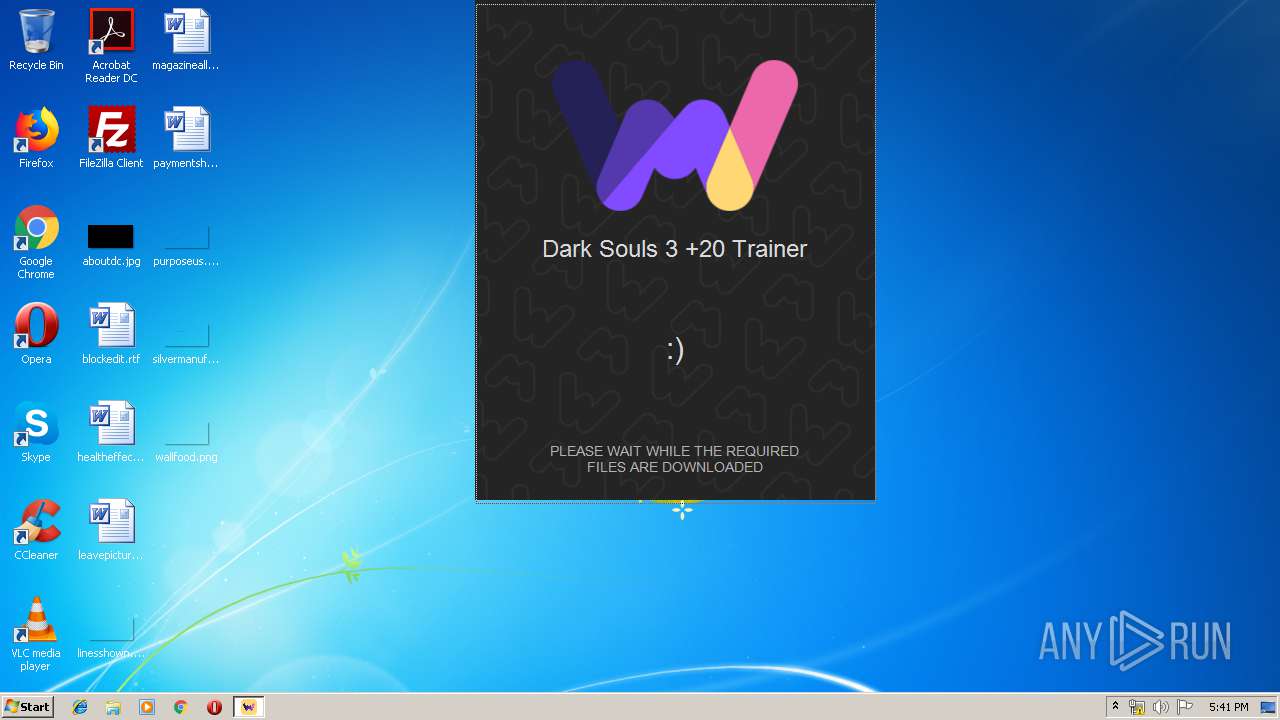
| File name: | Dark Souls 3 Trainer Setup.exe |
| Full analysis: | https://app.any.run/tasks/11f0a382-479e-478b-834f-300fe03a79d9 |
| Verdict: | Malicious activity |
| Analysis date: | March 21, 2019, 17:36:58 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows, UPX compressed |
| MD5: | 123C72727CBE31B21F9596580A963D1D |
| SHA1: | 28313BF9581E23D2BD8E3D3C08A1D38757B6EA91 |
| SHA256: | 4A5C87E97675A2D88575305526439C9F956DF6BAF8AB1A452198A7E3EDF6A209 |
| SSDEEP: | 1536:uP3C75n6UGB8M/kLu9qtz5IsH6aEu4afE91rkc3/oclgRV905bPy+9G:8Sx6UG+Fu9qwIXfE/kc3/ov2e+9 |
MALICIOUS
Application was dropped or rewritten from another process
- NDP8A66.exe (PID: 3020)
- NDP8A66.exe (PID: 3264)
- Setup.exe (PID: 2972)
- SetupUtility.exe (PID: 3028)
- SetupUtility.exe (PID: 1092)
- aspnet_regiis.exe (PID: 3928)
Loads dropped or rewritten executable
- Setup.exe (PID: 2972)
- ngen.exe (PID: 1184)
- mscorsvw.exe (PID: 3064)
- ngen.exe (PID: 3960)
- ngen.exe (PID: 2640)
Changes settings of System certificates
- Setup.exe (PID: 2972)
Loads the Task Scheduler COM API
- ngen.exe (PID: 1184)
- ngen.exe (PID: 3960)
- mscorsvw.exe (PID: 3064)
SUSPICIOUS
Creates files in the user directory
- Dark Souls 3 Trainer Setup.exe (PID: 2840)
Executable content was dropped or overwritten
- WeMod-6.0.3[1].exe (PID: 3192)
- NDP8A66.exe (PID: 3264)
- TMPC16C.tmp.exe (PID: 2456)
- Setup.exe (PID: 2972)
- msiexec.exe (PID: 2780)
Adds / modifies Windows certificates
- Setup.exe (PID: 2972)
Removes files from Windows directory
- lodctr.exe (PID: 352)
- lodctr.exe (PID: 2408)
- lodctr.exe (PID: 1100)
- lodctr.exe (PID: 3268)
- lodctr.exe (PID: 2312)
- aspnet_regiis.exe (PID: 3928)
- msiexec.exe (PID: 2780)
Creates COM task schedule object
- msiexec.exe (PID: 2780)
- aspnet_regiis.exe (PID: 3928)
Changes the autorun value in the registry
- msiexec.exe (PID: 2780)
Creates files in the Windows directory
- lodctr.exe (PID: 352)
- aspnet_regiis.exe (PID: 3928)
- ngen.exe (PID: 1184)
- mscorsvw.exe (PID: 3064)
- lodctr.exe (PID: 1100)
- lodctr.exe (PID: 2408)
- lodctr.exe (PID: 3268)
- lodctr.exe (PID: 2312)
- ngen.exe (PID: 3960)
- msiexec.exe (PID: 2780)
INFO
Dropped object may contain Bitcoin addresses
- Setup.exe (PID: 2972)
- msiexec.exe (PID: 2780)
Application launched itself
- msiexec.exe (PID: 2780)
Loads dropped or rewritten executable
- MsiExec.exe (PID: 2072)
- MsiExec.exe (PID: 1864)
- msiexec.exe (PID: 2780)
Creates a software uninstall entry
- msiexec.exe (PID: 2780)
Creates or modifies windows services
- msiexec.exe (PID: 2780)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | UPX compressed Win32 Executable (39.3) |
|---|---|---|
| .exe | | | Win32 EXE Yoda's Crypter (38.6) |
| .dll | | | Win32 Dynamic Link Library (generic) (9.5) |
| .exe | | | Win32 Executable (generic) (6.5) |
| .exe | | | Generic Win/DOS Executable (2.9) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2018:09:27 04:43:27+02:00 |
| PEType: | PE32 |
| LinkerVersion: | 14.15 |
| CodeSize: | 53248 |
| InitializedDataSize: | 16384 |
| UninitializedDataSize: | 77824 |
| EntryPoint: | 0x20950 |
| OSVersion: | 6 |
| ImageVersion: | - |
| SubsystemVersion: | 6 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 5.0.0.0 |
| ProductVersionNumber: | 5.0.0.0 |
| FileFlagsMask: | 0x003f |
| FileFlags: | (none) |
| FileOS: | Windows NT 32-bit |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | English (U.S.) |
| CharacterSet: | Unicode |
| CompanyName: | Daring Development Inc. |
| FileDescription: | WeMod Setup |
| FileVersion: | 5.0.0.0 |
| LegalCopyright: | Copyright (C) 2018 |
| ProductName: | WeMod |
| ProductVersion: | 5.0.0.0 |
Summary
| Architecture: | IMAGE_FILE_MACHINE_I386 |
|---|---|
| Subsystem: | IMAGE_SUBSYSTEM_WINDOWS_GUI |
| Compilation Date: | 27-Sep-2018 02:43:27 |
| Detected languages: |
|
| CompanyName: | Daring Development Inc. |
| FileDescription: | WeMod Setup |
| FileVersion: | 5.0.0.0 |
| LegalCopyright: | Copyright (C) 2018 |
| ProductName: | WeMod |
| ProductVersion: | 5.0.0.0 |
DOS Header
| Magic number: | MZ |
|---|---|
| Bytes on last page of file: | 0x0090 |
| Pages in file: | 0x0003 |
| Relocations: | 0x0000 |
| Size of header: | 0x0004 |
| Min extra paragraphs: | 0x0000 |
| Max extra paragraphs: | 0xFFFF |
| Initial SS value: | 0x0000 |
| Initial SP value: | 0x00B8 |
| Checksum: | 0x0000 |
| Initial IP value: | 0x0000 |
| Initial CS value: | 0x0000 |
| Overlay number: | 0x0000 |
| OEM identifier: | 0x0000 |
| OEM information: | 0x0000 |
| Address of NE header: | 0x00000108 |
PE Headers
| Signature: | PE |
|---|---|
| Machine: | IMAGE_FILE_MACHINE_I386 |
| Number of sections: | 3 |
| Time date stamp: | 27-Sep-2018 02:43:27 |
| Pointer to Symbol Table: | 0x00000000 |
| Number of symbols: | 0 |
| Size of Optional Header: | 0x00E0 |
| Characteristics: |
|
Sections
Name | Virtual Address | Virtual Size | Raw Size | Charateristics | Entropy |
|---|---|---|---|---|---|
UPX0 | 0x00001000 | 0x00013000 | 0x00000000 | IMAGE_SCN_CNT_UNINITIALIZED_DATA, IMAGE_SCN_MEM_EXECUTE, IMAGE_SCN_MEM_READ, IMAGE_SCN_MEM_WRITE | 0 |
UPX1 | 0x00014000 | 0x0000D000 | 0x0000CC00 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_EXECUTE, IMAGE_SCN_MEM_READ, IMAGE_SCN_MEM_WRITE | 7.91245 |
.rsrc | 0x00021000 | 0x00004000 | 0x00003800 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ, IMAGE_SCN_MEM_WRITE | 7.67704 |
Resources
Title | Entropy | Size | Codepage | Language | Type |
|---|---|---|---|---|---|
1 | 5.14523 | 1556 | UNKNOWN | English - United States | RT_MANIFEST |
102 | 1.51664 | 20 | UNKNOWN | English - United States | RT_GROUP_ICON |
Imports
GDI32.dll |
KERNEL32.DLL |
SHELL32.dll |
SHLWAPI.dll |
USER32.dll |
WININET.dll |
gdiplus.dll |
urlmon.dll |
Total processes
97
Monitored processes
42
Malicious processes
14
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 352 | "C:\Windows\system32\lodctr.exe" "C:\Windows\Microsoft.NET\Framework\v4.0.30319\netmemorycache.ini" | C:\Windows\system32\lodctr.exe | — | MsiExec.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Load PerfMon Counters Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 584 | "C:\Windows\system32\lodctr.exe" /m:"C:\Windows\Microsoft.NET\Framework\v4.0.30319\WorkflowServiceHostPerformanceCounters.man" | C:\Windows\system32\lodctr.exe | — | MsiExec.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Load PerfMon Counters Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1092 | SetupUtility.exe /screboot | C:\06ef353ac8ac6208cbf668e0e2c033\SetupUtility.exe | — | Setup.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Microsoft .NET Framework 4.5 Setup Exit code: 0 Version: 14.7.2558.0 built by: NET471REL1 Modules
| |||||||||||||||
| 1100 | "C:\Windows\system32\lodctr.exe" C:\Windows\Microsoft.NET\Framework\v4.0.30319\_Networkingperfcounters.ini | C:\Windows\system32\lodctr.exe | — | MsiExec.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Load PerfMon Counters Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1184 | C:\Windows\Microsoft.NET\Framework\v4.0.30319\ngen.exe update /queue | C:\Windows\Microsoft.NET\Framework\v4.0.30319\ngen.exe | — | MsiExec.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Microsoft Common Language Runtime native compiler Exit code: 0 Version: 4.7.2558.0 built by: NET471REL1 Modules
| |||||||||||||||
| 1240 | C:\Windows\Microsoft.NET\Framework\v4.0.30319\mscorsvw.exe -StartupEvent 174 -InterruptEvent 0 -NGENProcess 184 -Pipe 16c -Comment "NGen Worker Process" | C:\Windows\Microsoft.NET\Framework\v4.0.30319\mscorsvw.exe | — | ngen.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: .NET Runtime Optimization Service Exit code: 0 Version: 4.7.2558.0 built by: NET471REL1 | |||||||||||||||
| 1412 | "C:\Windows\Microsoft.NET\Framework\v4.0.30319\regtlibv12.exe" "C:\Windows\Microsoft.NET\Framework\v4.0.30319\System.Drawing.tlb" | C:\Windows\Microsoft.NET\Framework\v4.0.30319\regtlibv12.exe | — | MsiExec.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: RegTLib Exit code: 0 Version: 14.7.2558.0 built by: NET471REL1 Modules
| |||||||||||||||
| 1672 | "C:\Windows\Microsoft.NET\Framework\v4.0.30319\ServiceModelReg.exe" -msi -ia -v | C:\Windows\Microsoft.NET\Framework\v4.0.30319\ServiceModelReg.exe | — | MsiExec.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: WCF Generic Command for Vista Setup Exit code: 0 Version: 4.7.2558.0 built by: NET471REL1 Modules
| |||||||||||||||
| 1864 | C:\Windows\system32\MsiExec.exe -Embedding 8123DFE29FA5B604B2A4C10E5127CE96 M Global\MSI0000 | C:\Windows\system32\MsiExec.exe | — | msiexec.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows® installer Exit code: 0 Version: 5.0.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2072 | C:\Windows\system32\MsiExec.exe -Embedding 5E47125218BA271C3886E12489FC85F5 | C:\Windows\system32\MsiExec.exe | — | msiexec.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows® installer Exit code: 0 Version: 5.0.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
Total events
20 178
Read events
7 294
Write events
11 066
Delete events
1 818
Modification events
| (PID) Process: | (2840) Dark Souls 3 Trainer Setup.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\Dark Souls 3 Trainer Setup_RASAPI32 |
| Operation: | write | Name: | EnableFileTracing |
Value: 0 | |||
| (PID) Process: | (2840) Dark Souls 3 Trainer Setup.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\Dark Souls 3 Trainer Setup_RASAPI32 |
| Operation: | write | Name: | EnableConsoleTracing |
Value: 0 | |||
| (PID) Process: | (2840) Dark Souls 3 Trainer Setup.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\Dark Souls 3 Trainer Setup_RASAPI32 |
| Operation: | write | Name: | FileTracingMask |
Value: 4294901760 | |||
| (PID) Process: | (2840) Dark Souls 3 Trainer Setup.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\Dark Souls 3 Trainer Setup_RASAPI32 |
| Operation: | write | Name: | ConsoleTracingMask |
Value: 4294901760 | |||
| (PID) Process: | (2840) Dark Souls 3 Trainer Setup.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\Dark Souls 3 Trainer Setup_RASAPI32 |
| Operation: | write | Name: | MaxFileSize |
Value: 1048576 | |||
| (PID) Process: | (2840) Dark Souls 3 Trainer Setup.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\Dark Souls 3 Trainer Setup_RASAPI32 |
| Operation: | write | Name: | FileDirectory |
Value: %windir%\tracing | |||
| (PID) Process: | (2840) Dark Souls 3 Trainer Setup.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\Dark Souls 3 Trainer Setup_RASMANCS |
| Operation: | write | Name: | EnableFileTracing |
Value: 0 | |||
| (PID) Process: | (2840) Dark Souls 3 Trainer Setup.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\Dark Souls 3 Trainer Setup_RASMANCS |
| Operation: | write | Name: | EnableConsoleTracing |
Value: 0 | |||
| (PID) Process: | (2840) Dark Souls 3 Trainer Setup.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\Dark Souls 3 Trainer Setup_RASMANCS |
| Operation: | write | Name: | FileTracingMask |
Value: 4294901760 | |||
| (PID) Process: | (2840) Dark Souls 3 Trainer Setup.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\Dark Souls 3 Trainer Setup_RASMANCS |
| Operation: | write | Name: | ConsoleTracingMask |
Value: 4294901760 | |||
Executable files
523
Suspicious files
21
Text files
220
Unknown types
5
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2840 | Dark Souls 3 Trainer Setup.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\H6QNMHE9\WeMod-6.0.3[1].exe | — | |
MD5:— | SHA256:— | |||
| 3192 | WeMod-6.0.3[1].exe | C:\Users\admin\AppData\Local\Temp\NDP8A66.exe | — | |
MD5:— | SHA256:— | |||
| 2840 | Dark Souls 3 Trainer Setup.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Cookies\admin@wemod[1].txt | text | |
MD5:— | SHA256:— | |||
| 3264 | NDP8A66.exe | C:\06ef353ac8ac6208cbf668e0e2c033\watermark.bmp | image | |
MD5:B0075CEE80173D764C0237E840BA5879 | SHA256:AB18374B3AAB10E5979E080D0410579F9771DB888BA1B80A5D81BA8896E2D33A | |||
| 3264 | NDP8A66.exe | C:\06ef353ac8ac6208cbf668e0e2c033\header.bmp | image | |
MD5:41C22EFA84CA74F0CE7076EB9A482E38 | SHA256:255025A0D79EF2DAC04BD610363F966EF58328400BF31E1F8915E676478CD750 | |||
| 3264 | NDP8A66.exe | C:\06ef353ac8ac6208cbf668e0e2c033\SplashScreen.bmp | image | |
MD5:BC32088BFAA1C76BA4B56639A2DEC592 | SHA256:B05141DBC71669A7872A8E735E5E43A7F9713D4363B7A97543E1E05DCD7470A7 | |||
| 3264 | NDP8A66.exe | C:\06ef353ac8ac6208cbf668e0e2c033\Graphics\stop.ico | image | |
MD5:7D1BCCCE4F2EE7C824C6304C4A2F9736 | SHA256:BFB0332DF9FA20DEA30F0DB53CEAA389DF2722FD1ACF37F40AF954237717532D | |||
| 3192 | WeMod-6.0.3[1].exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\JGRR2OYX\NDP471-KB4033344-Web[1].exe | executable | |
MD5:4FB795478A8F346C337A1F84BACCC85B | SHA256:65A7CB8FD1C7C529C40345B4746818F8947BE736AA105007DFCC57B05897ED62 | |||
| 3264 | NDP8A66.exe | C:\06ef353ac8ac6208cbf668e0e2c033\Graphics\Print.ico | image | |
MD5:D39BAD9DDA7B91613CB29B6BD55F0901 | SHA256:D80FFEB020927F047C11FC4D9F34F985E0C7E5DFEA9FB23F2BC134874070E4E6 | |||
| 3264 | NDP8A66.exe | C:\06ef353ac8ac6208cbf668e0e2c033\Graphics\Rotate3.ico | image | |
MD5:0ADE6BE0DF29400E5534AA71ABFA03F6 | SHA256:C2F6FAA18B16F728AE5536D5992CC76A4B83530A1EA74B9D11BEBDF871CF3B4E | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
17
TCP/UDP connections
9
DNS requests
6
Threats
2
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
— | — | HEAD | 200 | 2.18.233.19:80 | http://download.microsoft.com/download/2/F/4/2F4F48F4-D980-43AA-906A-8FFF40BCB832/Windows6.1-KB4019990-x86.msu | unknown | — | — | whitelisted |
— | — | GET | 302 | 104.109.80.115:80 | http://go.microsoft.com/fwlink/?prd=11324&pver=netfx&sbp=Net471Rel1&plcid=0x409&clcid=0x409&ar=02558.00&sar=x86&o1=netfx_Full.mzz | NL | — | — | whitelisted |
2972 | Setup.exe | GET | 200 | 2.16.186.74:80 | http://crl.microsoft.com/pki/crl/products/microsoftrootcert.crl | unknown | der | 781 b | whitelisted |
2972 | Setup.exe | GET | 200 | 2.16.186.74:80 | http://crl.microsoft.com/pki/crl/products/MicrosoftTimeStampPCA.crl | unknown | der | 550 b | whitelisted |
— | — | HEAD | 302 | 104.109.80.115:80 | http://go.microsoft.com/fwlink/?prd=11324&pver=netfx&sbp=Net471Rel1&plcid=0x409&clcid=0x409&ar=02558.00&sar=amd64&o1=netfx_Full_x86.msi | NL | — | — | whitelisted |
— | — | GET | 302 | 104.109.80.115:80 | http://go.microsoft.com/fwlink/?prd=11324&pver=netfx&sbp=Net471Rel1&plcid=0x409&clcid=0x409&ar=02558.00&sar=amd64&o1=netfx_Full_x86.msi | NL | — | — | whitelisted |
— | — | HEAD | 302 | 104.109.80.115:80 | http://go.microsoft.com/fwlink/?LinkId=848159 | NL | — | — | whitelisted |
— | — | GET | 302 | 104.109.80.115:80 | http://go.microsoft.com/fwlink/?LinkId=848159 | NL | — | — | whitelisted |
— | — | GET | 200 | 2.18.233.19:80 | http://download.microsoft.com/download/2/F/4/2F4F48F4-D980-43AA-906A-8FFF40BCB832/Windows6.1-KB4019990-x86.msu | unknown | compressed | 1.36 Mb | whitelisted |
2972 | Setup.exe | GET | 200 | 2.23.106.83:80 | http://www.microsoft.com/pkiops/crl/MicCodSigPCA2011_2011-07-08.crl | unknown | der | 813 b | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
2840 | Dark Souls 3 Trainer Setup.exe | 104.24.26.12:443 | api.wemod.com | Cloudflare Inc | US | shared |
3192 | WeMod-6.0.3[1].exe | 104.24.26.12:443 | api.wemod.com | Cloudflare Inc | US | shared |
3192 | WeMod-6.0.3[1].exe | 2.18.233.19:443 | download.microsoft.com | Akamai International B.V. | — | whitelisted |
2972 | Setup.exe | 2.16.186.74:80 | crl.microsoft.com | Akamai International B.V. | — | whitelisted |
— | — | 104.109.80.115:80 | go.microsoft.com | Akamai International B.V. | NL | whitelisted |
— | — | 2.18.233.19:443 | download.microsoft.com | Akamai International B.V. | — | whitelisted |
— | — | 2.18.233.19:80 | download.microsoft.com | Akamai International B.V. | — | whitelisted |
2972 | Setup.exe | 2.23.106.83:80 | www.microsoft.com | Akamai International B.V. | — | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
api.wemod.com |
| unknown |
storage-cdn.wemod.com |
| suspicious |
download.microsoft.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
go.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2840 | Dark Souls 3 Trainer Setup.exe | Generic Protocol Command Decode | SURICATA STREAM excessive retransmissions |
3192 | WeMod-6.0.3[1].exe | Generic Protocol Command Decode | SURICATA STREAM excessive retransmissions |