| File name: | 4a29f762e7a3910c4b52bb55e27cdc5efcb54f79c9f2f50b5a84c72115ec9502 |
| Full analysis: | https://app.any.run/tasks/f61273cf-e24b-4286-ac9a-1551c5412eac |
| Verdict: | Malicious activity |
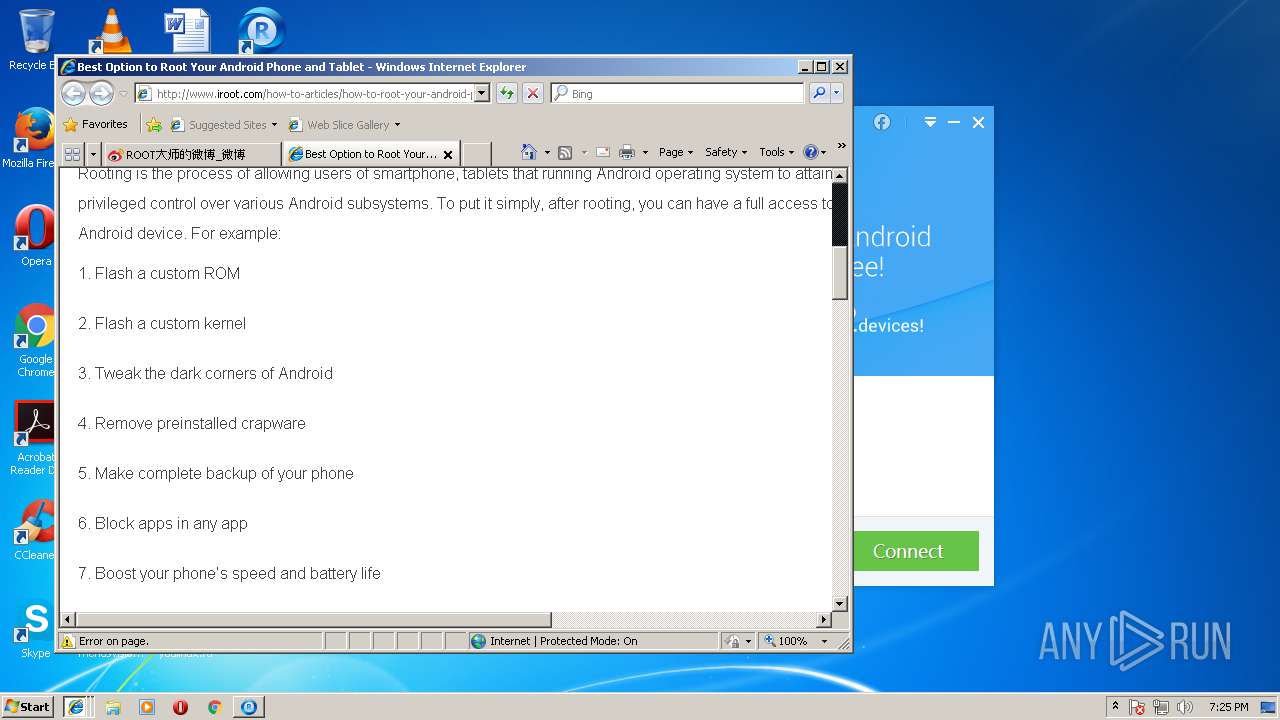
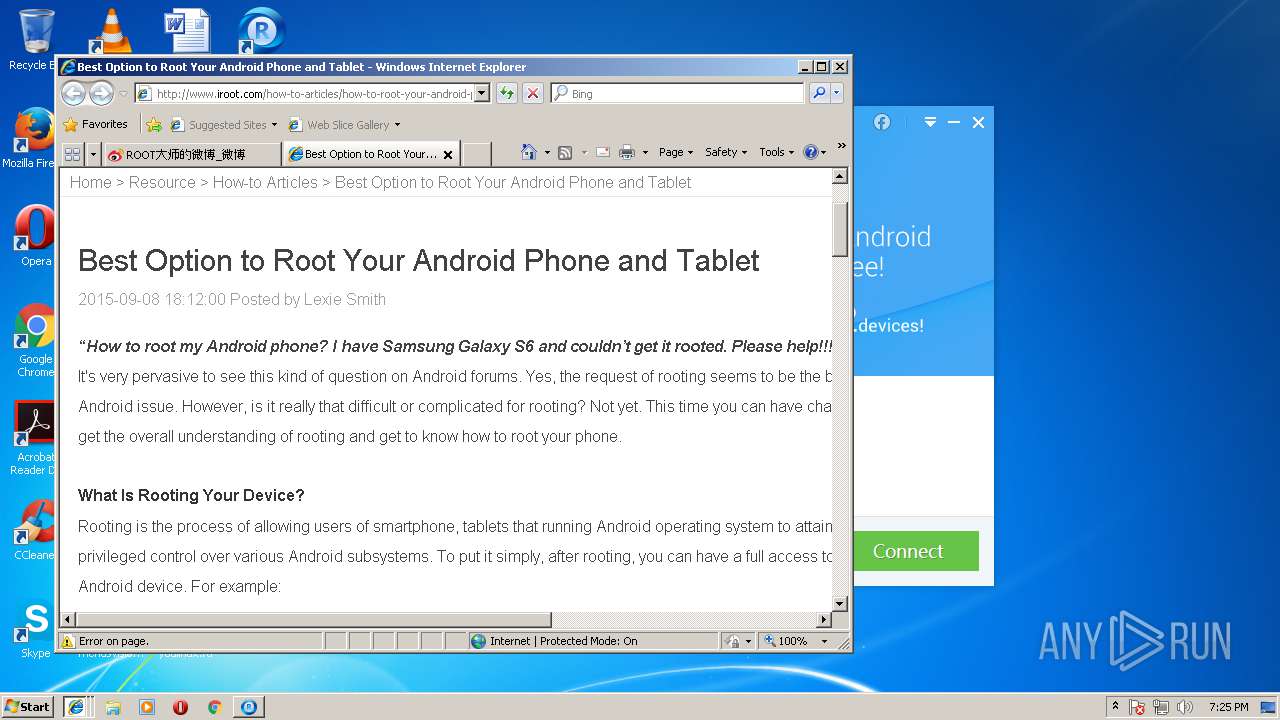
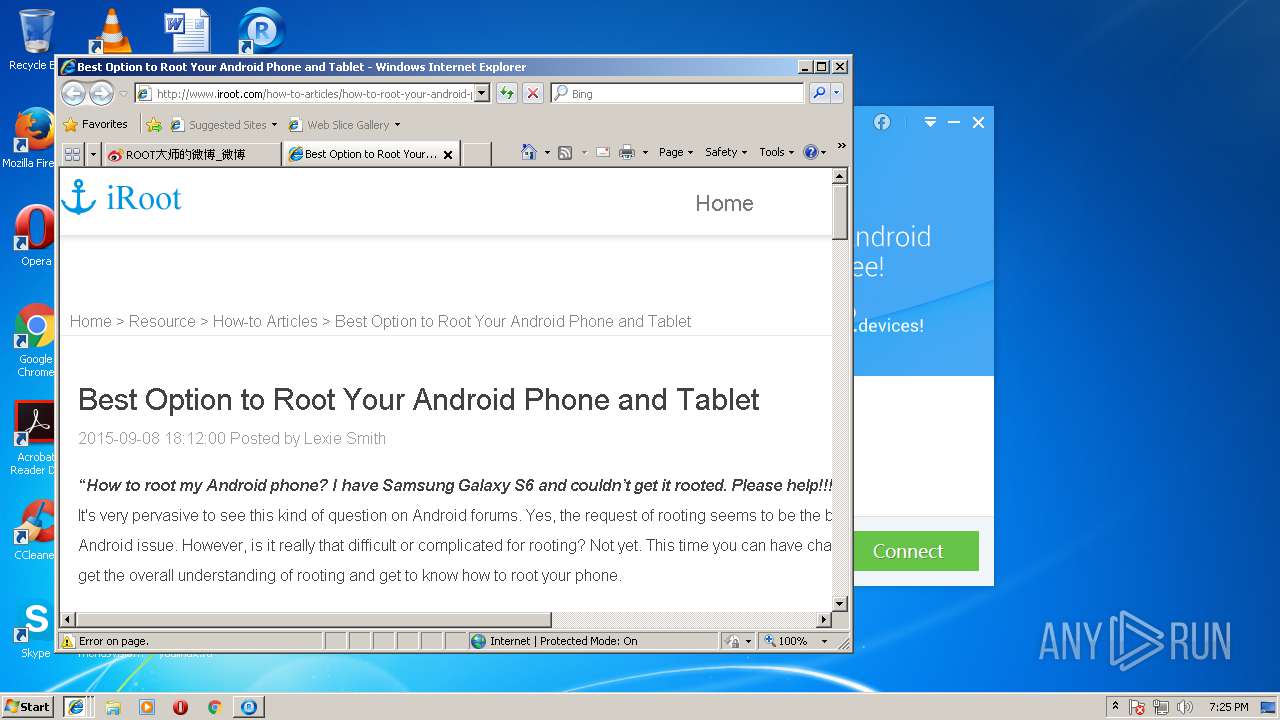
| Threats: | A loader is malicious software that infiltrates devices to deliver malicious payloads. This malware is capable of infecting victims’ computers, analyzing their system information, and installing other types of threats, such as trojans or stealers. Criminals usually deliver loaders through phishing emails and links by relying on social engineering to trick users into downloading and running their executables. Loaders employ advanced evasion and persistence tactics to avoid detection. |
| Analysis date: | May 09, 2018, 18:21:33 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows |
| MD5: | 5FF7C44810D1B0759B8CF5F8965F1C7A |
| SHA1: | 8B00576A871EED67AE515E9BAAA2A392B63D51F0 |
| SHA256: | 4A29F762E7A3910C4B52BB55E27CDC5EFCB54F79C9F2F50B5A84C72115EC9502 |
| SSDEEP: | 98304:FylpmFVXii95yQLc4Bnj73kCRC7Mbu4yGNCQHF+HXu0RhL5UGLDfeZoIpJ:glkPXjh7BlCIbu4ywHiRhWqDfPSJ |
MALICIOUS
Application was dropped or rewritten from another process
- Root.exe (PID: 2228)
- RomasterConnection.exe (PID: 2840)
- romaster_daemon.exe (PID: 2464)
- _iu14D2N.tmp (PID: 3876)
- unins000.exe (PID: 3188)
- Root.exe (PID: 3792)
- romaster_daemon.exe (PID: 3816)
- RomasterConnection.exe (PID: 2800)
Application loaded dropped or rewritten executable
- Root.exe (PID: 2228)
- RomasterConnection.exe (PID: 2840)
- romaster_daemon.exe (PID: 2464)
- _iu14D2N.tmp (PID: 3876)
- Root.exe (PID: 3792)
- RomasterConnection.exe (PID: 2800)
- romaster_daemon.exe (PID: 3816)
SUSPICIOUS
Creates files in the user directory
- RomasterConnection.exe (PID: 2840)
- FlashUtil32_26_0_0_137_ActiveX.exe (PID: 3300)
- Root.exe (PID: 3792)
- vroot_1896352004.tmp (PID: 4076)
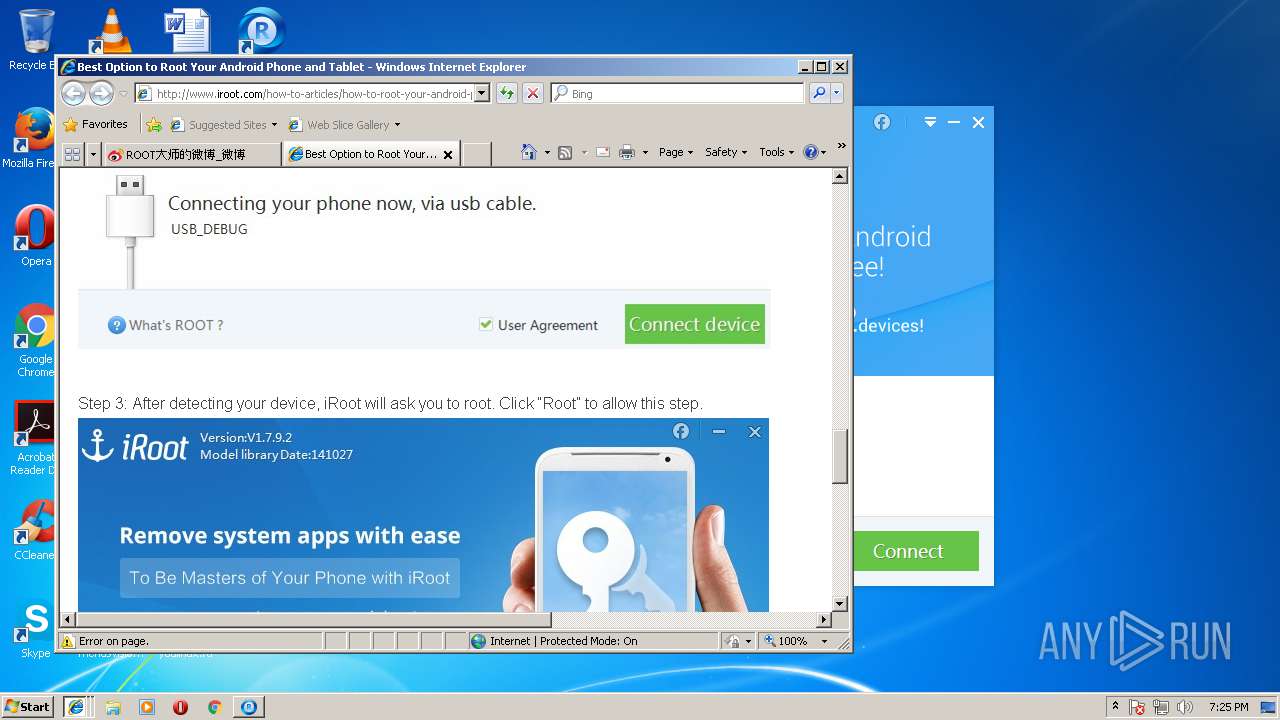
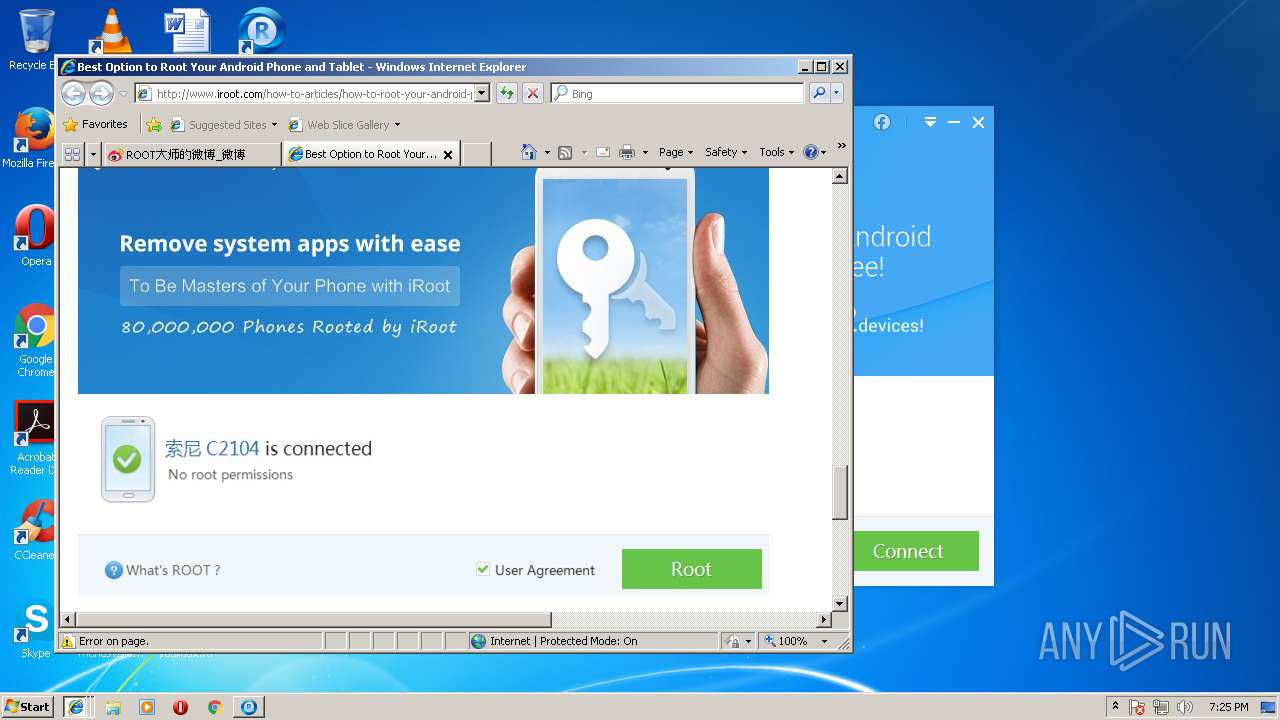
Starts Internet Explorer
- Root.exe (PID: 2228)
Reads Windows owner settings
- vroot_1896352004.tmp (PID: 4076)
Reads the Windows organization settings
- vroot_1896352004.tmp (PID: 4076)
Starts application with an unusual extension
- unins000.exe (PID: 3188)
Searches for installed software
- vroot_1896352004.tmp (PID: 4076)
Starts CMD.EXE for commands execution
- vroot_1896352004.tmp (PID: 4076)
Reads internet explorer settings
- Root.exe (PID: 3792)
INFO
Dropped object may contain URL's
- 4a29f762e7a3910c4b52bb55e27cdc5efcb54f79c9f2f50b5a84c72115ec9502.exe (PID: 2988)
- 4a29f762e7a3910c4b52bb55e27cdc5efcb54f79c9f2f50b5a84c72115ec9502.exe (PID: 3460)
- 4a29f762e7a3910c4b52bb55e27cdc5efcb54f79c9f2f50b5a84c72115ec9502.tmp (PID: 3824)
- iexplore.exe (PID: 2628)
- iexplore.exe (PID: 3496)
- unins000.exe (PID: 3188)
- iexplore.exe (PID: 3040)
- Root.exe (PID: 3792)
- vroot_1896352004.tmp (PID: 4076)
Application was dropped or rewritten from another process
- 4a29f762e7a3910c4b52bb55e27cdc5efcb54f79c9f2f50b5a84c72115ec9502.tmp (PID: 3632)
- 4a29f762e7a3910c4b52bb55e27cdc5efcb54f79c9f2f50b5a84c72115ec9502.tmp (PID: 3824)
- vroot_1896352004.tmp (PID: 2724)
- vroot_1896352004.tmp (PID: 4076)
Loads rich edit control libraries
- 4a29f762e7a3910c4b52bb55e27cdc5efcb54f79c9f2f50b5a84c72115ec9502.tmp (PID: 3824)
- FlashUtil32_26_0_0_137_ActiveX.exe (PID: 3300)
Application loaded dropped or rewritten executable
- 4a29f762e7a3910c4b52bb55e27cdc5efcb54f79c9f2f50b5a84c72115ec9502.tmp (PID: 3824)
- vroot_1896352004.tmp (PID: 4076)
Creates files in the program directory
- 4a29f762e7a3910c4b52bb55e27cdc5efcb54f79c9f2f50b5a84c72115ec9502.tmp (PID: 3824)
- vroot_1896352004.tmp (PID: 4076)
Creates a software uninstall entry
- 4a29f762e7a3910c4b52bb55e27cdc5efcb54f79c9f2f50b5a84c72115ec9502.tmp (PID: 3824)
- vroot_1896352004.tmp (PID: 4076)
Changes internet zones settings
- iexplore.exe (PID: 2628)
Application launched itself
- iexplore.exe (PID: 2628)
Reads settings of System Certificates
- iexplore.exe (PID: 2628)
- iexplore.exe (PID: 3496)
Reads Internet Cache Settings
- iexplore.exe (PID: 3496)
- iexplore.exe (PID: 2628)
- iexplore.exe (PID: 3040)
Dropped object may contain Bitcoin addresses
- iexplore.exe (PID: 3040)
- vroot_1896352004.tmp (PID: 4076)
Adds / modifies Windows certificates
- iexplore.exe (PID: 2628)
Reads internet explorer settings
- iexplore.exe (PID: 3040)
- iexplore.exe (PID: 3496)
Creates files in the user directory
- iexplore.exe (PID: 3040)
- iexplore.exe (PID: 3496)
- iexplore.exe (PID: 2628)
Changes settings of System certificates
- iexplore.exe (PID: 2628)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Inno Setup installer (74.3) |
|---|---|---|
| .exe | | | Win32 Executable Delphi generic (9.6) |
| .scr | | | Windows screen saver (8.8) |
| .exe | | | Win32 Executable (generic) (3) |
| .exe | | | Win16/32 Executable Delphi generic (1.4) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 1992:06:20 00:22:17+02:00 |
| PEType: | PE32 |
| LinkerVersion: | 2.25 |
| CodeSize: | 40448 |
| InitializedDataSize: | 204800 |
| UninitializedDataSize: | - |
| EntryPoint: | 0xa5f8 |
| OSVersion: | 1 |
| ImageVersion: | 6 |
| SubsystemVersion: | 4 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 1.7.0.3882 |
| ProductVersionNumber: | 1.7.0.3882 |
| FileFlagsMask: | 0x003f |
| FileFlags: | (none) |
| FileOS: | Win32 |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | Neutral |
| CharacterSet: | Unicode |
| Comments: | This installation was built with Inno Setup. |
| CompanyName: | 深圳市信一网络有限公司 |
| FileDescription: | ROOT大师 Setup |
| FileVersion: | 1.7.0.3882 |
| LegalCopyright: | Copyright © 2013 Xinyi All Rights Reserved |
| ProductName: | ROOT大师 |
| ProductVersion: | 1.7.0.3882 |
Summary
| Architecture: | IMAGE_FILE_MACHINE_I386 |
|---|---|
| Subsystem: | IMAGE_SUBSYSTEM_WINDOWS_GUI |
| Compilation Date: | 19-Jun-1992 22:22:17 |
| Detected languages: |
|
| Comments: | This installation was built with Inno Setup. |
| CompanyName: | 深圳市信一网络有限公司 |
| FileDescription: | ROOT大师 Setup |
| FileVersion: | 1.7.0.3882 |
| LegalCopyright: | Copyright © 2013 Xinyi All Rights Reserved |
| ProductName: | ROOT大师 |
| ProductVersion: | 1.7.0.3882 |
DOS Header
| Magic number: | MZ |
|---|---|
| Bytes on last page of file: | 0x0050 |
| Pages in file: | 0x0002 |
| Relocations: | 0x0000 |
| Size of header: | 0x0004 |
| Min extra paragraphs: | 0x000F |
| Max extra paragraphs: | 0xFFFF |
| Initial SS value: | 0x0000 |
| Initial SP value: | 0x00B8 |
| Checksum: | 0x0000 |
| Initial IP value: | 0x0000 |
| Initial CS value: | 0x0000 |
| Overlay number: | 0x001A |
| OEM identifier: | 0x0000 |
| OEM information: | 0x0000 |
| Address of NE header: | 0x00000100 |
PE Headers
| Signature: | PE |
|---|---|
| Machine: | IMAGE_FILE_MACHINE_I386 |
| Number of sections: | 8 |
| Time date stamp: | 19-Jun-1992 22:22:17 |
| Pointer to Symbol Table: | 0x00000000 |
| Number of symbols: | 0 |
| Size of Optional Header: | 0x00E0 |
| Characteristics: |
|
Sections
Name | Virtual Address | Virtual Size | Raw Size | Charateristics | Entropy |
|---|---|---|---|---|---|
CODE | 0x00001000 | 0x00009D30 | 0x00009E00 | IMAGE_SCN_CNT_CODE, IMAGE_SCN_MEM_EXECUTE, IMAGE_SCN_MEM_READ | 6.63177 |
DATA | 0x0000B000 | 0x00000250 | 0x00000400 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ, IMAGE_SCN_MEM_WRITE | 2.75182 |
BSS | 0x0000C000 | 0x00000E8C | 0x00000000 | IMAGE_SCN_MEM_READ, IMAGE_SCN_MEM_WRITE | 0 |
.idata | 0x0000D000 | 0x00000950 | 0x00000A00 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ, IMAGE_SCN_MEM_WRITE | 4.43073 |
.tls | 0x0000E000 | 0x00000008 | 0x00000000 | IMAGE_SCN_MEM_READ, IMAGE_SCN_MEM_WRITE | 0 |
.rdata | 0x0000F000 | 0x00000018 | 0x00000200 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ, IMAGE_SCN_MEM_SHARED | 0.204488 |
.reloc | 0x00010000 | 0x000008C4 | 0x00000000 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ, IMAGE_SCN_MEM_SHARED | 0 |
.rsrc | 0x00011000 | 0x00030FB4 | 0x00031000 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ, IMAGE_SCN_MEM_SHARED | 6.17533 |
Resources
Title | Entropy | Size | Codepage | Language | Type |
|---|---|---|---|---|---|
1 | 5.08452 | 1444 | Latin 1 / Western European | English - United States | RT_MANIFEST |
2 | 5.35417 | 67624 | Latin 1 / Western European | English - United States | RT_ICON |
3 | 5.64911 | 38056 | Latin 1 / Western European | English - United States | RT_ICON |
4 | 5.67058 | 21640 | Latin 1 / Western European | English - United States | RT_ICON |
5 | 5.64416 | 16936 | Latin 1 / Western European | English - United States | RT_ICON |
6 | 5.86331 | 9640 | Latin 1 / Western European | English - United States | RT_ICON |
7 | 5.93423 | 4264 | Latin 1 / Western European | English - United States | RT_ICON |
8 | 6.10543 | 2440 | Latin 1 / Western European | English - United States | RT_ICON |
9 | 6.16006 | 1128 | Latin 1 / Western European | English - United States | RT_ICON |
4089 | 3.21823 | 754 | Latin 1 / Western European | UNKNOWN | RT_STRING |
Imports
advapi32.dll |
comctl32.dll |
kernel32.dll |
oleaut32.dll |
user32.dll |
Total processes
66
Monitored processes
22
Malicious processes
10
Suspicious processes
5
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 332 | "C:\Windows\system32\cmd.exe" /c ping 127.0.0.1 -n 3 >nul & del /f /q "C:\Users\admin\AppData\Local\Temp\Root\autoupdate\vroot_1896352004.exe" | C:\Windows\system32\cmd.exe | — | vroot_1896352004.tmp | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 2228 | "C:\Program Files\VROOT\Root.exe" | C:\Program Files\VROOT\Root.exe | 4a29f762e7a3910c4b52bb55e27cdc5efcb54f79c9f2f50b5a84c72115ec9502.tmp | ||||||||||||
User: admin Company: 信一网络 Integrity Level: MEDIUM Description: Root大师 Exit code: 0 Version: 1, 7, 0, 0 Modules
| |||||||||||||||
| 2464 | "C:\Program Files\VROOT\romaster_daemon.exe" fork-server server | C:\Program Files\VROOT\romaster_daemon.exe | — | RomasterConnection.exe | |||||||||||
User: admin Integrity Level: MEDIUM Description: Android Debug Bridge Exit code: 0 Version: 1.0.26.21 Modules
| |||||||||||||||
| 2468 | ping 127.0.0.1 -n 3 | C:\Windows\system32\PING.EXE | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: TCP/IP Ping Command Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2628 | "C:\Program Files\Internet Explorer\iexplore.exe" -nohome | C:\Program Files\Internet Explorer\iexplore.exe | — | Root.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Internet Explorer Exit code: 0 Version: 8.00.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2724 | "C:\Users\admin\AppData\Local\Temp\is-AMK5E.tmp\vroot_1896352004.tmp" /SL5="$301B6,37926101,308736,C:\Users\admin\AppData\Local\Temp\Root\autoupdate\vroot_1896352004.exe" /SILENT | C:\Users\admin\AppData\Local\Temp\is-AMK5E.tmp\vroot_1896352004.tmp | — | vroot_1896352004.exe | |||||||||||
User: admin Integrity Level: MEDIUM Description: Setup/Uninstall Exit code: 0 Version: 51.1052.0.0 Modules
| |||||||||||||||
| 2800 | "C:\Program Files\VROOT\RomasterConnection.exe" /hwnd=328120 /lcid=1033 | C:\Program Files\VROOT\RomasterConnection.exe | — | Root.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 2840 | "C:\Program Files\VROOT\RomasterConnection.exe" /hwnd=65986 | C:\Program Files\VROOT\RomasterConnection.exe | Root.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 2956 | "C:\Users\admin\AppData\Local\Temp\Root\autoupdate\vroot_1896352004.exe" /SPAWNWND=$30140 /NOTIFYWND=$301B6 /SILENT | C:\Users\admin\AppData\Local\Temp\Root\autoupdate\vroot_1896352004.exe | vroot_1896352004.tmp | ||||||||||||
User: admin Company: Integrity Level: HIGH Description: Exit code: 0 Version: 1.8.9.21061 Modules
| |||||||||||||||
| 2988 | "C:\Users\admin\AppData\Local\Temp\4a29f762e7a3910c4b52bb55e27cdc5efcb54f79c9f2f50b5a84c72115ec9502.exe" | C:\Users\admin\AppData\Local\Temp\4a29f762e7a3910c4b52bb55e27cdc5efcb54f79c9f2f50b5a84c72115ec9502.exe | explorer.exe | ||||||||||||
User: admin Company: 深圳市信一网络有限公司 Integrity Level: MEDIUM Description: ROOT大师 Setup Exit code: 0 Version: 1.7.0.3882 Modules
| |||||||||||||||
Total events
3 794
Read events
2 931
Write events
838
Delete events
25
Modification events
| (PID) Process: | (3824) 4a29f762e7a3910c4b52bb55e27cdc5efcb54f79c9f2f50b5a84c72115ec9502.tmp | Key: | HKEY_CURRENT_USER\Software\Microsoft\RestartManager\Session0000 |
| Operation: | write | Name: | Owner |
Value: F00E0000846EAE9DC2E7D301 | |||
| (PID) Process: | (3824) 4a29f762e7a3910c4b52bb55e27cdc5efcb54f79c9f2f50b5a84c72115ec9502.tmp | Key: | HKEY_CURRENT_USER\Software\Microsoft\RestartManager\Session0000 |
| Operation: | write | Name: | SessionHash |
Value: 1339E3918C0851BA61D9BEA4F38216269D849940040AE4B04BE7F34371F3A7CC | |||
| (PID) Process: | (3824) 4a29f762e7a3910c4b52bb55e27cdc5efcb54f79c9f2f50b5a84c72115ec9502.tmp | Key: | HKEY_CURRENT_USER\Software\Microsoft\RestartManager\Session0000 |
| Operation: | write | Name: | Sequence |
Value: 1 | |||
| (PID) Process: | (3824) 4a29f762e7a3910c4b52bb55e27cdc5efcb54f79c9f2f50b5a84c72115ec9502.tmp | Key: | HKEY_CURRENT_USER\Software\Microsoft\RestartManager\Session0000 |
| Operation: | write | Name: | RegFiles0000 |
Value: C:\Program Files\VROOT\ISTask.dll | |||
| (PID) Process: | (3824) 4a29f762e7a3910c4b52bb55e27cdc5efcb54f79c9f2f50b5a84c72115ec9502.tmp | Key: | HKEY_CURRENT_USER\Software\Microsoft\RestartManager\Session0000 |
| Operation: | write | Name: | RegFilesHash |
Value: F8B4BC596D83875BF0A4EB18C0717F23AD1696ABD62924D8CFC73CD1D38BE868 | |||
| (PID) Process: | (3824) 4a29f762e7a3910c4b52bb55e27cdc5efcb54f79c9f2f50b5a84c72115ec9502.tmp | Key: | HKEY_CURRENT_USER\Software\XinYi Network\VRoot |
| Operation: | write | Name: | InstallPath |
Value: C:\Program Files\VROOT\Root.exe | |||
| (PID) Process: | (3824) 4a29f762e7a3910c4b52bb55e27cdc5efcb54f79c9f2f50b5a84c72115ec9502.tmp | Key: | HKEY_CURRENT_USER\Software\XinYi Network\VRoot |
| Operation: | write | Name: | Version |
Value: 1.7.0.3882 | |||
| (PID) Process: | (3824) 4a29f762e7a3910c4b52bb55e27cdc5efcb54f79c9f2f50b5a84c72115ec9502.tmp | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\XinYi Network\VRoot |
| Operation: | write | Name: | InstallPath |
Value: C:\Program Files\VROOT\Root.exe | |||
| (PID) Process: | (3824) 4a29f762e7a3910c4b52bb55e27cdc5efcb54f79c9f2f50b5a84c72115ec9502.tmp | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\XinYi Network\VRoot |
| Operation: | write | Name: | Version |
Value: 1.7.0.3882 | |||
| (PID) Process: | (3824) 4a29f762e7a3910c4b52bb55e27cdc5efcb54f79c9f2f50b5a84c72115ec9502.tmp | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall\{1295E43F-382A-4CB2-9E0F-079C0D7401BB}_is1 |
| Operation: | write | Name: | Inno Setup: Setup Version |
Value: 5.5.3 (a) | |||
Executable files
46
Suspicious files
60
Text files
147
Unknown types
65
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3824 | 4a29f762e7a3910c4b52bb55e27cdc5efcb54f79c9f2f50b5a84c72115ec9502.tmp | C:\Program Files\VROOT\is-6VQ19.tmp | — | |
MD5:— | SHA256:— | |||
| 3824 | 4a29f762e7a3910c4b52bb55e27cdc5efcb54f79c9f2f50b5a84c72115ec9502.tmp | C:\Program Files\VROOT\is-IGQMB.tmp | — | |
MD5:— | SHA256:— | |||
| 3824 | 4a29f762e7a3910c4b52bb55e27cdc5efcb54f79c9f2f50b5a84c72115ec9502.tmp | C:\Program Files\VROOT\is-JT47T.tmp | — | |
MD5:— | SHA256:— | |||
| 3824 | 4a29f762e7a3910c4b52bb55e27cdc5efcb54f79c9f2f50b5a84c72115ec9502.tmp | C:\Program Files\VROOT\is-JUR8V.tmp | — | |
MD5:— | SHA256:— | |||
| 3824 | 4a29f762e7a3910c4b52bb55e27cdc5efcb54f79c9f2f50b5a84c72115ec9502.tmp | C:\Program Files\VROOT\is-MDQSI.tmp | — | |
MD5:— | SHA256:— | |||
| 3824 | 4a29f762e7a3910c4b52bb55e27cdc5efcb54f79c9f2f50b5a84c72115ec9502.tmp | C:\Program Files\VROOT\is-CEV5P.tmp | — | |
MD5:— | SHA256:— | |||
| 3824 | 4a29f762e7a3910c4b52bb55e27cdc5efcb54f79c9f2f50b5a84c72115ec9502.tmp | C:\Program Files\VROOT\is-CIRO4.tmp | — | |
MD5:— | SHA256:— | |||
| 3824 | 4a29f762e7a3910c4b52bb55e27cdc5efcb54f79c9f2f50b5a84c72115ec9502.tmp | C:\Program Files\VROOT\is-M9M90.tmp | — | |
MD5:— | SHA256:— | |||
| 3824 | 4a29f762e7a3910c4b52bb55e27cdc5efcb54f79c9f2f50b5a84c72115ec9502.tmp | C:\Program Files\VROOT\is-99T7K.tmp | — | |
MD5:— | SHA256:— | |||
| 3824 | 4a29f762e7a3910c4b52bb55e27cdc5efcb54f79c9f2f50b5a84c72115ec9502.tmp | C:\Program Files\VROOT\is-53JK2.tmp | — | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
82
TCP/UDP connections
107
DNS requests
54
Threats
4
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
— | — | HEAD | — | 35.176.48.44:80 | http://cdnpic.mgyun.com/Files/FriendLink/2016/2/17/1340090a66f.png | GB | — | — | unknown |
— | — | GET | 302 | 36.51.254.231:80 | http://e.weibo.com/rootdashi | CN | — | — | unknown |
— | — | GET | — | 180.149.134.141:80 | http://weibo.com/3425147312 | CN | — | — | whitelisted |
— | — | GET | 304 | 2.16.186.81:80 | http://www.download.windowsupdate.com/msdownload/update/v3/static/trustedr/en/authrootstl.cab | unknown | — | — | whitelisted |
— | — | GET | 304 | 2.16.186.81:80 | http://www.download.windowsupdate.com/msdownload/update/v3/static/trustedr/en/authrootstl.cab | unknown | — | — | whitelisted |
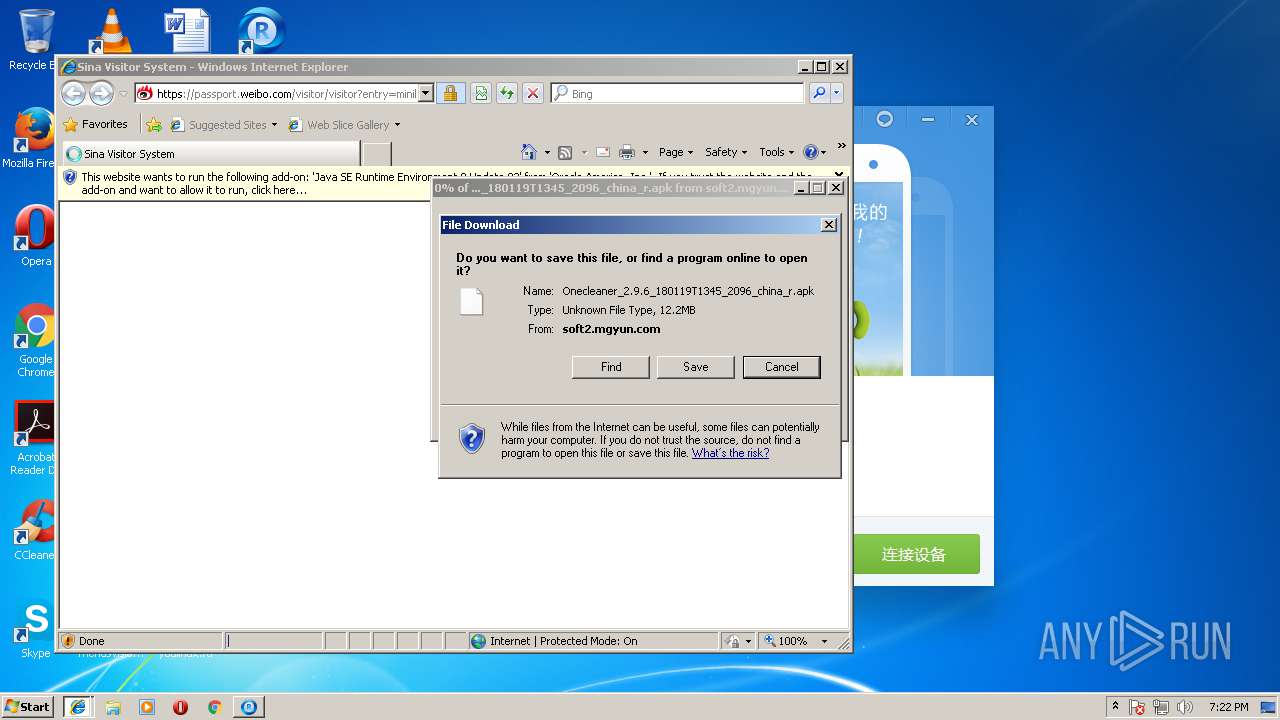
— | — | GET | 200 | 101.69.121.43:80 | http://products.mgyun.com/api/checkupdate?productCode=vroot&versioncode=17235968&pcid=370d4f947c3fd7a5d201957ec5aedb54 | CN | text | 422 b | malicious |
— | — | GET | 200 | 101.69.121.44:80 | http://links.mgyun.com/API/FriendLinks/GetLinks?code=vroot_banner | CN | text | 355 b | malicious |
— | — | GET | 200 | 35.176.48.44:80 | http://cdnpic.mgyun.com/Files/FriendLink/2016/2/17/1340090a66f.png | GB | image | 72.4 Kb | unknown |
— | — | GET | 200 | 58.61.34.195:80 | http://api.mgyun.com/system/getconfig?product=vroot&vcode=17235968&cid=1000&pcid=370d4f947c3fd7a5d201957ec5aedb54 | CN | text | 1.58 Kb | unknown |
— | — | GET | 302 | 101.69.121.43:80 | http://products.mgyun.com/api/downjump?id=7978 | CN | html | 207 b | malicious |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
— | — | 58.61.34.195:80 | api.mgyun.com | China Telecom (Group) | CN | unknown |
— | — | 58.61.34.202:80 | log.ibutian.com | China Telecom (Group) | CN | unknown |
— | — | 101.69.121.43:80 | links.mgyun.com | CHINA UNICOM China169 Backbone | CN | unknown |
— | — | 101.69.121.44:80 | links.mgyun.com | CHINA UNICOM China169 Backbone | CN | unknown |
— | — | 123.6.6.112:80 | links.mgyun.com | CHINA UNICOM China169 Backbone | CN | suspicious |
— | — | 35.176.48.44:80 | cdnpic.mgyun.com | Amazon.com, Inc. | GB | unknown |
— | — | 36.51.254.231:80 | e.weibo.com | ISP | CN | unknown |
— | — | 204.79.197.200:80 | www.bing.com | Microsoft Corporation | US | whitelisted |
— | — | 180.149.134.141:443 | weibo.com | IDC, China Telecommunications Corporation | CN | suspicious |
— | — | 180.149.134.141:80 | weibo.com | IDC, China Telecommunications Corporation | CN | suspicious |
DNS requests
Domain | IP | Reputation |
|---|---|---|
log.ibutian.com |
| unknown |
api.mgyun.com |
| unknown |
links.mgyun.com |
| malicious |
products.mgyun.com |
| malicious |
cdnpic.mgyun.com |
| unknown |
soft.mgyun.com |
| malicious |
www.bing.com |
| whitelisted |
e.weibo.com |
| unknown |
weibo.com |
| whitelisted |
ocsp.globalsign.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
— | — | Potential Corporate Privacy Violation | ET POLICY Windows 98 User-Agent Detected - Possible Malware or Non-Updated System |
— | — | Potential Corporate Privacy Violation | ET POLICY Unsupported/Fake Internet Explorer Version MSIE 5. |
— | — | Potential Corporate Privacy Violation | ET POLICY PE EXE or DLL Windows file download HTTP |
— | — | Potential Corporate Privacy Violation | ET POLICY Outdated Flash Version M1 |
Process | Message |
|---|---|
Root.exe | start of Thread::ThreadMain(report_thread)
|
Root.exe | start of Thread::ThreadMain(main_work_bk)
|
Root.exe | start of Thread::ThreadMain(autoupdate_thread)
|
RomasterConnection.exe | 2018-05-09 19:22:16 [2848] DEBUG [wWinMain] commandline: /hwnd=65986 [RomasterConnection.cpp:45]
|
RomasterConnection.exe | start of Thread::ThreadMain(connection_get_identify_thread)
|
RomasterConnection.exe | start of Thread::ThreadMain(device_helper_thread)
|
RomasterConnection.exe | start of Thread::ThreadMain(delayed_notify_thread)
|
RomasterConnection.exe | start of Thread::ThreadMain(adb_keeper_thread)
|
RomasterConnection.exe | 2018-05-09 19:22:16 [2848] INFO [RomasterPC::DeviceManager::_2354B663]
[DeviceManager.cpp:226]
|
RomasterConnection.exe | 2018-05-09 19:22:16 [2848] DEBUG [CCommunication::AddCommuWndHandle] curent vec size:1 [Communication.cpp:358]
|