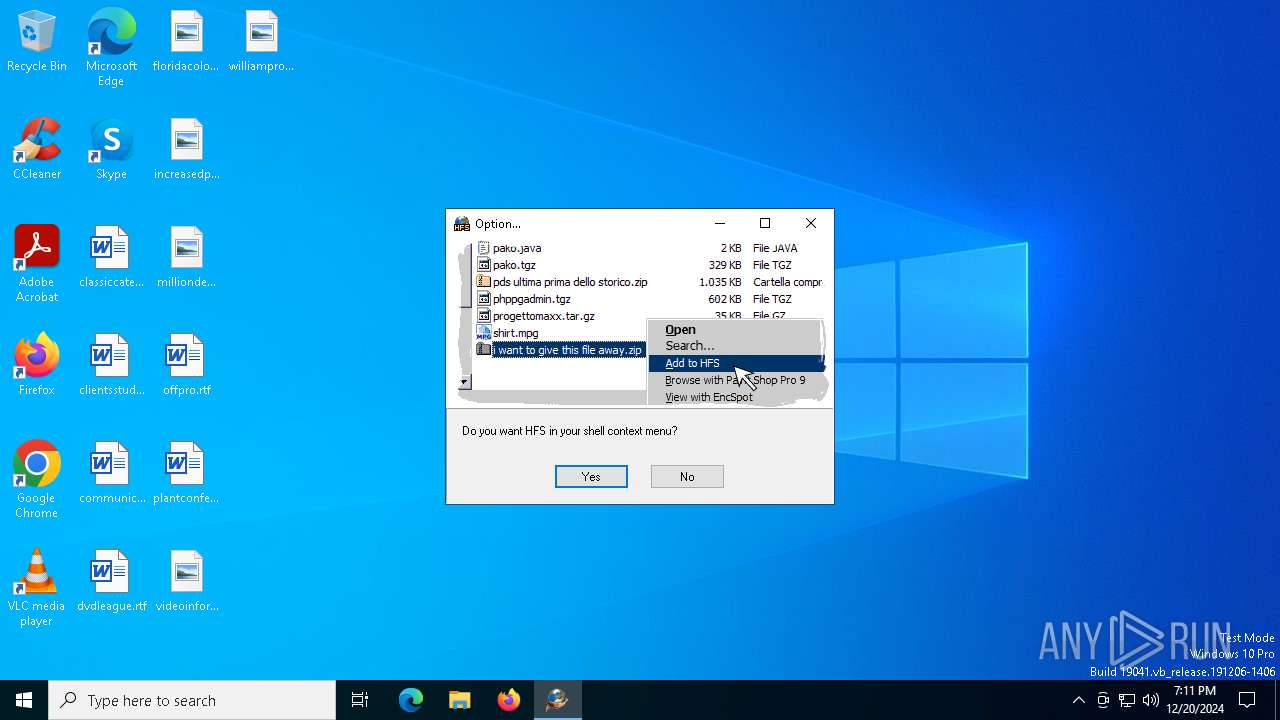
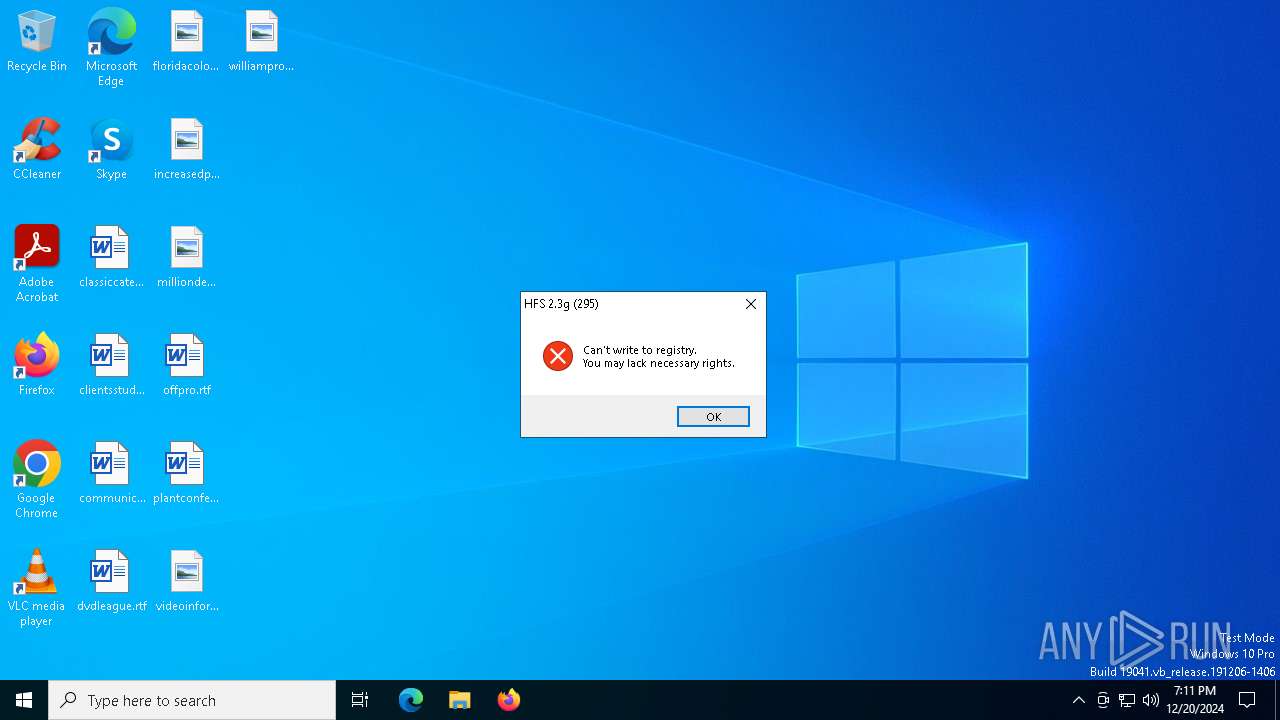
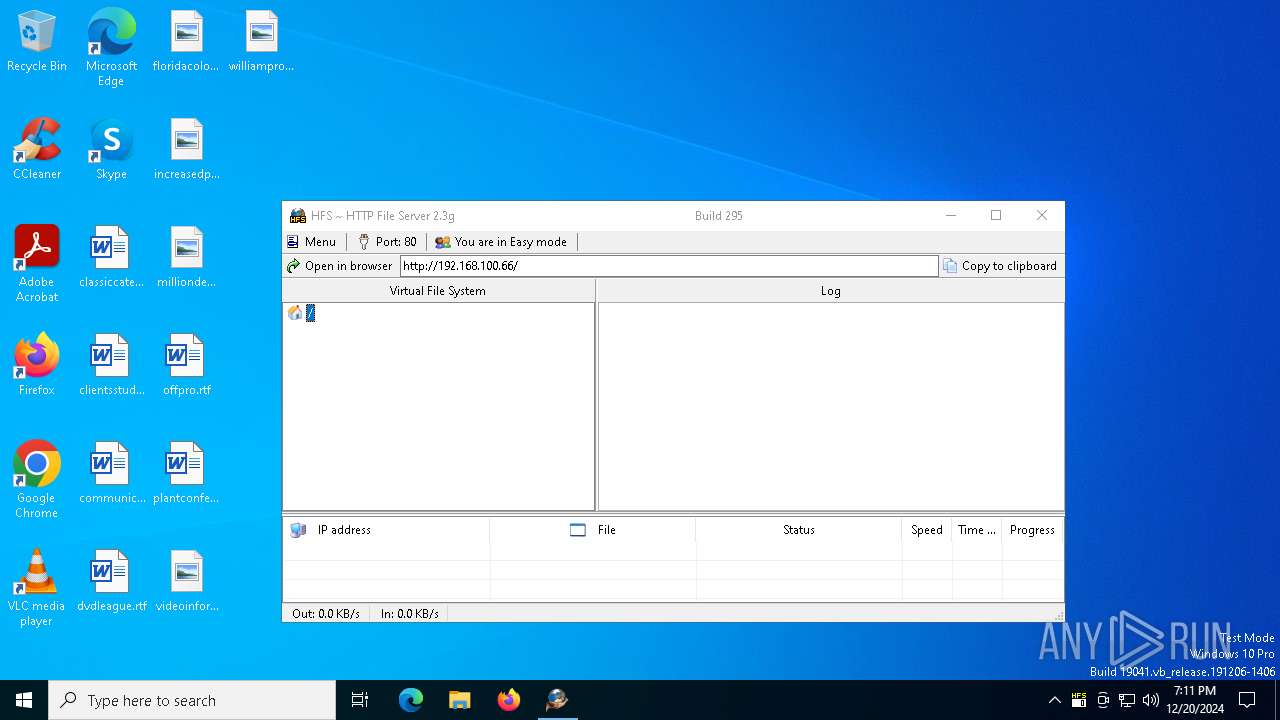
| File name: | hfs.exe |
| Full analysis: | https://app.any.run/tasks/f5ce486d-c0bd-4cf9-b282-3acd5ff45054 |
| Verdict: | Malicious activity |
| Analysis date: | December 20, 2024, 19:11:01 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/vnd.microsoft.portable-executable |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows, 10 sections |
| MD5: | C019D10F80409FC4C7D45EBFA48B0076 |
| SHA1: | 92149025980C28823FDBE7D5378C29606130EA03 |
| SHA256: | 4A267F297EB61547BA6CC7FAF0BBFAAD2B61556DD7D6E381108DB24FD6149AB5 |
| SSDEEP: | 49152:PxTpXZQmihIXHEvlTphplKhKr70LHTWkDqvy4ddxCce7SZs1S:PZpamihIXEvlt76Ywu6B8 |
MALICIOUS
EXPLOIT has been detected (SURICATA)
- svchost.exe (PID: 1176)
SUSPICIOUS
There is functionality for communication over UDP network (YARA)
- hfs.exe (PID: 6452)
There is functionality for taking screenshot (YARA)
- hfs.exe (PID: 6452)
There is functionality for capture public ip (YARA)
- hfs.exe (PID: 6452)
INFO
Create files in a temporary directory
- hfs.exe (PID: 6452)
Reads the computer name
- hfs.exe (PID: 6452)
The sample compiled with Italian language support
- hfs.exe (PID: 6452)
Checks supported languages
- hfs.exe (PID: 6452)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win32 EXE PECompact compressed (generic) (79.7) |
|---|---|---|
| .exe | | | Win32 Executable (generic) (8.6) |
| .exe | | | Win16/32 Executable Delphi generic (3.9) |
| .exe | | | Generic Win/DOS Executable (3.8) |
| .exe | | | DOS Executable Generic (3.8) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 1992:06:19 22:22:17+00:00 |
| ImageFileCharacteristics: | Executable, No line numbers, No symbols, Bytes reversed lo, 32-bit, Bytes reversed hi |
| PEType: | PE32 |
| LinkerVersion: | 2.25 |
| CodeSize: | 1511936 |
| InitializedDataSize: | 987136 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x172c70 |
| OSVersion: | 4 |
| ImageVersion: | - |
| SubsystemVersion: | 4 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 2.3.0.0 |
| ProductVersionNumber: | 2.3.0.0 |
| FileFlagsMask: | 0x003f |
| FileFlags: | Debug |
| FileOS: | Win32 |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | Italian |
| CharacterSet: | Windows, Latin1 |
| CompanyName: | rejetto |
| FileDescription: | - |
| FileVersion: | 2.3.0.0 |
| InternalName: | HFS |
| LegalCopyright: | Copyright (C) 2002-2010 Massimo Melina (www.rejetto.com) |
| LegalTrademarks: | - |
| OriginalFileName: | hfs.exe |
| ProductName: | Http File Server |
| ProductVersion: | 2.3 |
| Comments: | - |
Total processes
131
Monitored processes
2
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1176 | C:\WINDOWS\system32\svchost.exe -k netsvcs -p -s wlidsvc | C:\Windows\System32\svchost.exe | services.exe | ||||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Host Process for Windows Services Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6452 | "C:\Users\admin\AppData\Local\Temp\hfs.exe" | C:\Users\admin\AppData\Local\Temp\hfs.exe | — | explorer.exe | |||||||||||
User: admin Company: rejetto Integrity Level: MEDIUM Version: 2.3.0.0 Modules
| |||||||||||||||
Total events
501
Read events
488
Write events
13
Delete events
0
Modification events
| (PID) Process: | (1176) svchost.exe | Key: | HKEY_USERS\.DEFAULT\Software\Microsoft\IdentityCRL\DeviceIdentities\production\Logs\02gxadfupqvdmqba |
| Operation: | write | Name: | Provision Friday, December 20, 2024 19:11:15 |
Value: AQAAANCMnd8BFdERjHoAwE/Cl+sBAAAAHfTBGweZxkKEH9DMCV9BtgAAAAACAAAAAAAQZgAAAAEAACAAAADB2Gi0LGt0UhPV1sgav3Lf3WTF07bYrjIbahWx3UcAOAAAAAAOgAAAAAIAACAAAACmgTZuRoNZ3L1AB1t6ILPNWISXTRPF6wjcgdIGDgqxOSAAAACz4EFoUNCD8fE/0Le7FbVTPseStowuoPiSBtF0N+GaRUAAAAAAelw6A0NU6HT8s28PJXzLjqmz354Ace+4P+w9OXdlrKIG3IYX5xgRTy+f1a8mlF6o3qP0LztaUvYX6m1+0dEy | |||
| (PID) Process: | (1176) svchost.exe | Key: | HKEY_USERS\.DEFAULT\Software\Microsoft\IdentityCRL\DeviceIdentities\production\Logs\02lxglxdlxvajcfi |
| Operation: | write | Name: | Provision Friday, December 20, 2024 19:11:16 |
Value: AQAAANCMnd8BFdERjHoAwE/Cl+sBAAAAHfTBGweZxkKEH9DMCV9BtgAAAAACAAAAAAAQZgAAAAEAACAAAADFpeT5W01jwVRLtE3pOCxpin5LKXYZGN51pp4StkDA0gAAAAAOgAAAAAIAACAAAAC8ancVy2LTo+NM96BqENech6wLhw+x30X88VzpDjlEjiAAAAD3Ib4cas/2YCi0XqvgSVTsm4EMDH79WUbgktNkKSALXkAAAAAXuj8FL5M9Qn7KBdlFYUGFniLAdtV8iBvHgIYwvOE6Bl6zLZF3vD2OHfkDi+H6p2IaivO76CaMrui4sbzsZaYi | |||
| (PID) Process: | (1176) svchost.exe | Key: | HKEY_USERS\.DEFAULT\Software\Microsoft\IdentityCRL\DeviceIdentities\production\Logs\02oxxpmlgpehnood |
| Operation: | write | Name: | Provision Friday, December 20, 2024 19:11:16 |
Value: AQAAANCMnd8BFdERjHoAwE/Cl+sBAAAAHfTBGweZxkKEH9DMCV9BtgAAAAACAAAAAAAQZgAAAAEAACAAAAC0qXAivjVdPaCim6Se38mmG+yPE6cMRqi8BDaTxBOsSwAAAAAOgAAAAAIAACAAAACbEnJMWBV13u1FV23NmkD4bqhYcumtX2eFqQ30U+EE5iAAAAB1o08LQJHXXQnEuvV5zRZb8wpEw//+qZsef5cwmdPyu0AAAACnOPckGfyq809KTv+kV/D98+JR+xVnoBUj09qrwDJAjzY0k3FoVmcXtkrsiXjOdoVzMhKQMsZVLKxe9vvKRBOG | |||
| (PID) Process: | (1176) svchost.exe | Key: | HKEY_USERS\.DEFAULT\Software\Microsoft\IdentityCRL\DeviceIdentities\production\Logs\02iujlfqikskimth |
| Operation: | write | Name: | Provision Friday, December 20, 2024 19:11:18 |
Value: AQAAANCMnd8BFdERjHoAwE/Cl+sBAAAAHfTBGweZxkKEH9DMCV9BtgAAAAACAAAAAAAQZgAAAAEAACAAAAC7oP7y59sUeuXurji2XOyjOQJhzlDQYwIuLewFT+90cQAAAAAOgAAAAAIAACAAAAAn5Y+D/Pp27IjYjBF8TdYuWFxn8Kfpe6XyfmxlOv3n6yAAAABMDpfvNFQtyyC2iIfkvB4Fjpp+P4i1uWnON8p+HMwh+UAAAAAVvK6QZ6YDStkIq74nhosTraRBeg6Z8Ss6V5VMPr82hGLdGdYTgvYiZ3A5u7eOcZjFuOkU4SBkapCjn+h50FKI | |||
| (PID) Process: | (1176) svchost.exe | Key: | HKEY_USERS\.DEFAULT\Software\Microsoft\IdentityCRL\DeviceIdentities\production\Logs\02nlihsnmihgebqv |
| Operation: | write | Name: | Provision Friday, December 20, 2024 19:11:16 |
Value: AQAAANCMnd8BFdERjHoAwE/Cl+sBAAAAHfTBGweZxkKEH9DMCV9BtgAAAAACAAAAAAAQZgAAAAEAACAAAACauDe0lscC5M9OLTCl0sBGaDWyxFo116wpM17tXh4PfgAAAAAOgAAAAAIAACAAAABK2TUrXM8VF7CfaAtKQpTsjhywPUNZCy+2aRXkoNeEOCAAAAC8UGjxhrO2nuayRyvlPRlzh/mSClIe6GbR+NeirlG6OkAAAACxJpB28qtb4tvErq6G2LDuF3VRlRg5NcvRHVjfPTtBP4LAvcPpN4RuVqzBqsRZspR4X7zmFPouEPILfiNdR4A0 | |||
| (PID) Process: | (1176) svchost.exe | Key: | HKEY_USERS\.DEFAULT\Software\Microsoft\IdentityCRL\DeviceIdentities\production\Logs\02yrhrzkncmyxbfm |
| Operation: | write | Name: | Provision Friday, December 20, 2024 19:11:17 |
Value: AQAAANCMnd8BFdERjHoAwE/Cl+sBAAAAjGVohzrf7U+SR6PsI8h7nAAAAAACAAAAAAAQZgAAAAEAACAAAAAcFOjAHgAcXWousJBAScfKdVDaGYY4ae58w0/0TymMXgAAAAAOgAAAAAIAACAAAADSR2coOijU/sPZ6YiU4WYvs/ZTu/vEi99gGPEpF5yb7iAAAABNeMnY+6KOo1OaclAwdSI1nI90lJHCTCnjM+qSOkWruUAAAAAsvAnpI9NTGdMDiHGKg9c0jmoLsSZLpcMjC8wBxT7s2hD6Ad1Li6APUlS9jBm0rnf63LL6ItBsjR/xOqz+sQg6 | |||
| (PID) Process: | (1176) svchost.exe | Key: | HKEY_USERS\.DEFAULT\Software\Microsoft\IdentityCRL\DeviceIdentities\production\Logs\02kqdhtqipjggsgh |
| Operation: | write | Name: | Provision Friday, December 20, 2024 19:11:26 |
Value: AQAAANCMnd8BFdERjHoAwE/Cl+sBAAAAHfTBGweZxkKEH9DMCV9BtgAAAAACAAAAAAAQZgAAAAEAACAAAADkMWnhLp2OvTCHTWyISpSlbLHhqN2Va0wjCx79X2rbAQAAAAAOgAAAAAIAACAAAADQgXCDHbDyVlvcTrDtmshoYLqYDAUJp1jxd+PQZgqBCyAAAADzxgBVHJu+BonobTAdDX1+D0oQACL86wuI0em/XG8APUAAAAD1nREfZseWuKJJbdT9OtB7Q0vpQffwAs8xQ2XJgAS2AT1KpIUEp2doJ0Ouh0Av3VuaK7F1piA6Y78M7meiid4y | |||
| (PID) Process: | (1176) svchost.exe | Key: | HKEY_USERS\.DEFAULT\Software\Microsoft\IdentityCRL\DeviceIdentities\production\Logs\02ijqlmqkxxfzbux |
| Operation: | write | Name: | Provision Friday, December 20, 2024 19:11:26 |
Value: AQAAANCMnd8BFdERjHoAwE/Cl+sBAAAAHfTBGweZxkKEH9DMCV9BtgAAAAACAAAAAAAQZgAAAAEAACAAAACD9+5nTIUPZlaFuAw2iMjp3XSVTJJb1iAV/fqu+Rf1qQAAAAAOgAAAAAIAACAAAAA4XcOsM/cLizhCTOYh4n7T+cwZPVEZ5WSa6HEHvrZI9iAAAAAG2caPuMCPHklUVw6dgXCoFn7keYMhRSOfEmwraRD1/0AAAACn76aBKQDVA+WjFJXDFBIdhiWqUnK8e4ocy2oautXhUKBap1c1+Wf6gr5VdTSbeOtjxtfeaBbL28LWFEYPMKP7 | |||
| (PID) Process: | (1176) svchost.exe | Key: | HKEY_USERS\.DEFAULT\Software\Microsoft\IdentityCRL\DeviceIdentities\production\Logs\02tllrozqzgzqvcn |
| Operation: | write | Name: | Provision Friday, December 20, 2024 19:11:28 |
Value: AQAAANCMnd8BFdERjHoAwE/Cl+sBAAAAHfTBGweZxkKEH9DMCV9BtgAAAAACAAAAAAAQZgAAAAEAACAAAABqllI7dPxlo6rXAORtV7+kwSHl6Hxbiigbkw8rfaScfgAAAAAOgAAAAAIAACAAAAAKHHzAjPF1aI6qkdgquEKQWRnXMxqYmHvLialSeA5aTiAAAABY7R+zwuBkDTBRBDWMbbz9mtbr3/+hYhRytyFqILWj9EAAAAAVIdyz5bqXWq3PQKddTGiezW44tVCHJQ+ggAT+i8VycFiJfG1LwoP18GyjTWCKEvD/naMdYMnTl4zrG2ehdjjF | |||
| (PID) Process: | (1176) svchost.exe | Key: | HKEY_USERS\.DEFAULT\Software\Microsoft\IdentityCRL\DeviceIdentities\production\Logs\02fizizmmnvntyks |
| Operation: | write | Name: | Provision Friday, December 20, 2024 19:11:28 |
Value: AQAAANCMnd8BFdERjHoAwE/Cl+sBAAAAHfTBGweZxkKEH9DMCV9BtgAAAAACAAAAAAAQZgAAAAEAACAAAADeZmcymWqg4DSdBZ0e/VWtChSMWkfvMZzrHSIvOTRm4AAAAAAOgAAAAAIAACAAAADJRmSFVFvd42BBz+nyCurL4sqmtYnEweqCA1Wo58X0gyAAAABhZqJXgGJn6C2q/DxV/eC07m28HkWpKLXlnbNd9QsrfUAAAAD0d47nLmo9s20k+bygZLIE+O8ej/RLtVeR6BDMZ6PVmkwZgEZ4gDx5tEF6GW3T2fp8swbF1wPI8idWcvNKMTPT | |||
Executable files
0
Suspicious files
0
Text files
0
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 6452 | hfs.exe | C:\Users\admin\AppData\Local\Temp\test.tmp~1561005081.tmp | — | |
MD5:— | SHA256:— | |||
| 6452 | hfs.exe | C:\Users\admin\AppData\Local\Temp\test.tmp | — | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
6
TCP/UDP connections
29
DNS requests
17
Threats
1
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
— | — | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 2.20.245.138:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
2744 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
2744 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
5252 | backgroundTaskHost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAUZZSZEml49Gjh0j13P68w%3D | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4300 | RUXIMICS.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
— | — | 192.168.100.255:138 | — | — | — | whitelisted |
— | — | 104.126.37.178:443 | www.bing.com | Akamai International B.V. | DE | whitelisted |
4712 | MoUsoCoreWorker.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
— | — | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
— | — | 2.20.245.138:80 | crl.microsoft.com | Akamai International B.V. | SE | whitelisted |
— | — | 184.30.21.171:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
1176 | svchost.exe | 20.190.160.17:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
— | — | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
1076 | svchost.exe | 23.218.210.69:443 | go.microsoft.com | AKAMAI-AS | DE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
www.bing.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
go.microsoft.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
1176 | svchost.exe | Potentially Bad Traffic | ET EXPLOIT Possible OpenSSL HeartBleed Large HeartBeat Response from Common SSL Port (Outbound from Client) |