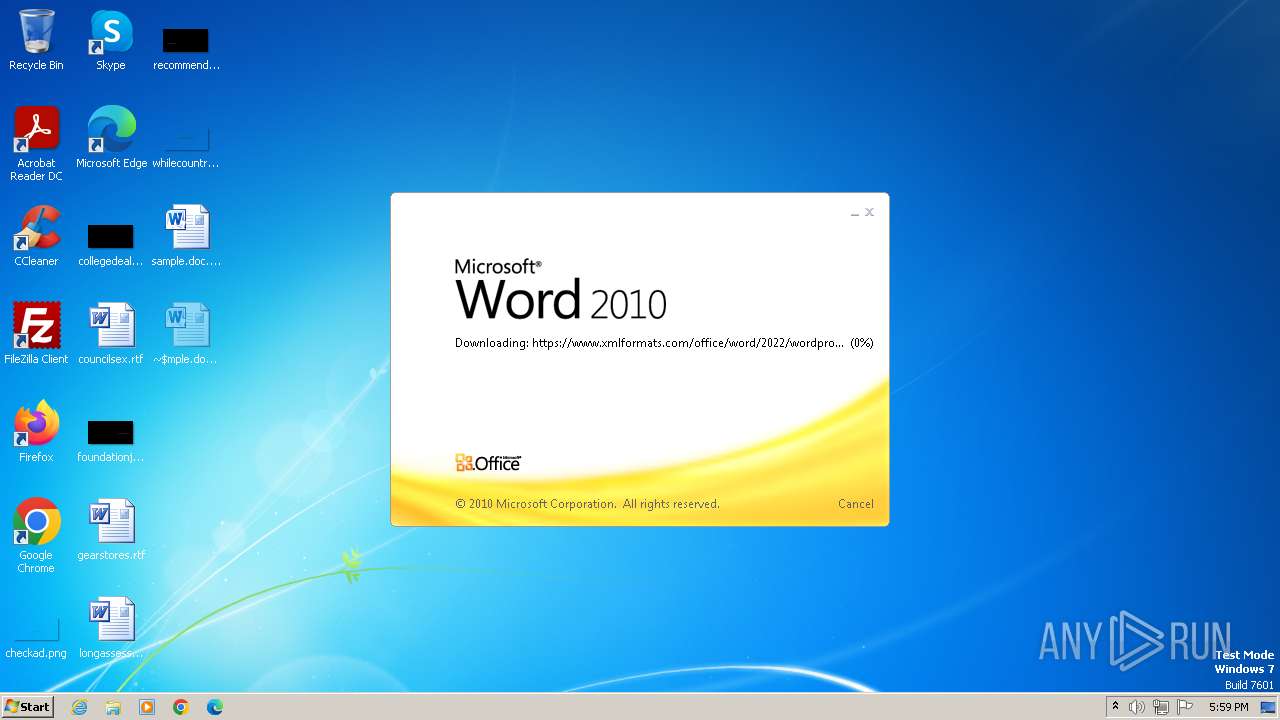
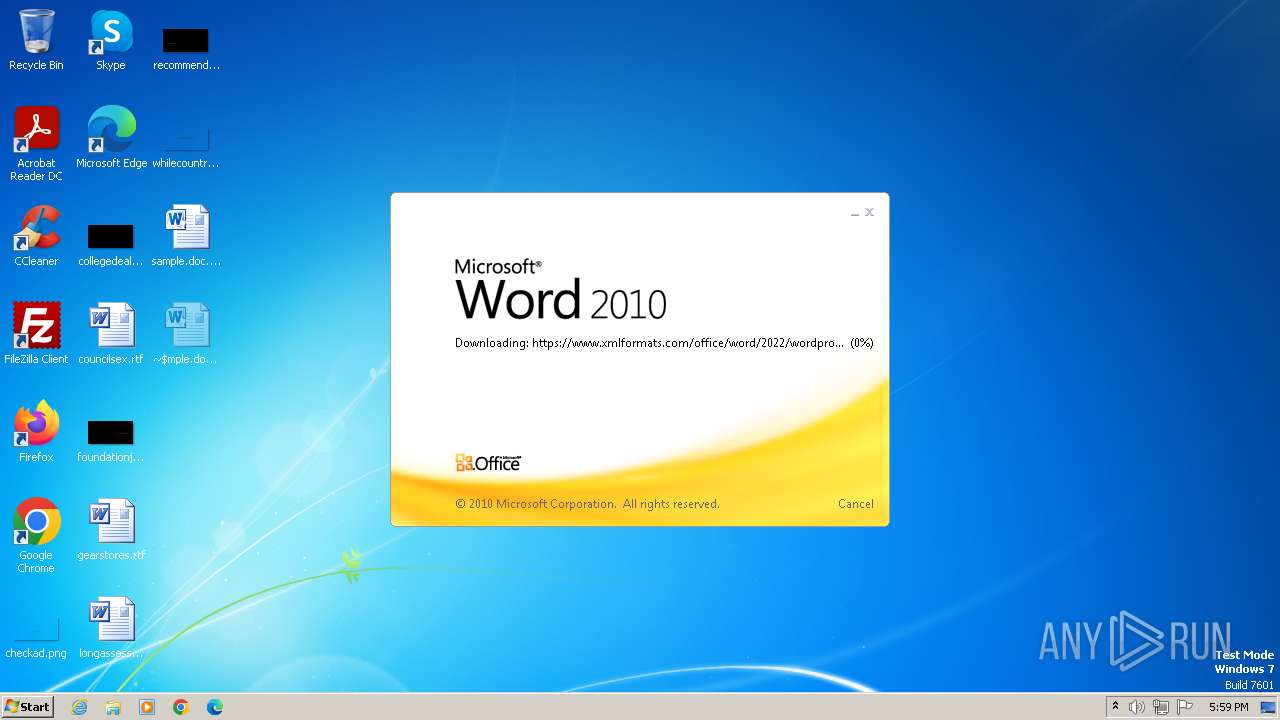
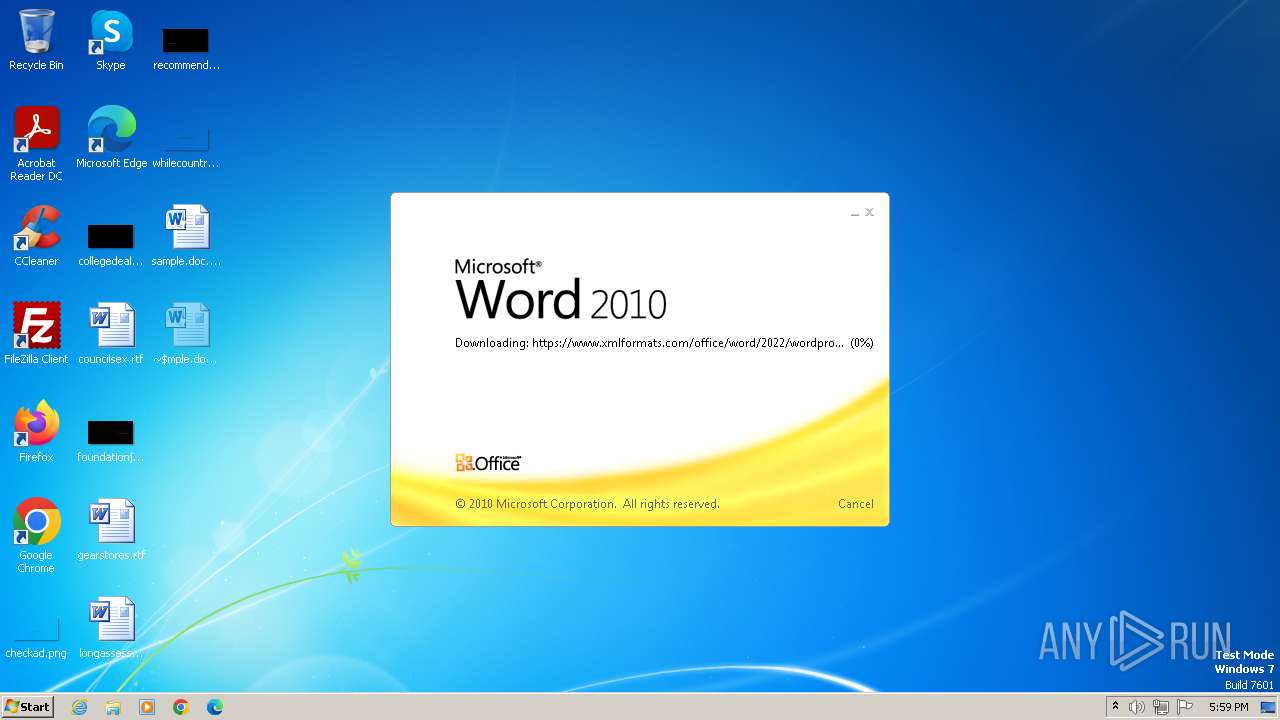
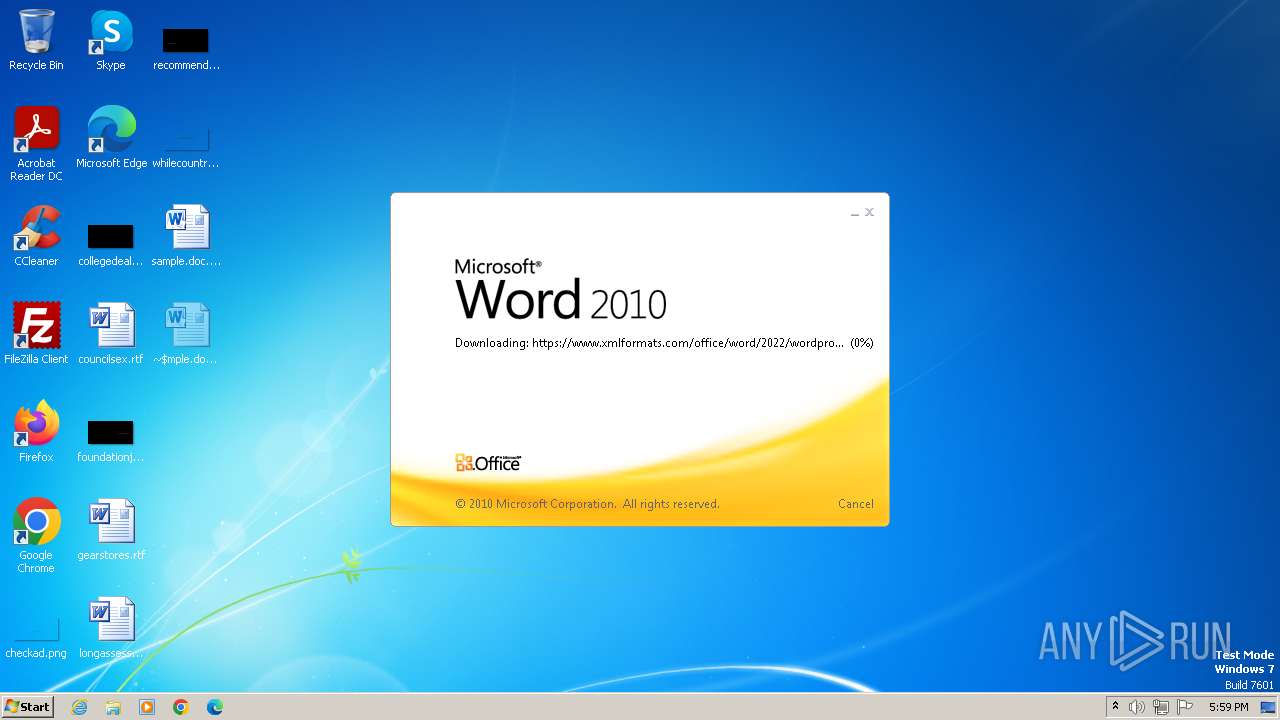
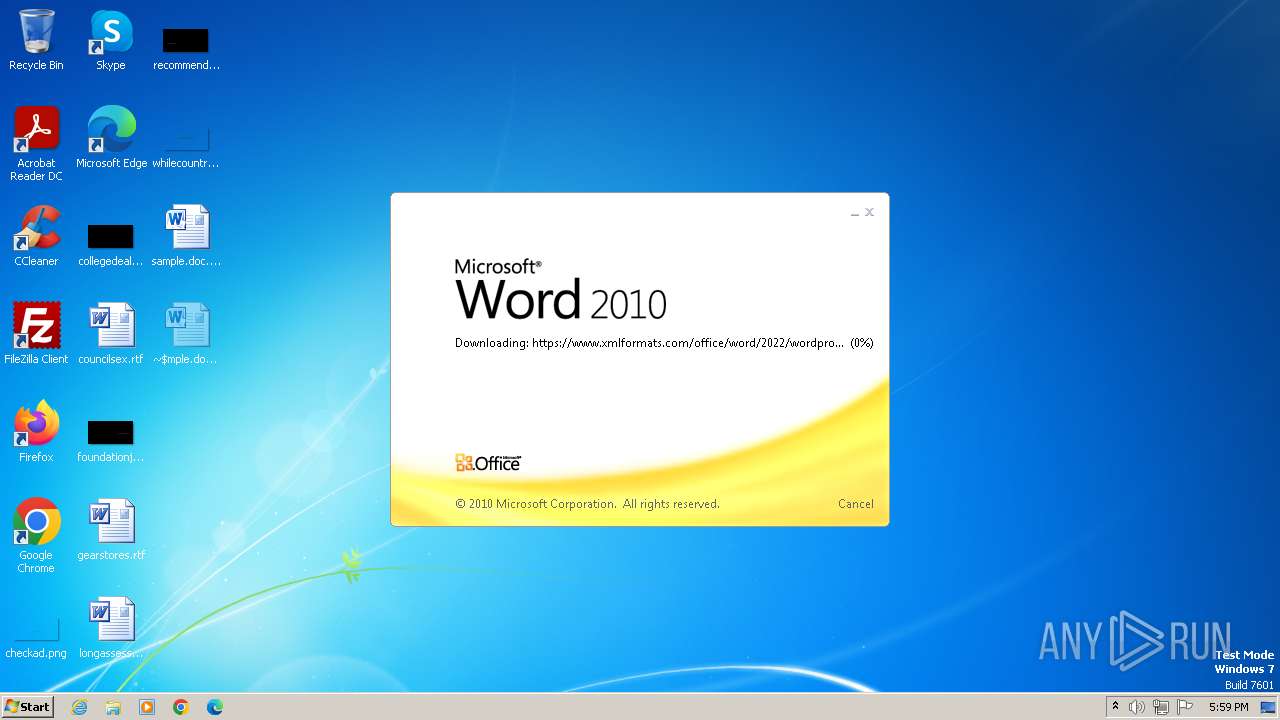
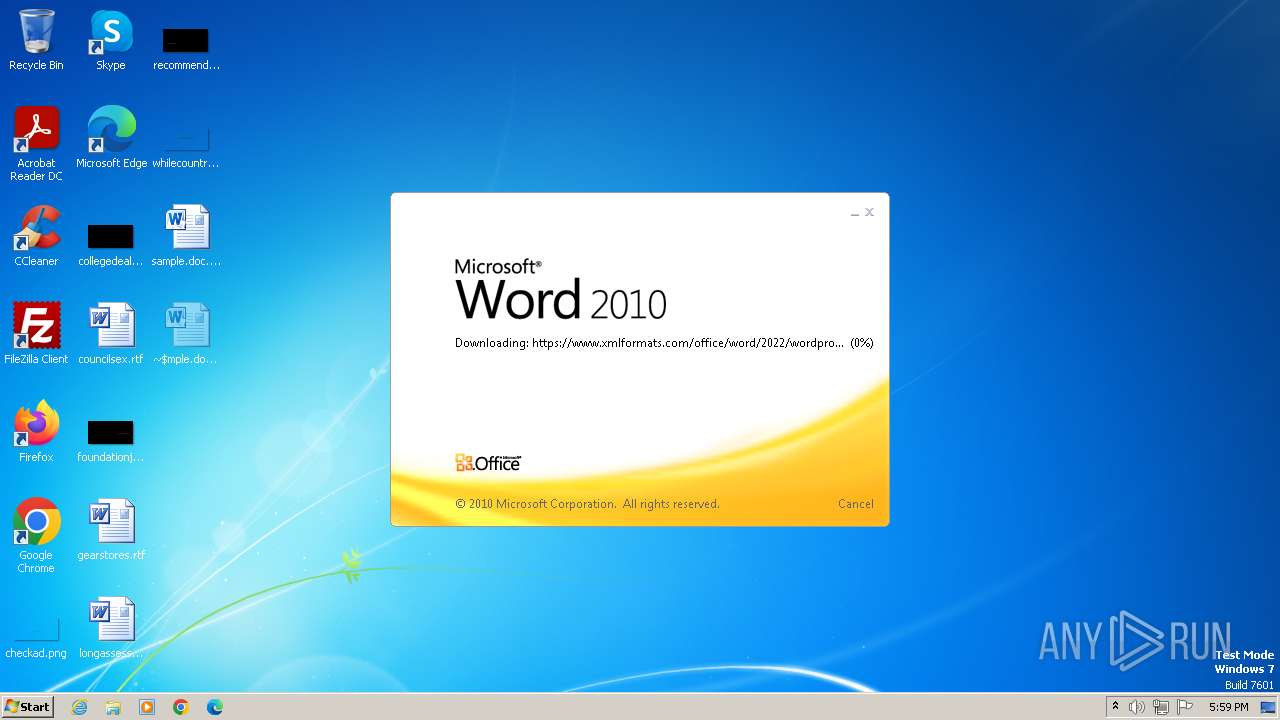
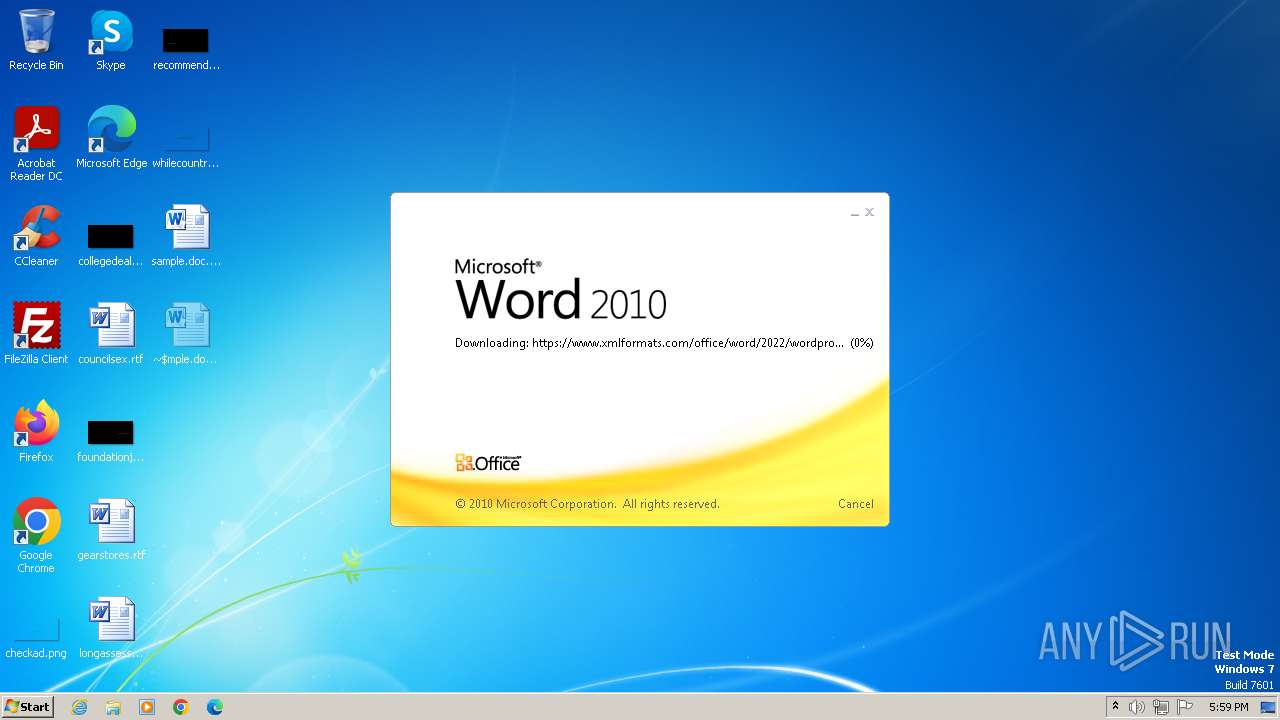
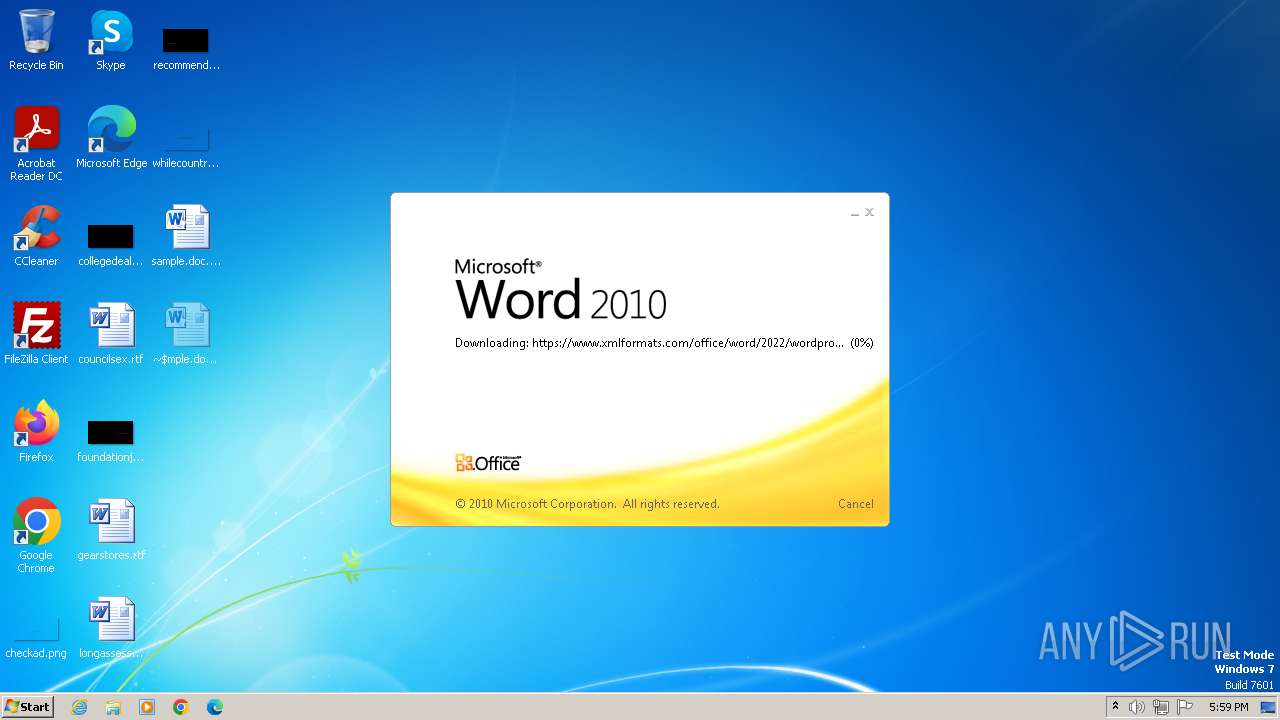
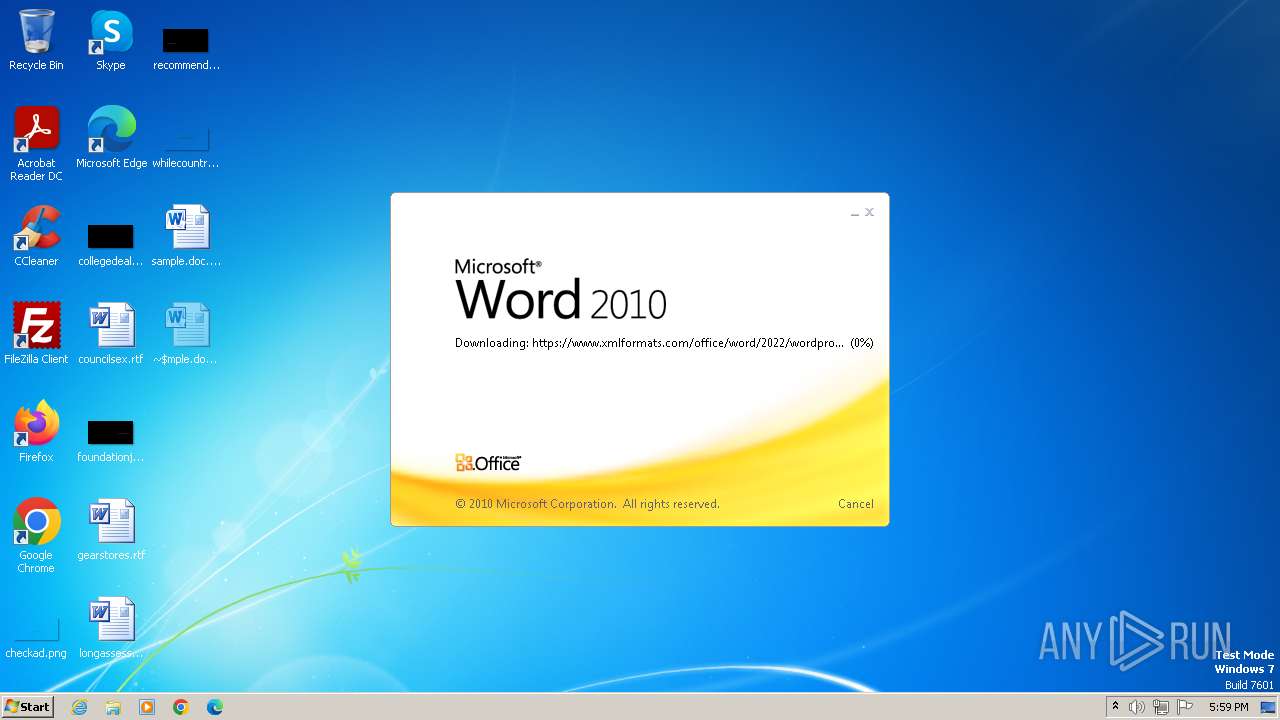
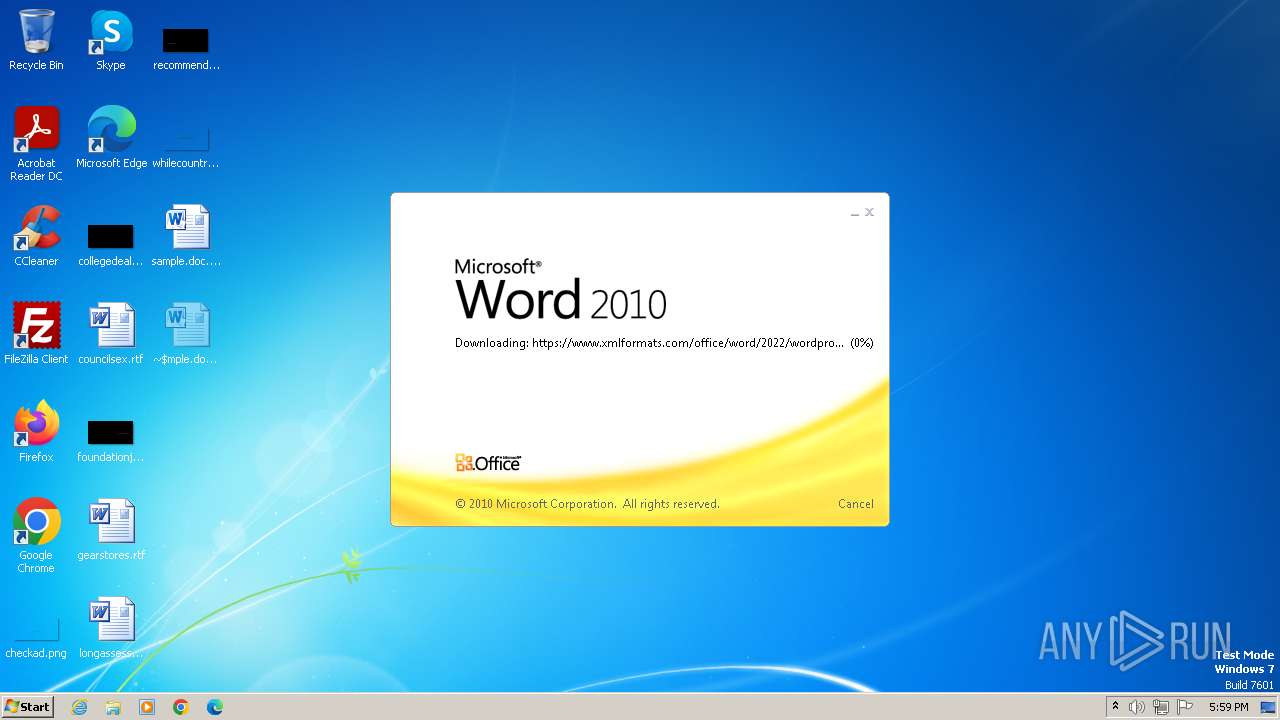
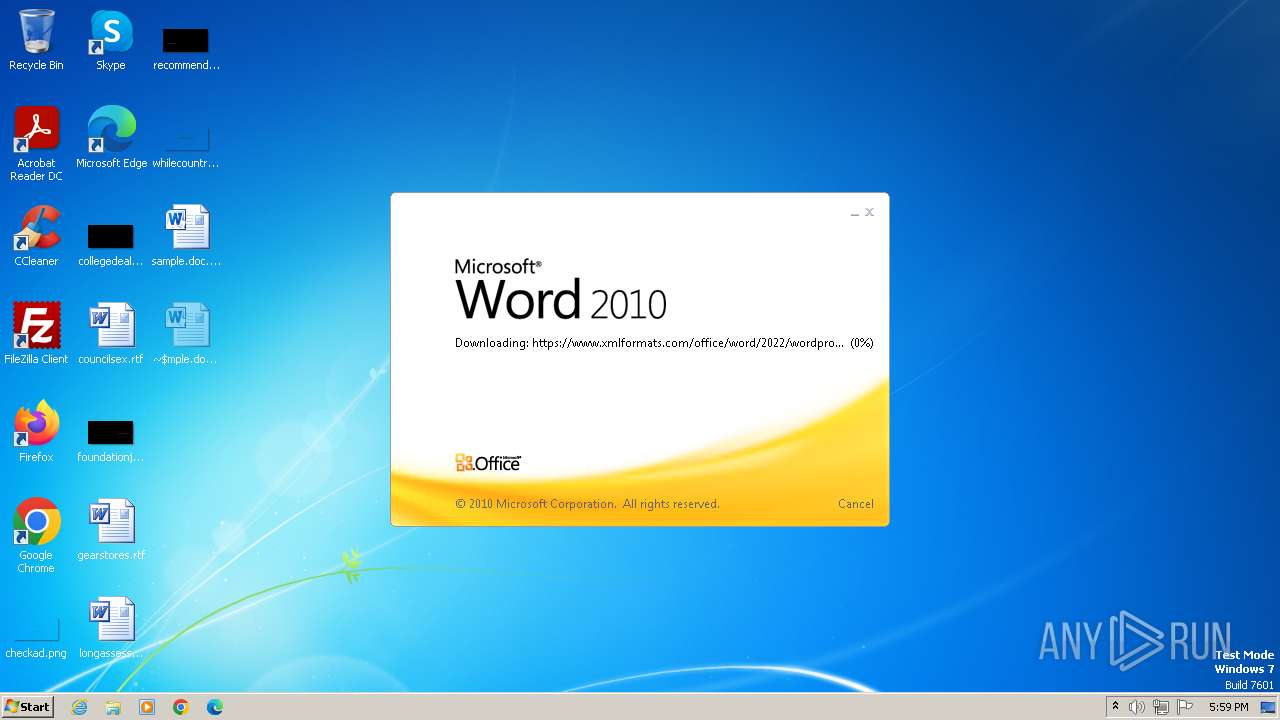
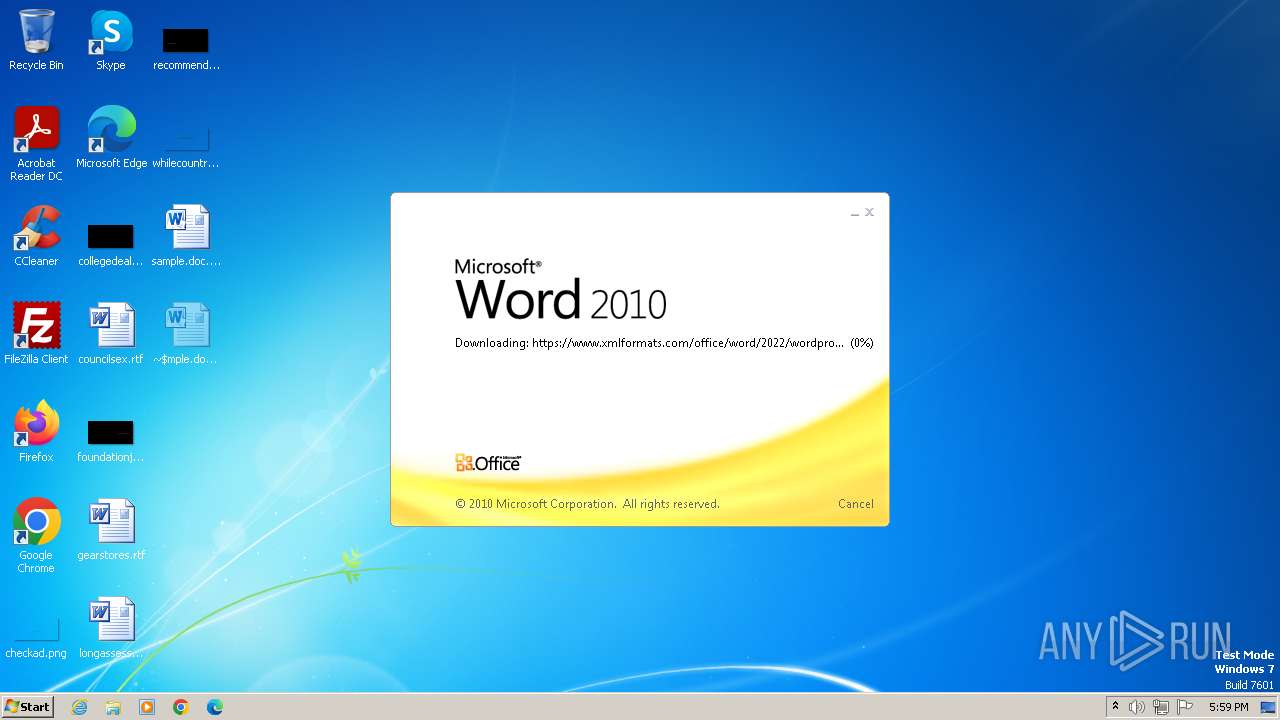
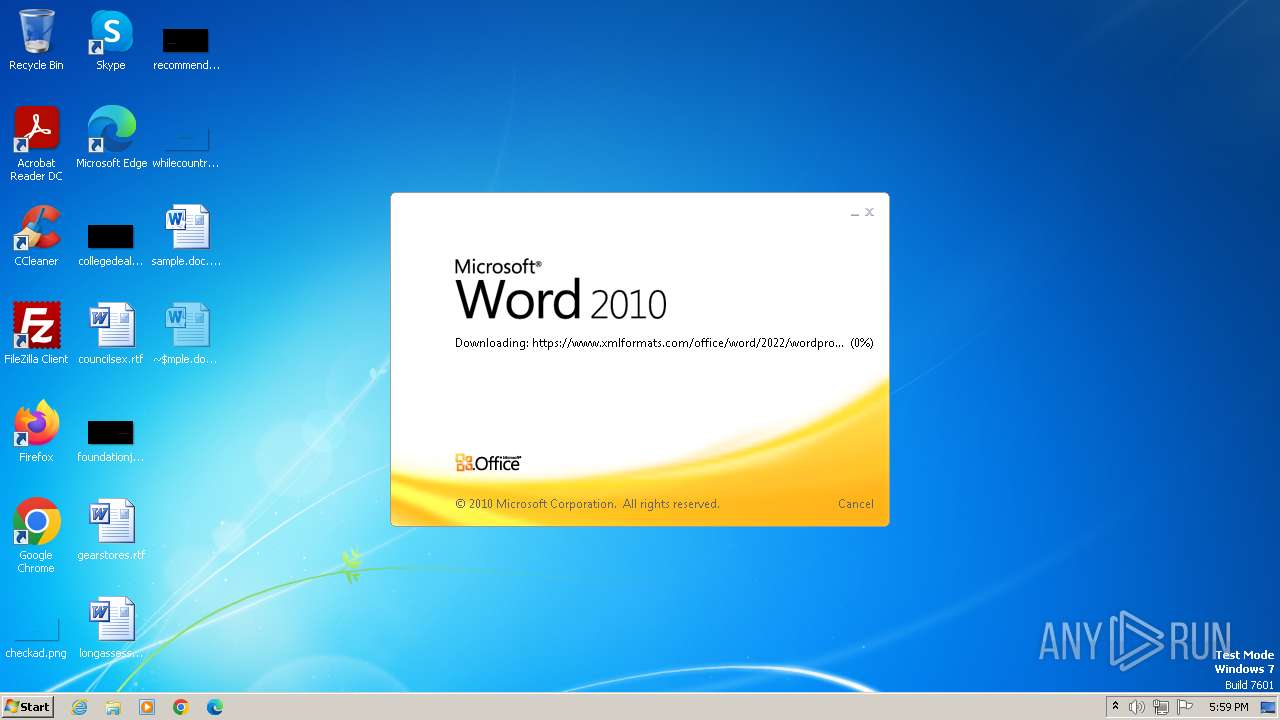
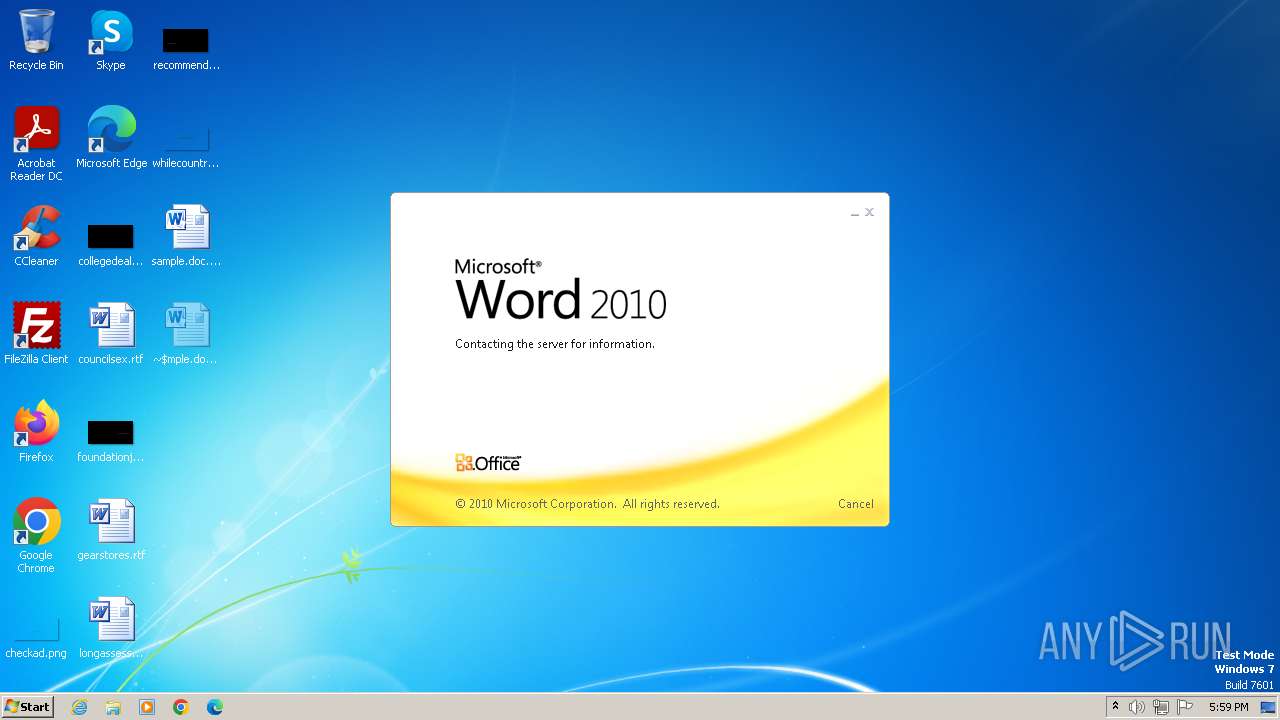
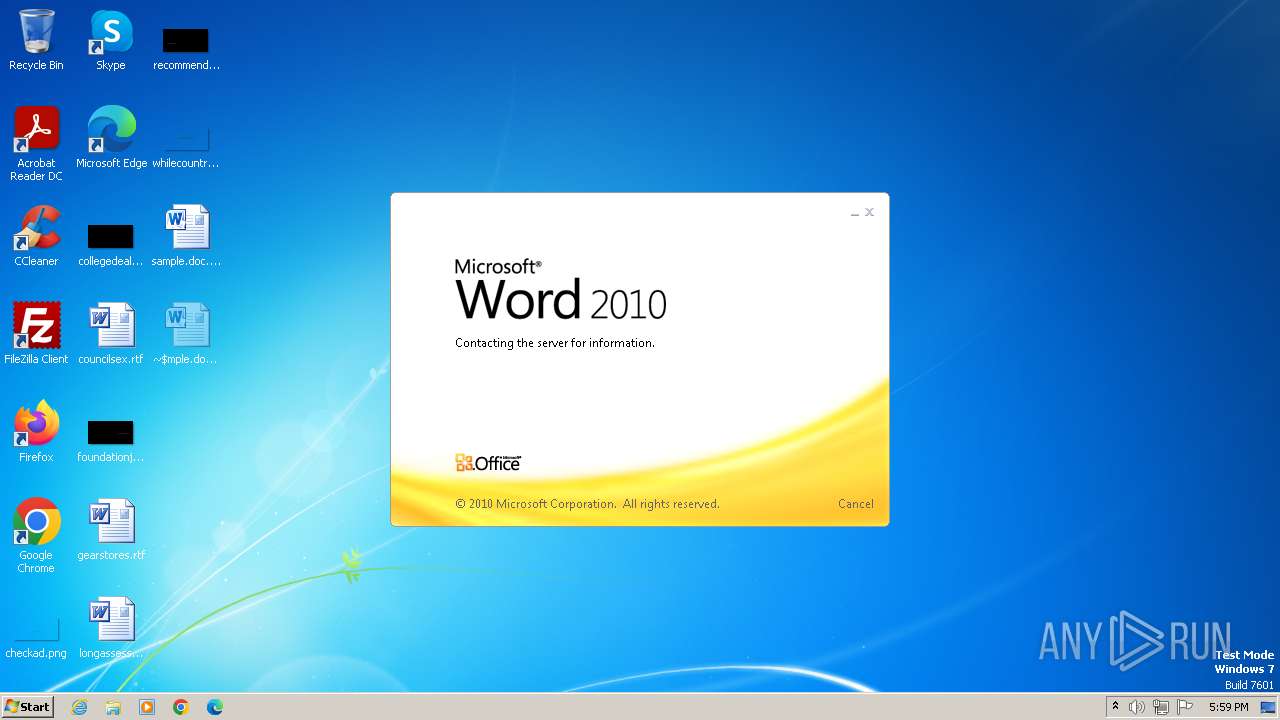
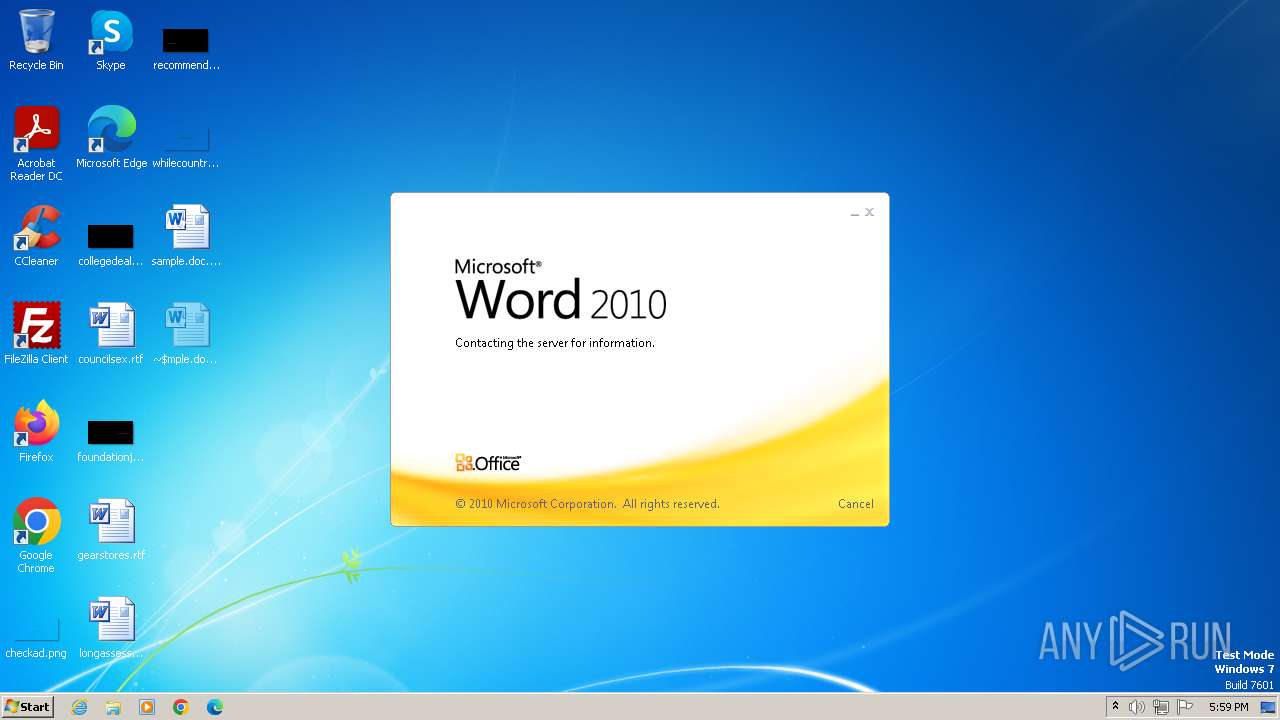
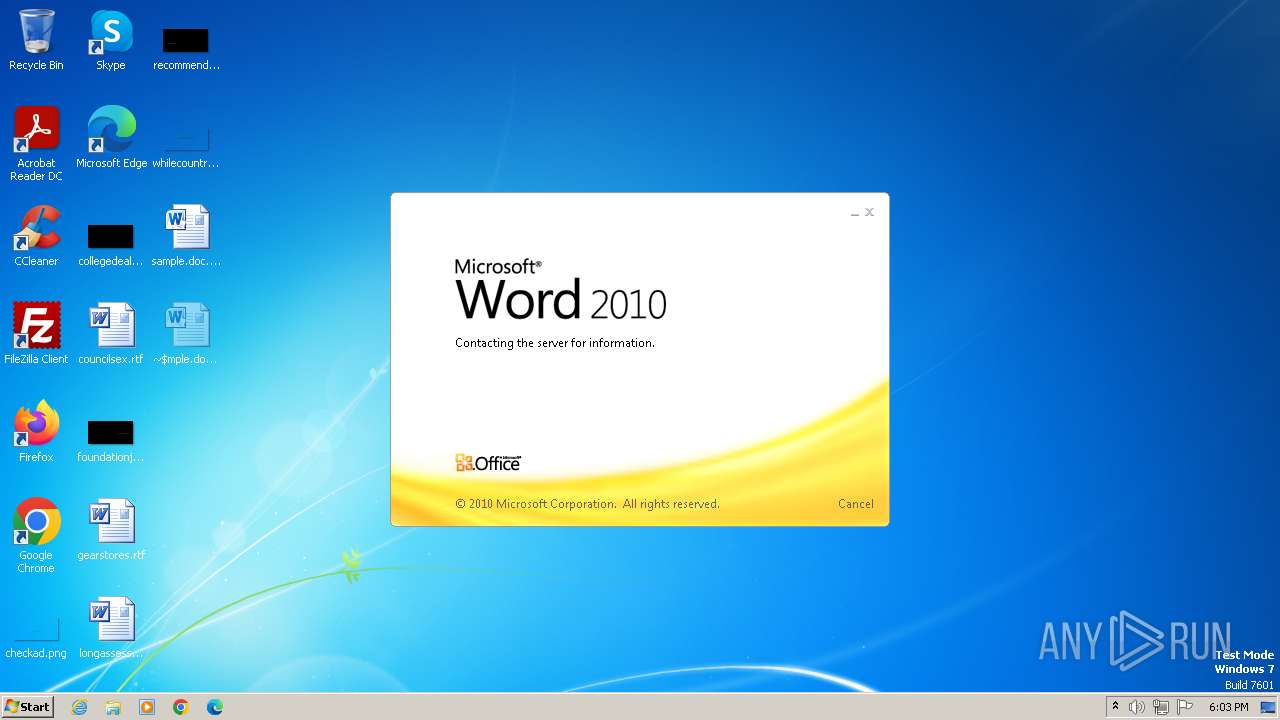
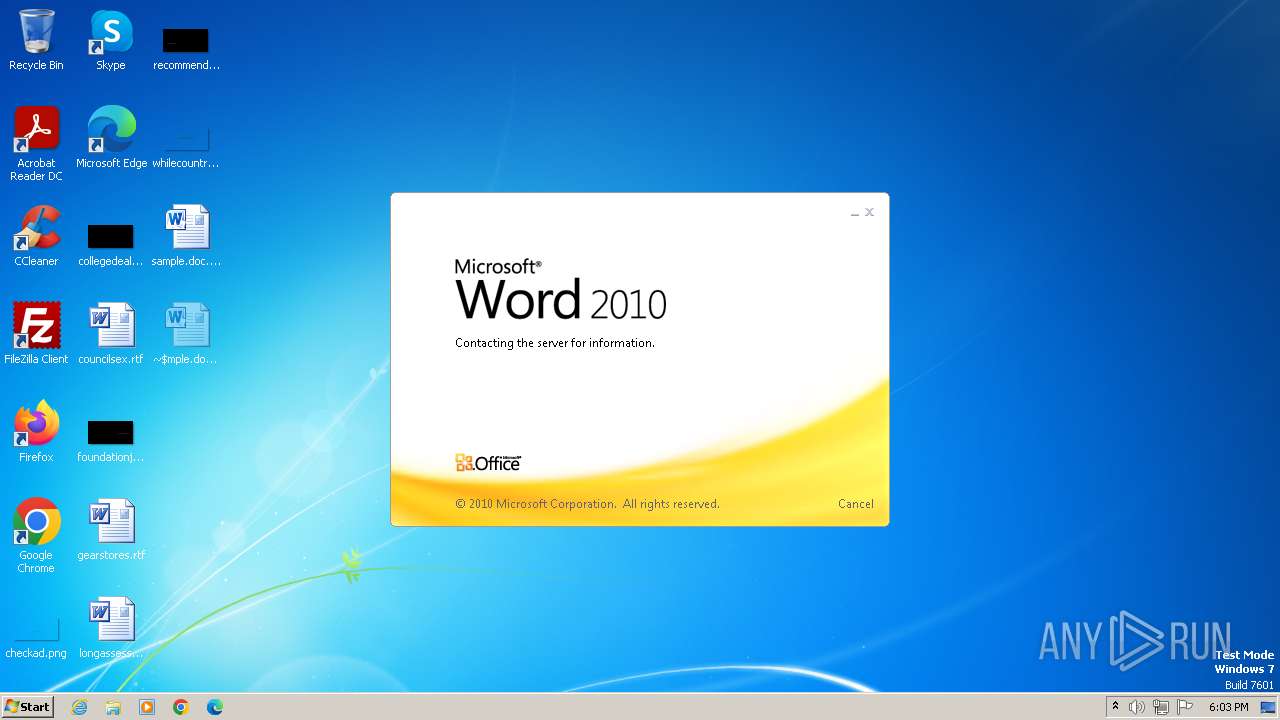
| File name: | sample.doc |
| Full analysis: | https://app.any.run/tasks/ff348024-7043-49c5-8165-48c8b2fc42ff |
| Verdict: | Malicious activity |
| Analysis date: | December 02, 2023, 17:58:10 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| MIME: | application/vnd.openxmlformats-officedocument.wordprocessingml.document |
| File info: | Microsoft Word 2007+ |
| MD5: | 52945AF1DEF85B171870B31FA4782E52 |
| SHA1: | 06727FFDA60359236A8029E0B3E8A0FD11C23313 |
| SHA256: | 4A24048F81AFBE9FB62E7A6A49ADBD1FAF41F266B5F9FEECDCEB567AEC096784 |
| SSDEEP: | 192:AEhM7fIUU09264wptGheab8h7Z/c+8poF1d3jvvtl59rGxjPQDasYBcG7h+:AqWfIz092hwLGAabkcfa7pr1lzyxjPQ9 |
MALICIOUS
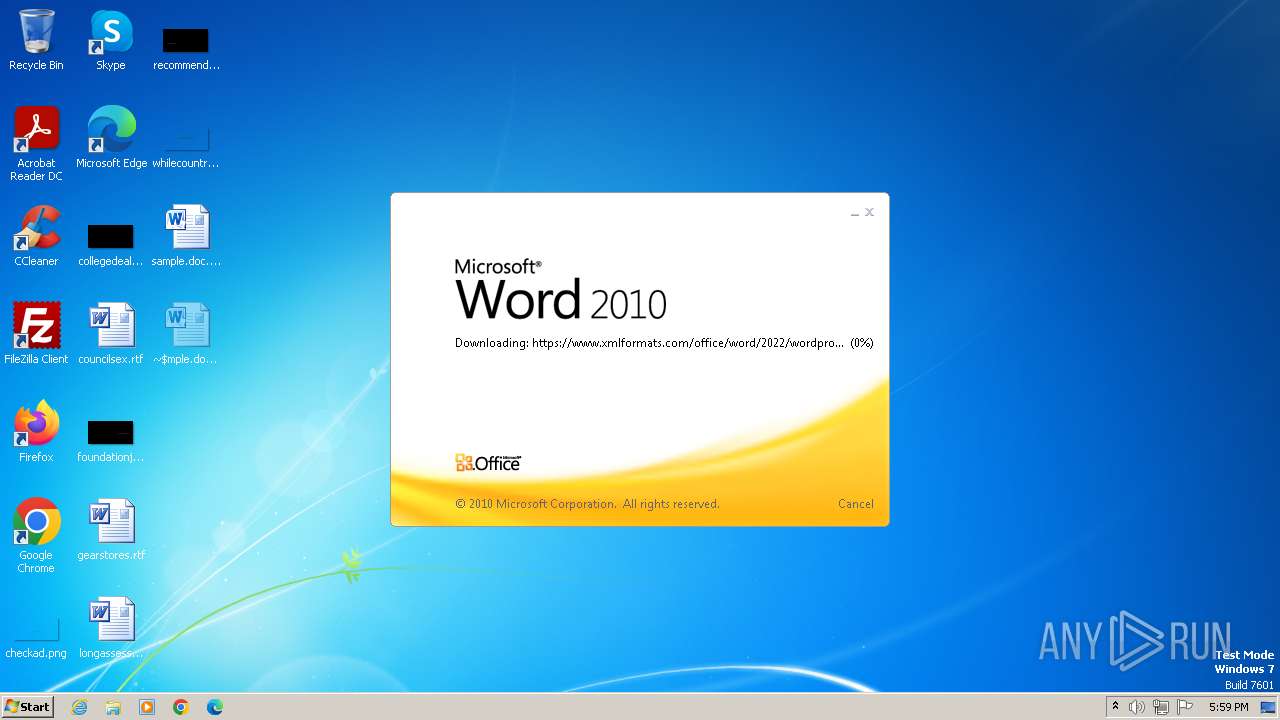
Connection from MS Office application
- WINWORD.EXE (PID: 2876)
CVE-2022-30190 detected
- WINWORD.EXE (PID: 2876)
SUSPICIOUS
No suspicious indicators.INFO
Reads the computer name
- wmpnscfg.exe (PID: 3028)
Checks supported languages
- wmpnscfg.exe (PID: 3028)
Manual execution by a user
- wmpnscfg.exe (PID: 3028)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .docx | | | Word Microsoft Office Open XML Format document (52.2) |
|---|---|---|
| .zip | | | Open Packaging Conventions container (38.8) |
| .zip | | | ZIP compressed archive (8.8) |
EXIF
ZIP
| ZipRequiredVersion: | 20 |
|---|---|
| ZipBitFlag: | - |
| ZipCompression: | Deflated |
| ZipModifyDate: | 2022:05:26 23:08:14 |
| ZipCRC: | 0x6cd2a4df |
| ZipCompressedSize: | 340 |
| ZipUncompressedSize: | 1312 |
| ZipFileName: | [Content_Types].xml |
XML
| Template: | Normal |
|---|---|
| TotalEditTime: | - |
| Pages: | 1 |
| Words: | - |
| Characters: | - |
| Application: | Microsoft Office Word |
| DocSecurity: | None |
| Lines: | - |
| Paragraphs: | - |
| ScaleCrop: | No |
| Company: | - |
| LinksUpToDate: | No |
| CharactersWithSpaces: | - |
| SharedDoc: | No |
| HyperlinksChanged: | No |
| AppVersion: | 16 |
| Keywords: | - |
| LastModifiedBy: | KIS2 |
| RevisionNumber: | 3 |
| CreateDate: | 2022:05:25 13:14:00Z |
| ModifyDate: | 2022:05:25 13:14:00Z |
XMP
| Title: | - |
|---|---|
| Subject: | - |
| Creator: | KIS2 |
| Description: | - |
Total processes
41
Monitored processes
2
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 2876 | "C:\Program Files\Microsoft Office\Office14\WINWORD.EXE" /n "C:\Users\admin\Desktop\sample.doc.docx" | C:\Program Files\Microsoft Office\Office14\WINWORD.EXE | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Word Exit code: 0 Version: 14.0.6024.1000 Modules
| |||||||||||||||
| 3028 | "C:\Program Files\Windows Media Player\wmpnscfg.exe" | C:\Program Files\Windows Media Player\wmpnscfg.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Media Player Network Sharing Service Configuration Application Exit code: 0 Version: 12.0.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
Total events
6 454
Read events
6 408
Write events
44
Delete events
2
Modification events
| (PID) Process: | (2876) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1033 |
Value: On | |||
| (PID) Process: | (2876) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1041 |
Value: On | |||
| (PID) Process: | (2876) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1046 |
Value: On | |||
| (PID) Process: | (2876) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1036 |
Value: On | |||
| (PID) Process: | (2876) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1031 |
Value: On | |||
| (PID) Process: | (2876) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1040 |
Value: On | |||
| (PID) Process: | (2876) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1049 |
Value: On | |||
| (PID) Process: | (2876) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 3082 |
Value: On | |||
| (PID) Process: | (2876) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1042 |
Value: On | |||
| (PID) Process: | (2876) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1055 |
Value: On | |||
Executable files
0
Suspicious files
20
Text files
1
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2876 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\CVR6891.tmp.cvr | — | |
MD5:— | SHA256:— | |||
| 2876 | WINWORD.EXE | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\77EC63BDA74BD0D0E0426DC8F8008506 | compressed | |
MD5:AC05D27423A85ADC1622C714F2CB6184 | SHA256:C6456E12E5E53287A547AF4103E0397CB9697E466CF75844312DC296D43D144D | |||
| 2876 | WINWORD.EXE | C:\Users\admin\AppData\Roaming\Microsoft\Templates\~$Normal.dotm | binary | |
MD5:A6959F09D40504F443D7D7F00B02C699 | SHA256:BD81C0921D598CE602CE539A4148E6474DD905DF44F02B62CEC1B95F68E20EDA | |||
| 2876 | WINWORD.EXE | C:\Users\admin\Desktop\~$mple.doc.docx | binary | |
MD5:5253C71CA6FF7570550C35658B7349F5 | SHA256:8865051516F865ED4111C1E3D5D21520381704495C44DF8E16ED6B678F62EE3F | |||
| 2876 | WINWORD.EXE | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\77EC63BDA74BD0D0E0426DC8F8008506 | binary | |
MD5:7B25080EAC5539509B93CB2890058E6B | SHA256:FD507B16886EEB52315AE2954B2395DE646583C48F208302F081C1C2A4065A60 | |||
| 2876 | WINWORD.EXE | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\57C8EDB95DF3F0AD4EE2DC2B8CFD4157 | compressed | |
MD5:1BFE591A4FE3D91B03CDF26EAACD8F89 | SHA256:9CF94355051BF0F4A45724CA20D1CC02F76371B963AB7D1E38BD8997737B13D8 | |||
| 2876 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\{0A2445B1-D1D3-4C0D-B4FE-DEE38519CA58} | binary | |
MD5:75B564A327C5E2B0C9590E10E89ECC97 | SHA256:885FFD6BB14E14CDE55EC2AB1CB78630E3DD51CD150D1A34B6BBDF0CAC2B43C8 | |||
| 2876 | WINWORD.EXE | C:\Users\admin\AppData\Local\Microsoft\Office\14.0\OfficeFileCache\FSF-CTBL.FSF | binary | |
MD5:D471A0BB5F0B8A9AC834E0172491B7F9 | SHA256:418B6AE0A39787583DCD77DA0ED040F8C3DDA03410E71D04C235EE6E736F298F | |||
| 2876 | WINWORD.EXE | C:\Users\admin\AppData\Local\Microsoft\Office\14.0\OfficeFileCache\FSD-CNRY.FSD | binary | |
MD5:75B564A327C5E2B0C9590E10E89ECC97 | SHA256:885FFD6BB14E14CDE55EC2AB1CB78630E3DD51CD150D1A34B6BBDF0CAC2B43C8 | |||
| 2876 | WINWORD.EXE | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\57C8EDB95DF3F0AD4EE2DC2B8CFD4157 | binary | |
MD5:E01DCB582C56CE61D54FB8EE14ECD24E | SHA256:D472085F6DF48B5193C947F43F19FF1F1C85556889D63490641100955438F8FB | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
4
TCP/UDP connections
17
DNS requests
4
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
2876 | WINWORD.EXE | GET | 200 | 184.24.77.182:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?6ea339178e435175 | unknown | compressed | 4.66 Kb | unknown |
2876 | WINWORD.EXE | GET | 200 | 184.24.77.182:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/authrootstl.cab?2f8511e6b388c308 | unknown | compressed | 65.2 Kb | unknown |
2876 | WINWORD.EXE | GET | 200 | 184.24.77.51:80 | http://r3.o.lencr.org/MFMwUTBPME0wSzAJBgUrDgMCGgUABBRI2smg%2ByvTLU%2Fw3mjS9We3NfmzxAQUFC6zF7dYVsuuUAlA5h%2BvnYsUwsYCEgMI8XpXEjsum17fv0J8zOHIgQ%3D%3D | unknown | binary | 503 b | unknown |
2876 | WINWORD.EXE | GET | 200 | 23.212.210.158:80 | http://x1.c.lencr.org/ | unknown | binary | 717 b | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
2588 | svchost.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
1080 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |
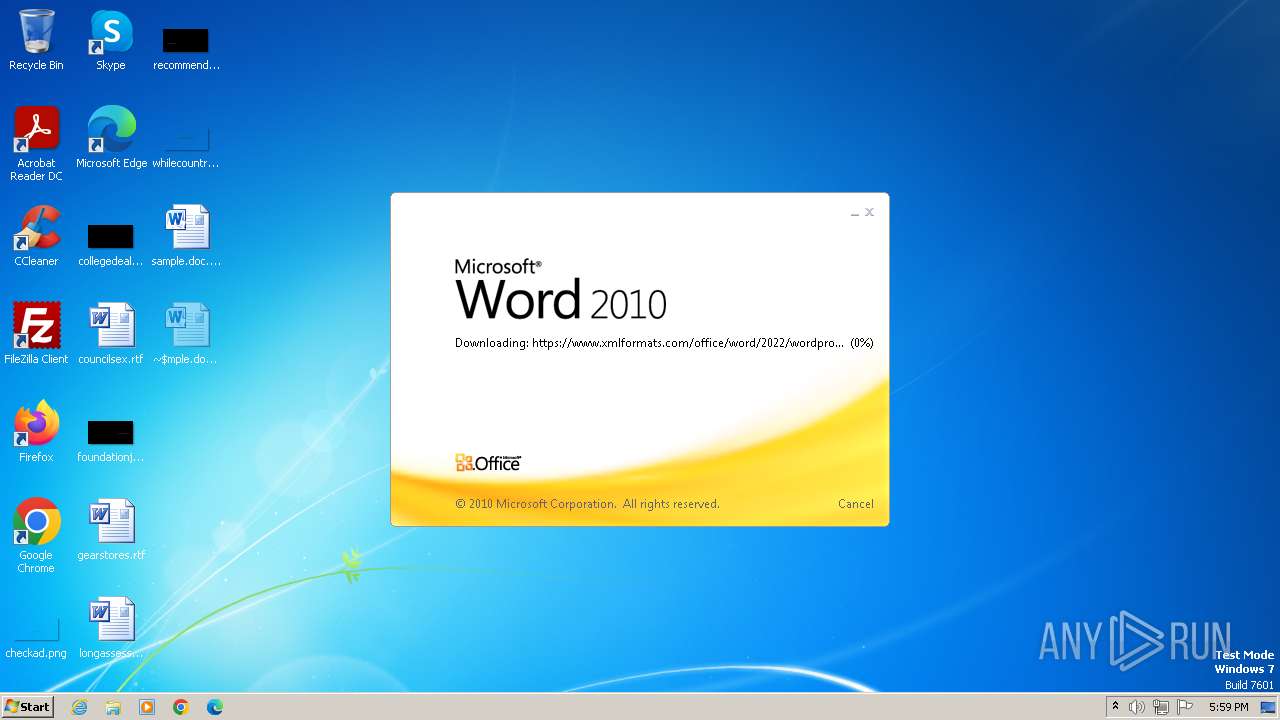
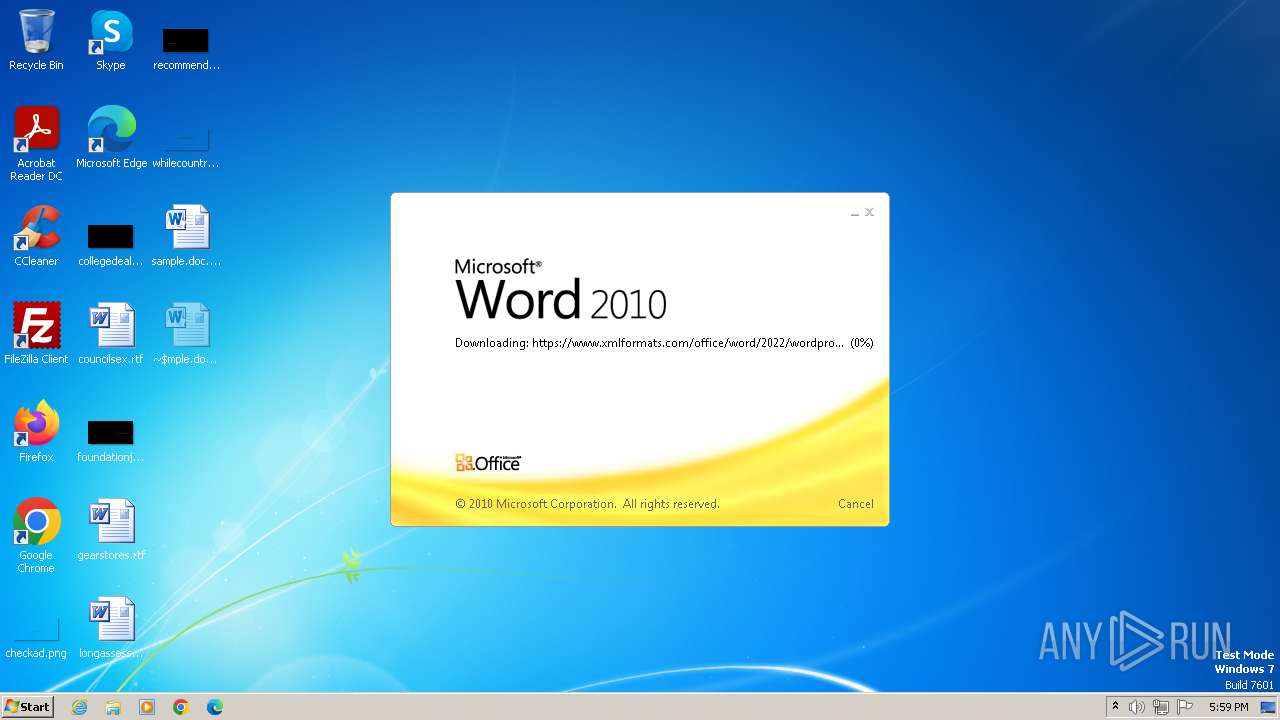
2876 | WINWORD.EXE | 162.210.196.172:443 | www.xmlformats.com | LEASEWEB-USA-WDC | US | unknown |
2876 | WINWORD.EXE | 184.24.77.182:80 | ctldl.windowsupdate.com | Akamai International B.V. | DE | unknown |
2876 | WINWORD.EXE | 23.212.210.158:80 | x1.c.lencr.org | AKAMAI-AS | AU | unknown |
2876 | WINWORD.EXE | 184.24.77.51:80 | r3.o.lencr.org | Akamai International B.V. | DE | unknown |
828 | svchost.exe | 162.210.196.172:443 | www.xmlformats.com | LEASEWEB-USA-WDC | US | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
www.xmlformats.com |
| unknown |
ctldl.windowsupdate.com |
| whitelisted |
x1.c.lencr.org |
| whitelisted |
r3.o.lencr.org |
| shared |