| File name: | sample.doc |
| Full analysis: | https://app.any.run/tasks/b52df907-15ab-4600-a766-e5f2bcb537e3 |
| Verdict: | Malicious activity |
| Analysis date: | June 21, 2025, 12:18:54 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/vnd.openxmlformats-officedocument.wordprocessingml.document |
| File info: | Microsoft Word 2007+ |
| MD5: | 52945AF1DEF85B171870B31FA4782E52 |
| SHA1: | 06727FFDA60359236A8029E0B3E8A0FD11C23313 |
| SHA256: | 4A24048F81AFBE9FB62E7A6A49ADBD1FAF41F266B5F9FEECDCEB567AEC096784 |
| SSDEEP: | 192:AEhM7fIUU09264wptGheab8h7Z/c+8poF1d3jvvtl59rGxjPQDasYBcG7h+:AqWfIz092hwLGAabkcfa7pr1lzyxjPQ9 |
MALICIOUS
PHISHING has been detected (SURICATA)
- svchost.exe (PID: 1080)
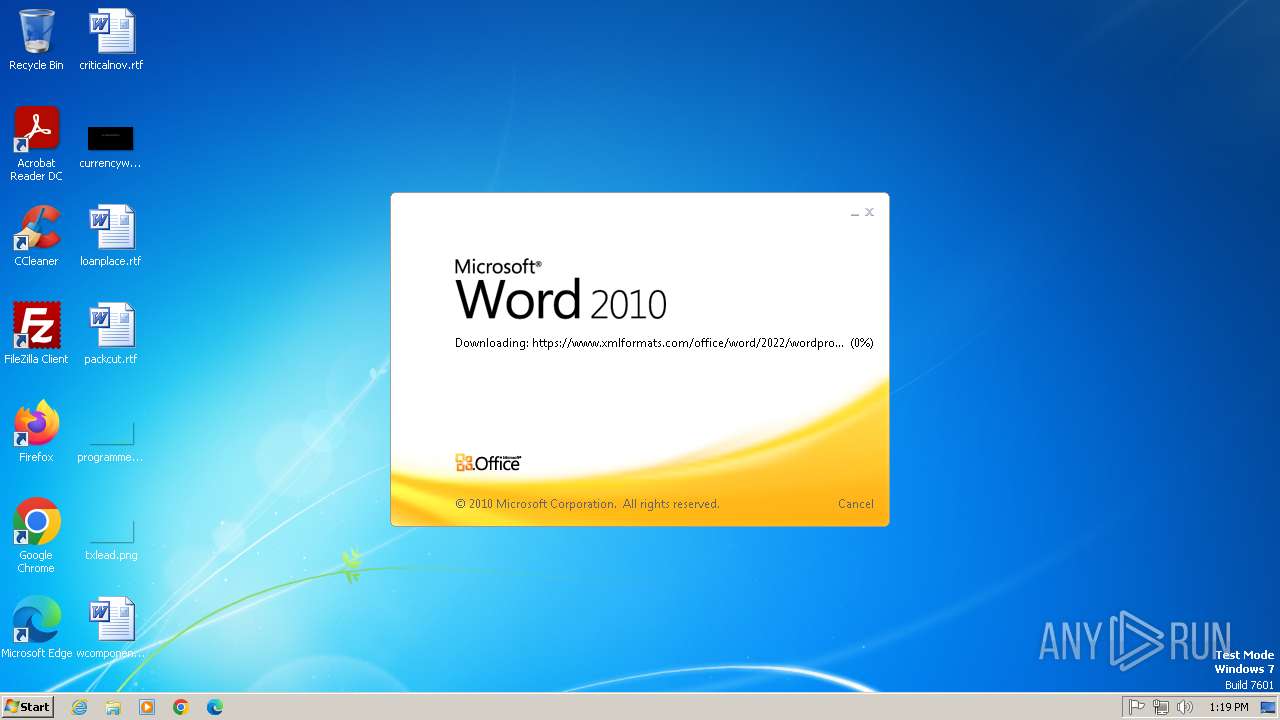
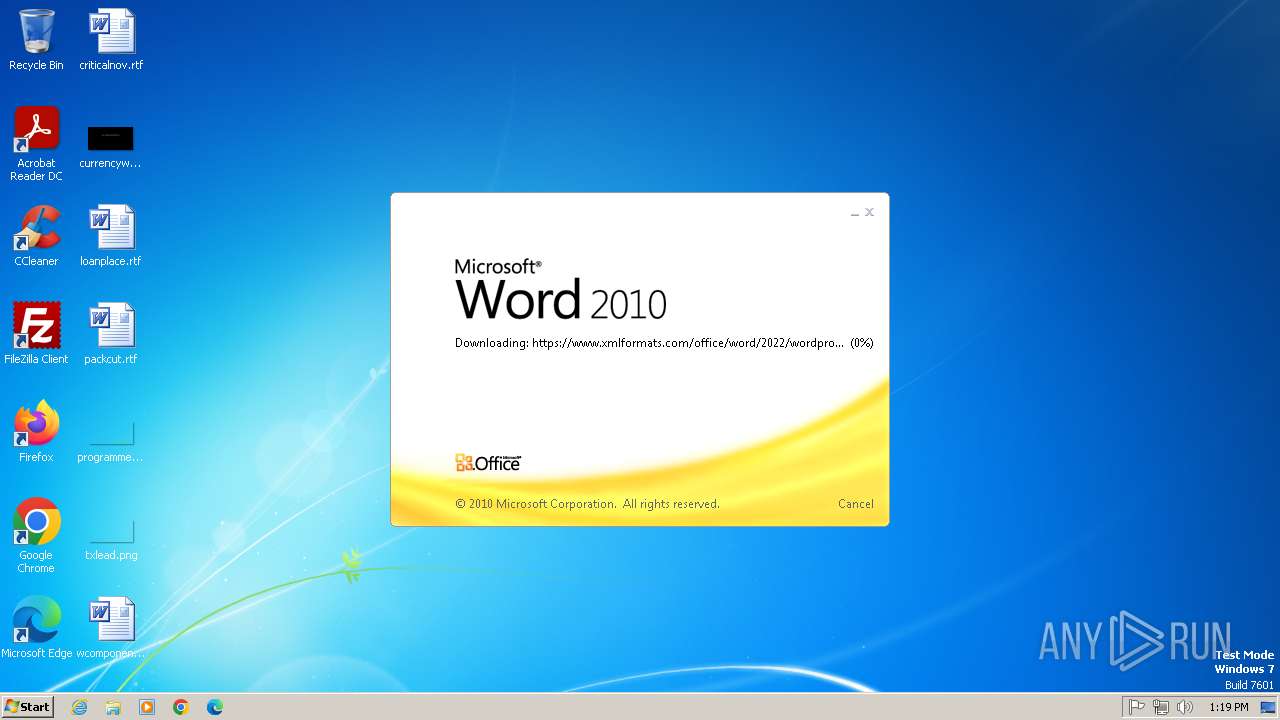
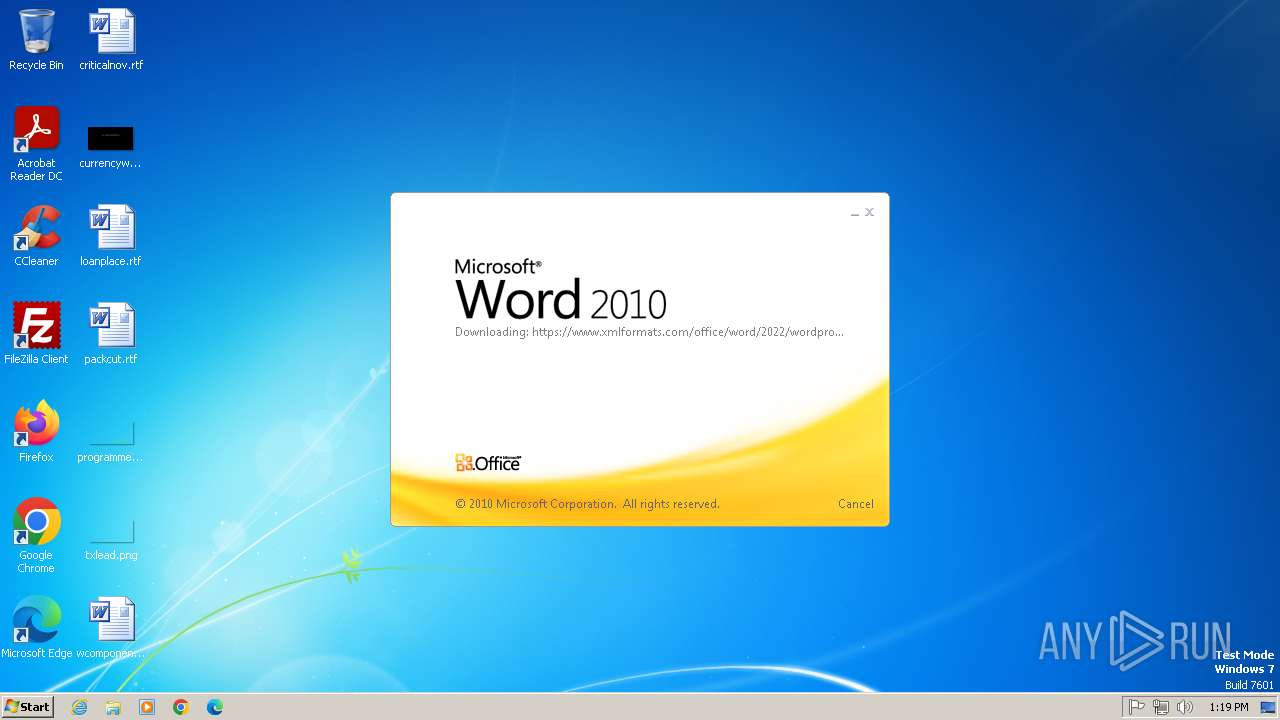
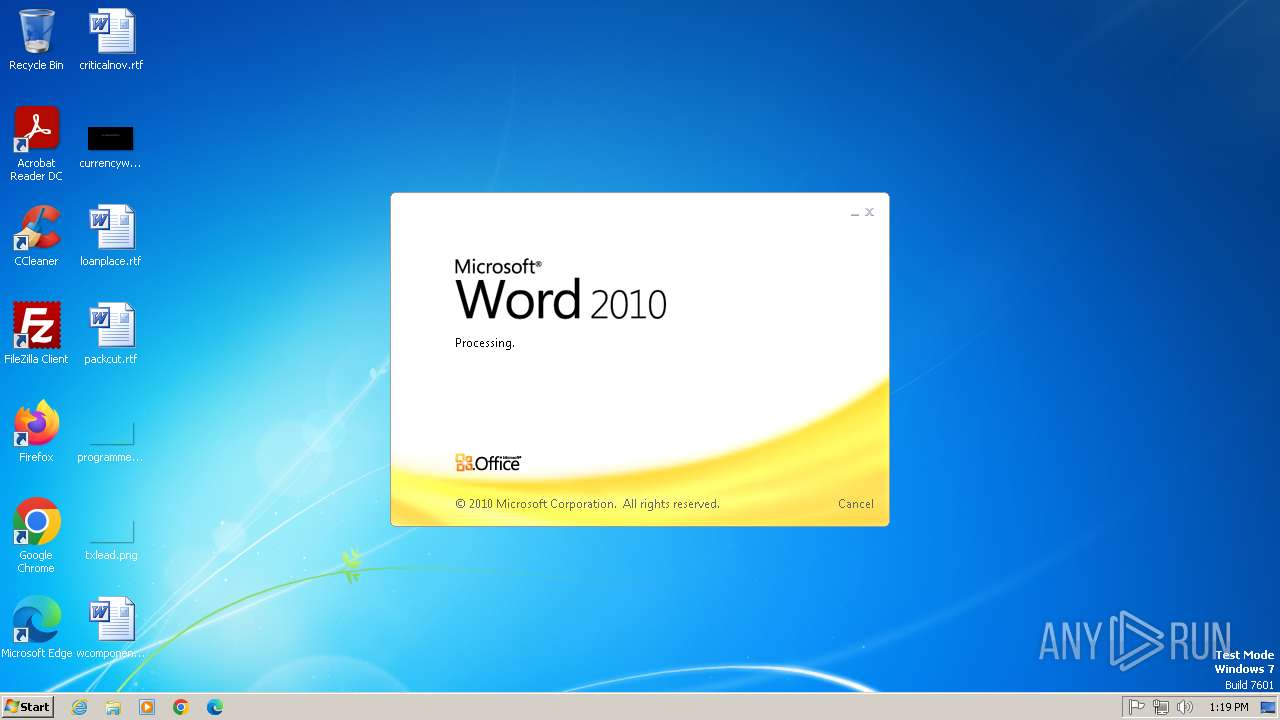
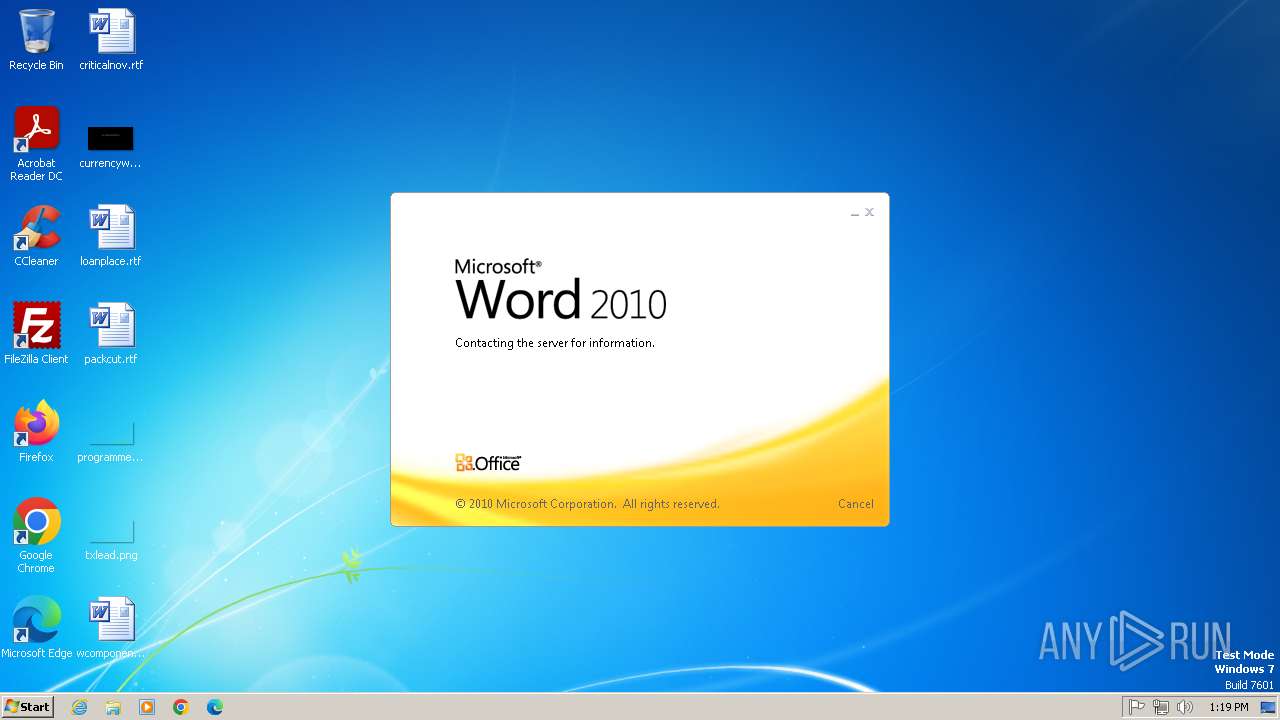
CVE-2022-30190 detected
- WINWORD.EXE (PID: 2784)
SUSPICIOUS
Uses RUNDLL32.EXE to load library
- svchost.exe (PID: 832)
Abuses WebDav for code execution
- svchost.exe (PID: 832)
INFO
An automatically generated document
- WINWORD.EXE (PID: 2784)
Reads Internet Explorer settings
- WINWORD.EXE (PID: 2784)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .docx | | | Word Microsoft Office Open XML Format document (52.2) |
|---|---|---|
| .zip | | | Open Packaging Conventions container (38.8) |
| .zip | | | ZIP compressed archive (8.8) |
EXIF
ZIP
| ZipRequiredVersion: | 20 |
|---|---|
| ZipBitFlag: | - |
| ZipCompression: | Deflated |
| ZipModifyDate: | 2022:05:26 23:08:14 |
| ZipCRC: | 0x6cd2a4df |
| ZipCompressedSize: | 340 |
| ZipUncompressedSize: | 1312 |
| ZipFileName: | [Content_Types].xml |
XML
| Template: | Normal |
|---|---|
| TotalEditTime: | - |
| Pages: | 1 |
| Words: | - |
| Characters: | - |
| Application: | Microsoft Office Word |
| DocSecurity: | None |
| Lines: | - |
| Paragraphs: | - |
| ScaleCrop: | No |
| Company: | - |
| LinksUpToDate: | No |
| CharactersWithSpaces: | - |
| SharedDoc: | No |
| HyperlinksChanged: | No |
| AppVersion: | 16 |
| Keywords: | - |
| LastModifiedBy: | KIS2 |
| RevisionNumber: | 3 |
| CreateDate: | 2022:05:25 13:14:00Z |
| ModifyDate: | 2022:05:25 13:14:00Z |
XMP
| Title: | - |
|---|---|
| Subject: | - |
| Creator: | KIS2 |
| Description: | - |
Total processes
36
Monitored processes
3
Malicious processes
2
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 832 | C:\Windows\system32\svchost.exe -k LocalService | C:\Windows\System32\svchost.exe | services.exe | ||||||||||||
User: LOCAL SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Host Process for Windows Services Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1080 | C:\Windows\system32\svchost.exe -k NetworkService | C:\Windows\System32\svchost.exe | services.exe | ||||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Host Process for Windows Services Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2784 | "C:\Program Files\Microsoft Office\Office14\WINWORD.EXE" /n C:\Users\admin\AppData\Local\Temp\sample.doc.docx | C:\Program Files\Microsoft Office\Office14\WINWORD.EXE | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Word Version: 14.0.6024.1000 Modules
| |||||||||||||||
Total events
17 085
Read events
16 122
Write events
641
Delete events
322
Modification events
| (PID) Process: | (2784) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1033 |
Value: Off | |||
| (PID) Process: | (2784) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1041 |
Value: Off | |||
| (PID) Process: | (2784) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1046 |
Value: Off | |||
| (PID) Process: | (2784) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1036 |
Value: Off | |||
| (PID) Process: | (2784) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1031 |
Value: Off | |||
| (PID) Process: | (2784) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1040 |
Value: Off | |||
| (PID) Process: | (2784) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1049 |
Value: Off | |||
| (PID) Process: | (2784) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 3082 |
Value: Off | |||
| (PID) Process: | (2784) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1042 |
Value: Off | |||
| (PID) Process: | (2784) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1055 |
Value: Off | |||
Executable files
0
Suspicious files
20
Text files
10
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2784 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\CVR198E.tmp.cvr | — | |
MD5:— | SHA256:— | |||
| 2784 | WINWORD.EXE | C:\Users\admin\AppData\Roaming\Microsoft\Templates\~$Normal.dotm | binary | |
MD5:19C57C60E19DBCE27F6478C3B6BDAE0E | SHA256:CEB02504CF0662570FDB98ACC49BDC2063F3C3132141553F455C1E39945554E9 | |||
| 2784 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\~$mple.doc.docx | binary | |
MD5:B7636505C87276635EF7BBAF1E98C4A3 | SHA256:3A60CE401BA2B5065987B448EC0676F82F54A50CF3F3A32303B66034197E9DC4 | |||
| 2784 | WINWORD.EXE | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\57C8EDB95DF3F0AD4EE2DC2B8CFD4157 | compressed | |
MD5:77B20B5CD41BC6BB475CCA3F91AE6E3C | SHA256:5511A9B9F9144ED7BDE4CCB074733B7C564D918D2A8B10D391AFC6BE5B3B1509 | |||
| 1080 | svchost.exe | C:\Windows\ServiceProfiles\NetworkService\AppData\Local\Temp\Tar1E03.tmp | binary | |
MD5:91A1B89AA7A488DBB204DBB4767F1F21 | SHA256:F6BE95C88C20EF82EE8A6878E16F9ECD77300BC1905EB826592A0DD41AD1C0F8 | |||
| 1080 | svchost.exe | C:\Windows\ServiceProfiles\NetworkService\AppData\Local\Temp\Cab1E02.tmp | compressed | |
MD5:77B20B5CD41BC6BB475CCA3F91AE6E3C | SHA256:5511A9B9F9144ED7BDE4CCB074733B7C564D918D2A8B10D391AFC6BE5B3B1509 | |||
| 2784 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\{3371FB17-B6AC-403D-A043-1C1110D38B47} | binary | |
MD5:1A0F556E1C4CA79AE00B39C63FE007CF | SHA256:25ABB96449B06C655644A82565673DD1DC24187E6DBD345E14848A0A89052673 | |||
| 2784 | WINWORD.EXE | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\57C8EDB95DF3F0AD4EE2DC2B8CFD4157 | binary | |
MD5:1F6A5E33A0BEF2689CA888477483275D | SHA256:11B511D275CE8DFCCC267B315BF52DA4BDAC8C681249C6589C4B75E73E48CCE7 | |||
| 2784 | WINWORD.EXE | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\96027925CAA49D567EF24E394DA96DDC_E3A1357637564DB9BE9C638629EAA28C | binary | |
MD5:49EC1E263A7FC5A4AF4EEF0819933CBA | SHA256:1B13195022F3DD626EF5E3D4E721D153BB41AD6119331D02DBD2CB90279B51CC | |||
| 2784 | WINWORD.EXE | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\103621DE9CD5414CC2538780B4B75751 | binary | |
MD5:E192462F281446B5D1500D474FBACC4B | SHA256:F1BA9F1B63C447682EBF9DE956D0DA2A027B1B779ABEF9522D347D3479139A60 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
10
TCP/UDP connections
25
DNS requests
8
Threats
2
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
2784 | WINWORD.EXE | GET | 200 | 199.232.210.172:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?e0bdab21959fb02a | unknown | — | — | whitelisted |
2784 | WINWORD.EXE | GET | 200 | 72.246.169.163:80 | http://x1.c.lencr.org/ | unknown | — | — | whitelisted |
2784 | WINWORD.EXE | GET | 200 | 184.24.77.65:80 | http://r10.o.lencr.org/MFMwUTBPME0wSzAJBgUrDgMCGgUABBRpD%2BQVZ%2B1vf7U0RGQGBm8JZwdxcgQUdKR2KRcYVIUxN75n5gZYwLzFBXICEgbDfqxCJlObkwJ9KGuu2JC5Yg%3D%3D | unknown | — | — | whitelisted |
2784 | WINWORD.EXE | HEAD | 200 | 199.59.243.228:80 | http://survey-smiles.com/ | unknown | — | — | whitelisted |
2784 | WINWORD.EXE | HEAD | 200 | 199.59.243.228:80 | http://survey-smiles.com/ | unknown | — | — | whitelisted |
2784 | WINWORD.EXE | HEAD | 200 | 199.59.243.228:80 | http://survey-smiles.com/ | unknown | — | — | whitelisted |
2784 | WINWORD.EXE | HEAD | 200 | 199.59.243.228:80 | http://survey-smiles.com/ | unknown | — | — | whitelisted |
2784 | WINWORD.EXE | POST | 302 | 2.18.97.227:80 | http://go.microsoft.com/fwlink/?LinkID=120750 | unknown | — | — | whitelisted |
2784 | WINWORD.EXE | POST | 302 | 2.18.97.227:80 | http://go.microsoft.com/fwlink/?LinkID=120751 | unknown | — | — | whitelisted |
2784 | WINWORD.EXE | POST | 302 | 2.18.97.227:80 | http://go.microsoft.com/fwlink/?LinkID=120752 | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
— | — | 224.0.0.252:5355 | — | — | — | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
1080 | svchost.exe | 224.0.0.252:5355 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
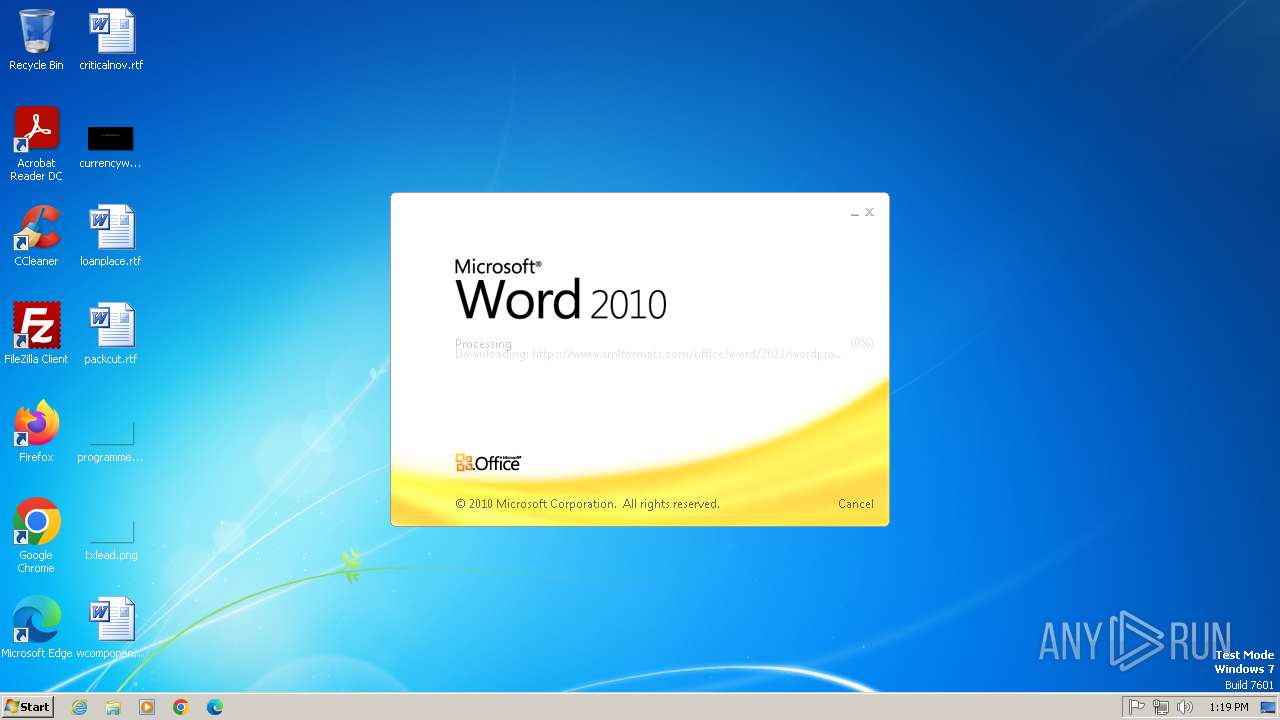
2784 | WINWORD.EXE | 185.107.56.60:443 | www.xmlformats.com | NForce Entertainment B.V. | NL | malicious |
2784 | WINWORD.EXE | 199.232.210.172:80 | ctldl.windowsupdate.com | FASTLY | US | whitelisted |
2784 | WINWORD.EXE | 72.246.169.163:80 | x1.c.lencr.org | AKAMAI-AS | DE | whitelisted |
2784 | WINWORD.EXE | 184.24.77.65:80 | r10.o.lencr.org | Akamai International B.V. | DE | whitelisted |
832 | svchost.exe | 185.107.56.60:443 | www.xmlformats.com | NForce Entertainment B.V. | NL | malicious |
2784 | WINWORD.EXE | 199.59.243.228:80 | survey-smiles.com | AMAZON-02 | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
google.com |
| whitelisted |
www.xmlformats.com |
| unknown |
ctldl.windowsupdate.com |
| whitelisted |
x1.c.lencr.org |
| whitelisted |
r10.o.lencr.org |
| whitelisted |
survey-smiles.com |
| whitelisted |
go.microsoft.com |
| whitelisted |
activation.sls.microsoft.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2784 | WINWORD.EXE | Misc activity | ET USER_AGENTS Microsoft Office Existence Discovery User-Agent |
1 ETPRO signatures available at the full report