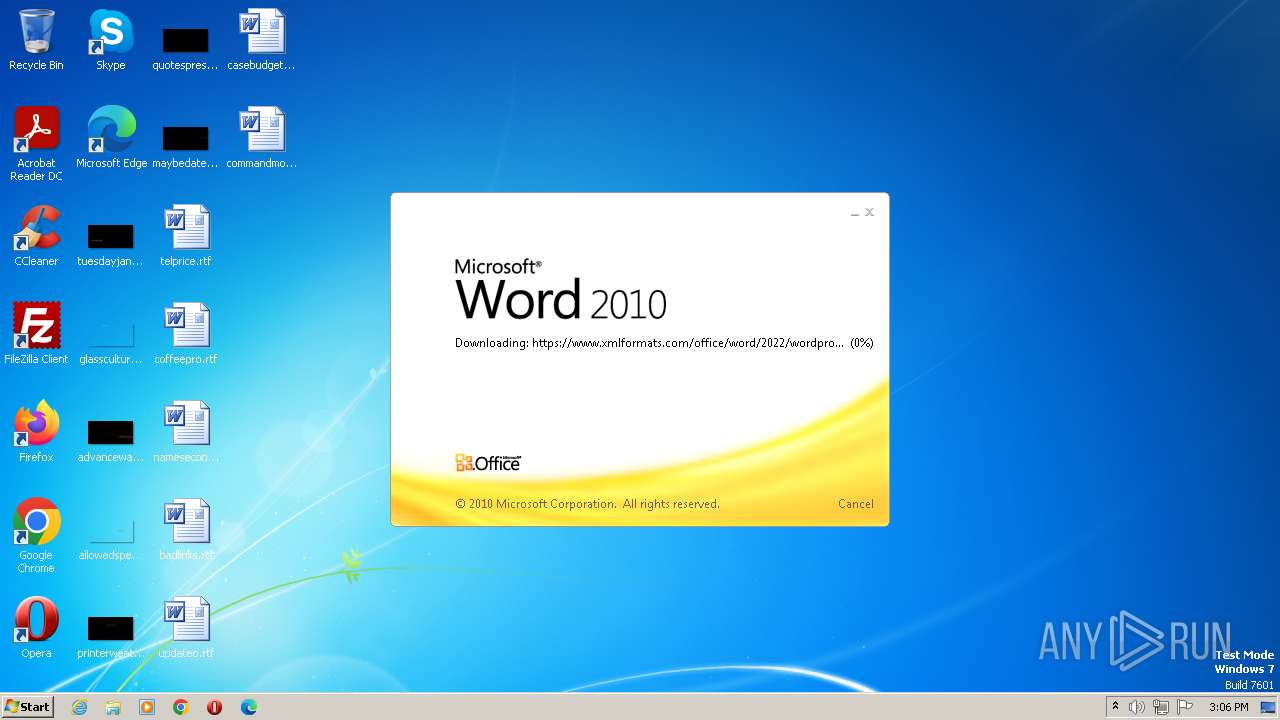
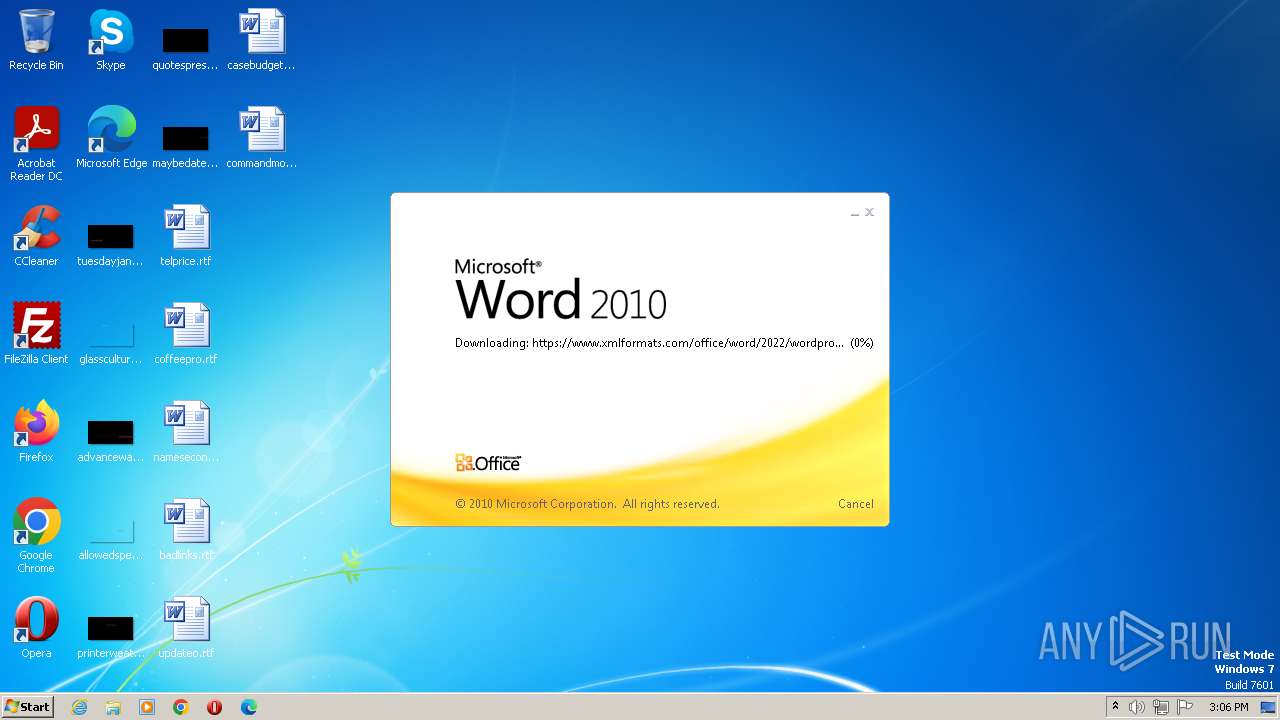
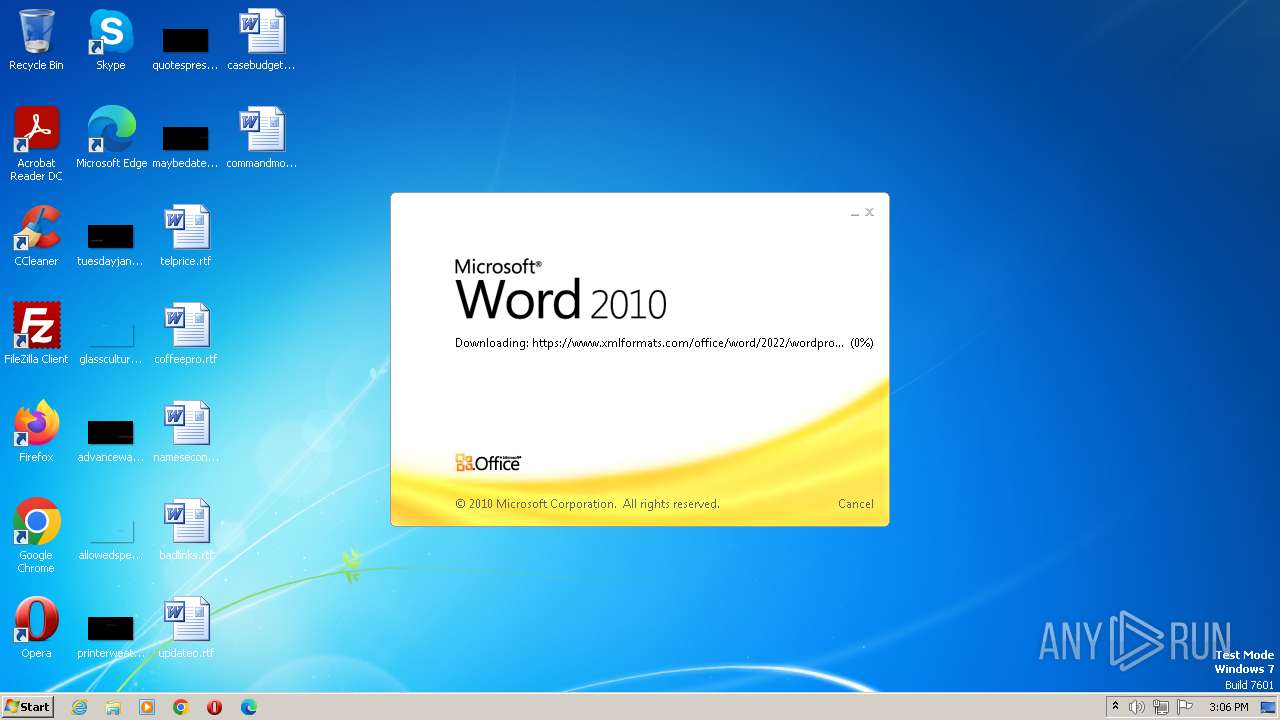
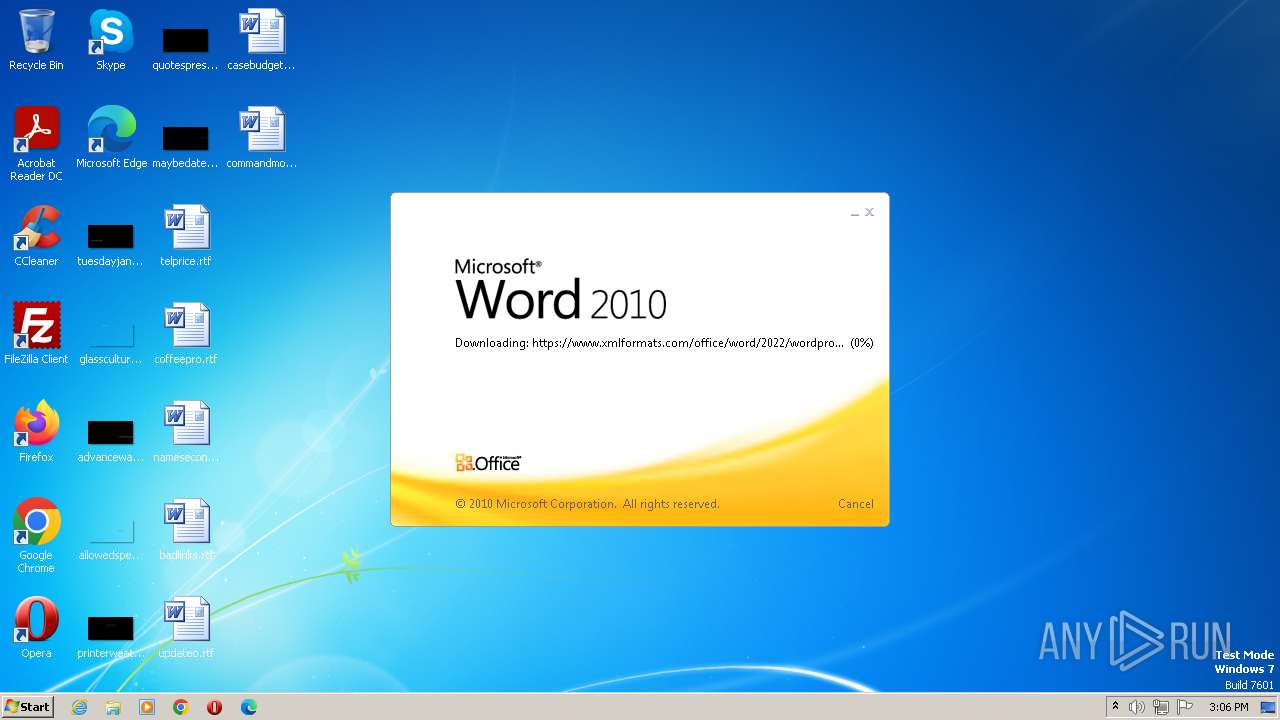
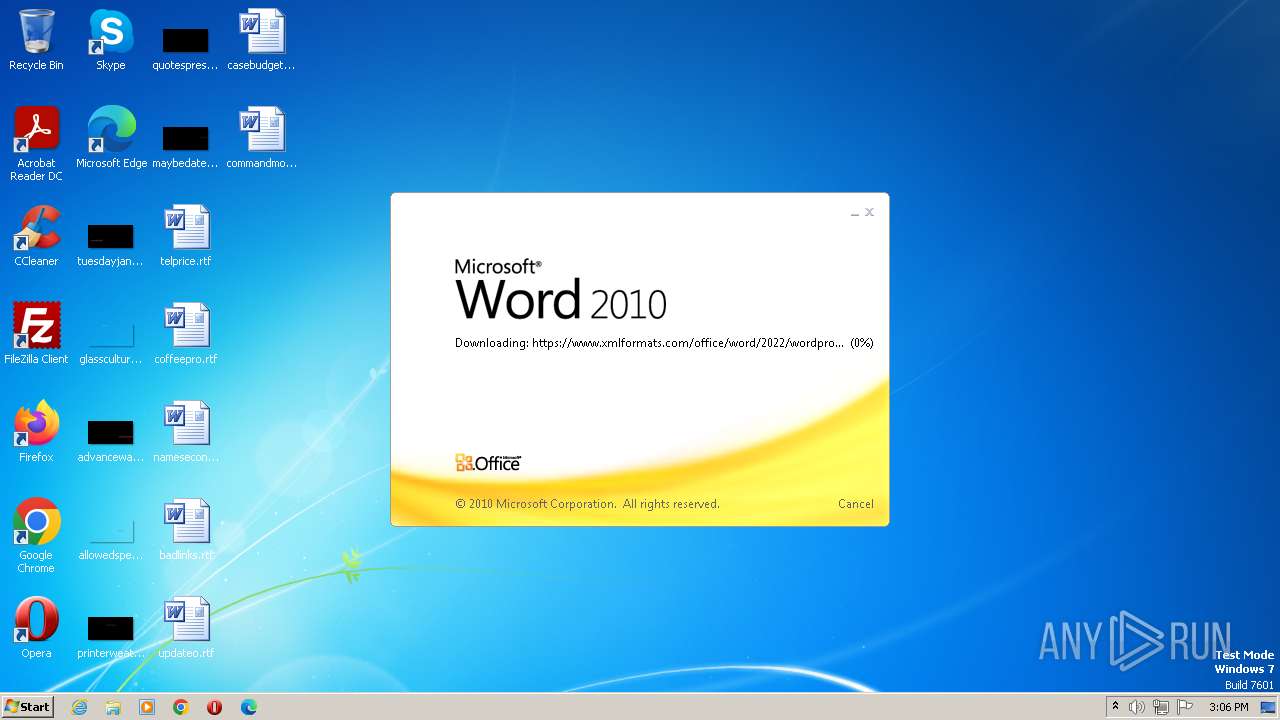
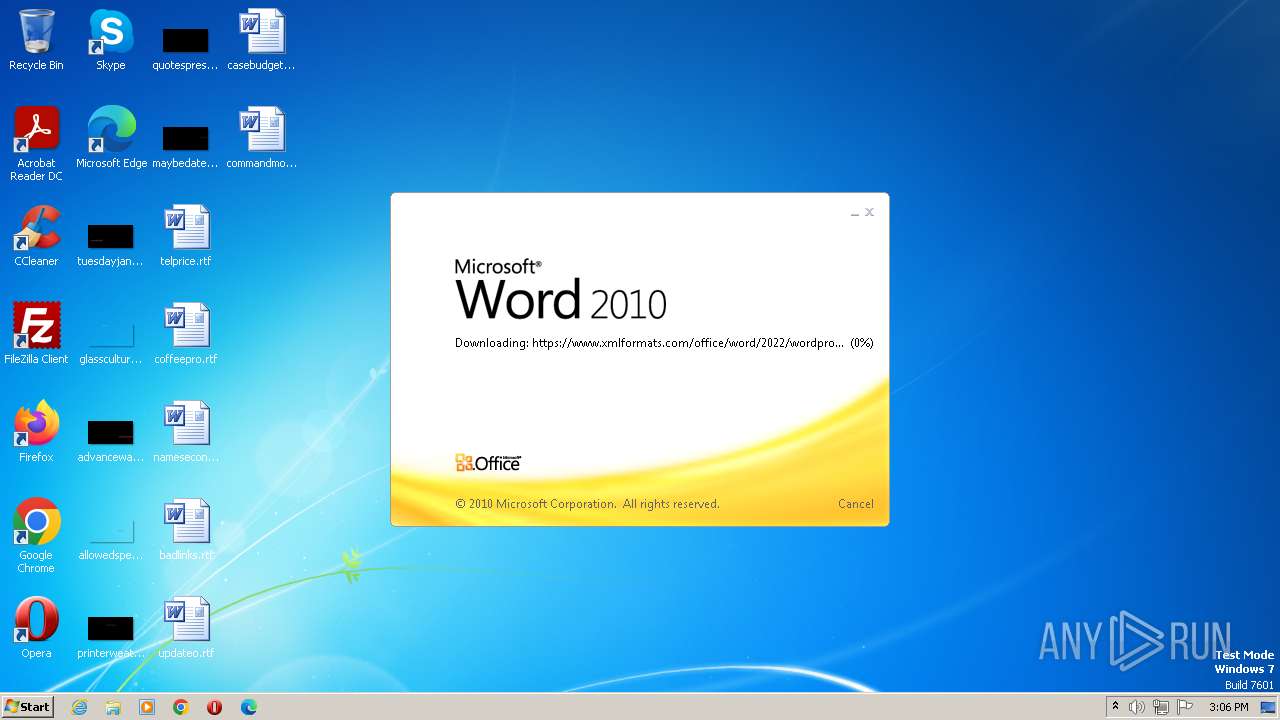
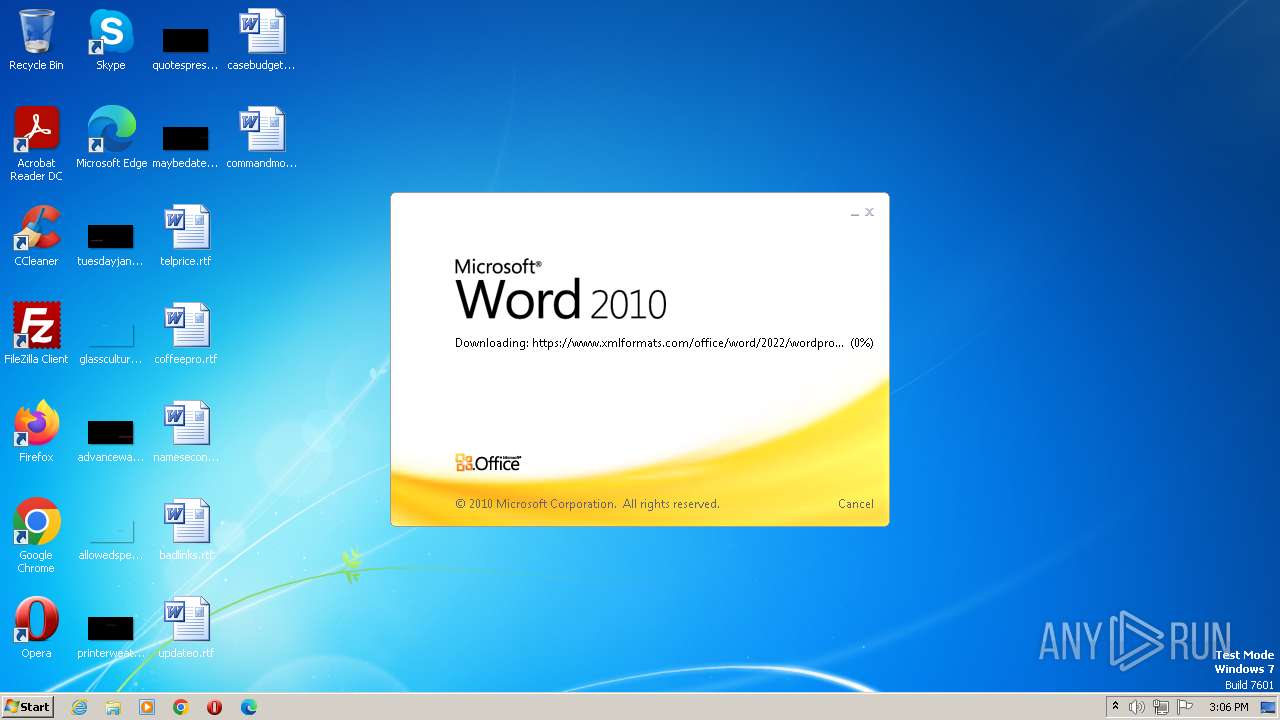
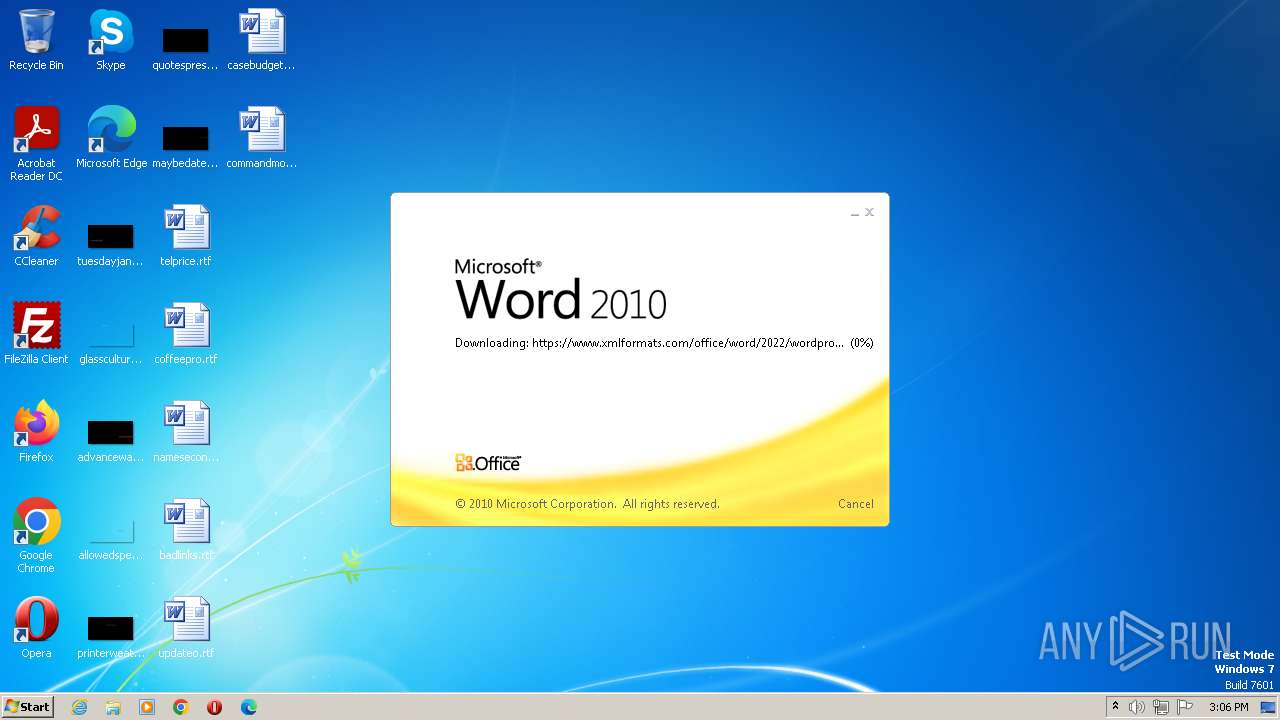
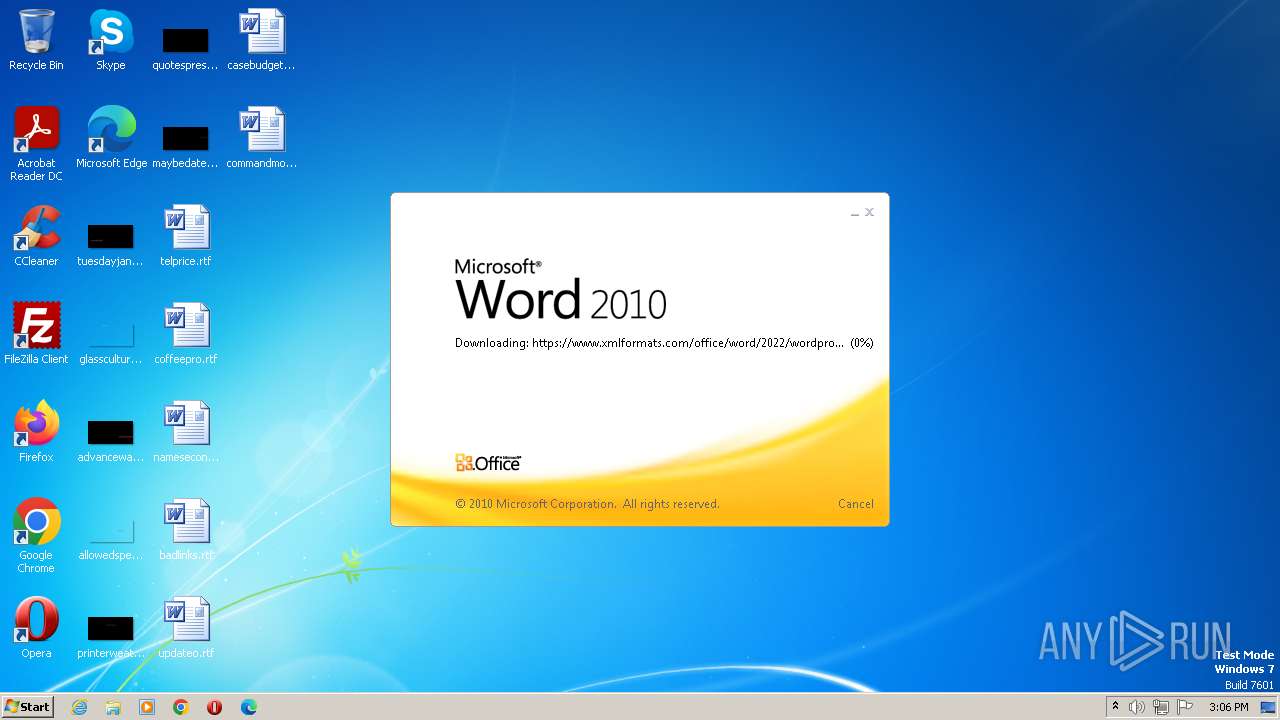
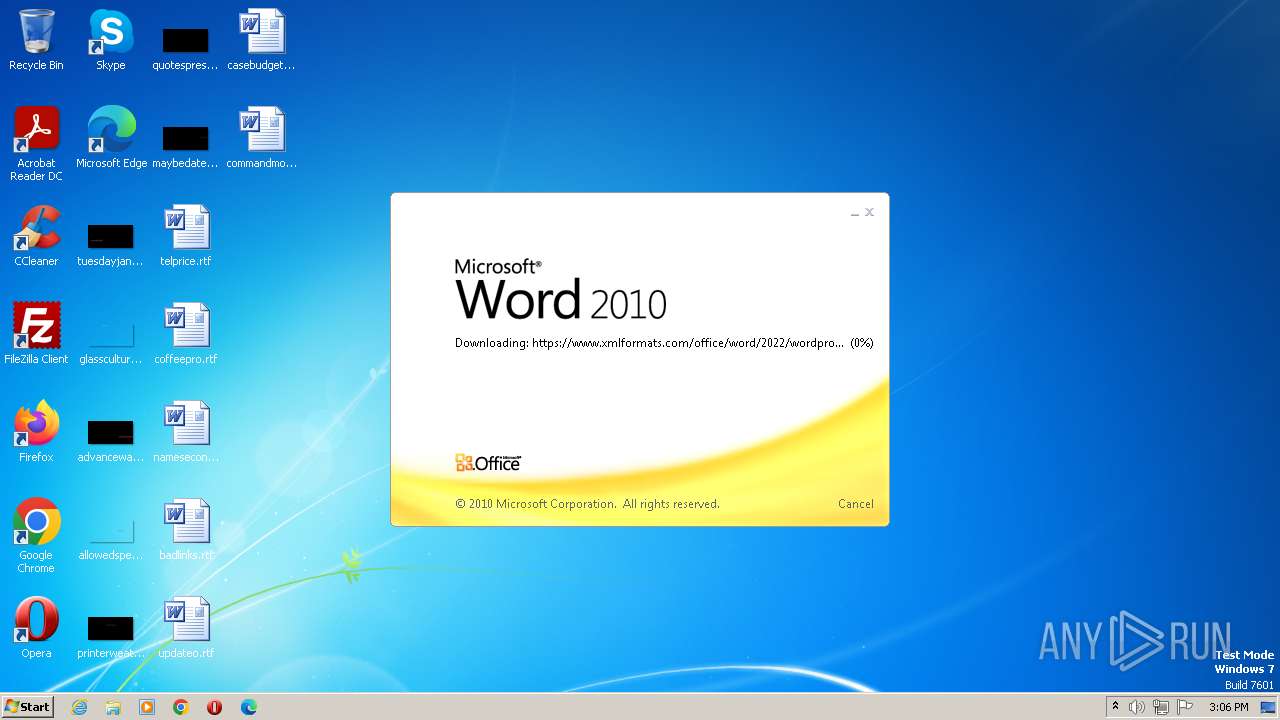
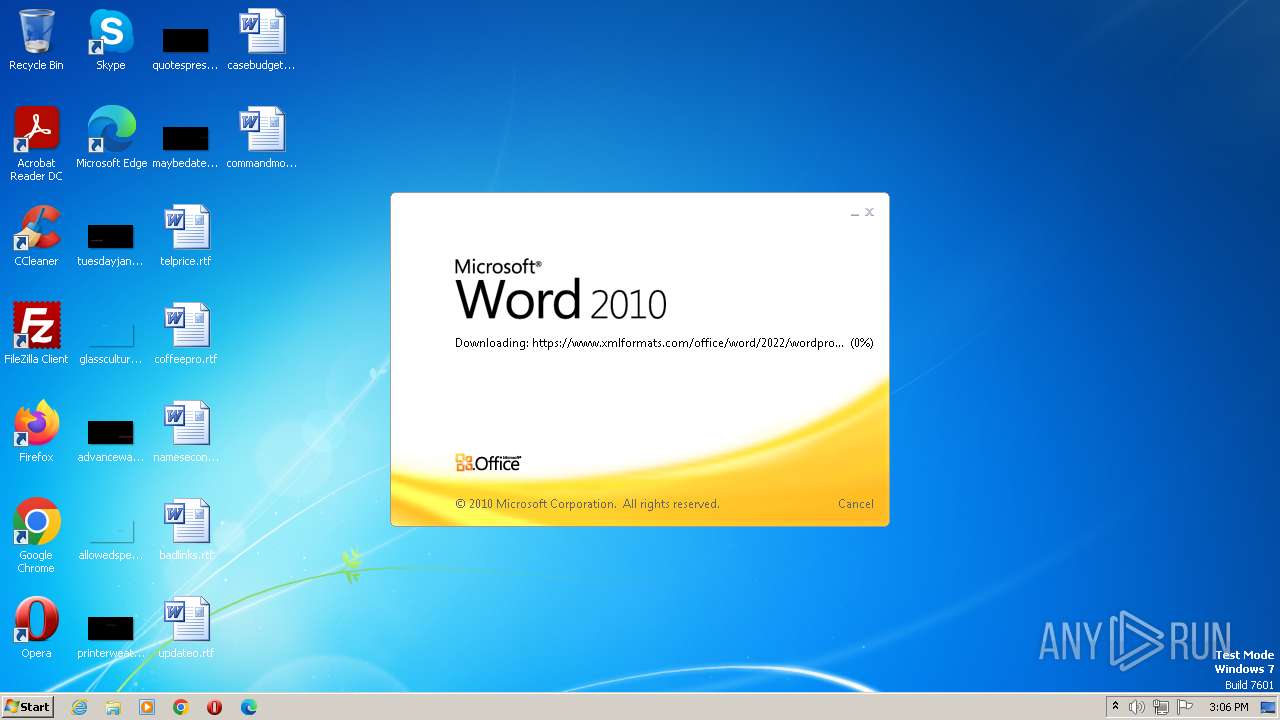
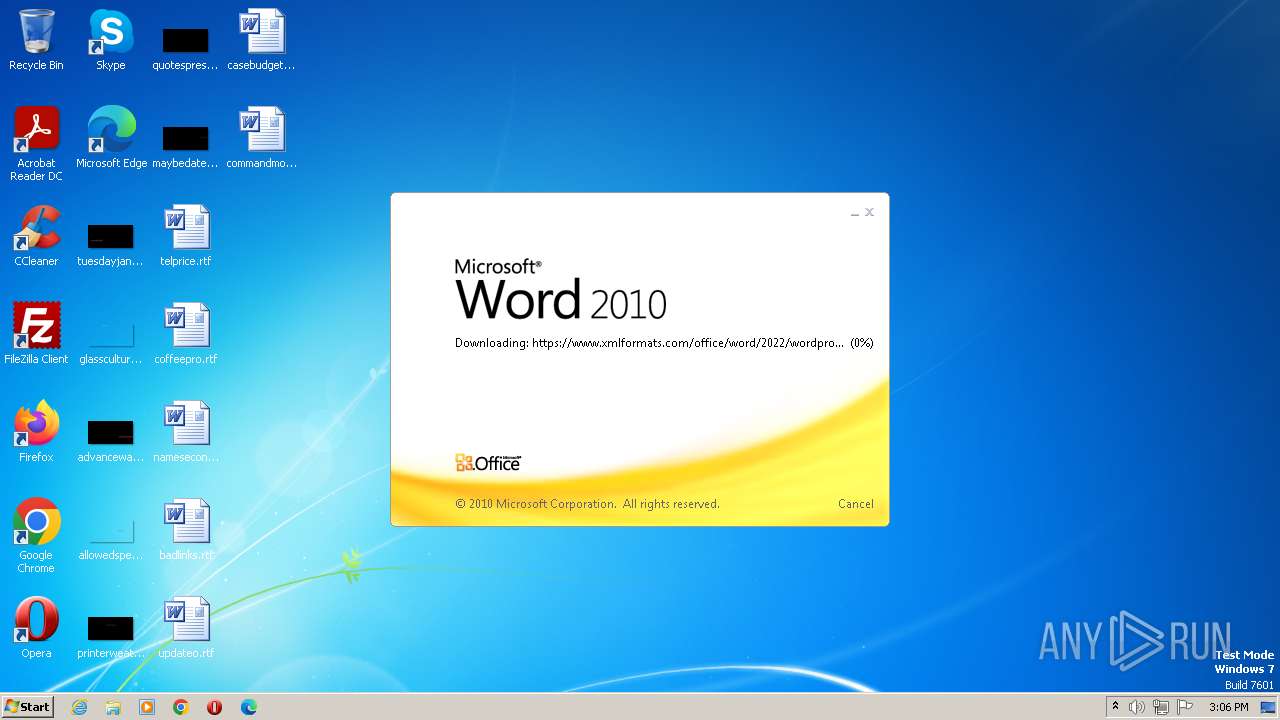
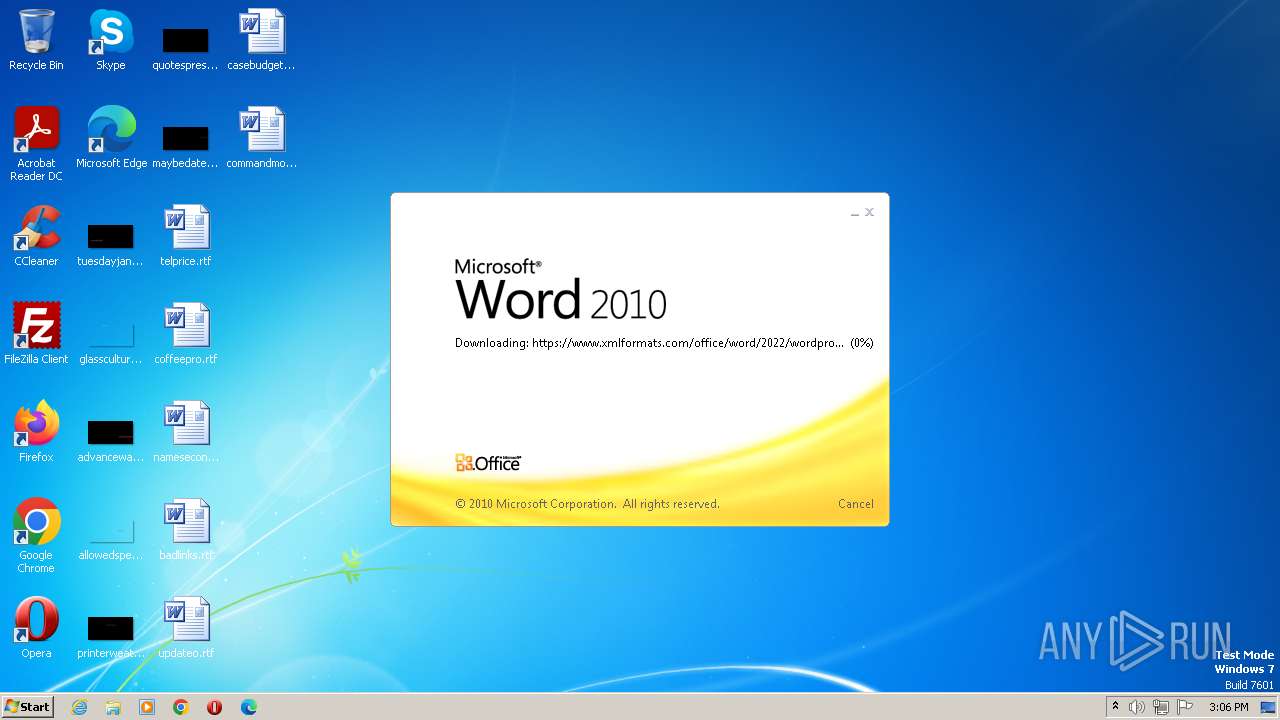
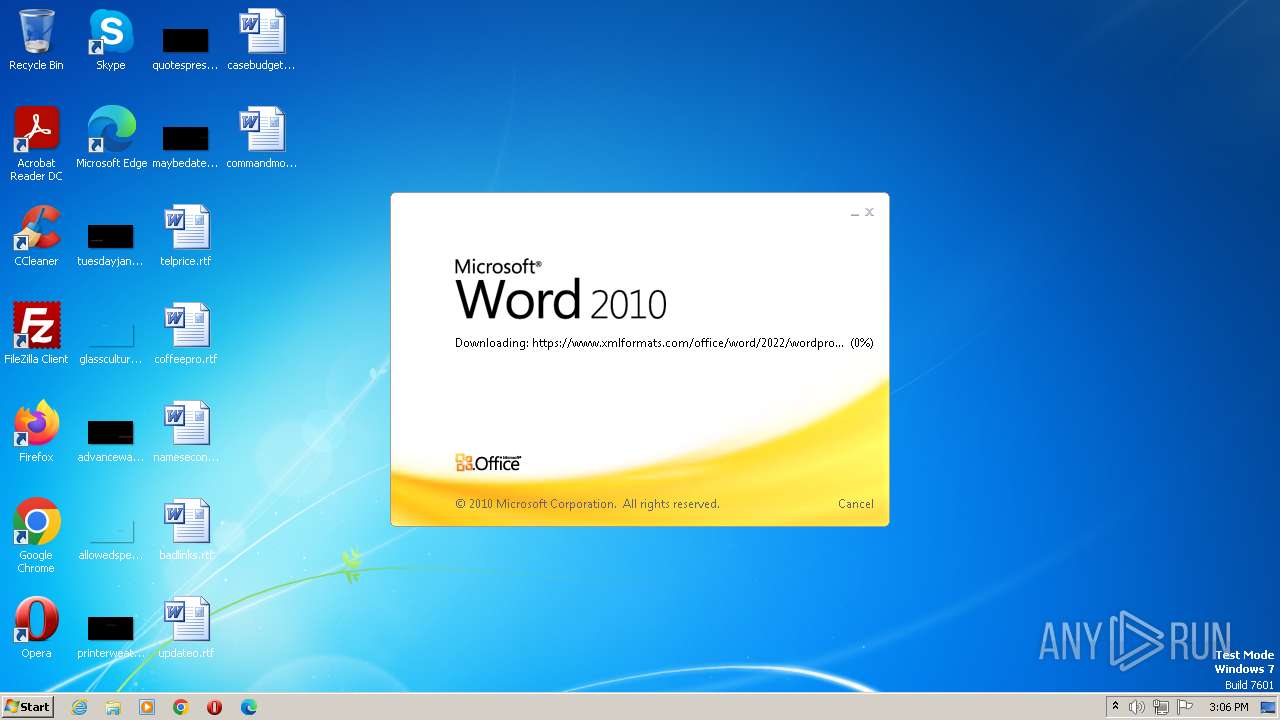
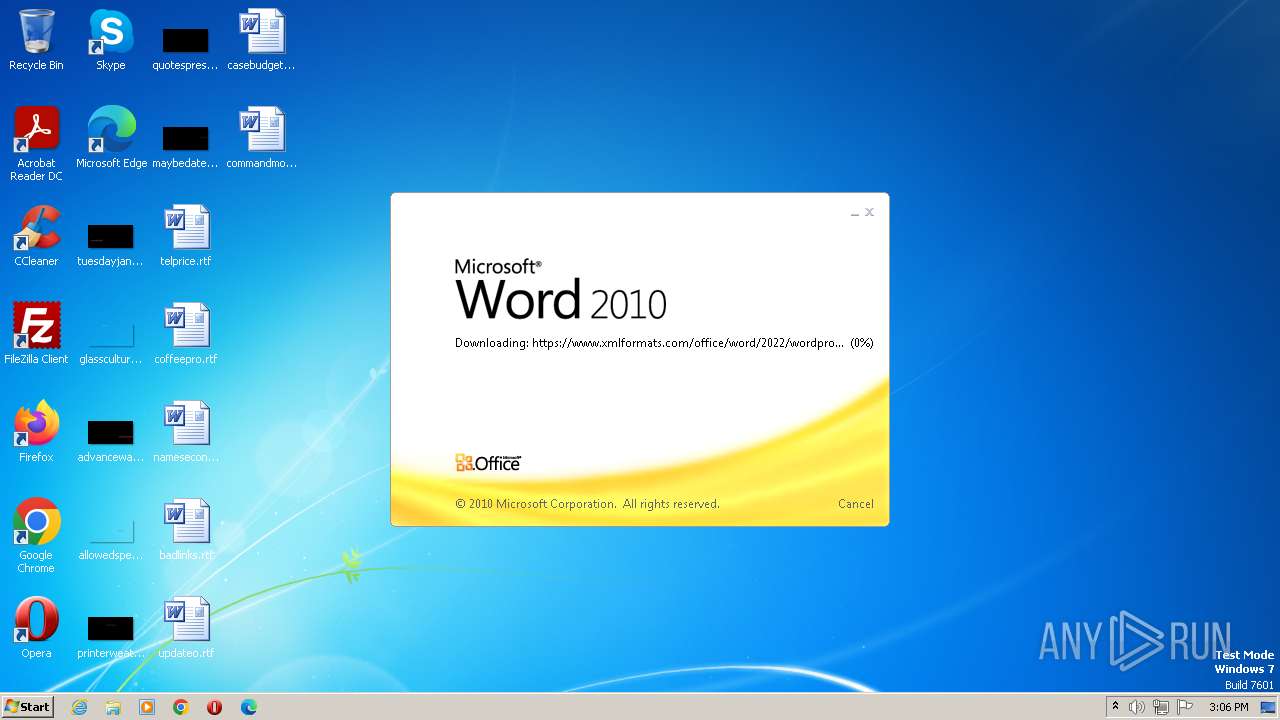
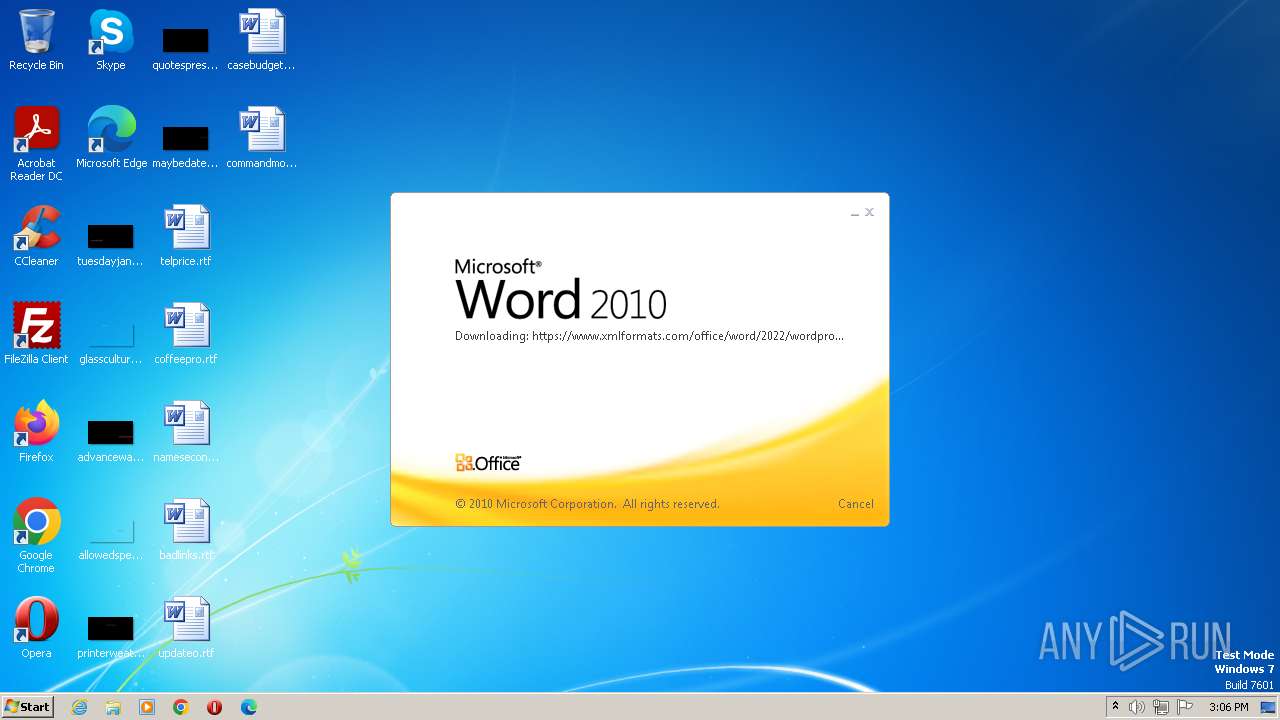
| File name: | sample.doc |
| Full analysis: | https://app.any.run/tasks/74918bfb-003f-4ad2-84b4-5e52fc69a132 |
| Verdict: | Malicious activity |
| Analysis date: | August 21, 2023, 14:05:42 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/vnd.openxmlformats-officedocument.wordprocessingml.document |
| File info: | Microsoft Word 2007+ |
| MD5: | 52945AF1DEF85B171870B31FA4782E52 |
| SHA1: | 06727FFDA60359236A8029E0B3E8A0FD11C23313 |
| SHA256: | 4A24048F81AFBE9FB62E7A6A49ADBD1FAF41F266B5F9FEECDCEB567AEC096784 |
| SSDEEP: | 192:AEhM7fIUU09264wptGheab8h7Z/c+8poF1d3jvvtl59rGxjPQDasYBcG7h+:AqWfIz092hwLGAabkcfa7pr1lzyxjPQ9 |
MALICIOUS
Connection from MS Office application
- WINWORD.EXE (PID: 3488)
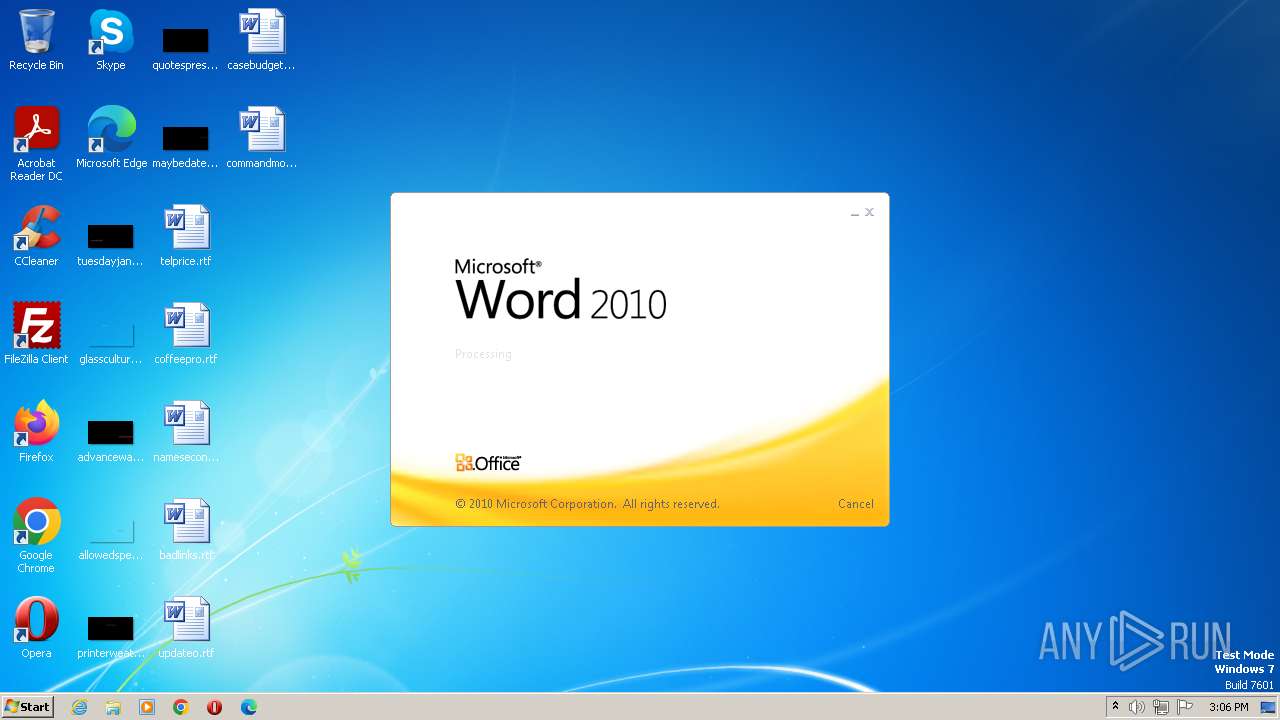
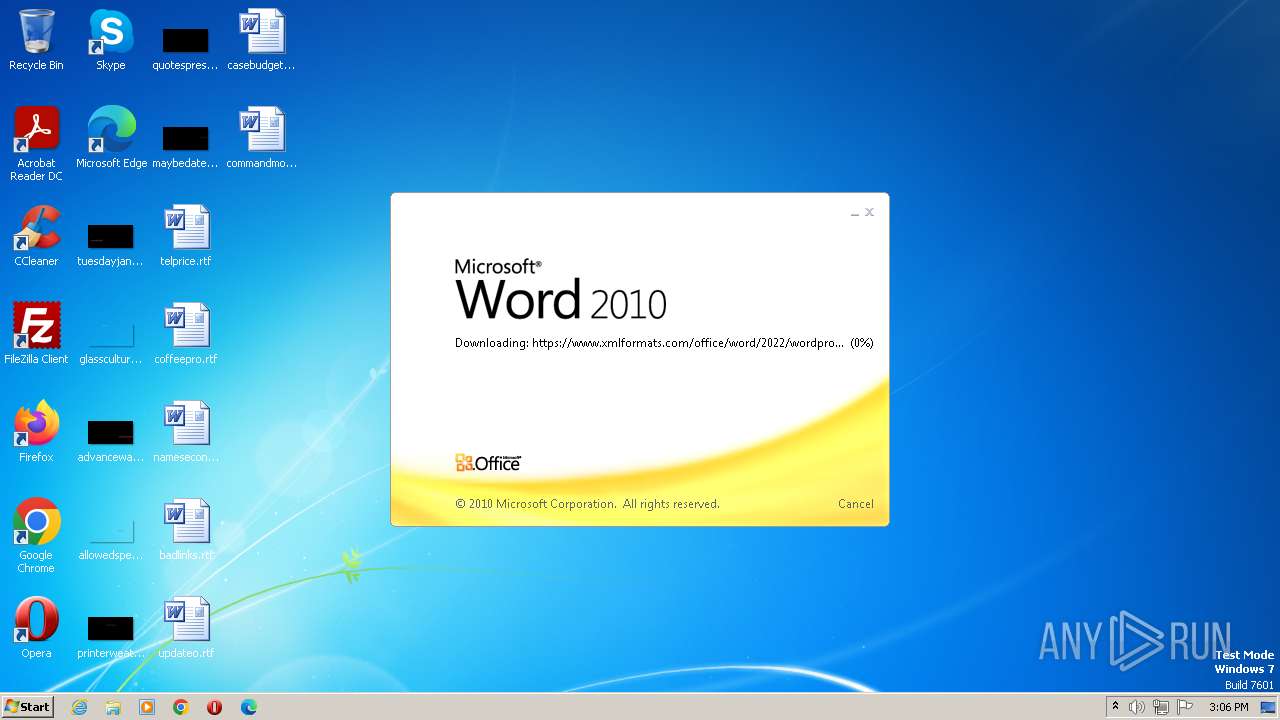
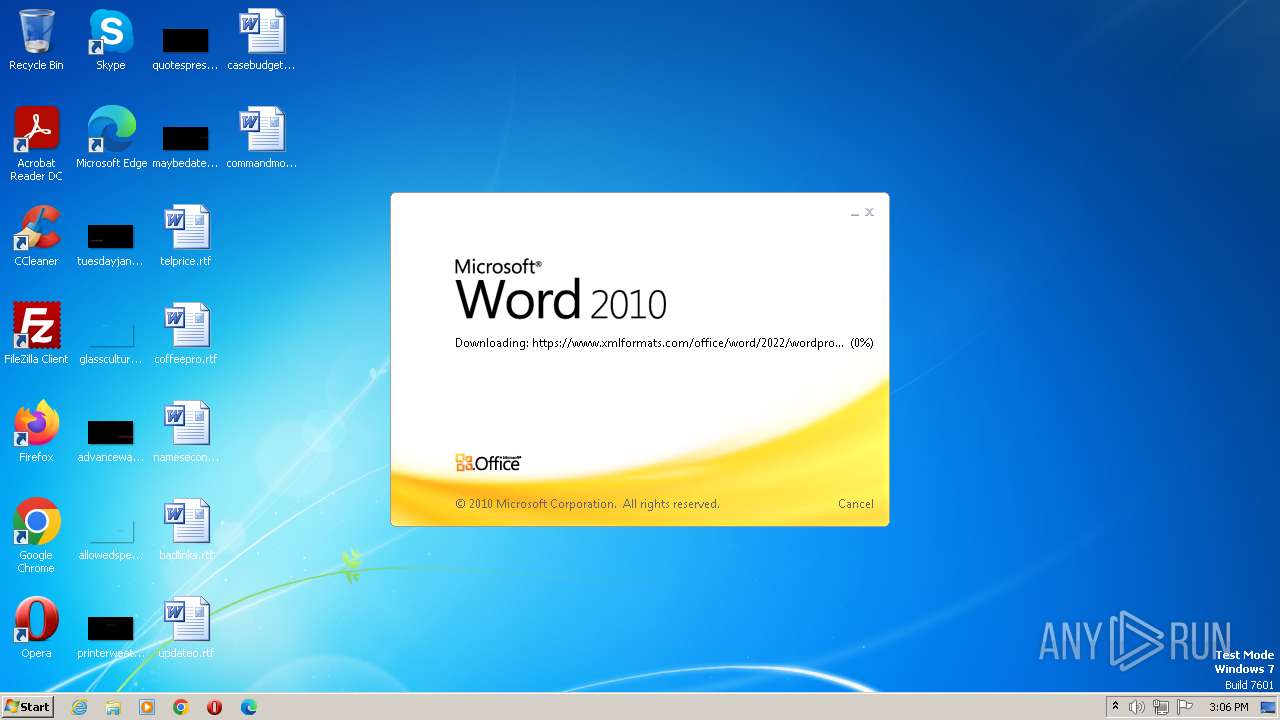
CVE-2022-30190 detected
- WINWORD.EXE (PID: 3488)
Steals credentials from Web Browsers
- CCleaner.exe (PID: 1900)
Actions looks like stealing of personal data
- CCleaner.exe (PID: 1900)
SUSPICIOUS
The process executes via Task Scheduler
- CCleanerBugReport.exe (PID: 3780)
- CCUpdate.exe (PID: 3744)
Reads settings of System Certificates
- CCleanerBugReport.exe (PID: 3780)
Executable content was dropped or overwritten
- CCUpdate.exe (PID: 3744)
Searches for installed software
- CCleaner.exe (PID: 1900)
INFO
Checks supported languages
- CCleanerBugReport.exe (PID: 3780)
- CCUpdate.exe (PID: 3744)
- CCleaner.exe (PID: 1900)
Reads the computer name
- CCleanerBugReport.exe (PID: 3780)
- CCUpdate.exe (PID: 3744)
- CCleaner.exe (PID: 1900)
Reads CPU info
- CCleanerBugReport.exe (PID: 3780)
- CCleaner.exe (PID: 1900)
Reads the machine GUID from the registry
- CCleanerBugReport.exe (PID: 3780)
- CCleaner.exe (PID: 1900)
Creates files in the program directory
- CCleanerBugReport.exe (PID: 3780)
- CCUpdate.exe (PID: 3744)
Reads Environment values
- CCleaner.exe (PID: 1900)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .docx | | | Word Microsoft Office Open XML Format document (52.2) |
|---|---|---|
| .zip | | | Open Packaging Conventions container (38.8) |
| .zip | | | ZIP compressed archive (8.8) |
EXIF
ZIP
| ZipFileName: | [Content_Types].xml |
|---|---|
| ZipUncompressedSize: | 1312 |
| ZipCompressedSize: | 340 |
| ZipCRC: | 0x6cd2a4df |
| ZipModifyDate: | 2022:05:26 23:08:14 |
| ZipCompression: | Deflated |
| ZipBitFlag: | - |
| ZipRequiredVersion: | 20 |
Total processes
45
Monitored processes
4
Malicious processes
4
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1900 | dummy /ccupdate | C:\Program Files\CCleaner\CCleaner.exe | CCUpdate.exe | ||||||||||||
User: SYSTEM Company: Piriform Software Ltd Integrity Level: SYSTEM Description: CCleaner Exit code: 0 Version: 6.14.0.10584 Modules
| |||||||||||||||
| 3488 | "C:\Program Files\Microsoft Office\Office14\WINWORD.EXE" /n "C:\Users\admin\AppData\Local\Temp\sample.doc.docx" | C:\Program Files\Microsoft Office\Office14\WINWORD.EXE | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Word Exit code: 0 Version: 14.0.6024.1000 Modules
| |||||||||||||||
| 3744 | "C:\Program Files\CCleaner\CCUpdate.exe" | C:\Program Files\CCleaner\CCUpdate.exe | taskeng.exe | ||||||||||||
User: SYSTEM Company: Piriform Software Ltd Integrity Level: SYSTEM Description: CCleaner CCleaner emergency updater Exit code: 0 Version: 23.3.12.0 Modules
| |||||||||||||||
| 3780 | "C:\Program Files\CCleaner\CCleanerBugReport.exe" --product 90 --send dumps|report --path "C:\Program Files\CCleaner\LOG" --programpath "C:\Program Files\CCleaner" --configpath "C:\Program Files\CCleaner\Setup" --guid "19ce970b-f6c0-4a09-bae4-274b971730e0" --version "6.14.10584" --silent | C:\Program Files\CCleaner\CCleanerBugReport.exe | taskeng.exe | ||||||||||||
User: admin Company: Piriform Software Integrity Level: HIGH Description: CCleaner Bug Report Exit code: 0 Version: 1.0.0.1 Modules
| |||||||||||||||
Total events
8 239
Read events
7 762
Write events
346
Delete events
131
Modification events
| (PID) Process: | (3488) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1033 |
Value: On | |||
| (PID) Process: | (3488) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1041 |
Value: On | |||
| (PID) Process: | (3488) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1046 |
Value: On | |||
| (PID) Process: | (3488) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1036 |
Value: On | |||
| (PID) Process: | (3488) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1031 |
Value: On | |||
| (PID) Process: | (3488) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1040 |
Value: On | |||
| (PID) Process: | (3488) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1049 |
Value: On | |||
| (PID) Process: | (3488) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 3082 |
Value: On | |||
| (PID) Process: | (3488) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1042 |
Value: On | |||
| (PID) Process: | (3488) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1055 |
Value: On | |||
Executable files
2
Suspicious files
9
Text files
4
Unknown types
2
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3488 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\CVR9AB0.tmp.cvr | — | |
MD5:— | SHA256:— | |||
| 3488 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\{9FEDDFB9-932D-4775-944C-67717BDD8A58} | binary | |
MD5:DDBE018FFC68137EB4973289AF0930E0 | SHA256:0E4FA8EE6B11F00F238A1F2BBABA6F6ABCB014DFC2576CBC4D1AB7CE415673CF | |||
| 3488 | WINWORD.EXE | C:\Users\admin\AppData\Roaming\Microsoft\Templates\~$Normal.dotm | pgc | |
MD5:FA22CA95E913BE2855D8120784640C1B | SHA256:43BB8030A2DC0564C530DB25FC9D4C5AB39142AC921461DABE8083D68343E25D | |||
| 3488 | WINWORD.EXE | C:\Users\admin\AppData\Local\Microsoft\Office\14.0\OfficeFileCache\FSD-{A253C6E7-0C92-4384-9F94-3EED57823E40}.FSD | binary | |
MD5:715B5B7BA60DA9998DA65D13A2B3BD2A | SHA256:ABC9DD8E4088EE40E9645AC5BB8CE3541BFE1301825364369134D40E5AD29B64 | |||
| 3488 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\{6224F66A-315D-4B99-B969-8634C09DCD7C} | binary | |
MD5:7B6F03FC123741DF091717D8F384CE08 | SHA256:88D25B359A5765E3D7A9D95EC0CBB9002D17E2CB1EB4A8E6A1C6FBDF4ACDCDFB | |||
| 3488 | WINWORD.EXE | C:\Users\admin\AppData\Local\Microsoft\Office\14.0\OfficeFileCache\FSD-CNRY.FSD | binary | |
MD5:DDBE018FFC68137EB4973289AF0930E0 | SHA256:0E4FA8EE6B11F00F238A1F2BBABA6F6ABCB014DFC2576CBC4D1AB7CE415673CF | |||
| 3488 | WINWORD.EXE | C:\Users\admin\AppData\Local\Microsoft\Office\14.0\OfficeFileCache\FSF-CTBL.FSF | binary | |
MD5:D471A0BB5F0B8A9AC834E0172491B7F9 | SHA256:418B6AE0A39787583DCD77DA0ED040F8C3DDA03410E71D04C235EE6E736F298F | |||
| 3488 | WINWORD.EXE | C:\Users\admin\AppData\Local\Microsoft\Office\14.0\OfficeFileCache\LocalCacheFileEditManager\FSD-CNRY.FSD | binary | |
MD5:7B6F03FC123741DF091717D8F384CE08 | SHA256:88D25B359A5765E3D7A9D95EC0CBB9002D17E2CB1EB4A8E6A1C6FBDF4ACDCDFB | |||
| 3488 | WINWORD.EXE | C:\Users\admin\AppData\Local\Microsoft\Office\14.0\OfficeFileCache\LocalCacheFileEditManager\FSF-{0E1EEE64-E8C6-4E2A-9759-63CF07FD8988}.FSF | binary | |
MD5:D471A0BB5F0B8A9AC834E0172491B7F9 | SHA256:418B6AE0A39787583DCD77DA0ED040F8C3DDA03410E71D04C235EE6E736F298F | |||
| 3488 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\~$mple.doc.docx | pgc | |
MD5:8F4A8CE51B2F5935D6C604251717DD30 | SHA256:E0756BF378F62DB26CE1A100086172D20C9ACBEAC51E9A5899052F5C08300951 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
4
TCP/UDP connections
15
DNS requests
21
Threats
4
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
3744 | CCUpdate.exe | GET | 200 | 2.19.126.82:80 | http://ccleaner.tools.avcdn.net/tools/ccleaner/update/patches.ini | DE | ini | 170 b | whitelisted |
3744 | CCUpdate.exe | HEAD | 200 | 2.19.126.76:80 | http://emupdate.avcdn.net/files/emupdate/pong.txt | DE | — | — | whitelisted |
3744 | CCUpdate.exe | GET | 200 | 2.19.126.82:80 | http://ccleaner.tools.avcdn.net/tools/ccleaner/update/ccupdate035.cab | DE | compressed | 414 Kb | whitelisted |
3744 | CCUpdate.exe | GET | 200 | 2.19.126.82:80 | http://ccleaner.tools.avcdn.net/tools/ccleaner/update/updates.xml | DE | xml | 1.58 Kb | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
3744 | CCUpdate.exe | 34.149.149.62:443 | ip-info.ff.avast.com | GOOGLE | US | suspicious |
3744 | CCUpdate.exe | 2.19.126.91:80 | ccleaner.tools.avcdn.net | Akamai International B.V. | DE | suspicious |
3744 | CCUpdate.exe | 2.19.126.82:80 | ccleaner.tools.avcdn.net | Akamai International B.V. | DE | suspicious |
1900 | CCleaner.exe | 34.117.223.223:443 | analytics.ff.avast.com | GOOGLE-CLOUD-PLATFORM | US | unknown |
3780 | CCleanerBugReport.exe | 34.78.50.65:443 | winqual.sb.avast.com | GOOGLE-CLOUD-PLATFORM | BE | unknown |
3744 | CCUpdate.exe | 2.19.126.76:80 | emupdate.avcdn.net | Akamai International B.V. | DE | suspicious |
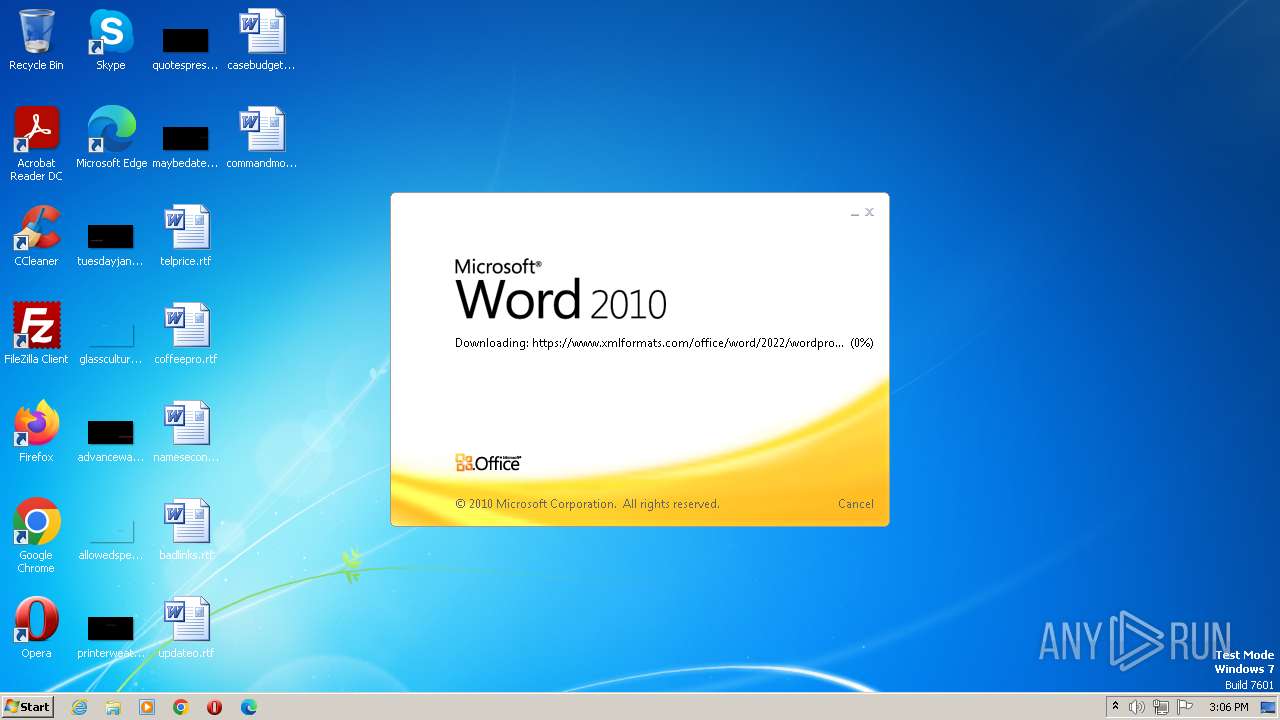
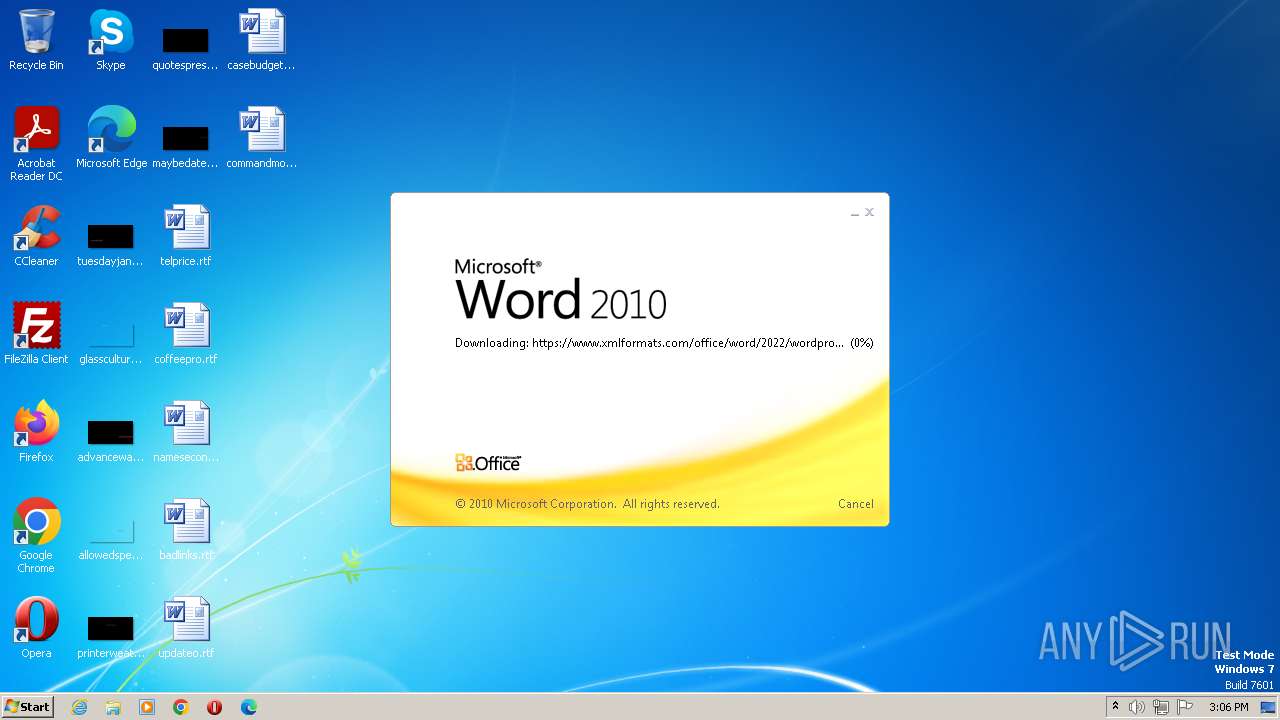
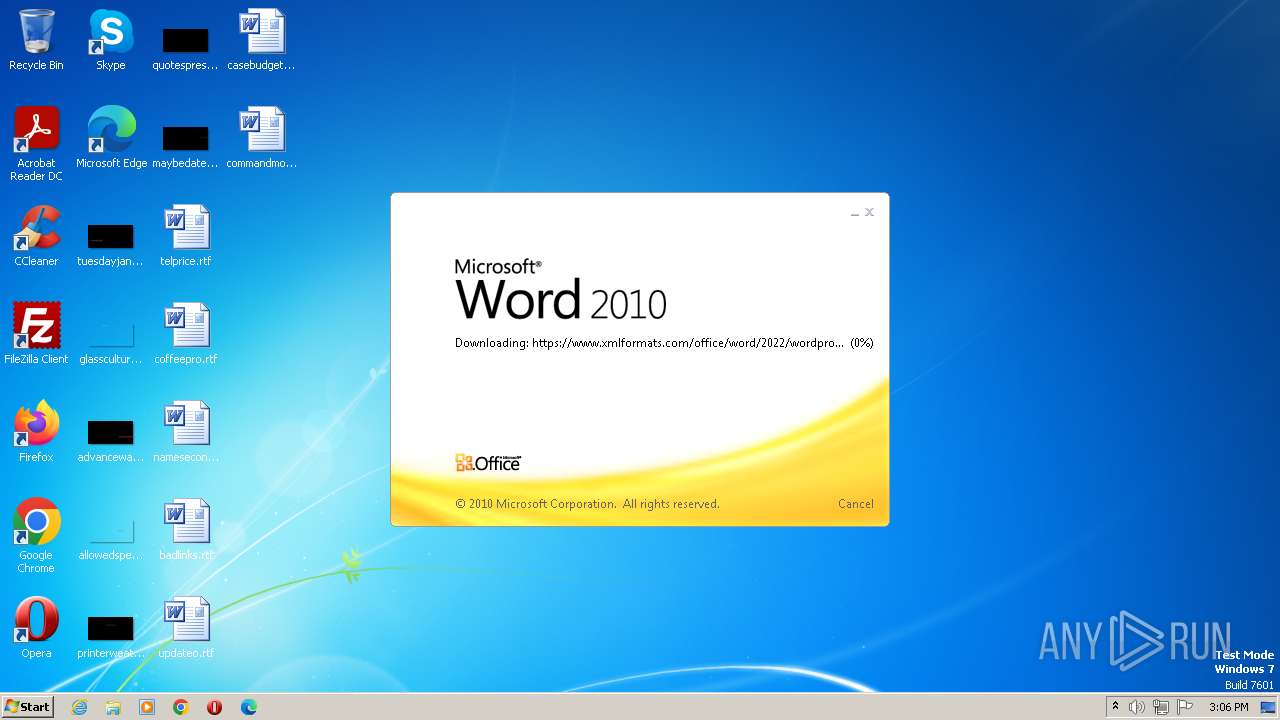
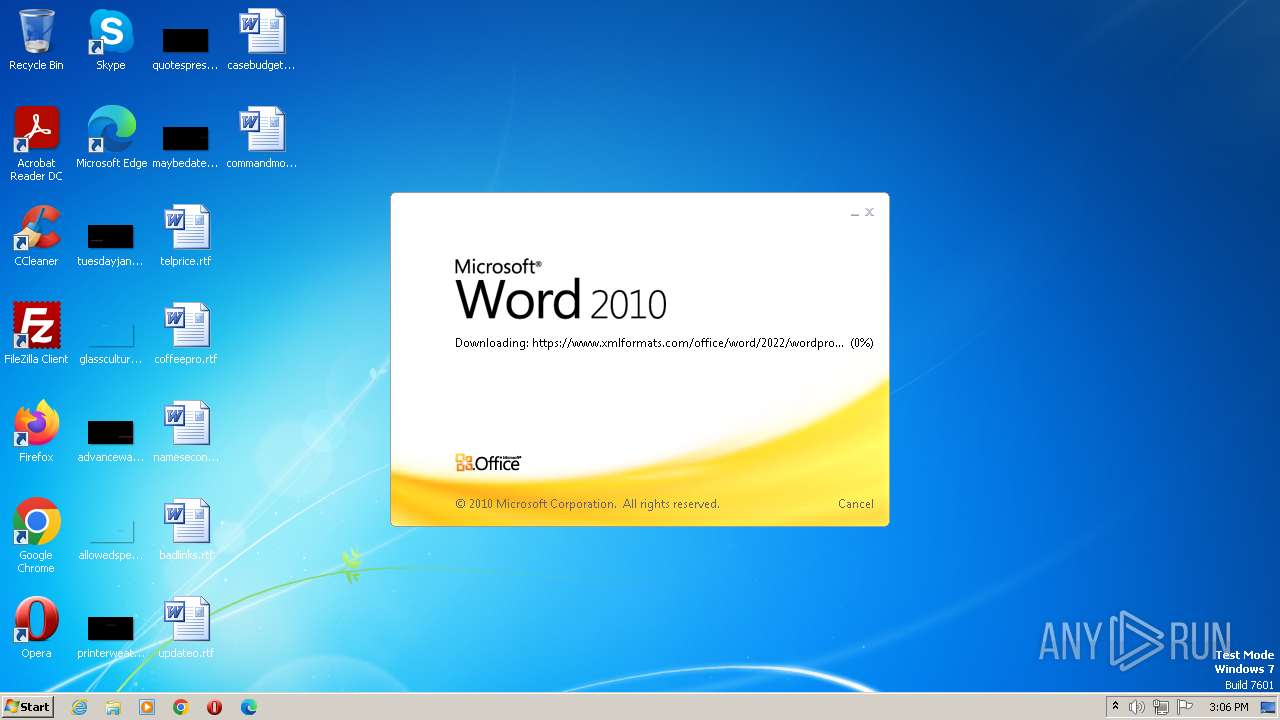
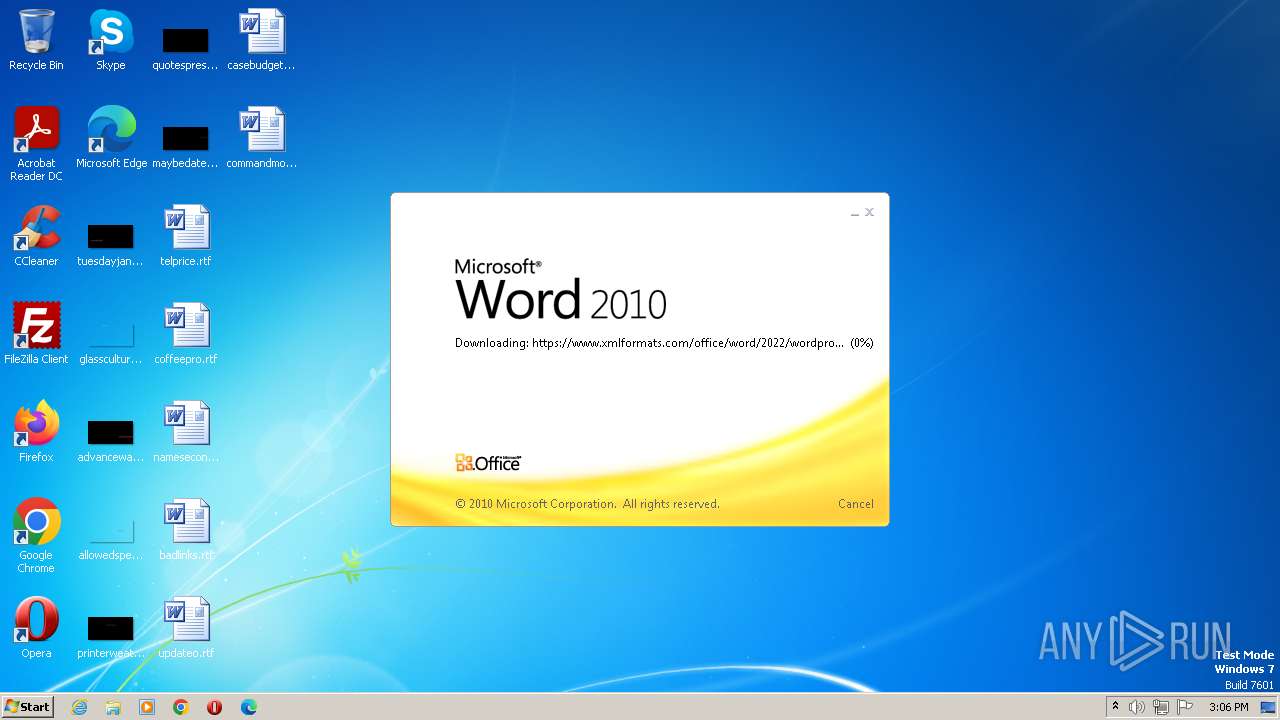
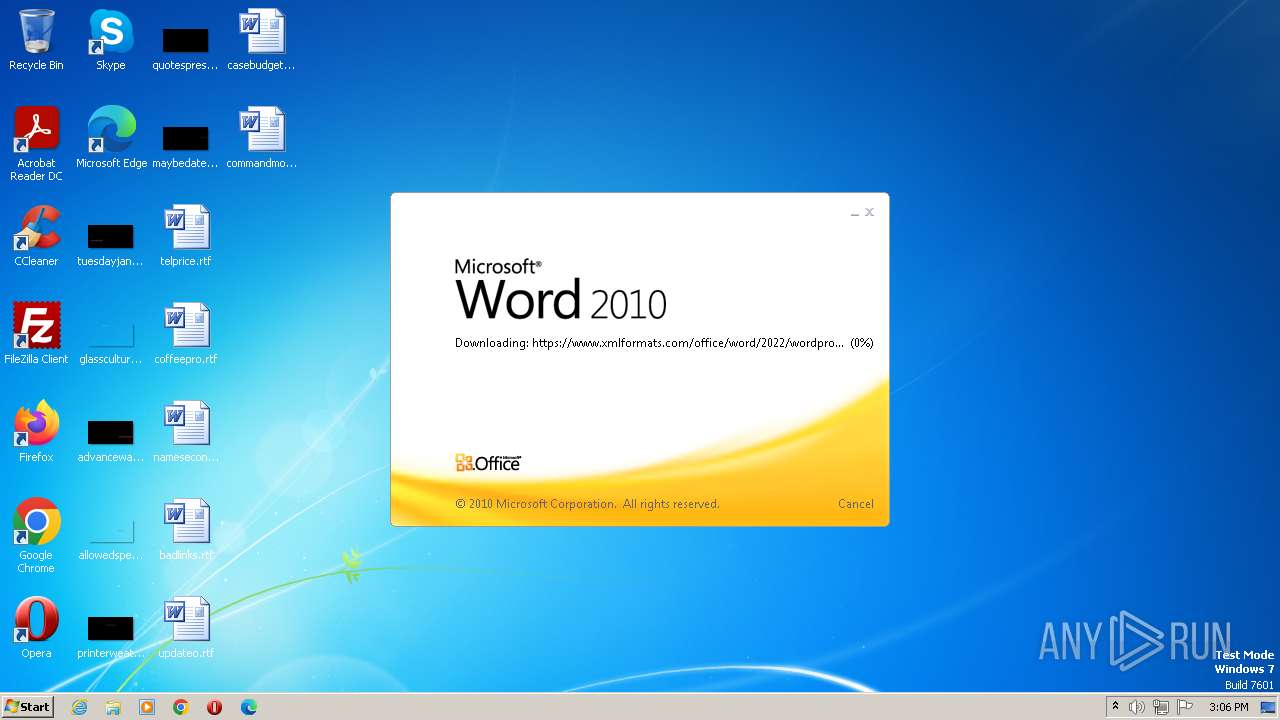
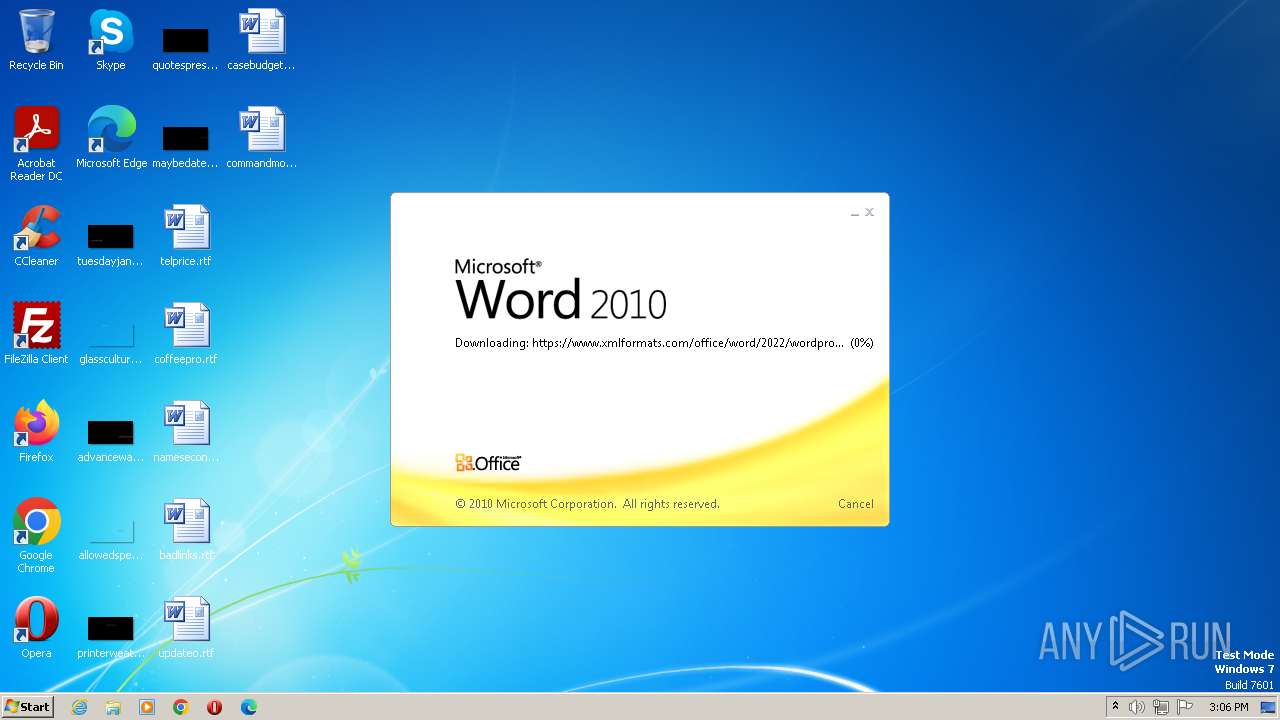
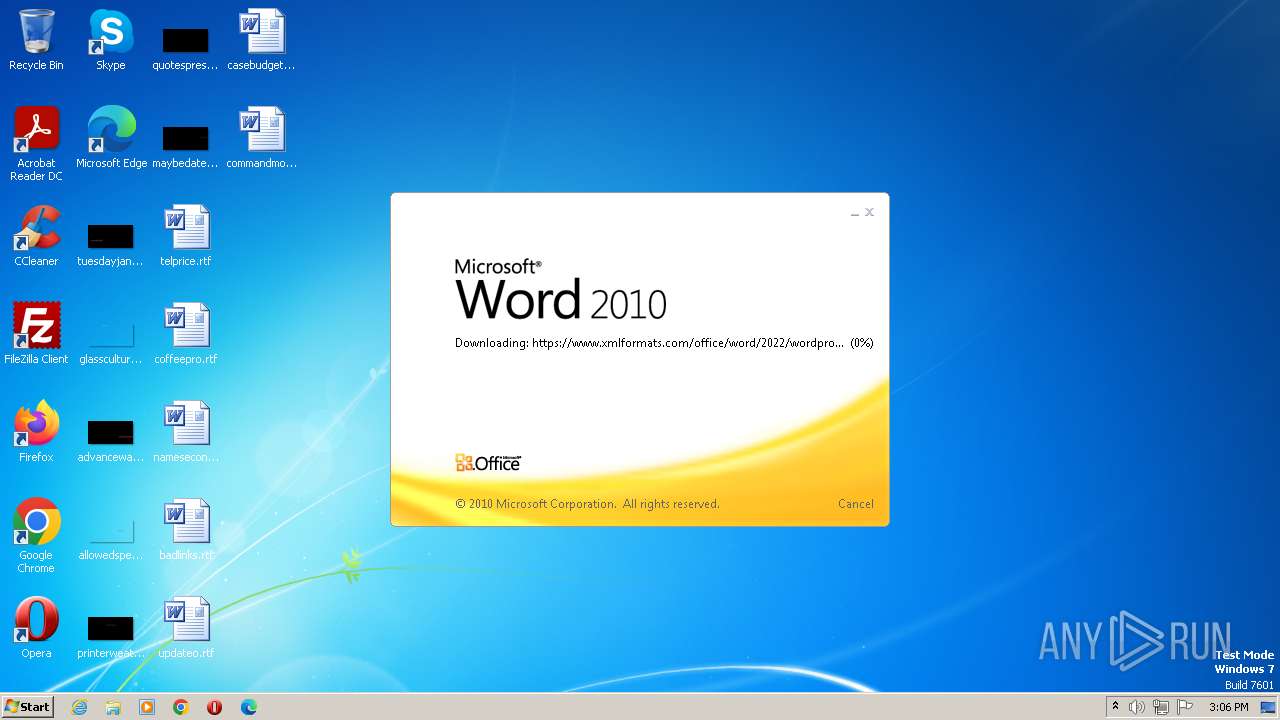
836 | svchost.exe | 185.107.56.58:443 | www.xmlformats.com | NForce Entertainment B.V. | NL | malicious |
3780 | CCleanerBugReport.exe | 34.107.19.138:443 | winqual.sb.avast.com | GOOGLE-CLOUD-PLATFORM | DE | unknown |
3488 | WINWORD.EXE | 185.107.56.58:443 | www.xmlformats.com | NForce Entertainment B.V. | NL | malicious |
DNS requests
Domain | IP | Reputation |
|---|---|---|
www.xmlformats.com |
| malicious |
dns.msftncsi.com |
| shared |
winqual.sb.avast.com |
| unknown |
ip-info.ff.avast.com |
| whitelisted |
emupdate.avcdn.net |
| whitelisted |
ccleaner.tools.avcdn.net |
| whitelisted |
analytics.ff.avast.com |
| whitelisted |
Threats
4 ETPRO signatures available at the full report
Process | Message |
|---|---|
CCleaner.exe | Failed to open log file 'C:\Program Files\CCleaner' |
CCleaner.exe | [2023-08-21 14:09:28.299] [error ] [settings ] [ 1900: 2320] [6000C4: 356] Failed to get program directory
Exception: Unable to determine program folder of product 'piriform-cc'!
Code: 0x000000c0 (192)
|
CCleaner.exe | [2023-08-21 14:09:28.315] [error ] [lil ] [ 1900: 2320] [81E517: 189] ~/ZIeepDOOIKB77M+twVIhbS6Fmc=
|
CCleaner.exe | [2023-08-21 14:09:28.315] [error ] [lif_utils ] [ 1900: 2320] [226DB9: 571] ~r6AMM4/ePpLRq6E5tw8PzK70EnKS3yuTzvm/bK4KXcSwsQt2jg==
|
CCleaner.exe | [2023-08-21 14:09:28.315] [error ] [lil ] [ 1900: 2320] [81E517: 189] ~vL5fVoTYL5fV4qki5EtcwKmhDzObziODgeK1bLMKQcG8oBBhhZs6htPqqymqDl2v/fRfM9ybaseBq+Zs/ksPhf30XzPcm2rHgavmbP5LD4X99F8z3Jtqx4Gr5mz+Sw+F/fRfM9ybaseBq+Zs/ksPhZ67G3bGm3qfkbv2fO5bGpL9/Eck1Q==
|