| File name: | sample.doc |
| Full analysis: | https://app.any.run/tasks/5865b9bc-2520-4feb-807a-ac02280bde4d |
| Verdict: | Malicious activity |
| Analysis date: | August 12, 2022, 14:36:41 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/octet-stream |
| File info: | Microsoft OOXML |
| MD5: | 52945AF1DEF85B171870B31FA4782E52 |
| SHA1: | 06727FFDA60359236A8029E0B3E8A0FD11C23313 |
| SHA256: | 4A24048F81AFBE9FB62E7A6A49ADBD1FAF41F266B5F9FEECDCEB567AEC096784 |
| SSDEEP: | 192:AEhM7fIUU09264wptGheab8h7Z/c+8poF1d3jvvtl59rGxjPQDasYBcG7h+:AqWfIz092hwLGAabkcfa7pr1lzyxjPQ9 |
MALICIOUS
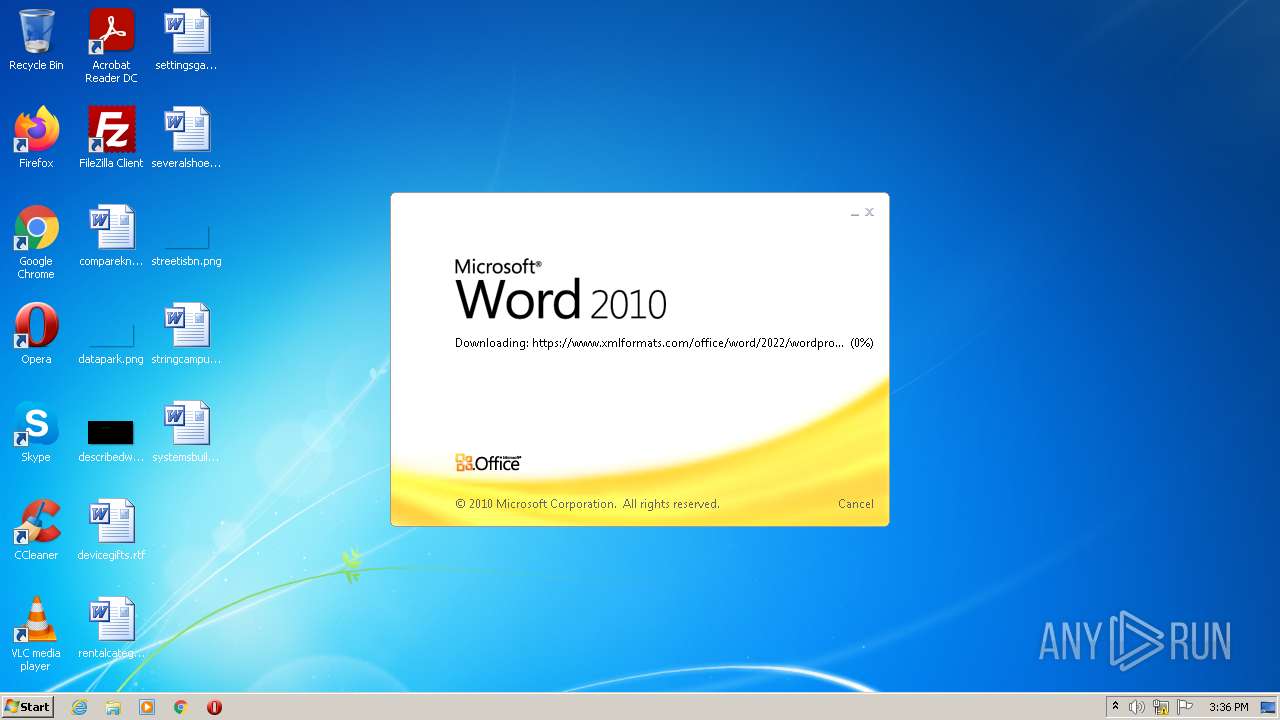
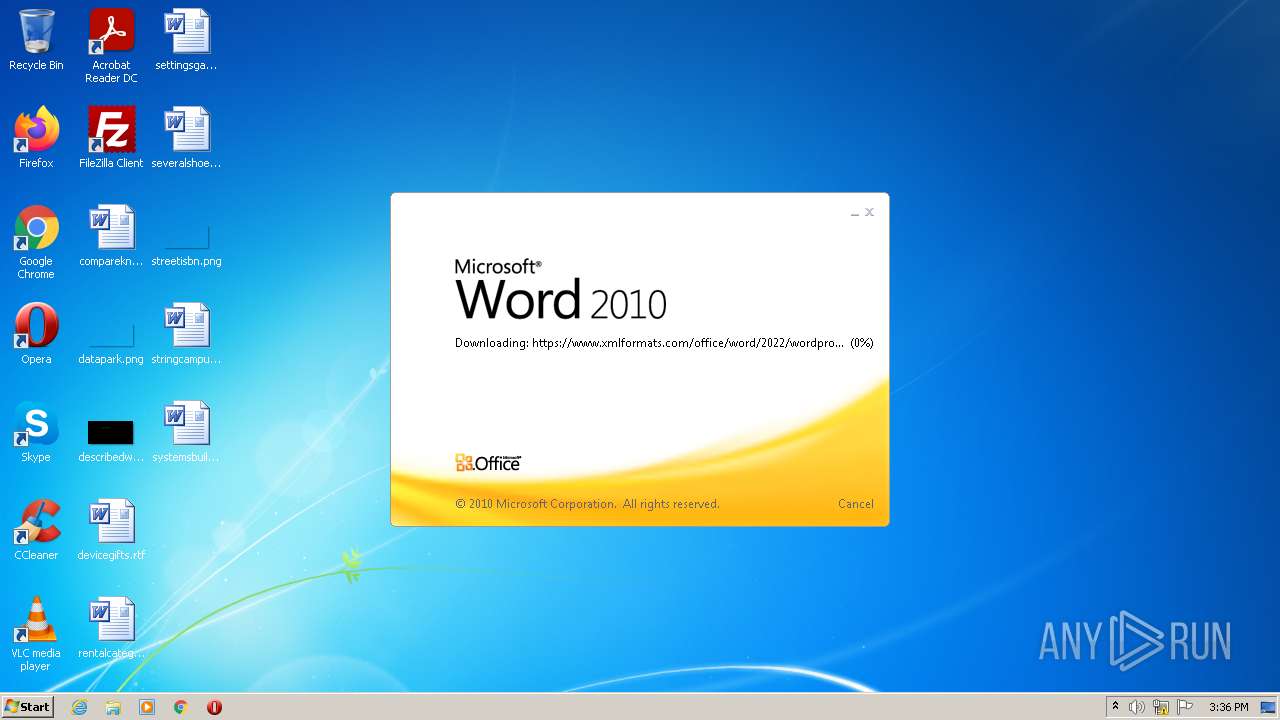
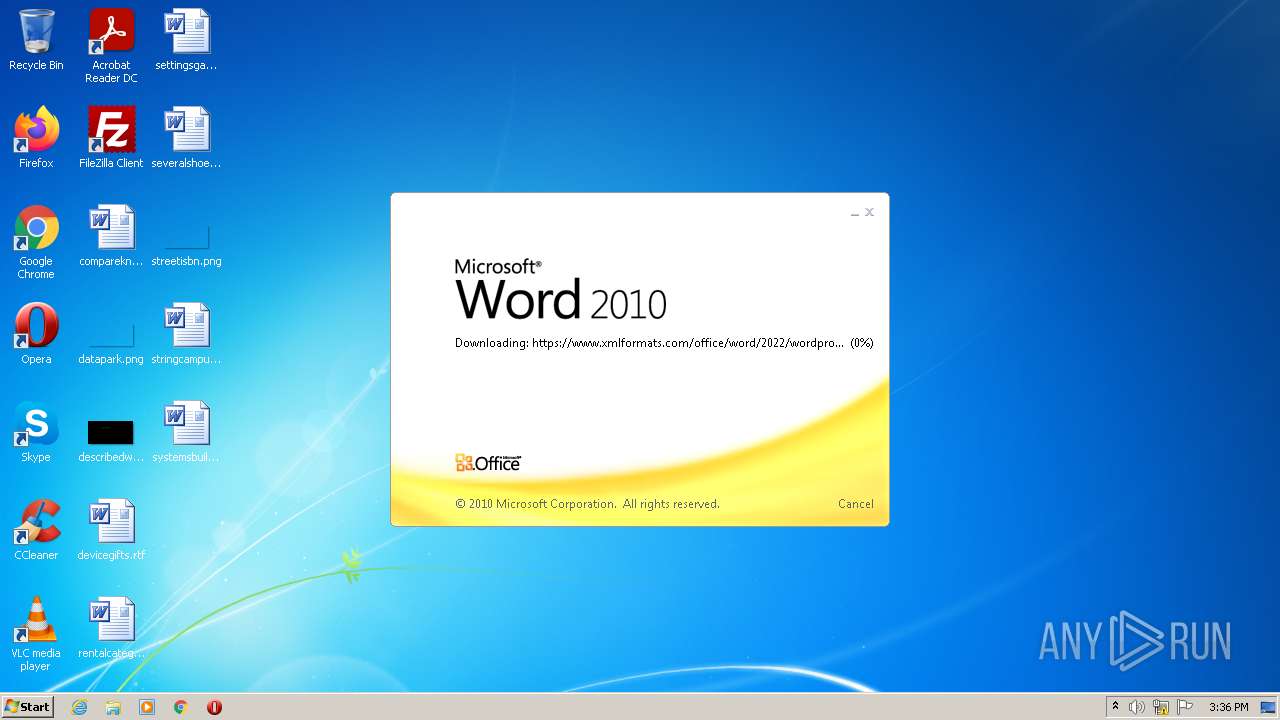
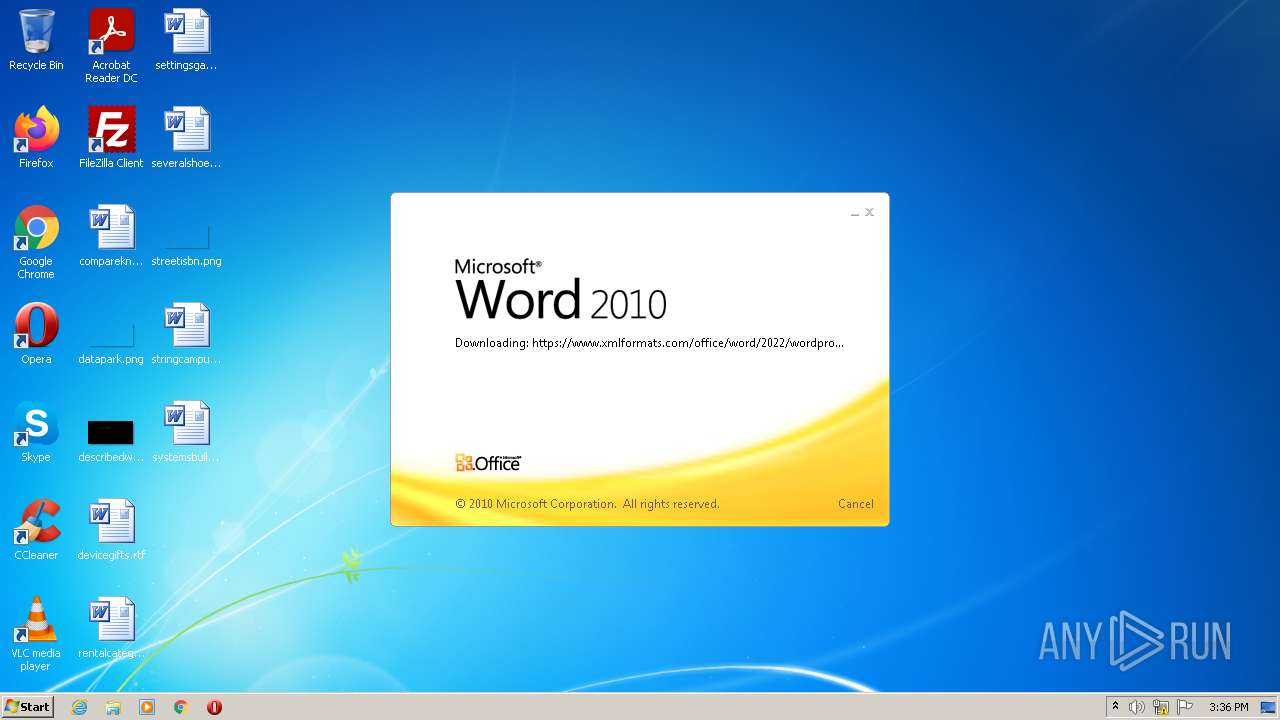
CVE-2022-30190 detected
- WINWORD.EXE (PID: 1388)
SUSPICIOUS
No suspicious indicators.INFO
Checks supported languages
- WINWORD.EXE (PID: 1388)
- chrome.exe (PID: 3216)
- chrome.exe (PID: 2108)
- chrome.exe (PID: 2448)
- chrome.exe (PID: 632)
- chrome.exe (PID: 2408)
- chrome.exe (PID: 2632)
- chrome.exe (PID: 3256)
- chrome.exe (PID: 2924)
- chrome.exe (PID: 3344)
- chrome.exe (PID: 904)
Reads the computer name
- WINWORD.EXE (PID: 1388)
- chrome.exe (PID: 3216)
- chrome.exe (PID: 632)
- chrome.exe (PID: 2448)
- chrome.exe (PID: 3344)
Manual execution by user
- chrome.exe (PID: 3216)
Application launched itself
- chrome.exe (PID: 3216)
Reads Microsoft Office registry keys
- WINWORD.EXE (PID: 1388)
Reads settings of System Certificates
- chrome.exe (PID: 632)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .docx | | | Word Microsoft Office Open XML Format document (52.2) |
|---|---|---|
| .zip | | | Open Packaging Conventions container (38.8) |
| .zip | | | ZIP compressed archive (8.8) |
EXIF
XMP
| Description: | - |
|---|---|
| Creator: | KIS2 |
| Subject: | - |
| Title: | - |
XML
| ModifyDate: | 2022:05:25 13:14:00Z |
|---|---|
| CreateDate: | 2022:05:25 13:14:00Z |
| RevisionNumber: | 3 |
| LastModifiedBy: | KIS2 |
| Keywords: | - |
| AppVersion: | 16 |
| HyperlinksChanged: | No |
| SharedDoc: | No |
| CharactersWithSpaces: | - |
| LinksUpToDate: | No |
| Company: | - |
| ScaleCrop: | No |
| Paragraphs: | - |
| Lines: | - |
| DocSecurity: | None |
| Application: | Microsoft Office Word |
| Characters: | - |
| Words: | - |
| Pages: | 1 |
| TotalEditTime: | - |
| Template: | Normal |
ZIP
| ZipFileName: | [Content_Types].xml |
|---|---|
| ZipUncompressedSize: | 1312 |
| ZipCompressedSize: | 340 |
| ZipCRC: | 0x6cd2a4df |
| ZipModifyDate: | 2022:05:26 23:08:07 |
| ZipCompression: | Deflated |
| ZipBitFlag: | - |
| ZipRequiredVersion: | 20 |
Total processes
49
Monitored processes
11
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 632 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=network.mojom.NetworkService --field-trial-handle=1040,6712105327734025716,12558157188902849727,131072 --enable-features=PasswordImport --lang=en-US --service-sandbox-type=network --mojo-platform-channel-handle=1328 /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | chrome.exe | ||||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 86.0.4240.198 Modules
| |||||||||||||||
| 904 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=data_decoder.mojom.DataDecoderService --field-trial-handle=1040,6712105327734025716,12558157188902849727,131072 --enable-features=PasswordImport --lang=en-US --service-sandbox-type=utility --mojo-platform-channel-handle=2944 /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 86.0.4240.198 Modules
| |||||||||||||||
| 1388 | "C:\Program Files\Microsoft Office\Office14\WINWORD.EXE" /n "C:\Users\admin\AppData\Local\Temp\sample.doc.docx" | C:\Program Files\Microsoft Office\Office14\WINWORD.EXE | — | Explorer.EXE | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Word Exit code: 0 Version: 14.0.6024.1000 Modules
| |||||||||||||||
| 2108 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=crashpad-handler "--user-data-dir=C:\Users\admin\AppData\Local\Google\Chrome\User Data" /prefetch:7 --monitor-self-annotation=ptype=crashpad-handler "--database=C:\Users\admin\AppData\Local\Google\Chrome\User Data\Crashpad" "--metrics-dir=C:\Users\admin\AppData\Local\Google\Chrome\User Data" --url=https://clients2.google.com/cr/report --annotation=channel= --annotation=plat=Win32 --annotation=prod=Chrome --annotation=ver=86.0.4240.198 --initial-client-data=0xc8,0xcc,0xd0,0x9c,0xd4,0x6932d988,0x6932d998,0x6932d9a4 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 86.0.4240.198 Modules
| |||||||||||||||
| 2408 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=1040,6712105327734025716,12558157188902849727,131072 --enable-features=PasswordImport --lang=en-US --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=6 --no-v8-untrusted-code-mitigations --mojo-platform-channel-handle=1908 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 86.0.4240.198 Modules
| |||||||||||||||
| 2448 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=gpu-process --field-trial-handle=1040,6712105327734025716,12558157188902849727,131072 --enable-features=PasswordImport --gpu-preferences=MAAAAAAAAADgAAAwAAAAAAAAAAAAAAAAAABgAAAAAAAQAAAAAAAAAAAAAAAAAAAAKAAAAAQAAAAgAAAAAAAAACgAAAAAAAAAMAAAAAAAAAA4AAAAAAAAABAAAAAAAAAAAAAAAAUAAAAQAAAAAAAAAAAAAAAGAAAAEAAAAAAAAAABAAAABQAAABAAAAAAAAAAAQAAAAYAAAA= --mojo-platform-channel-handle=1016 /prefetch:2 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 86.0.4240.198 Modules
| |||||||||||||||
| 2632 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=1040,6712105327734025716,12558157188902849727,131072 --enable-features=PasswordImport --lang=en-US --instant-process --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=5 --no-v8-untrusted-code-mitigations --mojo-platform-channel-handle=1912 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 86.0.4240.198 Modules
| |||||||||||||||
| 2924 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=data_decoder.mojom.DataDecoderService --field-trial-handle=1040,6712105327734025716,12558157188902849727,131072 --enable-features=PasswordImport --lang=en-US --service-sandbox-type=utility --mojo-platform-channel-handle=2840 /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 86.0.4240.198 Modules
| |||||||||||||||
| 3216 | "C:\Program Files\Google\Chrome\Application\chrome.exe" | C:\Program Files\Google\Chrome\Application\chrome.exe | — | Explorer.EXE | |||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 86.0.4240.198 Modules
| |||||||||||||||
| 3256 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=1040,6712105327734025716,12558157188902849727,131072 --enable-features=PasswordImport --lang=en-US --extension-process --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=4 --no-v8-untrusted-code-mitigations --mojo-platform-channel-handle=2240 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 86.0.4240.198 Modules
| |||||||||||||||
Total events
11 013
Read events
10 274
Write events
608
Delete events
131
Modification events
| (PID) Process: | (1388) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Word\Resiliency\StartupItems |
| Operation: | write | Name: | cu7 |
Value: 637537006C050000010000000000000000000000 | |||
| (PID) Process: | (1388) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1033 |
Value: Off | |||
| (PID) Process: | (1388) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1041 |
Value: Off | |||
| (PID) Process: | (1388) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1046 |
Value: Off | |||
| (PID) Process: | (1388) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1036 |
Value: Off | |||
| (PID) Process: | (1388) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1031 |
Value: Off | |||
| (PID) Process: | (1388) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1040 |
Value: Off | |||
| (PID) Process: | (1388) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1049 |
Value: Off | |||
| (PID) Process: | (1388) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 3082 |
Value: Off | |||
| (PID) Process: | (1388) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1042 |
Value: Off | |||
Executable files
0
Suspicious files
14
Text files
21
Unknown types
6
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 1388 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\CVR9943.tmp.cvr | — | |
MD5:— | SHA256:— | |||
| 3216 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\BrowserMetrics\BrowserMetrics-62F665AD-C90.pma | — | |
MD5:— | SHA256:— | |||
| 1388 | WINWORD.EXE | C:\Users\admin\AppData\Roaming\Microsoft\Templates\~$Normal.dotm | pgc | |
MD5:— | SHA256:— | |||
| 1388 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\~$mple.doc.docx | pgc | |
MD5:— | SHA256:— | |||
| 1388 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\{3B690B64-10E6-40A4-94C0-A02F79DC9883} | binary | |
MD5:— | SHA256:— | |||
| 1388 | WINWORD.EXE | C:\Users\admin\AppData\Local\Microsoft\Office\14.0\OfficeFileCache\LocalCacheFileEditManager\FSD-CNRY.FSD | binary | |
MD5:— | SHA256:— | |||
| 1388 | WINWORD.EXE | C:\Users\admin\AppData\Local\Microsoft\Office\14.0\OfficeFileCache\LocalCacheFileEditManager\FSD-{E10C60CE-F0EC-49E8-BA6A-E532755745B7}.FSD | binary | |
MD5:— | SHA256:— | |||
| 1388 | WINWORD.EXE | C:\Users\admin\AppData\Local\Microsoft\Office\14.0\OfficeFileCache\FSD-CNRY.FSD | binary | |
MD5:— | SHA256:— | |||
| 1388 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\{62F4B119-88DA-4478-82A1-C5B58194A8AC} | binary | |
MD5:— | SHA256:— | |||
| 1388 | WINWORD.EXE | C:\Users\admin\AppData\Local\Microsoft\Office\14.0\OfficeFileCache\FSD-{C1CEFA32-CB22-471D-A00A-2DF76DB7D83B}.FSD | binary | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
16
DNS requests
11
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
632 | chrome.exe | 142.250.186.163:443 | clientservices.googleapis.com | Google Inc. | US | whitelisted |
632 | chrome.exe | 142.250.184.206:443 | clients2.google.com | Google Inc. | US | whitelisted |
632 | chrome.exe | 216.58.212.173:443 | accounts.google.com | Google Inc. | US | whitelisted |
632 | chrome.exe | 142.250.185.100:443 | www.google.com | Google Inc. | US | whitelisted |
632 | chrome.exe | 142.250.185.202:443 | fonts.googleapis.com | Google Inc. | US | whitelisted |
632 | chrome.exe | 142.250.185.129:443 | clients2.googleusercontent.com | Google Inc. | US | whitelisted |
632 | chrome.exe | 142.250.186.67:443 | fonts.gstatic.com | Google Inc. | US | whitelisted |
632 | chrome.exe | 142.250.185.227:443 | www.gstatic.com | Google Inc. | US | whitelisted |
632 | chrome.exe | 172.217.16.131:443 | ssl.gstatic.com | Google Inc. | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
www.xmlformats.com |
| malicious |
accounts.google.com |
| shared |
clientservices.googleapis.com |
| whitelisted |
clients2.google.com |
| whitelisted |
www.google.com |
| malicious |
fonts.googleapis.com |
| whitelisted |
clients2.googleusercontent.com |
| whitelisted |
www.gstatic.com |
| whitelisted |
fonts.gstatic.com |
| whitelisted |
ssl.gstatic.com |
| whitelisted |