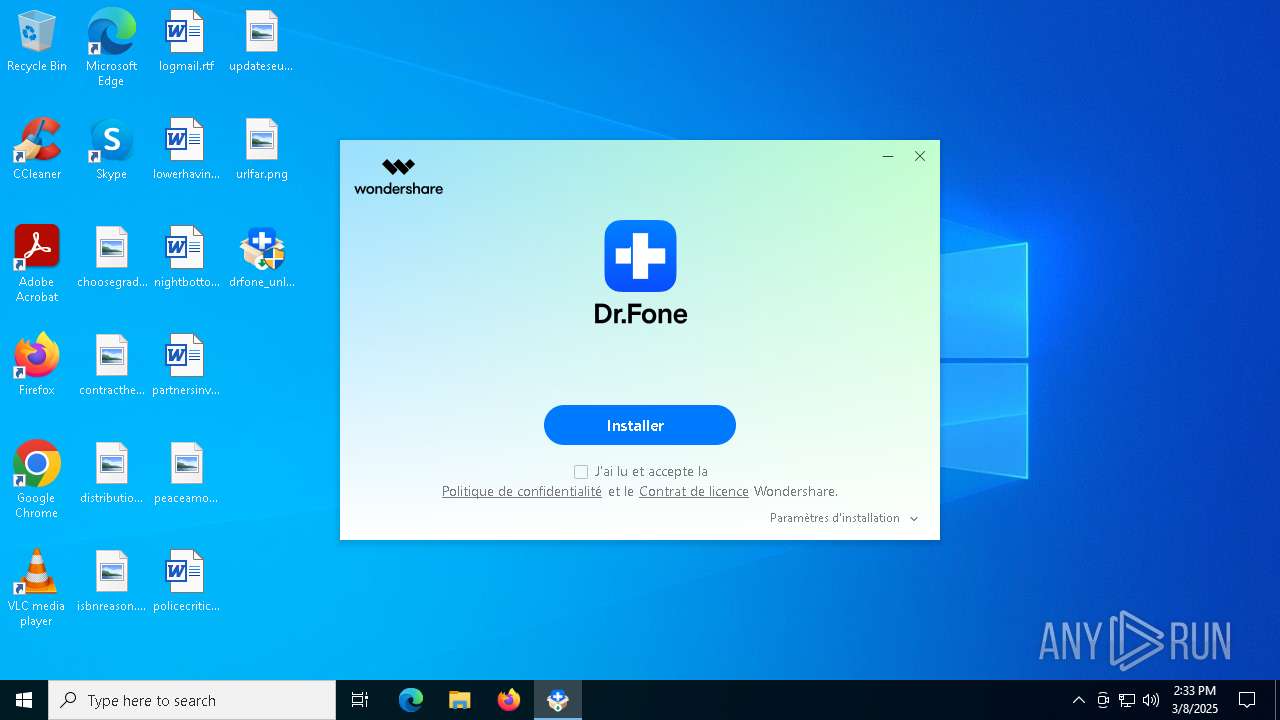
| File name: | drfone_unlock_setup_full4004.exe |
| Full analysis: | https://app.any.run/tasks/366a8273-4374-42f1-b96d-8d51e2a3f4a9 |
| Verdict: | Malicious activity |
| Analysis date: | March 08, 2025, 14:33:14 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Indicators: | |
| MIME: | application/vnd.microsoft.portable-executable |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows, 6 sections |
| MD5: | 2BD15055CE7FAE90E39B55221B7AA074 |
| SHA1: | 91D05D3A1DE9CBB97549FA5D8CC1225D38C223BB |
| SHA256: | 4A1D9E148DE2F04D3C88440673B24480788C9408D34EA93E9CC4CAADDEBD605C |
| SSDEEP: | 98304:Y1fgF4qf0vwxYa1s0ZNy1UMmetMj6gbNo7SCDP6Ple73U6D6VGUEGmutvDFM:RM |
MALICIOUS
No malicious indicators.SUSPICIOUS
Reads Microsoft Outlook installation path
- drfone_unlock_setup_full4004.exe (PID: 3100)
Executable content was dropped or overwritten
- drfone_unlock_setup_full4004.exe (PID: 3100)
Likely accesses (executes) a file from the Public directory
- NFWCHK.exe (PID: 5024)
Reads security settings of Internet Explorer
- drfone_unlock_setup_full4004.exe (PID: 3100)
Reads Internet Explorer settings
- drfone_unlock_setup_full4004.exe (PID: 3100)
Connects to unusual port
- drfone_unlock_setup_full4004.exe (PID: 3100)
INFO
The sample compiled with english language support
- drfone_unlock_setup_full4004.exe (PID: 3100)
Reads the computer name
- drfone_unlock_setup_full4004.exe (PID: 3100)
- NFWCHK.exe (PID: 5024)
Reads the machine GUID from the registry
- drfone_unlock_setup_full4004.exe (PID: 3100)
- NFWCHK.exe (PID: 5024)
Checks supported languages
- drfone_unlock_setup_full4004.exe (PID: 3100)
- NFWCHK.exe (PID: 5024)
Create files in a temporary directory
- drfone_unlock_setup_full4004.exe (PID: 3100)
Checks proxy server information
- drfone_unlock_setup_full4004.exe (PID: 3100)
- slui.exe (PID: 6268)
Reads the software policy settings
- slui.exe (PID: 6268)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win32 Executable (generic) (3.6) |
|---|---|---|
| .exe | | | Generic Win/DOS Executable (1.6) |
| .exe | | | DOS Executable Generic (1.5) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2024:05:30 06:40:05+00:00 |
| ImageFileCharacteristics: | Executable, 32-bit |
| PEType: | PE32 |
| LinkerVersion: | 12 |
| CodeSize: | 1285120 |
| InitializedDataSize: | 1250304 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x107e70 |
| OSVersion: | 6 |
| ImageVersion: | - |
| SubsystemVersion: | 6 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 4.0.4.22 |
| ProductVersionNumber: | 4.0.4.22 |
| FileFlagsMask: | 0x0017 |
| FileFlags: | (none) |
| FileOS: | Win32 |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | English (U.S.) |
| CharacterSet: | Unicode |
| FileDescription: | dr.fone_setup_full4004.exe |
| FileVersion: | 4.0.4.22 |
| LegalCopyright: | Copyright©2024 Wondershare. All rights reserved. |
| ProductName: | Dr.Fone |
| ProductVersion: | 12.5.7 |
Total processes
125
Monitored processes
6
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1072 | "C:\Users\admin\Desktop\drfone_unlock_setup_full4004.exe" | C:\Users\admin\Desktop\drfone_unlock_setup_full4004.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Description: dr.fone_setup_full4004.exe Exit code: 3221226540 Version: 4.0.4.22 Modules
| |||||||||||||||
| 1452 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | NFWCHK.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2196 | C:\WINDOWS\system32\svchost.exe -k NetworkService -p -s Dnscache | C:\Windows\System32\svchost.exe | services.exe | ||||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Host Process for Windows Services Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3100 | "C:\Users\admin\Desktop\drfone_unlock_setup_full4004.exe" | C:\Users\admin\Desktop\drfone_unlock_setup_full4004.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: HIGH Description: dr.fone_setup_full4004.exe Version: 4.0.4.22 Modules
| |||||||||||||||
| 5024 | C:\Users\Public\Documents\Wondershare\NFWCHK.exe | C:\Users\Public\Documents\Wondershare\NFWCHK.exe | — | drfone_unlock_setup_full4004.exe | |||||||||||
User: admin Company: Wondershare Integrity Level: HIGH Description: .NET Framework Checker Exit code: 0 Version: 1.0.0.0 Modules
| |||||||||||||||
| 6268 | C:\WINDOWS\System32\slui.exe -Embedding | C:\Windows\System32\slui.exe | svchost.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Activation Client Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
4 224
Read events
4 218
Write events
6
Delete events
0
Modification events
| (PID) Process: | (3100) drfone_unlock_setup_full4004.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\WafCX |
| Operation: | write | Name: | 4004 |
Value: sku-ppcfr | |||
| (PID) Process: | (3100) drfone_unlock_setup_full4004.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Wondershare\Wondershare Helper Compact |
| Operation: | write | Name: | ClientSign |
Value: {23988fdc-c28b-4d64-9dac-b34d6671aee1G} | |||
| (PID) Process: | (3100) drfone_unlock_setup_full4004.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Wondershare\WAF |
| Operation: | write | Name: | ClientSign |
Value: {23988fdc-c28b-4d64-9dac-b34d6671aee1G} | |||
| (PID) Process: | (3100) drfone_unlock_setup_full4004.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Content |
| Operation: | write | Name: | CachePrefix |
Value: | |||
| (PID) Process: | (3100) drfone_unlock_setup_full4004.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (3100) drfone_unlock_setup_full4004.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
Executable files
1
Suspicious files
0
Text files
3
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3100 | drfone_unlock_setup_full4004.exe | C:\Users\admin\AppData\Local\Temp\wsduilib.log | text | |
MD5:3AD1075C9FCF150F1795831BF68B54B7 | SHA256:3CEEC738CE3837A60E830382B7279EEBBE9F864A8A0DE5A072BCA8A588F3CEBF | |||
| 3100 | drfone_unlock_setup_full4004.exe | C:\Users\Public\Documents\Wondershare\NFWCHK.exe.config | xml | |
MD5:5BABF2A106C883A8E216F768DB99AD51 | SHA256:9E676A617EB0D0535AC05A67C0AE0C0E12D4E998AB55AC786A031BFC25E28300 | |||
| 3100 | drfone_unlock_setup_full4004.exe | C:\Users\admin\AppData\Local\Temp\Wondershare\WAE\wsWAE.log | text | |
MD5:9EA7FAB6DF16DA52655D8502C6335630 | SHA256:86979453EBB7EDCDFCABB6A9CFE65ECB96972E2BFFF09DFA854DF3B81EDBAC43 | |||
| 3100 | drfone_unlock_setup_full4004.exe | C:\Users\Public\Documents\Wondershare\NFWCHK.exe | executable | |
MD5:27CFB3990872CAA5930FA69D57AEFE7B | SHA256:43881549228975C7506B050BCE4D9B671412D3CDC08C7516C9DBBB7F50C25146 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
7
TCP/UDP connections
26
DNS requests
8
Threats
4
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
3100 | drfone_unlock_setup_full4004.exe | GET | — | 8.209.73.211:80 | http://platform.wondershare.cc/rest/v2/downloader/runtime/?client_sign={23988fdc-c28b-4d64-9dac-b34d6671aee1G}&product_id=4004&wae=4.0.4&platform=win_x64 | unknown | — | — | malicious |
3100 | drfone_unlock_setup_full4004.exe | HEAD | 200 | 23.48.23.41:80 | http://download.wondershare.net/cbs_down/drfone_full4007.exe | unknown | — | — | whitelisted |
— | — | POST | 200 | 8.209.72.213:443 | https://pc-api.wondershare.cc/v3/user/client/token | unknown | binary | 132 b | malicious |
— | — | GET | 200 | 47.91.89.51:443 | https://prod-web.wondershare.cc/api/v1/prodweb/trk?pid=4004&os=Windows | unknown | binary | 107 b | malicious |
— | — | POST | 500 | 40.91.76.224:443 | https://activation-v2.sls.microsoft.com/SLActivateProduct/SLActivateProduct.asmx?configextension=Retail | unknown | xml | 512 b | whitelisted |
— | — | POST | 200 | 8.209.72.213:443 | https://pc-api.wondershare.cc/v1/product/series | unknown | binary | 31 b | malicious |
— | — | POST | 500 | 40.91.76.224:443 | https://activation-v2.sls.microsoft.com/SLActivateProduct/SLActivateProduct.asmx?configextension=Retail | unknown | xml | 512 b | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
— | — | 192.168.100.255:138 | — | — | — | whitelisted |
— | — | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
3100 | drfone_unlock_setup_full4004.exe | 8.209.72.213:443 | pc-api.wondershare.cc | Alibaba US Technology Co., Ltd. | DE | malicious |
3100 | drfone_unlock_setup_full4004.exe | 8.209.73.211:80 | platform.wondershare.cc | Alibaba US Technology Co., Ltd. | DE | malicious |
3100 | drfone_unlock_setup_full4004.exe | 47.91.89.51:443 | prod-web.wondershare.cc | Alibaba US Technology Co., Ltd. | DE | malicious |
3100 | drfone_unlock_setup_full4004.exe | 23.48.23.41:80 | download.wondershare.net | Akamai International B.V. | DE | whitelisted |
3100 | drfone_unlock_setup_full4004.exe | 47.254.169.108:8106 | analytics.wondershare.cc | Alibaba US Technology Co., Ltd. | DE | malicious |
2908 | slui.exe | 40.91.76.224:443 | activation-v2.sls.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
6268 | slui.exe | 40.91.76.224:443 | activation-v2.sls.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
pc-api.wondershare.cc |
| malicious |
platform.wondershare.cc |
| malicious |
prod-web.wondershare.cc |
| malicious |
download.wondershare.net |
| whitelisted |
analytics.wondershare.cc |
| malicious |
activation-v2.sls.microsoft.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2196 | svchost.exe | Potentially Bad Traffic | ET DNS Query for .cc TLD |
2196 | svchost.exe | Potentially Bad Traffic | ET DNS Query for .cc TLD |
2196 | svchost.exe | Potentially Bad Traffic | ET DNS Query for .cc TLD |
2196 | svchost.exe | Potentially Bad Traffic | ET DNS Query for .cc TLD |