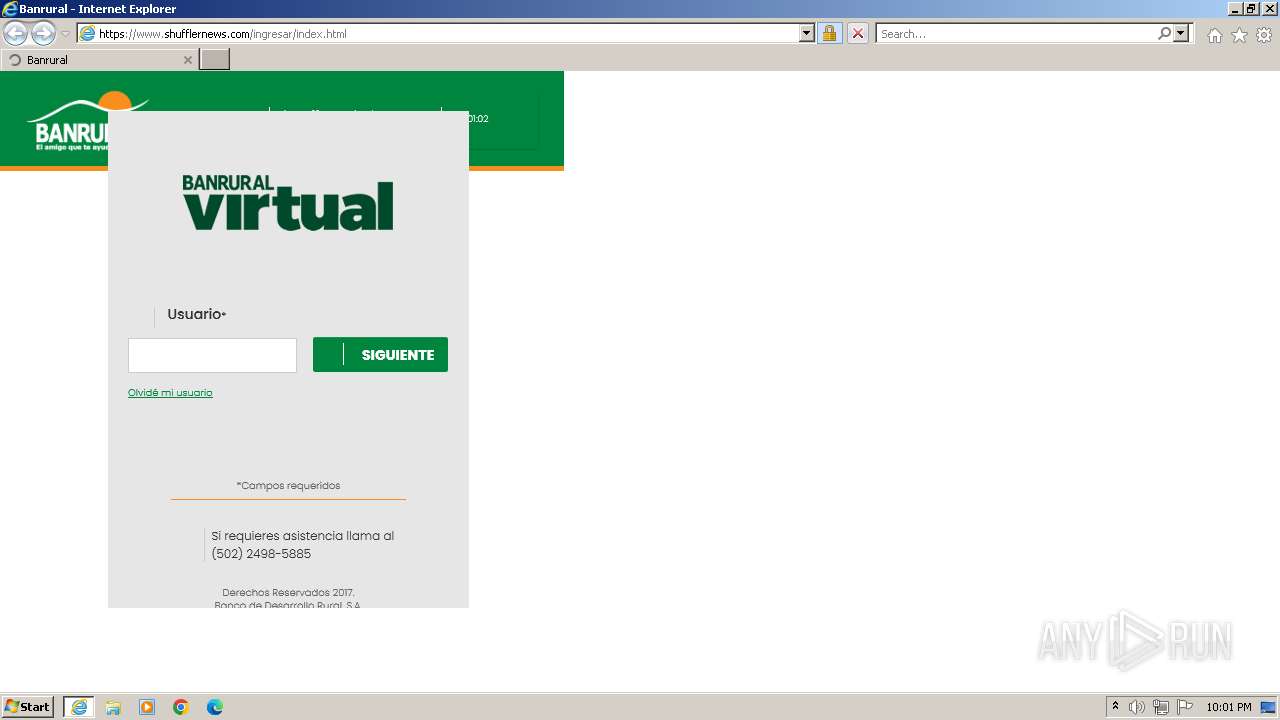
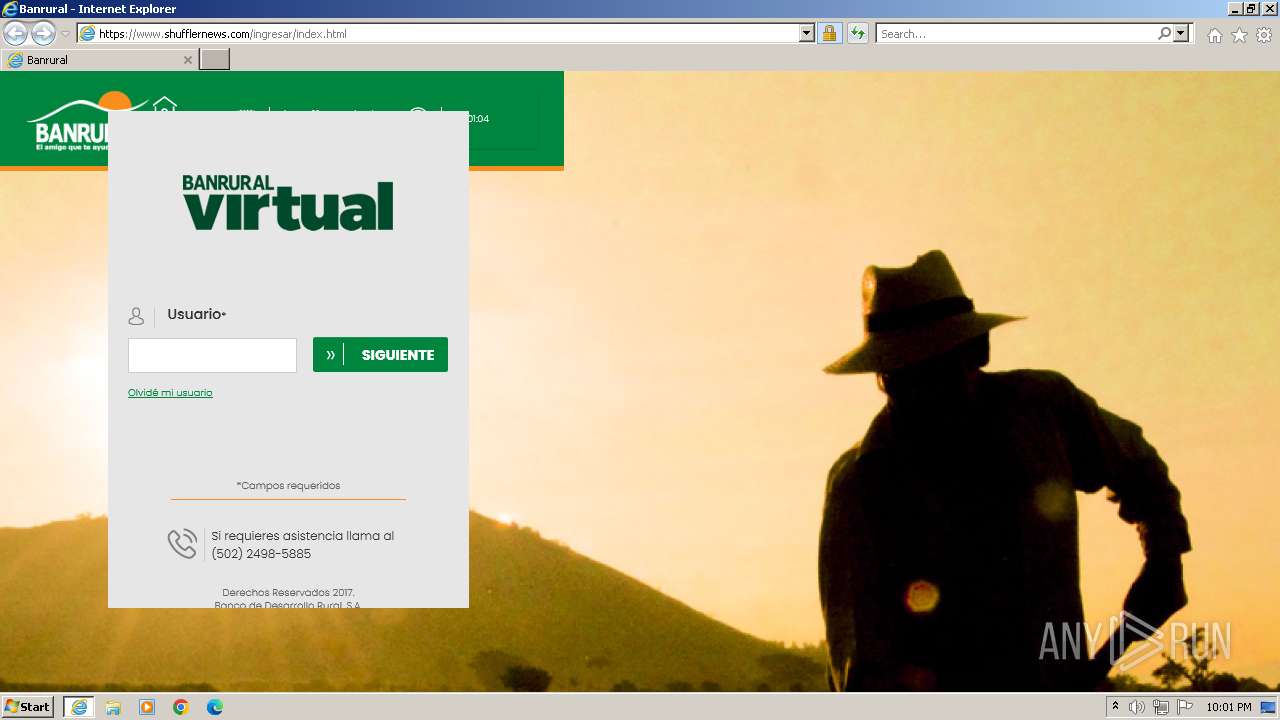
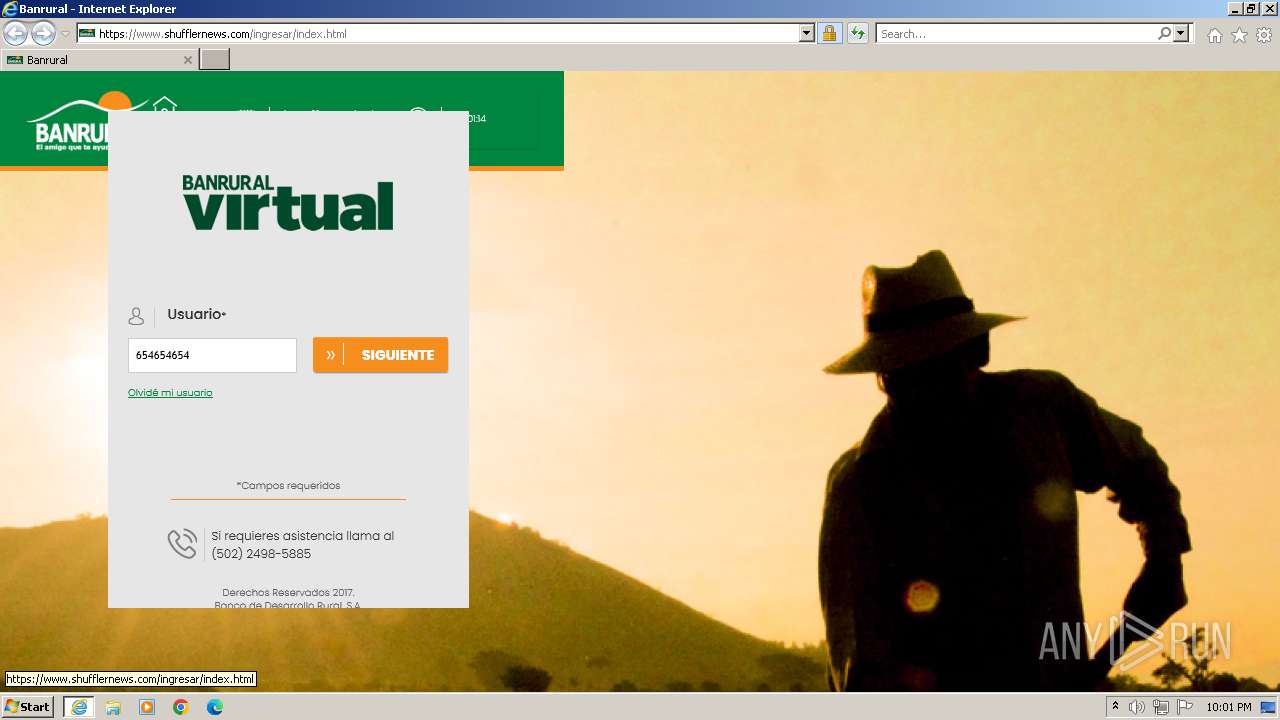
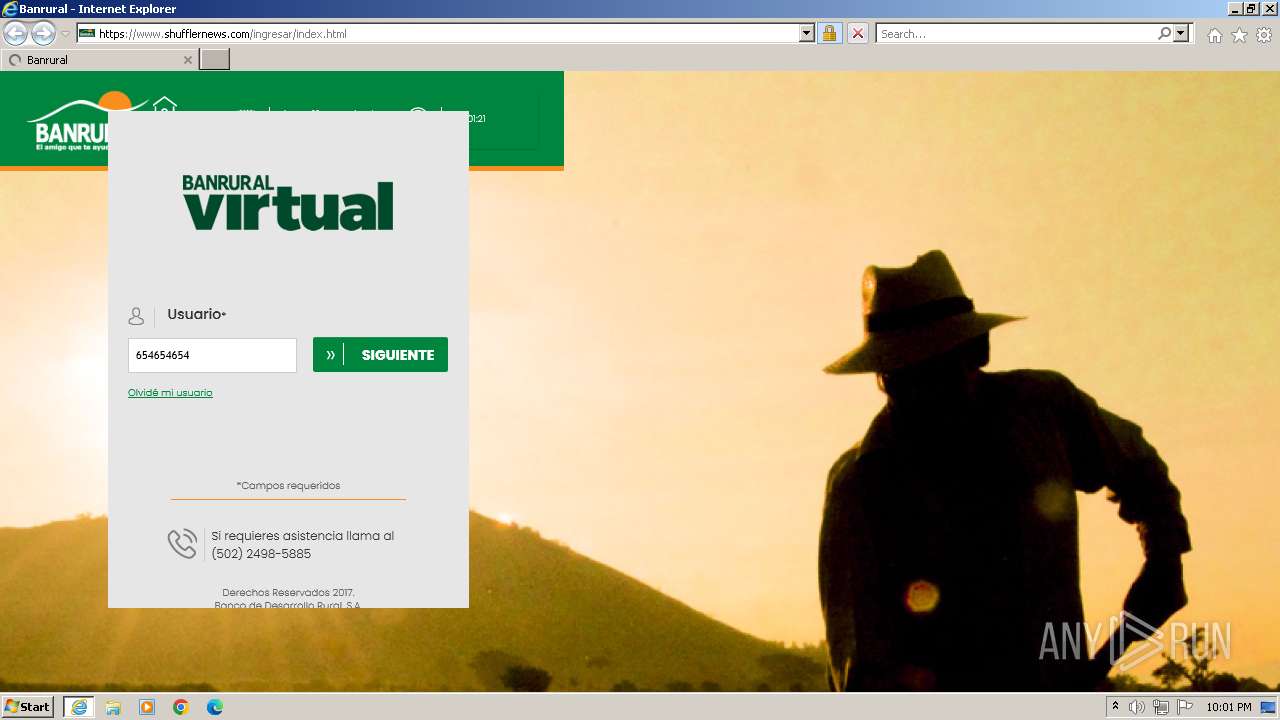
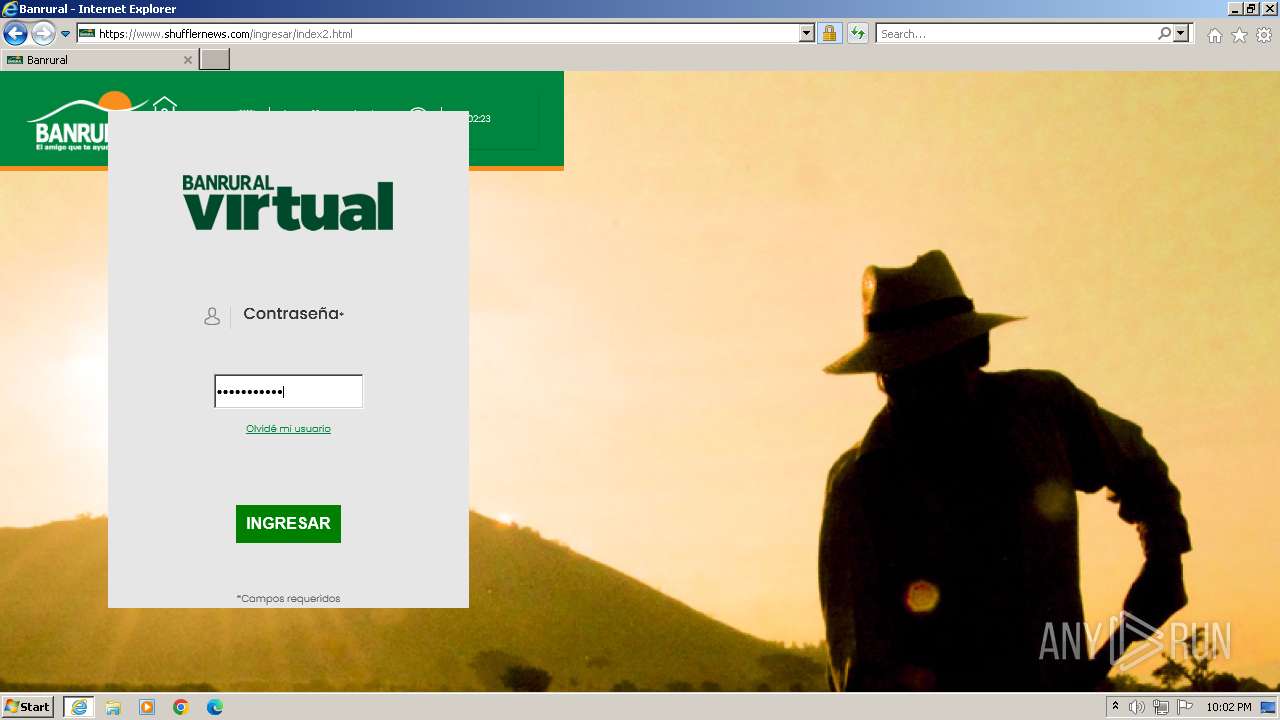
| URL: | https://www.shufflernews.com/ingresar/index.html |
| Full analysis: | https://app.any.run/tasks/030eef62-ade5-41da-9b61-0616f7b3ce56 |
| Verdict: | Malicious activity |
| Analysis date: | November 13, 2023, 22:00:52 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| SHA1: | C899EE5DA10C8E2D941B4165B4CF877D46EED1AB |
| SHA256: | 4A1C7F4220B099E36D0F7260D39313FA1C5D62CE7699A996BB64732FC846C7A5 |
| SSDEEP: | 3:N8DSLzJyCtMwAW1LDG:2OLB+wdG |
MALICIOUS
No malicious indicators.SUSPICIOUS
No suspicious indicators.INFO
Application launched itself
- iexplore.exe (PID: 3448)
Manual execution by a user
- wmpnscfg.exe (PID: 3680)
Reads the machine GUID from the registry
- wmpnscfg.exe (PID: 3680)
Checks supported languages
- wmpnscfg.exe (PID: 3680)
Reads the computer name
- wmpnscfg.exe (PID: 3680)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
38
Monitored processes
3
Malicious processes
0
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 3448 | "C:\Program Files\Internet Explorer\iexplore.exe" "https://www.shufflernews.com/ingresar/index.html" | C:\Program Files\Internet Explorer\iexplore.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Internet Explorer Exit code: 0 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
| 3484 | "C:\Program Files\Internet Explorer\iexplore.exe" SCODEF:3448 CREDAT:267521 /prefetch:2 | C:\Program Files\Internet Explorer\iexplore.exe | iexplore.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Internet Explorer Exit code: 0 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
| 3680 | "C:\Program Files\Windows Media Player\wmpnscfg.exe" | C:\Program Files\Windows Media Player\wmpnscfg.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Media Player Network Sharing Service Configuration Application Exit code: 0 Version: 12.0.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
Total events
17 639
Read events
17 568
Write events
66
Delete events
5
Modification events
| (PID) Process: | (3448) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPDaysSinceLastAutoMigration |
Value: 0 | |||
| (PID) Process: | (3448) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPLastLaunchHighDateTime |
Value: 30847387 | |||
| (PID) Process: | (3448) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\UrlBlockManager |
| Operation: | write | Name: | NextCheckForUpdateHighDateTime |
Value: 30847437 | |||
| (PID) Process: | (3448) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (3448) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
| (PID) Process: | (3448) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\Main |
| Operation: | write | Name: | CompatibilityFlags |
Value: 0 | |||
| (PID) Process: | (3448) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings |
| Operation: | write | Name: | ProxyEnable |
Value: 0 | |||
| (PID) Process: | (3448) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (3448) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
| (PID) Process: | (3448) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 1 | |||
Executable files
0
Suspicious files
47
Text files
41
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3484 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\77EC63BDA74BD0D0E0426DC8F8008506 | compressed | |
MD5:F3441B8572AAE8801C04F3060B550443 | SHA256:6720349E7D82EE0A8E73920D3C2B7CB2912D9FCF2EDB6FD98F2F12820158B0BF | |||
| 3484 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\77EC63BDA74BD0D0E0426DC8F8008506 | binary | |
MD5:7094400108CDF17CE582D1A42A3E1ECC | SHA256:C1F2540D6D19233810749C013FB388AFD854828139E95FD98FB678783C354DE4 | |||
| 3484 | iexplore.exe | C:\Users\admin\AppData\Local\Temp\Low\Cab7813.tmp | compressed | |
MD5:F3441B8572AAE8801C04F3060B550443 | SHA256:6720349E7D82EE0A8E73920D3C2B7CB2912D9FCF2EDB6FD98F2F12820158B0BF | |||
| 3484 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\103621DE9CD5414CC2538780B4B75751 | binary | |
MD5:D26F34C83619CA89192B1B1A1A3AA1C1 | SHA256:F8F478D27F145C581C24D8A0E570445D3986DB189571C6ED048D2C52441BC91C | |||
| 3484 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\MFAQUS6V\index[1].htm | html | |
MD5:AD984E70B260F6054E6B94156DF55E59 | SHA256:F7B6F2354C495FBDEF930533A4F5FC9561B2C40FCF8734B145E55B0BAC015F0C | |||
| 3484 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\F07644E38ED7C9F37D11EEC6D4335E02_17A1BB9C6401DC9652040571BD192211 | binary | |
MD5:8129546FDA89165745E8F4973F6AE25D | SHA256:B5EC48BCD0A6F77761E7D50ED71872CBF440E749460C8DF0F4A92B245922C533 | |||
| 3484 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\F07644E38ED7C9F37D11EEC6D4335E02_17A1BB9C6401DC9652040571BD192211 | binary | |
MD5:6BBF86B426FBD04D3850D3D5A7A28047 | SHA256:8965E74F6A6CA99C47A5FD765B44C871A583EBB90CB138C3F9461070341DD9D8 | |||
| 3484 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\24BD96D5497F70B3F510A6B53CD43F3E_3A89246FB90C5EE6620004F1AE0EB0EA | binary | |
MD5:ABB446415A64138672FE1CD5359195D9 | SHA256:2D984209E90EA2490FED1F267534C42814CC1443662D9B81AB0780F110C53D19 | |||
| 3484 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\CAF4703619713E3F18D8A9D5D88D6288_A7725538C46DE2D0088EE44974E2CEBA | binary | |
MD5:AC89A852C2AAA3D389B2D2DD312AD367 | SHA256:0B720E19270C672F9B6E0EC40B468AC49376807DE08A814573FE038779534F45 | |||
| 3484 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\MFAQUS6V\jquery.min[1].js | text | |
MD5:DC5E7F18C8D36AC1D3D4753A87C98D0A | SHA256:F7F6A5894F1D19DDAD6FA392B2ECE2C5E578CBF7DA4EA805B6885EB6985B6E3D | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
18
TCP/UDP connections
53
DNS requests
23
Threats
14
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
3484 | iexplore.exe | GET | 200 | 67.26.83.254:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?ef2e01c2b2bd93b0 | unknown | compressed | 4.66 Kb | unknown |
3484 | iexplore.exe | GET | 200 | 67.26.83.254:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/authrootstl.cab?a1f744e7e9e1d6c2 | unknown | compressed | 61.6 Kb | unknown |
3484 | iexplore.exe | GET | 200 | 67.26.83.254:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?d6bb2ad0af14907d | unknown | compressed | 4.66 Kb | unknown |
3484 | iexplore.exe | GET | 200 | 142.250.185.163:80 | http://ocsp.pki.goog/gsr1/MFEwTzBNMEswSTAJBgUrDgMCGgUABBS3V7W2nAf4FiMTjpDJKg6%2BMgGqMQQUYHtmGkUNl8qJUC99BM00qP%2F8%2FUsCEHe9DWzbNvka6iEPxPBY0w0%3D | unknown | binary | 1.41 Kb | unknown |
3484 | iexplore.exe | GET | 200 | 67.26.83.254:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/authrootstl.cab?0a000671939419a2 | unknown | compressed | 61.6 Kb | unknown |
3484 | iexplore.exe | GET | 200 | 23.56.202.135:80 | http://x1.c.lencr.org/ | unknown | der | 717 b | unknown |
3484 | iexplore.exe | GET | 200 | 142.250.185.163:80 | http://ocsp.pki.goog/gts1c3/MFIwUDBOMEwwSjAJBgUrDgMCGgUABBTHLnmK3f9hNLO67UdCuLvGwCQHYwQUinR%2Fr4XN7pXNPZzQ4kYU83E1HScCEQCSbiqNK5280hBN2lVZWzUN | unknown | binary | 472 b | unknown |
3484 | iexplore.exe | GET | 200 | 184.24.77.59:80 | http://r3.o.lencr.org/MFMwUTBPME0wSzAJBgUrDgMCGgUABBRI2smg%2ByvTLU%2Fw3mjS9We3NfmzxAQUFC6zF7dYVsuuUAlA5h%2BvnYsUwsYCEgOoFXMjwie%2BV%2FmGSEjIsZh5Lw%3D%3D | unknown | binary | 503 b | unknown |
3484 | iexplore.exe | GET | 200 | 142.250.185.163:80 | http://ocsp.pki.goog/gtsr1/ME4wTDBKMEgwRjAJBgUrDgMCGgUABBQwkcLWD4LqGJ7bE7B1XZsEbmfwUAQU5K8rJnEaK0gnhS9SZizv8IkTcT4CDQIDvFNZazTHGPUBUGY%3D | unknown | binary | 724 b | unknown |
3484 | iexplore.exe | GET | 200 | 142.250.185.163:80 | http://ocsp.pki.goog/gts1c3/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTHLnmK3f9hNLO67UdCuLvGwCQHYwQUinR%2Fr4XN7pXNPZzQ4kYU83E1HScCEGNkd7zfgP4rEhC%2BpCYwNEA%3D | unknown | binary | 471 b | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
1080 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
3484 | iexplore.exe | 67.26.83.254:80 | ctldl.windowsupdate.com | LEVEL3 | US | unknown |
3484 | iexplore.exe | 23.56.202.135:80 | x1.c.lencr.org | AKAMAI-AS | GB | unknown |
2588 | svchost.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
3484 | iexplore.exe | 103.188.22.9:443 | — | Host Universal Pty Ltd | AU | unknown |
3484 | iexplore.exe | 142.250.185.170:443 | fonts.googleapis.com | GOOGLE | US | whitelisted |
3484 | iexplore.exe | 142.250.186.42:443 | ajax.googleapis.com | GOOGLE | US | whitelisted |
3484 | iexplore.exe | 142.250.185.163:80 | ocsp.pki.goog | GOOGLE | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
ctldl.windowsupdate.com |
| whitelisted |
x1.c.lencr.org |
| whitelisted |
fonts.googleapis.com |
| whitelisted |
ajax.googleapis.com |
| whitelisted |
ocsp.pki.goog |
| whitelisted |
api.bing.com |
| whitelisted |
www.bing.com |
| whitelisted |
api.ipify.org |
| shared |
ipinfo.io |
| shared |
fonts.gstatic.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
1080 | svchost.exe | Misc activity | ET INFO External IP Lookup Domain (ipify .org) in DNS Lookup |
3484 | iexplore.exe | Device Retrieving External IP Address Detected | ET POLICY Possible External IP Lookup Domain Observed in SNI (ipinfo. io) |
3484 | iexplore.exe | Device Retrieving External IP Address Detected | ET POLICY Possible External IP Lookup Domain Observed in SNI (ipinfo. io) |
3484 | iexplore.exe | Device Retrieving External IP Address Detected | ET POLICY Possible External IP Lookup SSL Cert Observed (ipinfo.io) |
3484 | iexplore.exe | Device Retrieving External IP Address Detected | ET POLICY Possible External IP Lookup SSL Cert Observed (ipinfo.io) |
3484 | iexplore.exe | Misc activity | ET INFO External IP Address Lookup Domain (ipify .org) in TLS SNI |
3484 | iexplore.exe | Misc activity | ET INFO External IP Address Lookup Domain (ipify .org) in TLS SNI |
3484 | iexplore.exe | Misc activity | ET INFO External IP Address Lookup Domain (ipify .org) in TLS SNI |
3484 | iexplore.exe | Misc activity | ET INFO External IP Address Lookup Domain (ipify .org) in TLS SNI |
1080 | svchost.exe | Misc activity | ET HUNTING Telegram API Domain in DNS Lookup |