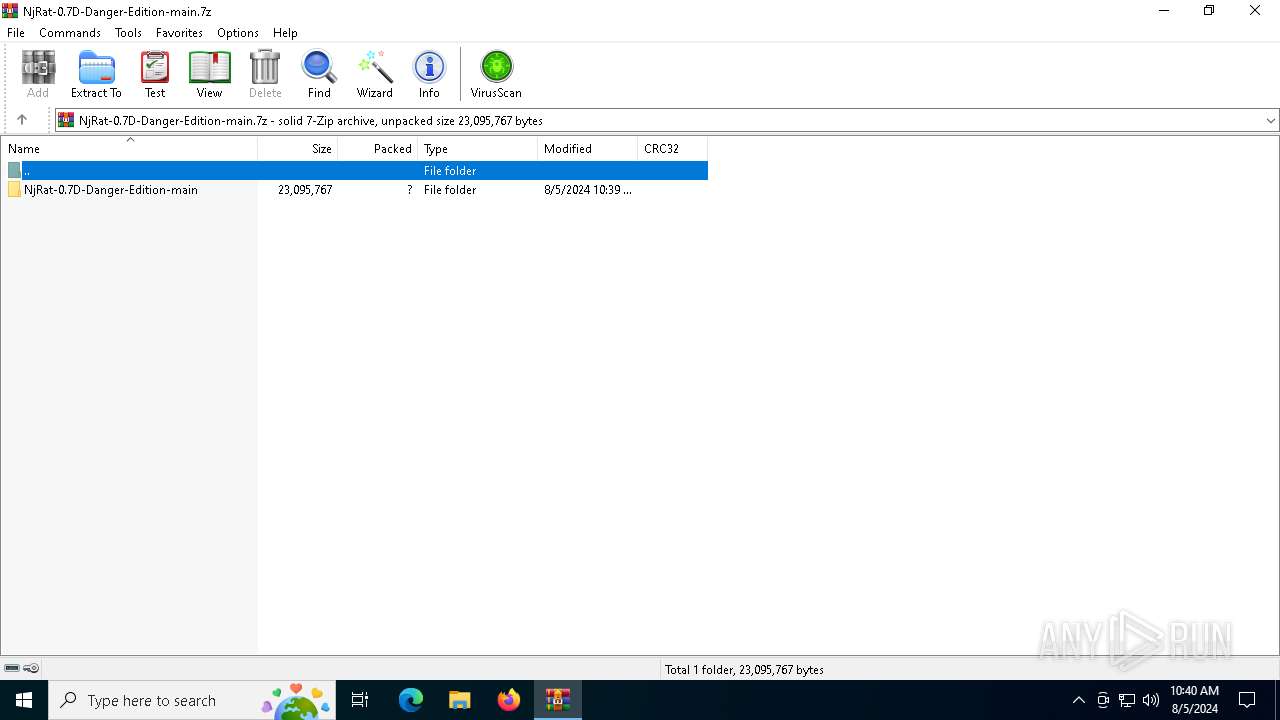
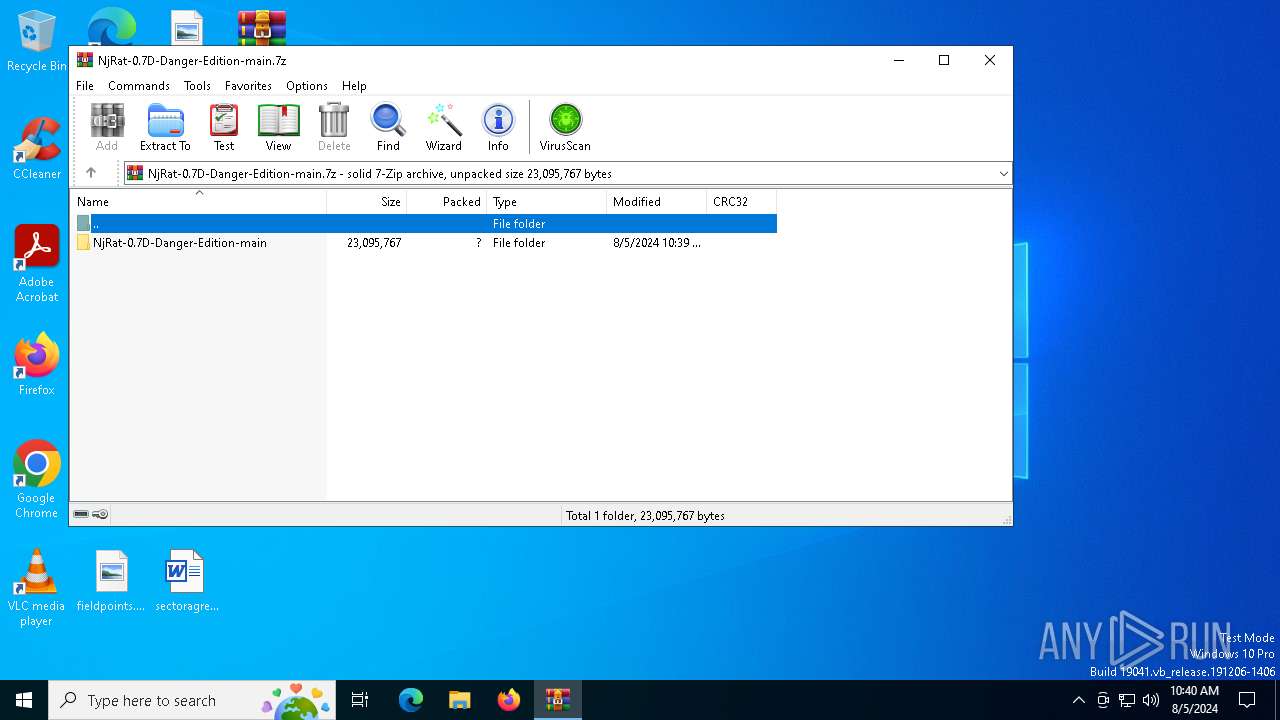
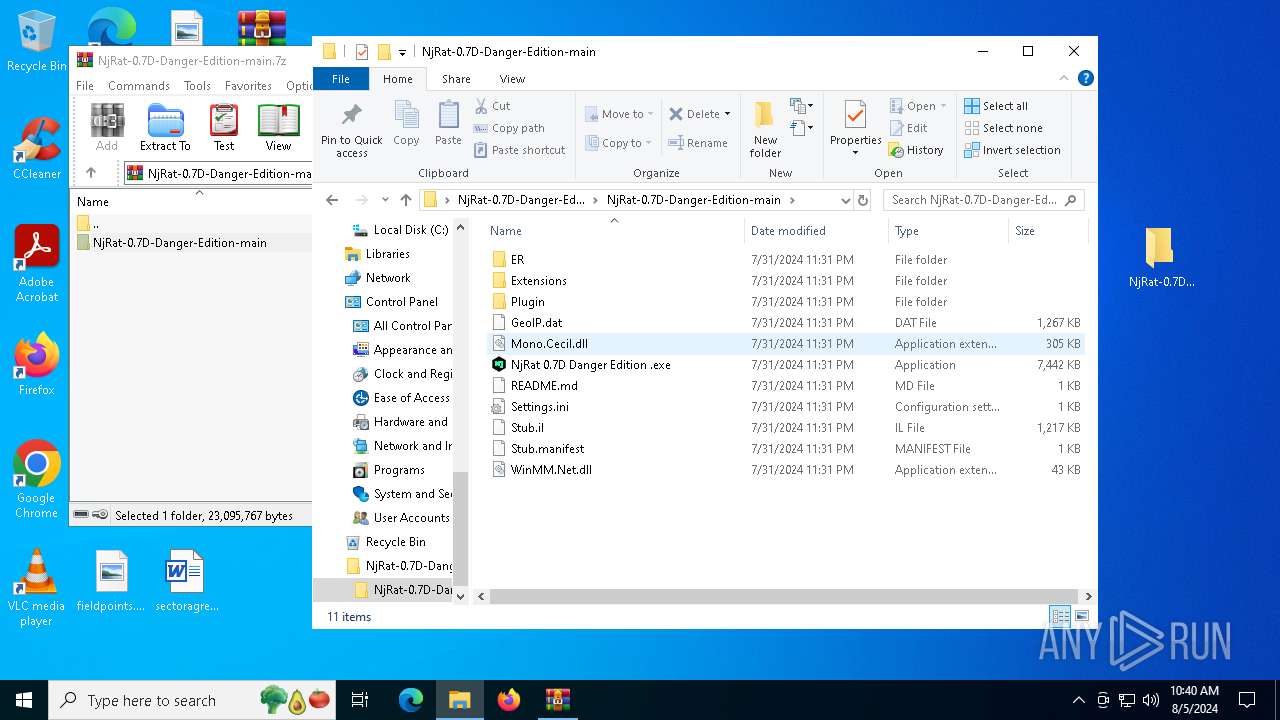
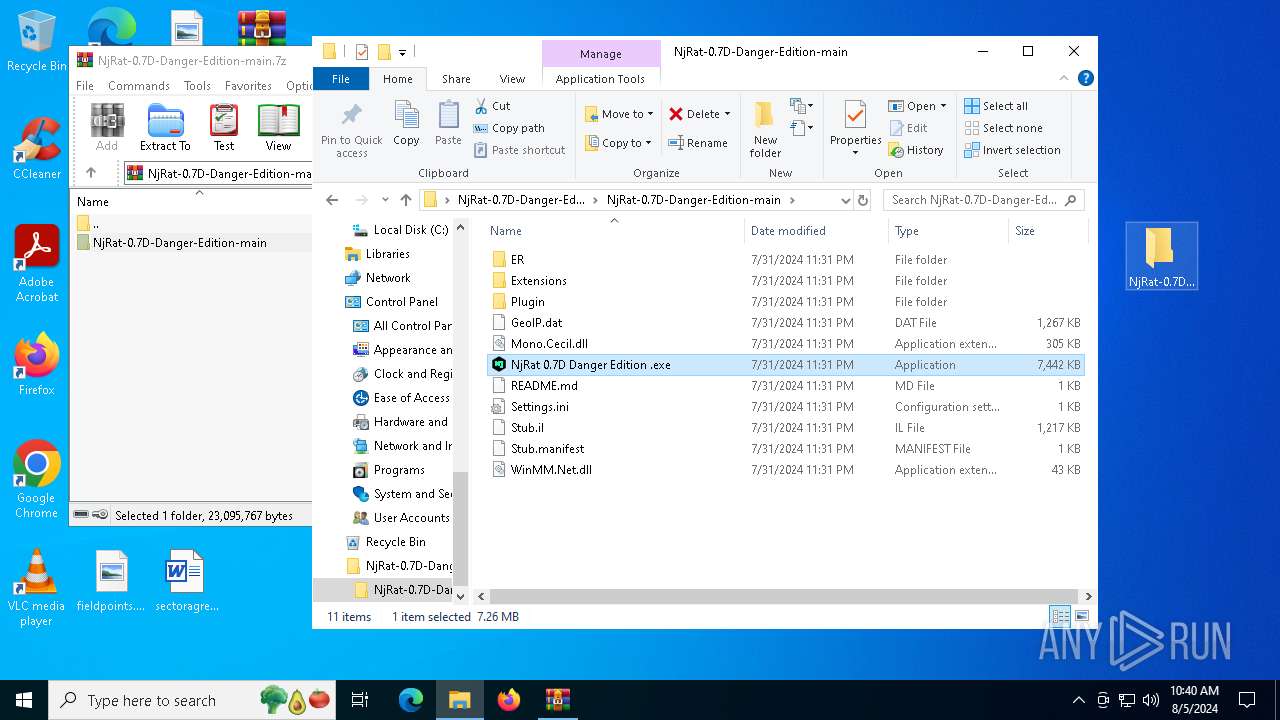
| File name: | NjRat-0.7D-Danger-Edition-main.7z |
| Full analysis: | https://app.any.run/tasks/41386db1-6f66-4dd3-9774-88416d95e6ff |
| Verdict: | Malicious activity |
| Analysis date: | August 05, 2024, 10:40:01 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Indicators: | |
| MIME: | application/x-7z-compressed |
| File info: | 7-zip archive data, version 0.4 |
| MD5: | BC1B18C0D46C1BEEE7603F1629AEAF97 |
| SHA1: | 0CB8D5EBF32D8CCFF35C553CD745C5A51CF8680D |
| SHA256: | 4A0D9EB6B910990F4243CB94B7A7B3F27CA452263984F2FF92A64E905BBBA597 |
| SSDEEP: | 98304:SvKMZudyTrbKWS60juAdHjuEiq4BA6YgLMxTa1Nz/6sHfZ/4XEEXkX1Z8MhXYdBA:J9xOD+gHYswXPCPQc6WJ5DvxqsF |
MALICIOUS
Drops the executable file immediately after the start
- WinRAR.exe (PID: 6460)
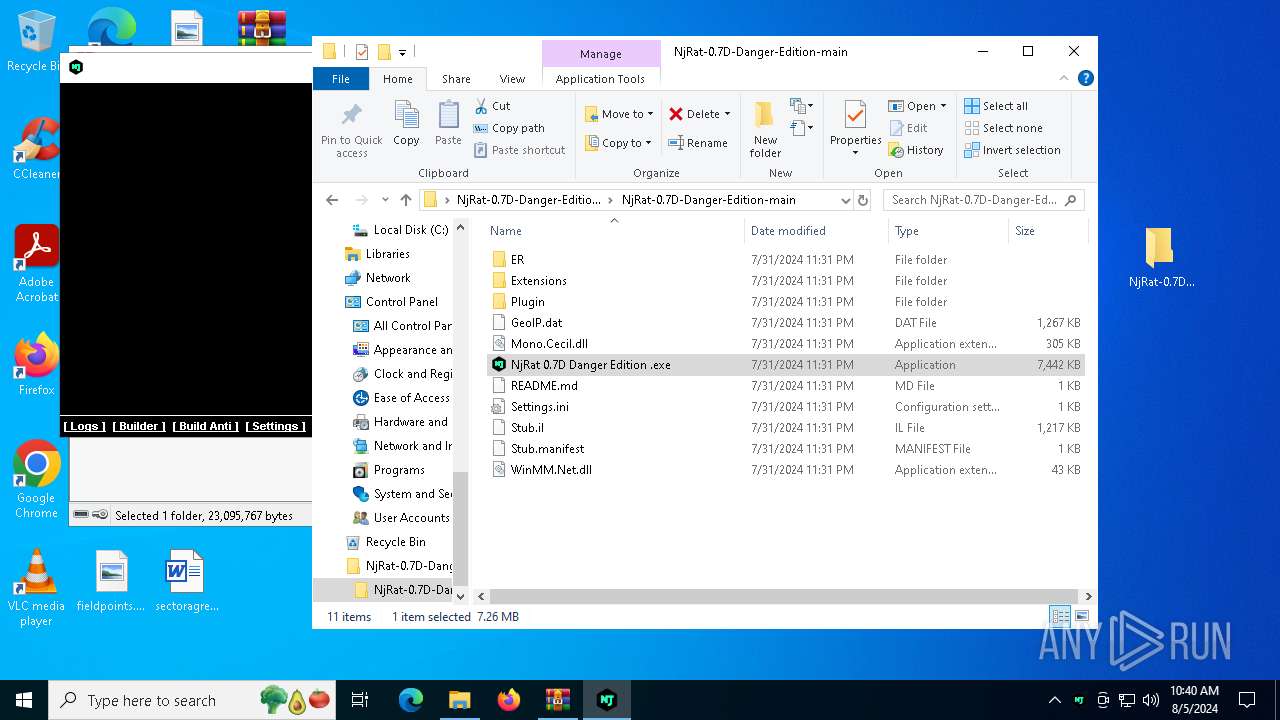
- NjRat 0.7D Danger Edition .exe (PID: 3028)
- system47.exe (PID: 6244)
Application was injected by another process
- dllhost.exe (PID: 3032)
Uses Task Scheduler to autorun other applications
- system47.exe (PID: 6244)
Known privilege escalation attack
- dllhost.exe (PID: 6264)
Runs injected code in another process
- MicrosoftEdgeUpdateTaskMachineUAC.COM (PID: 4280)
Scans artifacts that could help determine the target
- dw20.exe (PID: 6280)
XWORM has been detected (YARA)
- MicrosoftEdgeUpdateTaskMachineUACS.exe (PID: 6296)
SUSPICIOUS
Process drops legitimate windows executable
- WinRAR.exe (PID: 6460)
The process creates files with name similar to system file names
- WinRAR.exe (PID: 6460)
Executable content was dropped or overwritten
- NjRat 0.7D Danger Edition .exe (PID: 3028)
- system47.exe (PID: 6244)
Reads security settings of Internet Explorer
- NjRat 0.7D Danger Edition .exe (PID: 3028)
- system47.exe (PID: 4784)
- system47.exe (PID: 6244)
Reads the date of Windows installation
- NjRat 0.7D Danger Edition .exe (PID: 3028)
- system47.exe (PID: 4784)
- system47.exe (PID: 6244)
- dw20.exe (PID: 6280)
Starts application with an unusual extension
- system47.exe (PID: 6244)
Probably UAC bypass using CMSTP.exe (Connection Manager service profile)
- system47.exe (PID: 4784)
Uses TASKKILL.EXE to kill process
- mshta.exe (PID: 3520)
Runs shell command (SCRIPT)
- mshta.exe (PID: 3520)
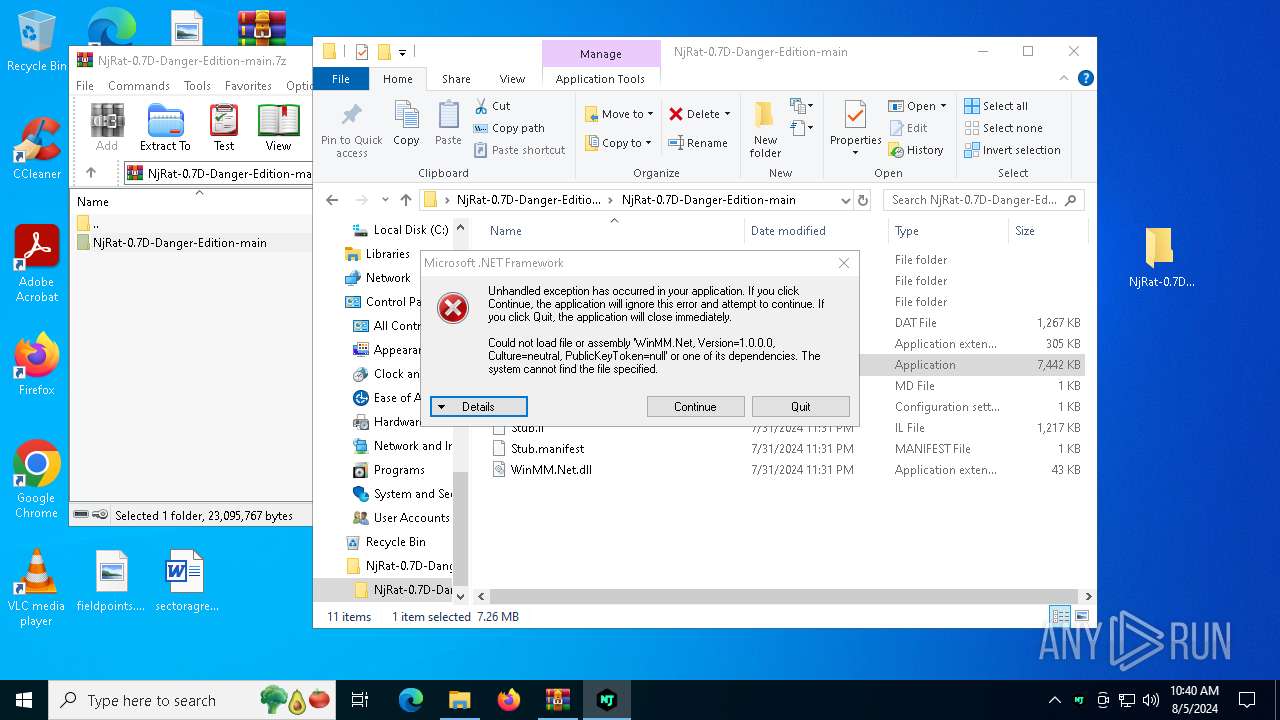
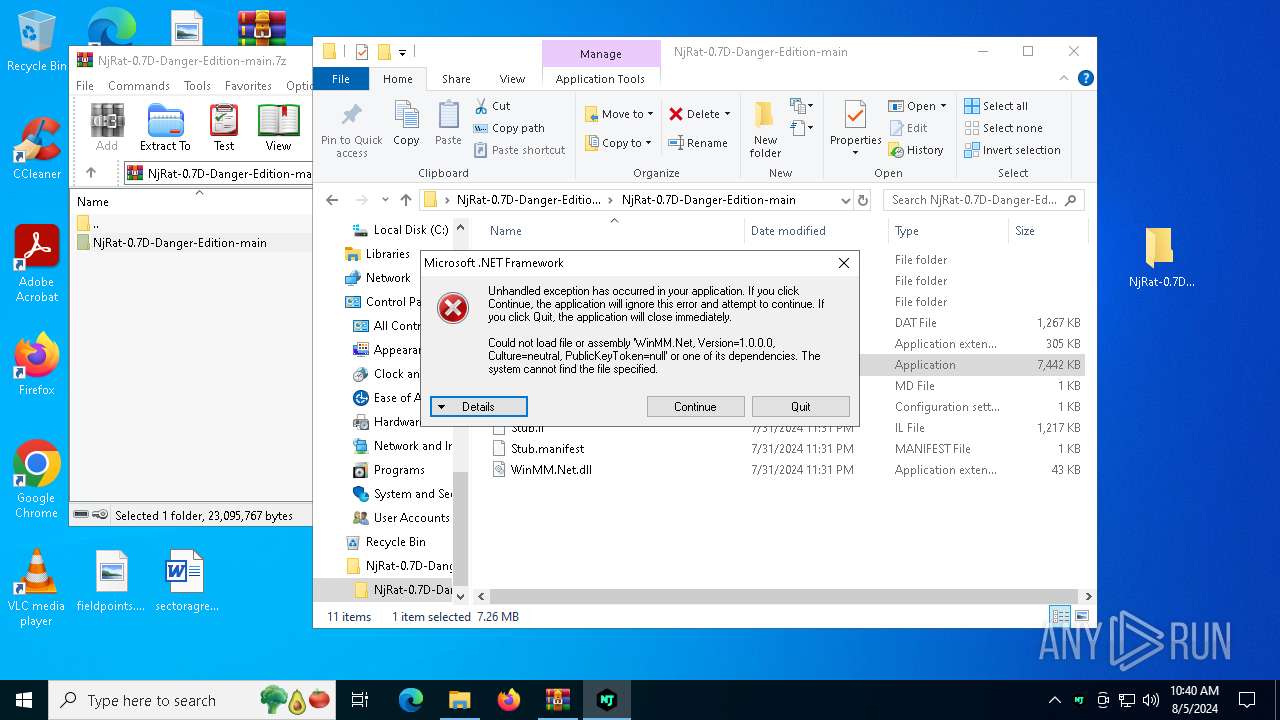
Executes application which crashes
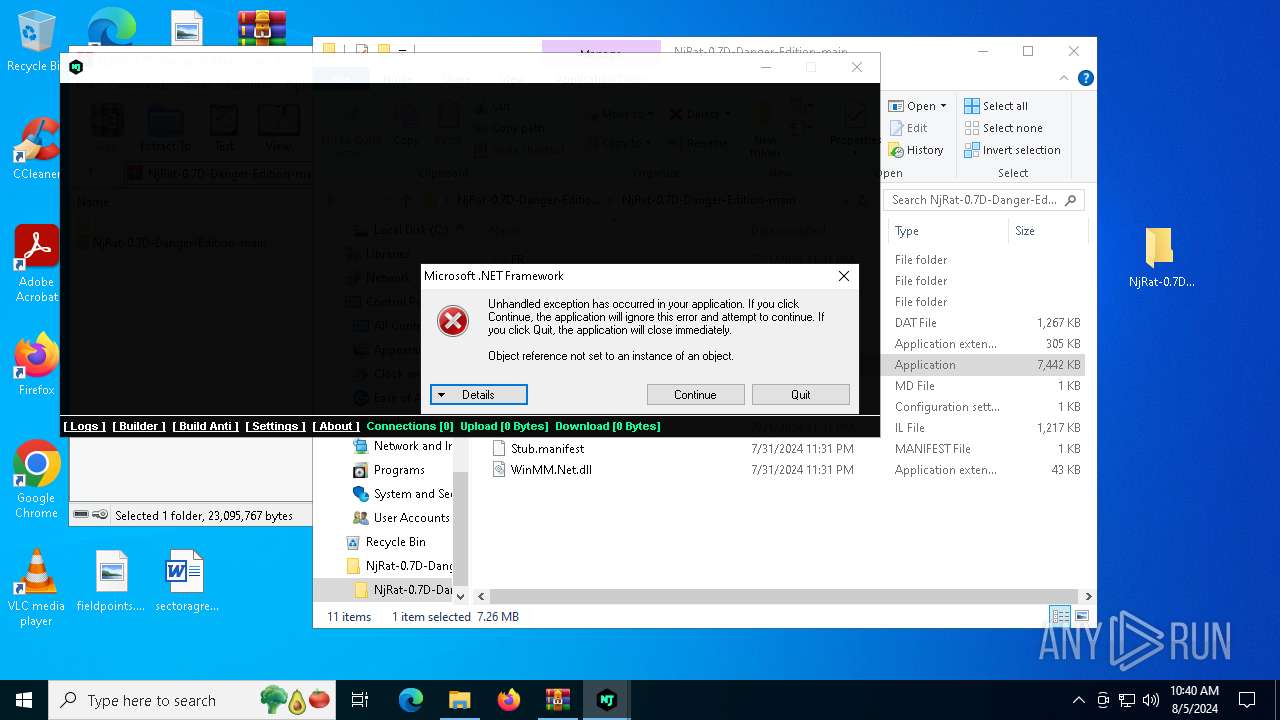
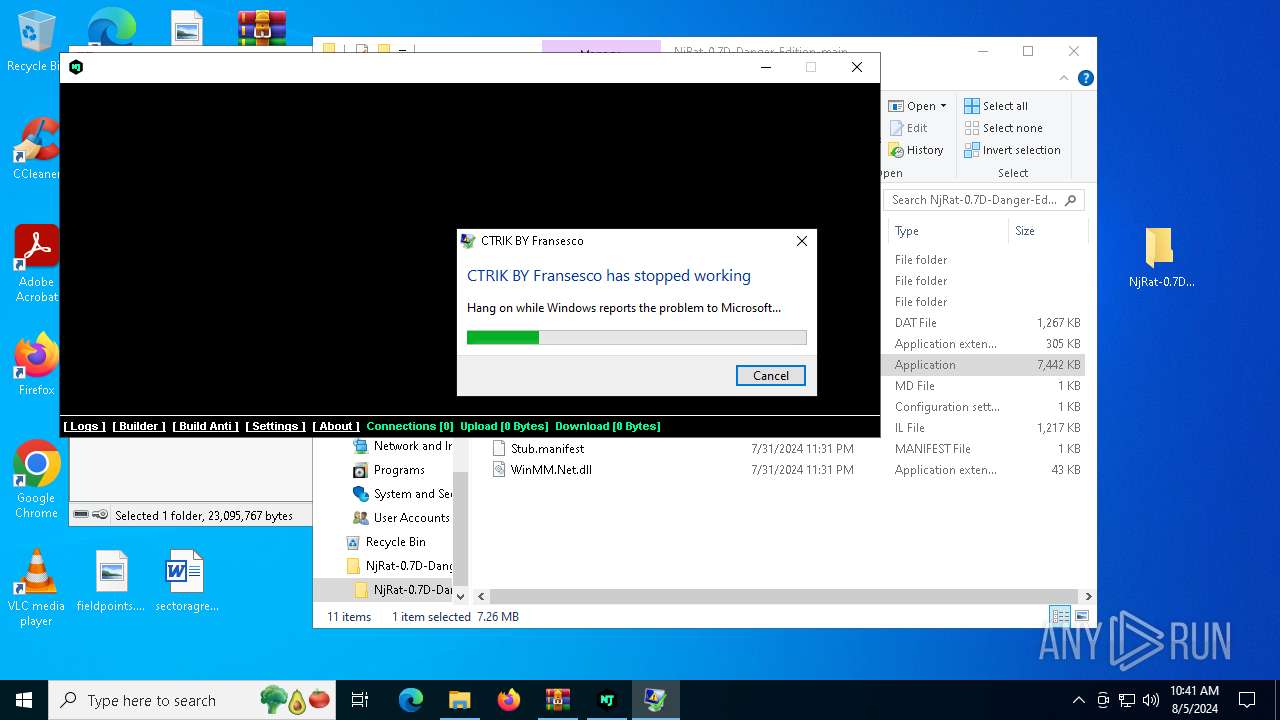
- NjRat 0.7D Danger Edition.exe (PID: 7084)
Connects to unusual port
- MicrosoftEdgeUpdateTaskMachineUACS.exe (PID: 6296)
INFO
Executable content was dropped or overwritten
- WinRAR.exe (PID: 6460)
Checks supported languages
- NjRat 0.7D Danger Edition .exe (PID: 3028)
- system47.exe (PID: 4784)
- NjRat 0.7D Danger Edition.exe (PID: 7084)
- system47.exe (PID: 6244)
- MicrosoftEdgeUpdateTaskMachineUAC.COM (PID: 4280)
- MicrosoftEdgeUpdateTaskMachineUACS.exe (PID: 6296)
- dw20.exe (PID: 6280)
Reads the computer name
- NjRat 0.7D Danger Edition .exe (PID: 3028)
- NjRat 0.7D Danger Edition.exe (PID: 7084)
- system47.exe (PID: 4784)
- system47.exe (PID: 6244)
- MicrosoftEdgeUpdateTaskMachineUAC.COM (PID: 4280)
- MicrosoftEdgeUpdateTaskMachineUACS.exe (PID: 6296)
- dw20.exe (PID: 6280)
Reads the machine GUID from the registry
- NjRat 0.7D Danger Edition .exe (PID: 3028)
- system47.exe (PID: 4784)
- NjRat 0.7D Danger Edition.exe (PID: 7084)
- system47.exe (PID: 6244)
- MicrosoftEdgeUpdateTaskMachineUACS.exe (PID: 6296)
- dw20.exe (PID: 6280)
Manual execution by a user
- NjRat 0.7D Danger Edition .exe (PID: 3028)
Create files in a temporary directory
- NjRat 0.7D Danger Edition .exe (PID: 3028)
Process checks computer location settings
- NjRat 0.7D Danger Edition .exe (PID: 3028)
- system47.exe (PID: 4784)
- system47.exe (PID: 6244)
- dw20.exe (PID: 6280)
Disables trace logs
- cmstp.exe (PID: 7156)
- MicrosoftEdgeUpdateTaskMachineUACS.exe (PID: 6296)
Checks transactions between databases Windows and Oracle
- cmstp.exe (PID: 7156)
Checks proxy server information
- MicrosoftEdgeUpdateTaskMachineUACS.exe (PID: 6296)
- dw20.exe (PID: 6280)
Reads Internet Explorer settings
- mshta.exe (PID: 3520)
Creates files in the program directory
- dllhost.exe (PID: 6264)
- dw20.exe (PID: 6280)
Reads product name
- dw20.exe (PID: 6280)
Reads Environment values
- MicrosoftEdgeUpdateTaskMachineUACS.exe (PID: 6296)
- dw20.exe (PID: 6280)
Reads the software policy settings
- MicrosoftEdgeUpdateTaskMachineUACS.exe (PID: 6296)
- dw20.exe (PID: 6280)
Reads CPU info
- dw20.exe (PID: 6280)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
XWorm
(PID) Process(6296) MicrosoftEdgeUpdateTaskMachineUACS.exe
C267iwnduNNk0l2tXU26CE+bcrkHoGEEq1sKUig1K15uT9rdM5I1WifHuL5X9LuT6k:%IP%
Keys
AES%Port%
Options
SplitterWmmfFV/uWsBOUM/NC8qRoQ==
USB drop nameV1H0rGCW+PxNOMqVLxNGLw==
Mutex2
TRiD
| .7z | | | 7-Zip compressed archive (v0.4) (57.1) |
|---|---|---|
| .7z | | | 7-Zip compressed archive (gen) (42.8) |
Total processes
152
Monitored processes
21
Malicious processes
6
Suspicious processes
4
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 208 | C:\WINDOWS\SysWOW64\WerFault.exe -u -p 7084 -s 1400 | C:\Windows\SysWOW64\WerFault.exe | — | NjRat 0.7D Danger Edition.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Problem Reporting Exit code: 0 Version: 10.0.19041.3996 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1248 | "C:\Windows\System32\taskkill.exe" /IM cmstp.exe /F | C:\Windows\System32\taskkill.exe | — | mshta.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Terminates Processes Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2132 | C:\WINDOWS\System32\rundll32.exe C:\WINDOWS\System32\shell32.dll,SHCreateLocalServerRunDll {9aa46009-3ce0-458a-a354-715610a075e6} -Embedding | C:\Windows\System32\rundll32.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows host process (Rundll32) Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2180 | "C:\Windows\System32\schtasks.exe" /Create /F /TN "MicrosoftEdgeUpdateTaskMachineUACT" /SC ONLOGON /TR "C:\WINDOWS\System32\MicrosoftEdgeUpdateTaskMachineUACT.exe" /RL HIGHEST | C:\Windows\System32\schtasks.exe | — | system47.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Task Scheduler Configuration Tool Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2256 | C:\WINDOWS\system32\svchost.exe -k NetworkService -p -s Dnscache | C:\Windows\System32\svchost.exe | services.exe | ||||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Host Process for Windows Services Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3028 | "C:\Users\admin\Desktop\NjRat-0.7D-Danger-Edition-main\NjRat-0.7D-Danger-Edition-main\NjRat 0.7D Danger Edition .exe" | C:\Users\admin\Desktop\NjRat-0.7D-Danger-Edition-main\NjRat-0.7D-Danger-Edition-main\NjRat 0.7D Danger Edition .exe | explorer.exe | ||||||||||||
User: admin Company: CTRIK BY Fransesco Integrity Level: MEDIUM Description: CTRIK BY Fransesco Exit code: 0 Version: 0.0.0.7 Modules
| |||||||||||||||
| 3032 | C:\Windows\System32\dllhost.exe /Processid:{88021b08-9e50-4fdf-9c9e-282c35c542ec} | C:\Windows\System32\dllhost.exe | winlogon.exe | ||||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: COM Surrogate Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3520 | mshta vbscript:Execute("CreateObject(""WScript.Shell"").Run ""taskkill /IM cmstp.exe /F"", 0, true:close") | C:\Windows\System32\mshta.exe | — | dllhost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Microsoft (R) HTML Application host Exit code: 0 Version: 11.00.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4280 | "C:\WINDOWS\System32\MicrosoftEdgeUpdateTaskMachineUAC.COM" | C:\Windows\System32\MicrosoftEdgeUpdateTaskMachineUAC.COM | — | system47.exe | |||||||||||
User: admin Integrity Level: HIGH Description: Exit code: 0 Version: 0.0.0.0 Modules
| |||||||||||||||
| 4784 | "C:\Users\admin\AppData\Local\Temp\system47.exe" | C:\Users\admin\AppData\Local\Temp\system47.exe | — | NjRat 0.7D Danger Edition .exe | |||||||||||
User: admin Integrity Level: MEDIUM Description: Exit code: 0 Version: 1.0.0.0 Modules
| |||||||||||||||
Total events
18 072
Read events
17 979
Write events
93
Delete events
0
Modification events
| (PID) Process: | (6460) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (6460) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (6460) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\GoogleChromeEnterpriseBundle64.zip | |||
| (PID) Process: | (6460) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Desktop\NjRat-0.7D-Danger-Edition-main.7z | |||
| (PID) Process: | (6460) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (6460) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (6460) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (6460) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (3028) NjRat 0.7D Danger Edition .exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (3028) NjRat 0.7D Danger Edition .exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
Executable files
49
Suspicious files
4
Text files
27
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 6460 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa6460.24522\NjRat-0.7D-Danger-Edition-main\NjRat-0.7D-Danger-Edition-main\Stub.manifest | xml | |
MD5:4D18AC38A92D15A64E2B80447B025B7E | SHA256:835A00D6E7C43DB49AE7B3FA12559F23C2920B7530F4D3F960FD285B42B1EFB5 | |||
| 6460 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa6460.24522\NjRat-0.7D-Danger-Edition-main\NjRat-0.7D-Danger-Edition-main\Settings.ini | text | |
MD5:332F4072F2109E4D81F2701C2387B186 | SHA256:17F547710BF4FEFB27FF4470E0F78089C4888567EEC25380E136D9FDE1E02276 | |||
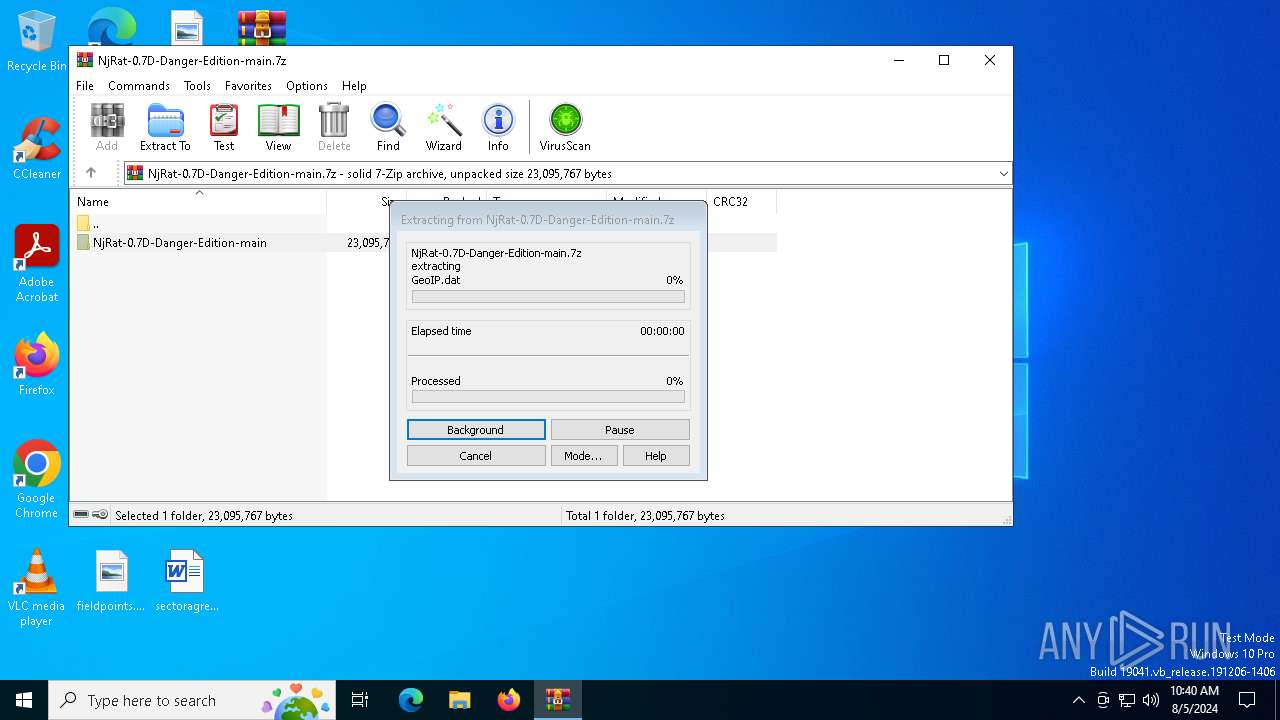
| 6460 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa6460.24522\NjRat-0.7D-Danger-Edition-main\NjRat-0.7D-Danger-Edition-main\GeoIP.dat | binary | |
MD5:797B96CC417D0CDE72E5C25D0898E95E | SHA256:8A0675001B5BC63D8389FC7ED80B4A7B0F9538C744350F00162533519E106426 | |||
| 6460 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa6460.24522\NjRat-0.7D-Danger-Edition-main\NjRat-0.7D-Danger-Edition-main\ER\logoff.dll | text | |
MD5:3D79995C5AF417FB5B26F78B02000F49 | SHA256:2036A894B2C0EAEB684A56B5DA1E2BBF992FF50FBA536E606FB1ADADF6CDEC4C | |||
| 6460 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa6460.24522\NjRat-0.7D-Danger-Edition-main\NjRat-0.7D-Danger-Edition-main\ER\Apraircam.dll | text | |
MD5:CC795C9C4A83AA1EDE067F96F1EB8D15 | SHA256:37D23694738615464BE8A3234BCC59592987432C8863DB67E30385B8BB3EF450 | |||
| 6460 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa6460.24522\NjRat-0.7D-Danger-Edition-main\NjRat-0.7D-Danger-Edition-main\ER\dromous.dll | text | |
MD5:1CC401169EF8CF1E8977F4E92DFE72C7 | SHA256:32C699EBB7394DDB2D56F092EF10FDE4D9F4BCF808DBE11BAD777E7BC73F7AAE | |||
| 6460 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa6460.24522\NjRat-0.7D-Danger-Edition-main\NjRat-0.7D-Danger-Edition-main\ER\Destentrnet.dll | text | |
MD5:0920BFE00503B41BC09350F6D60412E9 | SHA256:0EC9AD05AB5EAC77B92DCDF1B2F8F563D626B9B6A64619DA9FD64AA375F97638 | |||
| 6460 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa6460.24522\NjRat-0.7D-Danger-Edition-main\NjRat-0.7D-Danger-Edition-main\ER\destedmous.dll | text | |
MD5:86DB8AAA81D53BA3647175FA02AEC88D | SHA256:B7DFC64C735CB92F98937B9BB77CBEA0F8BC6BC94E3EF14155B2611A36482E25 | |||
| 6460 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa6460.24522\NjRat-0.7D-Danger-Edition-main\NjRat-0.7D-Danger-Edition-main\ER\laxer.dll | text | |
MD5:E67EE9FA20340544E65BC2CFBA5D8192 | SHA256:21AB187279045E81F550C170FDC8B73117F4E4DC2E608BDB80865540264FDAB6 | |||
| 6460 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa6460.24522\NjRat-0.7D-Danger-Edition-main\NjRat-0.7D-Danger-Edition-main\ER\maltExe.dll | text | |
MD5:94070806E01C1AE7FE2AAE46D929387A | SHA256:4F553023C9FDFEA5F806C86D6BDD40D94348843D4A4EFD91DC952A53229A4358 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
4
TCP/UDP connections
49
DNS requests
21
Threats
7
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
5336 | SearchApp.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
1344 | svchost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
6804 | backgroundTaskHost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | whitelisted |
6832 | backgroundTaskHost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
3888 | svchost.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
5388 | svchost.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
3164 | RUXIMICS.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
2120 | MoUsoCoreWorker.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
5388 | svchost.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
5336 | SearchApp.exe | 2.23.209.141:443 | www.bing.com | Akamai International B.V. | GB | unknown |
5336 | SearchApp.exe | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
3260 | svchost.exe | 40.113.103.199:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
www.bing.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
login.live.com |
| whitelisted |
th.bing.com |
| whitelisted |
fd.api.iris.microsoft.com |
| whitelisted |
arc.msn.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2256 | svchost.exe | Misc activity | ET INFO Pastebin Service Domain in DNS Lookup (rentry .co) |
6296 | MicrosoftEdgeUpdateTaskMachineUACS.exe | Misc activity | ET INFO Observed Pastebin Service Domain (rentry .co in TLS SNI) |
2256 | svchost.exe | Potentially Bad Traffic | ET INFO DYNAMIC_DNS Query to a *.theworkpc .com Domain |
6296 | MicrosoftEdgeUpdateTaskMachineUACS.exe | Not Suspicious Traffic | INFO [ANY.RUN] Image hosting service ImgBB |
2256 | svchost.exe | Not Suspicious Traffic | ET INFO Observed Free Hosting Domain (*.000webhostapp .com in DNS Lookup) |
6296 | MicrosoftEdgeUpdateTaskMachineUACS.exe | Not Suspicious Traffic | ET INFO Observed SSL Cert for Free Hosting Domain (*.000webhostapp .com) |
2256 | svchost.exe | Potentially Bad Traffic | ET POLICY DNS Query to DynDNS Domain *.bounceme .net |