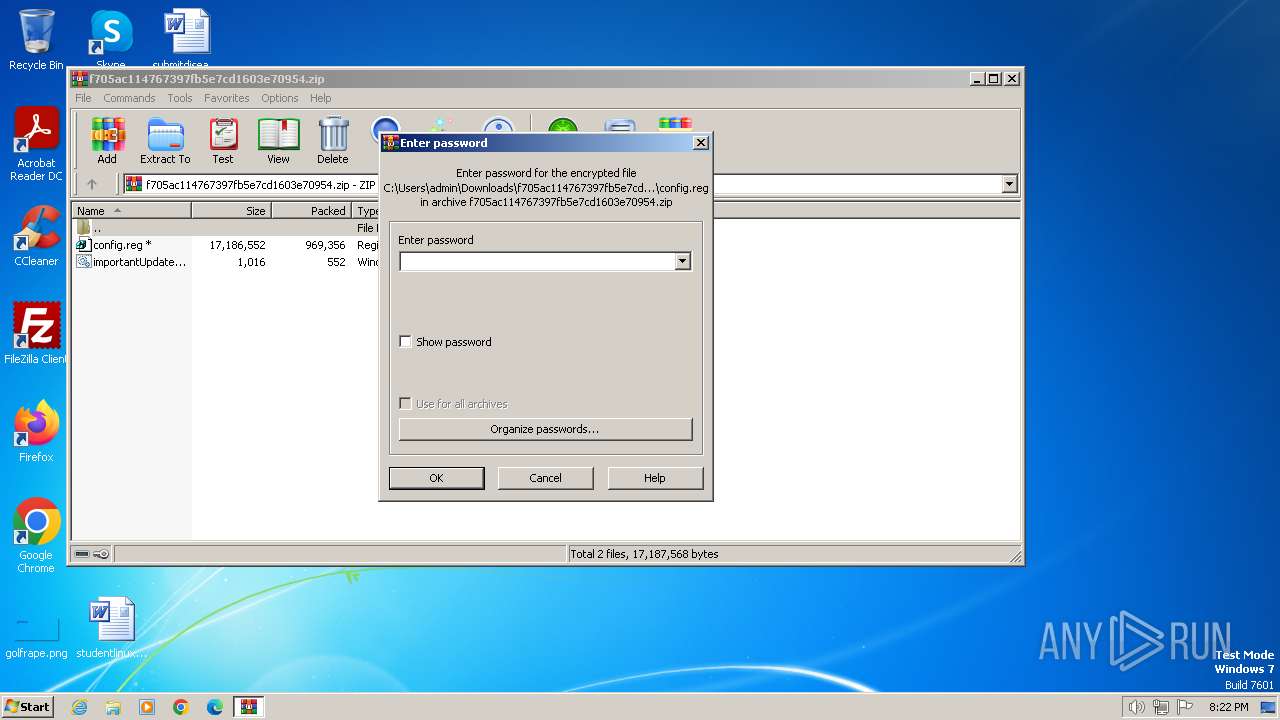
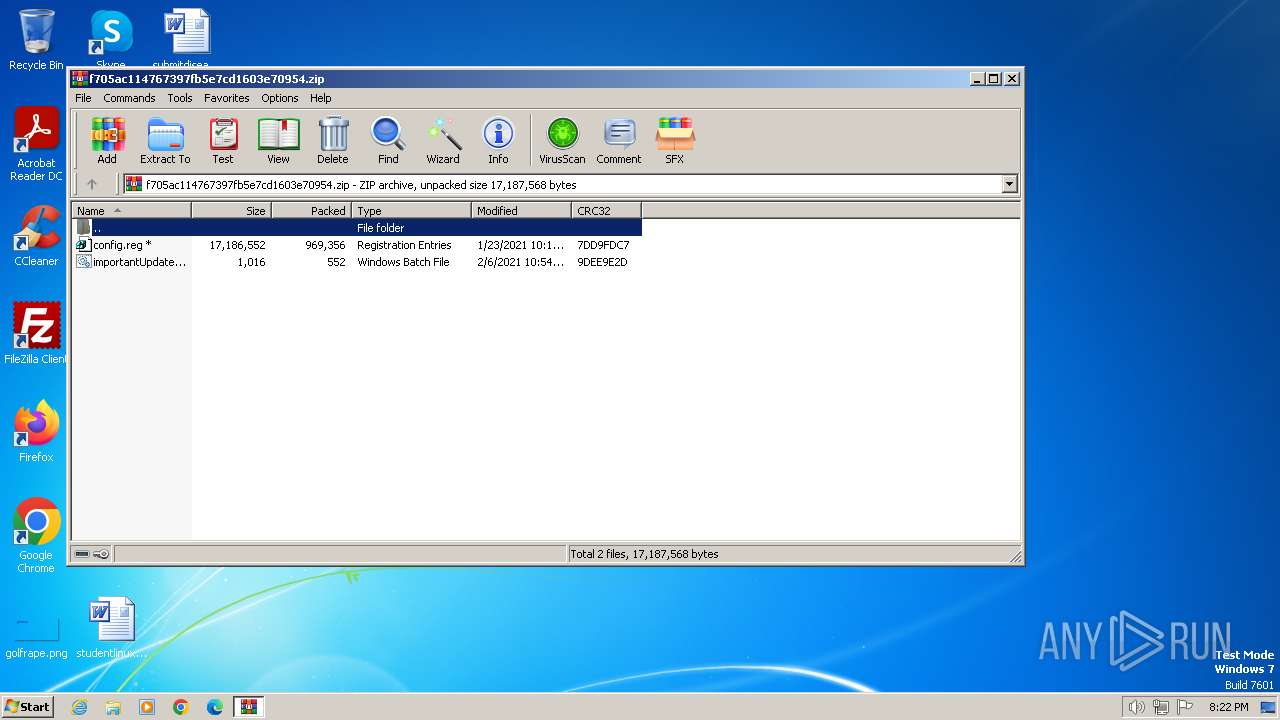
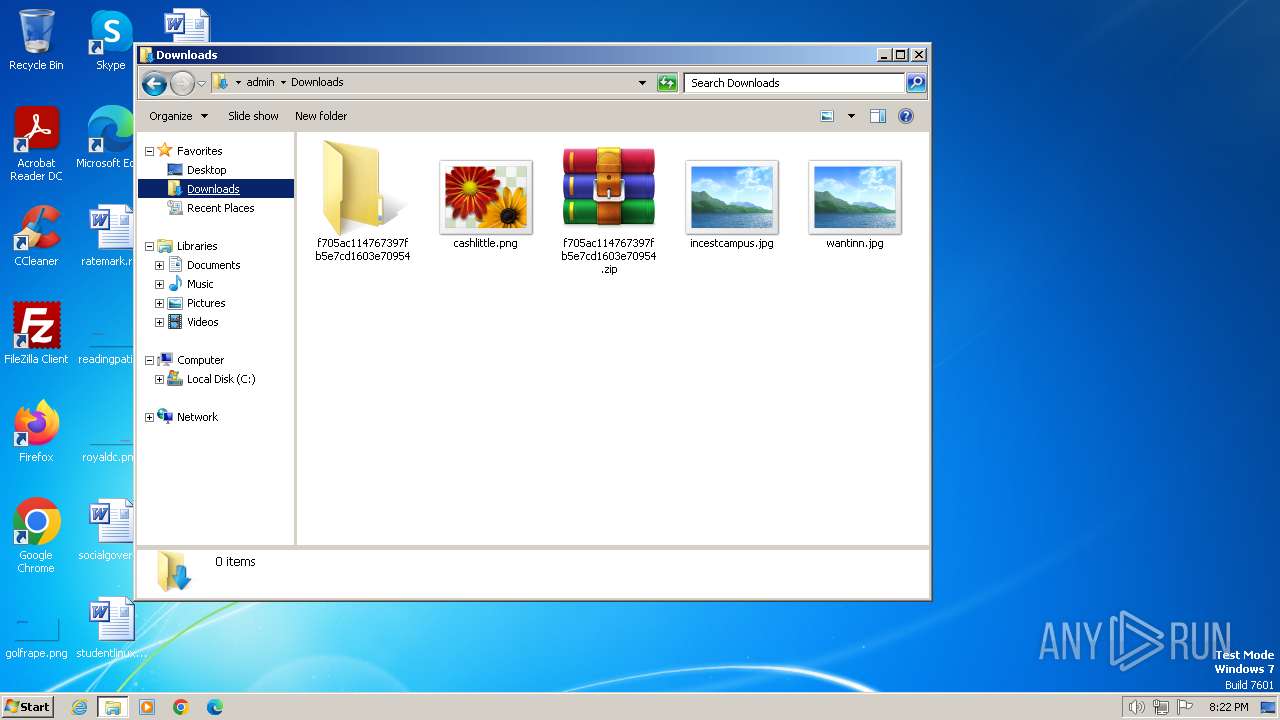
| File name: | f705ac114767397fb5e7cd1603e70954.zip |
| Full analysis: | https://app.any.run/tasks/5229b9a0-4696-4608-ad4a-cbd15d9d0dab |
| Verdict: | Malicious activity |
| Analysis date: | March 16, 2024, 20:21:55 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v2.0 to extract, compression method=AES Encrypted |
| MD5: | 1C18BD70D7D2C482D09E4328EBAD0EA6 |
| SHA1: | 51F906D225DF7BD9B85A4ED99F48C94DDB931428 |
| SHA256: | 4A02D610AB81E5A1861407C729775D15859B5C77E4E2894B230285B95155D020 |
| SSDEEP: | 24576:sv+KuewubKqd2AAC3tKwvQ54IlqysEQJURvytUzg0:sVuLpqkBCdtQmIIBHURP5 |
MALICIOUS
Starts NET.EXE for service management
- net.exe (PID: 1236)
- cmd.exe (PID: 1888)
- net.exe (PID: 1368)
Changes the autorun value in the registry
- reg.exe (PID: 3308)
- regedit.exe (PID: 968)
UAC/LUA settings modification
- regedit.exe (PID: 968)
SUSPICIOUS
Uses ATTRIB.EXE to modify file attributes
- cmd.exe (PID: 1888)
Executing commands from a ".bat" file
- cmd.exe (PID: 1888)
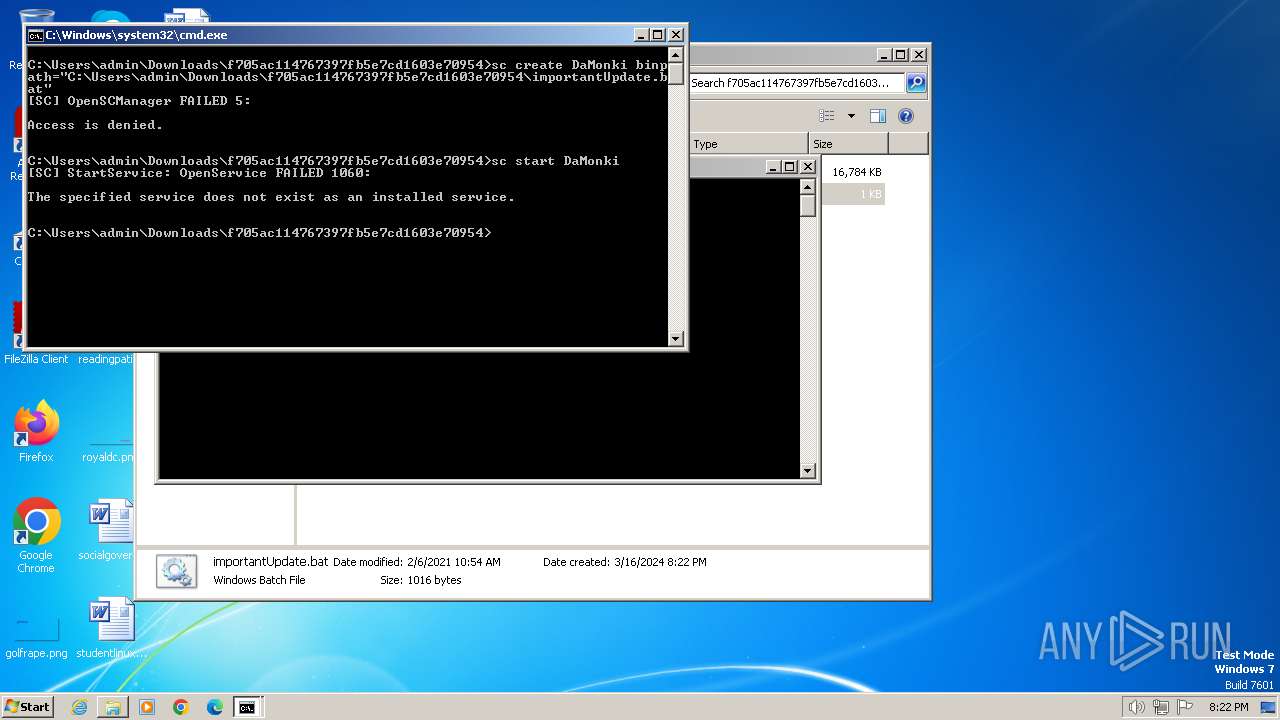
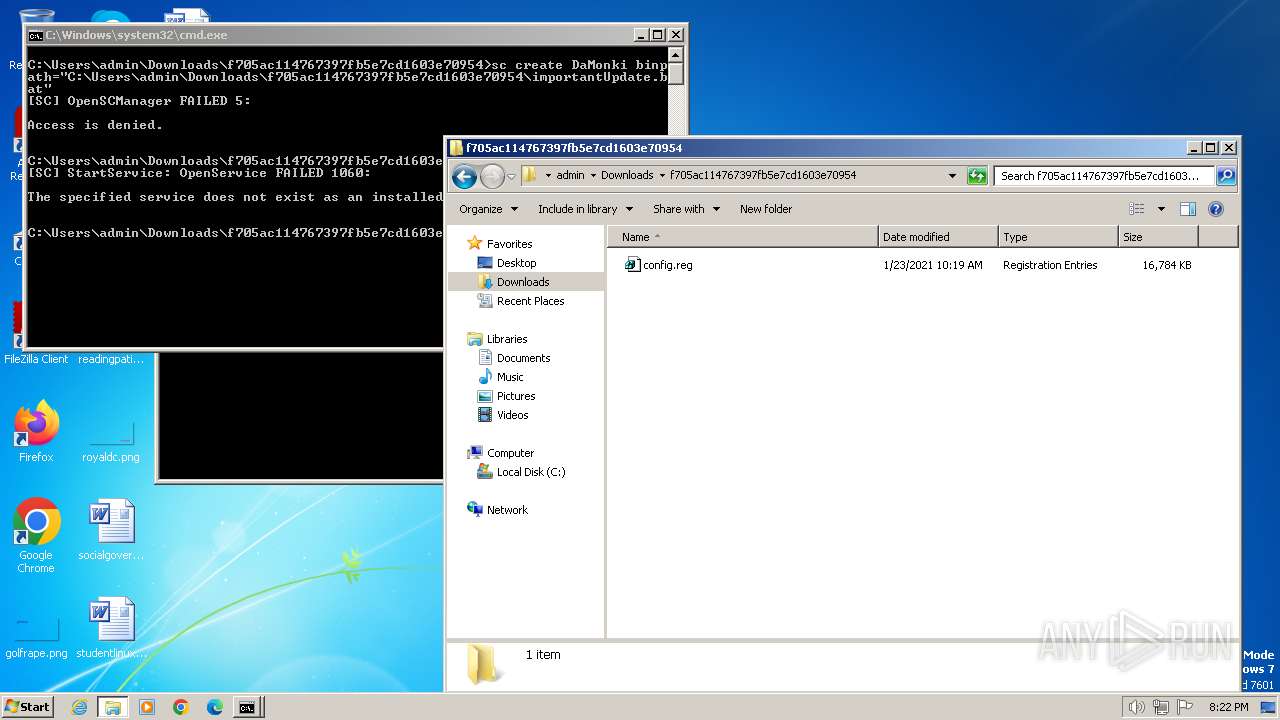
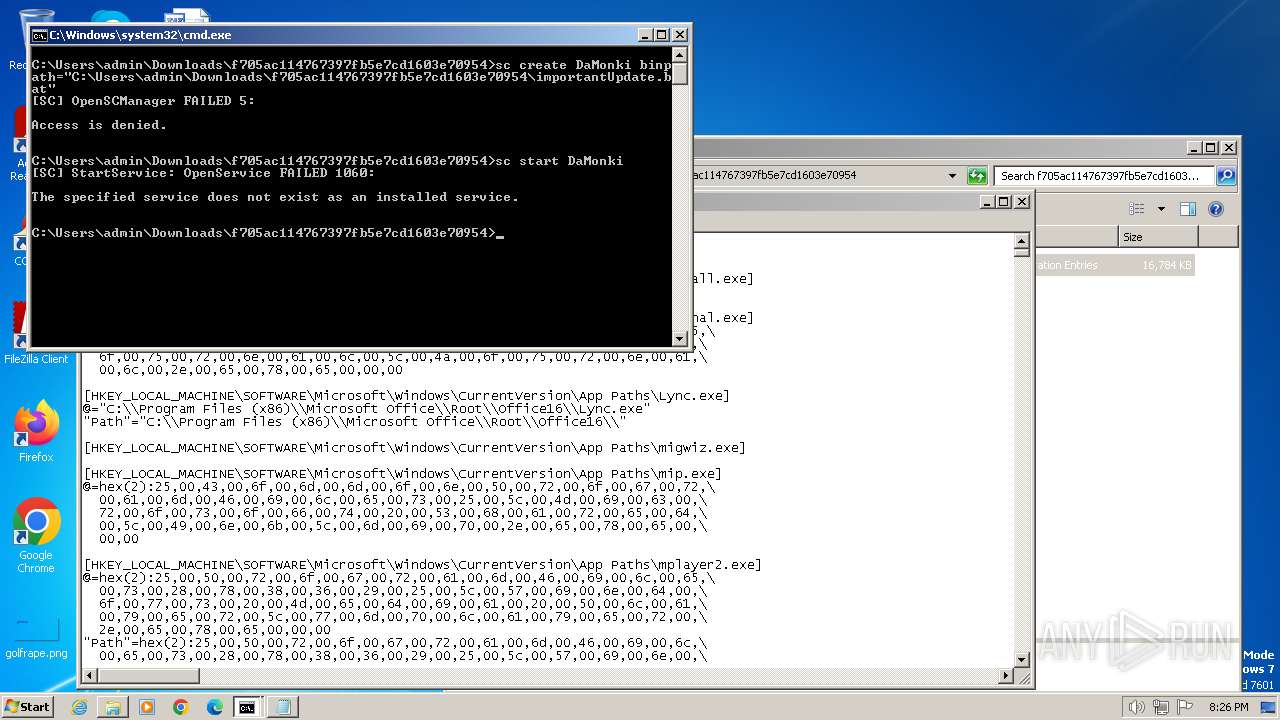
Starts SC.EXE for service management
- cmd.exe (PID: 240)
Application launched itself
- cmd.exe (PID: 1888)
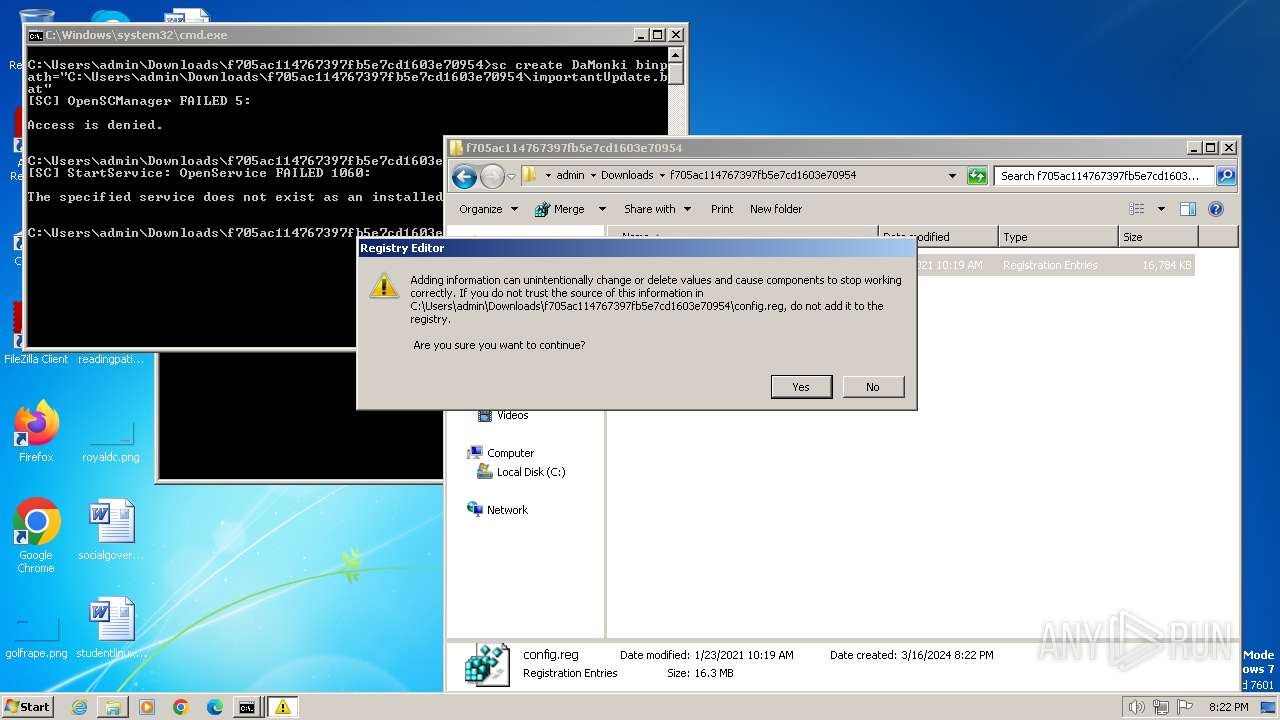
Uses REG/REGEDIT.EXE to modify registry
- cmd.exe (PID: 1888)
Starts CMD.EXE for commands execution
- cmd.exe (PID: 1888)
Reads the Internet Settings
- net.exe (PID: 2260)
- net.exe (PID: 1544)
- net.exe (PID: 948)
- net.exe (PID: 2516)
- net.exe (PID: 3140)
Starts NET.EXE to map network drives
- cmd.exe (PID: 1888)
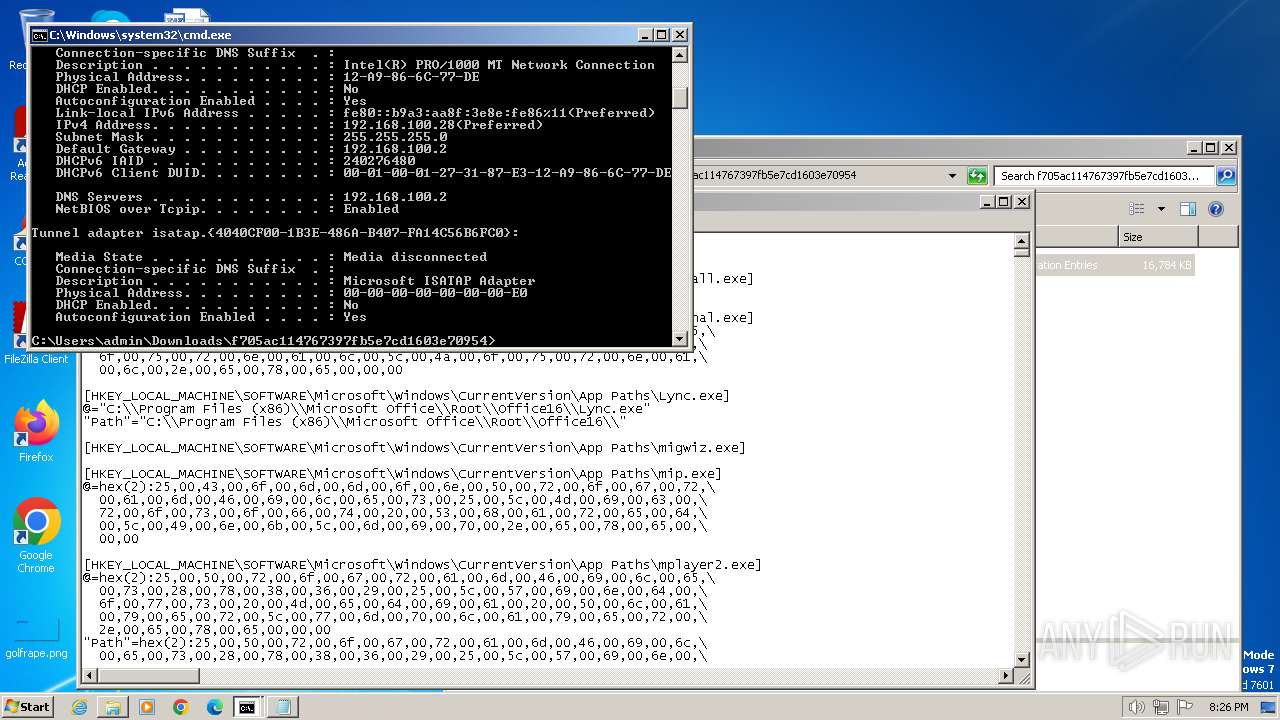
Process uses IPCONFIG to discover network configuration
- cmd.exe (PID: 240)
Changes internet zones settings
- regedit.exe (PID: 968)
Creates a software uninstall entry
- regedit.exe (PID: 968)
INFO
Manual execution by a user
- cmd.exe (PID: 1888)
- explorer.exe (PID: 2232)
- regedit.exe (PID: 2788)
- regedit.exe (PID: 968)
- notepad.exe (PID: 1840)
Changes appearance of the Explorer extensions
- regedit.exe (PID: 968)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 20 |
|---|---|
| ZipBitFlag: | 0x0009 |
| ZipCompression: | Unknown (99) |
| ZipModifyDate: | 2021:01:23 13:19:48 |
| ZipCRC: | 0x7dd9fdc7 |
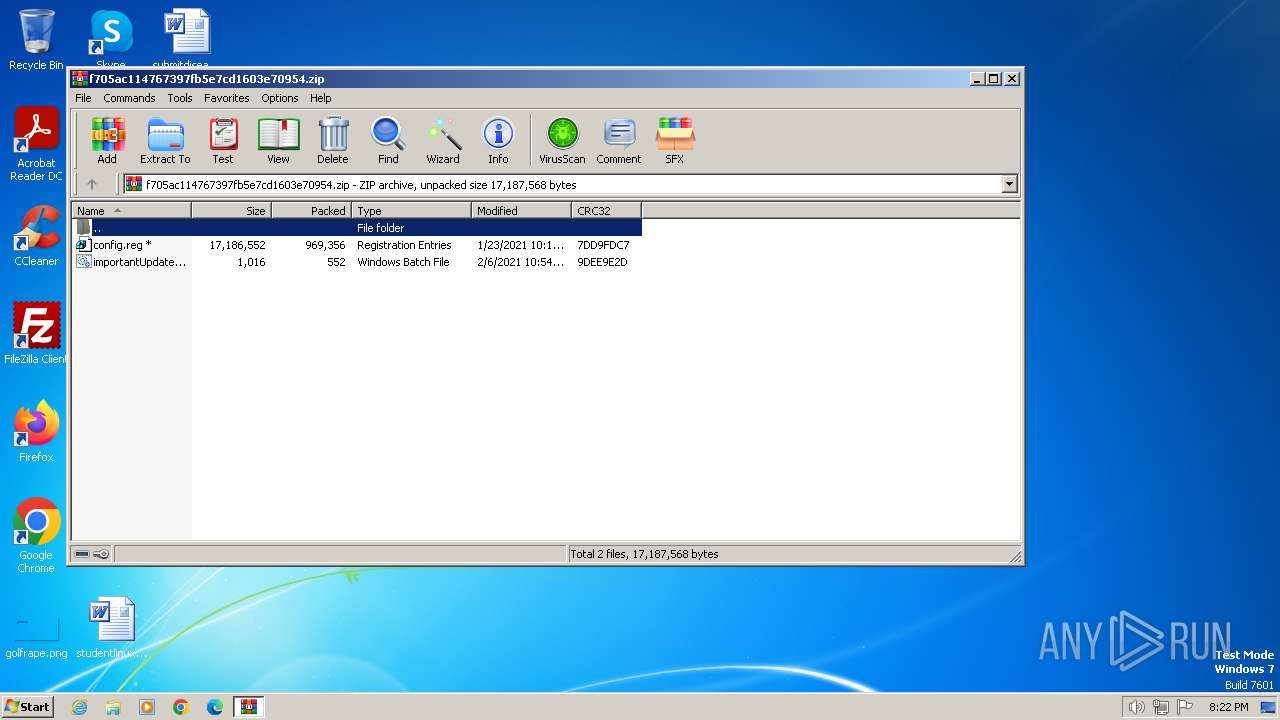
| ZipCompressedSize: | 969356 |
| ZipUncompressedSize: | 17186552 |
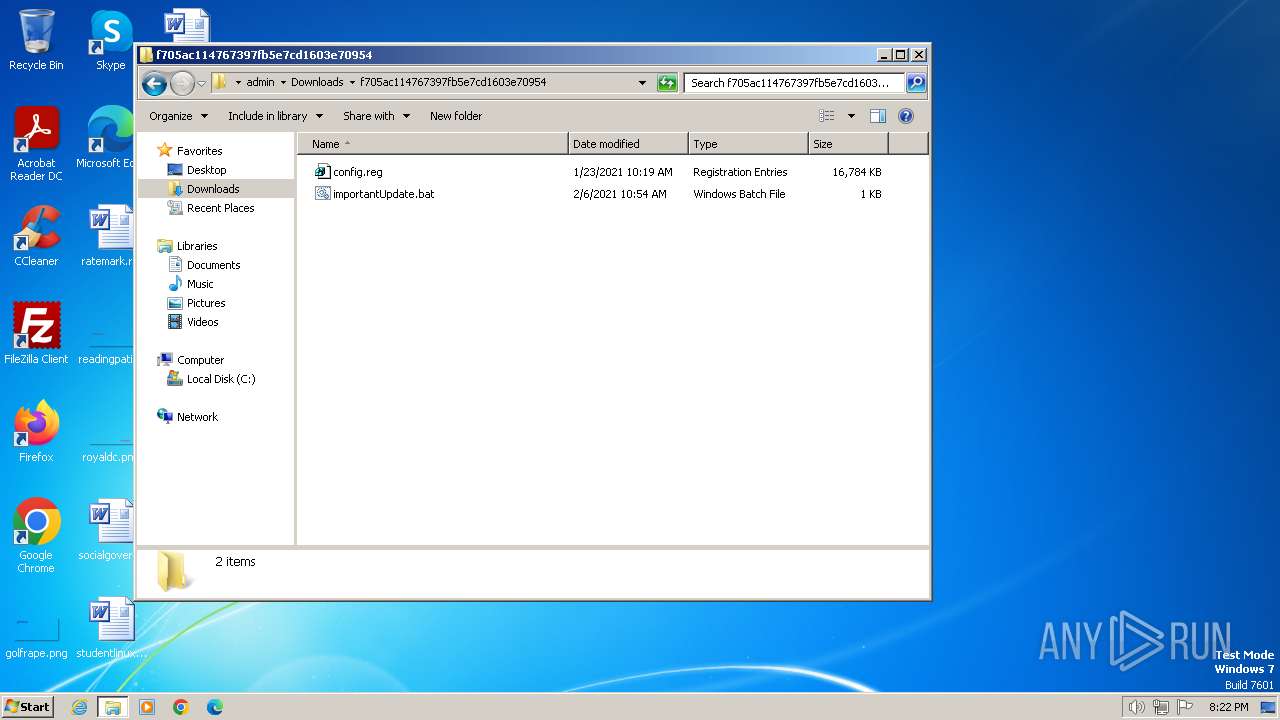
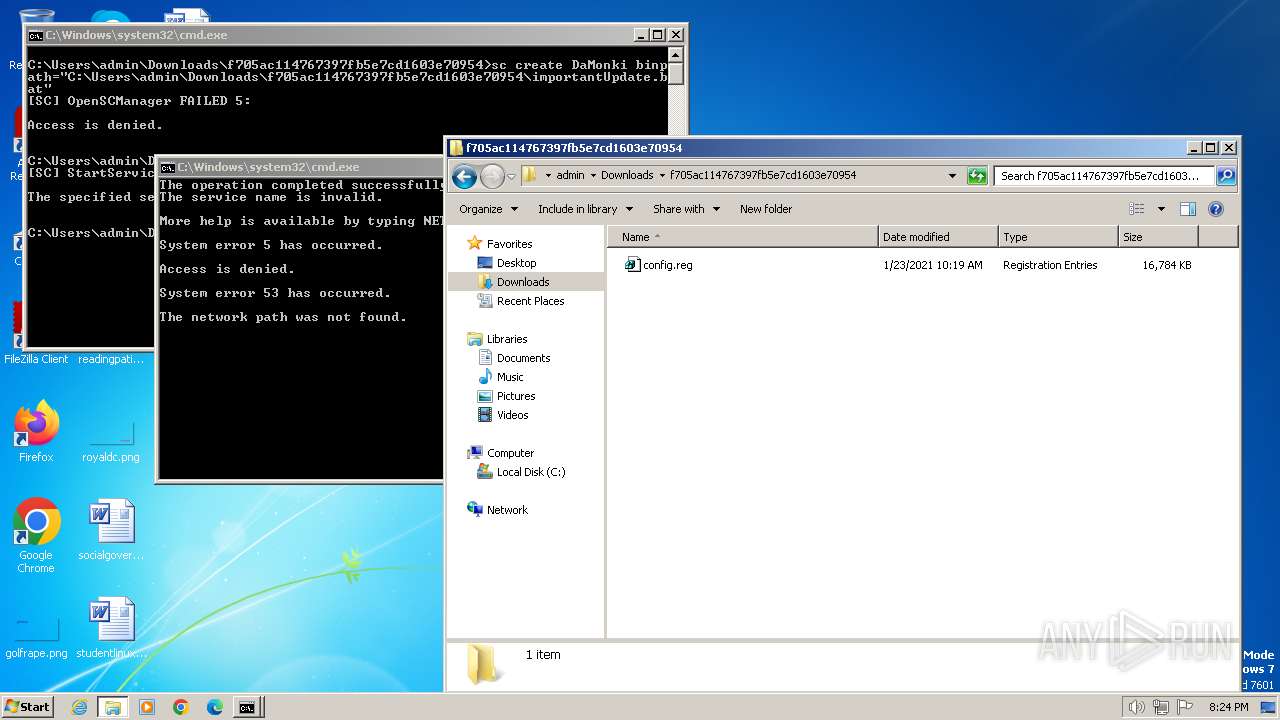
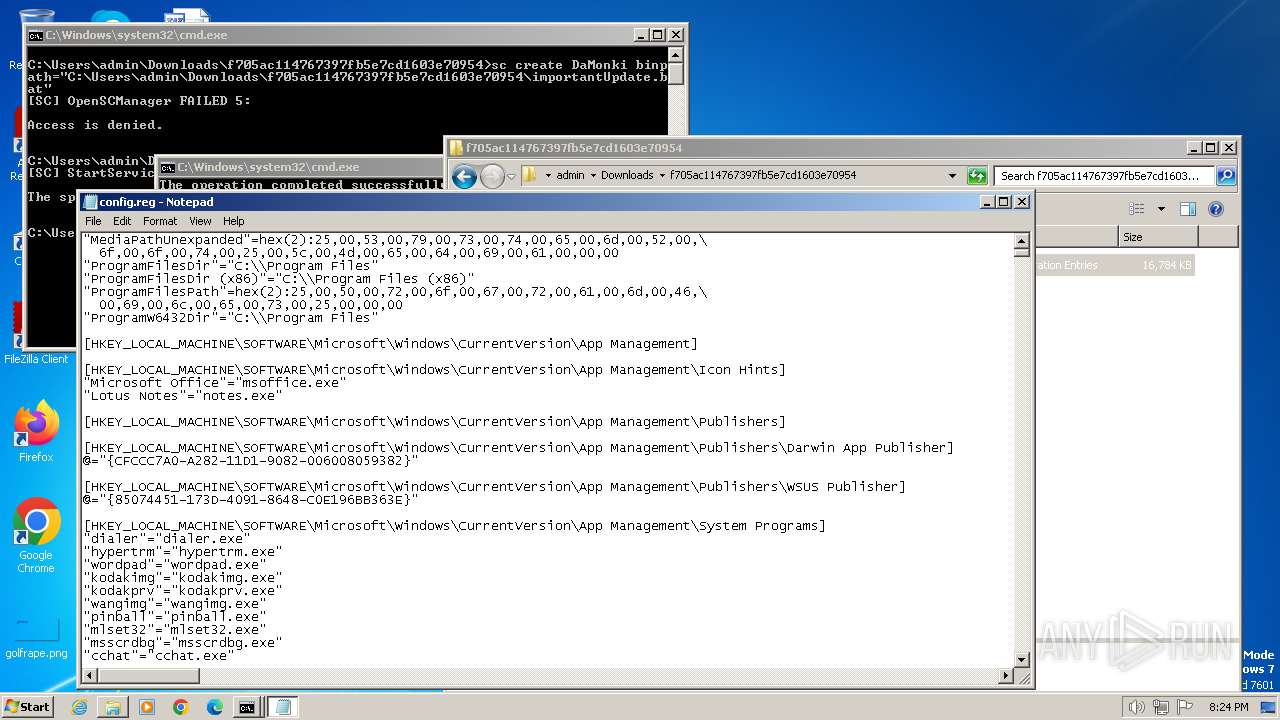
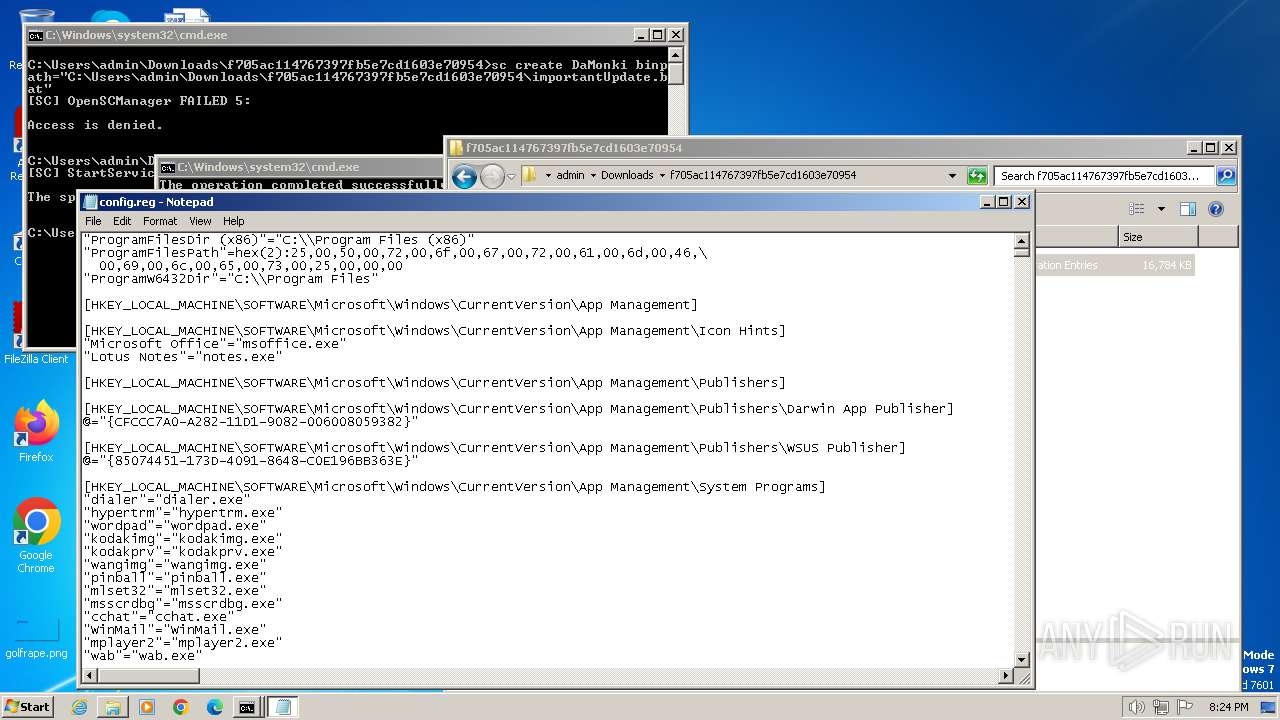
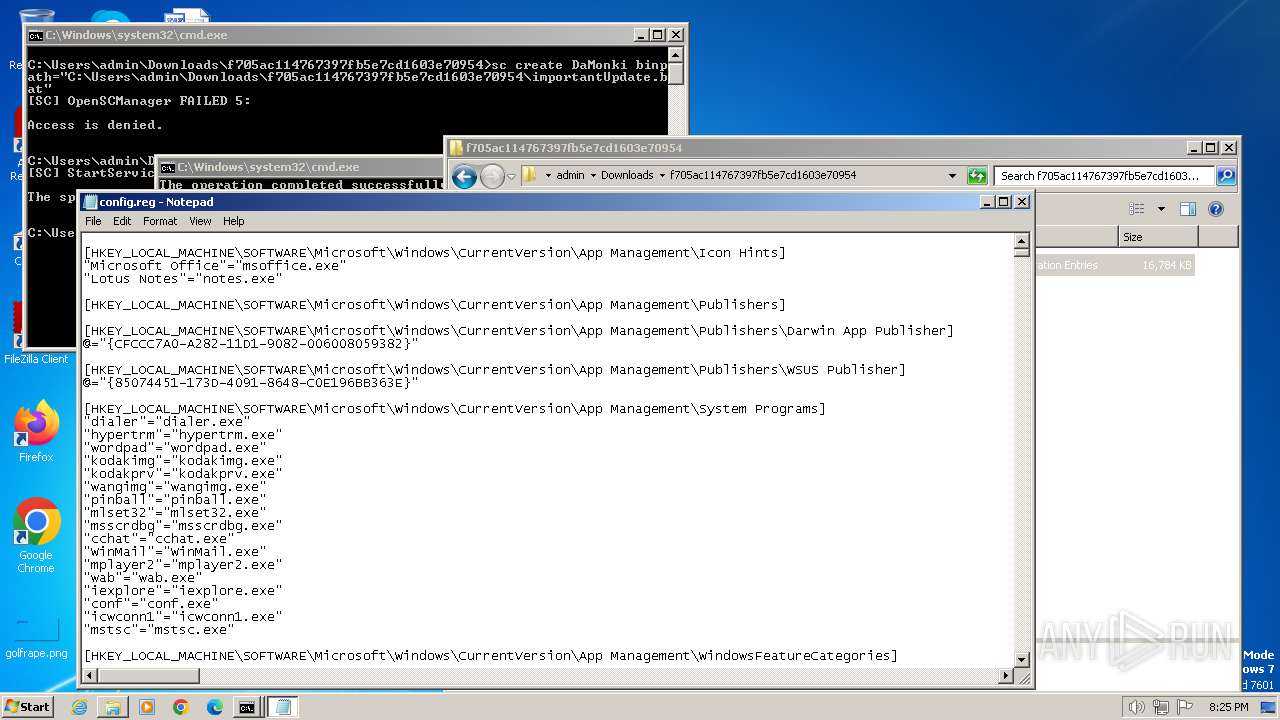
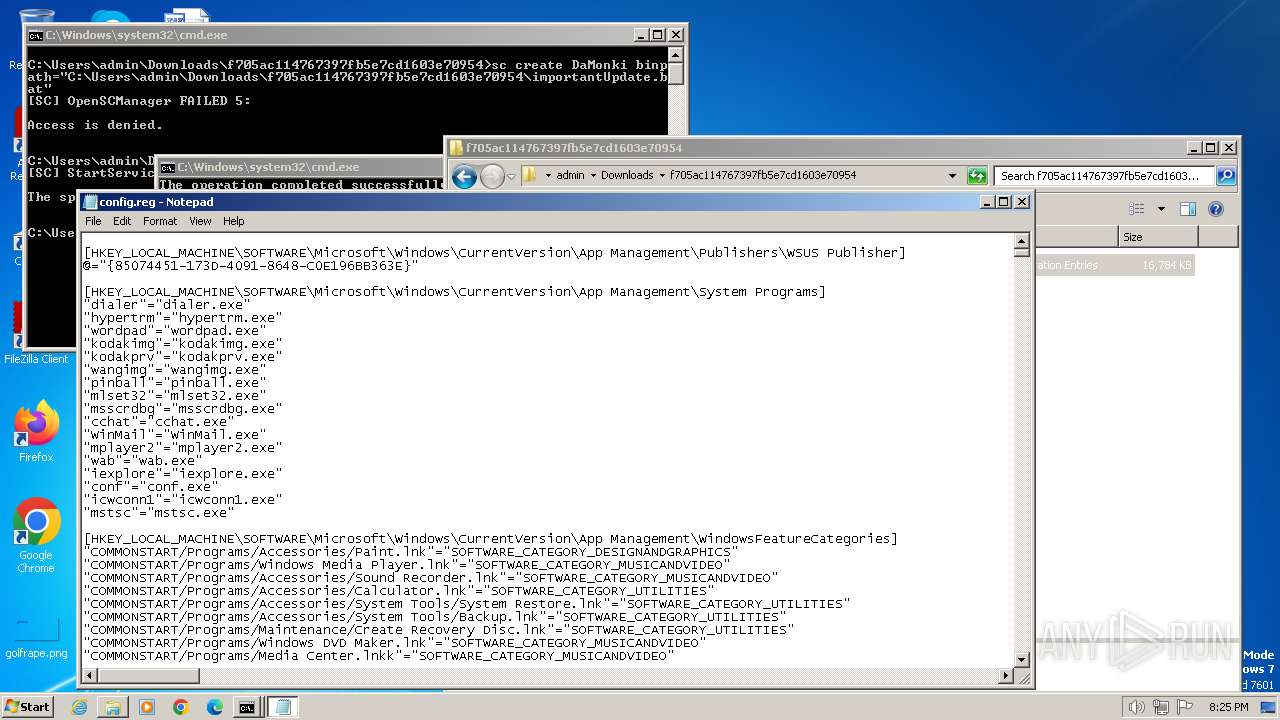
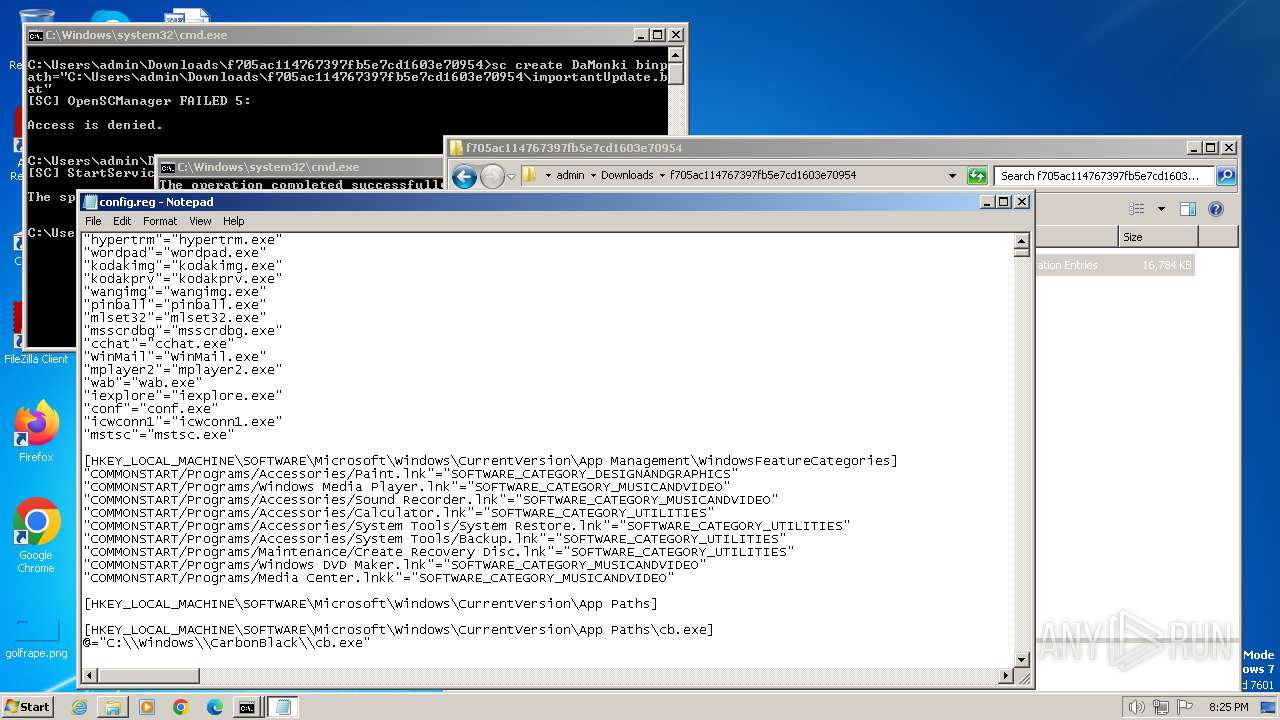
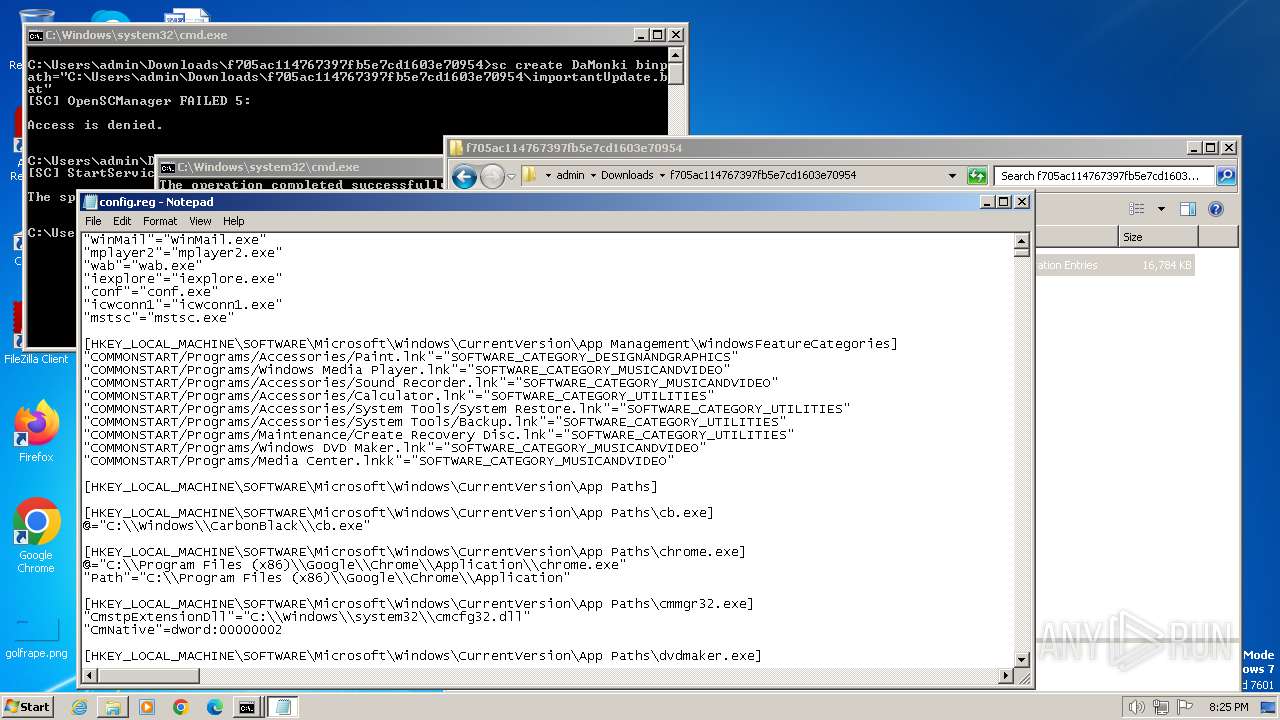
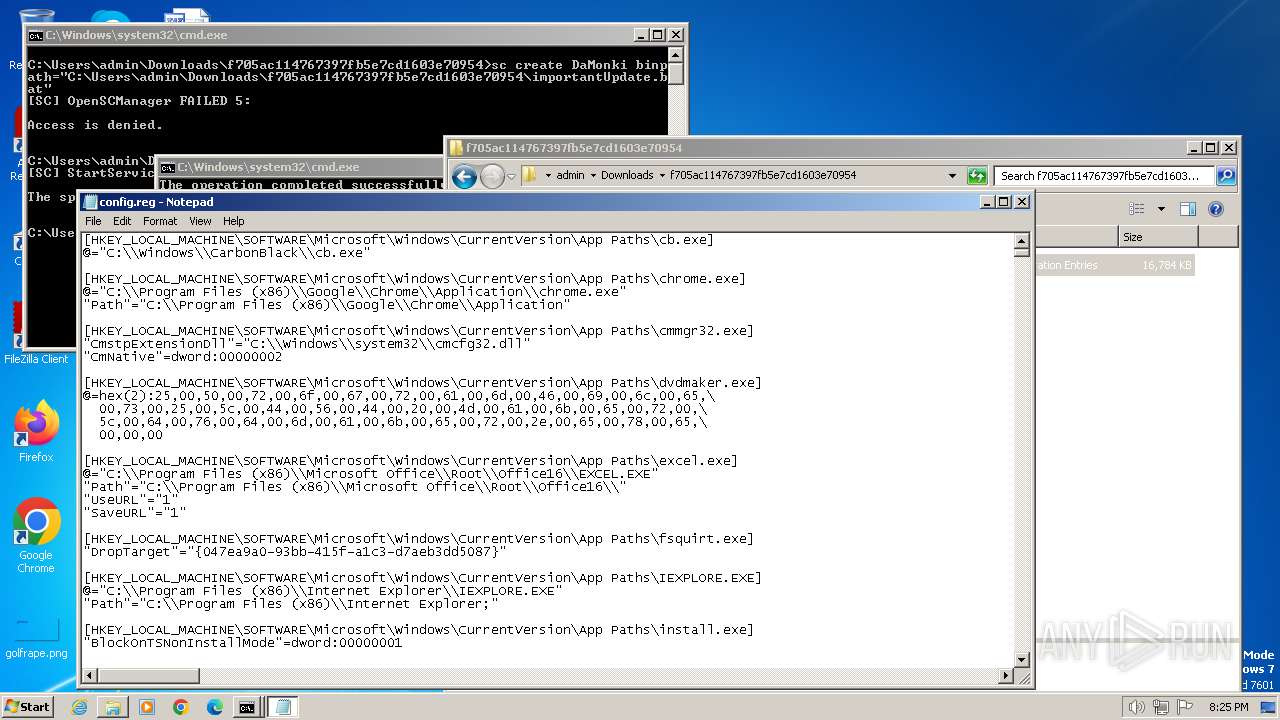
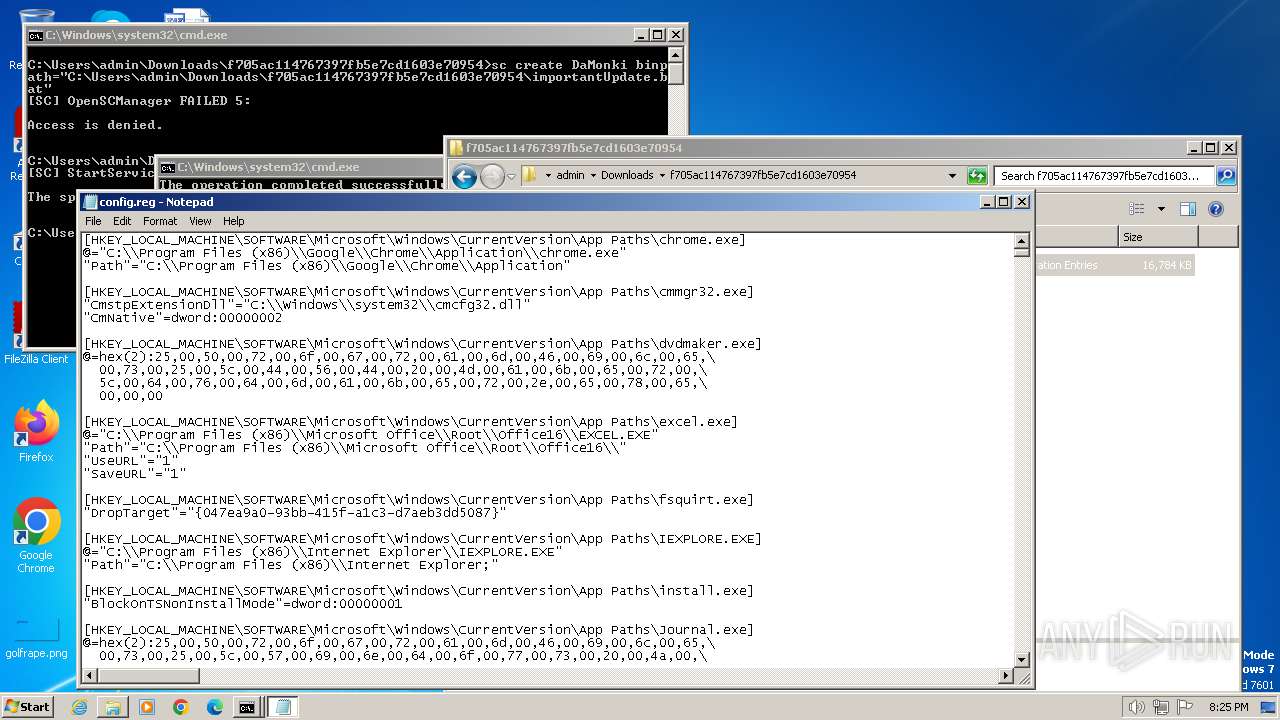
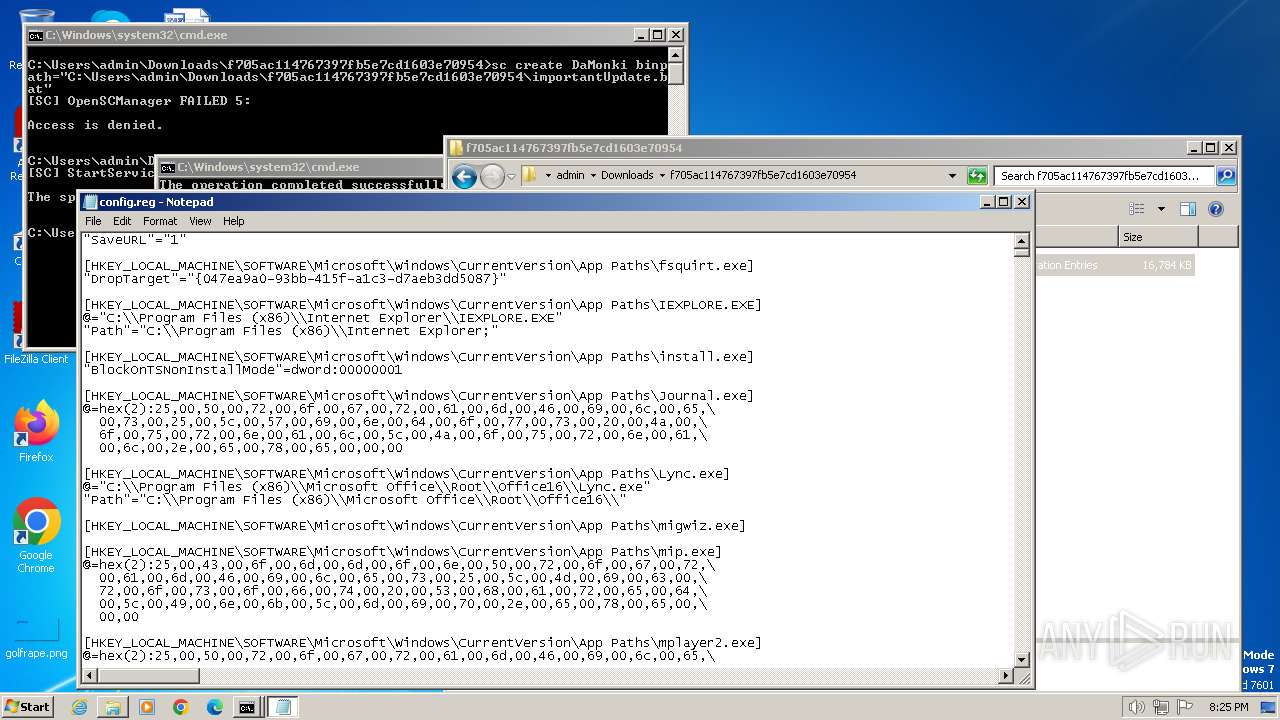
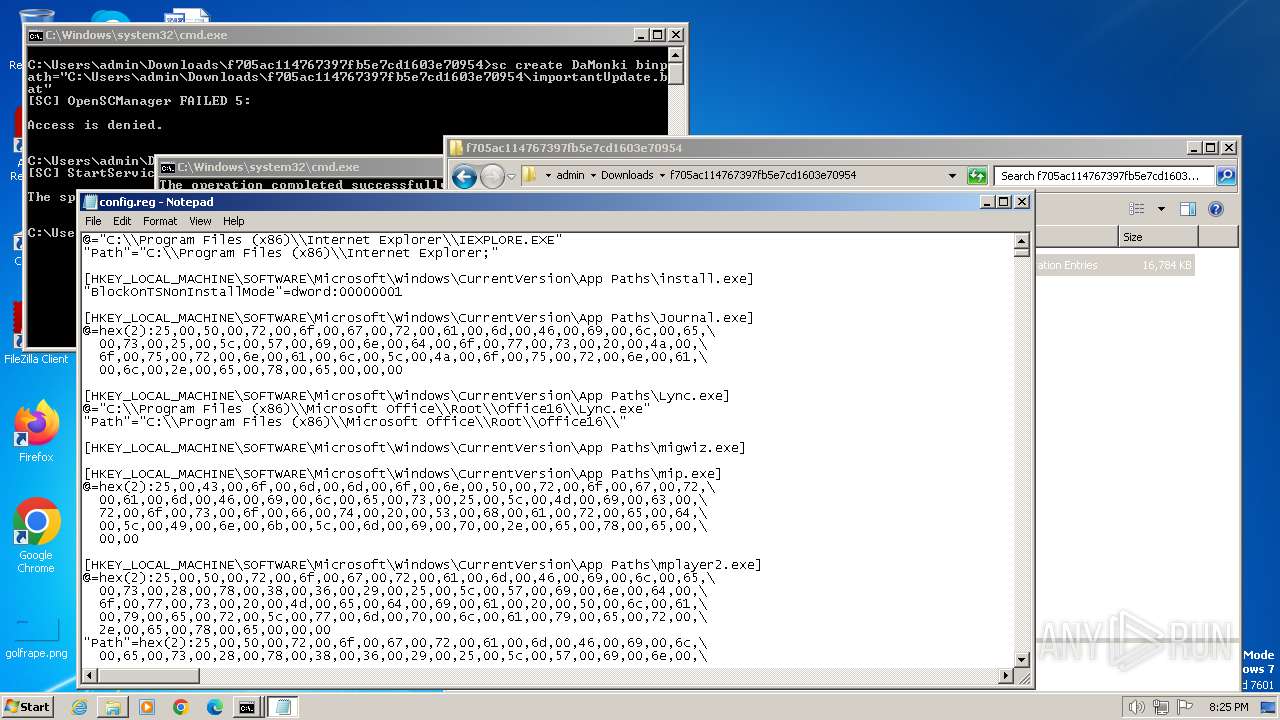
| ZipFileName: | config.reg |
Total processes
66
Monitored processes
23
Malicious processes
2
Suspicious processes
2
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
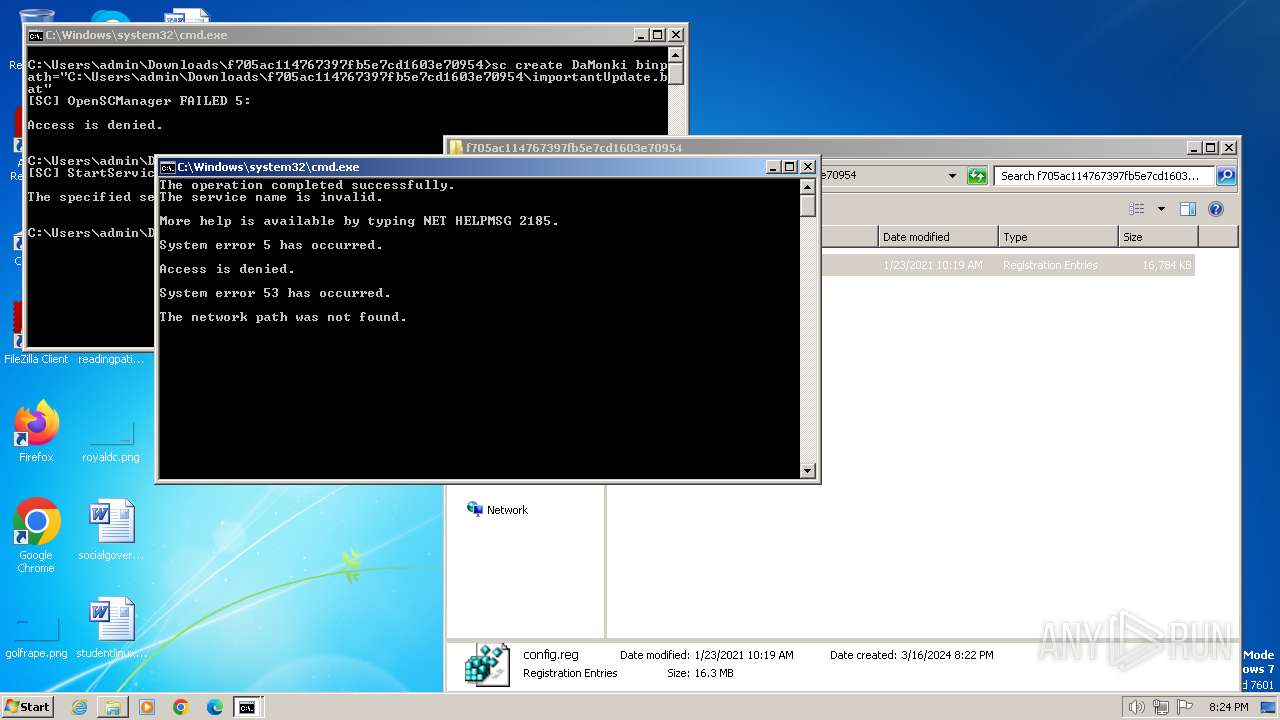
| 240 | C:\Windows\system32\cmd.exe /K service.bat | C:\Windows\System32\cmd.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 584 | net use Z: \\192.168.1.5\C$ | C:\Windows\System32\net.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Net Command Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 948 | net use Z: \\192.168.1.3\C$ | C:\Windows\System32\net.exe | cmd.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Net Command Exit code: 2 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
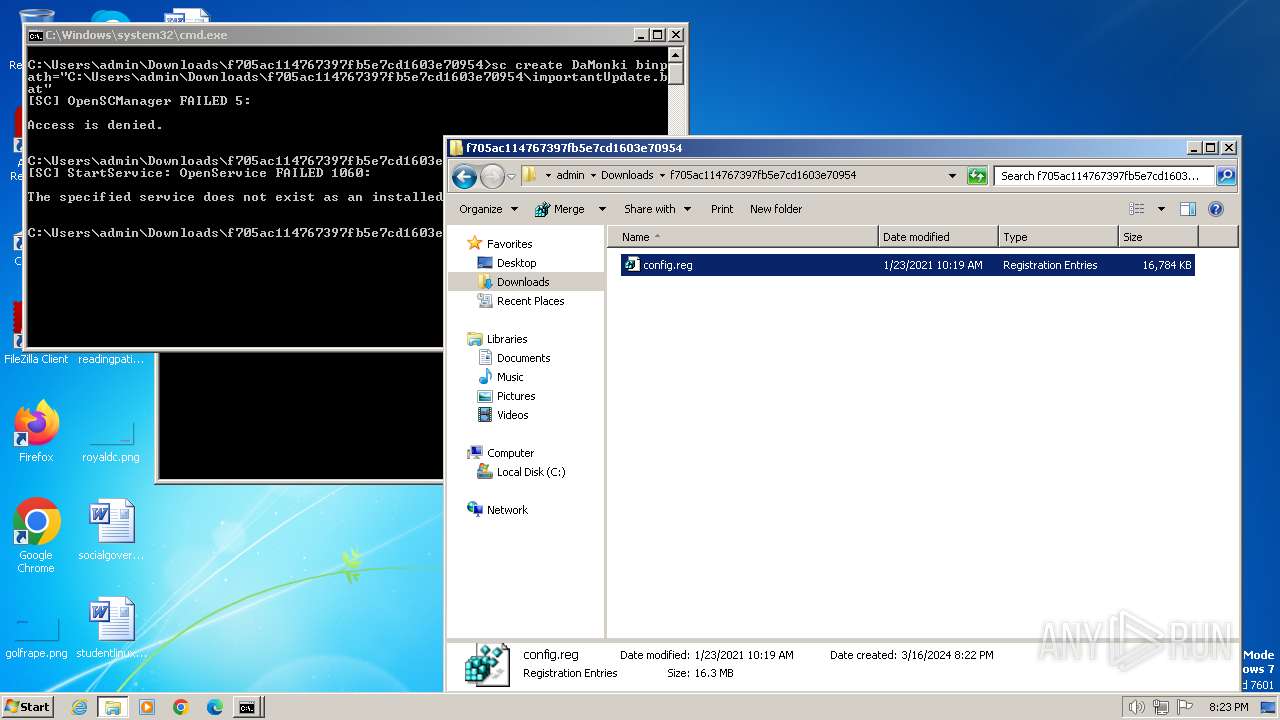
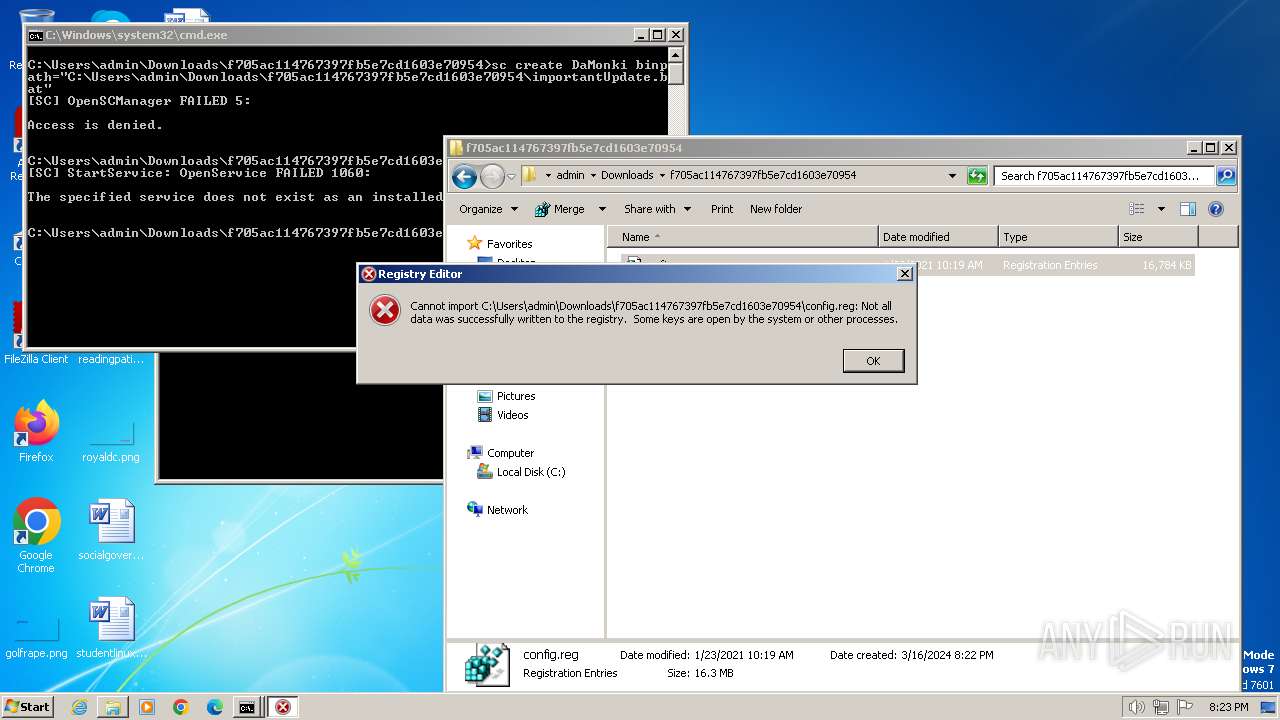
| 968 | "regedit.exe" "C:\Users\admin\Downloads\f705ac114767397fb5e7cd1603e70954\config.reg" | C:\Windows\regedit.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Registry Editor Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1236 | net stop "Windows Defender Service" | C:\Windows\System32\net.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Net Command Exit code: 2 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1308 | C:\Windows\system32\net1 stop "Windows Firewall" | C:\Windows\System32\net1.exe | — | net.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Net Command Exit code: 2 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 1352 | C:\Windows\system32\net1 stop "Windows Defender Service" | C:\Windows\System32\net1.exe | — | net.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Net Command Exit code: 2 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 1368 | net stop "Windows Firewall" | C:\Windows\System32\net.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Net Command Exit code: 2 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1504 | ipconfig /all | C:\Windows\System32\ipconfig.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: IP Configuration Utility Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1544 | net use Z: \\192.168.1.1\C$ | C:\Windows\System32\net.exe | cmd.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Net Command Exit code: 2 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
Total events
40 331
Read events
6 483
Write events
33 848
Delete events
0
Modification events
| (PID) Process: | (3500) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (3500) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (3500) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\182\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (3500) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\phacker.zip | |||
| (PID) Process: | (3500) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\Win7-KB3191566-x86.zip | |||
| (PID) Process: | (3500) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\curl-8.5.0_1-win32-mingw.zip | |||
| (PID) Process: | (3500) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Downloads\f705ac114767397fb5e7cd1603e70954.zip | |||
| (PID) Process: | (3500) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (3500) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (3500) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
Executable files
0
Suspicious files
0
Text files
2
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
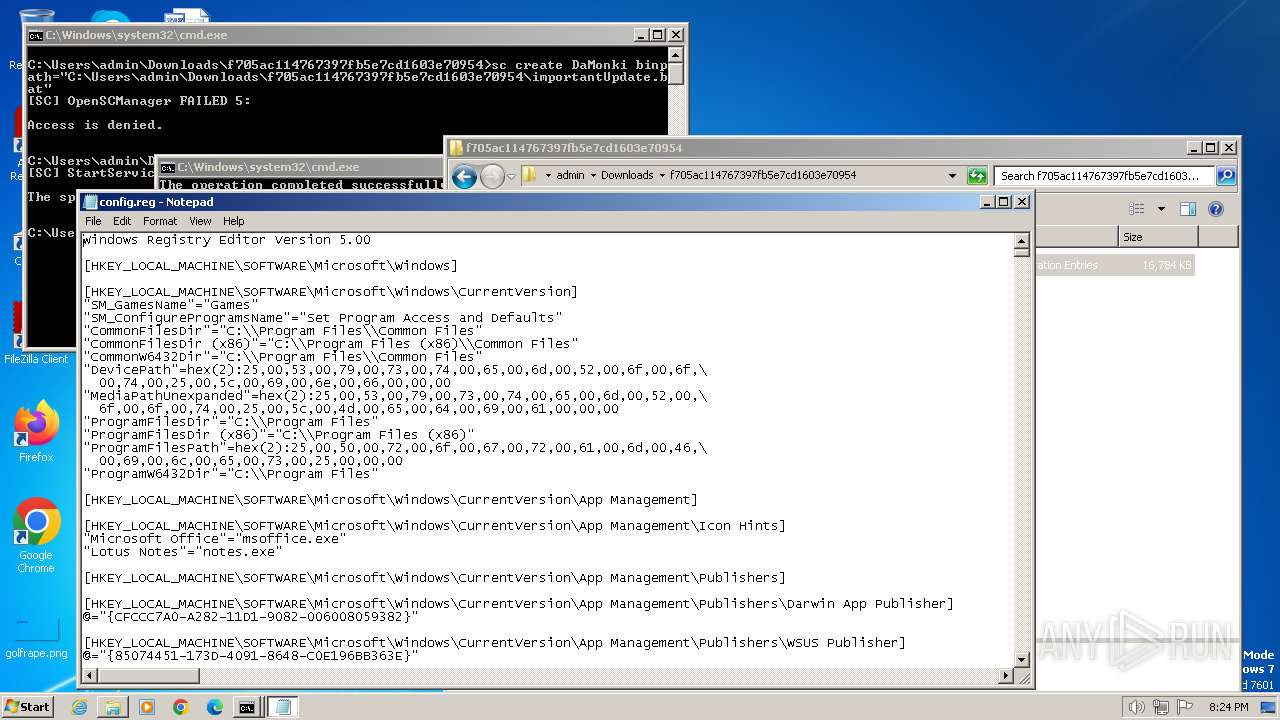
| 3500 | WinRAR.exe | C:\Users\admin\Downloads\f705ac114767397fb5e7cd1603e70954\config.reg | — | |
MD5:— | SHA256:— | |||
| 3500 | WinRAR.exe | C:\Users\admin\Downloads\f705ac114767397fb5e7cd1603e70954\importantUpdate.bat | text | |
MD5:BF16A6AEC517B7EC9C5D6EB3F4C60824 | SHA256:FC4DE26EDE0690DBC4EF4ED7FFCC28C086D5C8998F2CBE1E2C3C20516C7DA2DB | |||
| 1888 | cmd.exe | C:\Users\admin\Downloads\f705ac114767397fb5e7cd1603e70954\service.bat | text | |
MD5:4999CFE9520D021B369C1C3A9DFB5D13 | SHA256:6DF4EA95B5D6FE279A2FBCC7AD453D3B94EAC0F2103B4F9841FA94CFE489BAE1 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
39
DNS requests
0
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
— | — | 224.0.0.252:5355 | — | — | — | unknown |
1080 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |
— | — | 192.168.100.28:49207 | — | — | — | unknown |
— | — | 192.168.100.28:49208 | — | — | — | unknown |
— | — | 192.168.100.28:49209 | — | — | — | unknown |
— | — | 192.168.100.28:49211 | — | — | — | unknown |
— | — | 192.168.100.28:49212 | — | — | — | unknown |
— | — | 192.168.100.28:49213 | — | — | — | unknown |