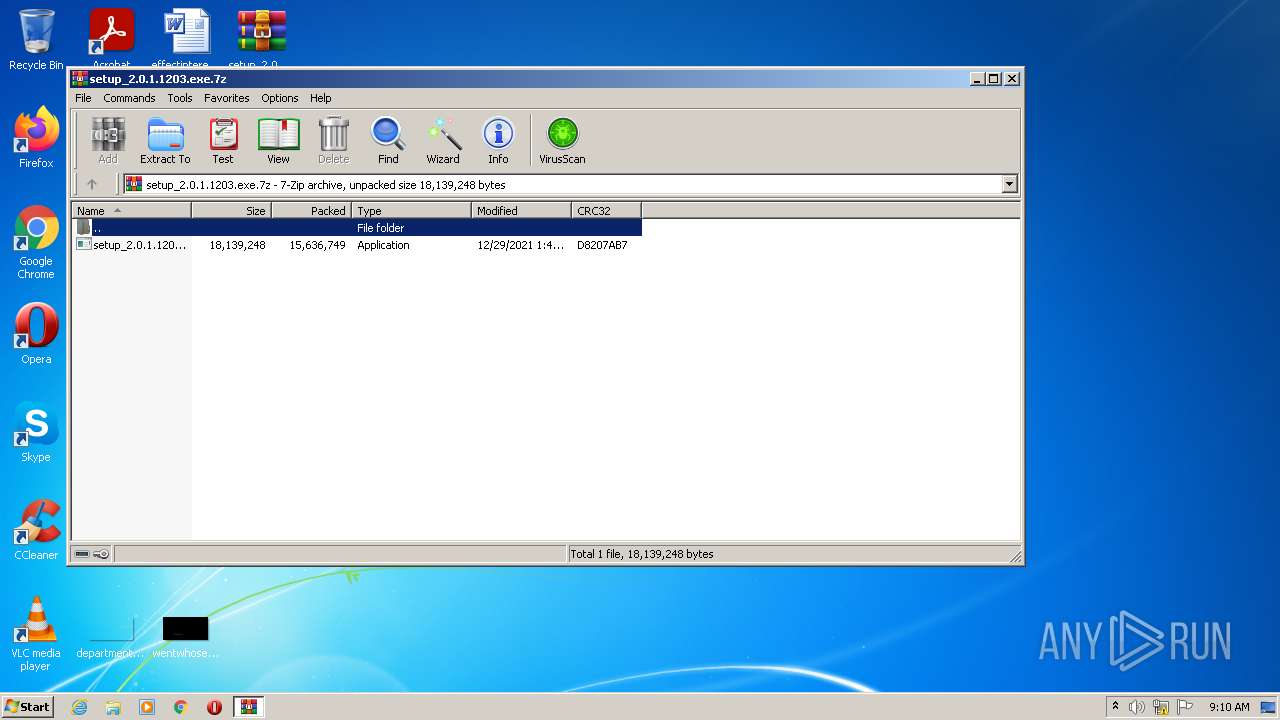
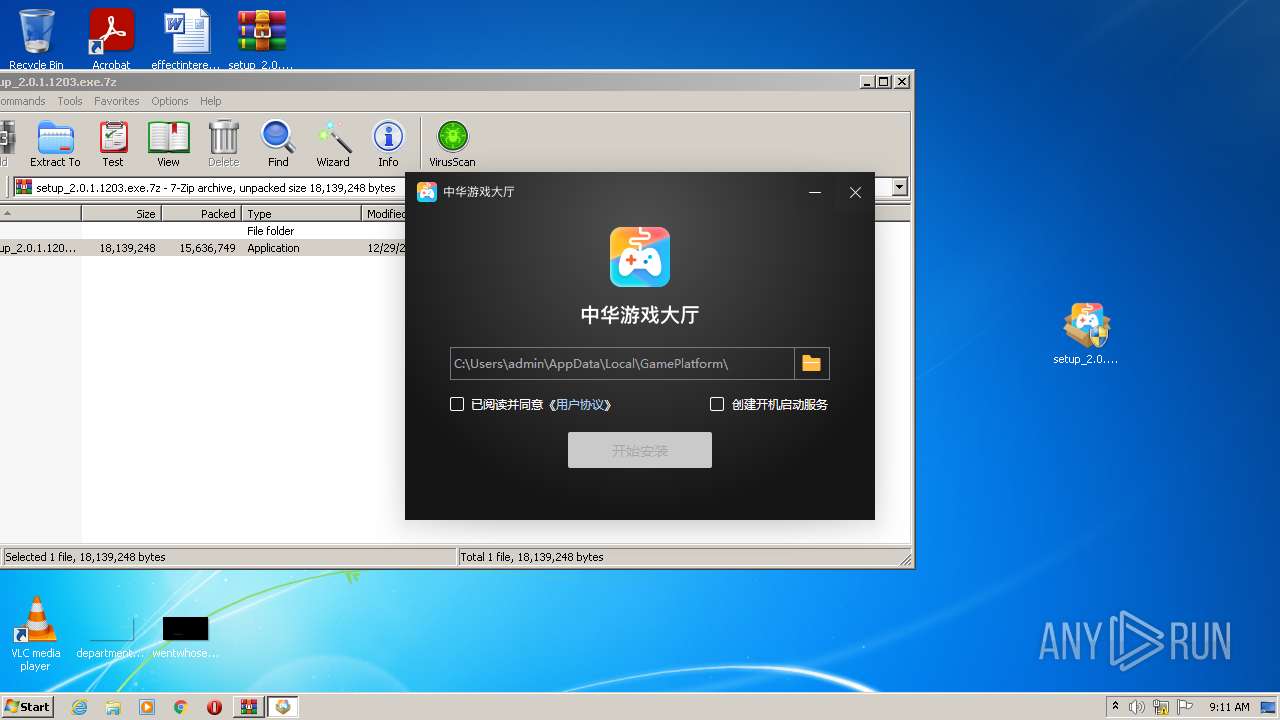
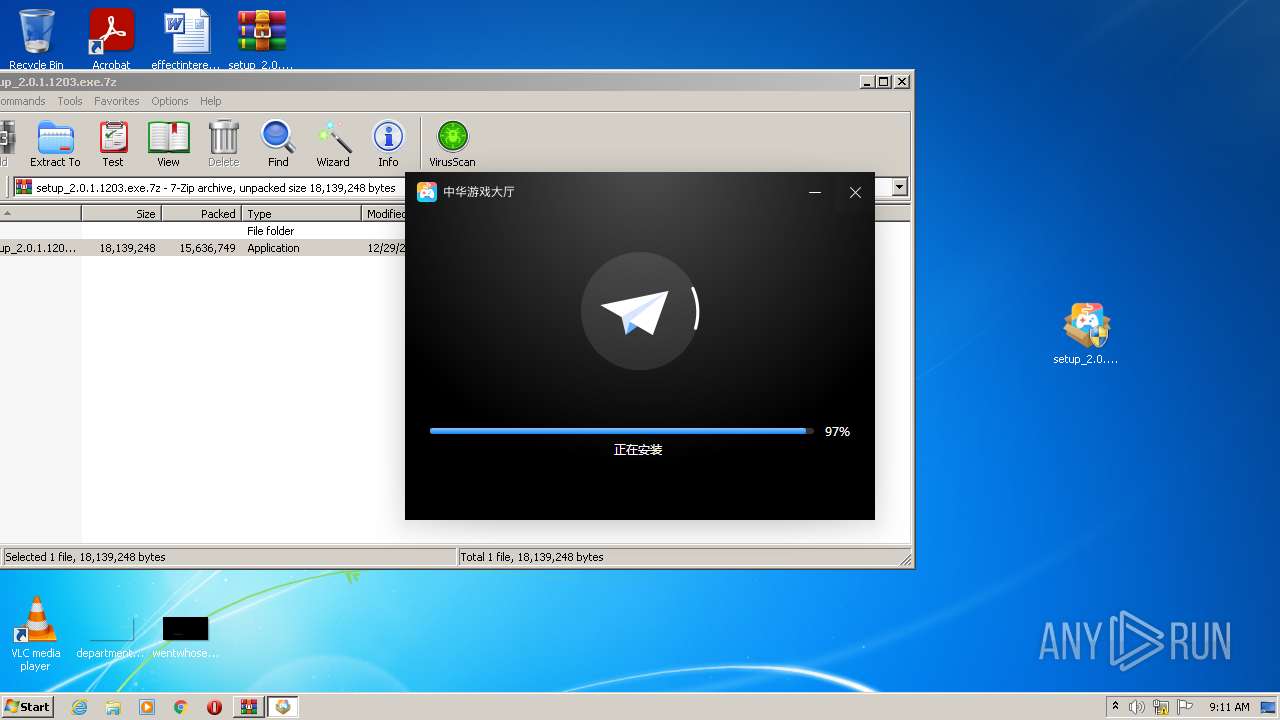
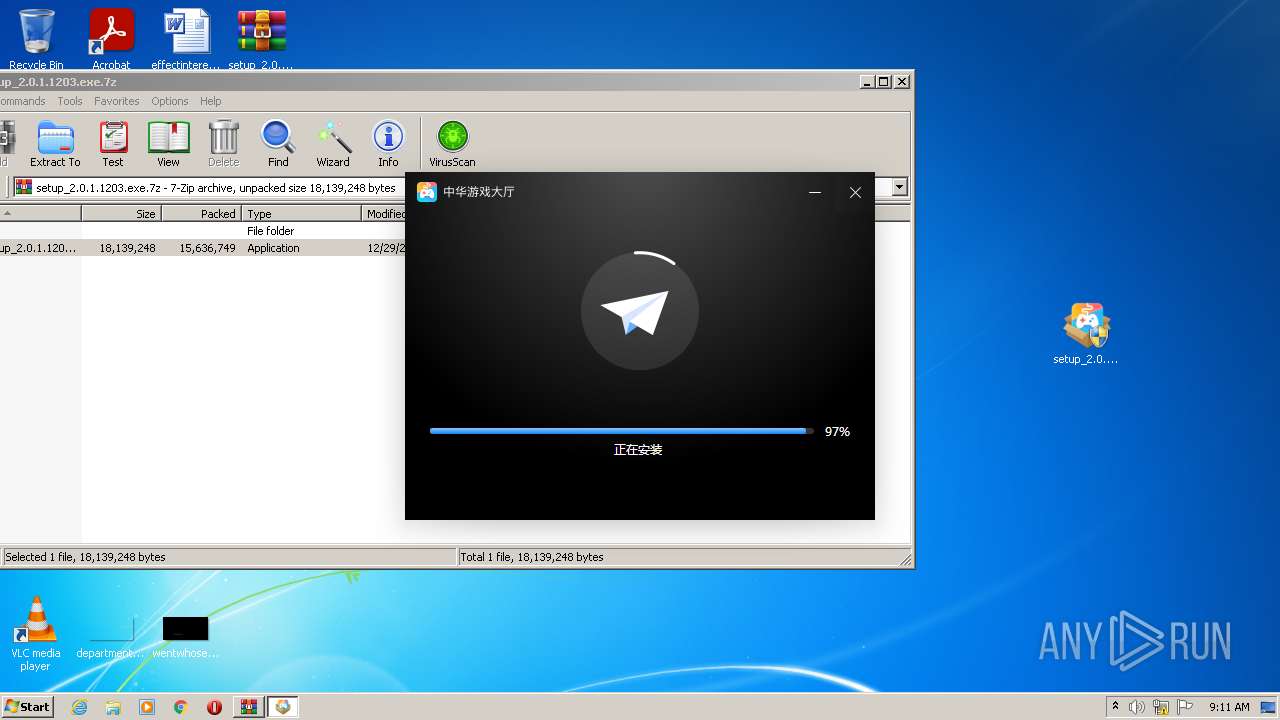
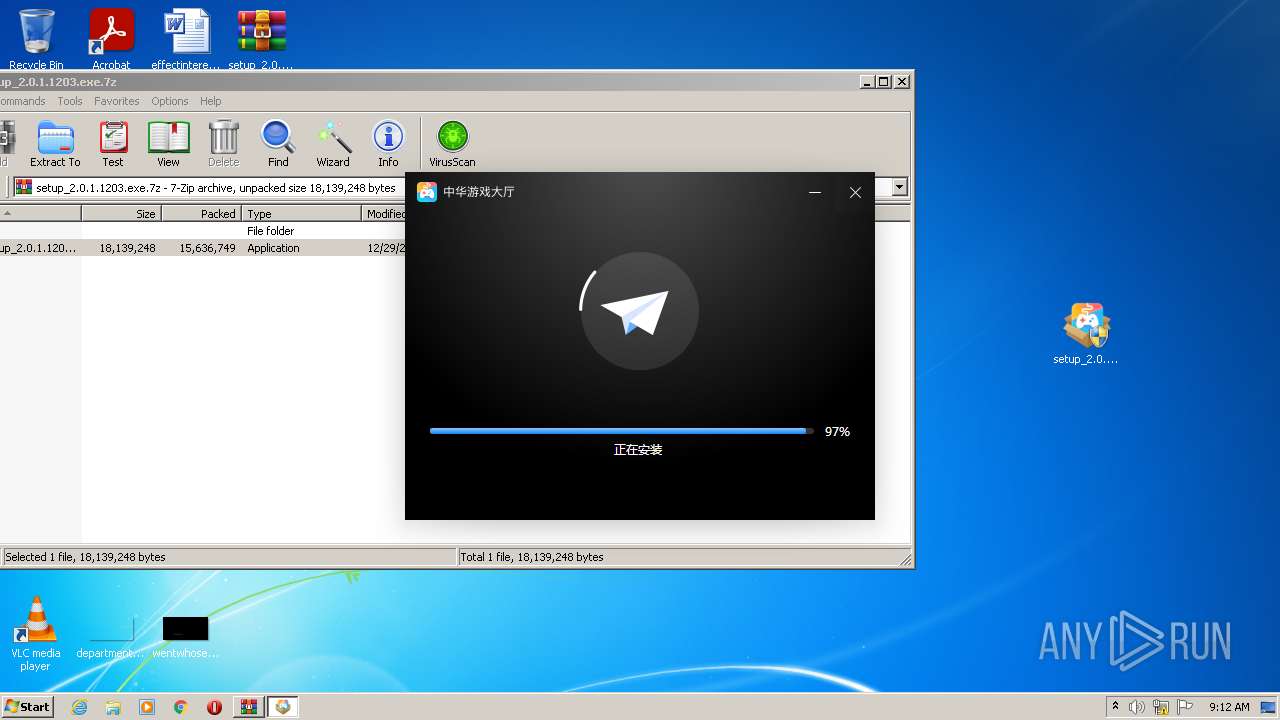
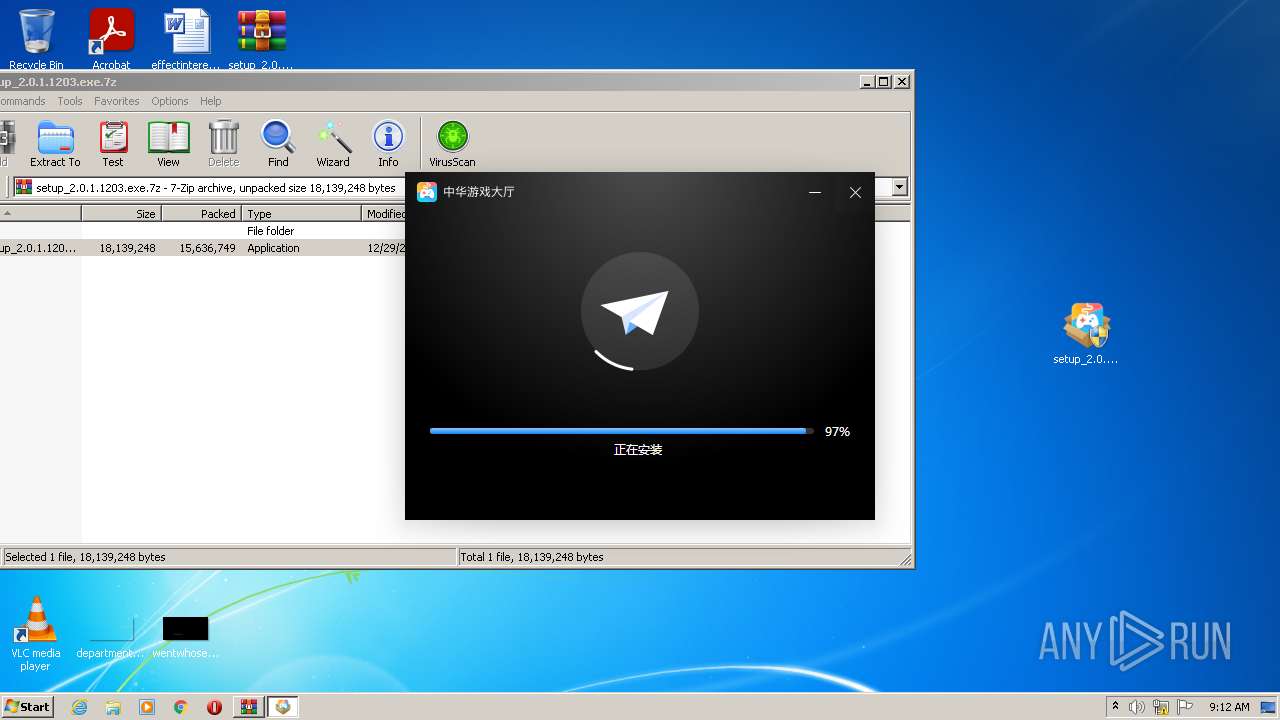
| File name: | setup_2.0.1.1203.exe.7z |
| Full analysis: | https://app.any.run/tasks/c11dd7be-c913-47c4-98c9-846d0730b766 |
| Verdict: | Malicious activity |
| Analysis date: | December 30, 2021, 09:09:55 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/x-7z-compressed |
| File info: | 7-zip archive data, version 0.4 |
| MD5: | 0BFF4585420698F11AA7697F9F86C721 |
| SHA1: | A99934246760DEFBBDB01EE707081587E3DF4F78 |
| SHA256: | 49FD642B48F56EE8989481FAA97CF88AD543881904989183B5ED57F64DC1329A |
| SSDEEP: | 196608:rYBWyKPvAJJ7to05zVjPgFF1bEbi2ccdP3E1ms3pskPU3n0J3YWvZ78s7UZU2YZU:rAKH05zVTg1bATbFnYe2tx2myrj |
MALICIOUS
Application was dropped or rewritten from another process
- setup_2.0.1.1203.exe (PID: 2476)
- Margot.exe (PID: 2072)
- setup_2.0.1.1203.exe (PID: 860)
Loads dropped or rewritten executable
- Margot.exe (PID: 2072)
SUSPICIOUS
Reads the computer name
- WinRAR.exe (PID: 3448)
- setup_2.0.1.1203.exe (PID: 2476)
- Margot.exe (PID: 2072)
Checks supported languages
- setup_2.0.1.1203.exe (PID: 2476)
- Margot.exe (PID: 2072)
- WinRAR.exe (PID: 3448)
Drops a file with a compile date too recent
- setup_2.0.1.1203.exe (PID: 2476)
- WinRAR.exe (PID: 3448)
Executable content was dropped or overwritten
- setup_2.0.1.1203.exe (PID: 2476)
- WinRAR.exe (PID: 3448)
Drops a file that was compiled in debug mode
- setup_2.0.1.1203.exe (PID: 2476)
Creates files in the user directory
- Margot.exe (PID: 2072)
INFO
Manual execution by user
- setup_2.0.1.1203.exe (PID: 860)
- setup_2.0.1.1203.exe (PID: 2476)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .7z | | | 7-Zip compressed archive (v0.4) (57.1) |
|---|---|---|
| .7z | | | 7-Zip compressed archive (gen) (42.8) |
Total processes
43
Monitored processes
4
Malicious processes
2
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 860 | "C:\Users\admin\Desktop\setup_2.0.1.1203.exe" | C:\Users\admin\Desktop\setup_2.0.1.1203.exe | — | Explorer.EXE | |||||||||||
User: admin Company: ???????????? Integrity Level: MEDIUM Description: gphall.exe Exit code: 3221226540 Version: 2.0.1.1203 Modules
| |||||||||||||||
| 2072 | "C:\Users\admin\AppData\Local\GamePlatform\Margot.exe" -fvzikmmwhwbwgolkdnjpxl=Ibvd3HBqkG+xeMqBMQLn4OLNyOoHtXmVGxS/cx96cZ2fP5IX16cbJlBn29vybCTjWBYsErPY6dEX4YfGS3NhwutvkLF3rMNtvLOF6azLvkg= | C:\Users\admin\AppData\Local\GamePlatform\Margot.exe | setup_2.0.1.1203.exe | ||||||||||||
User: admin Company: ???????????? Integrity Level: HIGH Description: Margot.exe Exit code: 0 Version: 2.0.1.1203 Modules
| |||||||||||||||
| 2476 | "C:\Users\admin\Desktop\setup_2.0.1.1203.exe" | C:\Users\admin\Desktop\setup_2.0.1.1203.exe | Explorer.EXE | ||||||||||||
User: admin Company: ???????????? Integrity Level: HIGH Description: gphall.exe Exit code: 0 Version: 2.0.1.1203 Modules
| |||||||||||||||
| 3448 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\Desktop\setup_2.0.1.1203.exe.7z" | C:\Program Files\WinRAR\WinRAR.exe | Explorer.EXE | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.91.0 Modules
| |||||||||||||||
Total events
1 849
Read events
1 820
Write events
29
Delete events
0
Modification events
| (PID) Process: | (3448) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (3448) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (3448) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\16C\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (3448) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\virtio_ivshmem_master_build.zip | |||
| (PID) Process: | (3448) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\Win7-KB3191566-x86.zip | |||
| (PID) Process: | (3448) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Desktop\setup_2.0.1.1203.exe.7z | |||
| (PID) Process: | (3448) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (3448) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (3448) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (3448) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
Executable files
25
Suspicious files
0
Text files
1
Unknown types
1
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2476 | setup_2.0.1.1203.exe | C:\Users\admin\AppData\Local\GamePlatform\node.dll | — | |
MD5:— | SHA256:— | |||
| 3448 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa3448.10241\setup_2.0.1.1203.exe | executable | |
MD5:— | SHA256:— | |||
| 2476 | setup_2.0.1.1203.exe | C:\Users\admin\AppData\Local\GamePlatform\GameFnrt.fad | executable | |
MD5:— | SHA256:— | |||
| 2476 | setup_2.0.1.1203.exe | C:\Users\admin\AppData\Local\GamePlatform\Dexter64.dll | executable | |
MD5:— | SHA256:— | |||
| 2476 | setup_2.0.1.1203.exe | C:\Users\admin\AppData\Local\GamePlatform\GamePrtfr.fds | executable | |
MD5:— | SHA256:— | |||
| 2476 | setup_2.0.1.1203.exe | C:\Users\admin\AppData\Local\GamePlatform\GamePjkt.fds | executable | |
MD5:— | SHA256:— | |||
| 2476 | setup_2.0.1.1203.exe | C:\Users\admin\AppData\Local\GamePlatform\Alison.dll | executable | |
MD5:— | SHA256:— | |||
| 2476 | setup_2.0.1.1203.exe | C:\Users\admin\AppData\Local\GamePlatform\Daniel.dll | executable | |
MD5:— | SHA256:— | |||
| 2476 | setup_2.0.1.1203.exe | C:\Users\admin\AppData\Local\GamePlatform\gphall.exe | executable | |
MD5:— | SHA256:— | |||
| 2476 | setup_2.0.1.1203.exe | C:\Users\admin\AppData\Local\GamePlatform\cef\hview.exe | executable | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
5
TCP/UDP connections
5
DNS requests
3
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
2072 | Margot.exe | GET | — | 47.100.208.145:80 | http://apin.wan.china.com/e1lu2gm8/l.php?d=BzdkSg7vZykIkfFf6Y2l9%2FXSFrMc0OhYJ3chZj30RQAgQ5UEiJuFIg0Wnk3rjxFE&_=1640855493 | CN | — | — | unknown |
2476 | setup_2.0.1.1203.exe | GET | 200 | 163.171.128.148:80 | http://dlln.wan.china.com/e1lu2gm8/cp/p/?p=Yq2GDTE0OkrfR%2BePmGPogSqaAjnUv6VJXokI4Pd9lrJgmnR%2FQzcCQBbC4u7TLWYj&_=1640855484 | US | text | 128 b | malicious |
2072 | Margot.exe | GET | 200 | 163.171.128.148:80 | http://dlln.wan.china.com/e1lu2gm8/cp/l/?p=n2ci925xSvDqb%2Bkx2Hpzu%2Bz3YX6tQRJ634gMoS3y59kboBNLXkMyV3tt%2FvOFyOFi&_=1640855485 | US | text | 108 b | malicious |
2072 | Margot.exe | GET | 200 | 163.171.128.148:80 | http://dlln.wan.china.com/microtime/?&_=1640855489 | US | binary | 37 b | malicious |
2072 | Margot.exe | GET | 200 | 163.171.128.148:80 | http://dlln.wan.china.com/e1lu2gm8/cp/i/?p=WXyAolBc%2BtRd0UPUdyDUhRaAZXKXTsRYSrsWJuDJUyXWByn%2F2Rsz4yHR%2BgAIQazsD2KB1WC5sFcBsgCoWL2pog%3D%3D&_=1640855485 | US | text | 172 b | malicious |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
2072 | Margot.exe | 163.171.128.148:80 | dlln.wan.china.com | — | US | malicious |
2476 | setup_2.0.1.1203.exe | 163.171.128.148:80 | dlln.wan.china.com | — | US | malicious |
2072 | Margot.exe | 47.100.208.145:80 | apin.wan.china.com | Hangzhou Alibaba Advertising Co.,Ltd. | CN | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
dlln.wan.china.com |
| malicious |
apin.wan.china.com |
| unknown |