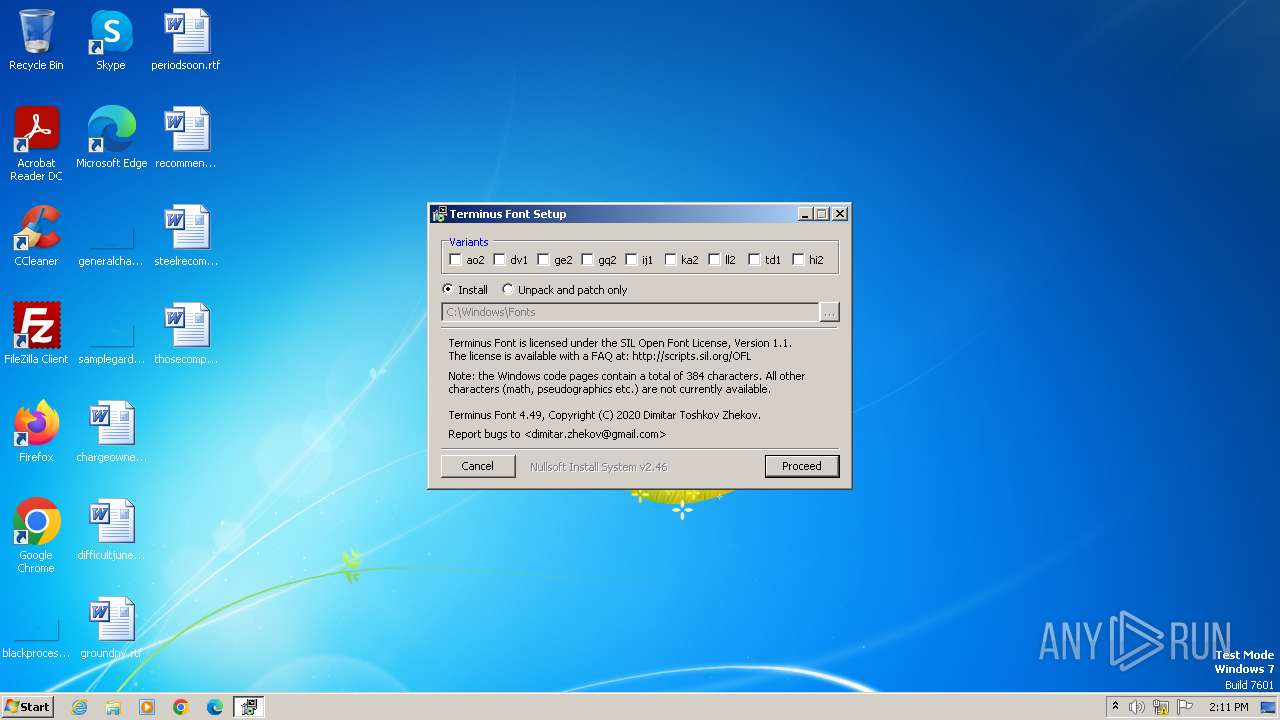
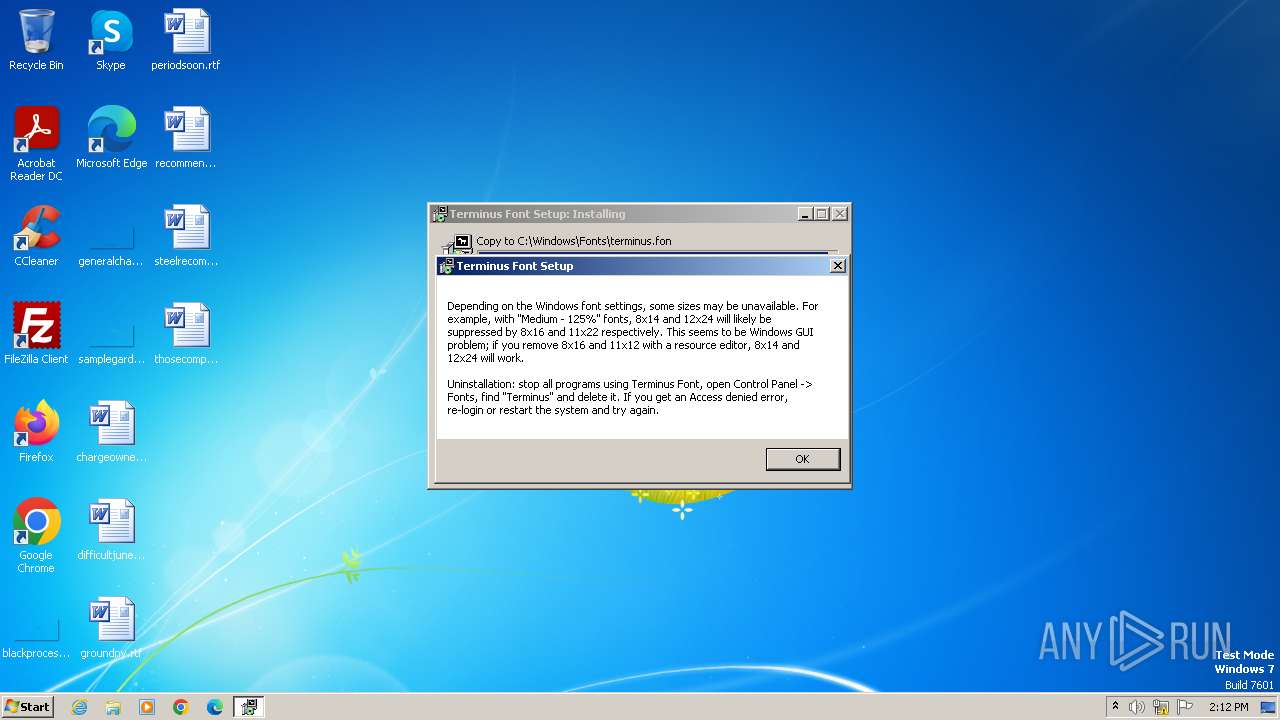
| File name: | terminus-font-4.49.exe |
| Full analysis: | https://app.any.run/tasks/bf7ce144-5f83-44d6-a354-dbecec810a1d |
| Verdict: | Malicious activity |
| Analysis date: | May 03, 2024, 13:11:45 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows, Nullsoft Installer self-extracting archive |
| MD5: | 85F3C4F0B500CCF8399EB763DB8FCA9E |
| SHA1: | CFFD90F435399ABFE9887A6F35C4E09BC30A18F5 |
| SHA256: | 49C6AA7B40744111953321332C27598193969FA1FA9666013C44FD02268CFFD3 |
| SSDEEP: | 12288:bWePQ2XzXG0nprMqKVnIONN5W+90c9TTONdhTpT0mve:aePrG0nprMquIONN56c9TTONdhTpTE |
MALICIOUS
Drops the executable file immediately after the start
- terminus-font-4.49.exe (PID: 4072)
SUSPICIOUS
Malware-specific behavior (creating "System.dll" in Temp)
- terminus-font-4.49.exe (PID: 4072)
The process creates files with name similar to system file names
- terminus-font-4.49.exe (PID: 4072)
Executable content was dropped or overwritten
- terminus-font-4.49.exe (PID: 4072)
INFO
Checks supported languages
- fcpw.exe (PID: 2104)
- fcpw.exe (PID: 1116)
- fcpw.exe (PID: 1136)
- terminus-font-4.49.exe (PID: 4072)
- fcpw.exe (PID: 820)
- fcpw.exe (PID: 112)
- fcpw.exe (PID: 2028)
- fcpw.exe (PID: 2036)
- fcpw.exe (PID: 116)
- fcpw.exe (PID: 328)
Reads the computer name
- terminus-font-4.49.exe (PID: 4072)
Create files in a temporary directory
- terminus-font-4.49.exe (PID: 4072)
Reads the machine GUID from the registry
- terminus-font-4.49.exe (PID: 4072)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | NSIS - Nullsoft Scriptable Install System (94.8) |
|---|---|---|
| .exe | | | Win32 Executable MS Visual C++ (generic) (3.4) |
| .dll | | | Win32 Dynamic Link Library (generic) (0.7) |
| .exe | | | Win32 Executable (generic) (0.5) |
| .exe | | | Generic Win/DOS Executable (0.2) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2009:12:05 22:50:52+00:00 |
| ImageFileCharacteristics: | No relocs, Executable, No line numbers, No symbols, 32-bit |
| PEType: | PE32 |
| LinkerVersion: | 6 |
| CodeSize: | 24064 |
| InitializedDataSize: | 164864 |
| UninitializedDataSize: | 1024 |
| EntryPoint: | 0x30fa |
| OSVersion: | 4 |
| ImageVersion: | 6 |
| SubsystemVersion: | 4 |
| Subsystem: | Windows GUI |
Total processes
45
Monitored processes
11
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 112 | "C:\Users\admin\AppData\Local\Temp\nsm3D1B.tmp\fcpw.exe" 4100 terminus.fon hi2.txt | C:\Users\admin\AppData\Local\Temp\nsm3D1B.tmp\fcpw.exe | — | terminus-font-4.49.exe | |||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
| 116 | "C:\Users\admin\AppData\Local\Temp\nsm3D1B.tmp\fcpw.exe" 4100 terminus.fon ll2.txt | C:\Users\admin\AppData\Local\Temp\nsm3D1B.tmp\fcpw.exe | — | terminus-font-4.49.exe | |||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
| 328 | "C:\Users\admin\AppData\Local\Temp\nsm3D1B.tmp\fcpw.exe" 4100 terminus.fon td1.txt | C:\Users\admin\AppData\Local\Temp\nsm3D1B.tmp\fcpw.exe | — | terminus-font-4.49.exe | |||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
| 820 | "C:\Users\admin\AppData\Local\Temp\nsm3D1B.tmp\fcpw.exe" 4100 terminus.fon ge2.txt | C:\Users\admin\AppData\Local\Temp\nsm3D1B.tmp\fcpw.exe | — | terminus-font-4.49.exe | |||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
| 1116 | "C:\Users\admin\AppData\Local\Temp\nsm3D1B.tmp\fcpw.exe" 4100 terminus.fon gq2.txt | C:\Users\admin\AppData\Local\Temp\nsm3D1B.tmp\fcpw.exe | — | terminus-font-4.49.exe | |||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
| 1136 | "C:\Users\admin\AppData\Local\Temp\nsm3D1B.tmp\fcpw.exe" 4100 terminus.fon ij1.txt | C:\Users\admin\AppData\Local\Temp\nsm3D1B.tmp\fcpw.exe | — | terminus-font-4.49.exe | |||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
| 2028 | "C:\Users\admin\AppData\Local\Temp\nsm3D1B.tmp\fcpw.exe" 4100 terminus.fon hi2-ka2.txt | C:\Users\admin\AppData\Local\Temp\nsm3D1B.tmp\fcpw.exe | — | terminus-font-4.49.exe | |||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
| 2036 | "C:\Users\admin\AppData\Local\Temp\nsm3D1B.tmp\fcpw.exe" 4100 terminus.fon hi2-dv1.txt | C:\Users\admin\AppData\Local\Temp\nsm3D1B.tmp\fcpw.exe | — | terminus-font-4.49.exe | |||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
| 2104 | "C:\Users\admin\AppData\Local\Temp\nsm3D1B.tmp\fcpw.exe" 4100 terminus.fon ao2.txt | C:\Users\admin\AppData\Local\Temp\nsm3D1B.tmp\fcpw.exe | — | terminus-font-4.49.exe | |||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
| 3968 | "C:\Users\admin\AppData\Local\Temp\terminus-font-4.49.exe" | C:\Users\admin\AppData\Local\Temp\terminus-font-4.49.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 3221226540 Modules
| |||||||||||||||
Total events
2 529
Read events
2 527
Write events
2
Delete events
0
Modification events
| (PID) Process: | (4072) terminus-font-4.49.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Fonts |
| Operation: | write | Name: | Terminus |
Value: terminus.fon | |||
| (PID) Process: | (4072) terminus-font-4.49.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Control\Session Manager |
| Operation: | write | Name: | PendingFileRenameOperations |
Value: \??\C:\Users\admin\AppData\Local\Temp\nsm3D1B.tmp\ | |||
Executable files
6
Suspicious files
0
Text files
11
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 4072 | terminus-font-4.49.exe | C:\Users\admin\AppData\Local\Temp\nsm3D1B.tmp\nsDialogs.dll | executable | |
MD5:C10E04DD4AD4277D5ADC951BB331C777 | SHA256:E31AD6C6E82E603378CB6B80E67D0E0DCD9CF384E1199AC5A65CB4935680021A | |||
| 4072 | terminus-font-4.49.exe | C:\Users\admin\AppData\Local\Temp\nsm3D1B.tmp\ao2.txt | text | |
MD5:F261B2733D31049D4E1DA8814700F5F1 | SHA256:E3CD752866688B3BD0C8384C9D4EA0394401AF293C27BF9C757FAF1A2EC15C95 | |||
| 4072 | terminus-font-4.49.exe | C:\Users\admin\AppData\Local\Temp\nsm3D1B.tmp\terminus.fon | executable | |
MD5:DCEBCC574CCB58F46D61D633A2741DA3 | SHA256:B1990A831672782E54110C4008DD4FCD65CF4C3E0750C9B1761DA4B3203D8B24 | |||
| 4072 | terminus-font-4.49.exe | C:\Users\admin\AppData\Local\Temp\nsm3D1B.tmp\fcpw.exe | executable | |
MD5:CAFD54B29A470F413C78181CE423FC74 | SHA256:886E10C5D5E102F1DB8B41324A9F4376A9EA88B1D62D68875B2A7F99C6CA1FC8 | |||
| 4072 | terminus-font-4.49.exe | C:\Windows\Fonts\terminus.fon | executable | |
MD5:CBBF94419FB923433A5B7B8E19BE62B7 | SHA256:5F6BDAAEBA4175A62AB4FA0B49B97F00DFAB6941ABBFFD3E54E7FCDD85468B3C | |||
| 4072 | terminus-font-4.49.exe | C:\Users\admin\AppData\Local\Temp\nsm3D1B.tmp\dv1.txt | text | |
MD5:04A16FDDED614978F4A8480D793FD516 | SHA256:67590D2BD98B6DC0ACF9574E174F6B027D71DD73A936227862D6AE5AA21E486A | |||
| 4072 | terminus-font-4.49.exe | C:\Users\admin\AppData\Local\Temp\nsm3D1B.tmp\ToolTips.dll | executable | |
MD5:9A0DA2692764BB842411A8B9687EBBB7 | SHA256:28AEAA48C929188A0D169887CC3F16370741467AE49E1DB59763F030710A6BBB | |||
| 4072 | terminus-font-4.49.exe | C:\Users\admin\AppData\Local\Temp\nsm3D1B.tmp\System.dll | executable | |
MD5:C17103AE9072A06DA581DEC998343FC1 | SHA256:DC58D8AD81CACB0C1ED72E33BFF8F23EA40B5252B5BB55D393A0903E6819AE2F | |||
| 4072 | terminus-font-4.49.exe | C:\Users\admin\AppData\Local\Temp\nsm3D1B.tmp\hi2-ka2.txt | text | |
MD5:09A9E73A5A3C67F06F94763186BB2772 | SHA256:6F25EAB687A0CA1B109B7892054FBFE86F5F9C95B7E0AFEC4F8E3DFD45079B1F | |||
| 4072 | terminus-font-4.49.exe | C:\Users\admin\AppData\Local\Temp\nsm3D1B.tmp\ll2.txt | text | |
MD5:607E5AE6B334FA085D437B1395EE0290 | SHA256:74F99A3C0A5960844E071B4DBC8739D2A4D814D2A7BB5D0349BF4487EF32742F | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
3
DNS requests
0
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
1088 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |