| File name: | AdskNLM.exe |
| Full analysis: | https://app.any.run/tasks/2d2874d6-a75a-4c22-a0ae-c9d43951b37f |
| Verdict: | Malicious activity |
| Analysis date: | April 28, 2025, 18:16:56 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/vnd.microsoft.portable-executable |
| File info: | PE32+ executable (GUI) x86-64, for MS Windows, 6 sections |
| MD5: | 92AC7F1A1A3250B9CC99F92634D44455 |
| SHA1: | 77A88E355C74168F189E22AC61968337AC80121E |
| SHA256: | 49C17DE629D9D3B013759B3755C8E168BCC42FD7C070C47C0F619A57F0DBEC91 |
| SSDEEP: | 98304:/F/XRKNzyUjS9zZB7T4R7IepI3shp5Cam5Im8yoqHNQTw380P7sFrMQQIqz9r0Mb:gpYbBxoY9fOWJv0IsKe/zqr |
MALICIOUS
Executing a file with an untrusted certificate
- adskflex.exe (PID: 616)
SUSPICIOUS
Reads security settings of Internet Explorer
- AdskNLM.exe (PID: 7408)
- AdskNLM.exe (PID: 7668)
- AdskNLM.exe (PID: 7780)
- AdskNLM.exe (PID: 7980)
- AdskNLM.exe (PID: 2516)
- AdskNLM.exe (PID: 7380)
- AdskNLM.exe (PID: 1164)
- AdskNLM.exe (PID: 6272)
- AdskNLM.exe (PID: 7712)
- AdskNLM.exe (PID: 4776)
- AdskNLM.exe (PID: 7828)
- AdskNLM.exe (PID: 1128)
- AdskNLM.exe (PID: 6576)
- AdskNLM.exe (PID: 8068)
- AdskNLM.exe (PID: 6584)
- AdskNLM.exe (PID: 7216)
- AdskNLM.exe (PID: 7312)
- AdskNLM.exe (PID: 7564)
- AdskNLM.exe (PID: 6540)
- AdskNLM.exe (PID: 4408)
- AdskNLM.exe (PID: 7844)
- AdskNLM.exe (PID: 1040)
- AdskNLM.exe (PID: 7536)
Reads the date of Windows installation
- AdskNLM.exe (PID: 7408)
- AdskNLM.exe (PID: 7668)
- AdskNLM.exe (PID: 7780)
- AdskNLM.exe (PID: 7980)
- AdskNLM.exe (PID: 7380)
- AdskNLM.exe (PID: 1164)
- AdskNLM.exe (PID: 2516)
- AdskNLM.exe (PID: 4776)
- AdskNLM.exe (PID: 7712)
- AdskNLM.exe (PID: 6272)
- AdskNLM.exe (PID: 1128)
- AdskNLM.exe (PID: 6576)
- AdskNLM.exe (PID: 7828)
- AdskNLM.exe (PID: 8068)
- AdskNLM.exe (PID: 6584)
- AdskNLM.exe (PID: 7216)
- AdskNLM.exe (PID: 7312)
- AdskNLM.exe (PID: 7564)
- AdskNLM.exe (PID: 6540)
- AdskNLM.exe (PID: 4408)
- AdskNLM.exe (PID: 7844)
- AdskNLM.exe (PID: 1040)
- AdskNLM.exe (PID: 7536)
Application launched itself
- AdskNLM.exe (PID: 7408)
- AdskNLM.exe (PID: 7564)
- msiexec.exe (PID: 8096)
- cmd.exe (PID: 6752)
- cmd.exe (PID: 4996)
- lmgrd.exe (PID: 4448)
- cmd.exe (PID: 4572)
Executable content was dropped or overwritten
- AdskNLM.exe (PID: 7564)
Stops a currently running service
- sc.exe (PID: 7708)
- sc.exe (PID: 2504)
- sc.exe (PID: 6800)
Starts CMD.EXE for commands execution
- AdskNLM.exe (PID: 7980)
- AdskNLM.exe (PID: 7256)
- AdskNLM.exe (PID: 2516)
- AdskNLM.exe (PID: 7380)
- AdskNLM.exe (PID: 1164)
- AdskNLM.exe (PID: 4776)
- AdskNLM.exe (PID: 7712)
- AdskNLM.exe (PID: 6272)
- AdskNLM.exe (PID: 1128)
- AdskNLM.exe (PID: 7844)
- AdskNLM.exe (PID: 1040)
- AdskNLM.exe (PID: 7536)
- cmd.exe (PID: 6752)
- AdskNLM.exe (PID: 6252)
- AdskNLM.exe (PID: 5984)
- AdskNLM.exe (PID: 5064)
- AdskNLM.exe (PID: 1660)
- AdskNLM.exe (PID: 1184)
- AdskNLM.exe (PID: 7728)
- AdskNLM.exe (PID: 3140)
- cmd.exe (PID: 4996)
- AdskNLM.exe (PID: 7452)
- AdskNLM.exe (PID: 2316)
- AdskNLM.exe (PID: 8160)
- AdskNLM.exe (PID: 6584)
- AdskNLM.exe (PID: 7868)
- cmd.exe (PID: 4572)
- AdskNLM.exe (PID: 7300)
Uses TASKKILL.EXE to kill process
- AdskNLM.exe (PID: 7780)
- AdskNLM.exe (PID: 7828)
- AdskNLM.exe (PID: 8068)
- AdskNLM.exe (PID: 6584)
- AdskNLM.exe (PID: 7216)
- AdskNLM.exe (PID: 7312)
Windows service management via SC.EXE
- sc.exe (PID: 7884)
- sc.exe (PID: 5204)
- sc.exe (PID: 3192)
Starts SC.EXE for service management
- AdskNLM.exe (PID: 6576)
- AdskNLM.exe (PID: 7668)
- AdskNLM.exe (PID: 4408)
- AdskNLM.exe (PID: 6540)
- AdskNLM.exe (PID: 6468)
- AdskNLM.exe (PID: 6048)
- AdskNLM.exe (PID: 7208)
Uses REG/REGEDIT.EXE to modify registry
- AdskNLM.exe (PID: 7564)
- AdskNLM.exe (PID: 8028)
- AdskNLM.exe (PID: 1760)
- AdskNLM.exe (PID: 6808)
- AdskNLM.exe (PID: 1912)
- AdskNLM.exe (PID: 728)
- AdskNLM.exe (PID: 7340)
- AdskNLM.exe (PID: 5212)
- AdskNLM.exe (PID: 2552)
- AdskNLM.exe (PID: 7232)
- AdskNLM.exe (PID: 1748)
- AdskNLM.exe (PID: 6676)
- AdskNLM.exe (PID: 3100)
- AdskNLM.exe (PID: 5064)
- AdskNLM.exe (PID: 7808)
There is functionality for taking screenshot (YARA)
- AdskNLM.exe (PID: 7408)
- AdskNLM.exe (PID: 7564)
Uses WMIC.EXE to obtain Windows Installer data
- cmd.exe (PID: 2420)
- cmd.exe (PID: 5956)
Uses WMIC.EXE to obtain service application data
- cmd.exe (PID: 6540)
Creates a new Windows service
- sc.exe (PID: 472)
Process copies executable file
- cmd.exe (PID: 6752)
Process uses IPCONFIG to clear DNS cache
- cmd.exe (PID: 5328)
Executes as Windows Service
- lmgrd.exe (PID: 4448)
There is functionality for VM detection VMWare (YARA)
- lmgrd.exe (PID: 4756)
- lmgrd.exe (PID: 4448)
There is functionality for VM detection antiVM strings (YARA)
- lmgrd.exe (PID: 4756)
- lmgrd.exe (PID: 4448)
There is functionality for VM detection VirtualBox (YARA)
- lmgrd.exe (PID: 4756)
- lmgrd.exe (PID: 4448)
INFO
Checks supported languages
- AdskNLM.exe (PID: 7408)
- AdskNLM.exe (PID: 7564)
- AdskNLM.exe (PID: 7668)
- AdskNLM.exe (PID: 7980)
- AdskNLM.exe (PID: 2516)
- AdskNLM.exe (PID: 4776)
- AdskNLM.exe (PID: 7380)
- AdskNLM.exe (PID: 1164)
- AdskNLM.exe (PID: 6272)
- AdskNLM.exe (PID: 7712)
- AdskNLM.exe (PID: 1128)
- AdskNLM.exe (PID: 6576)
- AdskNLM.exe (PID: 7828)
- AdskNLM.exe (PID: 8068)
- AdskNLM.exe (PID: 6584)
- AdskNLM.exe (PID: 7312)
- AdskNLM.exe (PID: 7216)
- AdskNLM.exe (PID: 7780)
- AdskNLM.exe (PID: 4408)
- AdskNLM.exe (PID: 6540)
- AdskNLM.exe (PID: 7536)
- AdskNLM.exe (PID: 1040)
- AdskNLM.exe (PID: 7844)
- msiexec.exe (PID: 8096)
Reads the computer name
- AdskNLM.exe (PID: 7408)
- AdskNLM.exe (PID: 7564)
- AdskNLM.exe (PID: 7668)
- AdskNLM.exe (PID: 7980)
- AdskNLM.exe (PID: 2516)
- AdskNLM.exe (PID: 7380)
- AdskNLM.exe (PID: 1164)
- AdskNLM.exe (PID: 4776)
- AdskNLM.exe (PID: 6272)
- AdskNLM.exe (PID: 7712)
- AdskNLM.exe (PID: 6576)
- AdskNLM.exe (PID: 7828)
- AdskNLM.exe (PID: 1128)
- AdskNLM.exe (PID: 6584)
- AdskNLM.exe (PID: 7216)
- AdskNLM.exe (PID: 8068)
- AdskNLM.exe (PID: 7780)
- AdskNLM.exe (PID: 7312)
- AdskNLM.exe (PID: 4408)
- AdskNLM.exe (PID: 6540)
- AdskNLM.exe (PID: 7536)
- AdskNLM.exe (PID: 1040)
- AdskNLM.exe (PID: 7844)
- msiexec.exe (PID: 8096)
Process checks computer location settings
- AdskNLM.exe (PID: 7408)
- AdskNLM.exe (PID: 7668)
- AdskNLM.exe (PID: 7780)
- AdskNLM.exe (PID: 7980)
- AdskNLM.exe (PID: 2516)
- AdskNLM.exe (PID: 7380)
- AdskNLM.exe (PID: 1164)
- AdskNLM.exe (PID: 4776)
- AdskNLM.exe (PID: 6272)
- AdskNLM.exe (PID: 7712)
- AdskNLM.exe (PID: 1128)
- AdskNLM.exe (PID: 6576)
- AdskNLM.exe (PID: 7828)
- AdskNLM.exe (PID: 6584)
- AdskNLM.exe (PID: 8068)
- AdskNLM.exe (PID: 7312)
- AdskNLM.exe (PID: 7216)
- AdskNLM.exe (PID: 7564)
- AdskNLM.exe (PID: 6540)
- AdskNLM.exe (PID: 4408)
- AdskNLM.exe (PID: 7844)
- AdskNLM.exe (PID: 1040)
- AdskNLM.exe (PID: 7536)
Create files in a temporary directory
- AdskNLM.exe (PID: 7564)
The sample compiled with english language support
- AdskNLM.exe (PID: 7564)
- msiexec.exe (PID: 8096)
Reads security settings of Internet Explorer
- WMIC.exe (PID: 7968)
Changes file name
- cmd.exe (PID: 4120)
- cmd.exe (PID: 5008)
Executable content was dropped or overwritten
- msiexec.exe (PID: 8096)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Generic Win/DOS Executable (50) |
|---|---|---|
| .exe | | | DOS Executable Generic (49.9) |
EXIF
EXE
| MachineType: | AMD AMD64 |
|---|---|
| TimeStamp: | 2018:05:21 01:49:42+00:00 |
| ImageFileCharacteristics: | Executable, Large address aware |
| PEType: | PE32+ |
| LinkerVersion: | 10 |
| CodeSize: | 130560 |
| InitializedDataSize: | 308736 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x20360 |
| OSVersion: | 5.2 |
| ImageVersion: | - |
| SubsystemVersion: | 5.2 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 10.0.0.0 |
| ProductVersionNumber: | 10.0.0.0 |
| FileFlagsMask: | 0x003f |
| FileFlags: | (none) |
| FileOS: | Windows NT 32-bit |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | Neutral |
| CharacterSet: | Unicode |
| CompanyName: | MAGNiTUDE & m0nkrus |
| FileDescription: | Autodesk 2020-2026 Cracked NLM Installer |
| FileVersion: | 10.0.0.0 |
| InternalName: | AdskNLM |
| LegalCopyright: | Copyright © 2022-2025 MAGNiTUDE & m0nkrus |
| OriginalFileName: | AdskNLM.exe |
| PrivateBuild: | March 25, 2025 |
| ProductName: | Autodesk Cracked NLM |
| ProductVersion: | 10.0.0.0 |
Total processes
321
Monitored processes
187
Malicious processes
2
Suspicious processes
6
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
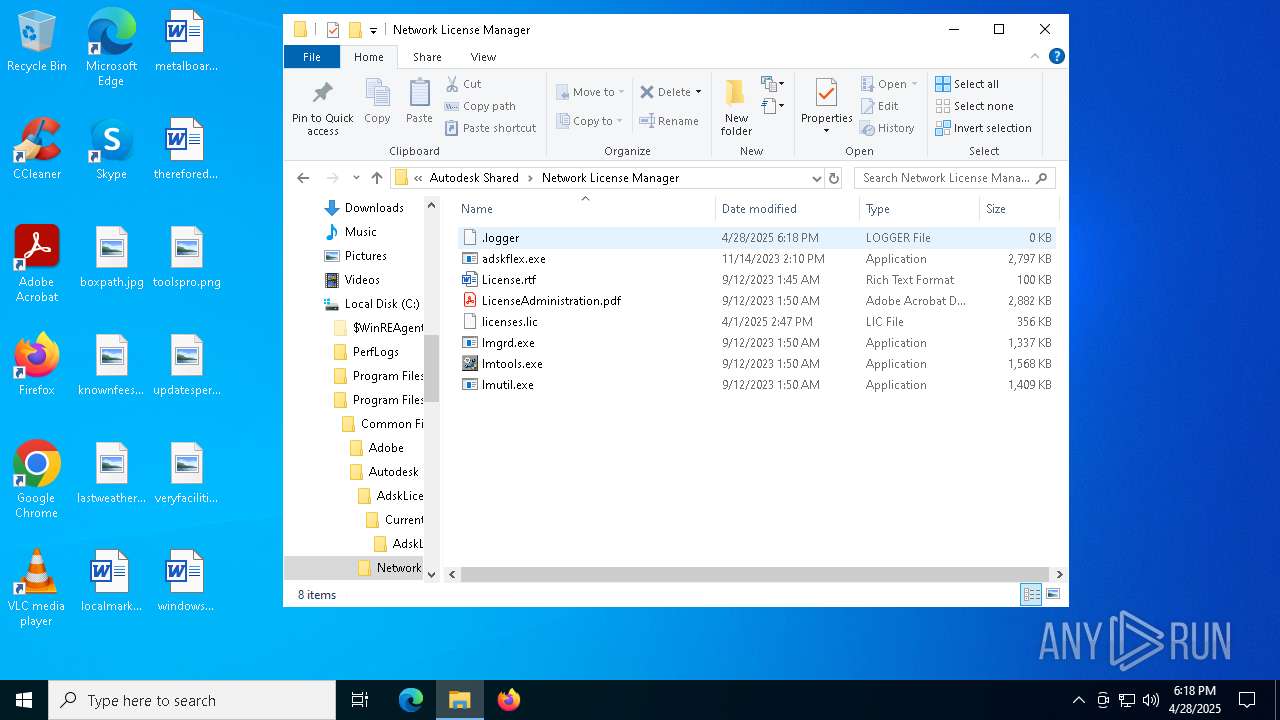
| 472 | "C:\Windows\System32\sc.exe" create AdskNLM binPath= "\"C:\Program Files (x86)\Common Files\Autodesk Shared\Network License Manager\lmgrd.exe\"" start= auto depend= WinMgmt/+NetworkProvider obj= "NT AUTHORITY\LocalService" displayname= AdskNLM | C:\Windows\System32\sc.exe | — | AdskNLM.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Service Control Manager Configuration Tool Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 516 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 616 | "C:\Windows\System32\cmd.exe" /c del /q /f "C:\Users\admin\AppData\Local\Autodesk\Genuine Autodesk Service\id.dat" | C:\Windows\System32\cmd.exe | — | AdskNLM.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 616 | adskflex.exe -T DESKTOP-JGLLJLD 11.19 -1 -c ";C:\Program Files (x86)\Common Files\Autodesk Shared\Network License Manager\licenses.lic;" -srv IxAEj39wedH9UEKYRZFoYPOY4d6IshfxDsPd6sXAVYYLGHzeuZY5flwNjxjz8LE --lmgrd_start 680fc65d -vdrestart 0 | C:\Program Files (x86)\Common Files\Autodesk Shared\Network License Manager\adskflex.exe | — | lmgrd.exe | |||||||||||
User: LOCAL SERVICE Company: Autodesk, Inc. Integrity Level: SYSTEM Description: Autodesk Licensing Vendor Daemon Version: 4 Modules
| |||||||||||||||
| 672 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | taskkill.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 680 | "C:\Windows\System32\cmd.exe" /c find /c /i "api.genuine-software.autodesk.com" "C:\WINDOWS\system32\drivers\etc\hosts" || echo ^0.0.0.0 api.genuine-software.autodesk.com >> "C:\WINDOWS\system32\drivers\etc\hosts" | C:\Windows\System32\cmd.exe | — | AdskNLM.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 728 | "C:\Windows\System32\cmd.exe" /c if exist "C:\Program Files (x86)\Common Files\Autodesk Shared\AdskLicensing\10.2.0.4231\AdskLicensingAgent\AdskLicensingAgent.exe" ( echo F | xcopy /hkry "C:\Users\admin\AppData\Local\Temp\Adsk-NLM\version_old.dll" "C:\Program Files (x86)\Common Files\Autodesk Shared\AdskLicensing\10.2.0.4231\AdskLicensingAgent\version.dll" ) | C:\Windows\System32\cmd.exe | — | AdskNLM.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 728 | "C:\Users\admin\Downloads\AdskNLM.exe" -sfxwaitall:0 "reg" add "HKLM\SOFTWARE\FLEXlm License Manager\AdskNLM" /v "Service" /d "AdskNLM" /f | C:\Users\admin\Downloads\AdskNLM.exe | — | AdskNLM.exe | |||||||||||
User: admin Company: MAGNiTUDE & m0nkrus Integrity Level: HIGH Description: Autodesk 2020-2026 Cracked NLM Installer Exit code: 0 Version: 10.0.0.0 Modules
| |||||||||||||||
| 872 | "C:\Windows\System32\reg.exe" delete "HKCU\SOFTWARE\FLEXlm License Manager" /v "ADSKFLEX_LICENSE_FILE" /f | C:\Windows\System32\reg.exe | — | AdskNLM.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Registry Console Tool Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 960 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
37 953
Read events
37 828
Write events
114
Delete events
11
Modification events
| (PID) Process: | (1852) reg.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Run |
| Operation: | delete value | Name: | Autodesk Access |
Value: | |||
| (PID) Process: | (8096) msiexec.exe | Key: | HKEY_USERS\S-1-5-21-1693682860-607145093-2874071422-1001\SOFTWARE\Microsoft\RestartManager\Session0000 |
| Operation: | write | Name: | Owner |
Value: A01F0000E54236C869B8DB01 | |||
| (PID) Process: | (8096) msiexec.exe | Key: | HKEY_USERS\S-1-5-21-1693682860-607145093-2874071422-1001\SOFTWARE\Microsoft\RestartManager\Session0000 |
| Operation: | write | Name: | SessionHash |
Value: 59203DCC318A4CD3B469EC680A52ABBCF7F0089D3ECC0D66EE8DA5F9D6D2AE58 | |||
| (PID) Process: | (8096) msiexec.exe | Key: | HKEY_USERS\S-1-5-21-1693682860-607145093-2874071422-1001\SOFTWARE\Microsoft\RestartManager\Session0000 |
| Operation: | write | Name: | Sequence |
Value: 1 | |||
| (PID) Process: | (8096) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Installer\UserData\S-1-5-18\Components\0F83F0DEEAA6FCF46A510E08A185B7DB |
| Operation: | write | Name: | 58619EB42361CF745B368A5A246C66C4 |
Value: C:\Program Files (x86)\Common Files\Autodesk Shared\Network License Manager\ | |||
| (PID) Process: | (8096) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Installer\Folders |
| Operation: | write | Name: | C:\Program Files (x86)\Common Files\Autodesk Shared\Network License Manager\ |
Value: 1 | |||
| (PID) Process: | (8096) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Installer\Folders |
| Operation: | write | Name: | C:\ProgramData\Microsoft\Windows\Start Menu\Programs\Autodesk\NLRM\ |
Value: | |||
| (PID) Process: | (8096) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Installer\Folders |
| Operation: | write | Name: | C:\ProgramData\Microsoft\Windows\Start Menu\Programs\Autodesk\ |
Value: | |||
| (PID) Process: | (8096) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall\{4BE91685-1632-47FC-B563-A8A542C6664C} |
| Operation: | write | Name: | InstallDate |
Value: 20250428 | |||
| (PID) Process: | (8096) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall\{4BE91685-1632-47FC-B563-A8A542C6664C} |
| Operation: | write | Name: | InstallLocation |
Value: | |||
Executable files
13
Suspicious files
25
Text files
7
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 7564 | AdskNLM.exe | C:\Users\admin\AppData\Local\Temp\Adsk-NLM\nlm11-19-4-1-ipv4-ipv6-win64.msi | — | |
MD5:— | SHA256:— | |||
| 8096 | msiexec.exe | C:\Windows\Installer\118e52.msi | — | |
MD5:— | SHA256:— | |||
| 7564 | AdskNLM.exe | C:\Users\admin\AppData\Local\Temp\Adsk-NLM\version_old.dll | executable | |
MD5:51F0E19B4CF164ECBA9A006C4CF3B2A5 | SHA256:6F13E52D797A732435C8BB456BE08C64D0B6FADEA29F85486F4B44559D6CC95F | |||
| 7564 | AdskNLM.exe | C:\Users\admin\AppData\Local\Temp\Adsk-NLM\nlm.mst | binary | |
MD5:29810BAB1EF69A3D26872093EF09372B | SHA256:90E413CD675EE085C441DF6327F6661A3459F4E109E0684B1A361C050D672BDB | |||
| 7564 | AdskNLM.exe | C:\Users\admin\AppData\Local\Temp\Adsk-NLM\version.dll | executable | |
MD5:4C059805319A0BB6830C563E41D85918 | SHA256:C6A4426B196F19B0A456908B20A1B5FA6D2DAE8CDB1EE7BC537F2842014BA6DB | |||
| 7564 | AdskNLM.exe | C:\Users\admin\AppData\Local\Temp\Adsk-NLM\licenses.lic | text | |
MD5:8A8D68BDD196D2C9D31D9E0E16372F8D | SHA256:7C106FCF99B817B40015CB387186317AB95C4C5809E759C871101119F832AC50 | |||
| 7564 | AdskNLM.exe | C:\Users\admin\AppData\Local\Temp\Adsk-NLM\delnowmic.ps1 | text | |
MD5:67924FF023F149E8B467A8905FF1B4FC | SHA256:4B5EF379990A4663A3341913B0BD4FEDF906B9F6AF8D8FA0CB8BEE4A09FF92F9 | |||
| 8096 | msiexec.exe | C:\Windows\Installer\118e53.mst | binary | |
MD5:29810BAB1EF69A3D26872093EF09372B | SHA256:90E413CD675EE085C441DF6327F6661A3459F4E109E0684B1A361C050D672BDB | |||
| 8096 | msiexec.exe | C:\Windows\Installer\MSI9141.tmp | executable | |
MD5:A3AE5D86ECF38DB9427359EA37A5F646 | SHA256:C8D190D5BE1EFD2D52F72A72AE9DFA3940AB3FACEB626405959349654FE18B74 | |||
| 8096 | msiexec.exe | C:\Windows\Installer\MSI926C.tmp | executable | |
MD5:A3AE5D86ECF38DB9427359EA37A5F646 | SHA256:C8D190D5BE1EFD2D52F72A72AE9DFA3940AB3FACEB626405959349654FE18B74 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
20
TCP/UDP connections
34
DNS requests
22
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
5496 | MoUsoCoreWorker.exe | GET | 200 | 2.16.168.114:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
5496 | MoUsoCoreWorker.exe | GET | 200 | 2.23.246.101:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
6544 | svchost.exe | GET | 200 | 2.23.77.188:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
7852 | WmiPrvSE.exe | GET | 200 | 2.16.241.19:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
7852 | WmiPrvSE.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/MicCodSigPCA2011_2011-07-08.crl | unknown | — | — | whitelisted |
7852 | WmiPrvSE.exe | GET | 200 | 2.16.241.12:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut_2010-06-23.crl | unknown | — | — | whitelisted |
7852 | WmiPrvSE.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/MicWinProPCA2011_2011-10-19.crl | unknown | — | — | whitelisted |
7852 | WmiPrvSE.exe | GET | 200 | 184.30.131.245:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSnR4FoxLLkI7vkvsUIFlZt%2BlGH3gQUWsS5eyoKo6XqcQPAYPkt9mV1DlgCEAkQWITrlZ07yLmU%2BRintu4%3D | unknown | — | — | whitelisted |
7852 | WmiPrvSE.exe | GET | 200 | 184.30.131.245:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBT3xL4LQLXDRDM9P665TW442vrsUQQUReuir%2FSSy4IxLVGLp6chnfNtyA8CEAQJGBtf1btmdVNDtW%2BVUAg%3D | unknown | — | — | whitelisted |
7852 | WmiPrvSE.exe | GET | 200 | 2.16.241.12:80 | http://crl.microsoft.com/pki/crl/products/microsoftrootcert.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
6248 | RUXIMICS.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
2104 | svchost.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
— | — | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
5496 | MoUsoCoreWorker.exe | 2.16.168.114:80 | crl.microsoft.com | Akamai International B.V. | RU | whitelisted |
5496 | MoUsoCoreWorker.exe | 2.23.246.101:80 | www.microsoft.com | Ooredoo Q.S.C. | QA | whitelisted |
3216 | svchost.exe | 172.211.123.249:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | FR | whitelisted |
6544 | svchost.exe | 40.126.32.134:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
6544 | svchost.exe | 2.23.77.188:80 | ocsp.digicert.com | AKAMAI-AS | DE | whitelisted |
7852 | WmiPrvSE.exe | 2.16.241.19:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
google.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
settings-win.data.microsoft.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |
activation-v2.sls.microsoft.com |
| whitelisted |