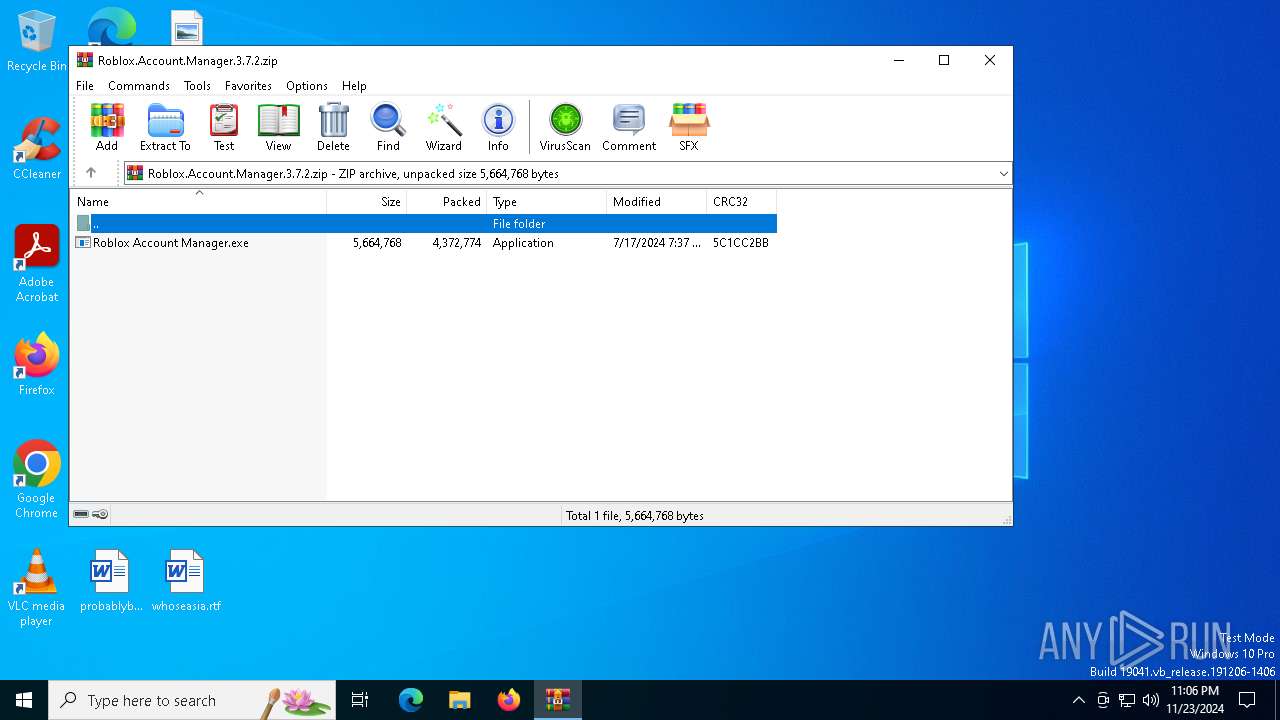
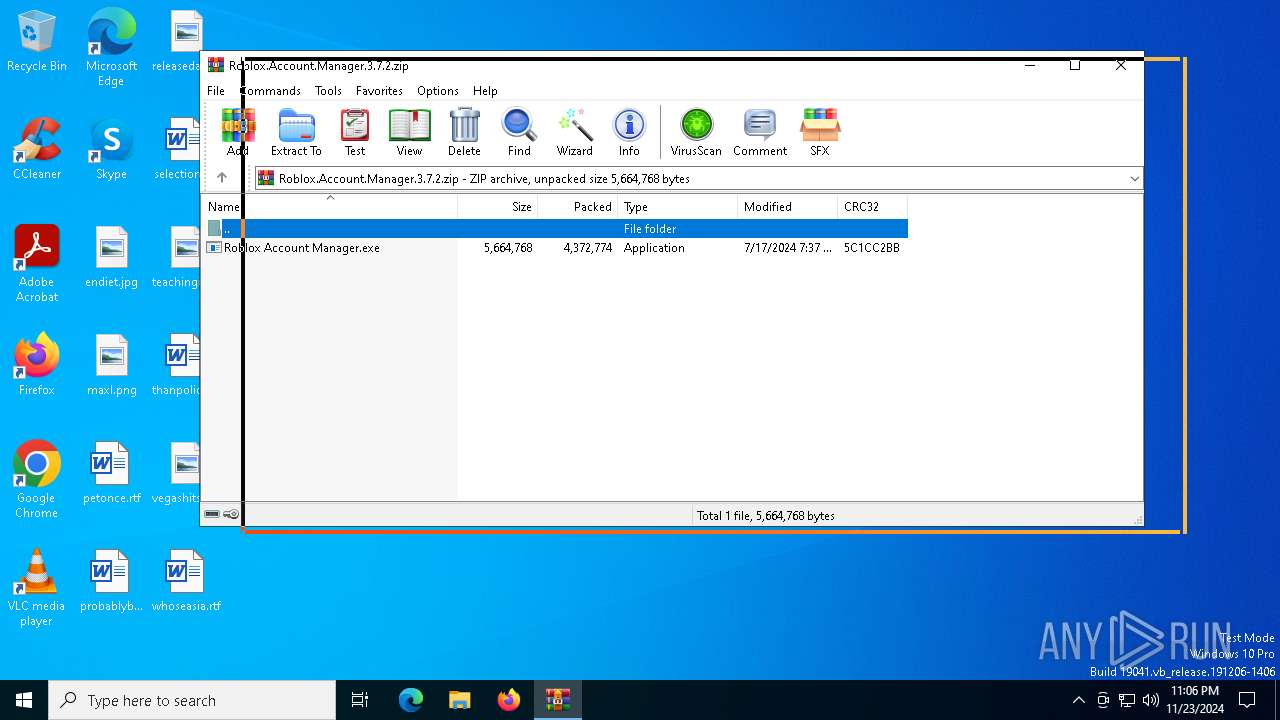
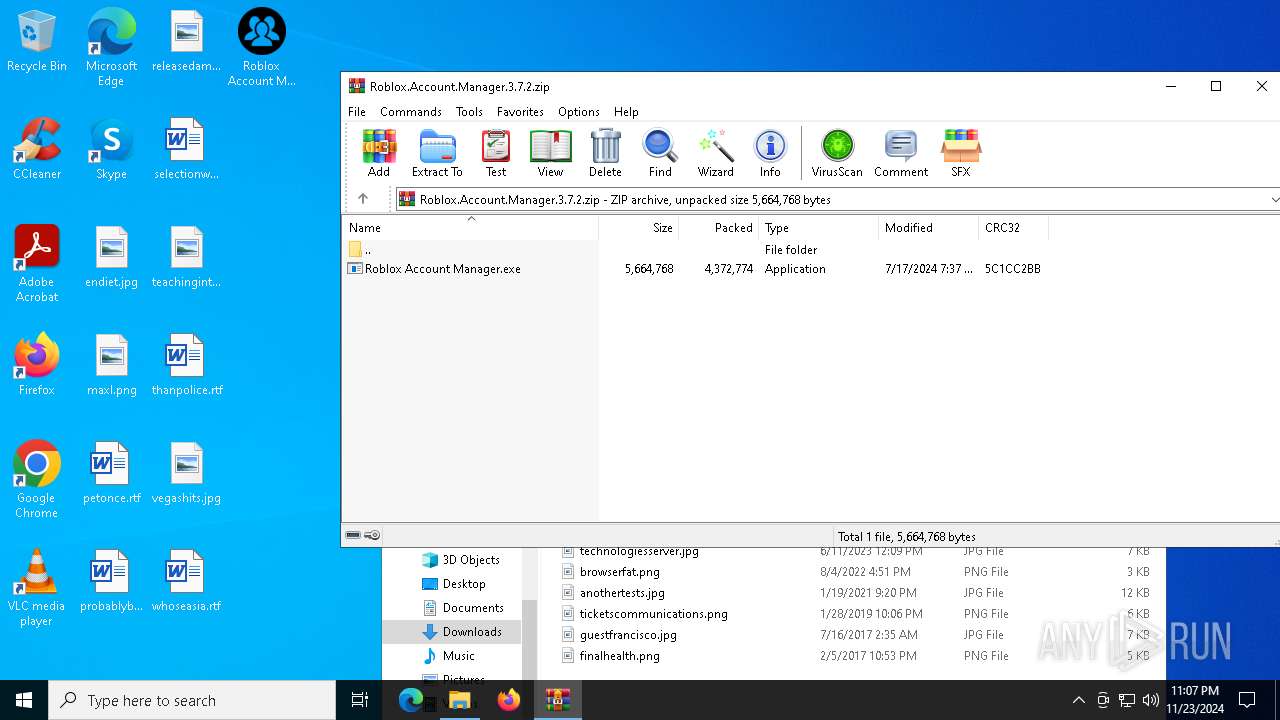
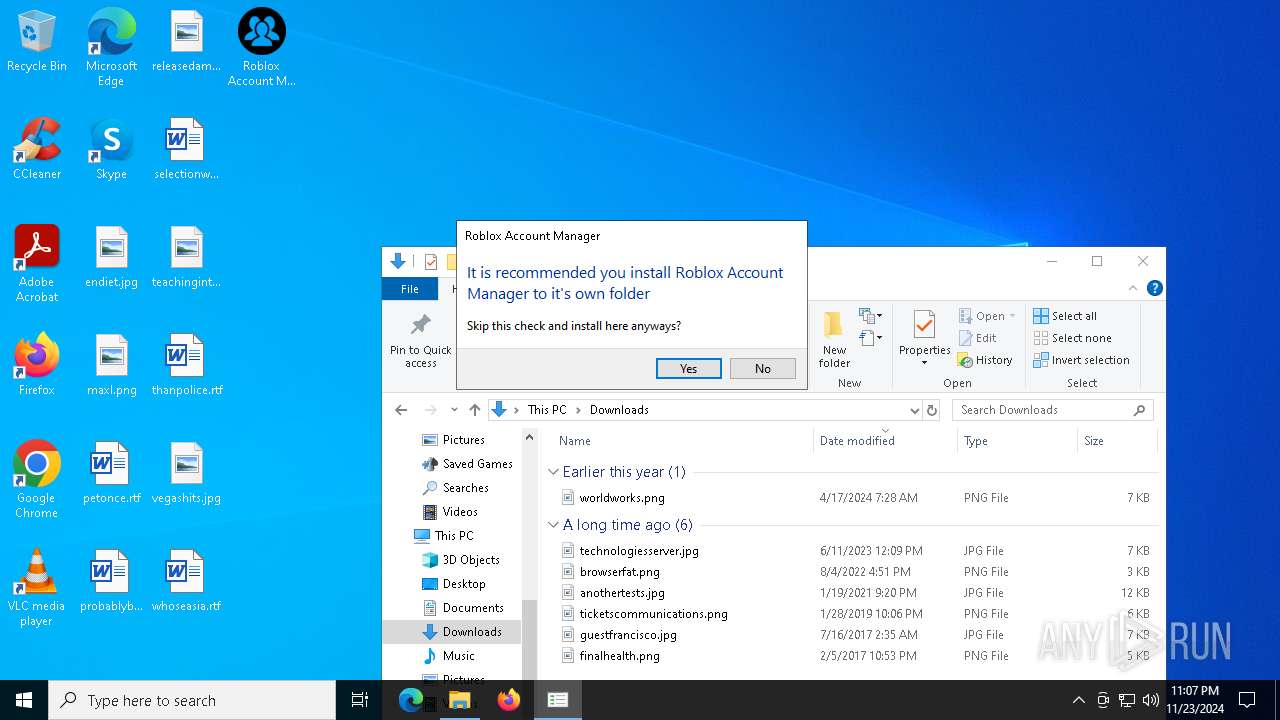
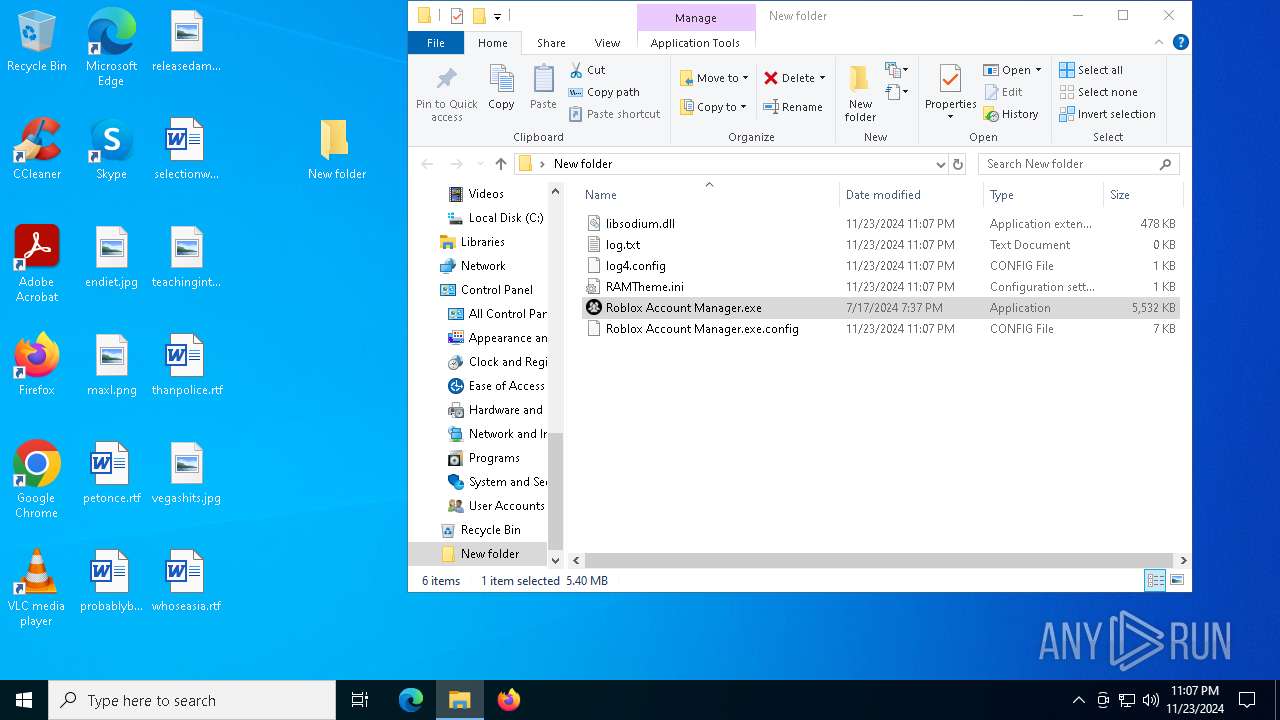
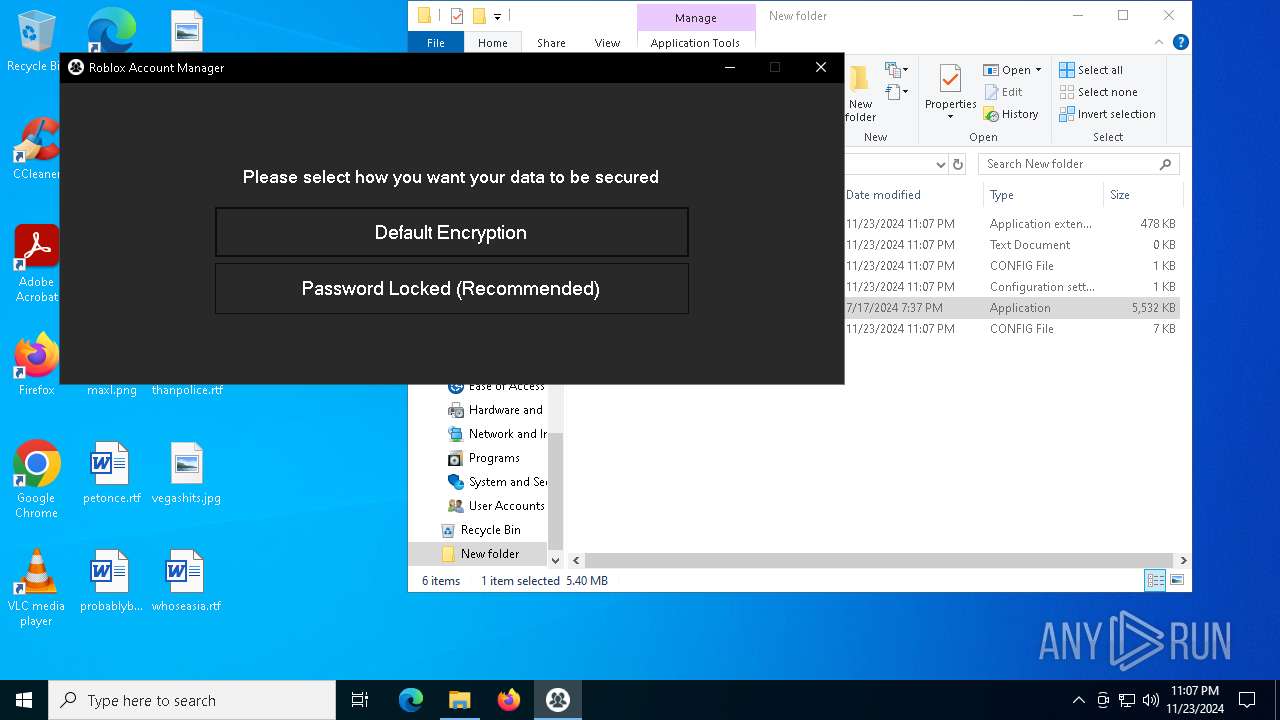
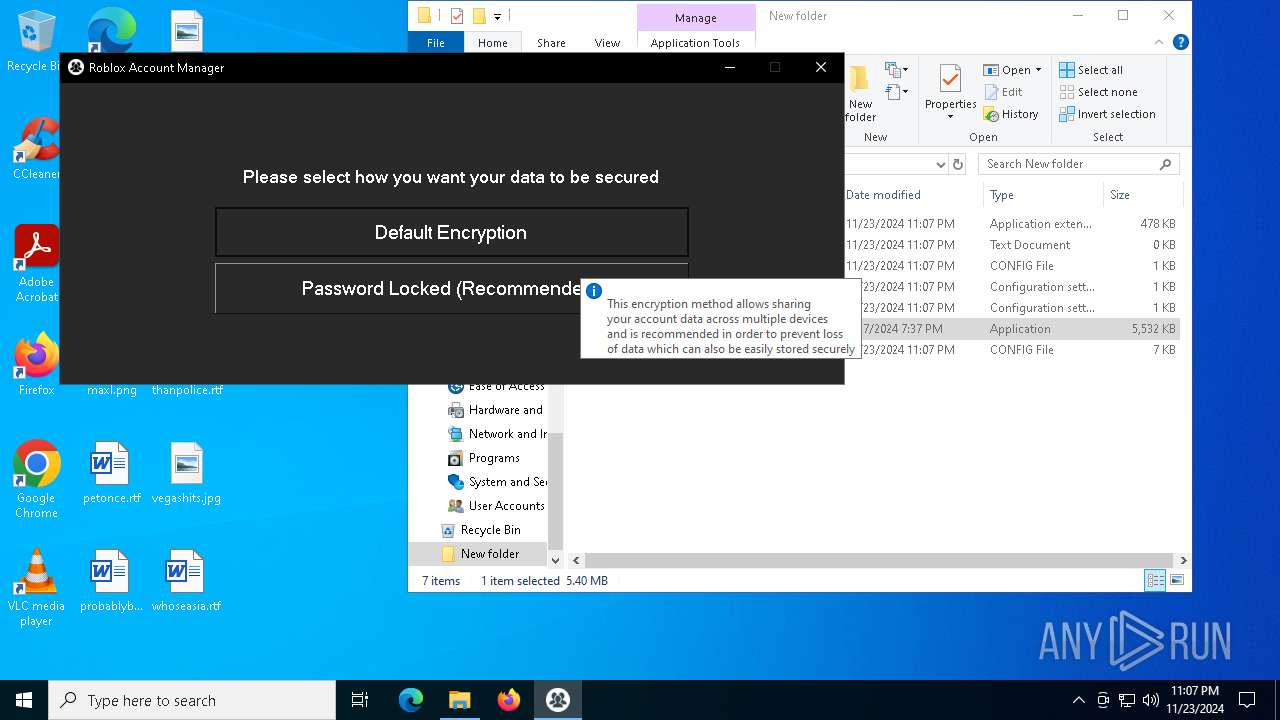
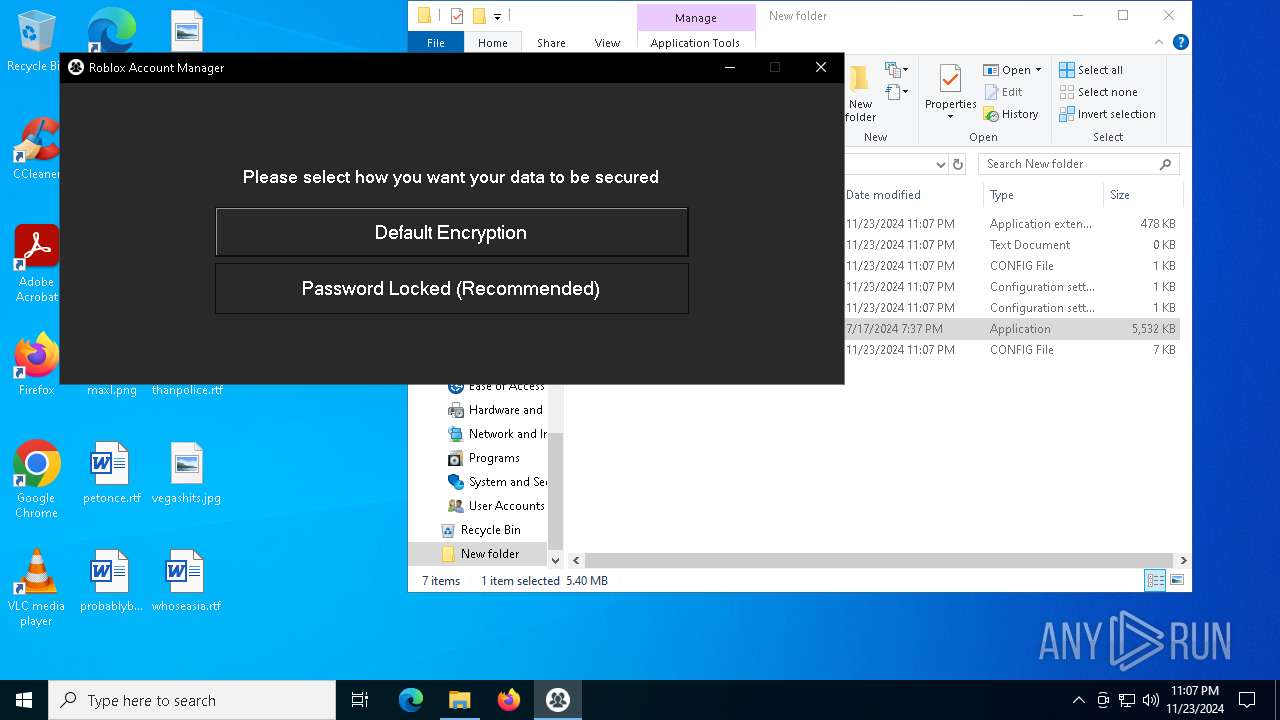
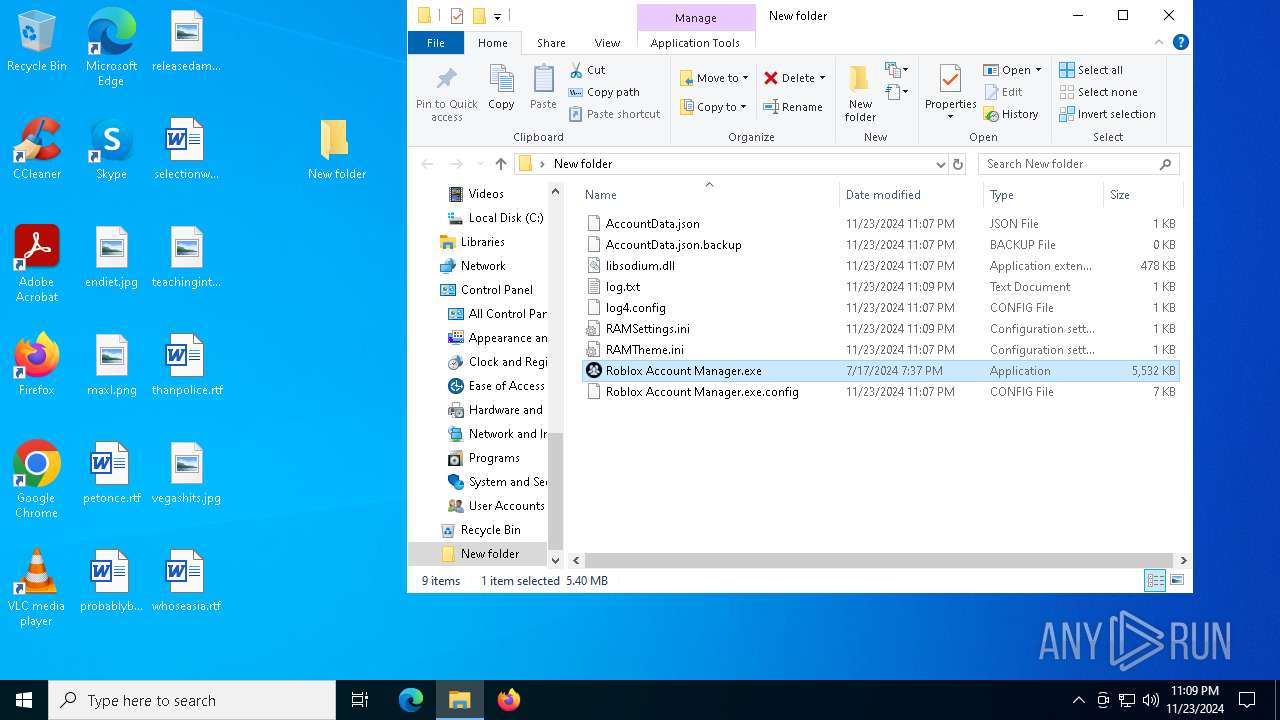
| download: | /ic3w0lf22/Roblox-Account-Manager/releases/download/3.7.2/Roblox.Account.Manager.3.7.2.zip |
| Full analysis: | https://app.any.run/tasks/d01fde25-5482-4358-bf96-0823245281e2 |
| Verdict: | Malicious activity |
| Analysis date: | November 23, 2024, 23:06:16 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v2.0 to extract, compression method=deflate |
| MD5: | D58B79CB3D3635BA963427362F75D075 |
| SHA1: | 0E33EEFF9B625FCEB2D2D0195E6F32523D57DB79 |
| SHA256: | 49B2C015DA0851A2ED43820799A7BCDA08E1BC5F315E107598F87F4B1BD36DAC |
| SSDEEP: | 98304:lEQBRQV3BdUKmD4I3UV5AaONlAUntE4vA0j1Yfyb/plXAWyz7N9j/SfH1e7zWIQ7:XcGtpl |
MALICIOUS
Generic archive extractor
- WinRAR.exe (PID: 2972)
SUSPICIOUS
Reads security settings of Internet Explorer
- Roblox Account Manager.exe (PID: 2396)
- Roblox Account Manager.exe (PID: 5592)
Application launched itself
- Roblox Account Manager.exe (PID: 2396)
- chrome.exe (PID: 712)
- chrome.exe (PID: 2456)
Executable content was dropped or overwritten
- Roblox Account Manager.exe (PID: 5592)
The process creates files with name similar to system file names
- Roblox Account Manager.exe (PID: 5592)
Process drops legitimate windows executable
- Roblox Account Manager.exe (PID: 5592)
INFO
Checks supported languages
- Roblox Account Manager.exe (PID: 5992)
- Roblox Account Manager.exe (PID: 2396)
- Roblox Account Manager.exe (PID: 5592)
- chrome.exe (PID: 1476)
- chrome.exe (PID: 712)
- chrome.exe (PID: 2456)
- chrome.exe (PID: 4528)
- chrome.exe (PID: 1792)
- chrome.exe (PID: 4708)
- chrome.exe (PID: 6092)
- chrome.exe (PID: 2512)
- Roblox Account Manager.exe (PID: 5748)
- chrome.exe (PID: 3544)
- chrome.exe (PID: 5748)
Creates files in the program directory
- Roblox Account Manager.exe (PID: 5992)
- Roblox Account Manager.exe (PID: 5592)
The process uses the downloaded file
- WinRAR.exe (PID: 2972)
- Roblox Account Manager.exe (PID: 2396)
Manual execution by a user
- Roblox Account Manager.exe (PID: 5992)
- Roblox Account Manager.exe (PID: 2396)
- Roblox Account Manager.exe (PID: 5748)
- Roblox Account Manager.exe (PID: 3224)
Reads the machine GUID from the registry
- Roblox Account Manager.exe (PID: 2396)
- Roblox Account Manager.exe (PID: 5992)
- Roblox Account Manager.exe (PID: 5592)
- chrome.exe (PID: 712)
- Roblox Account Manager.exe (PID: 5748)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 2972)
Reads the computer name
- Roblox Account Manager.exe (PID: 5992)
- Roblox Account Manager.exe (PID: 2396)
- Roblox Account Manager.exe (PID: 5592)
- chrome.exe (PID: 712)
- chrome.exe (PID: 2456)
- chrome.exe (PID: 3544)
- Roblox Account Manager.exe (PID: 5748)
- chrome.exe (PID: 2512)
- chrome.exe (PID: 4528)
Process checks computer location settings
- Roblox Account Manager.exe (PID: 2396)
- chrome.exe (PID: 712)
- chrome.exe (PID: 5748)
- chrome.exe (PID: 4708)
- chrome.exe (PID: 6092)
Reads the software policy settings
- Roblox Account Manager.exe (PID: 5592)
Disables trace logs
- Roblox Account Manager.exe (PID: 5592)
Checks proxy server information
- Roblox Account Manager.exe (PID: 5592)
- chrome.exe (PID: 712)
Creates files or folders in the user directory
- Roblox Account Manager.exe (PID: 5592)
Sends debugging messages
- chrome.exe (PID: 712)
Create files in a temporary directory
- chrome.exe (PID: 712)
- chrome.exe (PID: 4528)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 20 |
|---|---|
| ZipBitFlag: | - |
| ZipCompression: | Deflated |
| ZipModifyDate: | 2024:07:17 19:37:00 |
| ZipCRC: | 0x5c1cc2bb |
| ZipCompressedSize: | 4372774 |
| ZipUncompressedSize: | 5664768 |
| ZipFileName: | Roblox Account Manager.exe |
Total processes
151
Monitored processes
17
Malicious processes
3
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 712 | "C:\Users\admin\AppData\Local\PuppeteerSharp\Chrome\Win64-124.0.6367.201\chrome-win64\chrome.exe" --allow-pre-commit-input --disable-background-networking --disable-background-timer-throttling --disable-backgrounding-occluded-windows --disable-breakpad --disable-client-side-phishing-detection --disable-component-extensions-with-background-pages --disable-component-update --disable-default-apps --disable-dev-shm-usage --disable-extensions --disable-field-trial-config --disable-hang-monitor --disable-infobars --disable-ipc-flooding-protection --disable-popup-blocking --disable-prompt-on-repost --disable-renderer-backgrounding --disable-search-engine-choice-screen --disable-sync --enable-automation --enable-blink-features=IdleDetection --export-tagged-pdf --generate-pdf-document-outline --force-color-profile=srgb --metrics-recording-only --no-first-run --password-store=basic --use-mock-keychain --disable-features=Translate,AcceptCHFrame,MediaRouter,OptimizationHints,ProcessPerSiteUpToMainFrameThreshold --enable-features= about:blank --disable-web-security --window-size="880,740" --window-position="200,-30" --remote-debugging-port=0 --user-data-dir="C:\Users\admin\AppData\Local\Temp\4mepntm1.wg5" | C:\Users\admin\AppData\Local\PuppeteerSharp\Chrome\Win64-124.0.6367.201\chrome-win64\chrome.exe | Roblox Account Manager.exe | ||||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome for Testing Exit code: 0 Version: 124.0.6367.201 Modules
| |||||||||||||||
| 1476 | C:\Users\admin\AppData\Local\PuppeteerSharp\Chrome\Win64-124.0.6367.201\chrome-win64\chrome.exe --type=crashpad-handler --user-data-dir=C:\Users\admin\AppData\Local\Temp\4mepntm1.wg5 /prefetch:4 --no-periodic-tasks --monitor-self-annotation=ptype=crashpad-handler --database=C:\Users\admin\AppData\Local\Temp\4mepntm1.wg5\Crashpad --annotation=plat=Win64 "--annotation=prod=Google Chrome for Testing" --annotation=ver=124.0.6367.201 --initial-client-data=0x208,0x20c,0x210,0x18c,0x214,0x7ff780859900,0x7ff78085990c,0x7ff780859918 | C:\Users\admin\AppData\Local\PuppeteerSharp\Chrome\Win64-124.0.6367.201\chrome-win64\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome for Testing Exit code: 0 Version: 124.0.6367.201 Modules
| |||||||||||||||
| 1556 | C:\WINDOWS\System32\rundll32.exe C:\WINDOWS\System32\shell32.dll,SHCreateLocalServerRunDll {9aa46009-3ce0-458a-a354-715610a075e6} -Embedding | C:\Windows\System32\rundll32.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows host process (Rundll32) Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1792 | "C:\Users\admin\AppData\Local\PuppeteerSharp\Chrome\Win64-124.0.6367.201\chrome-win64\chrome.exe" --type=utility --utility-sub-type=storage.mojom.StorageService --lang=en-US --service-sandbox-type=service --user-data-dir="C:\Users\admin\AppData\Local\Temp\4mepntm1.wg5" --no-appcompat-clear --field-trial-handle=2404,i,2475555366972672937,10361206212521700122,262144 --disable-features=AcceptCHFrame,MediaRouter,OptimizationHints,ProcessPerSiteUpToMainFrameThreshold,Translate --variations-seed-version --mojo-platform-channel-handle=2420 /prefetch:8 | C:\Users\admin\AppData\Local\PuppeteerSharp\Chrome\Win64-124.0.6367.201\chrome-win64\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome for Testing Exit code: 0 Version: 124.0.6367.201 Modules
| |||||||||||||||
| 2396 | "C:\Users\admin\Desktop\New folder\Roblox Account Manager.exe" | C:\Users\admin\Desktop\New folder\Roblox Account Manager.exe | — | explorer.exe | |||||||||||
User: admin Company: ic3 Integrity Level: MEDIUM Description: Roblox Account Manager Exit code: 0 Version: 3.7.2.0 Modules
| |||||||||||||||
| 2456 | C:\Users\admin\AppData\Local\PuppeteerSharp\Chrome\Win64-124.0.6367.201\chrome-win64\chrome.exe --type=crashpad-handler --user-data-dir=C:\Users\admin\AppData\Local\Temp\4mepntm1.wg5 /prefetch:4 --monitor-self --monitor-self-argument=--type=crashpad-handler --monitor-self-argument=--user-data-dir=C:\Users\admin\AppData\Local\Temp\4mepntm1.wg5 --monitor-self-argument=/prefetch:4 --monitor-self-annotation=ptype=crashpad-handler --database=C:\Users\admin\AppData\Local\Temp\4mepntm1.wg5\Crashpad --annotation=plat=Win64 "--annotation=prod=Google Chrome for Testing" --annotation=ver=124.0.6367.201 --initial-client-data=0x144,0x148,0x14c,0x11c,0x150,0x7ff8213bcc70,0x7ff8213bcc7c,0x7ff8213bcc88 | C:\Users\admin\AppData\Local\PuppeteerSharp\Chrome\Win64-124.0.6367.201\chrome-win64\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome for Testing Exit code: 0 Version: 124.0.6367.201 Modules
| |||||||||||||||
| 2512 | "C:\Users\admin\AppData\Local\PuppeteerSharp\Chrome\Win64-124.0.6367.201\chrome-win64\chrome.exe" --type=utility --utility-sub-type=chrome.mojom.ProcessorMetrics --lang=en-US --service-sandbox-type=none --user-data-dir="C:\Users\admin\AppData\Local\Temp\4mepntm1.wg5" --no-appcompat-clear --field-trial-handle=4980,i,2475555366972672937,10361206212521700122,262144 --disable-features=AcceptCHFrame,MediaRouter,OptimizationHints,ProcessPerSiteUpToMainFrameThreshold,Translate --variations-seed-version --mojo-platform-channel-handle=5000 /prefetch:8 | C:\Users\admin\AppData\Local\PuppeteerSharp\Chrome\Win64-124.0.6367.201\chrome-win64\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome for Testing Exit code: 0 Version: 124.0.6367.201 Modules
| |||||||||||||||
| 2972 | "C:\Program Files\WinRAR\WinRAR.exe" C:\Users\admin\AppData\Local\Temp\Roblox.Account.Manager.3.7.2.zip | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.91.0 Modules
| |||||||||||||||
| 3224 | "C:\Users\admin\Desktop\New folder\Roblox Account Manager.exe" | C:\Users\admin\Desktop\New folder\Roblox Account Manager.exe | explorer.exe | ||||||||||||
User: admin Company: ic3 Integrity Level: MEDIUM Description: Roblox Account Manager Exit code: 0 Version: 3.7.2.0 Modules
| |||||||||||||||
| 3544 | "C:\Users\admin\AppData\Local\PuppeteerSharp\Chrome\Win64-124.0.6367.201\chrome-win64\chrome.exe" --type=gpu-process --disable-breakpad --user-data-dir="C:\Users\admin\AppData\Local\Temp\4mepntm1.wg5" --no-appcompat-clear --start-stack-profiler --gpu-preferences=WAAAAAAAAADgAAAMAAAAAAAAAAAAAAAAAABgAAEAAAA4AAAAAAAAAAAAAAAEAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAGAAAAAAAAAAYAAAAAAAAAAgAAAAAAAAACAAAAAAAAAAIAAAAAAAAAA== --field-trial-handle=2012,i,2475555366972672937,10361206212521700122,262144 --disable-features=AcceptCHFrame,MediaRouter,OptimizationHints,ProcessPerSiteUpToMainFrameThreshold,Translate --variations-seed-version --mojo-platform-channel-handle=2008 /prefetch:2 | C:\Users\admin\AppData\Local\PuppeteerSharp\Chrome\Win64-124.0.6367.201\chrome-win64\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome for Testing Exit code: 0 Version: 124.0.6367.201 Modules
| |||||||||||||||
Total events
7 478
Read events
7 397
Write events
66
Delete events
15
Modification events
| (PID) Process: | (2972) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\preferences.zip | |||
| (PID) Process: | (2972) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\chromium_ext.zip | |||
| (PID) Process: | (2972) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\omni_23_10_2024_.zip | |||
| (PID) Process: | (2972) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\Roblox.Account.Manager.3.7.2.zip | |||
| (PID) Process: | (2972) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (2972) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (2972) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (2972) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (2972) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\DialogEditHistory\ExtrPath |
| Operation: | delete value | Name: | 15 |
Value: | |||
| (PID) Process: | (2972) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\DialogEditHistory\ExtrPath |
| Operation: | delete value | Name: | 14 |
Value: | |||
Executable files
22
Suspicious files
257
Text files
42
Unknown types
28
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 5592 | Roblox Account Manager.exe | C:\Users\admin\AppData\Local\PuppeteerSharp\chrome-win64.zip | — | |
MD5:— | SHA256:— | |||
| 5592 | Roblox Account Manager.exe | C:\Users\admin\AppData\Local\PuppeteerSharp\Chrome\Win64-124.0.6367.201\chrome-win64\chrome.dll | — | |
MD5:— | SHA256:— | |||
| 2396 | Roblox Account Manager.exe | C:\Users\admin\Desktop\New folder\RAMTheme.ini | text | |
MD5:F18FA783F4D27E35E54E54417334BFB4 | SHA256:563EB35FD613F4298CD4DCEFF67652A13BA516A6244D9407C5709323C4CA4BB1 | |||
| 2396 | Roblox Account Manager.exe | C:\Users\admin\Desktop\New folder\log4.config | xml | |
MD5:E4659AC08AF3582A23F38BF6C562F841 | SHA256:E4B10630D9EC2AF508DE31752FBBC6816C7426C40A3E57F0A085CE7F42C77BD5 | |||
| 2396 | Roblox Account Manager.exe | C:\Users\admin\Desktop\New folder\Roblox Account Manager.exe.config | xml | |
MD5:0A86FA27D09E26491DBBB4FE27F4B410 | SHA256:2B6D99DB8369B0FF6372737D89D1C9E4101815B4168A3852C7B513F2897E7F3D | |||
| 2972 | WinRAR.exe | C:\Users\admin\Desktop\Roblox Account Manager.exe | executable | |
MD5:334728F32A1144C893FDFFC579A7709B | SHA256:BE9DDCDEDF8C36C64E6B0A32D2686B74A112913C54217CCAA46675BFD1DC82F1 | |||
| 5592 | Roblox Account Manager.exe | C:\Users\admin\AppData\Local\PuppeteerSharp\Chrome\Win64-124.0.6367.201\chrome-win64\icudtl.dat | — | |
MD5:— | SHA256:— | |||
| 5592 | Roblox Account Manager.exe | C:\Users\admin\Desktop\New folder\libsodium.dll | executable | |
MD5:4F6426E3626D5D46FB19C13043CB84DE | SHA256:7A960129F6D3F8D44B4C6BE27F587C29AA8BAFB9C4D3C85BB84A5F5D8FA6E2BA | |||
| 5592 | Roblox Account Manager.exe | C:\Users\admin\AppData\Local\PuppeteerSharp\Chrome\Win64-124.0.6367.201\chrome-win64\MEIPreload\manifest.json | binary | |
MD5:442699C95B20A60470421C6A4D29960F | SHA256:44844CF3DDE6E80087AE0E6BF0D9326D7EF7D23326D24AC83AF0850BE26923D2 | |||
| 5592 | Roblox Account Manager.exe | C:\Users\admin\AppData\Local\PuppeteerSharp\Chrome\Win64-124.0.6367.201\chrome-win64\chrome_elf.dll | executable | |
MD5:561916711C707FE011411FD3D2CF71A8 | SHA256:0D2CCF801CEABBA978A77238E1B79AFC9A66983A11C07E011F876C063A71FFDB | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
7
TCP/UDP connections
71
DNS requests
57
Threats
1
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
1176 | svchost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
5064 | SearchApp.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
4712 | MoUsoCoreWorker.exe | GET | 200 | 23.53.40.178:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
4712 | MoUsoCoreWorker.exe | GET | 200 | 173.223.117.131:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
1876 | SIHClient.exe | GET | 200 | 173.223.117.131:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
1668 | backgroundTaskHost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | whitelisted |
1876 | SIHClient.exe | GET | 200 | 173.223.117.131:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
4712 | MoUsoCoreWorker.exe | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
448 | RUXIMICS.exe | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4932 | svchost.exe | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
5064 | SearchApp.exe | 95.101.74.36:443 | www.bing.com | Akamai International B.V. | NL | whitelisted |
5064 | SearchApp.exe | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
1176 | svchost.exe | 20.190.159.68:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
1176 | svchost.exe | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
1076 | svchost.exe | 23.218.210.69:443 | go.microsoft.com | AKAMAI-AS | DE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
www.bing.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
login.live.com |
| whitelisted |
go.microsoft.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
arc.msn.com |
| whitelisted |
fd.api.iris.microsoft.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2192 | svchost.exe | Not Suspicious Traffic | INFO [ANY.RUN] Attempting to access raw user content on GitHub |
Process | Message |
|---|---|
chrome.exe | RecursiveDirectoryCreate( C:\Users\admin\AppData\Local\Temp\4mepntm1.wg5 directory exists )
|