| download: | BAv1377345.msi |
| Full analysis: | https://app.any.run/tasks/8f692a41-0b25-4aae-9d7f-dd14e38ae7b9 |
| Verdict: | Malicious activity |
| Analysis date: | March 11, 2020, 19:38:15 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-msi |
| File info: | Composite Document File V2 Document, Little Endian, Os: Windows, Version 10.0, MSI Installer, Last Printed: Fri Dec 11 11:47:44 2009, Create Time/Date: Fri Dec 11 11:47:44 2009, Last Saved Time/Date: Fri Dec 11 11:47:44 2009, Security: 0, Code page: 1252, Revision Number: {40B96690-2EC4-49DE-B555-E803BA188823}, Number of Words: 10, Subject: Browser Assistant, Author: Realistic Media Inc., Name of Creating Application: Advanced Installer 15.2 build 30c2e84376, Template: ;1033, Comments: This installer database contains the logic and data required to install Browser Assistant., Title: Installation Database, Keywords: Installer, MSI, Database, Number of Pages: 200 |
| MD5: | 55BB68BF5EE6062C65764B71B730D68E |
| SHA1: | 5052A044B8609A0FC46A0D7441F2D9299555DA43 |
| SHA256: | 49AA7A38BF93426F022F919AEA638A730829E51D312AB1D6D3AF9C97AC492709 |
| SSDEEP: | 393216:DcRqtpS6AQi1t2pJSleH9Bzs9J4zEeJejES00wx5poNHrdjlxyvXW7CN:IwSRQLpGeH349JUJej60ukxjlxyTN |
MALICIOUS
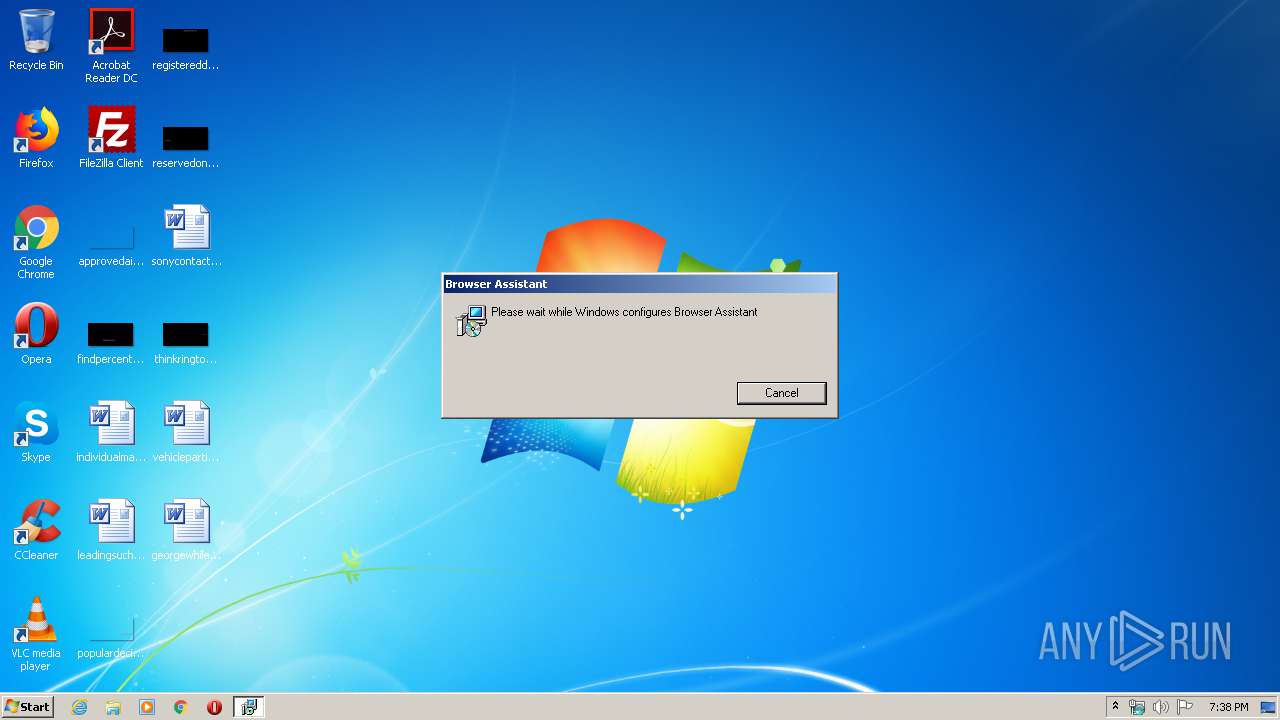
Application was dropped or rewritten from another process
- BrowserAssistant.exe (PID: 2320)
Loads dropped or rewritten executable
- BrowserAssistant.exe (PID: 2320)
Writes to a start menu file
- msiexec.exe (PID: 3956)
SUSPICIOUS
Executed as Windows Service
- vssvc.exe (PID: 3716)
Uses TASKKILL.EXE to kill process
- powershell.exe (PID: 2888)
Creates files in the user directory
- powershell.exe (PID: 2888)
- powershell.exe (PID: 3964)
- powershell.exe (PID: 2580)
- powershell.exe (PID: 3120)
- powershell.exe (PID: 2788)
- msiexec.exe (PID: 3956)
Executes PowerShell scripts
- MsiExec.exe (PID: 3292)
Reads Environment values
- MsiExec.exe (PID: 3292)
Executable content was dropped or overwritten
- msiexec.exe (PID: 3956)
INFO
Loads dropped or rewritten executable
- MsiExec.exe (PID: 3292)
Low-level read access rights to disk partition
- vssvc.exe (PID: 3716)
Searches for installed software
- msiexec.exe (PID: 3956)
Application launched itself
- msiexec.exe (PID: 3956)
Creates a software uninstall entry
- msiexec.exe (PID: 3956)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .msi | | | Microsoft Windows Installer (81.9) |
|---|---|---|
| .mst | | | Windows SDK Setup Transform Script (9.2) |
| .msp | | | Windows Installer Patch (7.6) |
| .msi | | | Microsoft Installer (100) |
EXIF
FlashPix
| LastPrinted: | 2009:12:11 11:47:44 |
|---|---|
| CreateDate: | 2009:12:11 11:47:44 |
| ModifyDate: | 2009:12:11 11:47:44 |
| Security: | None |
| CodePage: | Windows Latin 1 (Western European) |
| RevisionNumber: | {40B96690-2EC4-49DE-B555-E803BA188823} |
| Words: | 10 |
| Subject: | Browser Assistant |
| Author: | Realistic Media Inc. |
| LastModifiedBy: | - |
| Software: | Advanced Installer 15.2 build 30c2e84376 |
| Template: | ;1033 |
| Comments: | This installer database contains the logic and data required to install Browser Assistant. |
| Title: | Installation Database |
| Keywords: | Installer, MSI, Database |
| Pages: | 200 |
Total processes
51
Monitored processes
11
Malicious processes
2
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 2280 | "C:\Windows\system32\taskkill.exe" /F /IM BrowserAssistant.exe | C:\Windows\system32\taskkill.exe | — | powershell.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Terminates Processes Exit code: 128 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2320 | "C:\Users\admin\AppData\Roaming\Browser Assistant\BrowserAssistant.exe" | C:\Users\admin\AppData\Roaming\Browser Assistant\BrowserAssistant.exe | msiexec.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Description: BrowserAssistant Exit code: 0 Version: 1.37.7345.30189 Modules
| |||||||||||||||
| 2580 | -NoProfile -Noninteractive -ExecutionPolicy Bypass -File "C:\Users\admin\AppData\Local\Temp\pssD525.ps1" | C:\Windows\system32\WindowsPowerShell\v1.0\powershell.exe | — | MsiExec.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2788 | -NoProfile -Noninteractive -ExecutionPolicy Bypass -File "C:\Users\admin\AppData\Local\Temp\pss4617.ps1" | C:\Windows\system32\WindowsPowerShell\v1.0\powershell.exe | MsiExec.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2888 | -NoProfile -Noninteractive -ExecutionPolicy Bypass -File "C:\Users\admin\AppData\Local\Temp\pssCE1C.ps1" | C:\Windows\system32\WindowsPowerShell\v1.0\powershell.exe | — | MsiExec.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Exit code: 128 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3120 | -NoProfile -Noninteractive -ExecutionPolicy Bypass -File "C:\Users\admin\AppData\Local\Temp\pss1743.ps1" | C:\Windows\system32\WindowsPowerShell\v1.0\powershell.exe | MsiExec.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3292 | C:\Windows\system32\MsiExec.exe -Embedding DCA40E2EA77DDBC15F9FDD81B234E903 | C:\Windows\system32\MsiExec.exe | — | msiexec.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows® installer Exit code: 0 Version: 5.0.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3716 | C:\Windows\system32\vssvc.exe | C:\Windows\system32\vssvc.exe | — | services.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Microsoft® Volume Shadow Copy Service Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3928 | "C:\Windows\System32\msiexec.exe" /i "C:\Users\admin\AppData\Local\Temp\BAv1377345.msi" | C:\Windows\System32\msiexec.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows® installer Exit code: 0 Version: 5.0.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3956 | C:\Windows\system32\msiexec.exe /V | C:\Windows\system32\msiexec.exe | services.exe | ||||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows® installer Exit code: 0 Version: 5.0.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
Total events
2 693
Read events
1 751
Write events
930
Delete events
12
Modification events
| (PID) Process: | (3928) msiexec.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\12B\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (3956) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\services\VSS\Diag\SystemRestore |
| Operation: | write | Name: | SrCreateRp (Enter) |
Value: 4000000000000000B2BB48ACDCF7D501740F0000AC0C0000D5070000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (3956) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\services\VSS\Diag\SPP |
| Operation: | write | Name: | SppCreate (Enter) |
Value: 4000000000000000B2BB48ACDCF7D501740F0000AC0C0000D0070000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (3956) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\SPP |
| Operation: | write | Name: | LastIndex |
Value: 34 | |||
| (PID) Process: | (3956) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\services\VSS\Diag\SPP |
| Operation: | write | Name: | SppGatherWriterMetadata (Enter) |
Value: 40000000000000003E4290ACDCF7D501740F0000AC0C0000D3070000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (3956) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\services\VSS\Diag\VssapiPublisher |
| Operation: | write | Name: | IDENTIFY (Enter) |
Value: 40000000000000003E4290ACDCF7D501740F000078010000E8030000010000000000000000000000DCAD6DEF728B5A4DB030C8F2E3FE129F0000000000000000 | |||
| (PID) Process: | (3716) vssvc.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\services\VSS\Diag\ASR Writer |
| Operation: | write | Name: | IDENTIFY (Enter) |
Value: 400000000000000068B7A5ACDCF7D501840E0000740B0000E8030000010000000100000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (3716) vssvc.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\services\VSS\Diag\COM+ REGDB Writer |
| Operation: | write | Name: | IDENTIFY (Enter) |
Value: 400000000000000068B7A5ACDCF7D501840E0000880F0000E8030000010000000100000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (3716) vssvc.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\services\VSS\Diag\Registry Writer |
| Operation: | write | Name: | IDENTIFY (Enter) |
Value: 400000000000000068B7A5ACDCF7D501840E000098060000E8030000010000000100000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (3716) vssvc.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\services\VSS\Diag\Shadow Copy Optimization Writer |
| Operation: | write | Name: | IDENTIFY (Enter) |
Value: 400000000000000068B7A5ACDCF7D501840E0000A00C0000E8030000010000000100000000000000000000000000000000000000000000000000000000000000 | |||
Executable files
72
Suspicious files
16
Text files
2 014
Unknown types
3
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3956 | msiexec.exe | C:\System Volume Information\SPP\metadata-2 | — | |
MD5:— | SHA256:— | |||
| 3956 | msiexec.exe | C:\Windows\Installer\a6bf8f.msi | — | |
MD5:— | SHA256:— | |||
| 3964 | powershell.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\Z4WRBXLY4SHQSSREWQ5B.temp | — | |
MD5:— | SHA256:— | |||
| 3716 | vssvc.exe | C: | — | |
MD5:— | SHA256:— | |||
| 3292 | MsiExec.exe | C:\Users\admin\AppData\Local\Temp\ProC445.tmp | — | |
MD5:— | SHA256:— | |||
| 2888 | powershell.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\CPNKB2U9YYL8UMIE7YVW.temp | — | |
MD5:— | SHA256:— | |||
| 3292 | MsiExec.exe | C:\Users\admin\AppData\Local\Temp\ProCE1D.tmp | — | |
MD5:— | SHA256:— | |||
| 3956 | msiexec.exe | C:\Windows\Installer\MSID4B1.tmp | — | |
MD5:— | SHA256:— | |||
| 3956 | msiexec.exe | C:\Windows\Installer\MSID4C2.tmp | — | |
MD5:— | SHA256:— | |||
| 2580 | powershell.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\M63WUALZ6YHO9D6L8ILF.temp | — | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
5
TCP/UDP connections
6
DNS requests
2
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
3964 | powershell.exe | POST | 200 | 52.33.155.26:80 | http://logs-01.loggly.com/inputs/1f667d94-35d0-4958-aa21-54e5d3fd784d/tag/browser-assistant/ | US | text | 19 b | whitelisted |
2788 | powershell.exe | POST | — | 52.33.155.26:80 | http://logs-01.loggly.com/inputs/1f667d94-35d0-4958-aa21-54e5d3fd784d/tag/browser-assistant/ | US | — | — | whitelisted |
3120 | powershell.exe | POST | — | 52.33.155.26:80 | http://logs-01.loggly.com/inputs/1f667d94-35d0-4958-aa21-54e5d3fd784d/tag/browser-assistant/ | US | — | — | whitelisted |
2320 | BrowserAssistant.exe | GET | 404 | 99.86.3.11:80 | http://pads289.net/ext/fhg?key= | US | — | — | shared |
2320 | BrowserAssistant.exe | POST | 200 | 52.33.155.26:80 | http://logs-01.loggly.com/inputs/1f667d94-35d0-4958-aa21-54e5d3fd784d/tag/browser-assistant/ | US | text | 19 b | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
3964 | powershell.exe | 52.33.155.26:80 | logs-01.loggly.com | Amazon.com, Inc. | US | unknown |
3120 | powershell.exe | 52.33.155.26:80 | logs-01.loggly.com | Amazon.com, Inc. | US | unknown |
2320 | BrowserAssistant.exe | 52.33.155.26:80 | logs-01.loggly.com | Amazon.com, Inc. | US | unknown |
2788 | powershell.exe | 52.33.155.26:80 | logs-01.loggly.com | Amazon.com, Inc. | US | unknown |
2320 | BrowserAssistant.exe | 99.86.3.11:80 | pads289.net | AT&T Services, Inc. | US | suspicious |
DNS requests
Domain | IP | Reputation |
|---|---|---|
logs-01.loggly.com |
| whitelisted |
pads289.net |
| shared |