| File name: | cpuz_x64.exe |
| Full analysis: | https://app.any.run/tasks/7367f04f-7d0b-4f12-bd51-7f146c339948 |
| Verdict: | Malicious activity |
| Analysis date: | August 13, 2024, 10:04:39 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows |
| MD5: | E0A9F8364B0BAD7067CB29C6B883D15B |
| SHA1: | E036B184FD0FE4877E1F414A5225FD6D97A3B4FE |
| SHA256: | 499DD1973C114811F73F2C843FCBC8ECEA28D921672A82589CECAF9539C05943 |
| SSDEEP: | 98304:qP3oCZukctcEEqyco8+UxGy7FDEAoV7xzadDepzjHxKBa1bgJlVT904xgFx0ZuWv:PDDB904g0Zn |
MALICIOUS
UAC/LUA settings modification
- icsys.ico.exe (PID: 6456)
- cpuz_x64.exe (PID: 6408)
- wininit.exe (PID: 6896)
- spoolsv.exe (PID: 7128)
- svchost.exe (PID: 6312)
Changes the autorun value in the registry
- icsys.ico.exe (PID: 6456)
Changes the login/logoff helper path in the registry
- icsys.ico.exe (PID: 6456)
- wininit.exe (PID: 6896)
- svchost.exe (PID: 6312)
Changes appearance of the Explorer extensions
- wininit.exe (PID: 6896)
- svchost.exe (PID: 6312)
SUSPICIOUS
Executable content was dropped or overwritten
- cpuz_x64.exe (PID: 6408)
- icsys.ico.exe (PID: 6456)
- cpuz_x64.exe (PID: 6712)
- wininit.exe (PID: 6896)
- spoolsv.exe (PID: 7128)
Drops the executable file immediately after the start
- cpuz_x64.exe (PID: 6408)
- icsys.ico.exe (PID: 6456)
- cpuz_x64.exe (PID: 6712)
- wininit.exe (PID: 6896)
- spoolsv.exe (PID: 7128)
Starts itself from another location
- cpuz_x64.exe (PID: 6408)
- wininit.exe (PID: 6896)
- icsys.ico.exe (PID: 6456)
- spoolsv.exe (PID: 7128)
Starts application with an unusual extension
- cpuz_x64.exe (PID: 6408)
Reads security settings of Internet Explorer
- ShellExperienceHost.exe (PID: 6544)
- icsys.ico.exe (PID: 6456)
- cpuz_x64.exe (PID: 6712)
- wininit.exe (PID: 6896)
- spoolsv.exe (PID: 7128)
Checks Windows Trust Settings
- cpuz_x64.exe (PID: 6712)
Drops a system driver (possible attempt to evade defenses)
- cpuz_x64.exe (PID: 6712)
Reads the date of Windows installation
- cpuz_x64.exe (PID: 6712)
- icsys.ico.exe (PID: 6456)
- wininit.exe (PID: 6896)
- spoolsv.exe (PID: 7128)
The process creates files with name similar to system file names
- spoolsv.exe (PID: 7128)
INFO
Reads the computer name
- icsys.ico.exe (PID: 6456)
- cpuz_x64.exe (PID: 6408)
- ShellExperienceHost.exe (PID: 6544)
- cpuz_x64.exe (PID: 6712)
- spoolsv.exe (PID: 7128)
- wininit.exe (PID: 6896)
- spoolsv.exe (PID: 6288)
- svchost.exe (PID: 6312)
Process checks whether UAC notifications are on
- icsys.ico.exe (PID: 6456)
- cpuz_x64.exe (PID: 6408)
- wininit.exe (PID: 6896)
- spoolsv.exe (PID: 7128)
- svchost.exe (PID: 6312)
Checks supported languages
- icsys.ico.exe (PID: 6456)
- cpuz_x64.exe (PID: 6408)
- ShellExperienceHost.exe (PID: 6544)
- cpuz_x64.exe (PID: 6712)
- spoolsv.exe (PID: 7128)
- wininit.exe (PID: 6896)
- svchost.exe (PID: 6312)
- spoolsv.exe (PID: 6288)
Create files in a temporary directory
- cpuz_x64.exe (PID: 6408)
Creates files or folders in the user directory
- cpuz_x64.exe (PID: 6408)
- cpuz_x64.exe (PID: 6712)
- wininit.exe (PID: 6896)
Reads the machine GUID from the registry
- cpuz_x64.exe (PID: 6712)
Reads the software policy settings
- cpuz_x64.exe (PID: 6712)
Process checks computer location settings
- icsys.ico.exe (PID: 6456)
- wininit.exe (PID: 6896)
- spoolsv.exe (PID: 7128)
Checks proxy server information
- cpuz_x64.exe (PID: 6712)
Reads Environment values
- cpuz_x64.exe (PID: 6712)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Inno Setup installer (34.1) |
|---|---|---|
| .exe | | | InstallShield setup (13.3) |
| .exe | | | Win32 EXE PECompact compressed (generic) (12.9) |
| .exe | | | Win32 Executable (generic) (1.4) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2018:10:24 07:34:01+00:00 |
| ImageFileCharacteristics: | Executable, No line numbers, No symbols, Bytes reversed lo, 32-bit, Bytes reversed hi |
| PEType: | PE32 |
| LinkerVersion: | 2.25 |
| CodeSize: | 2472448 |
| InitializedDataSize: | 519168 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x25c7d4 |
| OSVersion: | 5 |
| ImageVersion: | - |
| SubsystemVersion: | 5 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 1.0.0.0 |
| ProductVersionNumber: | 1.0.0.0 |
| FileFlagsMask: | 0x003f |
| FileFlags: | (none) |
| FileOS: | Win32 |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | English (U.S.) |
| CharacterSet: | Windows, Latin1 |
| FileVersion: | 1.0.0.0 |
| ProductVersion: | 1.0.0.0 |
Total processes
138
Monitored processes
9
Malicious processes
5
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 6288 | "C:\Users\admin\appdata\roaming\spoolsv.exe" /SE | C:\Users\admin\AppData\Roaming\spoolsv.exe | — | wininit.exe | |||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Version: 1.0.0.0 Modules
| |||||||||||||||
| 6312 | "C:\windows\svchost.exe" | C:\Windows\svchost.exe | spoolsv.exe | ||||||||||||
User: admin Integrity Level: HIGH Version: 1.0.0.0 Modules
| |||||||||||||||
| 6360 | "C:\Users\admin\AppData\Local\Temp\cpuz_x64.exe" | C:\Users\admin\AppData\Local\Temp\cpuz_x64.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 3221226540 Version: 1.0.0.0 Modules
| |||||||||||||||
| 6408 | "C:\Users\admin\AppData\Local\Temp\cpuz_x64.exe" | C:\Users\admin\AppData\Local\Temp\cpuz_x64.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Version: 1.0.0.0 Modules
| |||||||||||||||
| 6456 | C:\Users\admin\AppData\Roaming\icsys.ico.exe | C:\Users\admin\AppData\Roaming\icsys.ico.exe | cpuz_x64.exe | ||||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Version: 1.0.0.0 Modules
| |||||||||||||||
| 6544 | "C:\WINDOWS\SystemApps\ShellExperienceHost_cw5n1h2txyewy\ShellExperienceHost.exe" -ServerName:App.AppXtk181tbxbce2qsex02s8tw7hfxa9xb3t.mca | C:\Windows\SystemApps\ShellExperienceHost_cw5n1h2txyewy\ShellExperienceHost.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Shell Experience Host Version: 10.0.19041.3758 (WinBuild.160101.0800) Modules
| |||||||||||||||
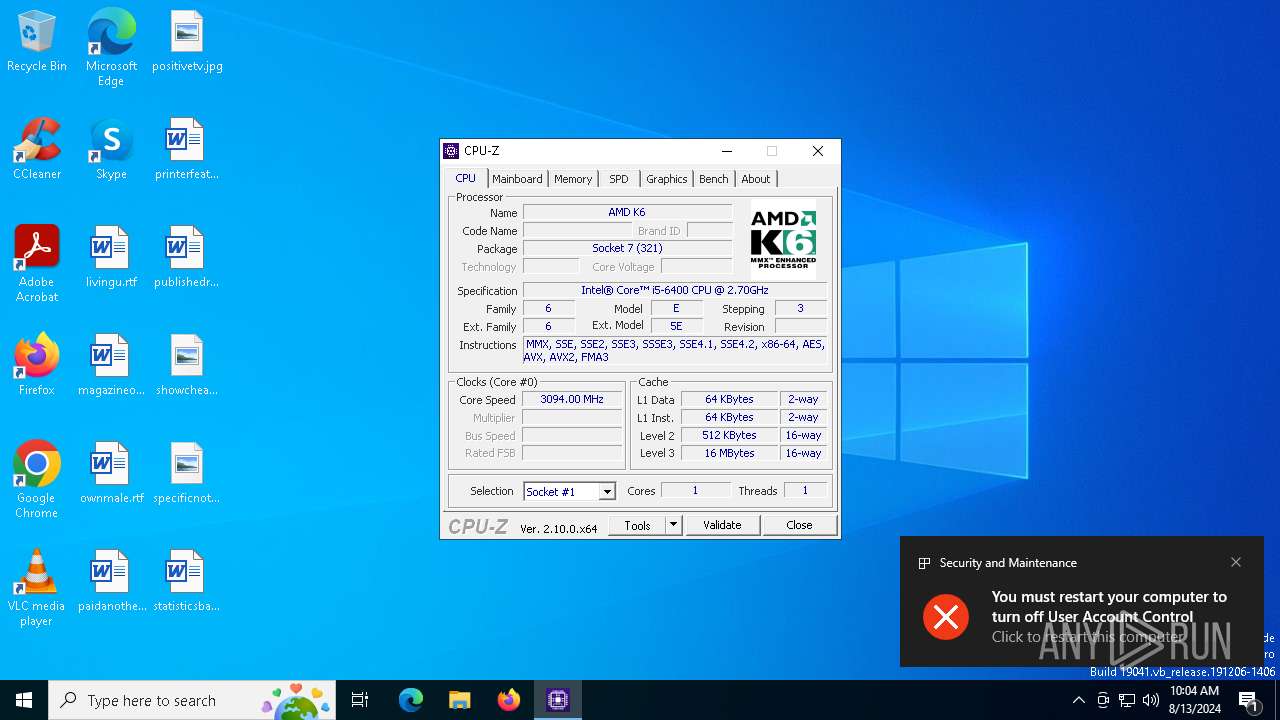
| 6712 | c:\users\admin\appdata\local\temp\cpuz_x64.exe | C:\Users\admin\AppData\Local\Temp\cpuz_x64.exe | cpuz_x64.exe | ||||||||||||
User: admin Company: CPUID Integrity Level: HIGH Description: CPU-Z Application Version: 2, 1, 0, 0 Modules
| |||||||||||||||
| 6896 | "C:\windows\wininit.exe" | C:\Windows\wininit.exe | icsys.ico.exe | ||||||||||||
User: admin Integrity Level: HIGH Version: 1.0.0.0 Modules
| |||||||||||||||
| 7128 | "C:\Users\admin\appdata\roaming\spoolsv.exe" /SE | C:\Users\admin\AppData\Roaming\spoolsv.exe | wininit.exe | ||||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Version: 1.0.0.0 Modules
| |||||||||||||||
Total events
10 088
Read events
10 013
Write events
71
Delete events
4
Modification events
| (PID) Process: | (6408) cpuz_x64.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Policies\System |
| Operation: | write | Name: | ConsentPromptBehaviorAdmin |
Value: 0 | |||
| (PID) Process: | (6408) cpuz_x64.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Policies\System |
| Operation: | write | Name: | EnableLUA |
Value: 0 | |||
| (PID) Process: | (6408) cpuz_x64.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Policies\System |
| Operation: | write | Name: | PromptOnSecureDesktop |
Value: 0 | |||
| (PID) Process: | (6456) icsys.ico.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Policies\System |
| Operation: | write | Name: | ConsentPromptBehaviorAdmin |
Value: 0 | |||
| (PID) Process: | (6456) icsys.ico.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Policies\System |
| Operation: | write | Name: | EnableLUA |
Value: 0 | |||
| (PID) Process: | (6456) icsys.ico.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Policies\System |
| Operation: | write | Name: | PromptOnSecureDesktop |
Value: 0 | |||
| (PID) Process: | (6456) icsys.ico.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer |
| Operation: | write | Name: | SlowContextMenuEntries |
Value: 6024B221EA3A6910A2DC08002B30309D0A010000BD0E0C47735D584D9CEDE91E22E23282770100000114020000000000C0000000000000468D0000006078A409B011A54DAFA526D86198A780390100009AD298B2EDA6DE11BA8CA68E55D895936E000000 | |||
| (PID) Process: | (6456) icsys.ico.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (6456) icsys.ico.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
| (PID) Process: | (6456) icsys.ico.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 1 | |||
Executable files
6
Suspicious files
2
Text files
3
Unknown types
1
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 6408 | cpuz_x64.exe | C:\Users\admin\AppData\Roaming\icsys.ico.exe | executable | |
MD5:625123D968314B6D46D1BEC732E6750A | SHA256:1B687151B4C4A69CC386EDE0E93991DCAD76C529E8D27B18A3624C297E8FD8A1 | |||
| 6456 | icsys.ico.exe | C:\Windows\wininit.exe | executable | |
MD5:625123D968314B6D46D1BEC732E6750A | SHA256:1B687151B4C4A69CC386EDE0E93991DCAD76C529E8D27B18A3624C297E8FD8A1 | |||
| 7128 | spoolsv.exe | C:\Windows\svchost.exe | executable | |
MD5:625123D968314B6D46D1BEC732E6750A | SHA256:1B687151B4C4A69CC386EDE0E93991DCAD76C529E8D27B18A3624C297E8FD8A1 | |||
| 6712 | cpuz_x64.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\INetCache\IE\AH8CR9J5\cpuid[1].ver | text | |
MD5:004BFA2894DBE6DD62B015B3E2CECD1B | SHA256:DE73B539E869A34A3AB54A83642284EC5CB067F12846A90AA8247F62B9B2CAA9 | |||
| 6712 | cpuz_x64.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\103621DE9CD5414CC2538780B4B75751 | binary | |
MD5:3DFCA46E00FFA4795C72A41375F159D3 | SHA256:DCBA1A505396539BAC40A7253C9F5DCCF06CBB79957E21D56305E1FC3AF5F40E | |||
| 6896 | wininit.exe | C:\Users\admin\AppData\Roaming\spoolsv.exe | executable | |
MD5:625123D968314B6D46D1BEC732E6750A | SHA256:1B687151B4C4A69CC386EDE0E93991DCAD76C529E8D27B18A3624C297E8FD8A1 | |||
| 6712 | cpuz_x64.exe | C:\Windows\Temp\cpuz_driver_6712.log | text | |
MD5:F984605BE6B69FF678CAAE40B1FE0E0A | SHA256:55F8D9530CB14690868D406B3078DE8625E22FF8F225CEFBD237B080B35AAB31 | |||
| 6712 | cpuz_x64.exe | C:\Windows\Temp\cpuz159\cpuz159_x64.sys | executable | |
MD5:7D571663F62629E6945D600E2A050464 | SHA256:A0B2F26BDDD76F8A8B73713099EF5C71864A10B86B8E46EBD7AECB12B627B703 | |||
| 6712 | cpuz_x64.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\A4EEE1B0550754EDC37DCC5F80FA19DF | binary | |
MD5:8D35DA6671B566C1D9808209661628A9 | SHA256:366E909B27D131B7E67C6F1B773596B9957F023B29605C0F938CD141A63A8ADA | |||
| 6712 | cpuz_x64.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\A4EEE1B0550754EDC37DCC5F80FA19DF | der | |
MD5:62D8EFE6E2C7607FBFC8C782673756C1 | SHA256:B6A3102CF5FEA340AD88108A34BCF545AA7FF998EDEB005BD03243D20A1F3F21 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
5
TCP/UDP connections
40
DNS requests
17
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
5336 | SearchApp.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
6712 | cpuz_x64.exe | GET | 200 | 184.24.77.54:80 | http://r11.o.lencr.org/MFMwUTBPME0wSzAJBgUrDgMCGgUABBQaUrm0WeTDM5ghfoZtS72KO9ZnzgQUCLkRO6XQhRi06g%2BgrZ%2BGHo78OCcCEgSTi%2FCGxZ2Esn2oh5KTXh7Xlg%3D%3D | unknown | — | — | whitelisted |
3276 | svchost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
2136 | backgroundTaskHost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | whitelisted |
1748 | backgroundTaskHost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
— | — | 192.168.100.255:138 | — | — | — | whitelisted |
— | — | 239.255.255.250:1900 | — | — | — | whitelisted |
3508 | svchost.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
5244 | RUXIMICS.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
2120 | MoUsoCoreWorker.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
6712 | cpuz_x64.exe | 195.154.81.43:443 | download.cpuid.com | Online S.a.s. | FR | unknown |
— | — | 184.24.77.54:80 | r11.o.lencr.org | Akamai International B.V. | DE | unknown |
5336 | SearchApp.exe | 104.126.37.128:443 | www.bing.com | Akamai International B.V. | DE | unknown |
5336 | SearchApp.exe | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
3260 | svchost.exe | 40.113.103.199:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
download.cpuid.com |
| whitelisted |
r11.o.lencr.org |
| whitelisted |
www.bing.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
login.live.com |
| whitelisted |
th.bing.com |
| whitelisted |
fd.api.iris.microsoft.com |
| whitelisted |