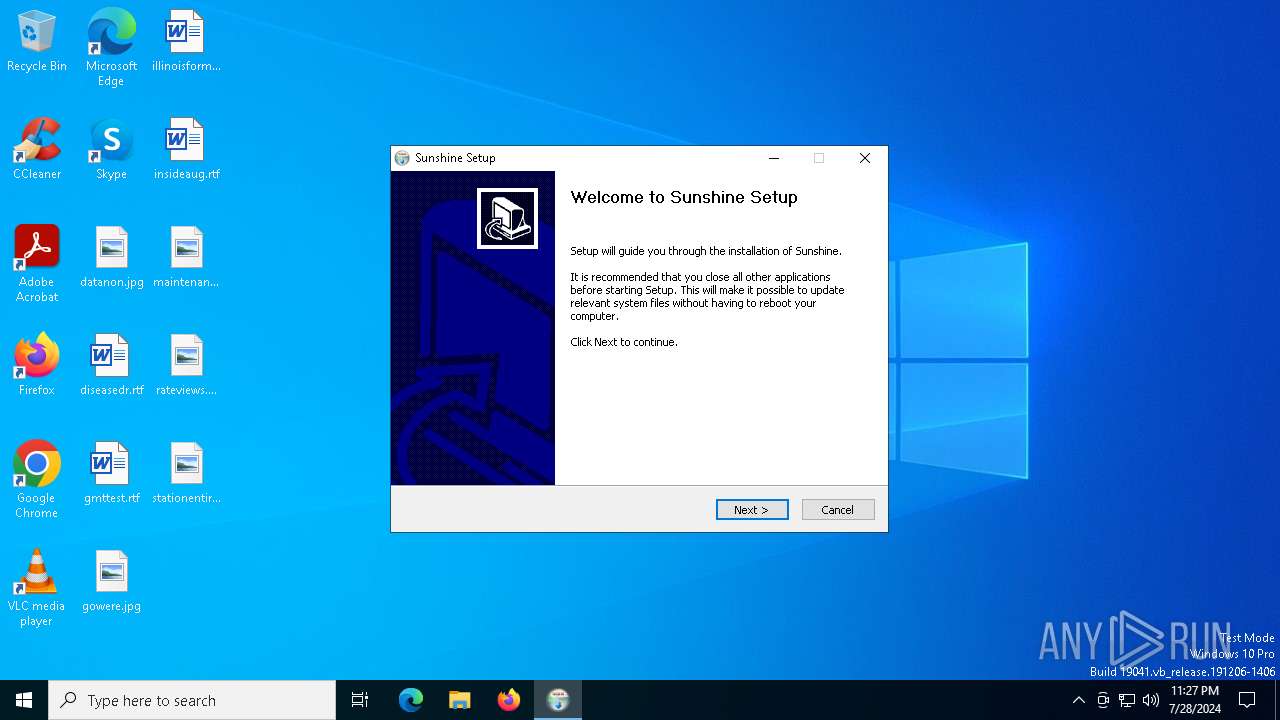
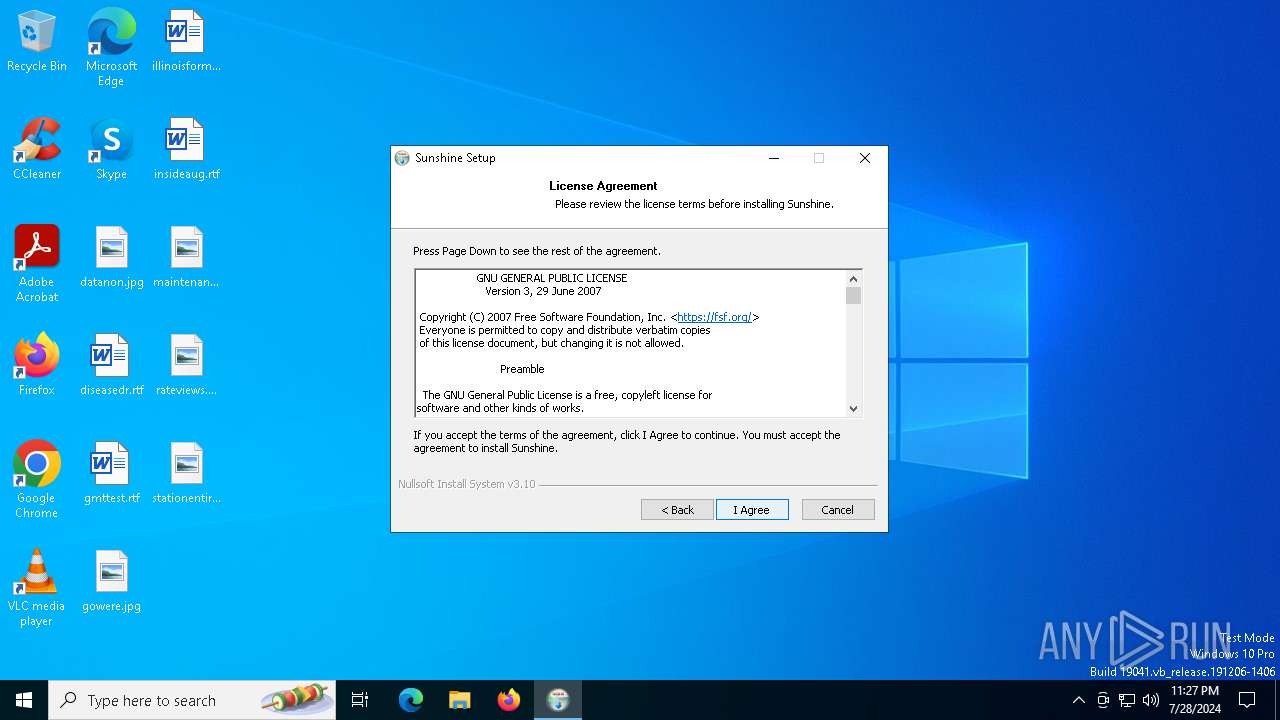
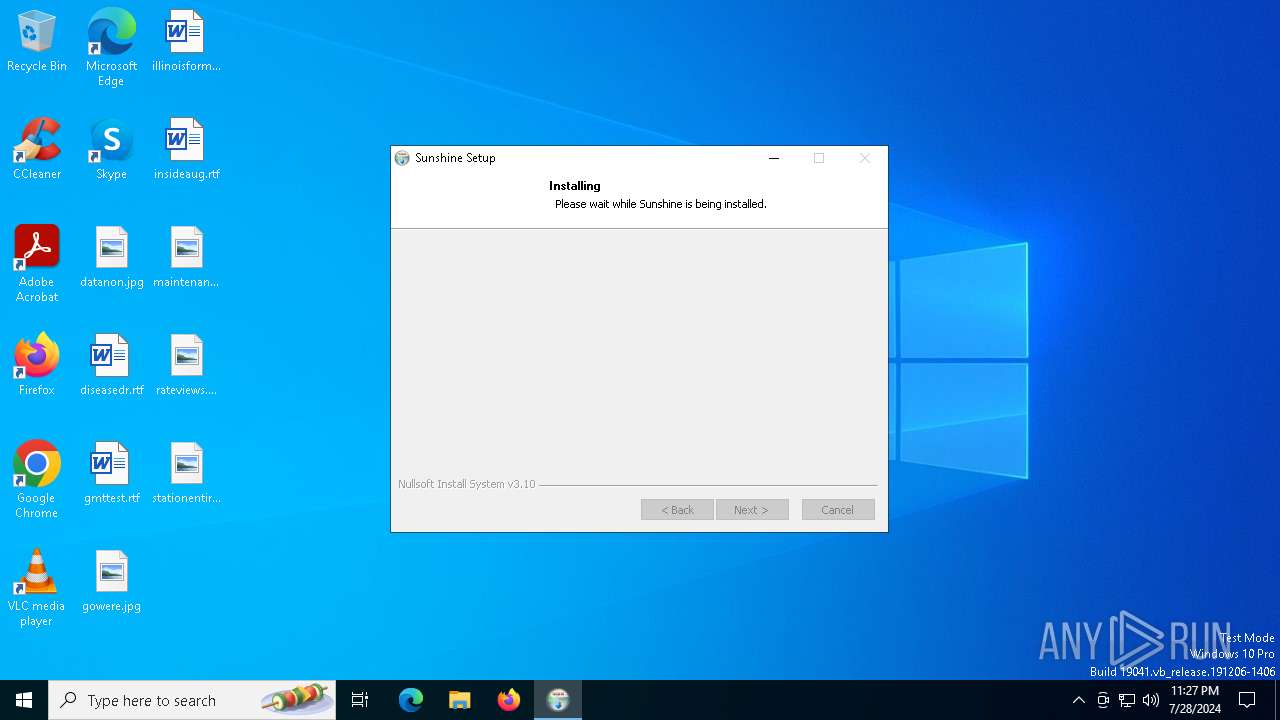
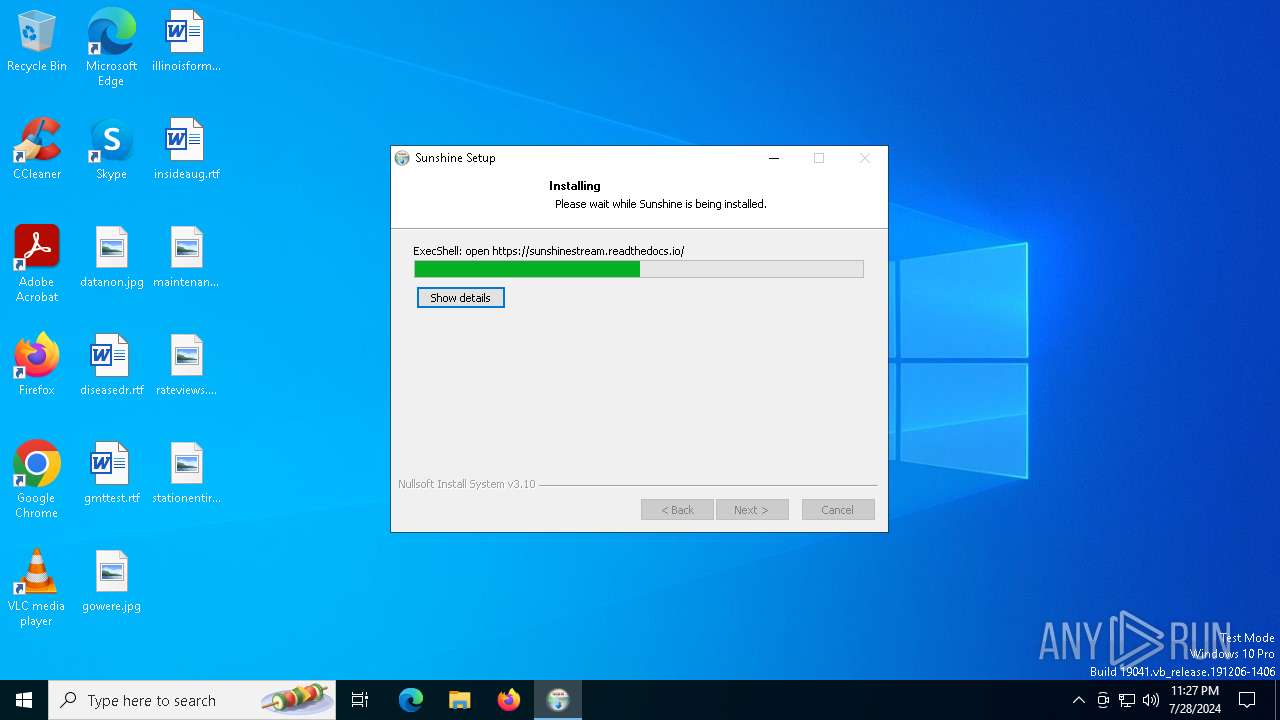
| File name: | sunshine-windows-installer.exe |
| Full analysis: | https://app.any.run/tasks/59345b5c-8bb7-459e-b0dc-8ac64a2204cb |
| Verdict: | Malicious activity |
| Analysis date: | July 28, 2024, 23:27:08 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32+ executable (GUI) x86-64 (stripped to external PDB), for MS Windows |
| MD5: | B3A9D2D2C677F7AF2C3AC3DE54B93798 |
| SHA1: | 8E2DEBBE73EEDF9C00F1E10F393F4D9D9E6B9228 |
| SHA256: | 499A907E93B40F015534958E8F2BB1D13E9C1583C228A458E5F81D8703185977 |
| SSDEEP: | 98304:oprGgqBUZWw1iei8tLmRKAKLTwM3Ut4R/lH3UdXx9uPYByf4OJvMx+9rkKcyiVdv:2TastXICriMNgMiYz28ViPCPce4 |
MALICIOUS
Drops the executable file immediately after the start
- sunshine-windows-installer.exe (PID: 1712)
- curl.exe (PID: 6232)
- virtual_gamepad.exe (PID: 7772)
- msiexec.exe (PID: 7860)
- drvinst.exe (PID: 8712)
- nefconw.exe (PID: 8644)
Starts NET.EXE for service management
- net.exe (PID: 8912)
- cmd.exe (PID: 8892)
- net.exe (PID: 9040)
SUSPICIOUS
Executable content was dropped or overwritten
- sunshine-windows-installer.exe (PID: 1712)
- virtual_gamepad.exe (PID: 7772)
- curl.exe (PID: 6232)
- nefconw.exe (PID: 8644)
- drvinst.exe (PID: 8712)
Reads security settings of Internet Explorer
- sunshine-windows-installer.exe (PID: 1712)
- virtual_gamepad.exe (PID: 7772)
Uses ICACLS.EXE to modify access control lists
- ns5945.tmp (PID: 1136)
- cmd.exe (PID: 6772)
Creates a software uninstall entry
- sunshine-windows-installer.exe (PID: 1712)
Starts application with an unusual extension
- sunshine-windows-installer.exe (PID: 1712)
Starts CMD.EXE for commands execution
- ns5A30.tmp (PID: 2960)
- ns5C64.tmp (PID: 2984)
- ns6231.tmp (PID: 7584)
- cmd.exe (PID: 7672)
- nsEAAC.tmp (PID: 8836)
Executing commands from a ".bat" file
- ns5A30.tmp (PID: 2960)
- ns5C64.tmp (PID: 2984)
- ns6231.tmp (PID: 7584)
- nsEAAC.tmp (PID: 8836)
Uses NETSH.EXE to add a firewall rule or allowed programs
- cmd.exe (PID: 1388)
Starts POWERSHELL.EXE for commands execution
- cmd.exe (PID: 7672)
Application launched itself
- cmd.exe (PID: 7672)
Using 'findstr.exe' to search for text patterns in files and output
- cmd.exe (PID: 2748)
The executable file from the user directory is run by the CMD process
- virtual_gamepad.exe (PID: 7772)
Checks Windows Trust Settings
- virtual_gamepad.exe (PID: 7772)
Reads the Windows owner or organization settings
- virtual_gamepad.exe (PID: 7772)
Executes as Windows Service
- VSSVC.exe (PID: 7232)
- sunshinesvc.exe (PID: 9080)
Drops a system driver (possible attempt to evade defenses)
- nefconw.exe (PID: 8644)
- msiexec.exe (PID: 7860)
- virtual_gamepad.exe (PID: 7772)
- drvinst.exe (PID: 8712)
Process drops legitimate windows executable
- virtual_gamepad.exe (PID: 7772)
Starts SC.EXE for service management
- cmd.exe (PID: 8892)
INFO
Create files in a temporary directory
- sunshine-windows-installer.exe (PID: 1712)
- curl.exe (PID: 6232)
- virtual_gamepad.exe (PID: 7772)
Checks supported languages
- sunshine-windows-installer.exe (PID: 1712)
- ns5945.tmp (PID: 1136)
- ns5A30.tmp (PID: 2960)
- ns5C64.tmp (PID: 2984)
- ns6231.tmp (PID: 7584)
- identity_helper.exe (PID: 7556)
- curl.exe (PID: 4548)
- curl.exe (PID: 6232)
- virtual_gamepad.exe (PID: 7772)
- msiexec.exe (PID: 8048)
- msiexec.exe (PID: 7860)
Reads the computer name
- sunshine-windows-installer.exe (PID: 1712)
- identity_helper.exe (PID: 7556)
- curl.exe (PID: 4548)
- virtual_gamepad.exe (PID: 7772)
- curl.exe (PID: 6232)
- msiexec.exe (PID: 8048)
- msiexec.exe (PID: 7860)
Creates files in the program directory
- sunshine-windows-installer.exe (PID: 1712)
- cmd.exe (PID: 6772)
- virtual_gamepad.exe (PID: 7772)
Reads Microsoft Office registry keys
- sunshine-windows-installer.exe (PID: 1712)
- msedge.exe (PID: 6136)
- msedge.exe (PID: 3940)
Manual execution by a user
- msedge.exe (PID: 3940)
Application launched itself
- msedge.exe (PID: 6136)
- msedge.exe (PID: 3940)
Reads Environment values
- identity_helper.exe (PID: 7556)
- virtual_gamepad.exe (PID: 7772)
- msiexec.exe (PID: 8048)
Script raised an exception (POWERSHELL)
- powershell.exe (PID: 7804)
Checks proxy server information
- reg.exe (PID: 7200)
- virtual_gamepad.exe (PID: 7772)
Reads the software policy settings
- virtual_gamepad.exe (PID: 7772)
Reads the machine GUID from the registry
- virtual_gamepad.exe (PID: 7772)
Creates files or folders in the user directory
- virtual_gamepad.exe (PID: 7772)
Executable content was dropped or overwritten
- msiexec.exe (PID: 7860)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win64 Executable (generic) (87.3) |
|---|---|---|
| .exe | | | Generic Win/DOS Executable (6.3) |
| .exe | | | DOS Executable Generic (6.3) |
EXIF
EXE
| MachineType: | AMD AMD64 |
|---|---|
| TimeStamp: | 2024:05:28 20:33:36+00:00 |
| ImageFileCharacteristics: | No relocs, Executable, No line numbers, No symbols, Large address aware, No debug |
| PEType: | PE32+ |
| LinkerVersion: | 2.42 |
| CodeSize: | 35840 |
| InitializedDataSize: | 73728 |
| UninitializedDataSize: | 402432 |
| EntryPoint: | 0x4280 |
| OSVersion: | 4 |
| ImageVersion: | 6 |
| SubsystemVersion: | 5.2 |
| Subsystem: | Windows GUI |
Total processes
228
Monitored processes
87
Malicious processes
7
Suspicious processes
2
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1112 | icacls "C:\Program Files\Sunshine" /reset | C:\Windows\System32\icacls.exe | — | ns5945.tmp | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1136 | "C:\Users\admin\AppData\Local\Temp\nsp11EA.tmp\ns5945.tmp" icacls "C:\Program Files\Sunshine" /reset | C:\Users\admin\AppData\Local\Temp\nsp11EA.tmp\ns5945.tmp | — | sunshine-windows-installer.exe | |||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
| 1388 | C:\WINDOWS\system32\cmd.exe /c ""C:\Program Files\Sunshine\scripts\add-firewall-rule.bat"" | C:\Windows\System32\cmd.exe | — | ns5C64.tmp | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1468 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=gpu-process --no-appcompat-clear --gpu-preferences=WAAAAAAAAADgAAAMAAAAAAAAAAAAAAAAAABgAAAAAAA4AAAAAAAAAAAAAAAEAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAGAAAAAAAAAAYAAAAAAAAAAgAAAAAAAAACAAAAAAAAAAIAAAAAAAAAA== --mojo-platform-channel-handle=2372 --field-trial-handle=2384,i,9919873122401949564,15552813696419212606,262144 --variations-seed-version /prefetch:2 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
| 1712 | "C:\Users\admin\AppData\Local\Temp\sunshine-windows-installer.exe" | C:\Users\admin\AppData\Local\Temp\sunshine-windows-installer.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: HIGH Modules
| |||||||||||||||
| 2424 | C:\WINDOWS\System32\slui.exe -Embedding | C:\Windows\System32\slui.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Activation Client Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2748 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=renderer --no-appcompat-clear --lang=en-US --js-flags=--ms-user-locale= --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=5 --mojo-platform-channel-handle=3788 --field-trial-handle=2440,i,15253032227465673545,2868408939031417653,262144 --variations-seed-version /prefetch:1 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
| 2748 | C:\WINDOWS\system32\cmd.exe /c curl -s -L https://api.github.com/repos/nefarius/vigembus/releases/latest | findstr browser_download_url | C:\Windows\System32\cmd.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2960 | "C:\Users\admin\AppData\Local\Temp\nsp11EA.tmp\ns5A30.tmp" "C:\Program Files\Sunshine\scripts\migrate-config.bat" | C:\Users\admin\AppData\Local\Temp\nsp11EA.tmp\ns5A30.tmp | — | sunshine-windows-installer.exe | |||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
| 2968 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=chrome.mojom.UtilWin --lang=en-US --service-sandbox-type=none --no-appcompat-clear --mojo-platform-channel-handle=5976 --field-trial-handle=2440,i,15253032227465673545,2868408939031417653,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 | |||||||||||||||
Total events
25 841
Read events
25 732
Write events
98
Delete events
11
Modification events
| (PID) Process: | (1712) sunshine-windows-installer.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall\Sunshine |
| Operation: | write | Name: | DisplayName |
Value: Sunshine | |||
| (PID) Process: | (1712) sunshine-windows-installer.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall\Sunshine |
| Operation: | write | Name: | DisplayVersion |
Value: 0.0.0 | |||
| (PID) Process: | (1712) sunshine-windows-installer.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall\Sunshine |
| Operation: | write | Name: | Publisher |
Value: LizardByte | |||
| (PID) Process: | (1712) sunshine-windows-installer.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall\Sunshine |
| Operation: | write | Name: | UninstallString |
Value: "C:\Program Files\Sunshine\Uninstall.exe" | |||
| (PID) Process: | (1712) sunshine-windows-installer.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall\Sunshine |
| Operation: | write | Name: | NoRepair |
Value: 1 | |||
| (PID) Process: | (1712) sunshine-windows-installer.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall\Sunshine |
| Operation: | write | Name: | NoModify |
Value: 1 | |||
| (PID) Process: | (1712) sunshine-windows-installer.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall\Sunshine |
| Operation: | write | Name: | DisplayIcon |
Value: C:\Program Files\Sunshine\Sunshine.exe | |||
| (PID) Process: | (1712) sunshine-windows-installer.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall\Sunshine |
| Operation: | write | Name: | HelpLink |
Value: https://sunshinestream.readthedocs.io/en/latest/about/installation.html | |||
| (PID) Process: | (1712) sunshine-windows-installer.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall\Sunshine |
| Operation: | write | Name: | URLInfoAbout |
Value: https://app.lizardbyte.dev/Sunshine | |||
| (PID) Process: | (1712) sunshine-windows-installer.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall\Sunshine |
| Operation: | write | Name: | Contact |
Value: https://app.lizardbyte.dev/Sunshine/support | |||
Executable files
45
Suspicious files
110
Text files
120
Unknown types
21
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 1712 | sunshine-windows-installer.exe | C:\Users\admin\AppData\Local\Temp\nsp11EA.tmp\modern-header.bmp | image | |
MD5:92FCFB4F2E95D8BA0EC7DE564E62F68A | SHA256:1967D92ABD7EE2151CA9A50CEEF9210FDBF0023ECCEF294B2042F5FBBEE08067 | |||
| 1712 | sunshine-windows-installer.exe | C:\Program Files\Sunshine\sunshine.exe | executable | |
MD5:71EDA1FE1133CBF77D3CB3402E2DF3DE | SHA256:8D220B89010EDDD993F6E3EDE99E67FCC0984D9B09AC8489A180A06AD22E9559 | |||
| 1712 | sunshine-windows-installer.exe | C:\Users\admin\AppData\Local\Temp\nsp11EA.tmp\ioSpecial.ini | ini | |
MD5:E2D5070BC28DB1AC745613689FF86067 | SHA256:D95AED234F932A1C48A2B1B0D98C60CA31F962310C03158E2884AB4DDD3EA1E0 | |||
| 1712 | sunshine-windows-installer.exe | C:\Program Files\Sunshine\assets\apps.json | binary | |
MD5:4DEC1CF39B94CC2A310BEF765E607724 | SHA256:6AA14F95E7BA22B05A06ACB24C077DF2B0959DE43C201A686A5EF5A628FD6DE5 | |||
| 1712 | sunshine-windows-installer.exe | C:\Program Files\Sunshine\tools\sunshinesvc.exe | executable | |
MD5:417311259B8C0D984CA7A9976DE94202 | SHA256:C4B3F72771D96E4CFC6151E03648A024C781851CFC382A1CD80B73317E36DFCF | |||
| 1712 | sunshine-windows-installer.exe | C:\Users\admin\AppData\Local\Temp\nsp11EA.tmp\UserInfo.dll | executable | |
MD5:2C4D44DF9AEA8F958567D1F553BE57AB | SHA256:E4E377E4EE465CEB76764B20542EC59D780024B82765A7AE3338ACAA73C5D7B2 | |||
| 1712 | sunshine-windows-installer.exe | C:\Program Files\Sunshine\assets\shaders\directx\convert_yuv420_packed_uv_type0_ps.hlsl | text | |
MD5:920BFD762632909D51768DF25483356C | SHA256:897BC37D0319B5400E142EE5D04C7DD260AF1071040B4D8F0BB6DCA90C510A3E | |||
| 1712 | sunshine-windows-installer.exe | C:\Users\admin\AppData\Local\Temp\nsp11EA.tmp\modern-wizard.bmp | image | |
MD5:CBE40FD2B1EC96DAEDC65DA172D90022 | SHA256:3AD2DC318056D0A2024AF1804EA741146CFC18CC404649A44610CBF8B2056CF2 | |||
| 1712 | sunshine-windows-installer.exe | C:\Program Files\Sunshine\assets\shaders\directx\convert_yuv420_packed_uv_type0_ps_linear.hlsl | text | |
MD5:7BA99F704E3D336B7DA19EC698373F18 | SHA256:C0A67152C118E59C7B19BB55D180B3DBC7FC5841FC93688D799BD572F62997B8 | |||
| 1712 | sunshine-windows-installer.exe | C:\Program Files\Sunshine\zlib1.dll | executable | |
MD5:EE01439A96E6C269C5D3D42C46C4516E | SHA256:1DC85208162EE57FE97E892BB5160FE9588903992995F90ADC3A3A358DAC6FC6 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
14
TCP/UDP connections
75
DNS requests
63
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
7772 | virtual_gamepad.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSRXerF0eFeSWRripTgTkcJWMm7iQQUaDfg67Y7%2BF8Rhvv%2BYXsIiGX0TkICEA4sR33wtnOE7yQZOQX4O%2F0%3D | unknown | — | — | whitelisted |
4424 | svchost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
5368 | SearchApp.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
3848 | backgroundTaskHost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | whitelisted |
3676 | backgroundTaskHost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | whitelisted |
5368 | SearchApp.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEApDqVCbATUviZV57HIIulA%3D | unknown | — | — | whitelisted |
4132 | OfficeClickToRun.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | whitelisted |
760 | lsass.exe | GET | 200 | 104.18.38.233:80 | http://ocsp.comodoca.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBRTtU9uFqgVGHhJwXZyWCNXmVR5ngQUoBEKIz6W8Qfs4q8p74Klf9AwpLQCEFZnHQTqT5lMbxCBR1nSdZQ%3D | unknown | — | — | whitelisted |
760 | lsass.exe | GET | 200 | 104.18.38.233:80 | http://ocsp.sectigo.com/MFIwUDBOMEwwSjAJBgUrDgMCGgUABBTPlNxcMEqnlIVyH5VuZ4lawhZX3QQU9oUKOxGG4QR9DqoLLNLuzGR7e64CEQCL3A%2F%2FVHcvqtFzJz8jNiqv | unknown | — | — | whitelisted |
760 | lsass.exe | GET | 200 | 172.64.149.23:80 | http://ocsp.usertrust.com/MFIwUDBOMEwwSjAJBgUrDgMCGgUABBSr83eyJy3njhjVpn5bEpfc6MXawQQUOuEJhtTPGcKWdnRJdtzgNcZjY5oCEQDzZE5rbgBQI34JRr174fUd | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
1428 | svchost.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
— | — | 131.253.33.254:443 | a-ring-fallback.msedge.net | MICROSOFT-CORP-MSN-AS-BLOCK | US | unknown |
— | — | 104.126.37.136:443 | www.bing.com | Akamai International B.V. | DE | unknown |
1156 | slui.exe | 20.83.72.98:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
6012 | MoUsoCoreWorker.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
132 | RUXIMICS.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
— | — | 20.83.72.98:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
3952 | svchost.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
5368 | SearchApp.exe | 13.107.246.45:443 | fp-afd-nocache-ccp.azureedge.net | MICROSOFT-CORP-MSN-AS-BLOCK | US | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
t-ring-fdv2.msedge.net |
| unknown |
settings-win.data.microsoft.com |
| whitelisted |
a-ring-fallback.msedge.net |
| unknown |
www.bing.com |
| whitelisted |
google.com |
| whitelisted |
fp-afd-nocache-ccp.azureedge.net |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
login.live.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
fd.api.iris.microsoft.com |
| whitelisted |