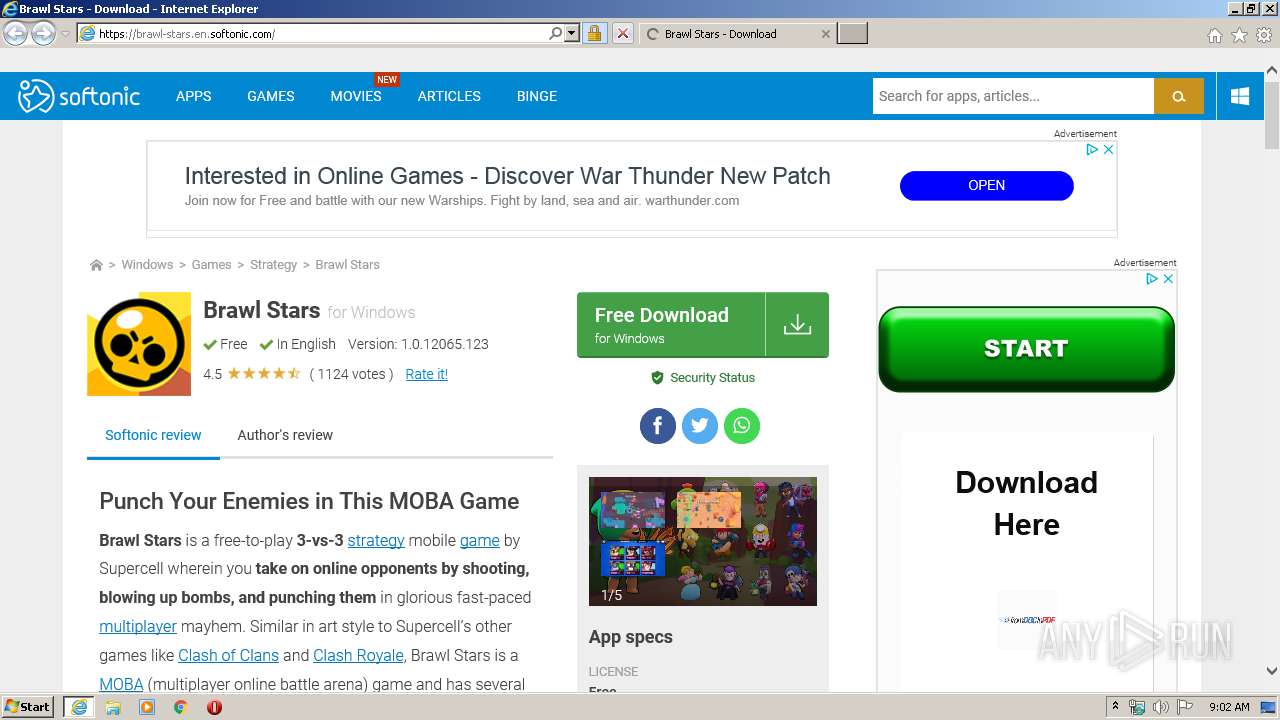
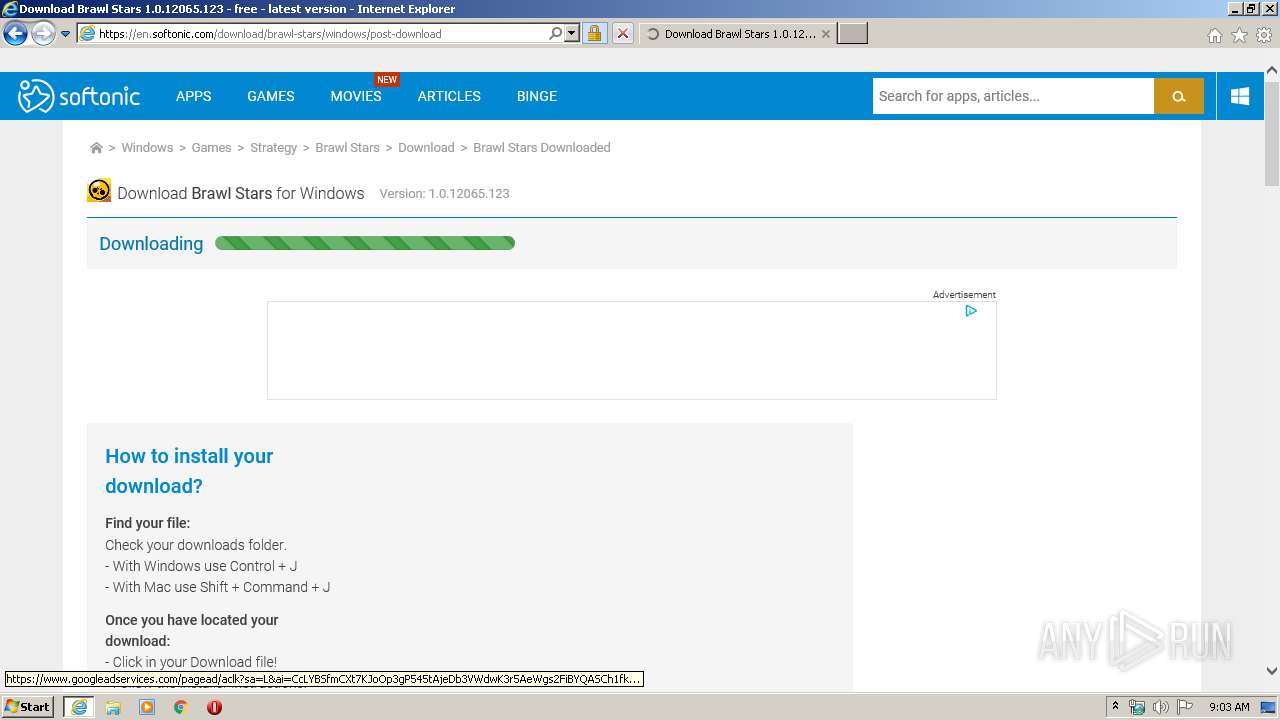
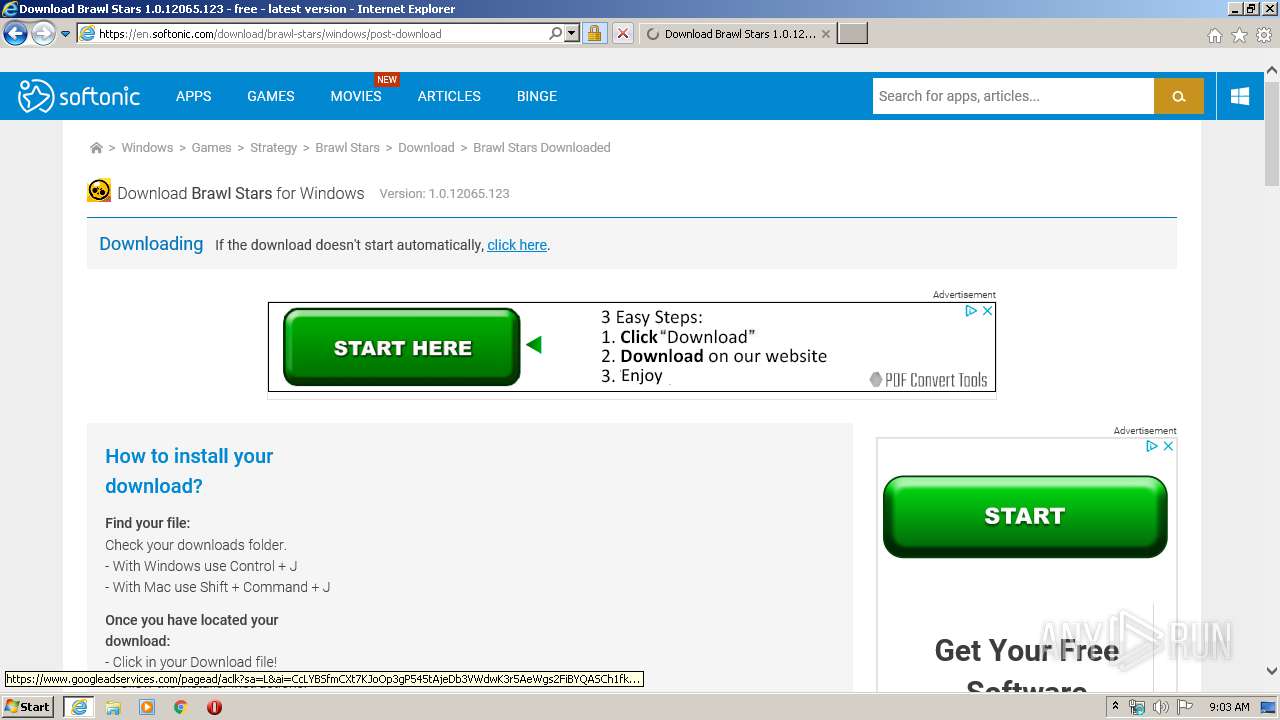
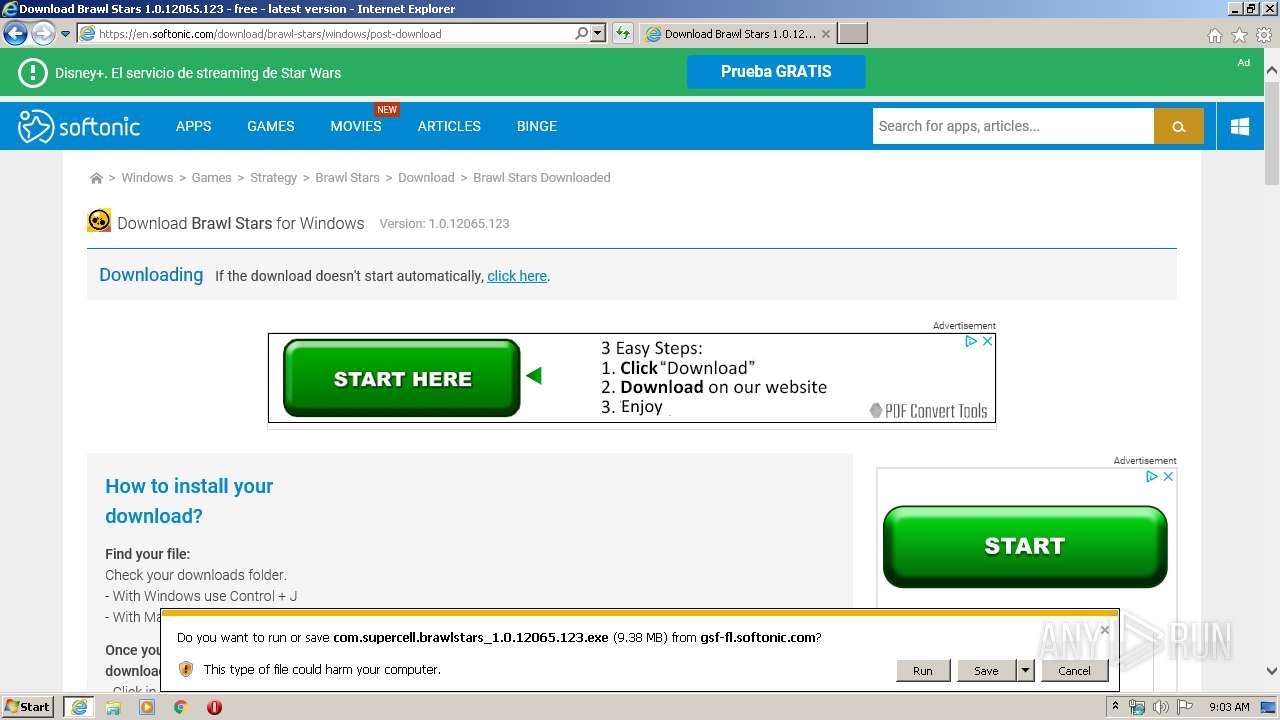
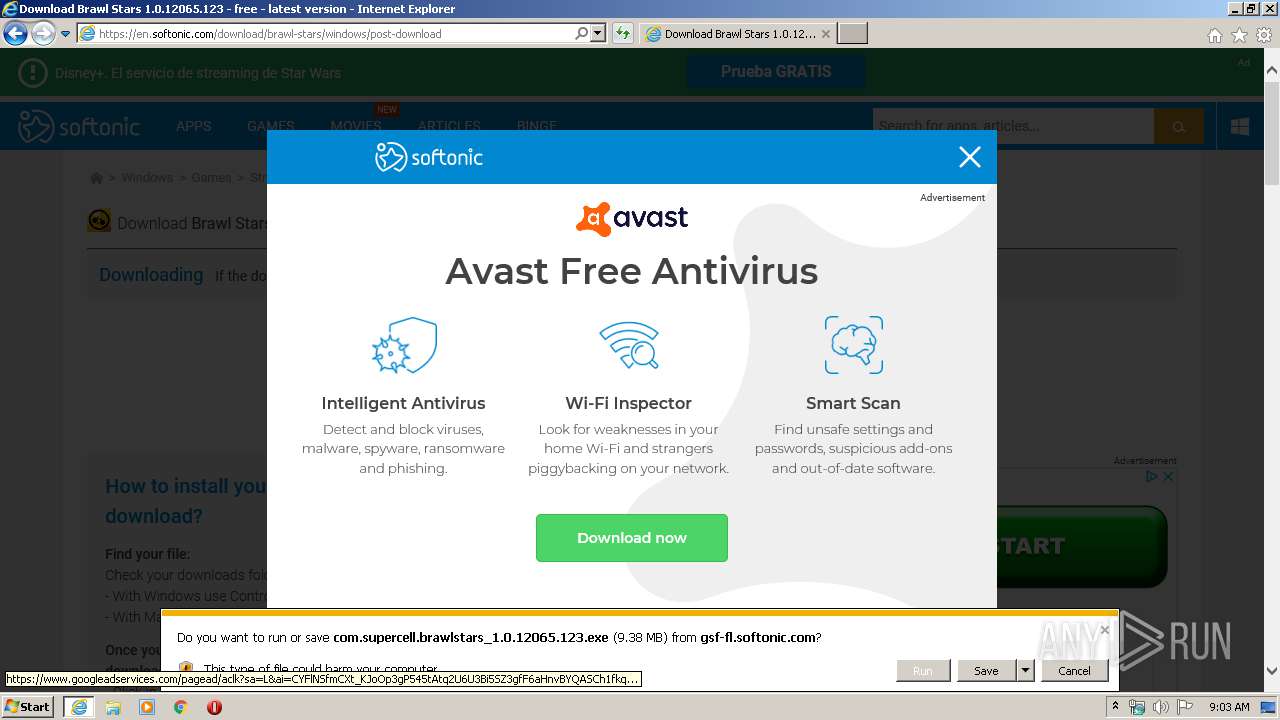
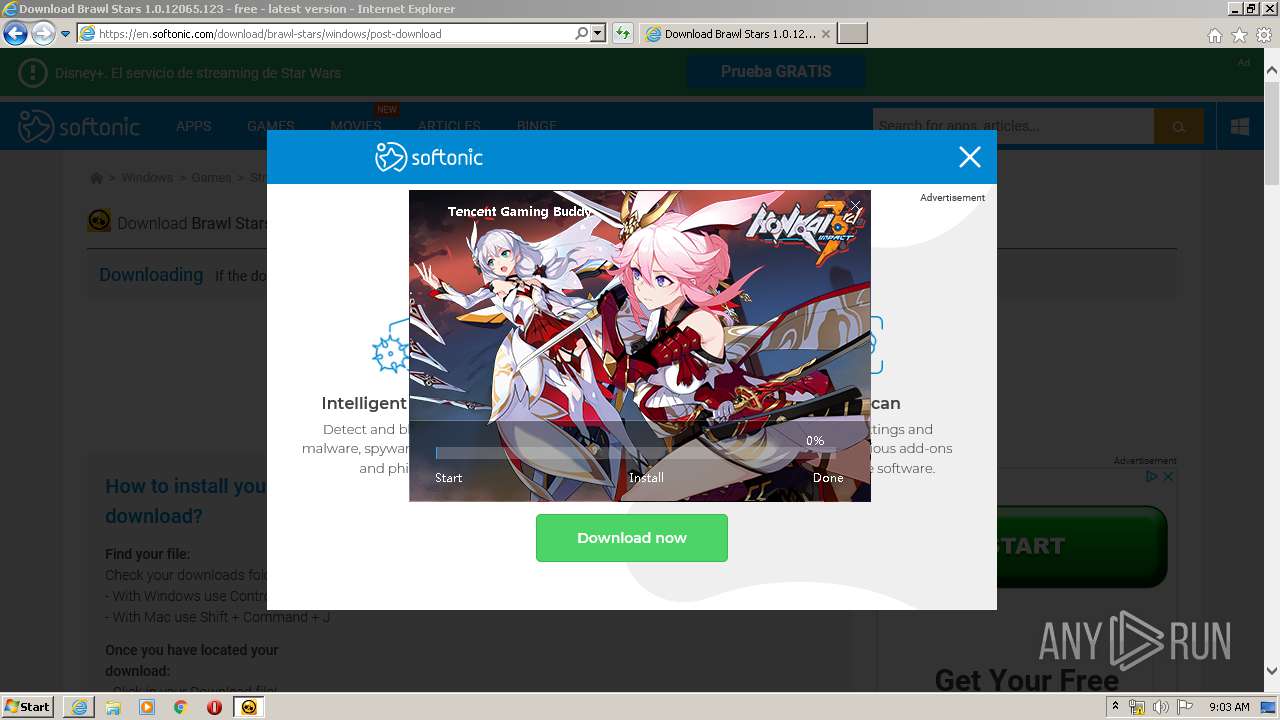
| URL: | https://brawl-stars.en.softonic.com/ |
| Full analysis: | https://app.any.run/tasks/9a394a3f-a512-470b-976e-bb862b4dbe2d |
| Verdict: | Malicious activity |
| Analysis date: | March 31, 2020, 08:02:34 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MD5: | 7929DB20BDC041B51CF01603A66DAA72 |
| SHA1: | B214D1B9B61F7E6BDAA29053FF57E0C75CD3FBE2 |
| SHA256: | 4987EC24D9445B240EC34AC46CED8E0A4CDAE30280514158A6AD728A40664517 |
| SSDEEP: | 3:N8a/2HLGK3:2OSLGK3 |
MALICIOUS
Application was dropped or rewritten from another process
- com.supercell.brawlstars_1.0.12065.123.exe (PID: 3240)
- com.supercell.brawlstars_1.0.12065.123.exe (PID: 956)
- TenioDL.exe (PID: 3840)
Loads dropped or rewritten executable
- com.supercell.brawlstars_1.0.12065.123.exe (PID: 956)
- TenioDL.exe (PID: 3840)
SUSPICIOUS
Executable content was dropped or overwritten
- iexplore.exe (PID: 2544)
- com.supercell.brawlstars_1.0.12065.123.exe (PID: 956)
Creates files in the user directory
- com.supercell.brawlstars_1.0.12065.123.exe (PID: 956)
- TenioDL.exe (PID: 3840)
Low-level read access rights to disk partition
- com.supercell.brawlstars_1.0.12065.123.exe (PID: 956)
Connects to unusual port
- com.supercell.brawlstars_1.0.12065.123.exe (PID: 956)
- TenioDL.exe (PID: 3840)
Reads Internet Cache Settings
- com.supercell.brawlstars_1.0.12065.123.exe (PID: 956)
Uses ICACLS.EXE to modify access control list
- TenioDL.exe (PID: 3840)
INFO
Application launched itself
- iexplore.exe (PID: 2544)
Modifies the phishing filter of IE
- iexplore.exe (PID: 2544)
Reads Internet Cache Settings
- iexplore.exe (PID: 2544)
- iexplore.exe (PID: 3596)
Changes internet zones settings
- iexplore.exe (PID: 2544)
Reads the hosts file
- com.supercell.brawlstars_1.0.12065.123.exe (PID: 956)
Reads internet explorer settings
- iexplore.exe (PID: 3596)
Creates files in the user directory
- iexplore.exe (PID: 3596)
Reads settings of System Certificates
- iexplore.exe (PID: 2544)
Adds / modifies Windows certificates
- iexplore.exe (PID: 2544)
Changes settings of System certificates
- iexplore.exe (PID: 2544)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
44
Monitored processes
6
Malicious processes
1
Suspicious processes
2
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 956 | "C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\B6QGX7LP\com.supercell.brawlstars_1.0.12065.123.exe" | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\B6QGX7LP\com.supercell.brawlstars_1.0.12065.123.exe | iexplore.exe | ||||||||||||
User: admin Company: Tencent Integrity Level: HIGH Description: Tencent Gaming Buddy - Install Exit code: 0 Version: 1.0.12065.123 Modules
| |||||||||||||||
| 1544 | "C:\Windows\System32\icacls.exe" C:\Users\admin\AppData\Roaming\Tencent\Config\ /t /setintegritylevel low | C:\Windows\System32\icacls.exe | — | TenioDL.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2544 | "C:\Program Files\Internet Explorer\iexplore.exe" https://brawl-stars.en.softonic.com/ | C:\Program Files\Internet Explorer\iexplore.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Internet Explorer Exit code: 0 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
| 3240 | "C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\B6QGX7LP\com.supercell.brawlstars_1.0.12065.123.exe" | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\B6QGX7LP\com.supercell.brawlstars_1.0.12065.123.exe | — | iexplore.exe | |||||||||||
User: admin Company: Tencent Integrity Level: MEDIUM Description: Tencent Gaming Buddy - Install Exit code: 3221226540 Version: 1.0.12065.123 Modules
| |||||||||||||||
| 3596 | "C:\Program Files\Internet Explorer\iexplore.exe" SCODEF:2544 CREDAT:267521 /prefetch:2 | C:\Program Files\Internet Explorer\iexplore.exe | iexplore.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Internet Explorer Exit code: 0 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
| 3840 | C:\Users\admin\AppData\Roaming\Tencent\TxGameAssistant\GameDownload\TenioDL.exe | C:\Users\admin\AppData\Roaming\Tencent\TxGameAssistant\GameDownload\TenioDL.exe | com.supercell.brawlstars_1.0.12065.123.exe | ||||||||||||
User: admin Company: Tencent Integrity Level: HIGH Description: 腾讯游戏云加速下载引擎(旋风Inside) Exit code: 0 Version: 2, 0, 15, 26 Modules
| |||||||||||||||
Total events
7 373
Read events
1 488
Write events
4 166
Delete events
1 719
Modification events
| (PID) Process: | (3596) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\LowCache\Content |
| Operation: | write | Name: | CachePrefix |
Value: | |||
| (PID) Process: | (3596) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\LowCache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (2544) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\UrlBlockManager |
| Operation: | write | Name: | NextCheckForUpdateLowDateTime |
Value: 3616276198 | |||
| (PID) Process: | (2544) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\UrlBlockManager |
| Operation: | write | Name: | NextCheckForUpdateHighDateTime |
Value: 30803762 | |||
| (PID) Process: | (2544) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Content |
| Operation: | write | Name: | CachePrefix |
Value: | |||
| (PID) Process: | (2544) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (2544) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
| (PID) Process: | (2544) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\Main |
| Operation: | write | Name: | CompatibilityFlags |
Value: 0 | |||
| (PID) Process: | (2544) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings |
| Operation: | write | Name: | ProxyEnable |
Value: 0 | |||
| (PID) Process: | (2544) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\Connections |
| Operation: | write | Name: | SavedLegacySettings |
Value: 46000000A1000000010000000000000000000000000000000000000000000000C0E333BBEAB1D301000000000000000000000000020000001700000000000000FE800000000000007D6CB050D9C573F70B000000000000006D00330032005C004D00530049004D004700330032002E0064006C000100000004AA400014AA4000040000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000002000000C0A8016400000000000000000000000000000000000000000800000000000000805D3F00983740000008000002000000000000600000002060040000B8A94000020000008802000060040000B8A9400004000000F8010000B284000088B64000B84B400043003A000000000000000000000000000000000000000000 | |||
Executable files
6
Suspicious files
299
Text files
503
Unknown types
151
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3596 | iexplore.exe | C:\Users\admin\AppData\Local\Temp\Low\Cab79CC.tmp | — | |
MD5:— | SHA256:— | |||
| 3596 | iexplore.exe | C:\Users\admin\AppData\Local\Temp\Low\Tar79CD.tmp | — | |
MD5:— | SHA256:— | |||
| 3596 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\5457A8CE4B2A7499F8299A013B6E1C7C_CBB16B7A61CE4E298043181730D3CE9B | binary | |
MD5:— | SHA256:— | |||
| 3596 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\CFE86DBBE02D859DC92F1E17E0574EE8_46766FC45507C0B9E264E4C18BC7288B | der | |
MD5:— | SHA256:— | |||
| 3596 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\5457A8CE4B2A7499F8299A013B6E1C7C_CBB16B7A61CE4E298043181730D3CE9B | der | |
MD5:— | SHA256:— | |||
| 3596 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\07CEF2F654E3ED6050FFC9B6EB844250_649D3C9717A1D0B02735FC14F09C533D | binary | |
MD5:— | SHA256:— | |||
| 3596 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\DY534W2X\57bea-b6f3c[1].js | text | |
MD5:— | SHA256:— | |||
| 3596 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\45040AF7C7D072CACDA5FF0A66591DBD | der | |
MD5:— | SHA256:— | |||
| 3596 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\45040AF7C7D072CACDA5FF0A66591DBD | binary | |
MD5:— | SHA256:— | |||
| 3596 | iexplore.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Cookies\Low\I62BBKP0.txt | text | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
157
TCP/UDP connections
432
DNS requests
171
Threats
4
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
3596 | iexplore.exe | GET | 200 | 151.139.128.14:80 | http://ocsp.usertrust.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBR8sWZUnKvbRO5iJhat9GV793rVlAQUrb2YejS0Jvf6xCZU7wO94CTLVBoCEBPqKHBb9OztDDZjCYBhQzY%3D | US | der | 471 b | whitelisted |
3596 | iexplore.exe | GET | 200 | 104.18.21.226:80 | http://ocsp.globalsign.com/rootr1/ME8wTTBLMEkwRzAJBgUrDgMCGgUABBS3V7W2nAf4FiMTjpDJKg6%2BMgGqMQQUYHtmGkUNl8qJUC99BM00qP%2F8%2FUsCDkbwjNvPLFRm7zMB3V80 | US | der | 1.49 Kb | whitelisted |
3596 | iexplore.exe | GET | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTBL0V27RVZ7LBduom%2FnYB45SPUEwQU5Z1ZMIJHWMys%2BghUNoZ7OrUETfACEA8sEMlbBsCTf7jUSfg%2BhWk%3D | US | der | 1.47 Kb | whitelisted |
3596 | iexplore.exe | GET | 200 | 172.217.23.131:80 | http://ocsp.pki.goog/gts1o1/MFIwUDBOMEwwSjAJBgUrDgMCGgUABBRCRjDCJxnb3nDwj%2Fxz5aZfZjgXvAQUmNH4bhDrz5vsYJ8YkBug630J%2FSsCEQDy4NKedukSQwgAAAAAMgpY | US | der | 472 b | whitelisted |
3596 | iexplore.exe | GET | 200 | 151.139.128.14:80 | http://ocsp.sectigo.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBRDC9IOTxN6GmyRjyTl2n4yTUczyAQUjYxexFStiuF36Zv5mwXhuAGNYeECEFRVTJ0uA2JgqrS%2FqKflP9g%3D | US | der | 471 b | whitelisted |
3596 | iexplore.exe | GET | 200 | 151.139.128.14:80 | http://crl.usertrust.com/USERTrustRSACertificationAuthority.crl | US | der | 922 b | whitelisted |
3596 | iexplore.exe | GET | 200 | 52.222.149.182:80 | http://o.ss2.us//MEowSDBGMEQwQjAJBgUrDgMCGgUABBSLwZ6EW5gdYc9UaSEaaLjjETNtkAQUv1%2B30c7dH4b0W1Ws3NcQwg6piOcCCQCnDkpMNIK3fw%3D%3D | US | der | 1.70 Kb | whitelisted |
3596 | iexplore.exe | GET | 200 | 104.18.21.226:80 | http://ocsp.globalsign.com/rootr1/ME8wTTBLMEkwRzAJBgUrDgMCGgUABBS3V7W2nAf4FiMTjpDJKg6%2BMgGqMQQUYHtmGkUNl8qJUC99BM00qP%2F8%2FUsCDkbwjNvPLFRm7zMB3V80 | US | der | 1.49 Kb | whitelisted |
3596 | iexplore.exe | GET | 200 | 172.217.23.131:80 | http://ocsp.pki.goog/gsr2/ME4wTDBKMEgwRjAJBgUrDgMCGgUABBTgXIsxbvr2lBkPpoIEVRE6gHlCnAQUm%2BIHV2ccHsBqBt5ZtJot39wZhi4CDQHjtJqhjYqpgSVpULg%3D | US | der | 468 b | whitelisted |
3596 | iexplore.exe | GET | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTBL0V27RVZ7LBduom%2FnYB45SPUEwQU5Z1ZMIJHWMys%2BghUNoZ7OrUETfACEA8sEMlbBsCTf7jUSfg%2BhWk%3D | US | der | 1.47 Kb | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
3596 | iexplore.exe | 151.101.2.133:443 | sc.sftcdn.net | Fastly | US | malicious |
3596 | iexplore.exe | 172.217.23.98:443 | www.googletagservices.com | Google Inc. | US | whitelisted |
3596 | iexplore.exe | 151.101.2.97:443 | images.sftcdn.net | Fastly | US | unknown |
3596 | iexplore.exe | 52.222.149.182:80 | o.ss2.us | Amazon.com, Inc. | US | whitelisted |
3596 | iexplore.exe | 52.222.153.47:443 | c.amazon-adsystem.com | Amazon.com, Inc. | US | unknown |
3596 | iexplore.exe | 35.158.248.67:443 | tlx.3lift.com | Amazon.com, Inc. | DE | unknown |
3596 | iexplore.exe | 185.33.223.202:443 | ib.adnxs.com | AppNexus, Inc | — | unknown |
3596 | iexplore.exe | 172.217.23.131:80 | ocsp.pki.goog | Google Inc. | US | whitelisted |
2544 | iexplore.exe | 204.79.197.200:80 | www.bing.com | Microsoft Corporation | US | whitelisted |
3596 | iexplore.exe | 93.184.220.29:80 | ocsp.digicert.com | MCI Communications Services, Inc. d/b/a Verizon Business | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
brawl-stars.en.softonic.com |
| malicious |
ocsp.usertrust.com |
| whitelisted |
crl.usertrust.com |
| whitelisted |
ocsp.sectigo.com |
| whitelisted |
api.bing.com |
| whitelisted |
www.bing.com |
| whitelisted |
sc.sftcdn.net |
| whitelisted |
www.googletagservices.com |
| whitelisted |
images.sftcdn.net |
| whitelisted |
fonts.googleapis.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
3840 | TenioDL.exe | Generic Protocol Command Decode | ET INFO Session Traversal Utilities for NAT (STUN Binding Request obsolete rfc 3489 CHANGE-REQUEST attribute change IP flag false change port flag false) |
3840 | TenioDL.exe | Generic Protocol Command Decode | ET INFO Session Traversal Utilities for NAT (STUN Binding Request obsolete rfc 3489 CHANGE-REQUEST attribute change IP flag true change port flag false) |
3840 | TenioDL.exe | Generic Protocol Command Decode | ET INFO Session Traversal Utilities for NAT (STUN Binding Request obsolete rfc 3489 CHANGE-REQUEST attribute change IP flag false change port flag true) |
3840 | TenioDL.exe | Potential Corporate Privacy Violation | ET POLICY PE EXE or DLL Windows file download HTTP |
Process | Message |
|---|---|
com.supercell.brawlstars_1.0.12065.123.exe | [Downloader] DriverType C: = 3
|
com.supercell.brawlstars_1.0.12065.123.exe | [Downloader] GetLogicalDrives 4
|
com.supercell.brawlstars_1.0.12065.123.exe | [Downloader] DriverType C: = 3
|
com.supercell.brawlstars_1.0.12065.123.exe | [Downloader] GetLogicalDrives 4
|