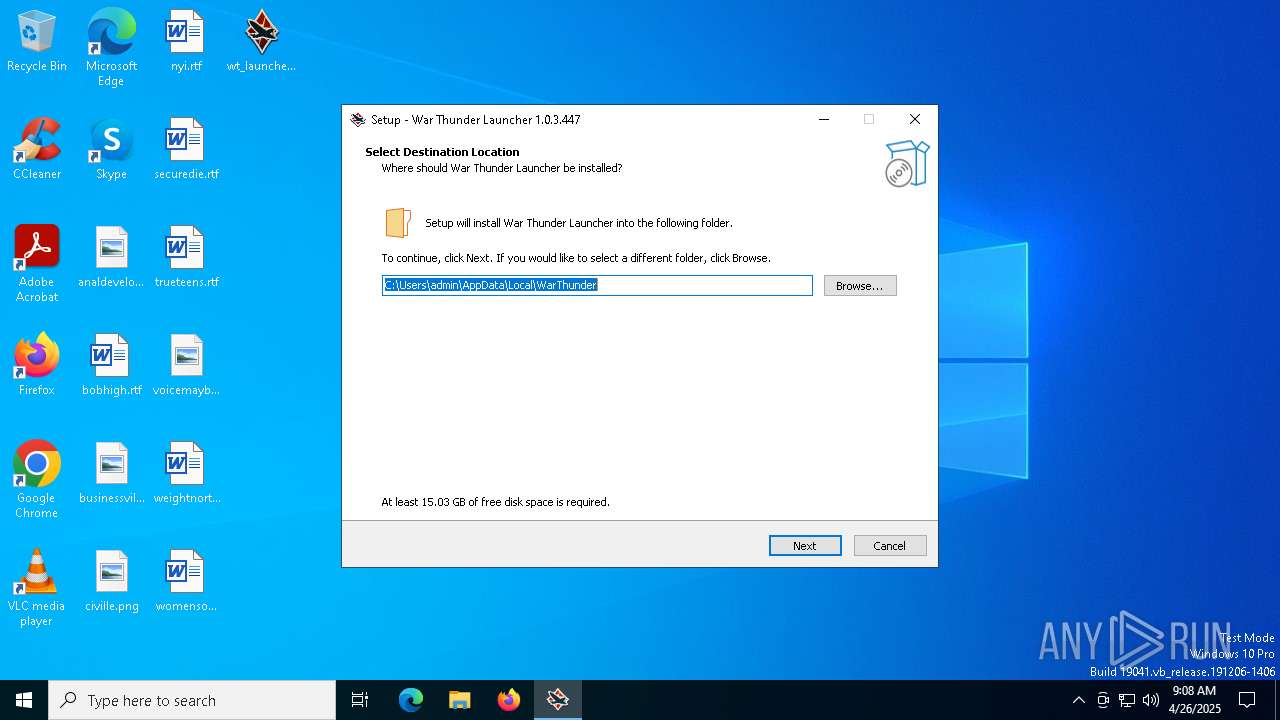
| File name: | wt_launcher_1.0.3.447-a2p7dh6ho.exe |
| Full analysis: | https://app.any.run/tasks/e99117c5-5621-45c6-9284-b631b2513b9f |
| Verdict: | Malicious activity |
| Analysis date: | April 26, 2025, 09:08:27 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/vnd.microsoft.portable-executable |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows, 10 sections |
| MD5: | 66FC6557F8E0DD75A964CFEB7DB53673 |
| SHA1: | C73D15EB1DF3FE6D9536D25D65D92B77DE72007F |
| SHA256: | 497E6622AEA51718B0739EA7CB94BADFD7371F2A2AF9A7459DE7DBFF3A40FAAF |
| SSDEEP: | 98304:3+cD4dnveSD4ZrVVZg8R5ljpuvcMOIZxIu7XuMBcWjgJB4V1H7VpBt9JplknATDD:3M0H1DSeuKS8+XwHSkEr |
MALICIOUS
No malicious indicators.SUSPICIOUS
Executable content was dropped or overwritten
- wt_launcher_1.0.3.447-a2p7dh6ho.exe (PID: 1324)
- wt_launcher_1.0.3.447-a2p7dh6ho.tmp (PID: 4620)
Uses NETSH.EXE to add a firewall rule or allowed programs
- wt_launcher_1.0.3.447-a2p7dh6ho.tmp (PID: 4620)
Reads the Windows owner or organization settings
- wt_launcher_1.0.3.447-a2p7dh6ho.tmp (PID: 4620)
INFO
Reads the computer name
- wt_launcher_1.0.3.447-a2p7dh6ho.tmp (PID: 4620)
- identity_helper.exe (PID: 7836)
Checks supported languages
- wt_launcher_1.0.3.447-a2p7dh6ho.tmp (PID: 4620)
- wt_launcher_1.0.3.447-a2p7dh6ho.exe (PID: 1324)
- identity_helper.exe (PID: 7836)
Create files in a temporary directory
- wt_launcher_1.0.3.447-a2p7dh6ho.exe (PID: 1324)
- wt_launcher_1.0.3.447-a2p7dh6ho.tmp (PID: 4620)
Manual execution by a user
- msedge.exe (PID: 5800)
- notepad.exe (PID: 2560)
- rundll32.exe (PID: 7596)
- msedge.exe (PID: 7348)
- rundll32.exe (PID: 8068)
- msedge.exe (PID: 7476)
- rundll32.exe (PID: 8132)
- msedge.exe (PID: 7928)
- msedge.exe (PID: 7628)
- rundll32.exe (PID: 8020)
- msedge.exe (PID: 7792)
- msedge.exe (PID: 7988)
- msedge.exe (PID: 872)
- msedge.exe (PID: 2084)
- msedge.exe (PID: 8312)
- msedge.exe (PID: 8432)
- OpenWith.exe (PID: 7648)
Reads security settings of Internet Explorer
- notepad.exe (PID: 2560)
- rundll32.exe (PID: 7596)
- rundll32.exe (PID: 8132)
- rundll32.exe (PID: 8020)
Reads the software policy settings
- wt_launcher_1.0.3.447-a2p7dh6ho.tmp (PID: 4620)
Detects InnoSetup installer (YARA)
- wt_launcher_1.0.3.447-a2p7dh6ho.exe (PID: 1324)
- wt_launcher_1.0.3.447-a2p7dh6ho.tmp (PID: 4620)
Reads the machine GUID from the registry
- wt_launcher_1.0.3.447-a2p7dh6ho.tmp (PID: 4620)
Compiled with Borland Delphi (YARA)
- wt_launcher_1.0.3.447-a2p7dh6ho.tmp (PID: 4620)
- wt_launcher_1.0.3.447-a2p7dh6ho.exe (PID: 1324)
Creates files or folders in the user directory
- wt_launcher_1.0.3.447-a2p7dh6ho.tmp (PID: 4620)
Creates a software uninstall entry
- wt_launcher_1.0.3.447-a2p7dh6ho.tmp (PID: 4620)
Application launched itself
- msedge.exe (PID: 5800)
Reads Environment values
- identity_helper.exe (PID: 7836)
Reads Microsoft Office registry keys
- rundll32.exe (PID: 7596)
- rundll32.exe (PID: 8132)
- rundll32.exe (PID: 8020)
- OpenWith.exe (PID: 7648)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Inno Setup installer (67.7) |
|---|---|---|
| .exe | | | Win32 EXE PECompact compressed (generic) (25.6) |
| .exe | | | Win32 Executable (generic) (2.7) |
| .exe | | | Win16/32 Executable Delphi generic (1.2) |
| .exe | | | Generic Win/DOS Executable (1.2) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2023:02:15 14:54:16+00:00 |
| ImageFileCharacteristics: | No relocs, Executable, No line numbers, No symbols, Bytes reversed lo, 32-bit, Bytes reversed hi |
| PEType: | PE32 |
| LinkerVersion: | 2.25 |
| CodeSize: | 741888 |
| InitializedDataSize: | 182272 |
| UninitializedDataSize: | - |
| EntryPoint: | 0xb5eec |
| OSVersion: | 6.1 |
| ImageVersion: | 6 |
| SubsystemVersion: | 6.1 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 0.0.0.0 |
| ProductVersionNumber: | 0.0.0.0 |
| FileFlagsMask: | 0x003f |
| FileFlags: | (none) |
| FileOS: | Win32 |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | Neutral |
| CharacterSet: | Unicode |
| Comments: | This installation was built with Inno Setup. |
| CompanyName: | Gaijin Network |
| FileDescription: | War Thunder Launcher Setup |
| FileVersion: | |
| LegalCopyright: | Copyright © 2019-2025 by Gaijin Entertainment |
| OriginalFileName: | |
| ProductName: | War Thunder Launcher |
| ProductVersion: |
Total processes
231
Monitored processes
105
Malicious processes
2
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 456 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=gpu-process --disable-gpu-sandbox --use-gl=disabled --gpu-vendor-id=5140 --gpu-device-id=140 --gpu-sub-system-id=0 --gpu-revision=0 --gpu-driver-version=10.0.19041.3636 --no-appcompat-clear --gpu-preferences=WAAAAAAAAADoAAAMAAAAAAAAAAAAAAAAAABgAAAAAAA4AAAAAAAAAAAAAABEAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAGAAAAAAAAAAYAAAAAAAAAAgAAAAAAAAACAAAAAAAAAAIAAAAAAAAAA== --mojo-platform-channel-handle=7744 --field-trial-handle=2368,i,14751982304962186000,9447653459328642170,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
| 536 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | netsh.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 728 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | netsh.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 736 | "C:\WINDOWS\system32\netsh.exe" firewall add allowedprogram "C:\Users\admin\AppData\Local\WarThunder\gaijin_downloader.exe" "War Thunder self updater" ENABLE ALL | C:\Windows\SysWOW64\netsh.exe | — | wt_launcher_1.0.3.447-a2p7dh6ho.tmp | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Network Command Shell Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 872 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" C:\Users\admin\Desktop\czech.svg | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
| 896 | "C:\WINDOWS\system32\netsh.exe" firewall add allowedprogram "C:\Users\admin\AppData\Local\WarThunder\AFR-FriendlyD3D.exe" "War Thunder Game Client for CrossFire\SLI" ENABLE ALL | C:\Windows\SysWOW64\netsh.exe | — | wt_launcher_1.0.3.447-a2p7dh6ho.tmp | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Network Command Shell Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1012 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | netsh.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1052 | "C:\WINDOWS\system32\netsh.exe" firewall add allowedprogram "C:\Users\admin\AppData\Local\WarThunder\win64\ForceSingleGPU.exe" "War Thunder Game Client for disabled CrossFire\SLI" ENABLE ALL | C:\Windows\SysWOW64\netsh.exe | — | wt_launcher_1.0.3.447-a2p7dh6ho.tmp | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Network Command Shell Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1096 | "C:\WINDOWS\system32\netsh.exe" firewall add allowedprogram "C:\Users\admin\AppData\Local\WarThunder\win32\bpreport.exe" "War Thunder Crash Reporter" ENABLE ALL | C:\Windows\SysWOW64\netsh.exe | — | wt_launcher_1.0.3.447-a2p7dh6ho.tmp | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Network Command Shell Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1116 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=storage.mojom.StorageService --lang=en-US --service-sandbox-type=service --no-appcompat-clear --mojo-platform-channel-handle=2724 --field-trial-handle=2368,i,14751982304962186000,9447653459328642170,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Version: 122.0.2365.59 Modules
| |||||||||||||||
Total events
29 917
Read events
29 822
Write events
95
Delete events
0
Modification events
| (PID) Process: | (4620) wt_launcher_1.0.3.447-a2p7dh6ho.tmp | Key: | HKEY_CURRENT_USER\SOFTWARE\Gaijin\WarThunder |
| Operation: | write | Name: | StartupWithWindows |
Value: Yes | |||
| (PID) Process: | (4620) wt_launcher_1.0.3.447-a2p7dh6ho.tmp | Key: | HKEY_CURRENT_USER\SOFTWARE\Gaijin\WarThunder |
| Operation: | write | Name: | InstallDir |
Value: C:\Users\admin\AppData\Local\WarThunder | |||
| (PID) Process: | (4620) wt_launcher_1.0.3.447-a2p7dh6ho.tmp | Key: | HKEY_CURRENT_USER\SOFTWARE\Gaijin\WarThunder |
| Operation: | write | Name: | InstallPath |
Value: C:\Users\admin\AppData\Local\WarThunder | |||
| (PID) Process: | (4620) wt_launcher_1.0.3.447-a2p7dh6ho.tmp | Key: | HKEY_CURRENT_USER\SOFTWARE\Gaijin\WarThunder |
| Operation: | write | Name: | Dir |
Value: C:\Users\admin\AppData\Local\WarThunder | |||
| (PID) Process: | (4620) wt_launcher_1.0.3.447-a2p7dh6ho.tmp | Key: | HKEY_CURRENT_USER\SOFTWARE\Gaijin\WarThunder |
| Operation: | write | Name: | Path |
Value: C:\Users\admin\AppData\Local\WarThunder\launcher.exe | |||
| (PID) Process: | (4620) wt_launcher_1.0.3.447-a2p7dh6ho.tmp | Key: | HKEY_CURRENT_USER\SOFTWARE\Gaijin\WarThunder |
| Operation: | write | Name: | language |
Value: English | |||
| (PID) Process: | (4620) wt_launcher_1.0.3.447-a2p7dh6ho.tmp | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall\{ed8deea4-29fa-3932-9612-e2122d8a62d9}}_is1 |
| Operation: | write | Name: | Inno Setup: Setup Version |
Value: 6.2.2 | |||
| (PID) Process: | (4620) wt_launcher_1.0.3.447-a2p7dh6ho.tmp | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall\{ed8deea4-29fa-3932-9612-e2122d8a62d9}}_is1 |
| Operation: | write | Name: | Inno Setup: App Path |
Value: C:\Users\admin\AppData\Local\WarThunder | |||
| (PID) Process: | (4620) wt_launcher_1.0.3.447-a2p7dh6ho.tmp | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall\{ed8deea4-29fa-3932-9612-e2122d8a62d9}}_is1 |
| Operation: | write | Name: | InstallLocation |
Value: C:\Users\admin\AppData\Local\WarThunder\ | |||
| (PID) Process: | (4620) wt_launcher_1.0.3.447-a2p7dh6ho.tmp | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall\{ed8deea4-29fa-3932-9612-e2122d8a62d9}}_is1 |
| Operation: | write | Name: | Inno Setup: Icon Group |
Value: WarThunder | |||
Executable files
21
Suspicious files
262
Text files
45
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 4620 | wt_launcher_1.0.3.447-a2p7dh6ho.tmp | C:\Users\admin\AppData\Local\WarThunder\unins000.exe | executable | |
MD5:C778E98BCF861DC31B513BD9C11E81CE | SHA256:4FA0E70C5CF3842A39ADF4C491212EE52574685DF39FC0A9A6078DC930352871 | |||
| 1324 | wt_launcher_1.0.3.447-a2p7dh6ho.exe | C:\Users\admin\AppData\Local\Temp\is-JKHLK.tmp\wt_launcher_1.0.3.447-a2p7dh6ho.tmp | executable | |
MD5:C778E98BCF861DC31B513BD9C11E81CE | SHA256:4FA0E70C5CF3842A39ADF4C491212EE52574685DF39FC0A9A6078DC930352871 | |||
| 4620 | wt_launcher_1.0.3.447-a2p7dh6ho.tmp | C:\Users\admin\AppData\Local\WarThunder\is-H5EL2.tmp | executable | |
MD5:65F9CBA4FB02014A13685D8358CB0E67 | SHA256:2ED5BFDA0B759B4CD795514C0F1FFBDBD0DF40A82EA4FD50044BDFD8AD25CE37 | |||
| 4620 | wt_launcher_1.0.3.447-a2p7dh6ho.tmp | C:\Users\admin\AppData\Local\WarThunder\gjagent.exe | executable | |
MD5:65F9CBA4FB02014A13685D8358CB0E67 | SHA256:2ED5BFDA0B759B4CD795514C0F1FFBDBD0DF40A82EA4FD50044BDFD8AD25CE37 | |||
| 4620 | wt_launcher_1.0.3.447-a2p7dh6ho.tmp | C:\Users\admin\AppData\Local\WarThunder\launcherr.dat | compressed | |
MD5:C5AC704CF67C4749BECF7A017A963669 | SHA256:597F67AF618C133B6B213FD135109BFD93384469713C6EC7E725DC66D145922A | |||
| 4620 | wt_launcher_1.0.3.447-a2p7dh6ho.tmp | C:\Users\admin\AppData\Local\WarThunder\sciter.dll | executable | |
MD5:58115B095C523466950E2F745B70B867 | SHA256:41CF304562A6240AF02157B17800C0EC01154626258A809D665AADD59E7276CA | |||
| 4620 | wt_launcher_1.0.3.447-a2p7dh6ho.tmp | C:\Users\admin\AppData\Local\WarThunder\is-NFQCI.tmp | compressed | |
MD5:C5AC704CF67C4749BECF7A017A963669 | SHA256:597F67AF618C133B6B213FD135109BFD93384469713C6EC7E725DC66D145922A | |||
| 4620 | wt_launcher_1.0.3.447-a2p7dh6ho.tmp | C:\Users\admin\AppData\Local\WarThunder\icon.ico | image | |
MD5:945B144169D97344B11E182F773DBB67 | SHA256:FAC97A96962BE6B9347FE414AACD99B02A0DE63D79BA6E49D8690506A3C96EE4 | |||
| 4620 | wt_launcher_1.0.3.447-a2p7dh6ho.tmp | C:\Users\admin\AppData\Local\WarThunder\is-U8PMO.tmp | text | |
MD5:1E32496378E8FEE43CB01B0689963A67 | SHA256:5B47AEE36F594B7737E00990C9922A87252729B74CC2F1A83C0FCEED9816BDB9 | |||
| 4620 | wt_launcher_1.0.3.447-a2p7dh6ho.tmp | C:\Users\admin\AppData\Local\WarThunder\is-715N7.tmp | executable | |
MD5:58115B095C523466950E2F745B70B867 | SHA256:41CF304562A6240AF02157B17800C0EC01154626258A809D665AADD59E7276CA | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
70
TCP/UDP connections
53
DNS requests
41
Threats
1
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
— | — | GET | 401 | 13.107.6.158:443 | https://business.bing.com/api/v1/user/token/microsoftgraph?&clienttype=edge-omnibox | unknown | — | — | unknown |
— | — | GET | 304 | 150.171.28.11:443 | https://edge.microsoft.com/abusiveadblocking/api/v1/blocklist | unknown | — | — | unknown |
— | — | OPTIONS | 200 | 23.48.23.51:443 | https://bzib.nelreports.net/api/report?cat=bingbusiness | unknown | — | — | unknown |
— | — | GET | 200 | 150.171.27.11:443 | https://edge.microsoft.com/serviceexperimentation/v3/?osname=win&channel=stable&osver=10.0.19045&devicefamily=desktop&installdate=1661339457&clientversion=122.0.2365.59&experimentationmode=2&scpguard=0&scpfull=0&scpver=0 | unknown | binary | 295 b | whitelisted |
— | — | POST | 200 | 188.42.61.240:443 | https://launcher-bq.gaijin.net/launcher | unknown | binary | 15 b | whitelisted |
— | — | GET | 200 | 13.107.253.45:443 | https://edge-mobile-static.azureedge.net/eccp/get?settenant=edge-config&setplatform=win&setmkt=en-US&setchannel=stable | unknown | binary | 16.0 Kb | whitelisted |
— | — | GET | 200 | 13.107.42.16:443 | https://config.edge.skype.com/config/v1/Edge/122.0.2365.59?clientId=4489578223053569932&agents=EdgeFirstRun%2CEdgeFirstRunConfig&osname=win&client=edge&channel=stable&scpfre=0&osarch=x86_64&osver=10.0.19045&wu=1&devicefamily=desktop&uma=0&sessionid=44&mngd=0&installdate=1661339457&edu=0&bphint=2&soobedate=1504771245&fg=1 | unknown | binary | 768 b | whitelisted |
— | — | POST | 200 | 188.42.61.240:443 | https://launcher-bq.gaijin.net/launcher | unknown | binary | 15 b | whitelisted |
— | — | GET | 401 | 13.107.6.158:443 | https://business.bing.com/work/api/v2/tenant/my/settingswithflights?&clienttype=edge-omnibox | unknown | binary | 591 b | whitelisted |
— | — | GET | 200 | 104.126.37.144:443 | https://edgeservices.bing.com/edgesvc/userstatus | unknown | binary | 381 b | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
— | — | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
— | — | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4620 | wt_launcher_1.0.3.447-a2p7dh6ho.tmp | 188.42.61.240:443 | launcher-bq.gaijin.net | SERVERS-COM | LU | whitelisted |
5800 | msedge.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
6004 | msedge.exe | 13.107.42.16:443 | config.edge.skype.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
6004 | msedge.exe | 150.171.27.11:443 | edge.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
6004 | msedge.exe | 13.107.253.45:443 | edge-mobile-static.azureedge.net | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
6004 | msedge.exe | 13.107.6.158:443 | business.bing.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
launcher-bq.gaijin.net |
| whitelisted |
config.edge.skype.com |
| whitelisted |
edge.microsoft.com |
| whitelisted |
edge-mobile-static.azureedge.net |
| whitelisted |
business.bing.com |
| whitelisted |
www.bing.com |
| whitelisted |
update.googleapis.com |
| whitelisted |
edgeservices.bing.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
— | — | Potentially Bad Traffic | ET INFO Possible Chrome Plugin install |