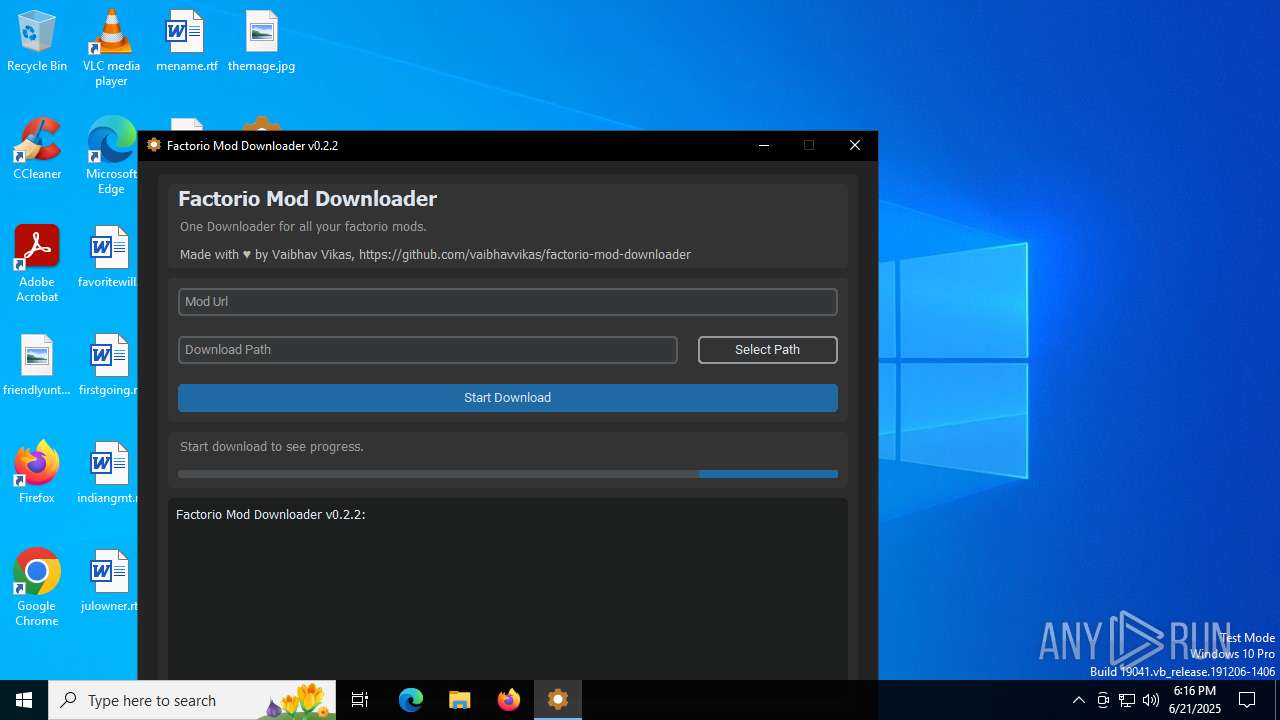
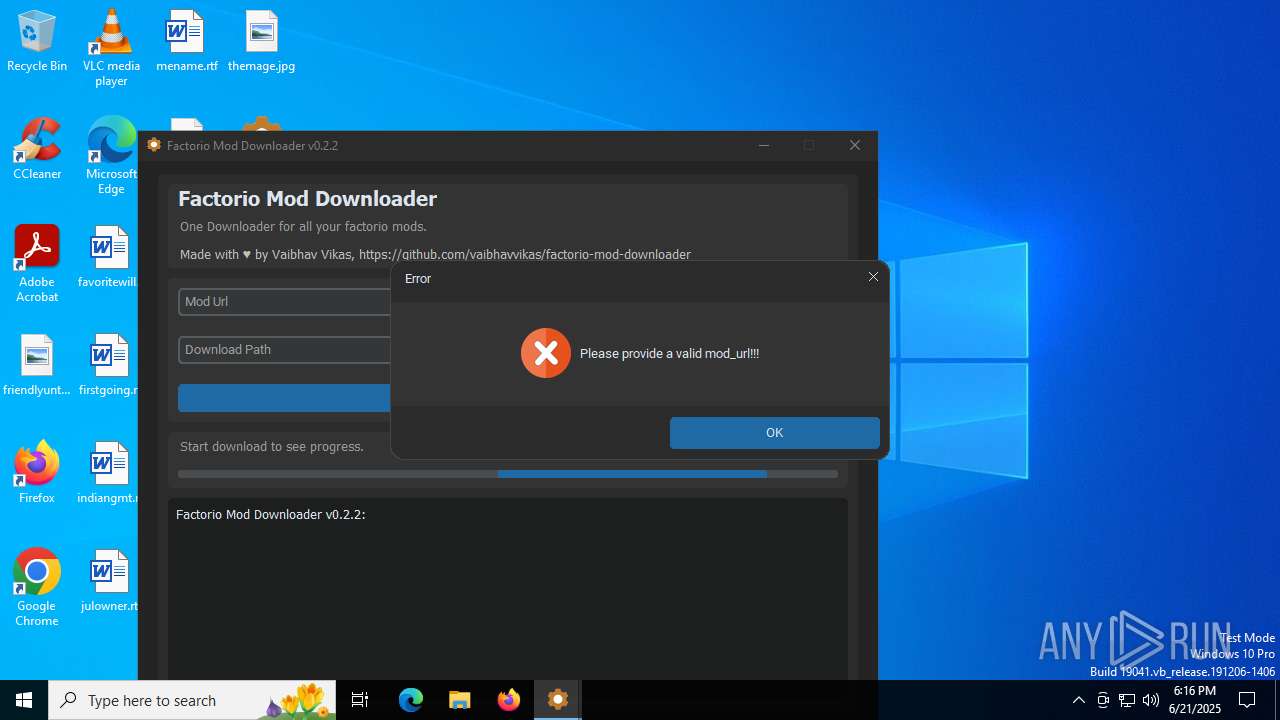
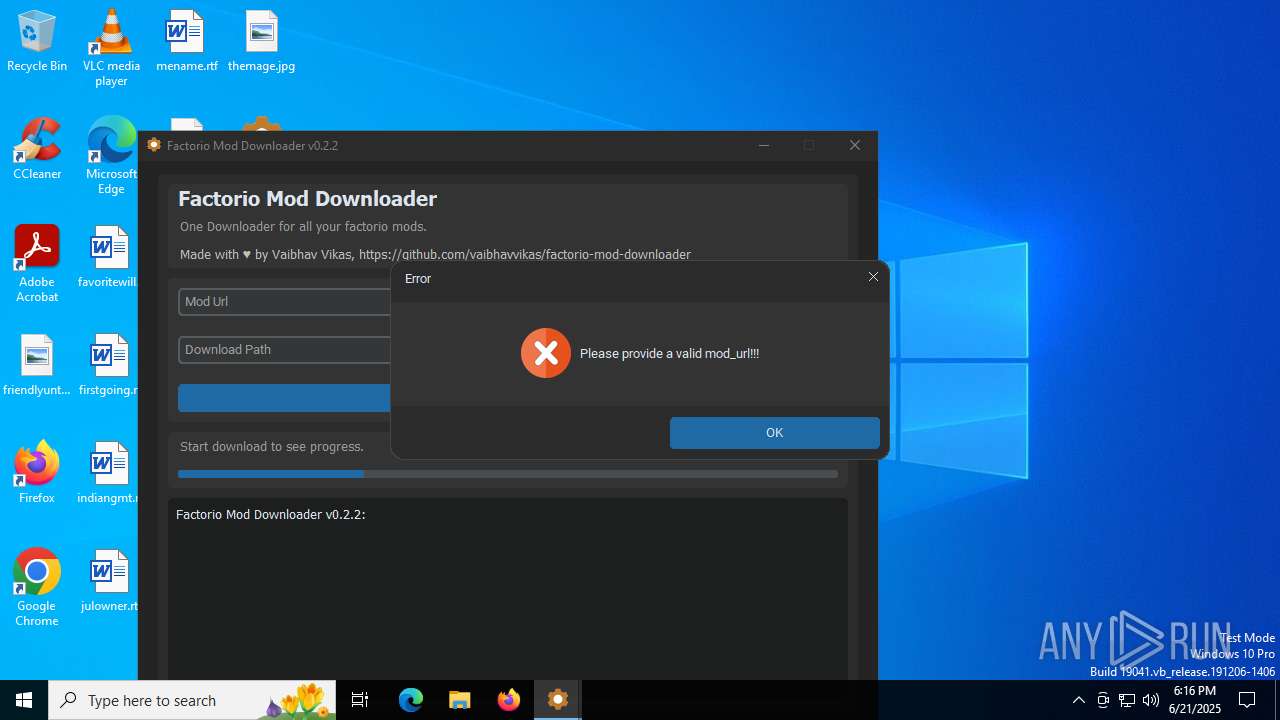
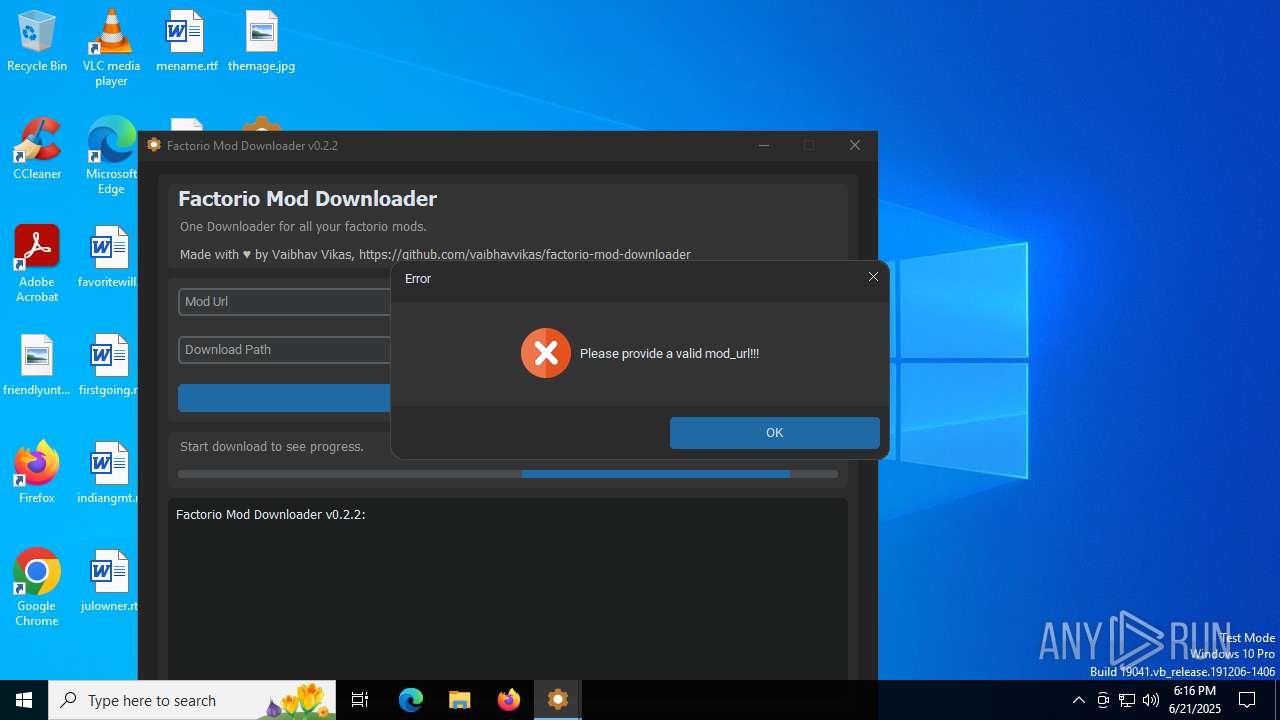
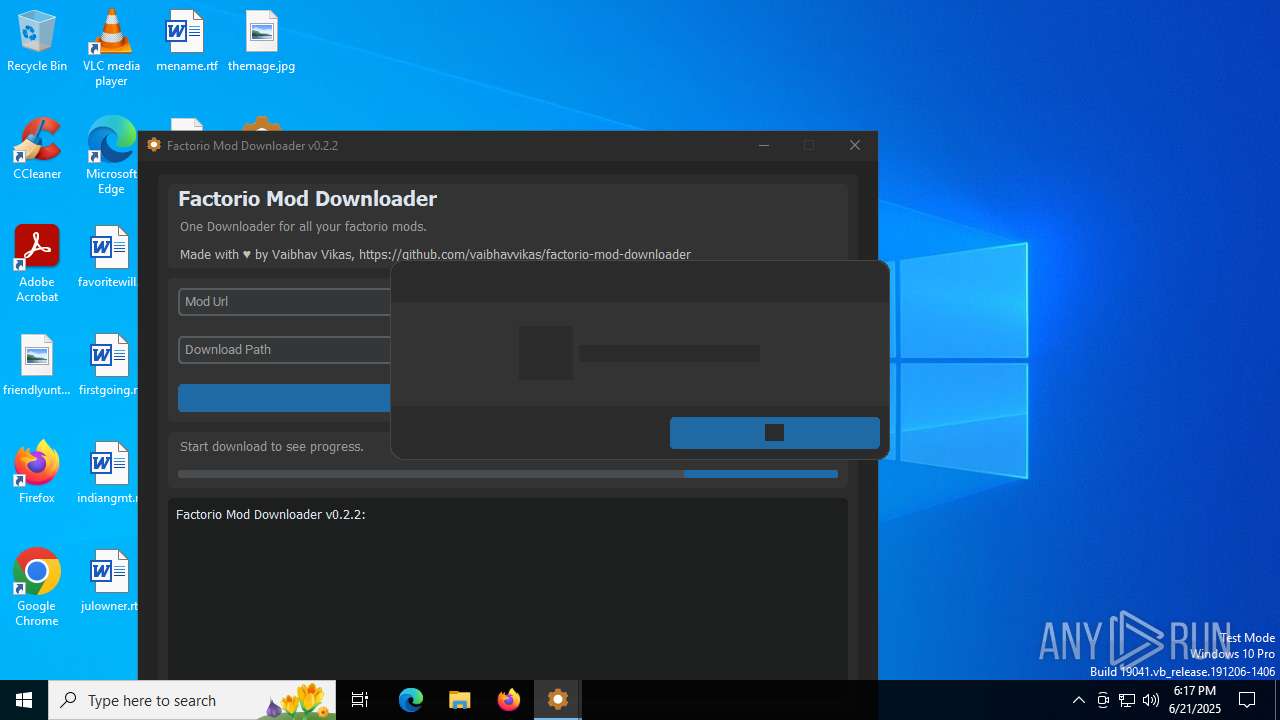
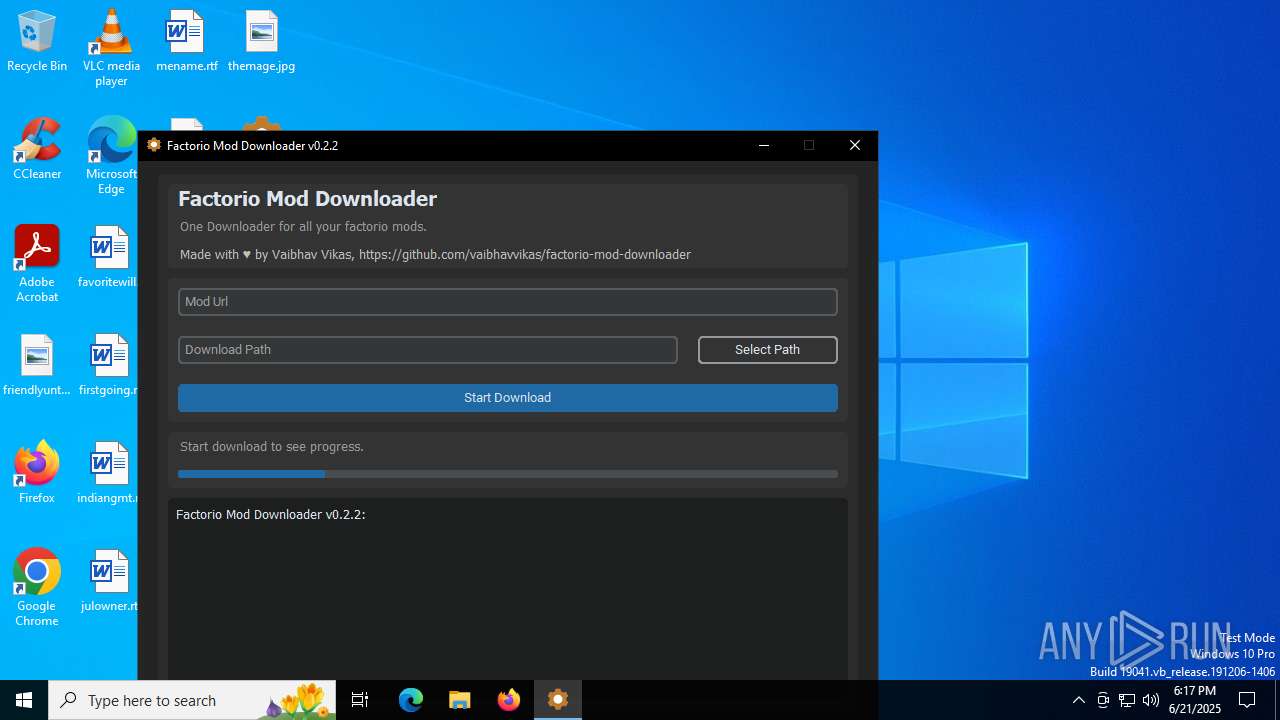
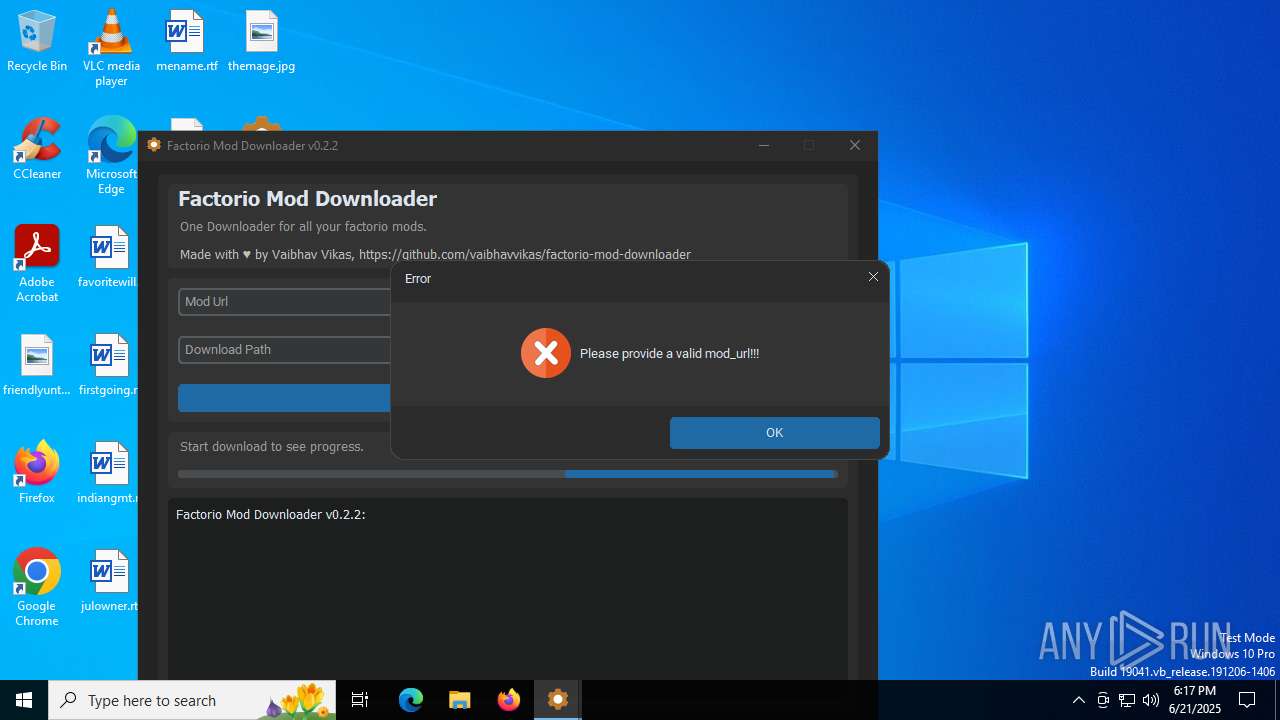
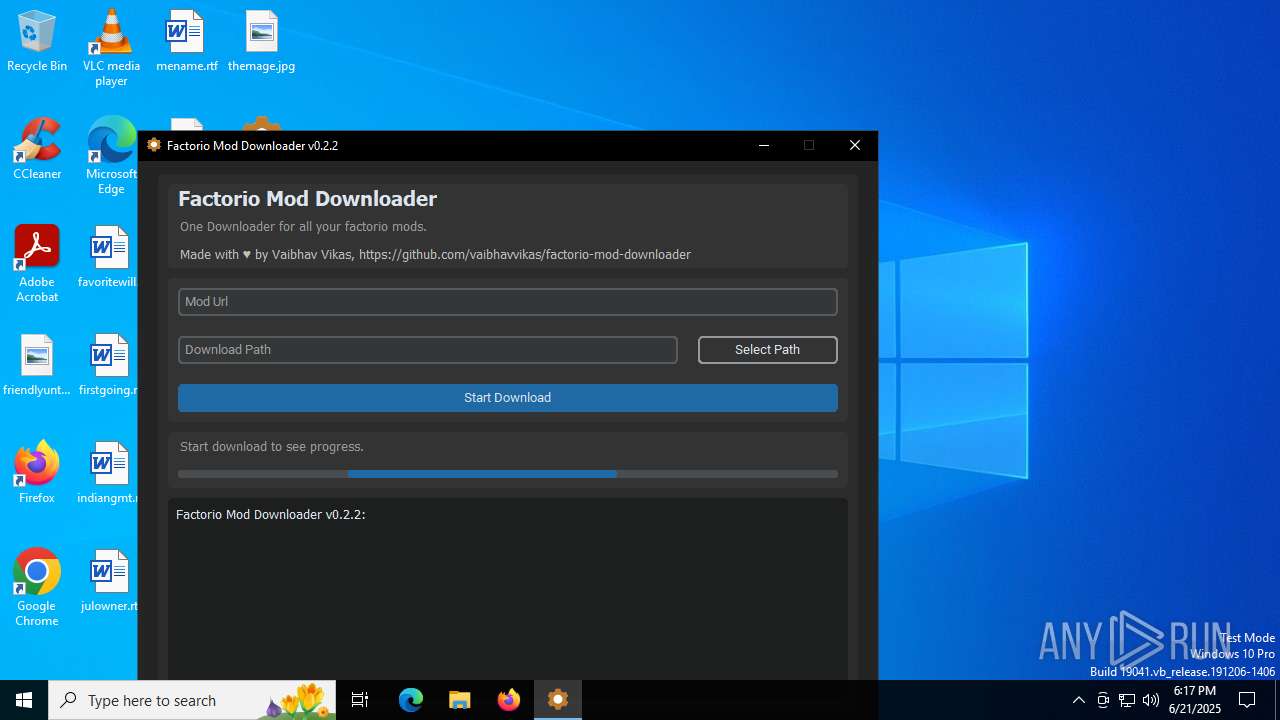
| File name: | factorio_mod_downloader-0.2.2.exe |
| Full analysis: | https://app.any.run/tasks/2839dc35-05b1-49b8-b0ae-a0c527ab0256 |
| Verdict: | Malicious activity |
| Analysis date: | June 21, 2025, 18:15:42 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/vnd.microsoft.portable-executable |
| File info: | PE32+ executable (GUI) x86-64, for MS Windows, 7 sections |
| MD5: | B881BC56F477E6BB2532DDEA8DFD8FE6 |
| SHA1: | BAC82D0717533D5964158E7B1307DCD1D0C891C4 |
| SHA256: | 49727B5DC457FE672F38F00B48000895FC482CEEC418271D6EC90265F1104561 |
| SSDEEP: | 196608:GI9j2TaMRF881mwd/kinK+8c7OM3Izm1GnLT23WIlxzXk:GI9yLF6wd/jd8c7vY61Ged/Xk |
MALICIOUS
No malicious indicators.SUSPICIOUS
Executable content was dropped or overwritten
- factorio_mod_downloader-0.2.2.exe (PID: 3820)
Process drops python dynamic module
- factorio_mod_downloader-0.2.2.exe (PID: 3820)
Process drops legitimate windows executable
- factorio_mod_downloader-0.2.2.exe (PID: 3820)
There is functionality for taking screenshot (YARA)
- factorio_mod_downloader-0.2.2.exe (PID: 3820)
- factorio_mod_downloader-0.2.2.exe (PID: 6948)
The process drops C-runtime libraries
- factorio_mod_downloader-0.2.2.exe (PID: 3820)
Application launched itself
- factorio_mod_downloader-0.2.2.exe (PID: 3820)
Loads Python modules
- factorio_mod_downloader-0.2.2.exe (PID: 6948)
INFO
Reads the computer name
- factorio_mod_downloader-0.2.2.exe (PID: 3820)
- factorio_mod_downloader-0.2.2.exe (PID: 6948)
Checks supported languages
- factorio_mod_downloader-0.2.2.exe (PID: 3820)
- factorio_mod_downloader-0.2.2.exe (PID: 6948)
The sample compiled with english language support
- factorio_mod_downloader-0.2.2.exe (PID: 3820)
PyInstaller has been detected (YARA)
- factorio_mod_downloader-0.2.2.exe (PID: 3820)
- factorio_mod_downloader-0.2.2.exe (PID: 6948)
Create files in a temporary directory
- factorio_mod_downloader-0.2.2.exe (PID: 3820)
Drops encrypted JS script (Microsoft Script Encoder)
- factorio_mod_downloader-0.2.2.exe (PID: 6948)
Checks proxy server information
- slui.exe (PID: 5628)
Reads the software policy settings
- slui.exe (PID: 5628)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | InstallShield setup (57.6) |
|---|---|---|
| .exe | | | Win64 Executable (generic) (36.9) |
| .exe | | | Generic Win/DOS Executable (2.6) |
| .exe | | | DOS Executable Generic (2.6) |
EXIF
EXE
| MachineType: | AMD AMD64 |
|---|---|
| TimeStamp: | 2025:05:24 08:39:33+00:00 |
| ImageFileCharacteristics: | Executable, Large address aware |
| PEType: | PE32+ |
| LinkerVersion: | 14.43 |
| CodeSize: | 173568 |
| InitializedDataSize: | 162304 |
| UninitializedDataSize: | - |
| EntryPoint: | 0xce30 |
| OSVersion: | 6 |
| ImageVersion: | - |
| SubsystemVersion: | 6 |
| Subsystem: | Windows GUI |
Total processes
138
Monitored processes
3
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 3820 | "C:\Users\admin\Desktop\factorio_mod_downloader-0.2.2.exe" | C:\Users\admin\Desktop\factorio_mod_downloader-0.2.2.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Modules
| |||||||||||||||
| 5628 | C:\WINDOWS\System32\slui.exe -Embedding | C:\Windows\System32\slui.exe | svchost.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Activation Client Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6948 | "C:\Users\admin\Desktop\factorio_mod_downloader-0.2.2.exe" | C:\Users\admin\Desktop\factorio_mod_downloader-0.2.2.exe | — | factorio_mod_downloader-0.2.2.exe | |||||||||||
User: admin Integrity Level: MEDIUM Modules
| |||||||||||||||
Total events
3 762
Read events
3 762
Write events
0
Delete events
0
Modification events
Executable files
35
Suspicious files
16
Text files
1 082
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3820 | factorio_mod_downloader-0.2.2.exe | C:\Users\admin\AppData\Local\Temp\_MEI38202\PIL\_imagingtk.cp313-win_amd64.pyd | executable | |
MD5:2CC0C18F26989042CDAD77EFE3CCF3FB | SHA256:A3183192C1CDC7B2D8331B6B78EED6826A0A0594FE45B06FD0E9809414AD6A53 | |||
| 3820 | factorio_mod_downloader-0.2.2.exe | C:\Users\admin\AppData\Local\Temp\_MEI38202\CTkMessagebox\icons\warning.png | image | |
MD5:55A808002C151452522E952D085BFD73 | SHA256:58997C1ECAE1FD72AFDEBB92792FB50B08ADBD556A707B30A75855DB53BDB737 | |||
| 3820 | factorio_mod_downloader-0.2.2.exe | C:\Users\admin\AppData\Local\Temp\_MEI38202\CTkMessagebox\icons\check.png | image | |
MD5:02E793010475310E5EE8AA9B57F4C395 | SHA256:1645515D51411C5231E72CC33A51B093A9AAA97CF3D8B801E567A60D8691C2B6 | |||
| 3820 | factorio_mod_downloader-0.2.2.exe | C:\Users\admin\AppData\Local\Temp\_MEI38202\PIL\_imaging.cp313-win_amd64.pyd | executable | |
MD5:A487E7AD30ED2DE466A8590A24D745E7 | SHA256:31621E7BB62091C2AA80CAC5F5C929132AF3EC568A061680564DC073F2630357 | |||
| 3820 | factorio_mod_downloader-0.2.2.exe | C:\Users\admin\AppData\Local\Temp\_MEI38202\CTkMessagebox\icons\info.png | image | |
MD5:86B817BACD70FAA8BBF57A157FC5F219 | SHA256:5D0F7B7F4E2632E7131D56783D1F90A0E96914893EF11458DB6E4C1F2C68B68C | |||
| 3820 | factorio_mod_downloader-0.2.2.exe | C:\Users\admin\AppData\Local\Temp\_MEI38202\_ctypes.pyd | executable | |
MD5:29873384E13B0A78EE9857604161514B | SHA256:3CC8500A958CC125809B0467930EBCCE88A09DCC0CEDD7A45FACF3E332F7DB33 | |||
| 3820 | factorio_mod_downloader-0.2.2.exe | C:\Users\admin\AppData\Local\Temp\_MEI38202\_lzma.pyd | executable | |
MD5:D63E2E743EA103626D33B3C1D882F419 | SHA256:7C2D2030D5D246739C5D85F087FCF404BC36E1815E69A8AC7C9541267734FC28 | |||
| 3820 | factorio_mod_downloader-0.2.2.exe | C:\Users\admin\AppData\Local\Temp\_MEI38202\CTkMessagebox\icons\question.png | image | |
MD5:ED57166A4DE94ADB66491FB28F69DADE | SHA256:22AD8D785FF7DE417F3424D28F81F7F99E4F3886AD53486E28699FD67A656B83 | |||
| 3820 | factorio_mod_downloader-0.2.2.exe | C:\Users\admin\AppData\Local\Temp\_MEI38202\_decimal.pyd | executable | |
MD5:21FCB8E3D4310346A5DC1A216E7E23CA | SHA256:9A0E05274CAD8D90F6BA6BC594261B36BFBDDF4F5CA6846B6367FE6A4E2FDCE4 | |||
| 3820 | factorio_mod_downloader-0.2.2.exe | C:\Users\admin\AppData\Local\Temp\_MEI38202\VCRUNTIME140.dll | executable | |
MD5:32DA96115C9D783A0769312C0482A62D | SHA256:8B10C53241726B0ACC9F513157E67FCB01C166FEC69E5E38CA6AADA8F9A3619F | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
36
TCP/UDP connections
51
DNS requests
20
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
1268 | svchost.exe | GET | 200 | 23.53.40.178:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
5944 | MoUsoCoreWorker.exe | GET | 200 | 23.53.40.178:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
2468 | RUXIMICS.exe | GET | 200 | 23.53.40.178:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
1268 | svchost.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
5944 | MoUsoCoreWorker.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
2468 | RUXIMICS.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
— | — | POST | 200 | 20.190.160.66:443 | https://login.live.com/RST2.srf | unknown | xml | 1.24 Kb | whitelisted |
— | — | POST | 200 | 20.190.159.23:443 | https://login.live.com/RST2.srf | unknown | xml | 11.1 Kb | whitelisted |
— | — | POST | 200 | 40.126.31.3:443 | https://login.live.com/RST2.srf | unknown | xml | 11.1 Kb | whitelisted |
— | — | GET | 304 | 20.109.210.53:443 | https://slscr.update.microsoft.com/SLS/%7B522D76A4-93E1-47F8-B8CE-07C937AD1A1E%7D/x64/10.0.19045.4046/0?CH=686&L=en-US&P=&PT=0x30&WUA=10.0.19041.3996&MK=DELL&MD=DELL | unknown | — | — | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
5944 | MoUsoCoreWorker.exe | 4.231.128.59:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
2468 | RUXIMICS.exe | 4.231.128.59:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
1268 | svchost.exe | 4.231.128.59:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
1268 | svchost.exe | 23.53.40.178:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
5944 | MoUsoCoreWorker.exe | 23.53.40.178:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
2468 | RUXIMICS.exe | 23.53.40.178:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
1268 | svchost.exe | 23.35.229.160:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
5944 | MoUsoCoreWorker.exe | 23.35.229.160:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
google.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
settings-win.data.microsoft.com |
| whitelisted |
login.live.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
nexusrules.officeapps.live.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |
activation-v2.sls.microsoft.com |
| whitelisted |