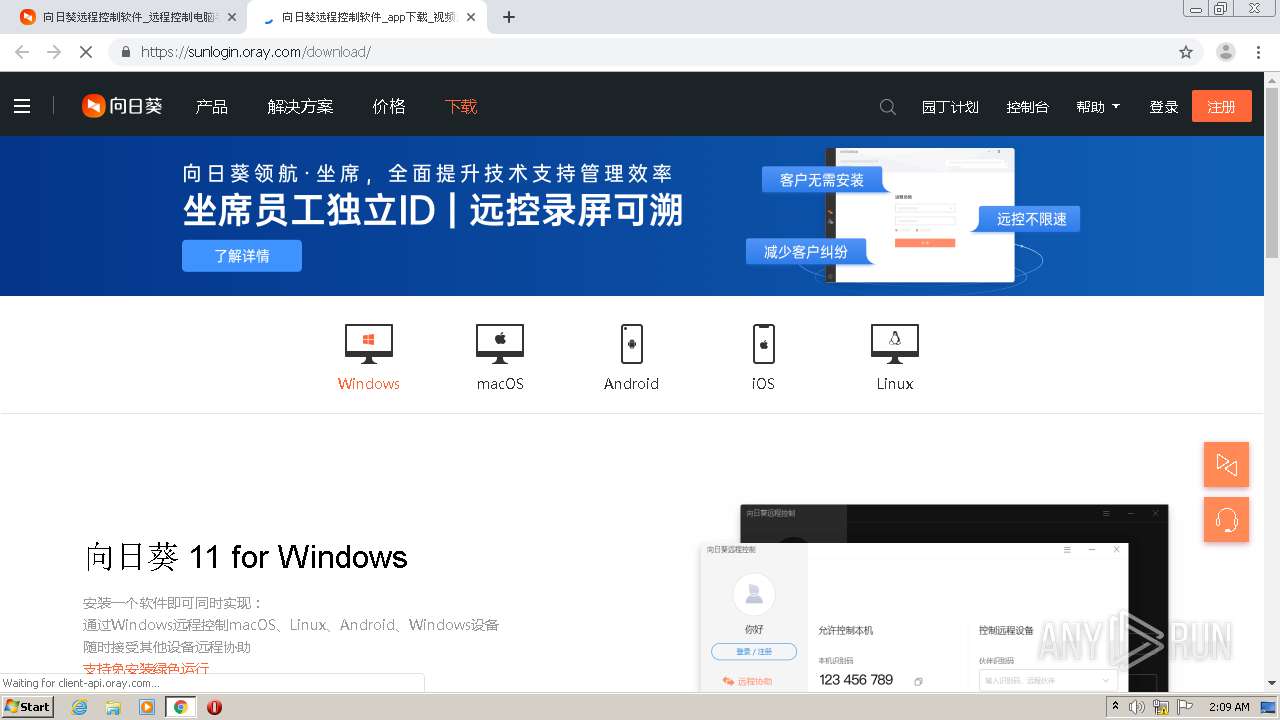
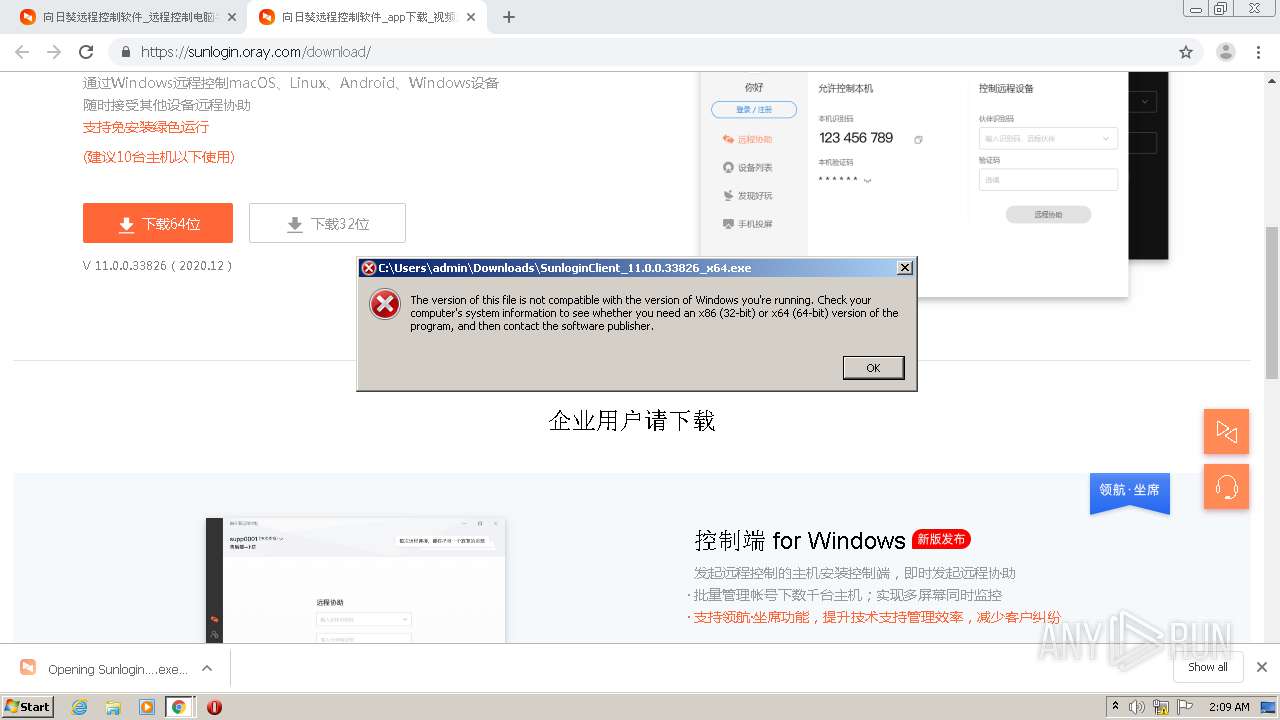
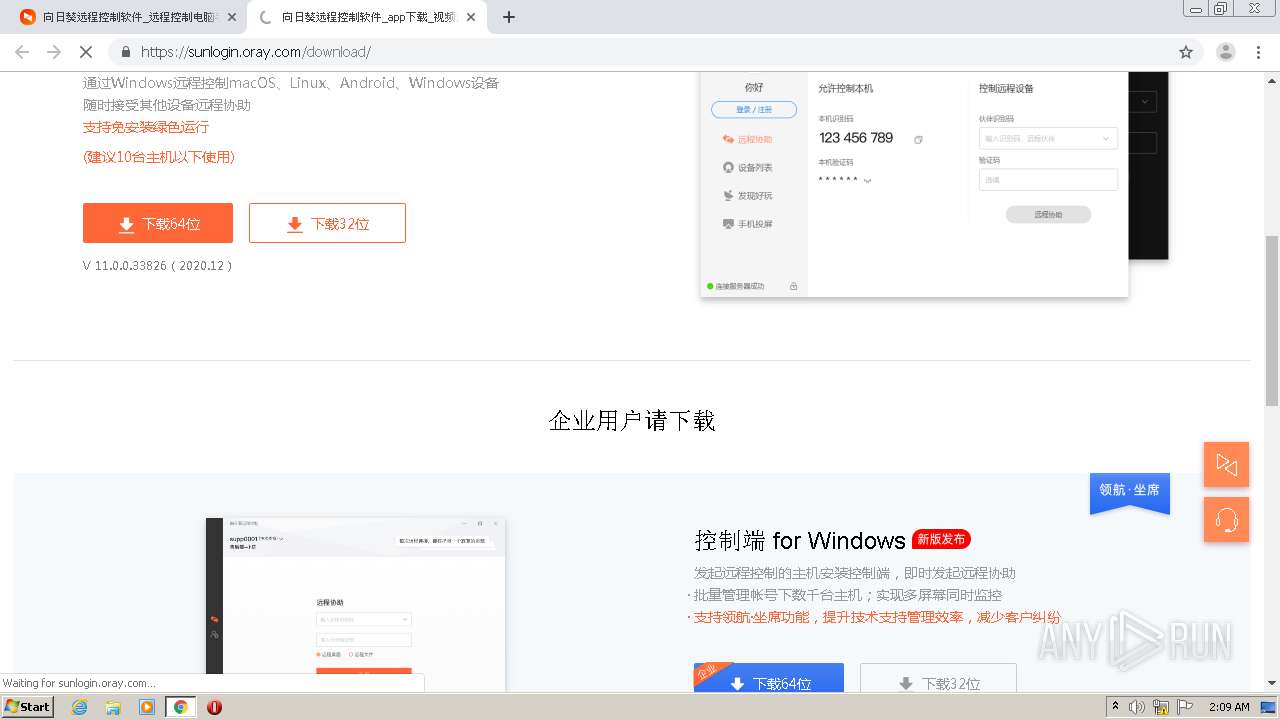
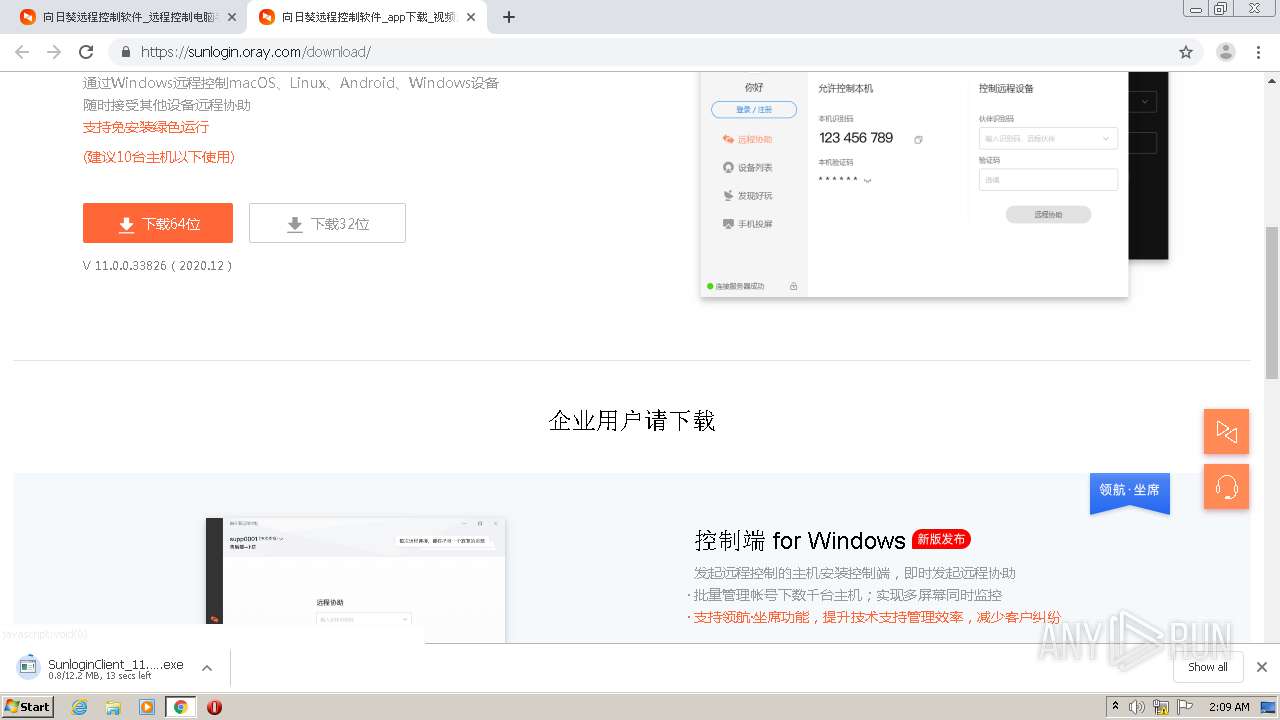
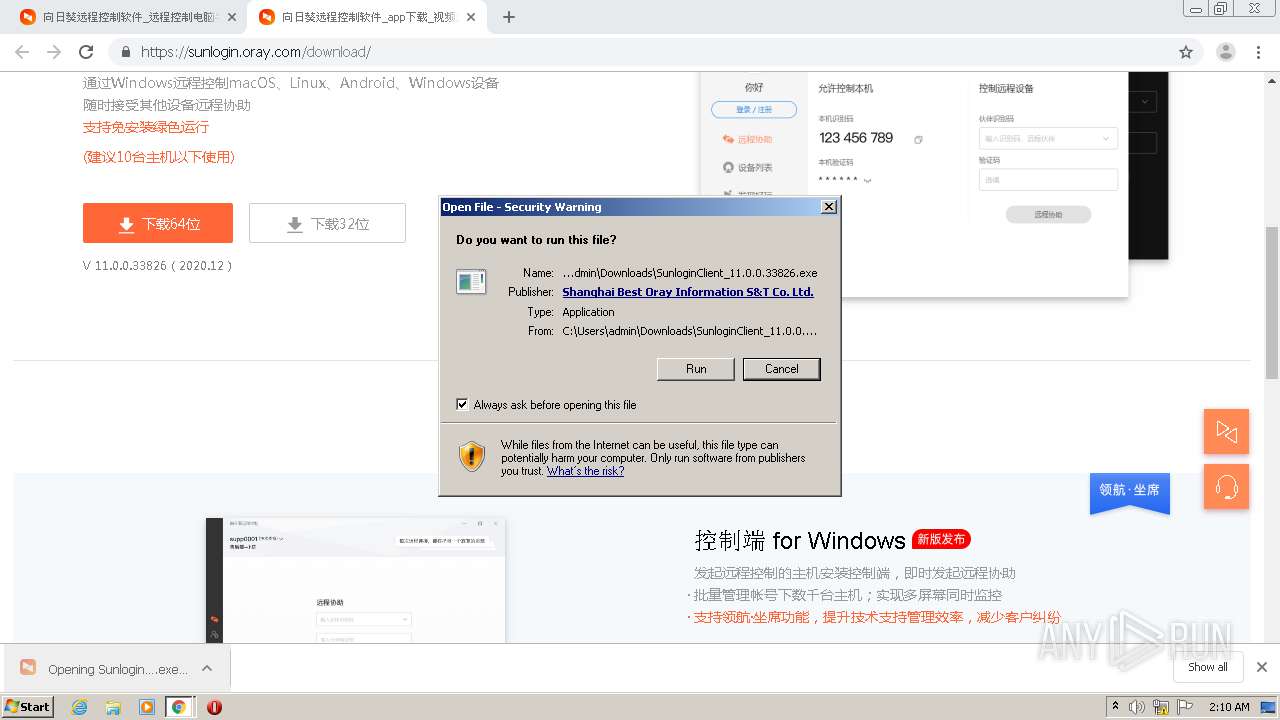
| URL: | https://sunlogin.oray.com/ |
| Full analysis: | https://app.any.run/tasks/42688157-f00e-4269-bf7d-a7d655497445 |
| Verdict: | Malicious activity |
| Analysis date: | December 28, 2020, 02:08:42 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MD5: | 8B12B7A9ADF7DB3533A2C7CD80BBE39E |
| SHA1: | 4E36D0656716007EAD2E6E68E6F888D8A44332B2 |
| SHA256: | 49690E1C1DC21237778BA4DB3EDC19D02898FF6059036B9682C5AA926529FD8F |
| SSDEEP: | 3:N8d9KMEcLGGn:2qmLGG |
MALICIOUS
Changes the autorun value in the registry
- SunloginClient_11.0.0.33826.exe (PID: 2220)
Application was dropped or rewritten from another process
- SunloginClient_11.0.0.33826.exe (PID: 3820)
- SunloginClient_11.0.0.33826.exe (PID: 2220)
- SunloginClient.exe (PID: 2248)
- devcon.exe (PID: 2160)
- SunloginClient.exe (PID: 3620)
- SunloginClient.exe (PID: 4052)
- SunloginClient.exe (PID: 2608)
- SunloginClient.exe (PID: 3584)
Changes settings of System certificates
- devcon.exe (PID: 2160)
Drops executable file immediately after starts
- SunloginClient.exe (PID: 3620)
- DrvInst.exe (PID: 1416)
SUSPICIOUS
Cleans NTFS data-stream (Zone Identifier)
- SunloginClient_11.0.0.33826.exe (PID: 3820)
Creates a directory in Program Files
- SunloginClient_11.0.0.33826.exe (PID: 2220)
- SunloginClient.exe (PID: 3620)
Drops a file with a compile date too recent
- SunloginClient_11.0.0.33826.exe (PID: 2220)
- SunloginClient.exe (PID: 3620)
- chrome.exe (PID: 2488)
- DrvInst.exe (PID: 1416)
- devcon.exe (PID: 2160)
- DrvInst.exe (PID: 1248)
Application launched itself
- cmd.exe (PID: 2916)
- SunloginClient_11.0.0.33826.exe (PID: 3820)
- SunloginClient.exe (PID: 3620)
Starts CMD.EXE for commands execution
- SunloginClient_11.0.0.33826.exe (PID: 2220)
- cmd.exe (PID: 2916)
Executable content was dropped or overwritten
- chrome.exe (PID: 2488)
- SunloginClient_11.0.0.33826.exe (PID: 2220)
- devcon.exe (PID: 2160)
- SunloginClient.exe (PID: 3620)
- DrvInst.exe (PID: 1416)
- DrvInst.exe (PID: 1248)
Creates files in the program directory
- SunloginClient_11.0.0.33826.exe (PID: 2220)
- SunloginClient.exe (PID: 3620)
- SunloginClient.exe (PID: 4052)
- SunloginClient.exe (PID: 3584)
Uses NETSH.EXE for network configuration
- cmd.exe (PID: 3948)
- cmd.exe (PID: 1508)
- cmd.exe (PID: 3628)
- cmd.exe (PID: 1848)
- cmd.exe (PID: 3780)
- cmd.exe (PID: 3140)
Executed as Windows Service
- SunloginClient.exe (PID: 3620)
Starts itself from another location
- SunloginClient_11.0.0.33826.exe (PID: 2220)
Creates a software uninstall entry
- SunloginClient_11.0.0.33826.exe (PID: 2220)
Adds / modifies Windows certificates
- devcon.exe (PID: 2160)
Drops a file that was compiled in debug mode
- devcon.exe (PID: 2160)
- DrvInst.exe (PID: 1416)
- DrvInst.exe (PID: 1248)
- SunloginClient_11.0.0.33826.exe (PID: 2220)
Executed via COM
- DrvInst.exe (PID: 1416)
- DrvInst.exe (PID: 1248)
Creates files in the driver directory
- DrvInst.exe (PID: 1416)
- DrvInst.exe (PID: 1248)
Creates files in the Windows directory
- DrvInst.exe (PID: 1416)
- DrvInst.exe (PID: 1248)
Removes files from Windows directory
- DrvInst.exe (PID: 1416)
- DrvInst.exe (PID: 1248)
Drops a file with too old compile date
- SunloginClient_11.0.0.33826.exe (PID: 2220)
INFO
Reads the hosts file
- chrome.exe (PID: 768)
- chrome.exe (PID: 2488)
Application launched itself
- chrome.exe (PID: 2488)
Reads settings of System Certificates
- devcon.exe (PID: 2160)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
77
Monitored processes
35
Malicious processes
8
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 768 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --field-trial-handle=1000,5466268395768713521,9049940342860823562,131072 --enable-features=PasswordImport --lang=en-US --service-sandbox-type=network --service-request-channel-token=6364556479292187320 --mojo-platform-channel-handle=1480 /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | chrome.exe | ||||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 944 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=gpu-process --field-trial-handle=1000,5466268395768713521,9049940342860823562,131072 --enable-features=PasswordImport --gpu-preferences=KAAAAAAAAADgACAgAQAAAAAAAAAAAGAAAAAAAAAAAAAIAAAAAAAAACgAAAAEAAAAIAAAAAAAAAAoAAAAAAAAADAAAAAAAAAAOAAAAAAAAAAQAAAAAAAAAAAAAAAFAAAAEAAAAAAAAAAAAAAABgAAABAAAAAAAAAAAQAAAAUAAAAQAAAAAAAAAAEAAAAGAAAA --service-request-channel-token=4167830258203466410 --mojo-platform-channel-handle=1004 --ignored=" --type=renderer " /prefetch:2 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 1004 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=1000,5466268395768713521,9049940342860823562,131072 --enable-features=PasswordImport --lang=en-US --enable-offline-auto-reload --enable-offline-auto-reload-visible-only --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --service-request-channel-token=4346516207986822945 --renderer-client-id=6 --no-v8-untrusted-code-mitigations --mojo-platform-channel-handle=2156 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 1036 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=watcher --main-thread-id=2068 --on-initialized-event-handle=316 --parent-handle=320 /prefetch:6 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 1192 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --field-trial-handle=1000,5466268395768713521,9049940342860823562,131072 --enable-features=PasswordImport --lang=en-US --no-sandbox --service-request-channel-token=16084894286486616141 --mojo-platform-channel-handle=1976 /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 1248 | DrvInst.exe "2" "211" "ROOT\DISPLAY\0000" "C:\Windows\INF\oem4.inf" "oraymir.inf:Oray:OrayMir_Inst:1.0.1.17485:c50b00d7-ae62-4936-8bc8-20e0b9f0befb" "6e6179ed3" "000004D0" "000005E0" "000005E4" | C:\Windows\system32\DrvInst.exe | svchost.exe | ||||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Driver Installation Module Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1416 | DrvInst.exe "4" "0" "C:\Users\admin\AppData\Local\Temp\{41898871-8c5c-154f-ec7f-ef7503194d0a}\oraymir.inf" "0" "6e6179ed3" "000003EC" "WinSta0\Default" "000004D0" "208" "c:\program files\oray\sunlogin\sunloginclient\driver\mirror" | C:\Windows\system32\DrvInst.exe | svchost.exe | ||||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Driver Installation Module Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1508 | cmd /c netsh advfirewall firewall add rule name="SunloginClient" dir=in action=allow program="C:\Program Files\Oray\SunLogin\SunloginClient\SunloginClient.exe" protocol=udp enable=yes profile=public | C:\Windows\system32\cmd.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 1524 | netsh advfirewall firewall add rule name="SunloginClient" dir=in action=allow program="C:\Program Files\Oray\SunLogin\SunloginClient\SunloginClient.exe" protocol=udp enable=yes profile=domain | C:\Windows\system32\netsh.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Network Command Shell Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1848 | cmd /c netsh advfirewall firewall add rule name="SunloginClient" dir=in action=allow program="C:\Program Files\Oray\SunLogin\SunloginClient\SunloginClient.exe" protocol=tcp enable=yes profile=private | C:\Windows\system32\cmd.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
Total events
1 996
Read events
1 583
Write events
408
Delete events
5
Modification events
| (PID) Process: | (2488) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\BLBeacon |
| Operation: | write | Name: | failed_count |
Value: 0 | |||
| (PID) Process: | (2488) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\BLBeacon |
| Operation: | write | Name: | state |
Value: 2 | |||
| (PID) Process: | (2488) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\ThirdParty |
| Operation: | write | Name: | StatusCodes |
Value: | |||
| (PID) Process: | (2488) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\ThirdParty |
| Operation: | write | Name: | StatusCodes |
Value: 01000000 | |||
| (PID) Process: | (2488) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\BLBeacon |
| Operation: | write | Name: | state |
Value: 1 | |||
| (PID) Process: | (1036) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\BrowserExitCodes |
| Operation: | write | Name: | 2488-13253594939810500 |
Value: 259 | |||
| (PID) Process: | (2488) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Update\ClientState\{8A69D345-D564-463c-AFF1-A69D9E530F96} |
| Operation: | write | Name: | dr |
Value: 1 | |||
| (PID) Process: | (2488) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome |
| Operation: | write | Name: | UsageStatsInSample |
Value: 0 | |||
| (PID) Process: | (2488) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\BrowserExitCodes |
| Operation: | delete value | Name: | 3252-13245750958665039 |
Value: 0 | |||
| (PID) Process: | (2488) chrome.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Google\Update\ClientStateMedium\{8A69D345-D564-463C-AFF1-A69D9E530F96} |
| Operation: | write | Name: | usagestats |
Value: 0 | |||
Executable files
34
Suspicious files
77
Text files
214
Unknown types
17
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2488 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\BrowserMetrics\BrowserMetrics-5FE93E3C-9B8.pma | — | |
MD5:— | SHA256:— | |||
| 2488 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\968ea505-0369-47d3-ac35-234a3fe3bf97.tmp | — | |
MD5:— | SHA256:— | |||
| 2488 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\data_reduction_proxy_leveldb\000048.dbtmp | — | |
MD5:— | SHA256:— | |||
| 2488 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\data_reduction_proxy_leveldb\LOG.old | text | |
MD5:— | SHA256:— | |||
| 2488 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\BudgetDatabase\LOG.old | text | |
MD5:— | SHA256:— | |||
| 2488 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\data_reduction_proxy_leveldb\LOG.old~RF1273d0.TMP | text | |
MD5:— | SHA256:— | |||
| 2488 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\Sync Data\LevelDB\LOG.old~RF1273c1.TMP | text | |
MD5:— | SHA256:— | |||
| 2488 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\Site Characteristics Database\LOG.old | text | |
MD5:— | SHA256:— | |||
| 2488 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\shared_proto_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 2488 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\shared_proto_db\LOG.old~RF127670.TMP | — | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
72
DNS requests
33
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
768 | chrome.exe | 47.110.217.173:443 | sunlogin.oray.com | — | CN | unknown |
768 | chrome.exe | 163.181.56.207:443 | res.orayimg.com | — | US | suspicious |
768 | chrome.exe | 103.235.46.191:443 | hm.baidu.com | Beijing Baidu Netcom Science and Technology Co., Ltd. | HK | suspicious |
768 | chrome.exe | 101.37.127.85:443 | webchat.7moor.com | Hangzhou Alibaba Advertising Co.,Ltd. | CN | unknown |
768 | chrome.exe | 121.199.57.34:443 | user-api.oray.com | Hangzhou Alibaba Advertising Co.,Ltd. | CN | unknown |
— | — | 163.181.56.207:443 | res.orayimg.com | — | US | suspicious |
768 | chrome.exe | 120.26.3.164:443 | tk.oray.com | Hangzhou Alibaba Advertising Co.,Ltd. | CN | unknown |
768 | chrome.exe | 110.242.68.204:443 | fxgate.baidu.com | CHINA UNICOM China169 Backbone | CN | unknown |
768 | chrome.exe | 101.89.124.227:443 | upload-cdn.orayimg.com | China Telecom (Group) | CN | unknown |
768 | chrome.exe | 121.196.50.151:443 | client-api.oray.com | Hangzhou Alibaba Advertising Co.,Ltd. | CN | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
sunlogin.oray.com |
| suspicious |
accounts.google.com |
| shared |
res.orayimg.com |
| malicious |
webchat.7moor.com |
| unknown |
static.orayimg.com |
| malicious |
cdn.orayimg.com |
| malicious |
hm.baidu.com |
| whitelisted |
fxgate.baidu.com |
| unknown |
tk.oray.com |
| unknown |
user-api.oray.com |
| unknown |
Threats
Process | Message |
|---|---|
SunloginClient_11.0.0.33826.exe | 2020-12-28 02:10:11.293 - Info - SetDPIAwareness isn't support.
|
SunloginClient_11.0.0.33826.exe | 2020-12-28 02:10:12.659 - Info - SetDPIAwareness isn't support.
|
SunloginClient_11.0.0.33826.exe | 2020-12-28 02:10:15.137 - Info - [http call3] new call id:1, url:https://sl-tk.oray.com/track
|
SunloginClient_11.0.0.33826.exe | 2020-12-28 02:10:15.139 - Info - [http call3] id:1 create new connection : https://sl-tk.oray.com:443
|
SunloginClient_11.0.0.33826.exe | 2020-12-28 02:10:15.164 - Info - attempt to connect server sl-tk.oray.com:443(116.62.101.24:443)
|
SunloginClient_11.0.0.33826.exe | 2020-12-28 02:10:16.416 = Debug = ! This certificate has no flags
|
SunloginClient_11.0.0.33826.exe | 2020-12-28 02:10:16.416 = Debug = ! This certificate has no flags
|
SunloginClient_11.0.0.33826.exe | 2020-12-28 02:10:16.416 = Debug = ! This certificate has no flags
|
SunloginClient_11.0.0.33826.exe | 2020-12-28 02:10:18.154 = Debug = [thread] set thread name Thread-2372 040e053c / 2372
|
SunloginClient_11.0.0.33826.exe | 2020-12-28 02:10:18.159 - Info - [http call3] disconnect id:1, error( 0 )
|