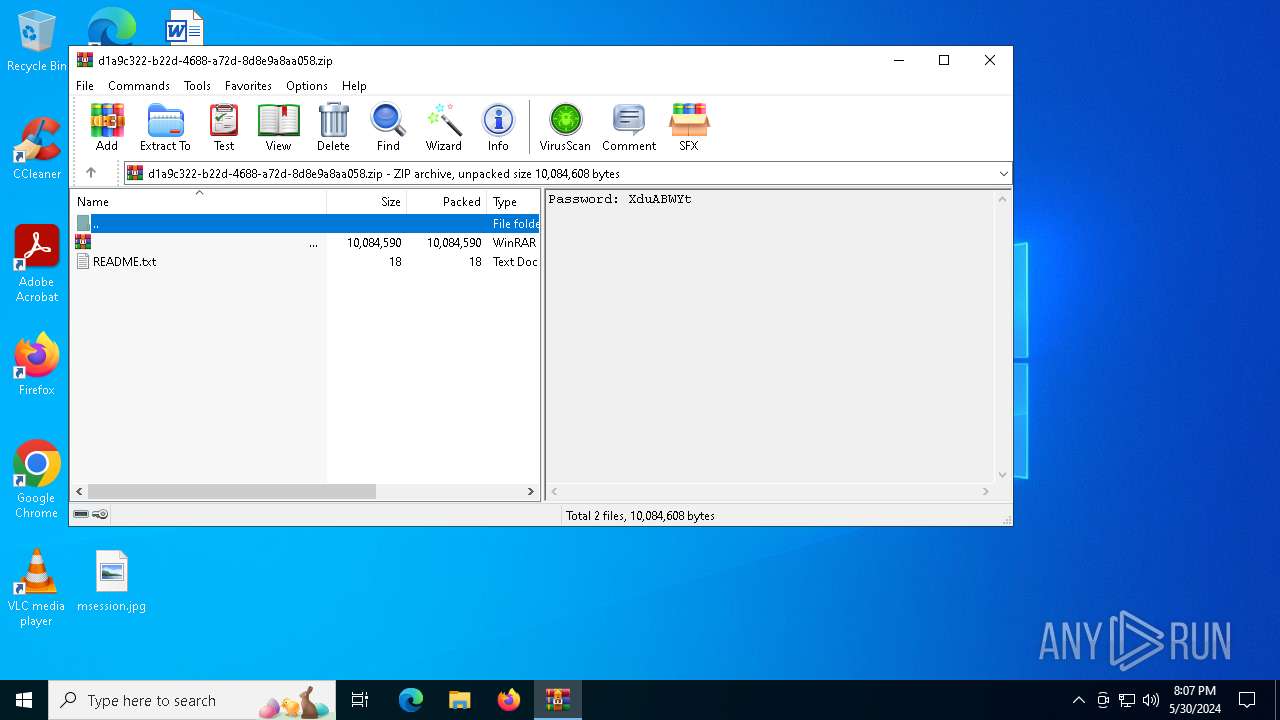
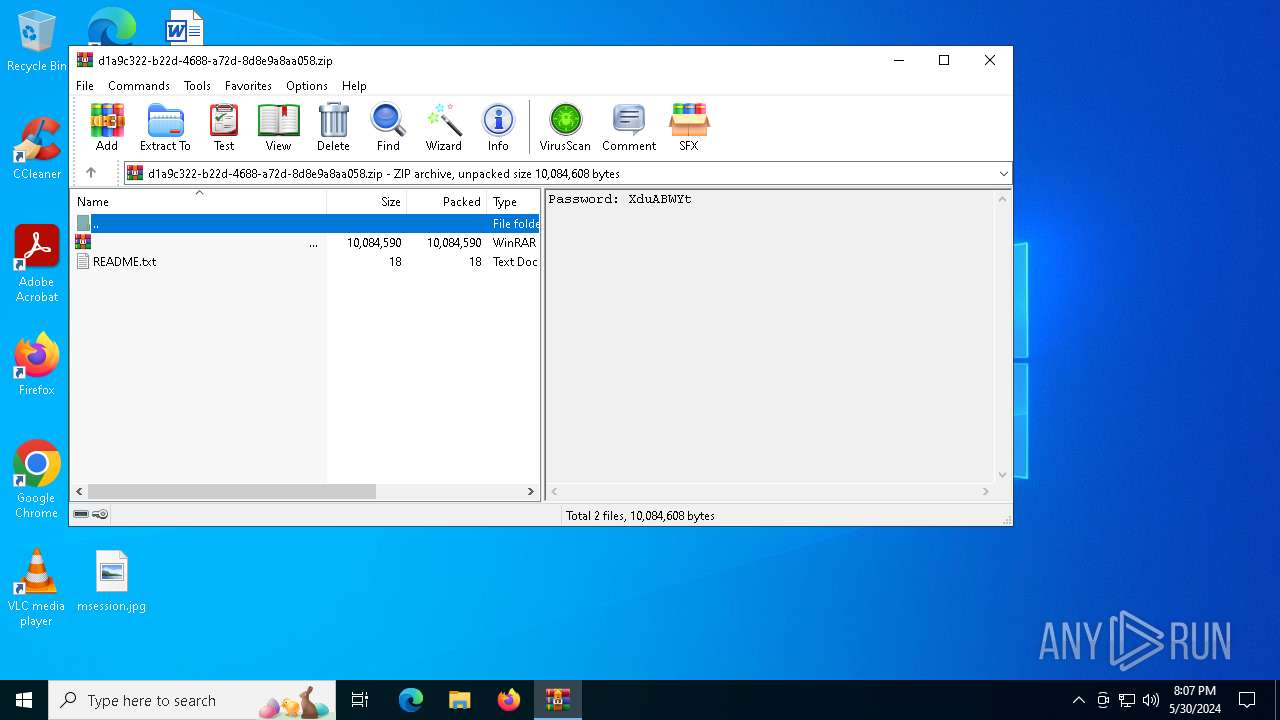
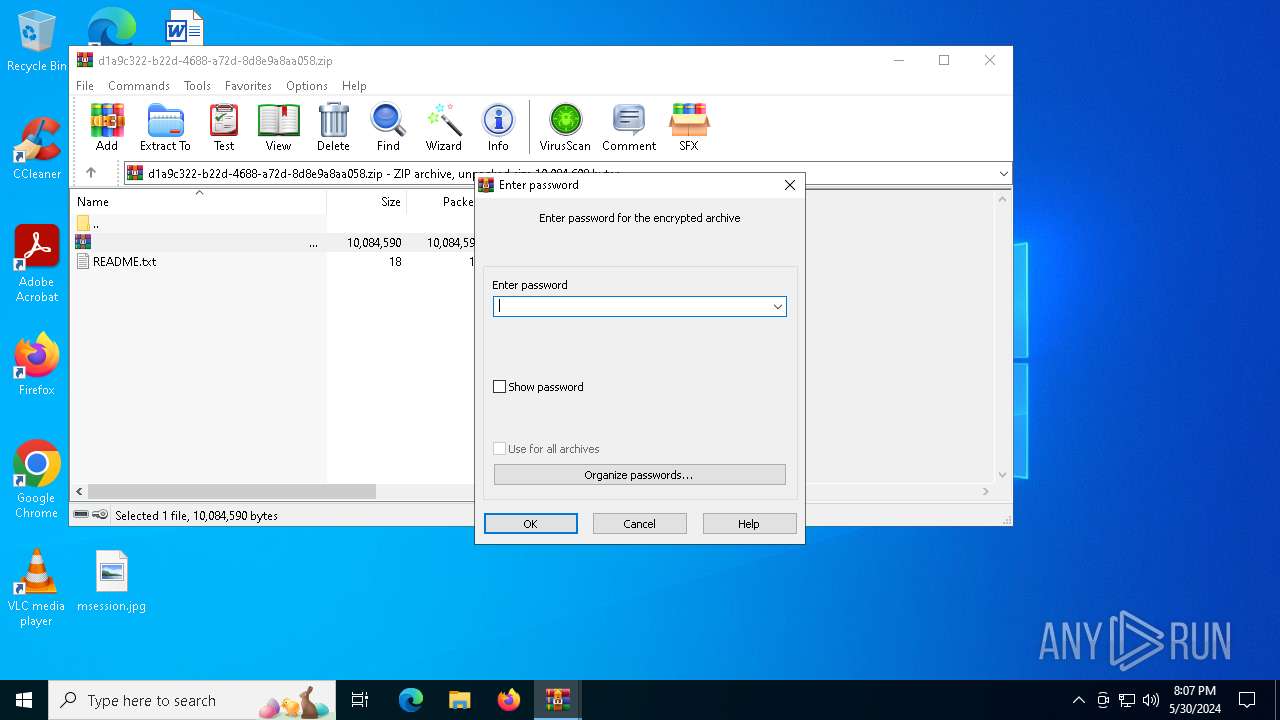
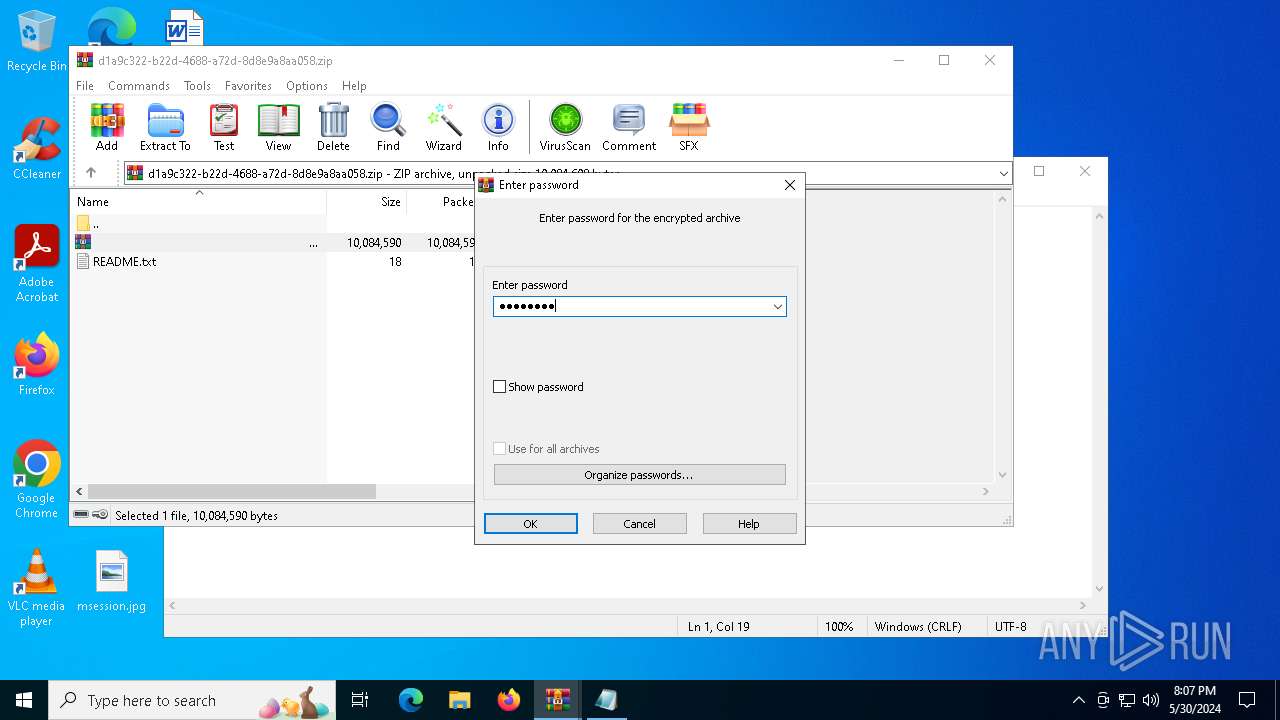
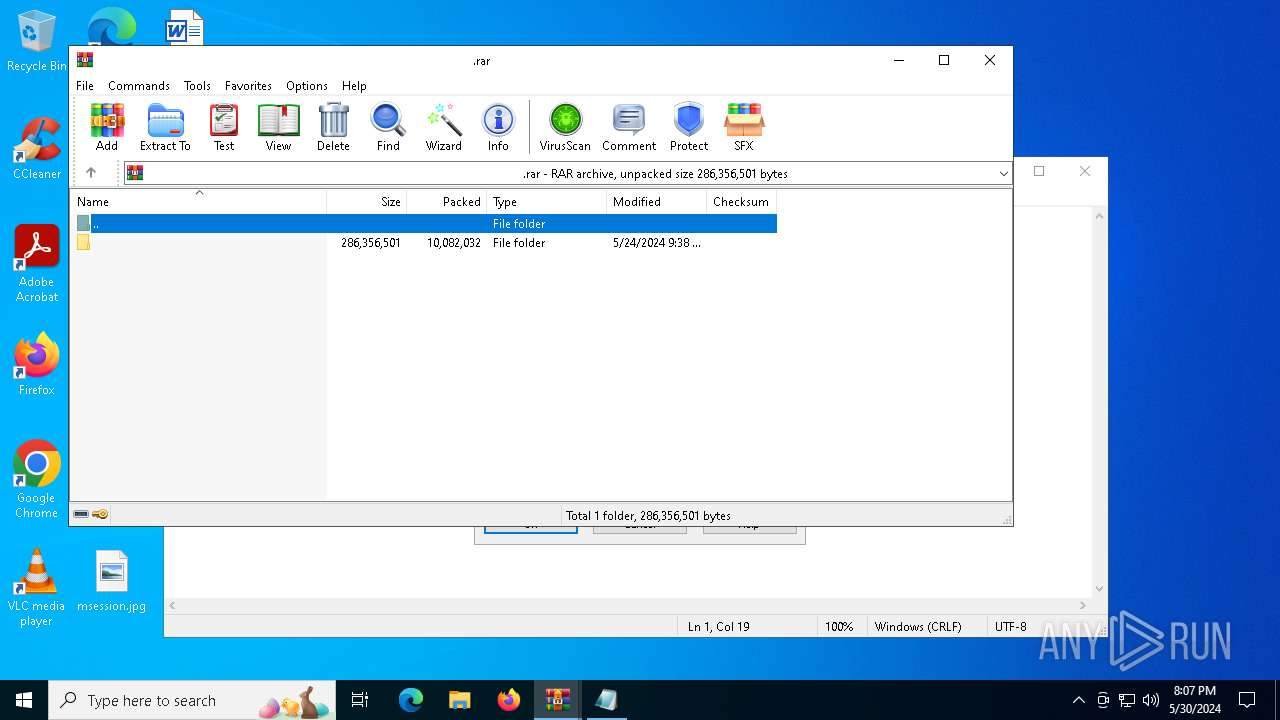
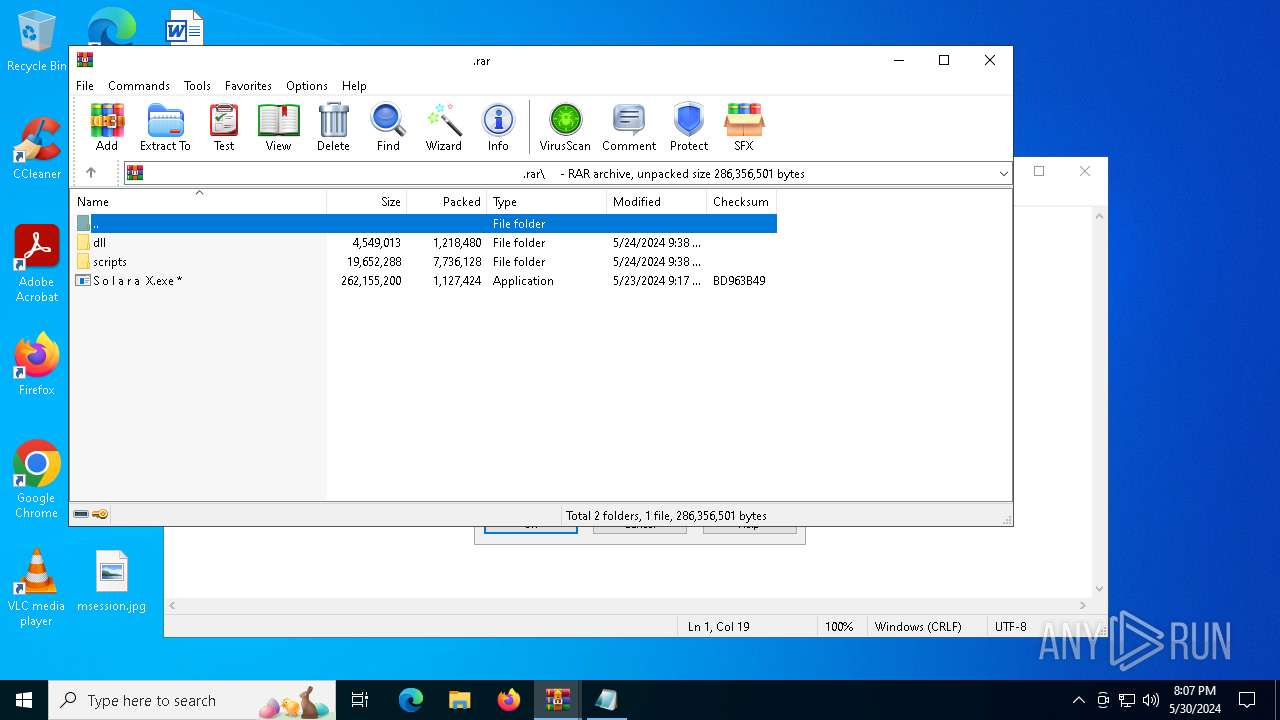
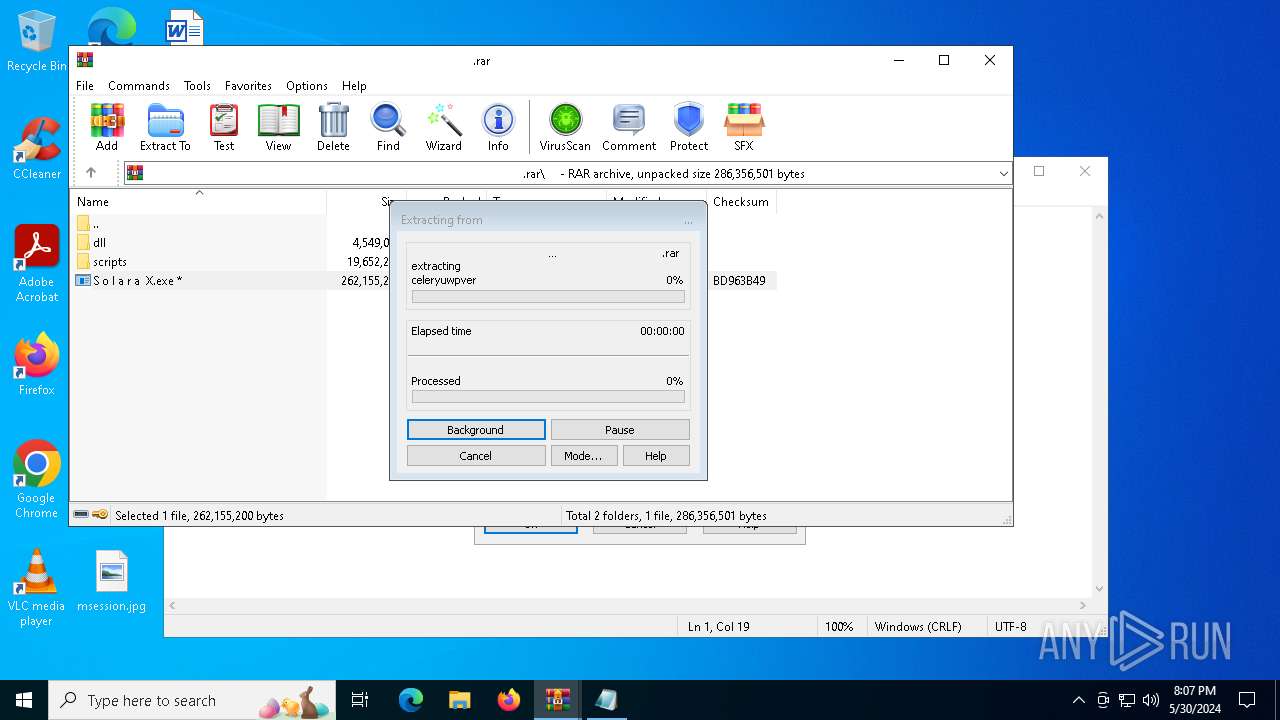
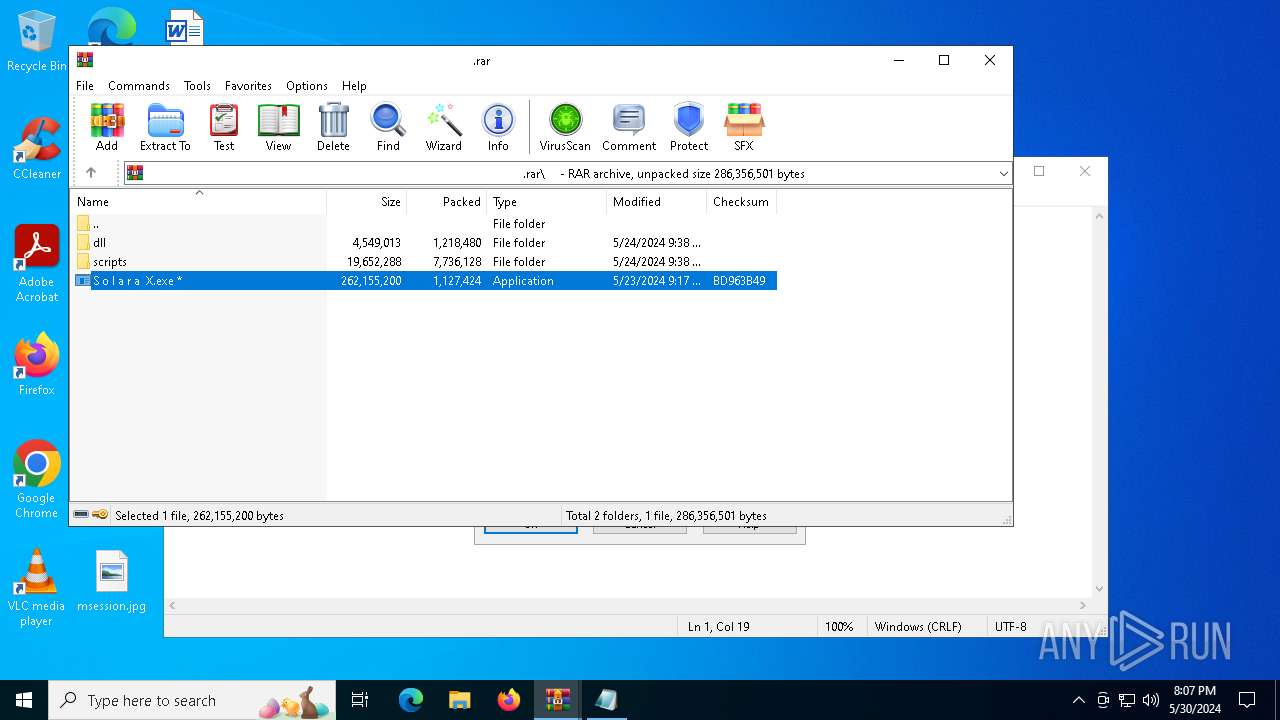
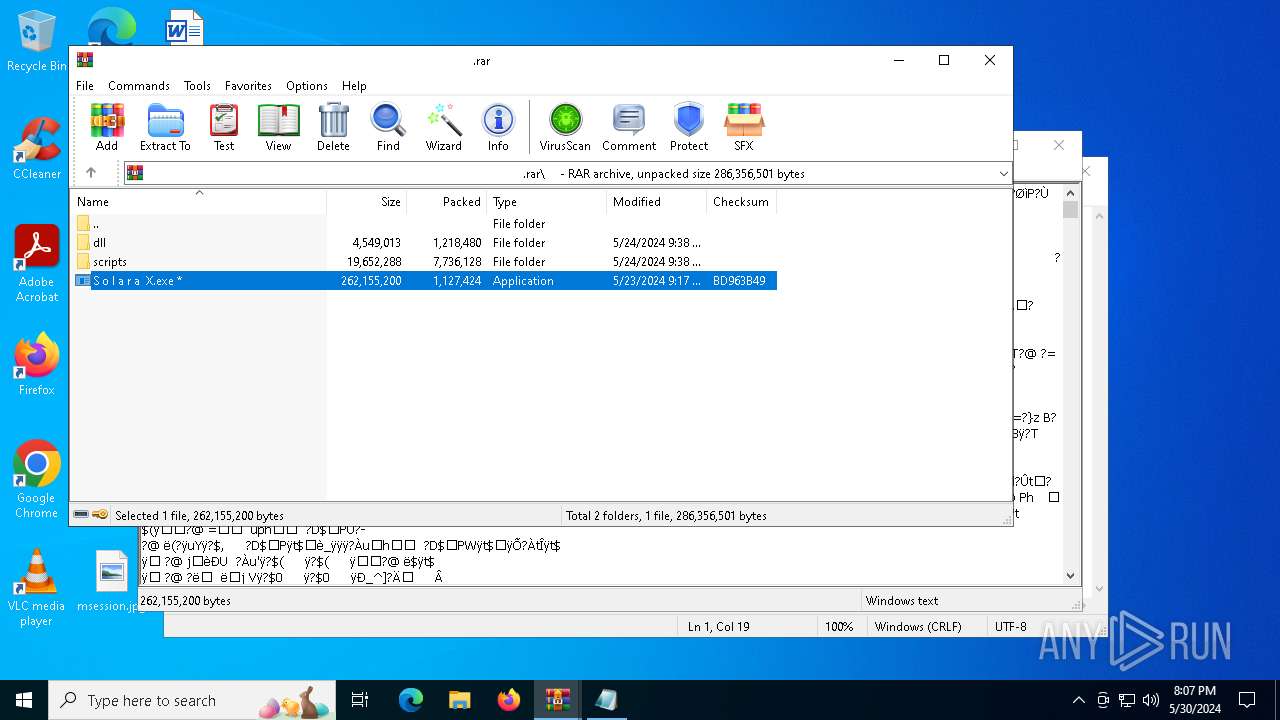
| File name: | .zip |
| Full analysis: | https://app.any.run/tasks/d1a9c322-b22d-4688-a72d-8d8e9a8aa058 |
| Verdict: | Malicious activity |
| Analysis date: | May 30, 2024, 20:06:54 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v1.0 to extract, compression method=store |
| MD5: | 118B664CFFC151B50257F9B058892E75 |
| SHA1: | 40BB786344E6EADBD76721E9B84011D16055E825 |
| SHA256: | 49643B1F483F32112775C305890180D4D11E12FF0A5A3202BFC1B83BC4B4C65F |
| SSDEEP: | 98304:Gafn/rgyYEQf2H74OnI1w0noglyPRvff1bEcE1l0Eb/VIff8nbSJYpXyDIxqOVoz:4QdyHz+ZRl3Cih6k9p3 |
MALICIOUS
Antivirus name has been found in the command line (generic signature)
- findstr.exe (PID: 736)
- findstr.exe (PID: 5428)
Drops the executable file immediately after the start
- cmd.exe (PID: 7156)
SUSPICIOUS
Reads security settings of Internet Explorer
- WinRAR.exe (PID: 6360)
- WinRAR.exe (PID: 7016)
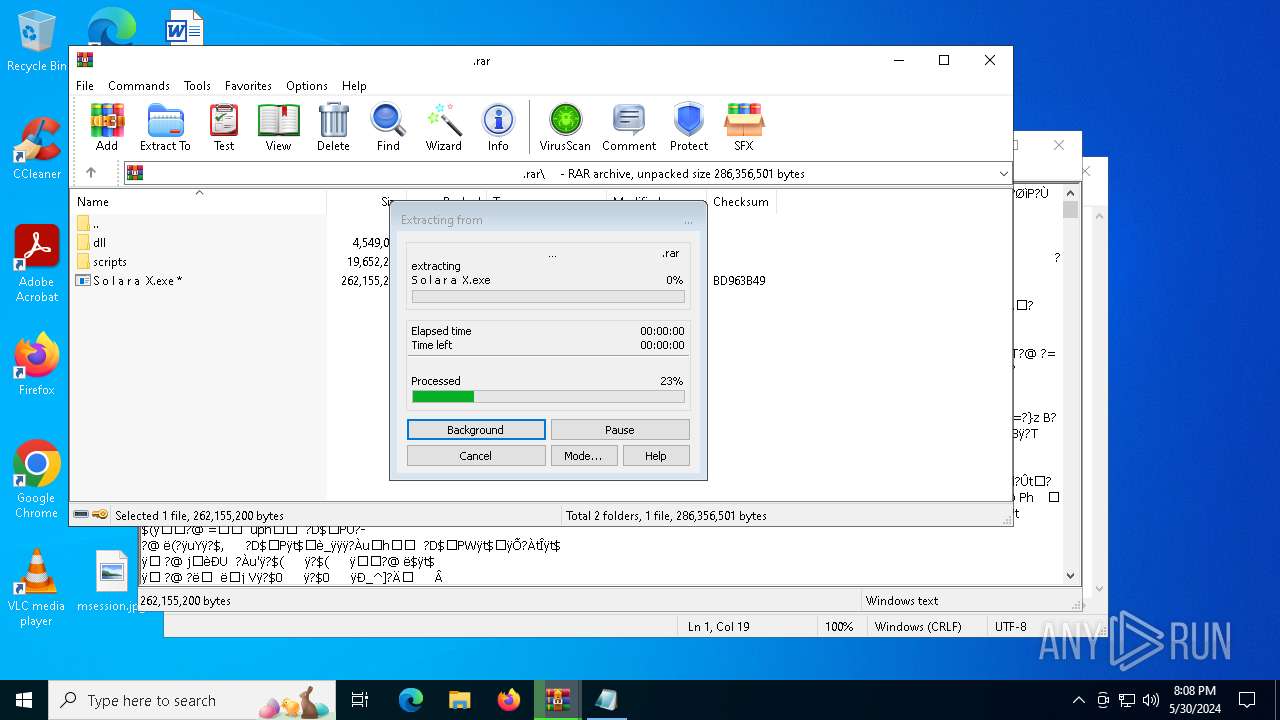
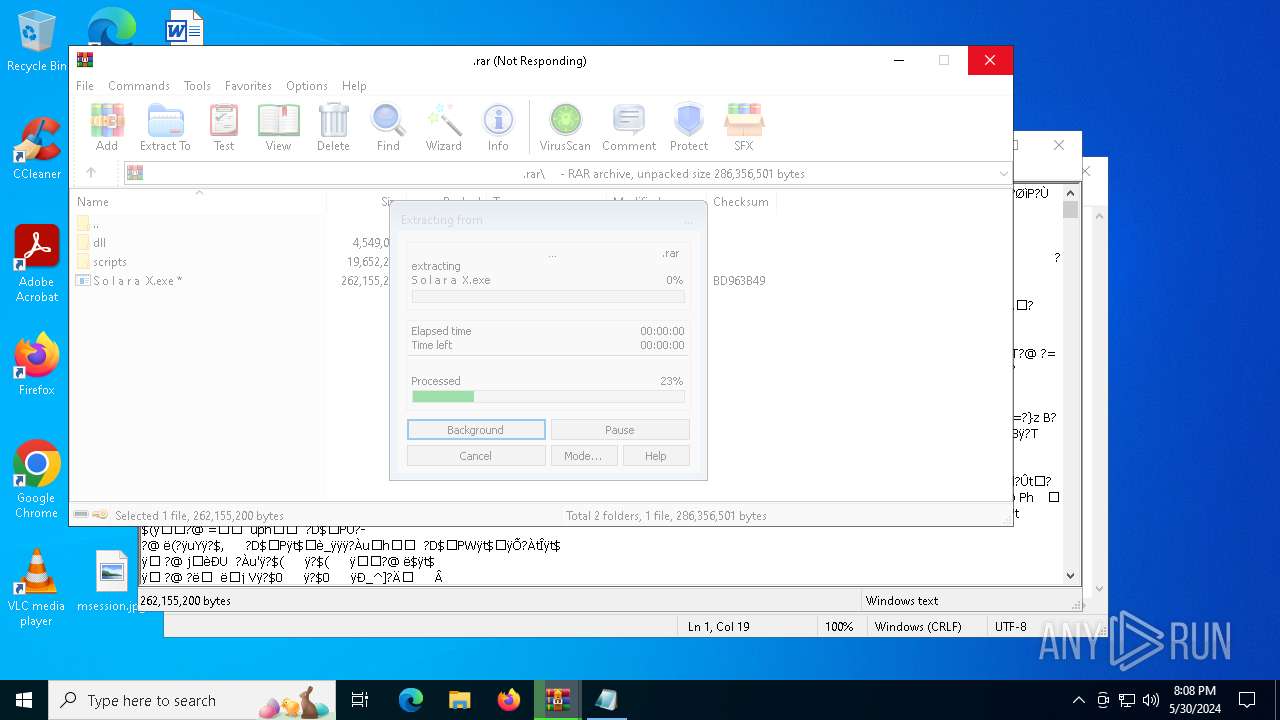
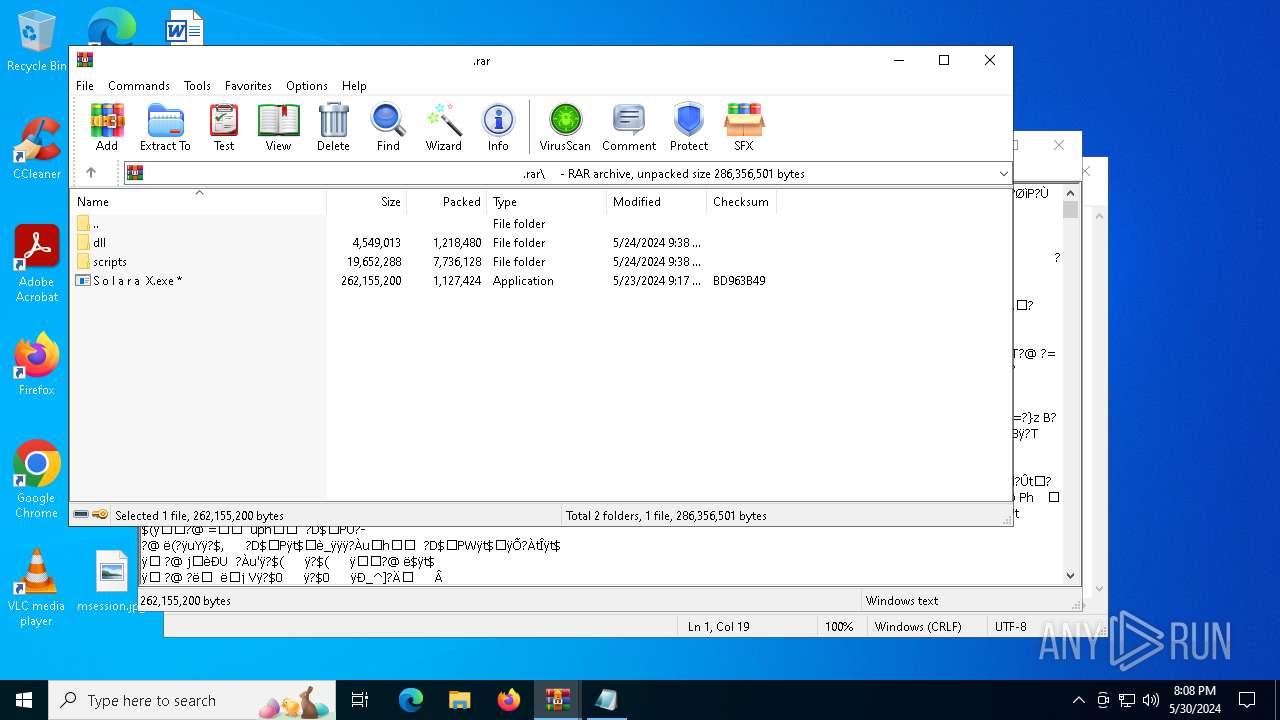
- S o l a r a X.exe (PID: 7096)
Application launched itself
- WinRAR.exe (PID: 6360)
- cmd.exe (PID: 7156)
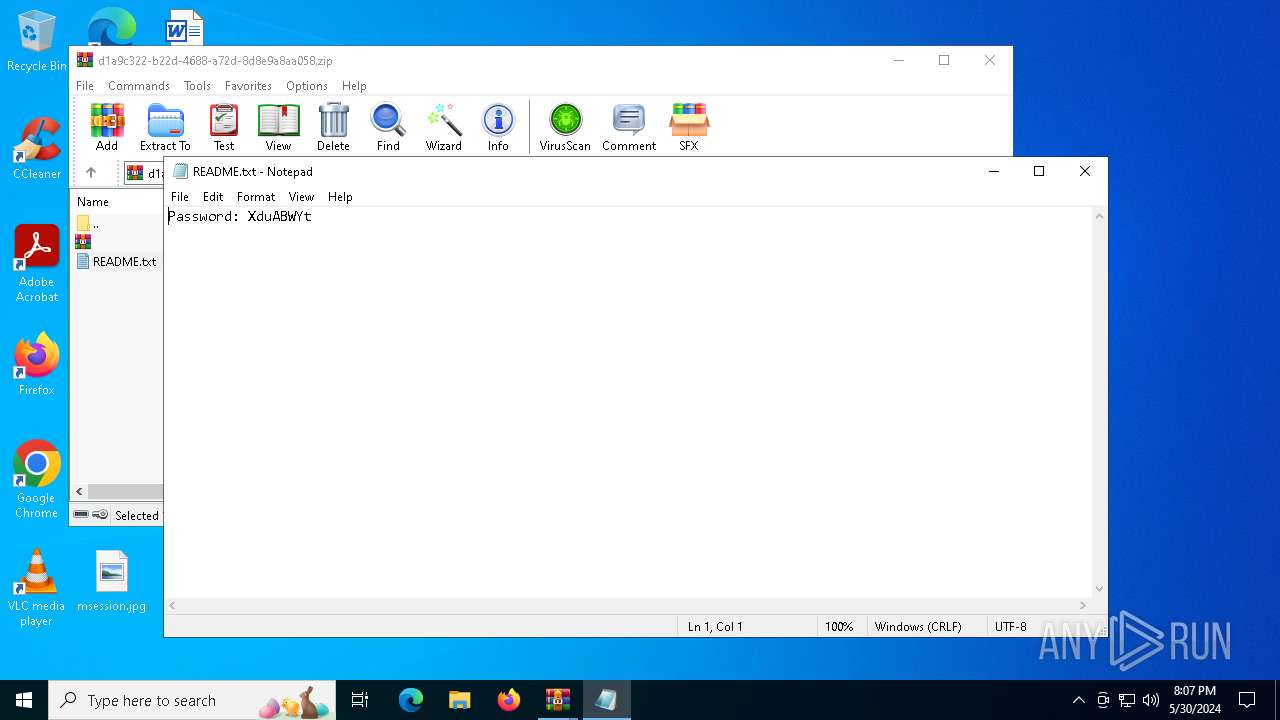
Start notepad (likely ransomware note)
- WinRAR.exe (PID: 6360)
Reads the date of Windows installation
- S o l a r a X.exe (PID: 7096)
Starts CMD.EXE for commands execution
- S o l a r a X.exe (PID: 7096)
- cmd.exe (PID: 7156)
Executing commands from ".cmd" file
- S o l a r a X.exe (PID: 7096)
Get information on the list of running processes
- cmd.exe (PID: 7156)
Using 'findstr.exe' to search for text patterns in files and output
- cmd.exe (PID: 7156)
The executable file from the user directory is run by the CMD process
- Locking.pif (PID: 2740)
Suspicious file concatenation
- cmd.exe (PID: 4720)
Runs PING.EXE to delay simulation
- cmd.exe (PID: 7156)
Executable content was dropped or overwritten
- cmd.exe (PID: 7156)
Drops a file with a rarely used extension (PIF)
- cmd.exe (PID: 7156)
Starts application with an unusual extension
- cmd.exe (PID: 7156)
INFO
Reads Microsoft Office registry keys
- WinRAR.exe (PID: 6360)
Checks supported languages
- S o l a r a X.exe (PID: 7096)
- Locking.pif (PID: 2740)
Create files in a temporary directory
- S o l a r a X.exe (PID: 7096)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 7016)
Reads security settings of Internet Explorer
- notepad.exe (PID: 6908)
Drops the executable file immediately after the start
- WinRAR.exe (PID: 7016)
Reads the computer name
- S o l a r a X.exe (PID: 7096)
- Locking.pif (PID: 2740)
Creates files or folders in the user directory
- S o l a r a X.exe (PID: 7096)
Process checks computer location settings
- S o l a r a X.exe (PID: 7096)
Reads mouse settings
- Locking.pif (PID: 2740)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 10 |
|---|---|
| ZipBitFlag: | - |
| ZipCompression: | None |
| ZipModifyDate: | 2024:05:24 14:39:30 |
| ZipCRC: | 0x363d229e |
| ZipCompressedSize: | 18 |
| ZipUncompressedSize: | 18 |
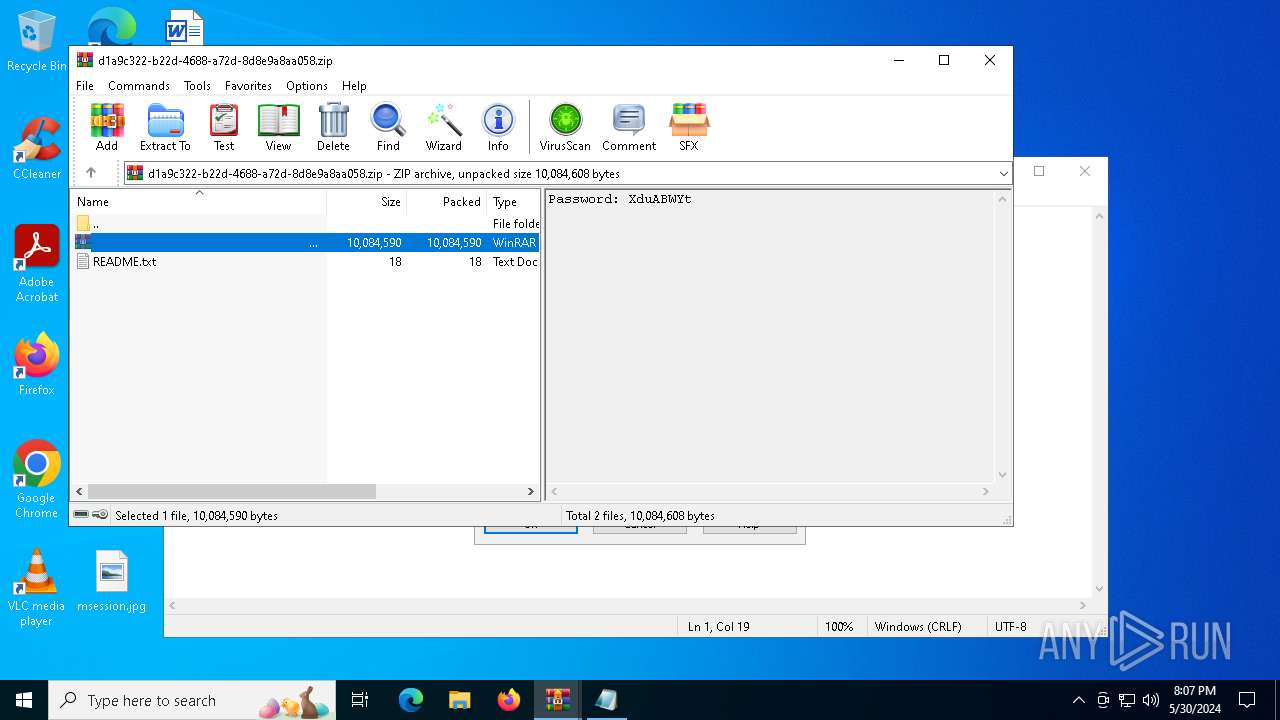
| ZipFileName: | README.txt |
Total processes
134
Monitored processes
18
Malicious processes
3
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 736 | findstr /I "wrsa.exe opssvc.exe" | C:\Windows\SysWOW64\findstr.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Find String (QGREP) Utility Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 928 | tasklist | C:\Windows\SysWOW64\tasklist.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Lists the current running tasks Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1720 | tasklist | C:\Windows\SysWOW64\tasklist.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Lists the current running tasks Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2740 | 122774\Locking.pif 122774\M | C:\Users\admin\AppData\Local\Microsoft\Windows\INetCache\122774\Locking.pif | — | cmd.exe | |||||||||||
User: admin Company: AutoIt Team Integrity Level: MEDIUM Description: AutoIt v3 Script Exit code: 0 Version: 3, 3, 14, 2 Modules
| |||||||||||||||
| 3688 | ping -n 5 127.0.0.1 | C:\Windows\SysWOW64\PING.EXE | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: TCP/IP Ping Command Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4720 | cmd /c copy /b Flooring + Textiles + Optical + Attractions + Assumption + Typical + Miracle 122774\M | C:\Windows\SysWOW64\cmd.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4916 | findstr /V "MasBathroomsCompoundInjection" Participants | C:\Windows\SysWOW64\findstr.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Find String (QGREP) Utility Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5428 | findstr /I "avastui.exe avgui.exe nswscsvc.exe sophoshealth.exe" | C:\Windows\SysWOW64\findstr.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Find String (QGREP) Utility Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5716 | cmd /c md 122774 | C:\Windows\SysWOW64\cmd.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6360 | "C:\Program Files\WinRAR\WinRAR.exe" C:\Users\admin\Desktop\d1a9c322-b22d-4688-a72d-8d8e9a8aa058.zip | C:\Program Files\WinRAR\WinRAR.exe | — | explorer.exe | |||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Version: 5.91.0 Modules
| |||||||||||||||
Total events
25 751
Read events
25 689
Write events
62
Delete events
0
Modification events
| (PID) Process: | (6360) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (6360) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (6360) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\GoogleChromeEnterpriseBundle64.zip | |||
| (PID) Process: | (6360) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Desktop\d1a9c322-b22d-4688-a72d-8d8e9a8aa058.zip | |||
| (PID) Process: | (6360) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (6360) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (6360) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (6360) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (6360) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface\Comment |
| Operation: | write | Name: | LeftBorder |
Value: 472 | |||
| (PID) Process: | (6360) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\ArcColumnWidths |
| Operation: | write | Name: | name |
Value: 256 | |||
Executable files
4
Suspicious files
41
Text files
7
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 6360 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DIa6360.44100\ㅤ ㅤ ㅤ ㅤ ㅤ ㅤ ㅤ ㅤ ㅤ ㅤ ㅤ ㅤ ㅤ ㅤ ㅤ ㅤ ㅤ ㅤ ㅤ ㅤ ㅤ .rar | — | |
MD5:— | SHA256:— | |||
| 6360 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DIa6360.44240\ㅤ ㅤ ㅤ ㅤ ㅤ ㅤ ㅤ ㅤ ㅤ ㅤ ㅤ ㅤ ㅤ ㅤ ㅤ ㅤ ㅤ ㅤ ㅤ ㅤ ㅤ .rar | — | |
MD5:— | SHA256:— | |||
| 6360 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DIa6360.44583\ㅤ ㅤ ㅤ ㅤ ㅤ ㅤ ㅤ ㅤ ㅤ ㅤ ㅤ ㅤ ㅤ ㅤ ㅤ ㅤ ㅤ ㅤ ㅤ ㅤ ㅤ .rar | — | |
MD5:— | SHA256:— | |||
| 6360 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DIa6360.44608\ㅤ ㅤ ㅤ ㅤ ㅤ ㅤ ㅤ ㅤ ㅤ ㅤ ㅤ ㅤ ㅤ ㅤ ㅤ ㅤ ㅤ ㅤ ㅤ ㅤ ㅤ .rar | — | |
MD5:— | SHA256:— | |||
| 7016 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXb7016.45040\ㅤ\S o l a r a X.exe | — | |
MD5:— | SHA256:— | |||
| 7016 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXb7016.45040\ㅤ\dll\celeryuwpver | text | |
MD5:CB5AE17636E975F9BF71DDF5BC542075 | SHA256:14BE4B45F18E0D8C67B4F719B5144EEE88497E413709D11D85B096D8E2346310 | |||
| 7016 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXb7016.45040\ㅤ\dll\autoexec\HOW_TO_USE.txt | text | |
MD5:4324149D23C0D89F490249E531460C21 | SHA256:A6F1509DDEB9B80F94E3EC9DE3821BB129979201C6833F472D25FAB16187C1EE | |||
| 7016 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXb7016.45040\ㅤ\dll\uwpoffver | text | |
MD5:CB5AE17636E975F9BF71DDF5BC542075 | SHA256:14BE4B45F18E0D8C67B4F719B5144EEE88497E413709D11D85B096D8E2346310 | |||
| 7016 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXb7016.45040\ㅤ\dll\uwpversion.txt | text | |
MD5:F0016F1D09AEA25AFCB3FB5948ACBB9F | SHA256:CC1A4126BA1A738F56187A2A2A9DF4F3D3F6BAA8DC966FEED9D0F6E09A5A486A | |||
| 7016 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXb7016.45040\ㅤ\scripts\scripts.dll | executable | |
MD5:88FD7DBF04BCF75123D02009AEA3F7F7 | SHA256:01481B9A862936FBC090BDA4033F22D7FFA5A7BFE5DC32F47C7794332B34EEC4 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
7
TCP/UDP connections
22
DNS requests
5
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
4232 | RUXIMICS.exe | GET | 200 | 2.22.242.90:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | unknown |
— | — | POST | 200 | 20.50.73.4:443 | https://self.events.data.microsoft.com/OneCollector/1.0/ | unknown | binary | 9 b | unknown |
5632 | svchost.exe | GET | 200 | 2.22.242.90:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | unknown |
5140 | MoUsoCoreWorker.exe | GET | 200 | 2.22.242.90:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | unknown |
5632 | svchost.exe | GET | 200 | 184.28.66.24:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | unknown |
4232 | RUXIMICS.exe | GET | 200 | 184.28.66.24:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | unknown |
5140 | MoUsoCoreWorker.exe | GET | 200 | 184.28.66.24:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4364 | svchost.exe | 239.255.255.250:1900 | — | — | — | unknown |
4 | System | 192.168.100.255:138 | — | — | — | unknown |
5632 | svchost.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4232 | RUXIMICS.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
5140 | MoUsoCoreWorker.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4232 | RUXIMICS.exe | 2.22.242.90:80 | crl.microsoft.com | Akamai International B.V. | DE | unknown |
5632 | svchost.exe | 2.22.242.90:80 | crl.microsoft.com | Akamai International B.V. | DE | unknown |
5140 | MoUsoCoreWorker.exe | 2.22.242.90:80 | crl.microsoft.com | Akamai International B.V. | DE | unknown |
5632 | svchost.exe | 184.28.66.24:80 | www.microsoft.com | Data Communication Business Group | TW | unknown |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
settings-win.data.microsoft.com |
| whitelisted |
HDCIZfrnmkrkibbwxQlVwAYZqH.HDCIZfrnmkrkibbwxQlVwAYZqH |
| unknown |
self.events.data.microsoft.com |
| whitelisted |