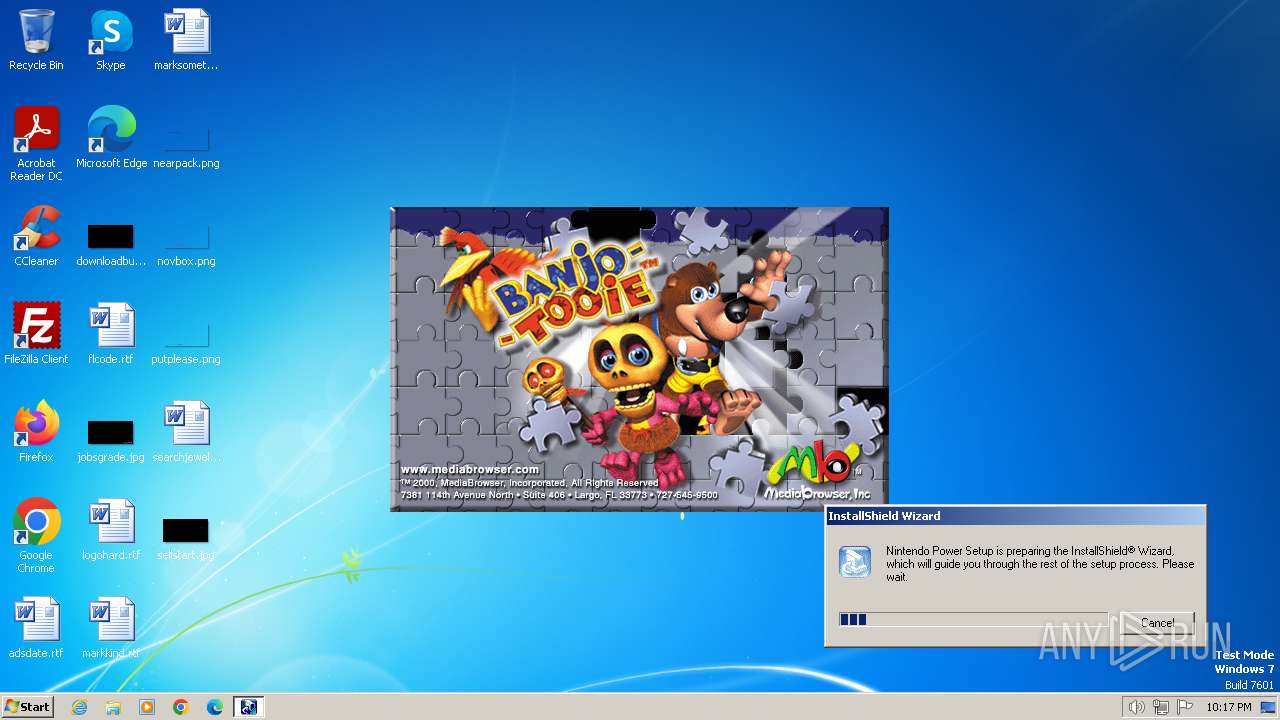
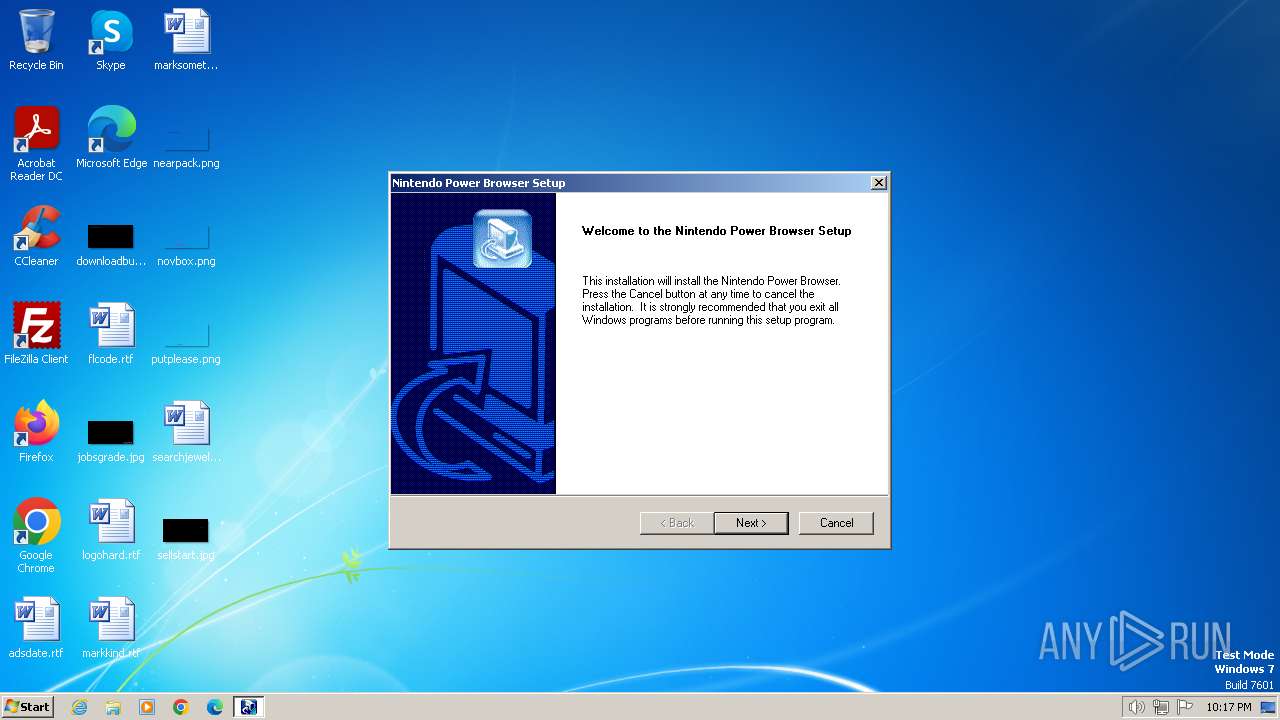
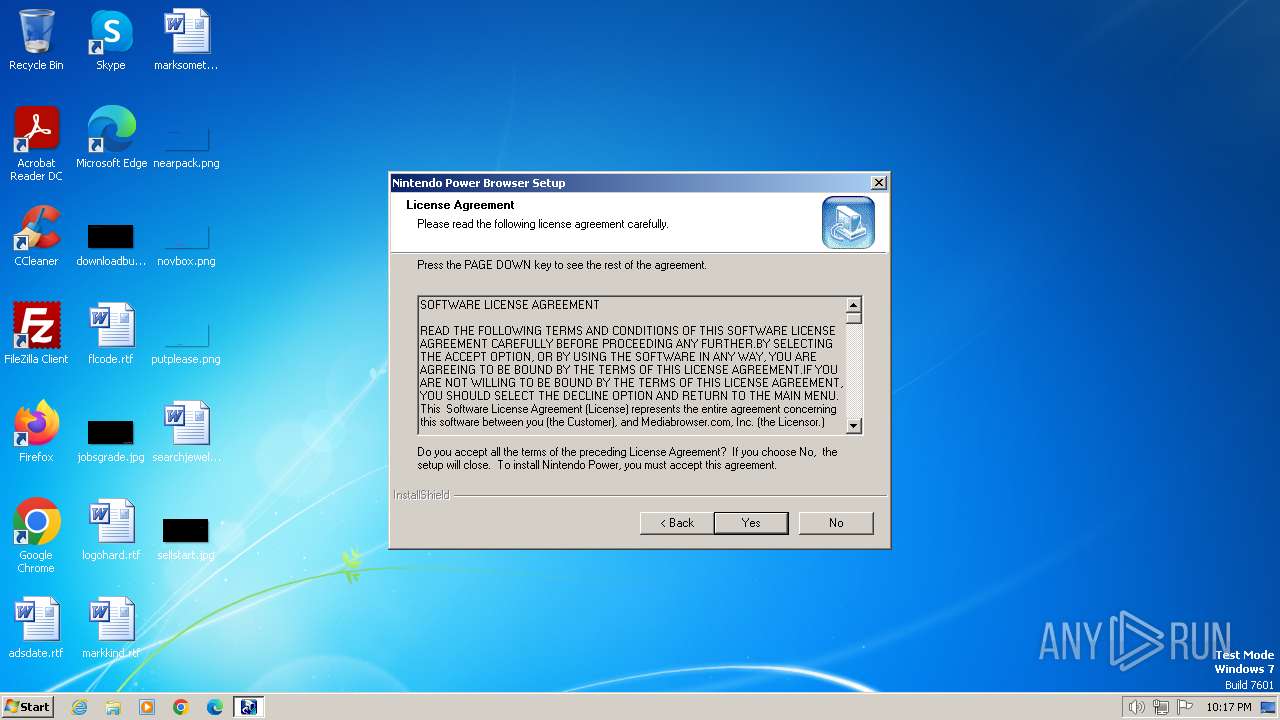
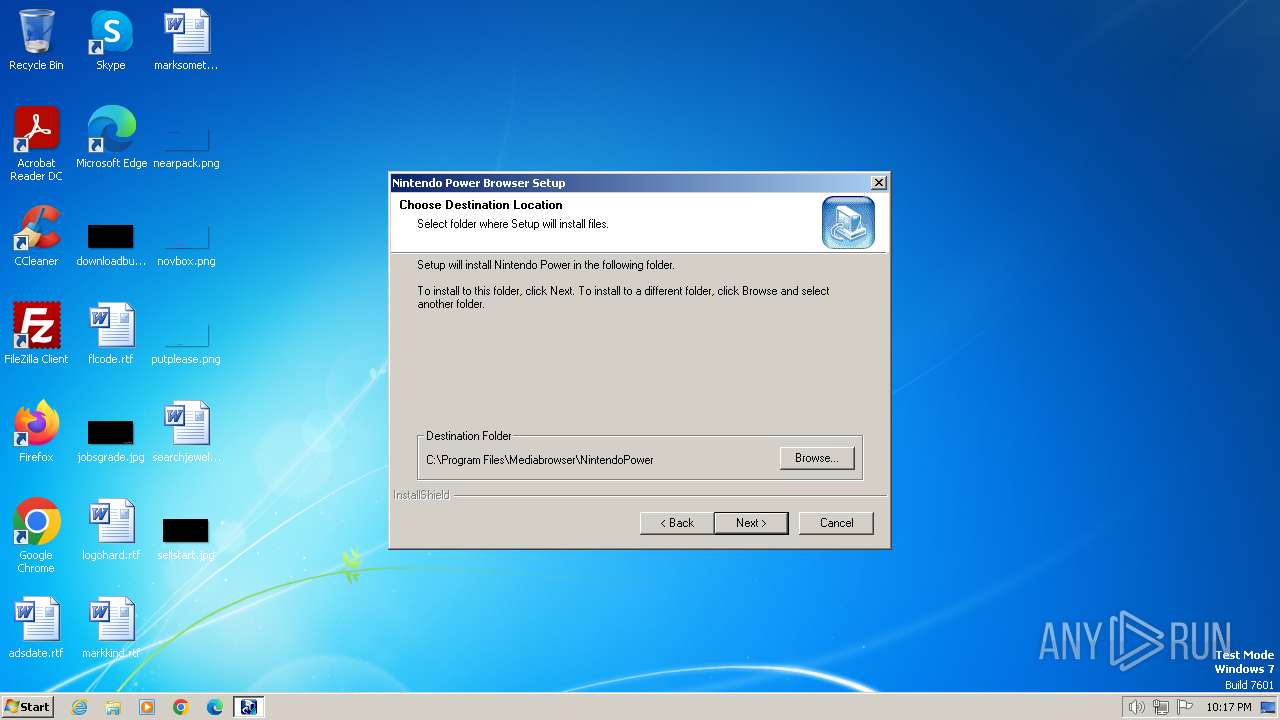
| File name: | NPS Nintendo Power.exe |
| Full analysis: | https://app.any.run/tasks/8f9e40cf-b8fe-4727-a5ca-c002cfc569ff |
| Verdict: | Malicious activity |
| Analysis date: | February 11, 2024, 22:17:33 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows, InstallShield self-extracting archive |
| MD5: | E43E5D068F1BDD6D48134476C9E5DE80 |
| SHA1: | 821FB7407CA206933019E5708879AD18E50AB7EC |
| SHA256: | 494DB8E94DF24FFA99E582ECEAED64CA215FF924EB8F08AEB1D3EF36CE6ED633 |
| SSDEEP: | 98304:2NOzpIpxBxahtmX6zjvCsyyPPzV7BtU4uULNzwi6Z+Ucz1PWcYG+gra2Mls5yQ/W:VJzqpgM |
MALICIOUS
Drops the executable file immediately after the start
- NPS Nintendo Power.exe (PID: 2852)
- Setup.exe (PID: 2840)
- IKernel.exe (PID: 3460)
SUSPICIOUS
Executable content was dropped or overwritten
- Setup.exe (PID: 2840)
- NPS Nintendo Power.exe (PID: 2852)
- IKernel.exe (PID: 3460)
Creates/Modifies COM task schedule object
- IKernel.exe (PID: 3460)
Application launched itself
- IKernel.exe (PID: 3460)
INFO
Create files in a temporary directory
- NPS Nintendo Power.exe (PID: 2852)
- IKernel.exe (PID: 3460)
- Setup.exe (PID: 2840)
Creates files in the program directory
- Setup.exe (PID: 2840)
- IKernel.exe (PID: 3460)
Reads the computer name
- Setup.exe (PID: 2840)
- IKernel.exe (PID: 3944)
- IKernel.exe (PID: 3460)
- IKernel.exe (PID: 864)
Checks supported languages
- NPS Nintendo Power.exe (PID: 2852)
- IKernel.exe (PID: 3944)
- IKernel.exe (PID: 3460)
- IKernel.exe (PID: 864)
- Setup.exe (PID: 2840)
Reads the machine GUID from the registry
- Setup.exe (PID: 2840)
- IKernel.exe (PID: 3460)
Reads Environment values
- IKernel.exe (PID: 3460)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win32 Executable MS Visual C++ (generic) (42.2) |
|---|---|---|
| .exe | | | Win64 Executable (generic) (37.3) |
| .dll | | | Win32 Dynamic Link Library (generic) (8.8) |
| .exe | | | Win32 Executable (generic) (6) |
| .exe | | | Generic Win/DOS Executable (2.7) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2000:06:16 18:00:04+00:00 |
| ImageFileCharacteristics: | No relocs, Executable, No line numbers, No symbols, 32-bit |
| PEType: | PE32 |
| LinkerVersion: | 6 |
| CodeSize: | 69632 |
| InitializedDataSize: | 98304 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x84a7 |
| OSVersion: | 4 |
| ImageVersion: | - |
| SubsystemVersion: | 4 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 2.11.15.0 |
| ProductVersionNumber: | 2.11.15.0 |
| FileFlagsMask: | 0x003f |
| FileFlags: | (none) |
| FileOS: | Windows 32-bit |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | English (U.S.) |
| CharacterSet: | Unicode |
| Comments: | - |
| CompanyName: | Mediabrowser |
| FileDescription: | - |
| FileVersion: | 3.3.0.0 |
| InternalName: | stub32i.exe |
| LegalCopyright: | 2000 |
| OriginalFileName: | stub32i.exe |
| ProductName: | Nintendo Power |
| ProductVersion: | 3.3.0.0 |
Total processes
44
Monitored processes
6
Malicious processes
2
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 864 | "C:\Program Files\Common Files\InstallShield\engine\6\Intel 32\iKernel.exe" /REGSERVER | C:\Program Files\Common Files\InstallShield\Engine\6\Intel 32\IKernel.exe | — | IKernel.exe | |||||||||||
User: admin Company: InstallShield Software Corporation Integrity Level: HIGH Description: InstallShield® Engine Exit code: 0 Version: 6, 22, 100, 1511 Modules
| |||||||||||||||
| 2840 | "C:\Users\admin\AppData\Local\Temp\pftF270~tmp\Disk1\Setup.exe" | C:\Users\admin\AppData\Local\Temp\pftF270~tmp\Disk1\Setup.exe | NPS Nintendo Power.exe | ||||||||||||
User: admin Company: InstallShield Software Corporation Integrity Level: HIGH Description: InstallShield (R) Setup Launcher Exit code: 0 Version: 6, 22, 100, 1441 Modules
| |||||||||||||||
| 2852 | "C:\Users\admin\AppData\Local\Temp\NPS Nintendo Power.exe" | C:\Users\admin\AppData\Local\Temp\NPS Nintendo Power.exe | explorer.exe | ||||||||||||
User: admin Company: Mediabrowser Integrity Level: HIGH Exit code: 0 Version: 3.3.0.0 Modules
| |||||||||||||||
| 3460 | C:\PROGRA~1\COMMON~1\INSTAL~1\Engine\6\INTEL3~1\IKernel.exe -Embedding | C:\Program Files\Common Files\InstallShield\Engine\6\Intel 32\IKernel.exe | svchost.exe | ||||||||||||
User: admin Company: InstallShield Software Corporation Integrity Level: HIGH Description: InstallShield® Engine Exit code: 0 Version: 6, 22, 100, 1511 Modules
| |||||||||||||||
| 3700 | "C:\Users\admin\AppData\Local\Temp\NPS Nintendo Power.exe" | C:\Users\admin\AppData\Local\Temp\NPS Nintendo Power.exe | — | explorer.exe | |||||||||||
User: admin Company: Mediabrowser Integrity Level: MEDIUM Exit code: 3221226540 Version: 3.3.0.0 Modules
| |||||||||||||||
| 3944 | "C:\Program Files\Common Files\InstallShield\Engine\6\Intel 32\IKernel.exe" -RegServer | C:\Program Files\Common Files\InstallShield\Engine\6\Intel 32\IKernel.exe | — | Setup.exe | |||||||||||
User: admin Company: InstallShield Software Corporation Integrity Level: HIGH Description: InstallShield® Engine Exit code: 0 Version: 6, 22, 100, 1511 Modules
| |||||||||||||||
Total events
1 050
Read events
967
Write events
83
Delete events
0
Modification events
| (PID) Process: | (3944) IKernel.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Classes\Interface\{AA7E2068-CB55-11D2-8094-00104B1F9838}\TypeLib |
| Operation: | write | Name: | Version |
Value: 1.0 | |||
| (PID) Process: | (3944) IKernel.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Classes\Interface\{AA7E2066-CB55-11D2-8094-00104B1F9838}\TypeLib |
| Operation: | write | Name: | Version |
Value: 1.0 | |||
| (PID) Process: | (3944) IKernel.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Classes\Interface\{CC096170-E2CB-11D2-80C8-00104B1F6CEA}\TypeLib |
| Operation: | write | Name: | Version |
Value: 1.0 | |||
| (PID) Process: | (3944) IKernel.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Classes\Interface\{8C3C1B11-E59D-11D2-B40B-00A024B9DDDD}\TypeLib |
| Operation: | write | Name: | Version |
Value: 1.0 | |||
| (PID) Process: | (3944) IKernel.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Classes\Interface\{8C3C1B13-E59D-11D2-B40B-00A024B9DDDD}\TypeLib |
| Operation: | write | Name: | Version |
Value: 1.0 | |||
| (PID) Process: | (3944) IKernel.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Classes\Interface\{8C3C1B12-E59D-11D2-B40B-00A024B9DDDD}\TypeLib |
| Operation: | write | Name: | Version |
Value: 1.0 | |||
| (PID) Process: | (3944) IKernel.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Classes\Interface\{8C3C1B10-E59D-11D2-B40B-00A024B9DDDD}\TypeLib |
| Operation: | write | Name: | Version |
Value: 1.0 | |||
| (PID) Process: | (3944) IKernel.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Classes\Interface\{8C3C1B16-E59D-11D2-B40B-00A024B9DDDD}\TypeLib |
| Operation: | write | Name: | Version |
Value: 1.0 | |||
| (PID) Process: | (3944) IKernel.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Classes\Interface\{8C3C1B15-E59D-11D2-B40B-00A024B9DDDD}\TypeLib |
| Operation: | write | Name: | Version |
Value: 1.0 | |||
| (PID) Process: | (3944) IKernel.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Classes\Interface\{2583251F-0A04-11D3-886B-00C04F72F303}\TypeLib |
| Operation: | write | Name: | Version |
Value: 1.0 | |||
Executable files
17
Suspicious files
10
Text files
8
Unknown types
2
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2852 | NPS Nintendo Power.exe | C:\Users\admin\AppData\Local\Temp\pftF270~tmp\Disk1\ikernel.ex_ | ex_ | |
MD5:E51E89D1D1967EB9BFD39D85638A8209 | SHA256:9FB0AC49D19B44B438AD7F4E3316D8C190981B7B3329BB01CF0010E295F26D81 | |||
| 2852 | NPS Nintendo Power.exe | C:\Users\admin\AppData\Local\Temp\pftF270~tmp\Disk1\setup.bmp | image | |
MD5:4249A1639F4A23DD69BAC7E4D4A0B3C6 | SHA256:14C34285B7AB18B442D49B42E6838F1F36A12A49A335EA253E996BAD2CFE2692 | |||
| 2852 | NPS Nintendo Power.exe | C:\Users\admin\AppData\Local\Temp\pftF270~tmp\Disk1\data1.hdr | hdr | |
MD5:0CB2AAC77C977B574506A5F67C5D1572 | SHA256:B890DA8819BB884FBC93C11F742859DCA0DA2531BD5B804140EFB9883790091B | |||
| 2852 | NPS Nintendo Power.exe | C:\Users\admin\AppData\Local\Temp\pftF270~tmp\pftw1.pkg | compressed | |
MD5:BD3A829CD004CBE00CE5AD7E64DB4C85 | SHA256:9CB29735D3A61251735C8705B549DB028053FB7EEBF185366648F90CCE3C4A1D | |||
| 2852 | NPS Nintendo Power.exe | C:\Users\admin\AppData\Local\Temp\pftF270~tmp\Disk1\setup.inx | inx | |
MD5:8FC15E5B4EB8649565E8CCF0B7566FAC | SHA256:FDCDB72B4FB637FA8DBFC83C1DC18ED8BF2BB15ACC60DF8AA0A1F83C348FF77A | |||
| 2852 | NPS Nintendo Power.exe | C:\Users\admin\AppData\Local\Temp\extF250.tmp | ini | |
MD5:19A2283172165182D05BBD5745372F62 | SHA256:379ADDFC2E4A0309EC0526507D564FC79EEB6635963C0E84F10CB8B103036C54 | |||
| 2852 | NPS Nintendo Power.exe | C:\Users\admin\AppData\Local\Temp\pftF270~tmp\Disk1\Setup.exe | executable | |
MD5:56FC94234252B533BBF91412E671F172 | SHA256:C8C7A1A9AD9ABB16299DD6FDF1B53BDCF91427DF6ADFA738E0AB90A53CE51ABC | |||
| 2852 | NPS Nintendo Power.exe | C:\Users\admin\AppData\Local\Temp\pftF270~tmp\Disk1\layout.bin | binary | |
MD5:DCAE721E75054DCE35B9FE6F96D54A4D | SHA256:BBE16F284BD305988F9744FEB1B0071C3EDFBF805637E1438CD9032008BC567E | |||
| 2840 | Setup.exe | C:\Program Files\Common Files\InstallShield\Engine\6\Intel 32\IKernel.exe | executable | |
MD5:D46FBCAE81EA095814E518CD6EBDD681 | SHA256:8FC3E417A63D236FABF34F8FD03BB6599520D9386A43094DD48E9C091E729EB7 | |||
| 3460 | IKernel.exe | C:\Program Files\Common Files\InstallShield\engine\6\Intel 32\objef6b4.rra | executable | |
MD5:9D396EA94CFC6ACB3F036B9C89467A71 | SHA256:1BBF964F27C554EB3830A13BC6226E5FC791C55A953AD10A2B6084047BDE8BF7 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
4
DNS requests
0
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
1080 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |
DNS requests
Threats
Process | Message |
|---|---|
IKernel.exe | IUnknown |
IKernel.exe | |
IKernel.exe | CMainWindow |
IKernel.exe | - |
IKernel.exe | IUnknown |
IKernel.exe | |
IKernel.exe | CMainWindow |
IKernel.exe | - |
IKernel.exe | ISetupMainWindow |
IKernel.exe | |