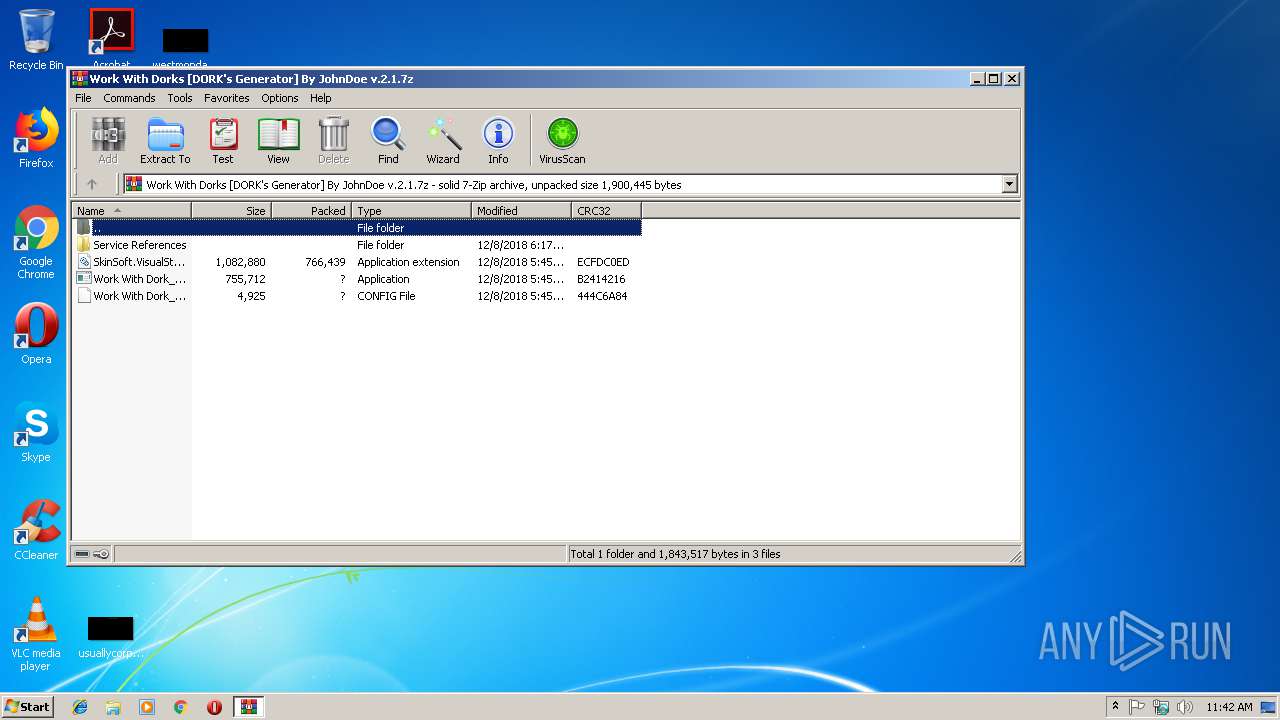
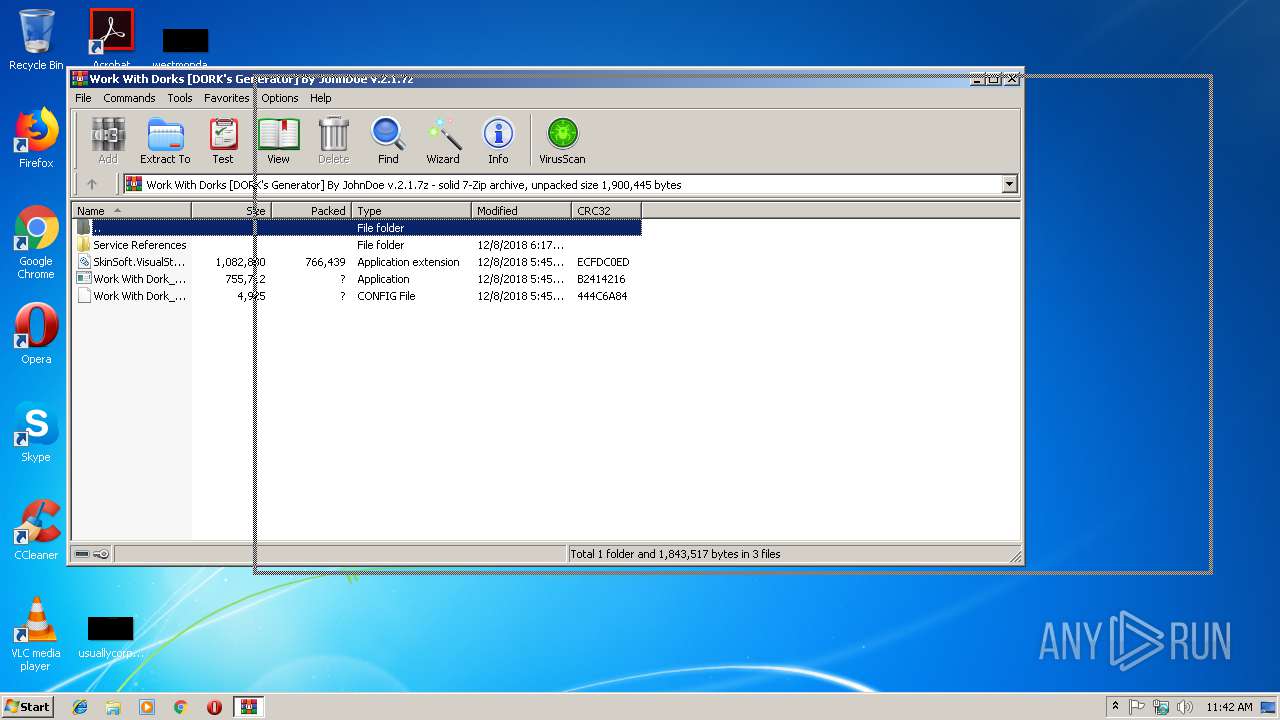
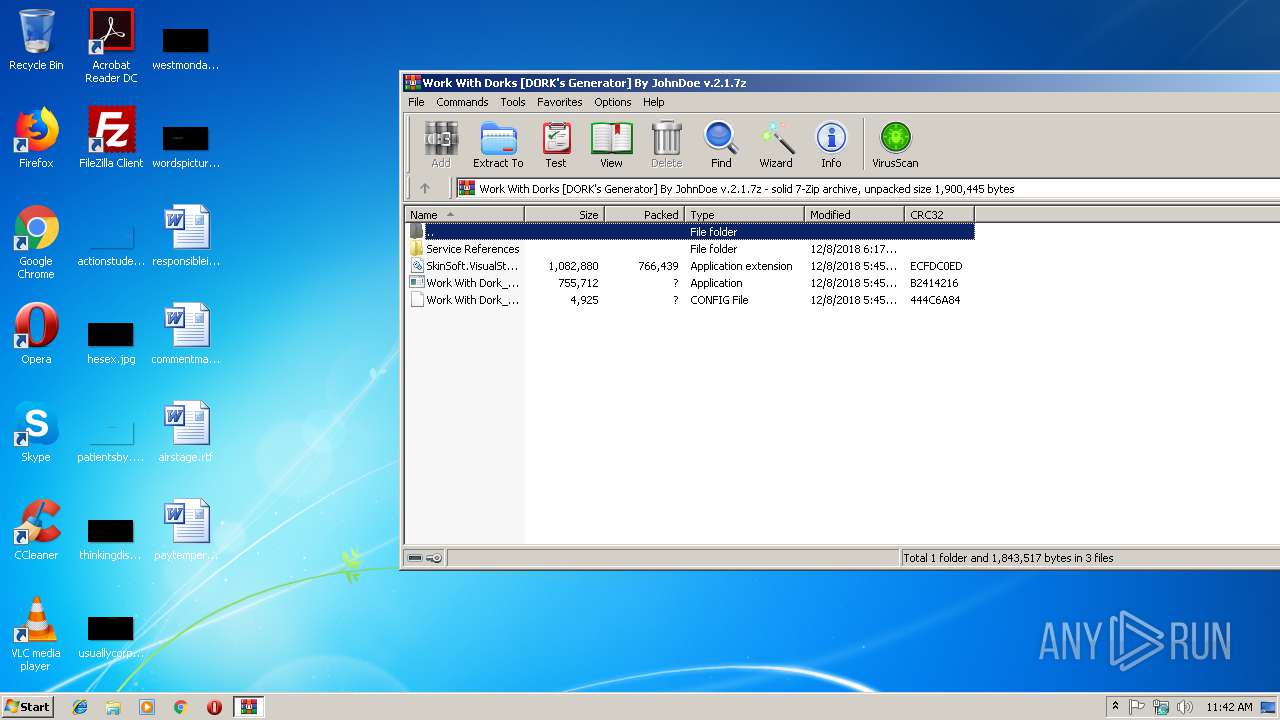
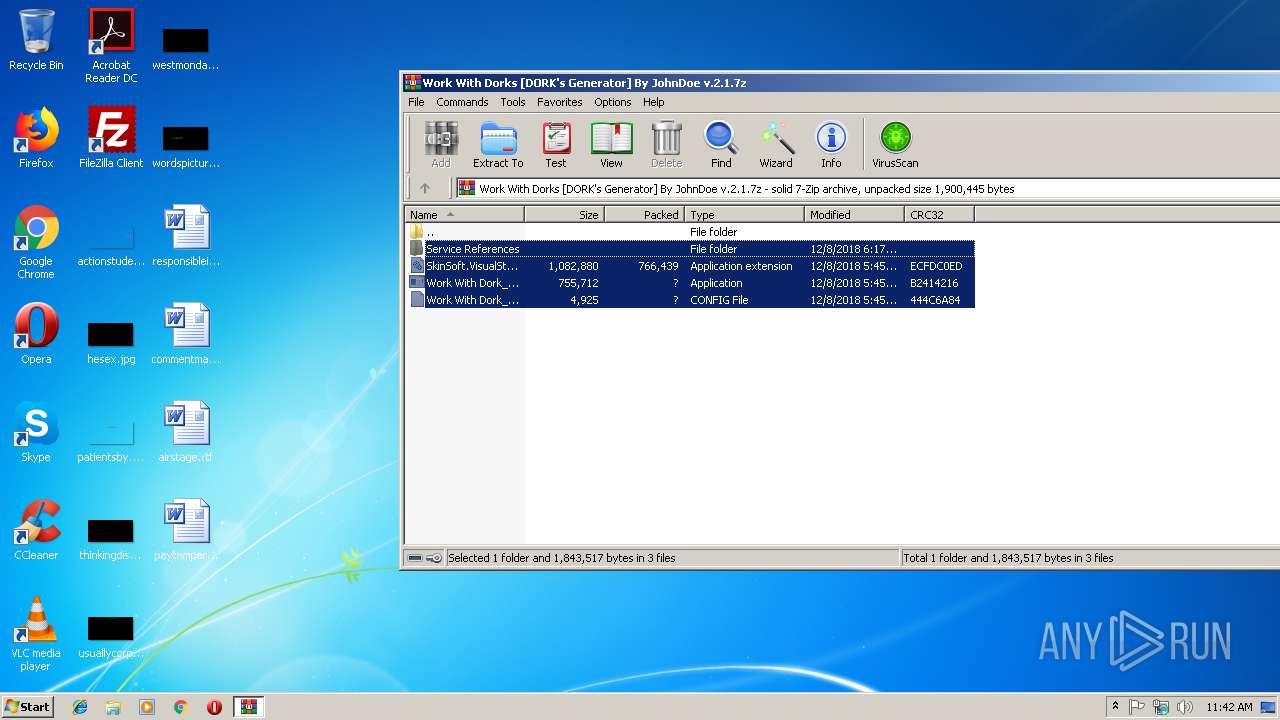
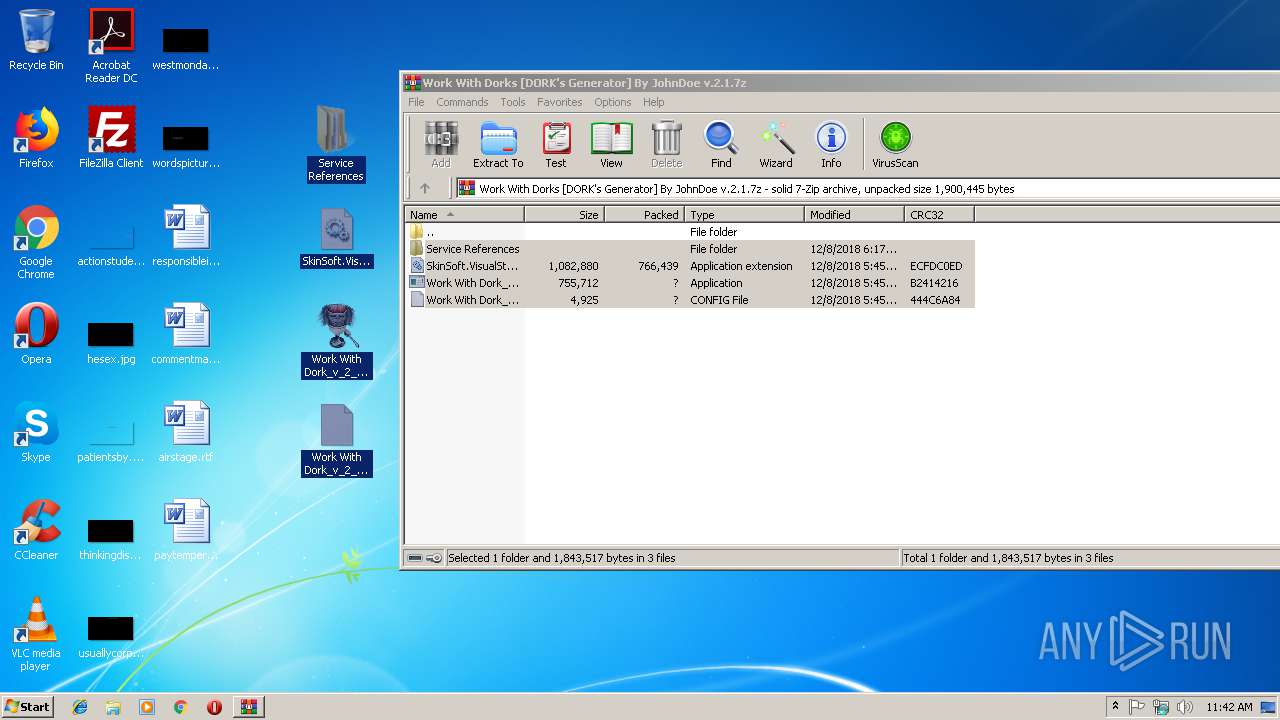
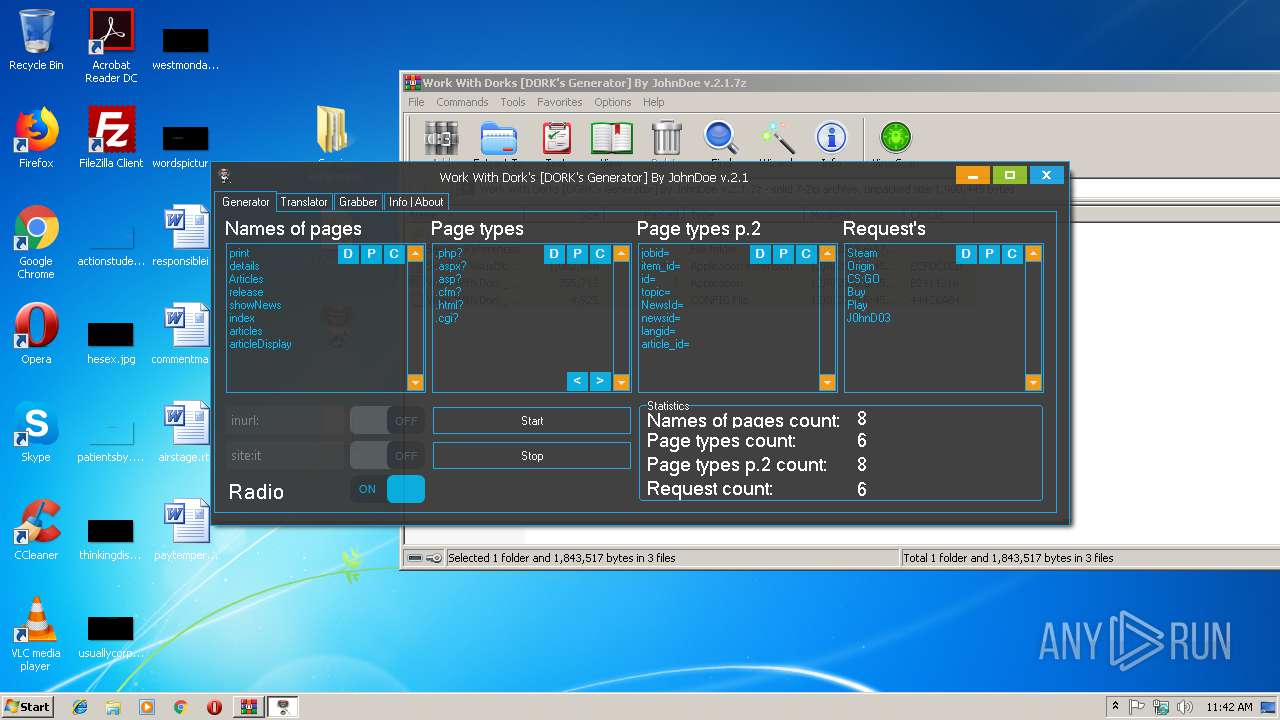
| File name: | Work With Dorks [DORK's Generator] By JohnDoe v.2.1.7z |
| Full analysis: | https://app.any.run/tasks/b3a44ad1-11e6-472c-9187-6b7eca47bd5c |
| Verdict: | Malicious activity |
| Analysis date: | December 15, 2018, 11:41:29 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/x-7z-compressed |
| File info: | 7-zip archive data, version 0.4 |
| MD5: | AEA2810BF7C63D9434BCDC162E54210F |
| SHA1: | 99F33A0E2DF3A8EBD18ECD3A8E6C1C9A533E2D1A |
| SHA256: | 494C4460B6B5FC4C211CB3AEF45D18D1B21F83AB3E10A596F90A7F368FF83B6C |
| SSDEEP: | 12288:0UwzXMFnHKFDglnAOC7K1kWJLJxideavA6JEH5mR4gx4kYLjPPMz49:0bKHKFDglnAOC7k/FCbK5T44kO7PMz49 |
MALICIOUS
Application was dropped or rewritten from another process
- Work With Dork_v_2_1.exe (PID: 2264)
Loads dropped or rewritten executable
- Work With Dork_v_2_1.exe (PID: 2264)
- SearchProtocolHost.exe (PID: 1684)
SUSPICIOUS
Executable content was dropped or overwritten
- WinRAR.exe (PID: 2952)
- Work With Dork_v_2_1.exe (PID: 2264)
Reads Internet Cache Settings
- Work With Dork_v_2_1.exe (PID: 2264)
INFO
No info indicators.
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .7z | | | 7-Zip compressed archive (v0.4) (57.1) |
|---|---|---|
| .7z | | | 7-Zip compressed archive (gen) (42.8) |
Total processes
34
Monitored processes
3
Malicious processes
2
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1684 | "C:\Windows\system32\SearchProtocolHost.exe" Global\UsGthrFltPipeMssGthrPipe6_ Global\UsGthrCtrlFltPipeMssGthrPipe6 1 -2147483646 "Software\Microsoft\Windows Search" "Mozilla/4.0 (compatible; MSIE 6.0; Windows NT; MS Search 4.0 Robot)" "C:\ProgramData\Microsoft\Search\Data\Temp\usgthrsvc" "DownLevelDaemon" | C:\Windows\System32\SearchProtocolHost.exe | — | SearchIndexer.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Microsoft Windows Search Protocol Host Exit code: 0 Version: 7.00.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2264 | "C:\Users\admin\Desktop\Work With Dork_v_2_1.exe" | C:\Users\admin\Desktop\Work With Dork_v_2_1.exe | explorer.exe | ||||||||||||
User: admin Company: J0hnD03 SoftWare Integrity Level: MEDIUM Description: Work With Dork_v_2_1 Exit code: 0 Version: 2.1.0.0 Modules
| |||||||||||||||
| 2952 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\AppData\Local\Temp\Work With Dorks [DORK's Generator] By JohnDoe v.2.1.7z" | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.60.0 Modules
| |||||||||||||||
Total events
820
Read events
805
Write events
14
Delete events
1
Modification events
| (PID) Process: | (2952) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (2952) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (2952) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\5F\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (2952) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\Work With Dorks [DORK's Generator] By JohnDoe v.2.1.7z | |||
| (PID) Process: | (2952) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (2952) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (2952) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (2952) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (2264) Work With Dork_v_2_1.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 0 | |||
| (PID) Process: | (2264) Work With Dork_v_2_1.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 1 | |||
Executable files
3
Suspicious files
0
Text files
12
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2952 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa2952.13073\Service References\TranslatorService\configuration.svcinfo | xml | |
MD5:D935CB832F65D86D7C2A57D1794F5953 | SHA256:42C0CA38FE255D41F4C1E5585C547D62C87FBE2E03BDDC17D16D42898819A32D | |||
| 2952 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa2952.13073\Service References\TranslatorService\soap.wsdl | xml | |
MD5:34E29BF87AB995613009041EE8EFBCCE | SHA256:E8FE1EDDB15B316C35A9D498C91081823212452226A42278B7A086CB2FC416CC | |||
| 2952 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa2952.13073\Work With Dork_v_2_1.exe.config | xml | |
MD5:9D185D4AA4E600A2CC281E7C26C6D2C4 | SHA256:9914D7BC13F12F7F745A9D2171DC671728B1F4CD87E175DA65B718CB087B59C0 | |||
| 2952 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa2952.13073\Service References\TranslatorService\SoapService1.wsdl | xml | |
MD5:E5EF3231B2DEF3FB6B82B54C186E3463 | SHA256:1273852CF9B1560DE77A97403E7DEABE49454425EB7C8E0740586B3E1E71FE90 | |||
| 2952 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa2952.13073\Service References\TranslatorService\Reference.svcmap | xml | |
MD5:09A372941AE01A4362EBA372D3C364B6 | SHA256:B94123D35DDB03C9D71D6BA4D58477280F457D4D139C3BC41A4CFEAA95BD9F4A | |||
| 2952 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa2952.13073\Service References\TranslatorService\soap2.xsd | xml | |
MD5:386E42D097C9828BBF74E907A04472C8 | SHA256:DCED826BCB9B7BCC3F435A23F7E8BE179F8A70C781B53ACBF3E4605AEDBF699A | |||
| 2952 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa2952.13073\Service References\TranslatorService\Reference.vb | text | |
MD5:3C79EE6CFDE291C2E03392CC15667D08 | SHA256:F2887D045B2FB51F8453118924B848CCB19E4A670DF526823BC923E50769BE3F | |||
| 2952 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa2952.13073\Service References\TranslatorService\soap.xsd | xml | |
MD5:A2213C9B642FE40C303DBECD10625284 | SHA256:95B5F1FA631A18CE2599D49E6DA7E0AC9B698370DDA6EFB8F101DB9542622E7B | |||
| 2952 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa2952.13073\Service References\TranslatorService\SoapService.wsdl | xml | |
MD5:E5EF3231B2DEF3FB6B82B54C186E3463 | SHA256:1273852CF9B1560DE77A97403E7DEABE49454425EB7C8E0740586B3E1E71FE90 | |||
| 2952 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa2952.13073\Service References\TranslatorService\configuration91.svcinfo | xml | |
MD5:3088E630D8B836EE5BACD9C867BC0AA3 | SHA256:297ECA8F517040AAD7FDA7CDBE12C3B7A0FD124CAC376C724871A2E2EA9CBAC5 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
0
DNS requests
0
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report