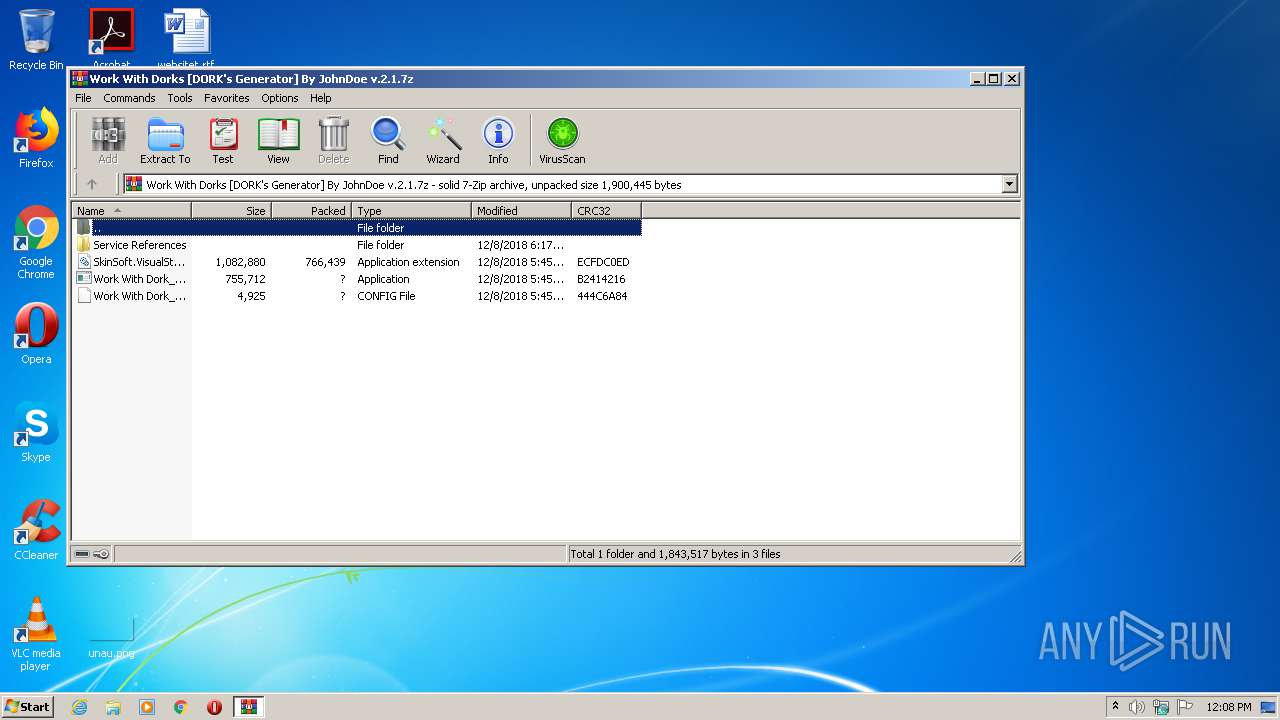
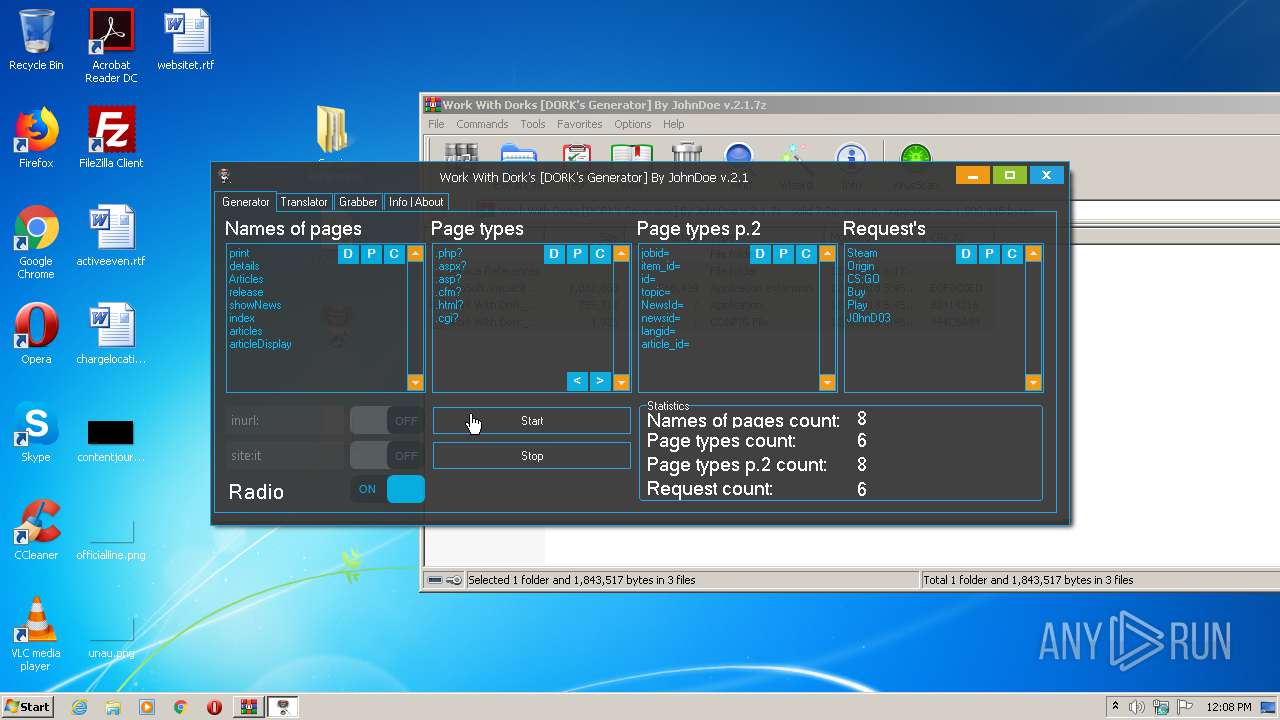
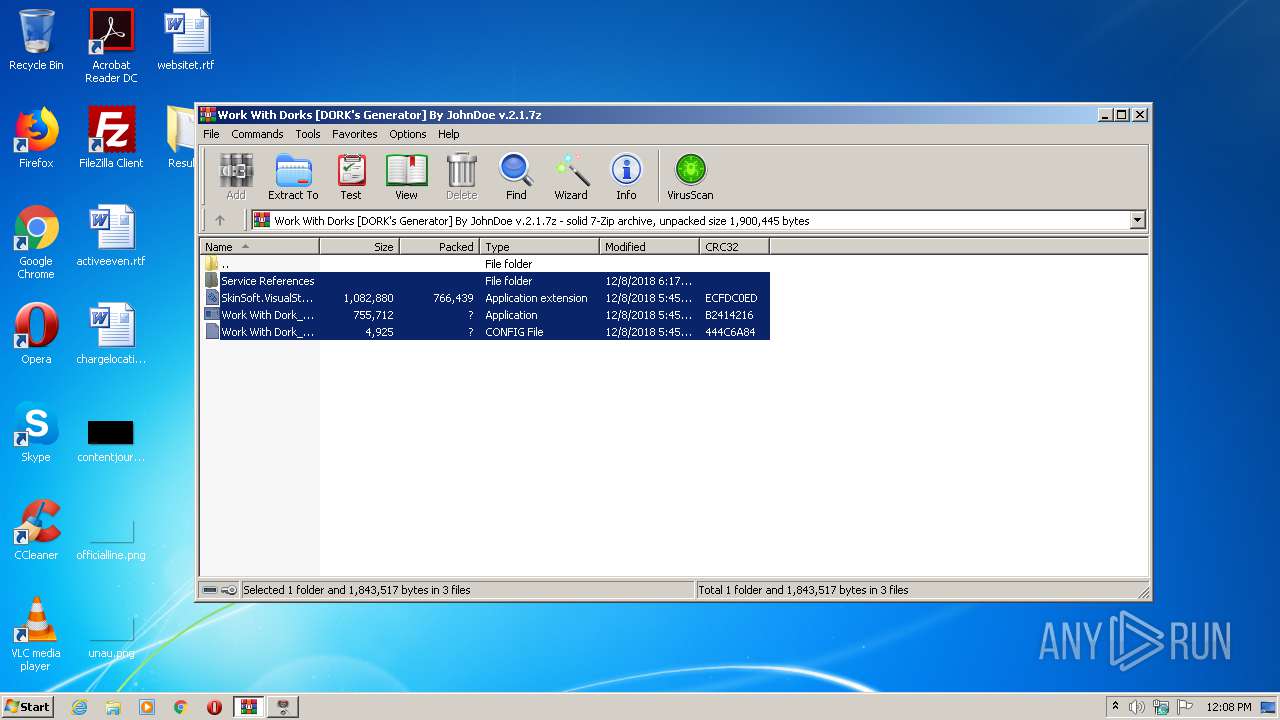
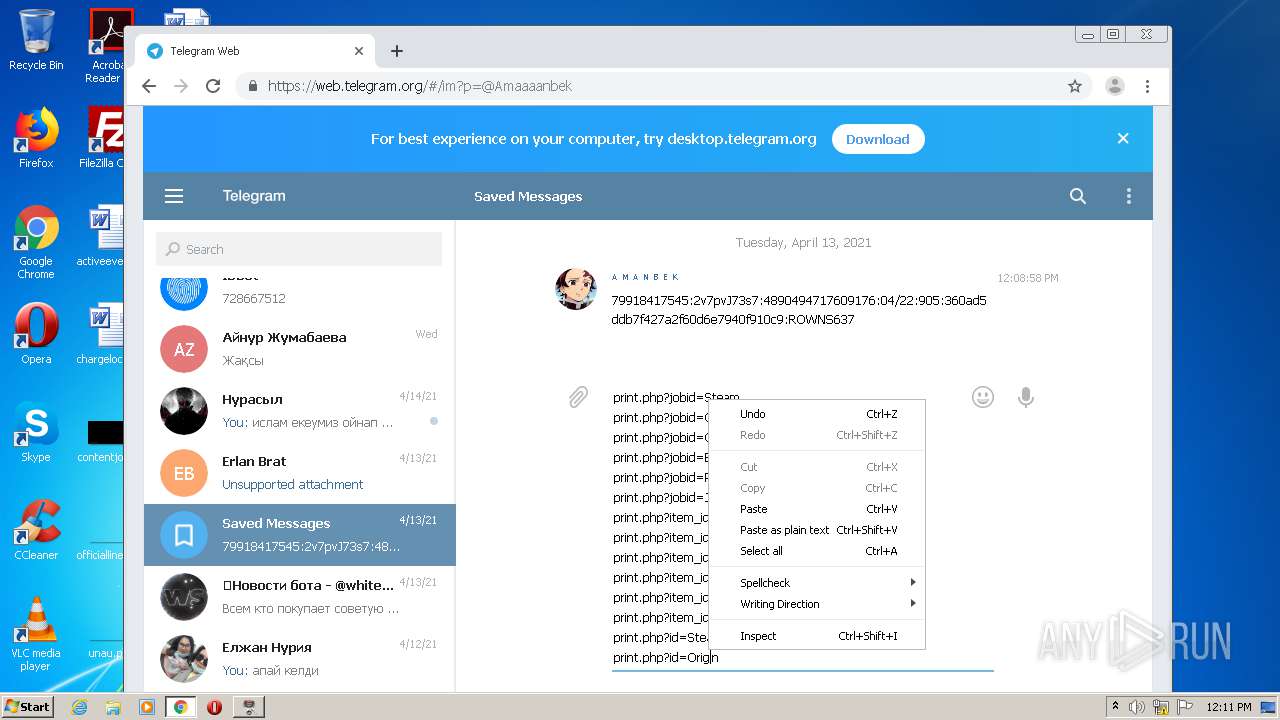
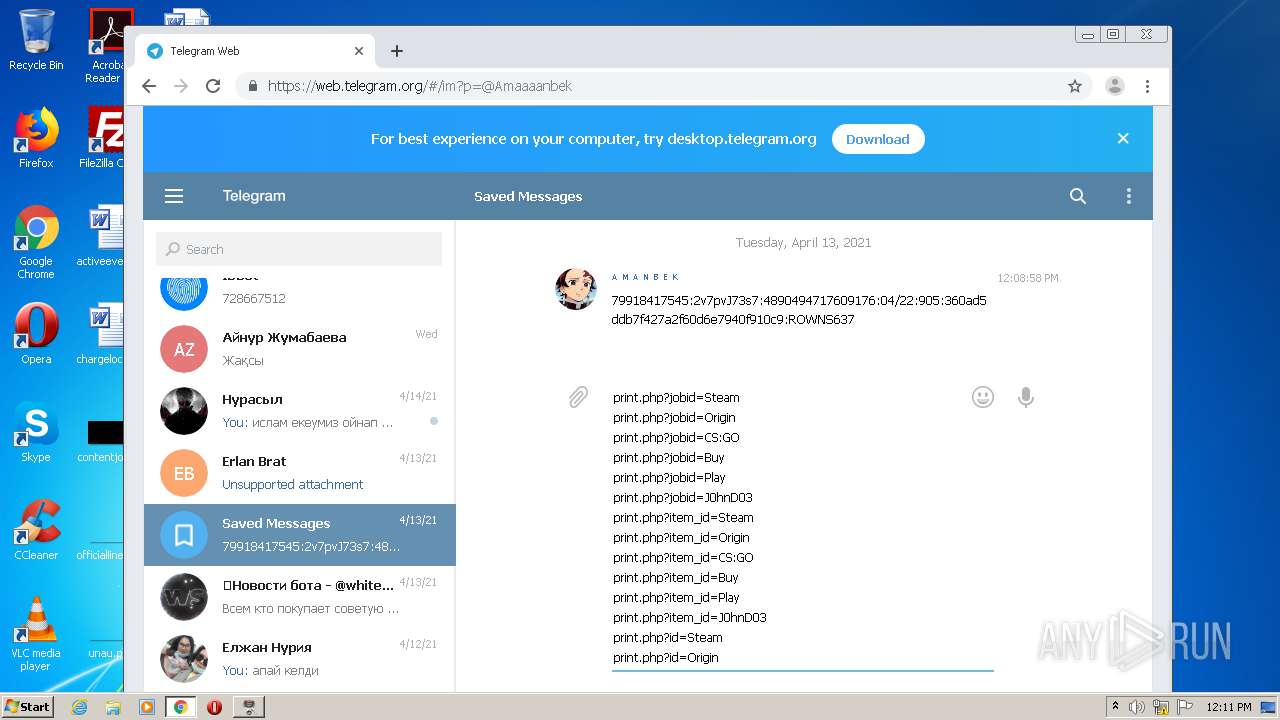
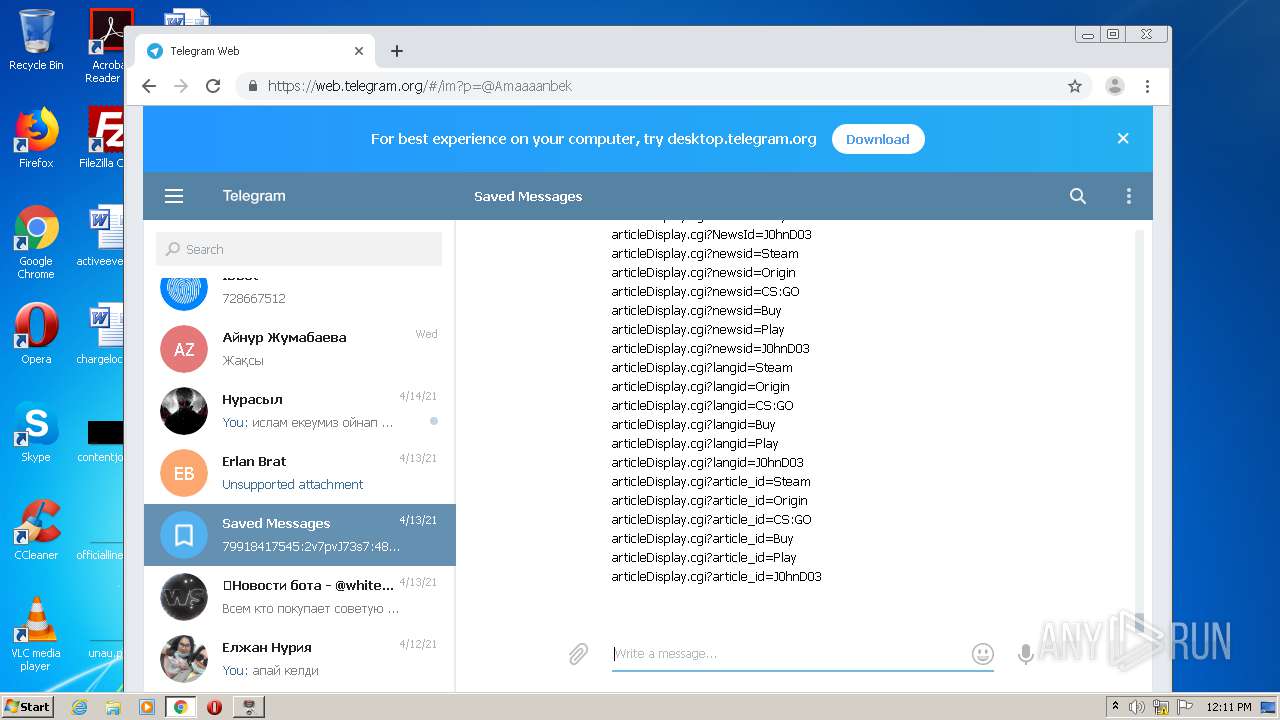
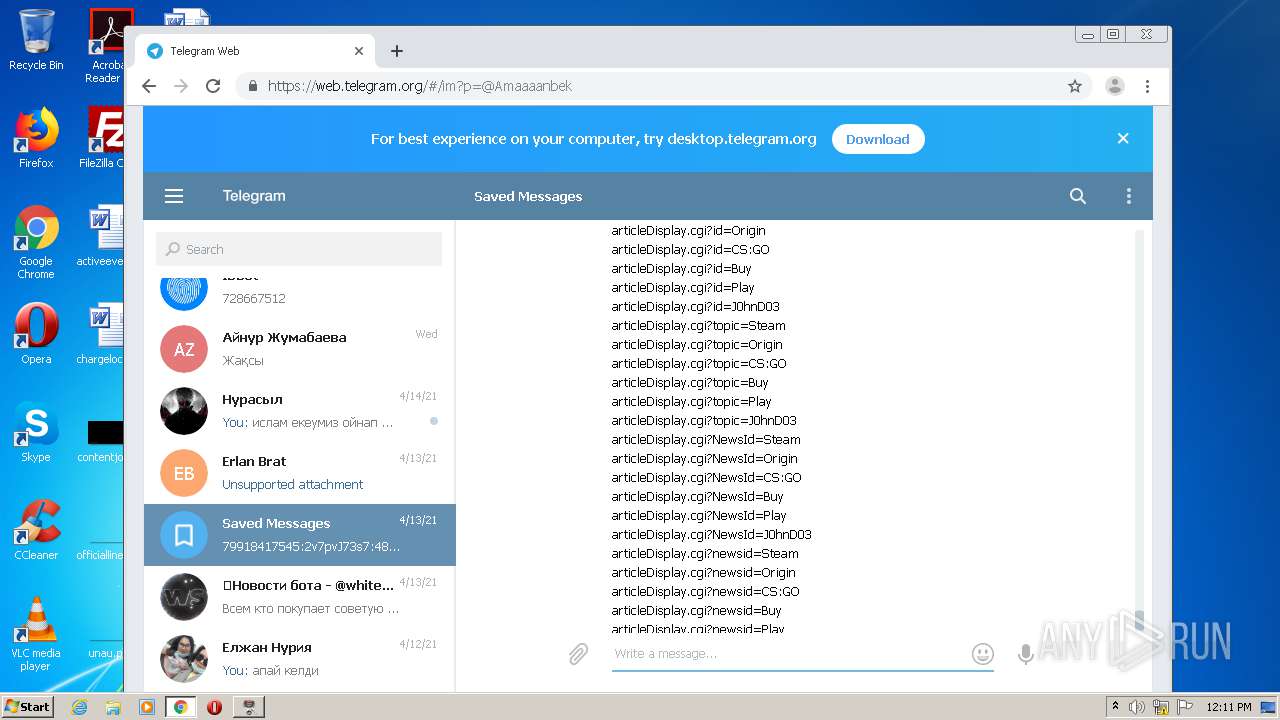
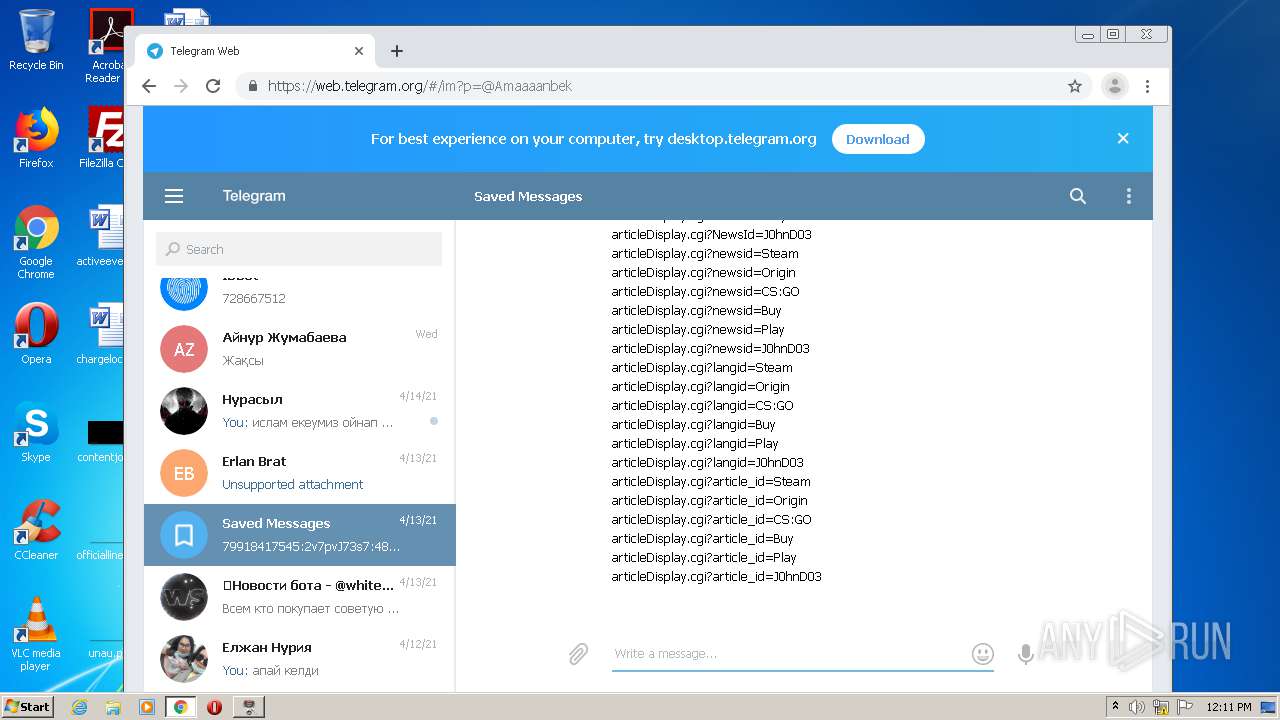
| File name: | Work With Dorks [DORK's Generator] By JohnDoe v.2.1.7z |
| Full analysis: | https://app.any.run/tasks/942cd527-9e09-4fd7-ac46-fb64fb826f10 |
| Verdict: | Malicious activity |
| Analysis date: | April 20, 2021, 11:07:56 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/x-7z-compressed |
| File info: | 7-zip archive data, version 0.4 |
| MD5: | AEA2810BF7C63D9434BCDC162E54210F |
| SHA1: | 99F33A0E2DF3A8EBD18ECD3A8E6C1C9A533E2D1A |
| SHA256: | 494C4460B6B5FC4C211CB3AEF45D18D1B21F83AB3E10A596F90A7F368FF83B6C |
| SSDEEP: | 12288:0UwzXMFnHKFDglnAOC7K1kWJLJxideavA6JEH5mR4gx4kYLjPPMz49:0bKHKFDglnAOC7k/FCbK5T44kO7PMz49 |
MALICIOUS
Application was dropped or rewritten from another process
- Work With Dork_v_2_1.exe (PID: 3252)
SUSPICIOUS
Executable content was dropped or overwritten
- WinRAR.exe (PID: 2540)
- Work With Dork_v_2_1.exe (PID: 3252)
Drops a file that was compiled in debug mode
- WinRAR.exe (PID: 2540)
Modifies files in Chrome extension folder
- chrome.exe (PID: 3520)
INFO
Manual execution by user
- Work With Dork_v_2_1.exe (PID: 3252)
- NOTEPAD.EXE (PID: 1536)
- chrome.exe (PID: 3520)
Reads the hosts file
- chrome.exe (PID: 3520)
- chrome.exe (PID: 1860)
Application launched itself
- chrome.exe (PID: 3520)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .7z | | | 7-Zip compressed archive (v0.4) (57.1) |
|---|---|---|
| .7z | | | 7-Zip compressed archive (gen) (42.8) |
Total processes
81
Monitored processes
40
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 252 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=crashpad-handler "--user-data-dir=C:\Users\admin\AppData\Local\Google\Chrome\User Data" /prefetch:7 --monitor-self-annotation=ptype=crashpad-handler "--database=C:\Users\admin\AppData\Local\Google\Chrome\User Data\Crashpad" "--metrics-dir=C:\Users\admin\AppData\Local\Google\Chrome\User Data" --url=https://clients2.google.com/cr/report --annotation=channel= --annotation=plat=Win32 --annotation=prod=Chrome --annotation=ver=75.0.3770.100 --initial-client-data=0x7c,0x80,0x84,0x78,0x88,0x6ea7a9d0,0x6ea7a9e0,0x6ea7a9ec | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 552 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --field-trial-handle=1044,14333885174459687595,9575208918745832173,131072 --enable-features=PasswordImport --lang=en-US --service-sandbox-type=utility --service-request-channel-token=16883391176057642671 --mojo-platform-channel-handle=3328 --ignored=" --type=renderer " /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 672 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --field-trial-handle=1044,14333885174459687595,9575208918745832173,131072 --enable-features=PasswordImport --lang=en-US --service-sandbox-type=utility --service-request-channel-token=4496595892504768167 --mojo-platform-channel-handle=3656 --ignored=" --type=renderer " /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 932 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=nacl-loader --field-trial-handle=1044,14333885174459687595,9575208918745832173,131072 --enable-features=PasswordImport --service-request-channel-token=13847399026320788666 --mojo-platform-channel-handle=3224 --ignored=" --type=renderer " /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 3221225496 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 1448 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --field-trial-handle=1044,14333885174459687595,9575208918745832173,131072 --enable-features=PasswordImport --lang=en-US --service-sandbox-type=utility --service-request-channel-token=1645393855685389549 --mojo-platform-channel-handle=3352 --ignored=" --type=renderer " /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 1460 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=1044,14333885174459687595,9575208918745832173,131072 --enable-features=PasswordImport --lang=en-US --extension-process --enable-offline-auto-reload --enable-offline-auto-reload-visible-only --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --service-request-channel-token=5450984594097532771 --renderer-client-id=4 --no-v8-untrusted-code-mitigations --mojo-platform-channel-handle=2492 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
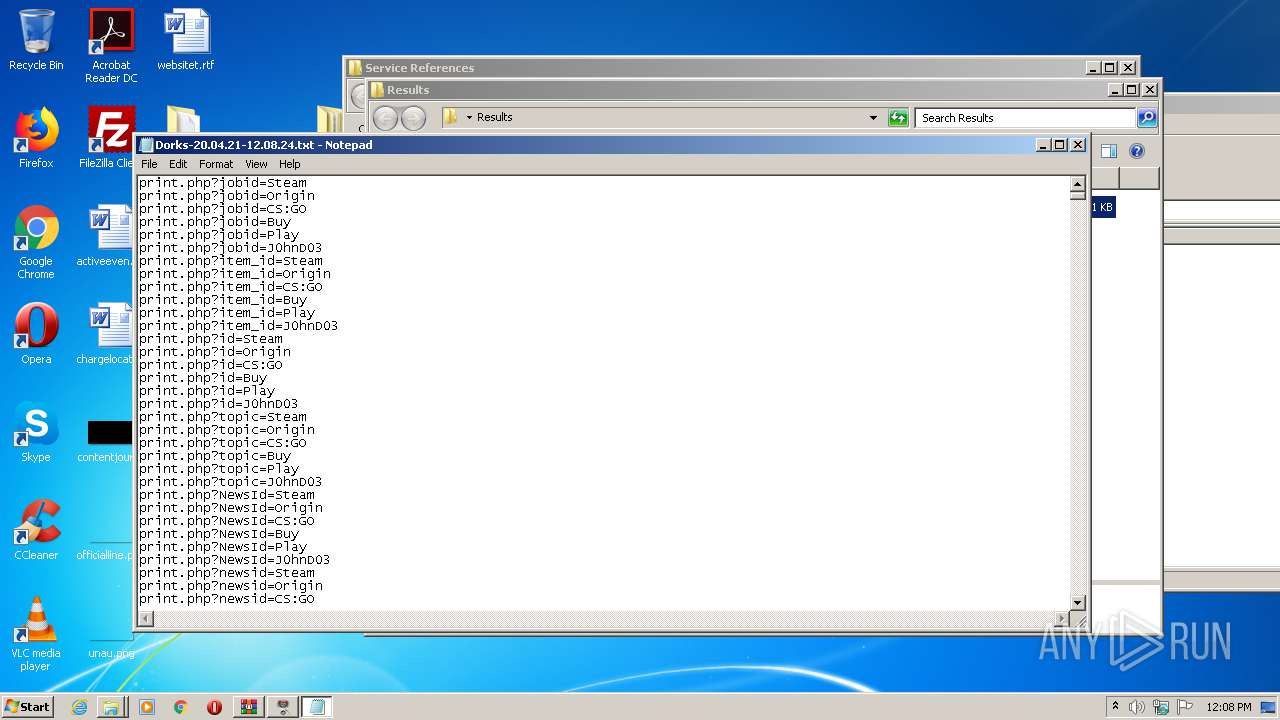
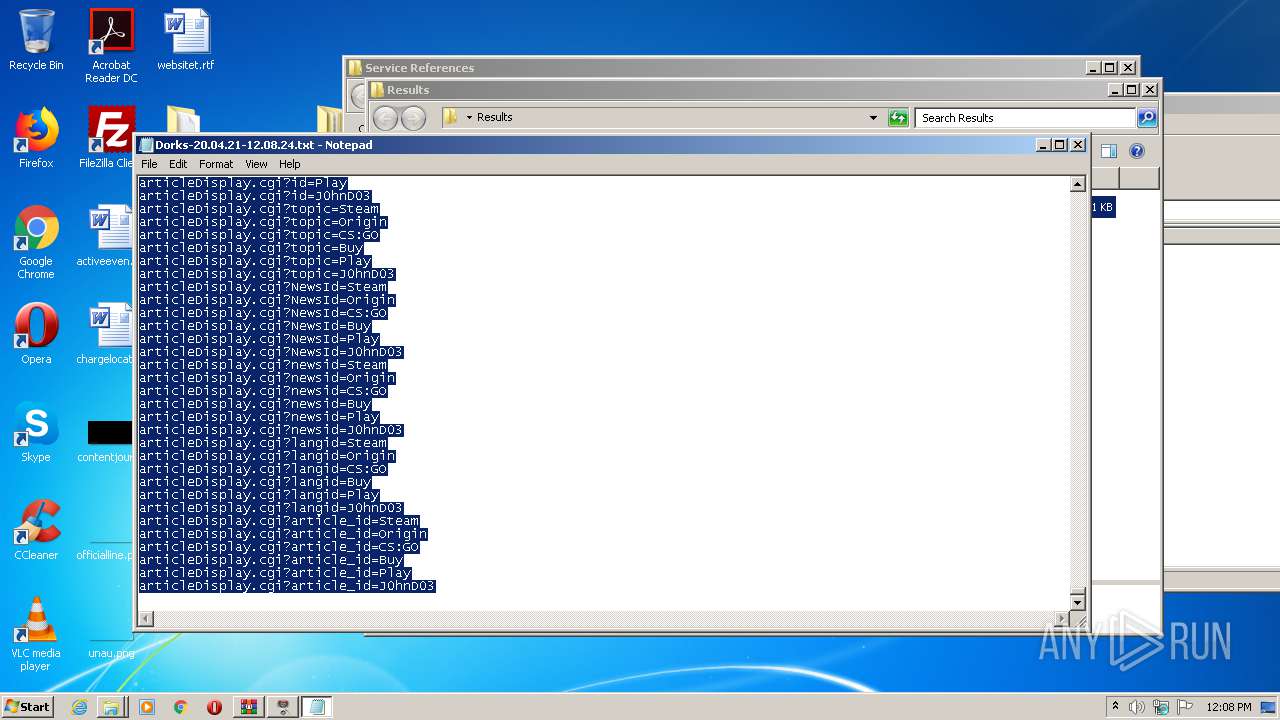
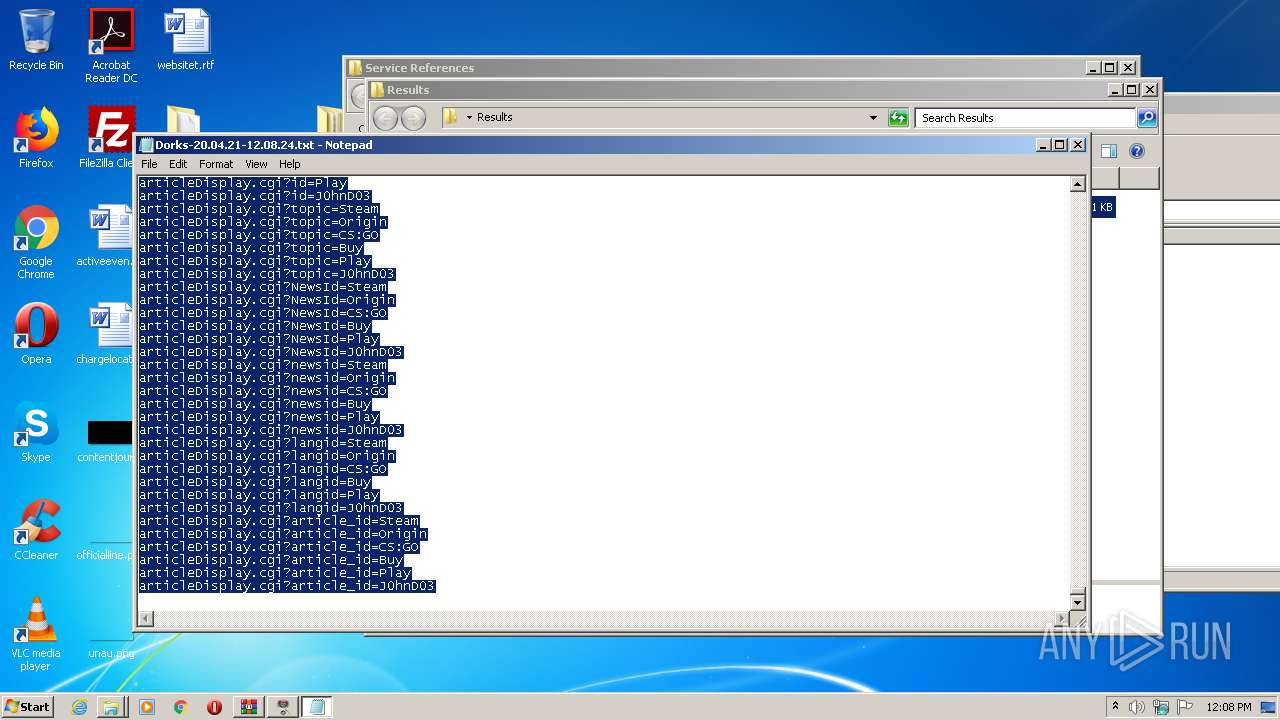
| 1536 | "C:\Windows\system32\NOTEPAD.EXE" C:\Users\admin\Desktop\Results\Dorks-20.04.21-12.08.24.txt | C:\Windows\system32\NOTEPAD.EXE | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Notepad Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1540 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=nacl-loader --field-trial-handle=1044,14333885174459687595,9575208918745832173,131072 --enable-features=PasswordImport --service-request-channel-token=4918166647193095608 --mojo-platform-channel-handle=4364 --ignored=" --type=renderer " /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 1672 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --field-trial-handle=1044,14333885174459687595,9575208918745832173,131072 --enable-features=PasswordImport --lang=en-US --service-sandbox-type=utility --service-request-channel-token=1179538996918417170 --mojo-platform-channel-handle=3484 --ignored=" --type=renderer " /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 1744 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --field-trial-handle=1044,14333885174459687595,9575208918745832173,131072 --enable-features=PasswordImport --lang=en-US --service-sandbox-type=utility --service-request-channel-token=4404679489896736493 --mojo-platform-channel-handle=3656 --ignored=" --type=renderer " /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
Total events
1 141
Read events
1 017
Write events
118
Delete events
6
Modification events
| (PID) Process: | (2540) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (2540) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (2540) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\13C\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (2540) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\13C\52C64B7E |
| Operation: | write | Name: | @C:\Windows\system32\NetworkExplorer.dll,-1 |
Value: Network | |||
| (PID) Process: | (2540) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\Work With Dorks [DORK's Generator] By JohnDoe v.2.1.7z | |||
| (PID) Process: | (2540) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (2540) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (2540) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (2540) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (3252) Work With Dork_v_2_1.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 0 | |||
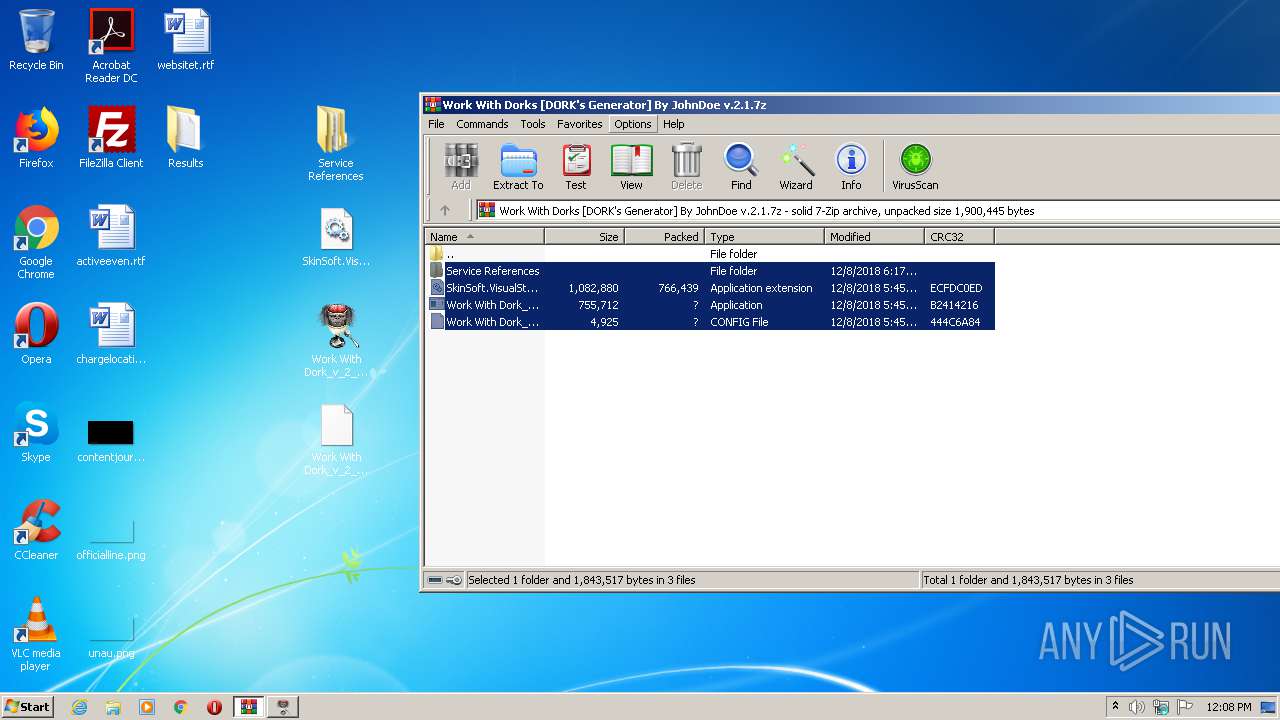
Executable files
3
Suspicious files
612
Text files
544
Unknown types
12
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3520 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\BrowserMetrics\BrowserMetrics-607EB64A-DC0.pma | — | |
MD5:— | SHA256:— | |||
| 3520 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\Site Characteristics Database\LOG.old | text | |
MD5:— | SHA256:— | |||
| 3520 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\Sync Data\LevelDB\LOG.old | text | |
MD5:— | SHA256:— | |||
| 2540 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa2540.22814\Service References\TranslatorService\soap.xsd | xml | |
MD5:A2213C9B642FE40C303DBECD10625284 | SHA256:95B5F1FA631A18CE2599D49E6DA7E0AC9B698370DDA6EFB8F101DB9542622E7B | |||
| 2540 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa2540.22814\Service References\TranslatorService\soap2.xsd | xml | |
MD5:386E42D097C9828BBF74E907A04472C8 | SHA256:DCED826BCB9B7BCC3F435A23F7E8BE179F8A70C781B53ACBF3E4605AEDBF699A | |||
| 2540 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa2540.22814\SkinSoft.VisualStyler.dll | executable | |
MD5:60AC512E63A6B95EB37CFD530A01B94E | SHA256:9F3E7EA22D052FEE0E5BE8CD904AC4425F3840DF7452C760D5CC5357830C394E | |||
| 3520 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\BudgetDatabase\LOG.old | — | |
MD5:— | SHA256:— | |||
| 3252 | Work With Dork_v_2_1.exe | C:\Users\admin\AppData\Local\SkinSoft\VisualStyler\2.4.59444.6\x86\ssapihook.dll | executable | |
MD5:9E7F44B8F1512476AA896E977C58830B | SHA256:8E6195B50BB0D22E4D346263F708F166DB726C84884FE78A6BB477CAED19E708 | |||
| 2540 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa2540.22814\Service References\TranslatorService\soap.wsdl | xml | |
MD5:34E29BF87AB995613009041EE8EFBCCE | SHA256:E8FE1EDDB15B316C35A9D498C91081823212452226A42278B7A086CB2FC416CC | |||
| 2540 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa2540.22814\Service References\TranslatorService\configuration.svcinfo | xml | |
MD5:D935CB832F65D86D7C2A57D1794F5953 | SHA256:42C0CA38FE255D41F4C1E5585C547D62C87FBE2E03BDDC17D16D42898819A32D | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
19
TCP/UDP connections
43
DNS requests
28
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
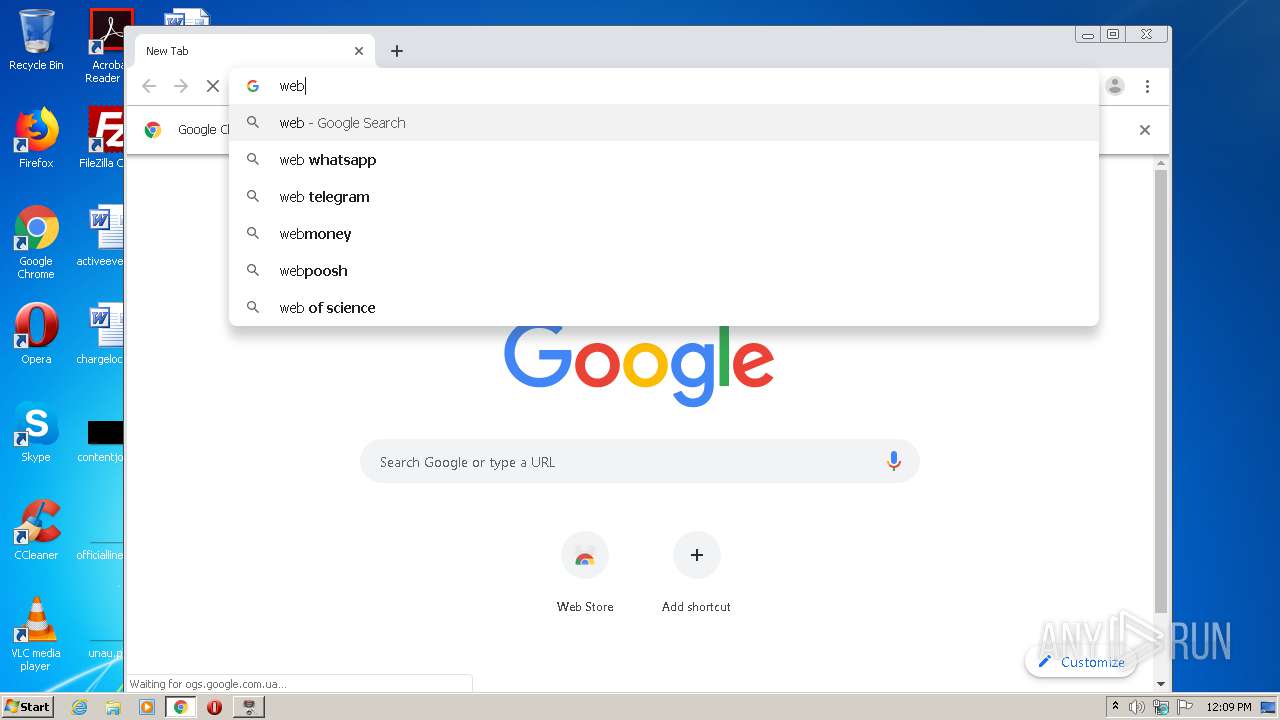
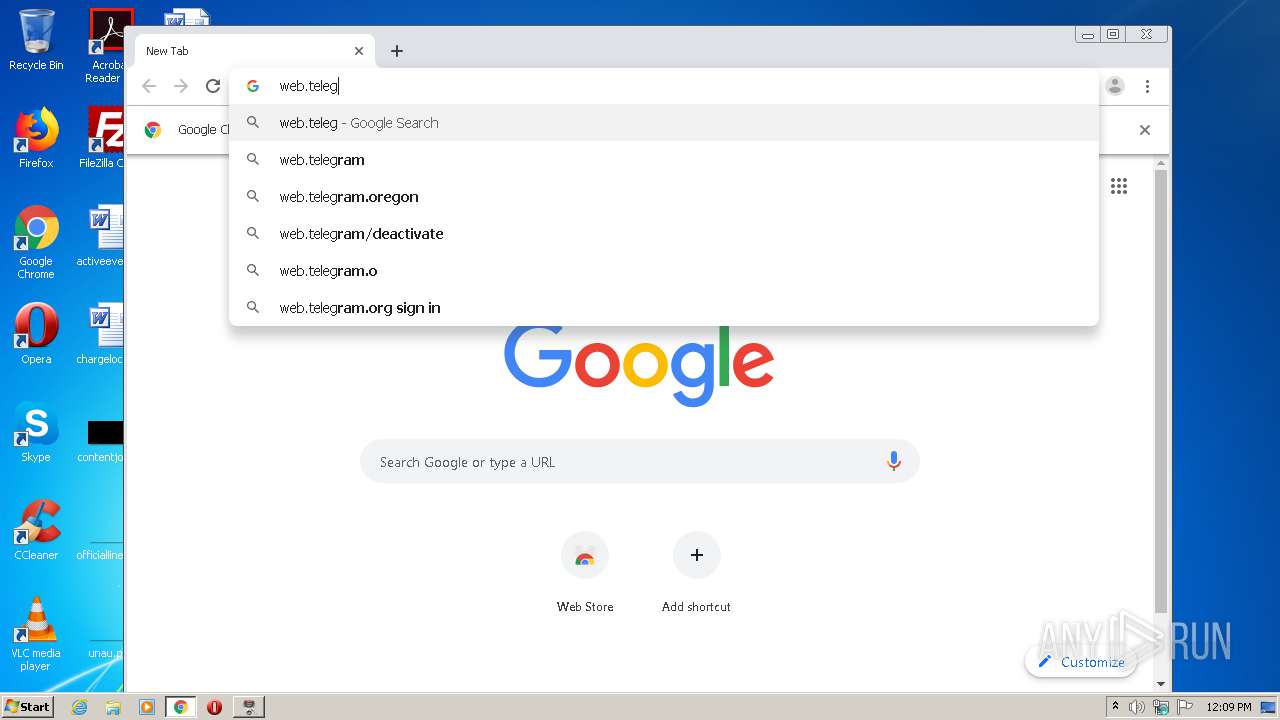
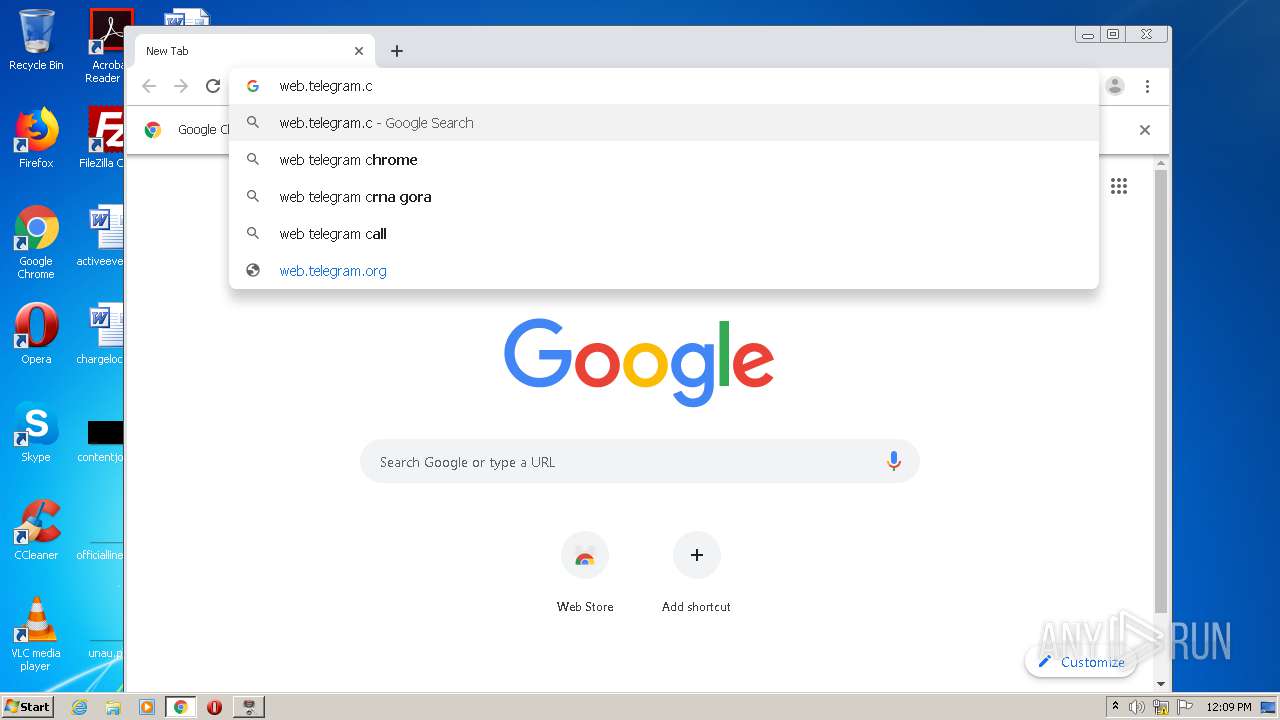
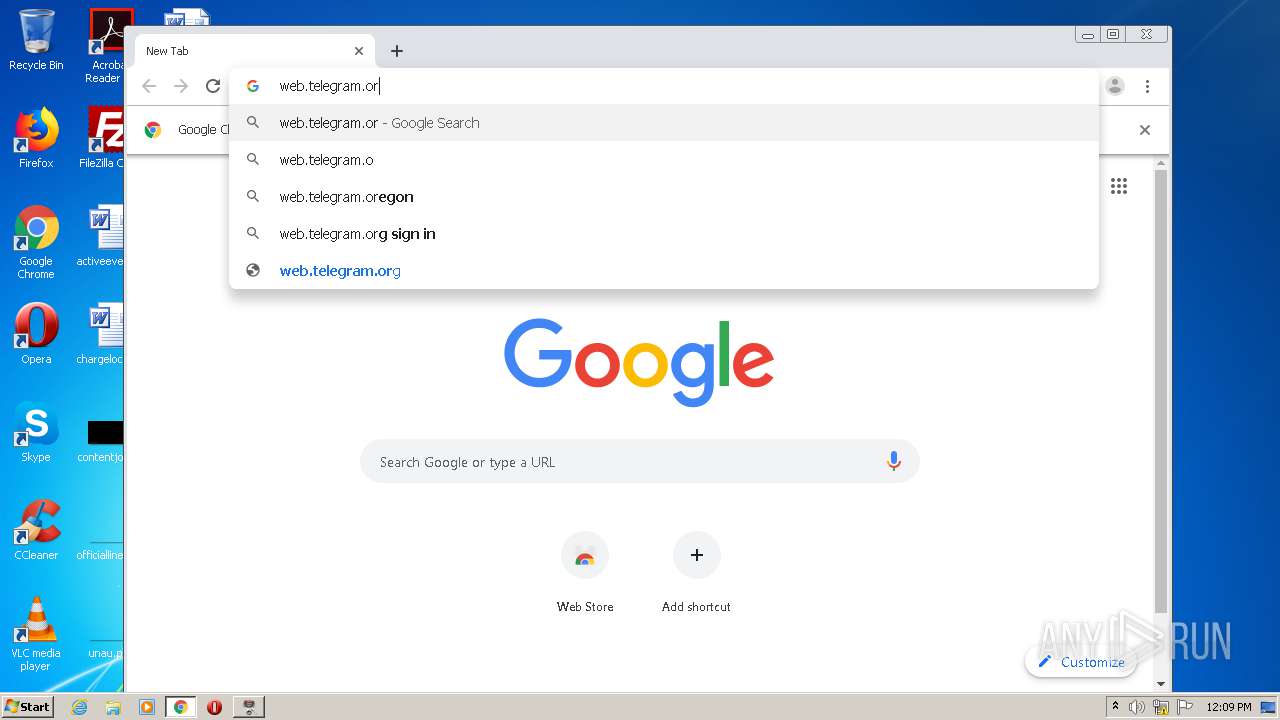
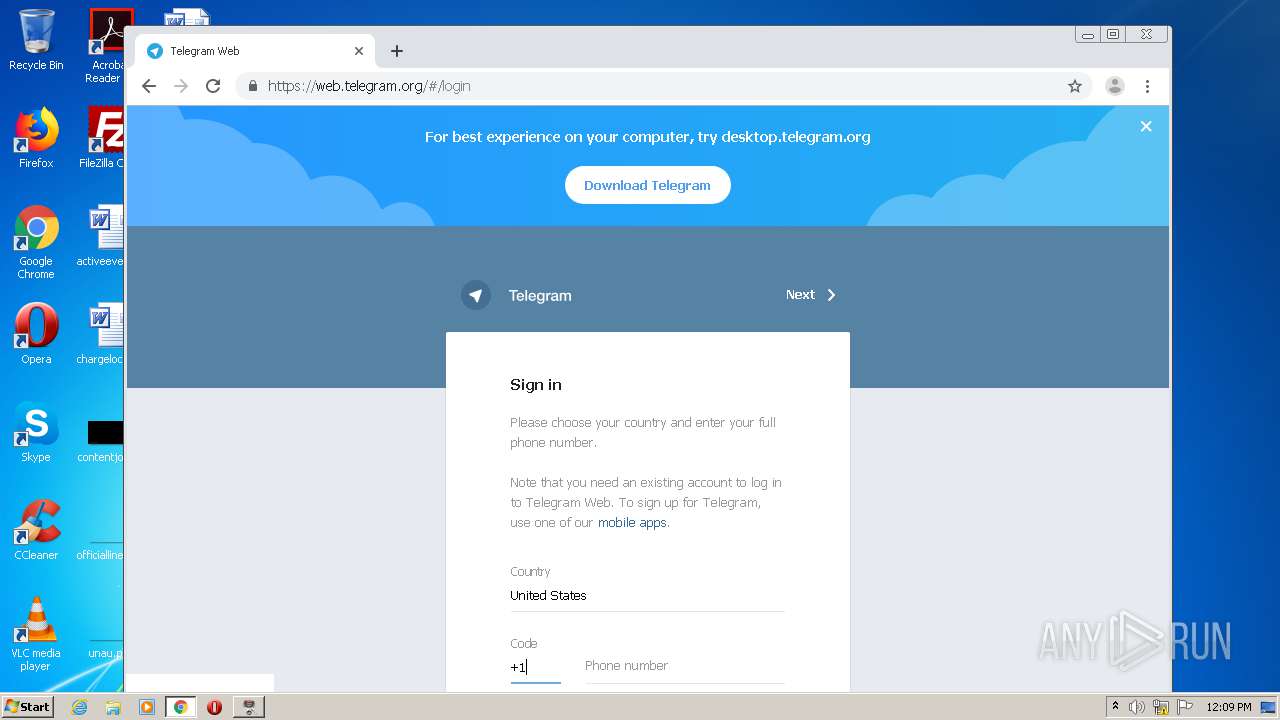
1860 | chrome.exe | GET | 200 | 149.154.167.99:80 | http://web.telegram.org/js/lib/crypto_worker.js | GB | text | 550 b | whitelisted |
1860 | chrome.exe | GET | 200 | 149.154.167.99:80 | http://web.telegram.org/js/app.js | GB | binary | 819 Kb | whitelisted |
1860 | chrome.exe | GET | 200 | 149.154.167.99:80 | http://web.telegram.org/nacl/mtproto_crypto.nmf | GB | text | 144 b | whitelisted |
1860 | chrome.exe | GET | 302 | 216.58.212.174:80 | http://redirector.gvt1.com/edgedl/chromewebstore/L2Nocm9tZV9leHRlbnNpb24vYmxvYnMvNzI0QUFXNV9zT2RvdUwyMERESEZGVmJnQQ/1.0.0.6_nmmhkkegccagdldgiimedpiccmgmieda.crx | US | html | 519 b | whitelisted |
1860 | chrome.exe | GET | 200 | 149.154.167.99:80 | http://web.telegram.org/nacl/mtproto_crypto.pexe?67 | GB | binary | 103 Kb | whitelisted |
1860 | chrome.exe | GET | 200 | 149.154.167.99:80 | http://web.telegram.org/js/lib/bin_utils.js | GB | text | 4.86 Kb | whitelisted |
1860 | chrome.exe | GET | 200 | 149.154.167.99:80 | http://web.telegram.org/css/app.css | GB | text | 45.2 Kb | whitelisted |
1860 | chrome.exe | GET | 200 | 173.194.5.40:80 | http://r3---sn-aigzrn7e.gvt1.com/edgedl/chromewebstore/L2Nocm9tZV9leHRlbnNpb24vYmxvYnMvNzI0QUFXNV9zT2RvdUwyMERESEZGVmJnQQ/1.0.0.6_nmmhkkegccagdldgiimedpiccmgmieda.crx?cms_redirect=yes&mh=e_&mip=85.203.34.115&mm=28&mn=sn-aigzrn7e&ms=nvh&mt=1618916661&mv=m&mvi=3&pl=24&shardbypass=yes | US | crx | 242 Kb | whitelisted |
1860 | chrome.exe | GET | 200 | 149.154.167.99:80 | http://web.telegram.org/ | GB | html | 690 b | whitelisted |
1860 | chrome.exe | GET | 301 | 149.154.167.99:80 | http://telegram.me/_websync_?authed=0 | GB | html | 169 b | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
1860 | chrome.exe | 142.250.186.99:443 | fonts.gstatic.com | Google Inc. | US | whitelisted |
1860 | chrome.exe | 142.250.186.129:443 | clients2.googleusercontent.com | Google Inc. | US | whitelisted |
1860 | chrome.exe | 216.58.212.174:80 | redirector.gvt1.com | Google Inc. | US | whitelisted |
1860 | chrome.exe | 173.194.5.40:80 | r3---sn-aigzrn7e.gvt1.com | Google Inc. | US | whitelisted |
1860 | chrome.exe | 142.250.185.228:443 | www.google.com | Google Inc. | US | whitelisted |
1860 | chrome.exe | 142.250.186.174:443 | clients4.google.com | Google Inc. | US | whitelisted |
1860 | chrome.exe | 142.250.185.74:443 | safebrowsing.googleapis.com | Google Inc. | US | whitelisted |
1860 | chrome.exe | 172.217.18.99:443 | clientservices.googleapis.com | Google Inc. | US | whitelisted |
1860 | chrome.exe | 142.250.185.99:443 | www.google.com.ua | Google Inc. | US | whitelisted |
1860 | chrome.exe | 142.250.185.206:443 | clients2.google.com | Google Inc. | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
clientservices.googleapis.com |
| whitelisted |
accounts.google.com |
| shared |
www.google.com.ua |
| whitelisted |
clients2.google.com |
| whitelisted |
fonts.googleapis.com |
| whitelisted |
www.gstatic.com |
| whitelisted |
fonts.gstatic.com |
| whitelisted |
clients2.googleusercontent.com |
| whitelisted |
redirector.gvt1.com |
| whitelisted |
apis.google.com |
| whitelisted |