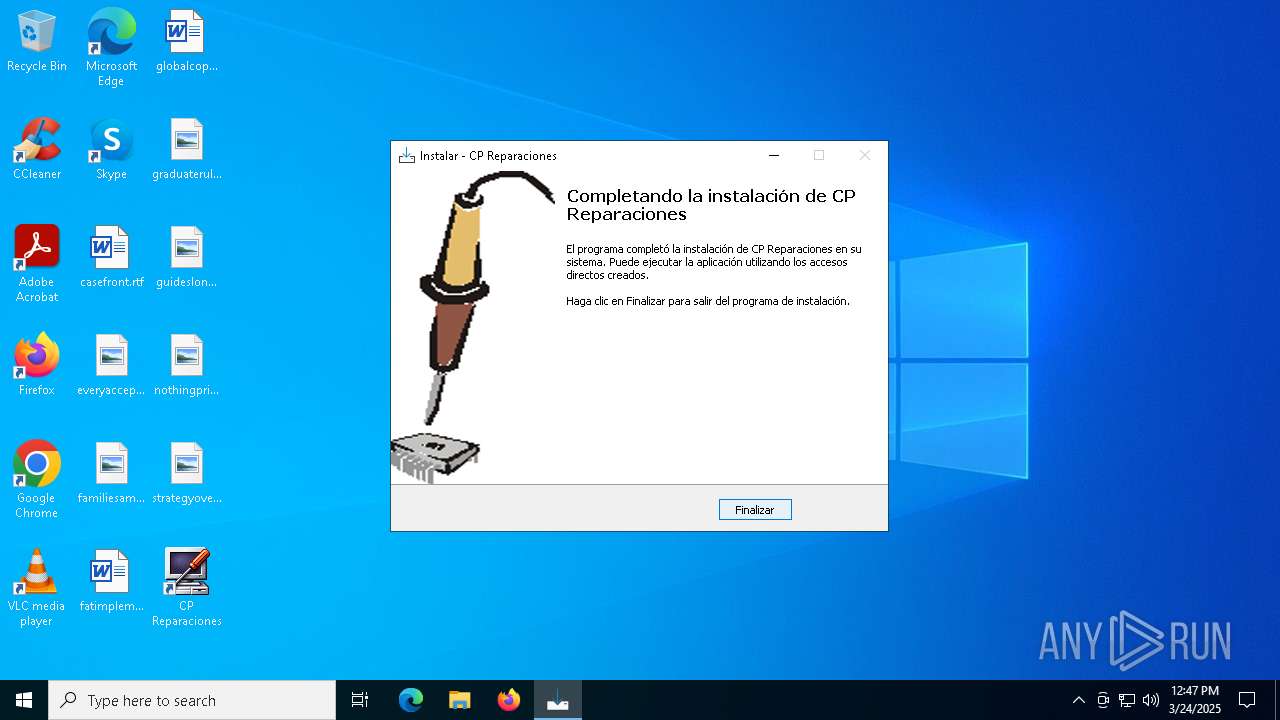
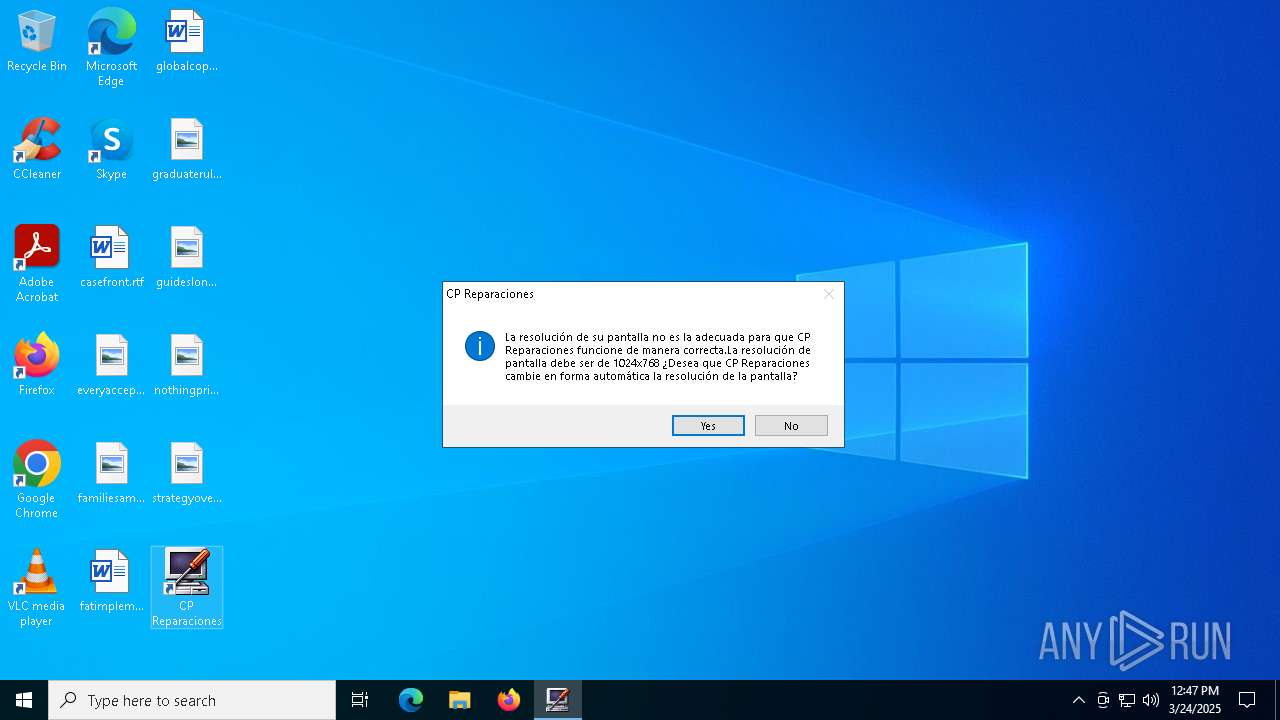
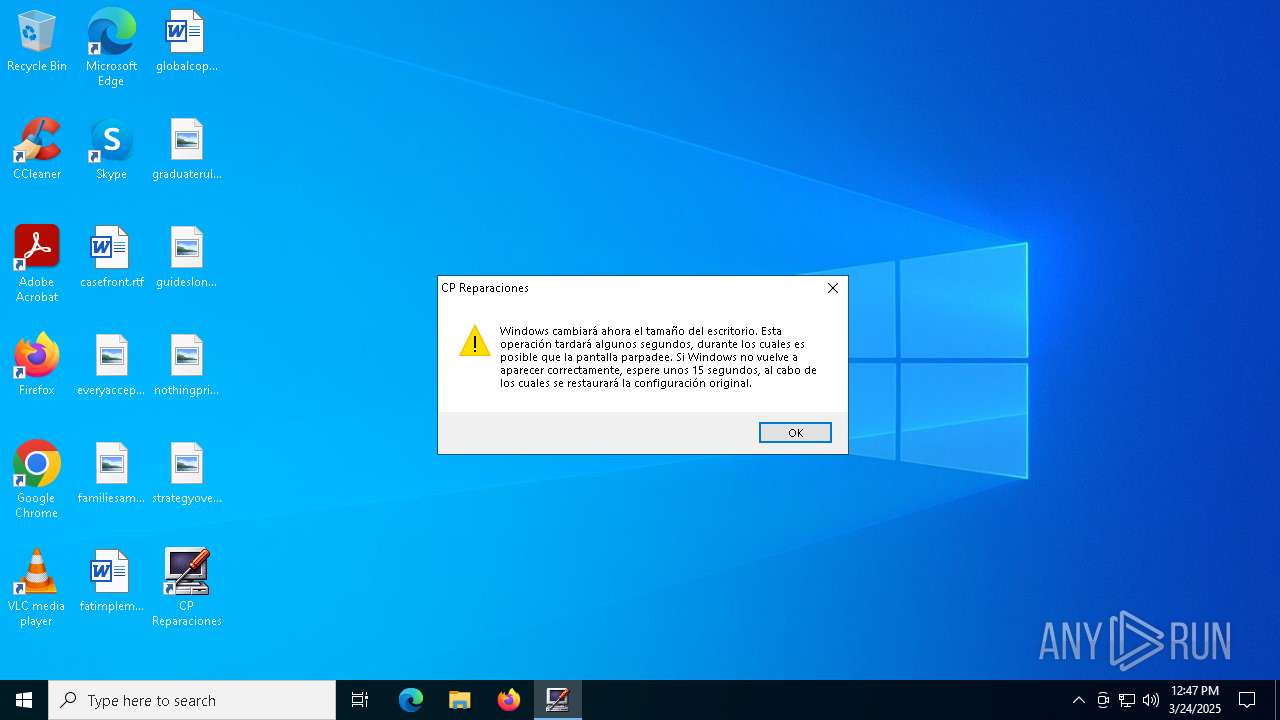
| File name: | cprepair.exe |
| Full analysis: | https://app.any.run/tasks/4f1a8e9b-08f8-4502-95dc-670ed60a8529 |
| Verdict: | Malicious activity |
| Analysis date: | March 24, 2025, 12:46:44 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/vnd.microsoft.portable-executable |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows, 11 sections |
| MD5: | A5A6C6C1EDBE87D744D0B148560A6C96 |
| SHA1: | 233C88DD8486377178A83547891D350CEF8EFE86 |
| SHA256: | 494523B18CBECC73DA06F46A286EA69E61F5A16FABBA55328661190510508770 |
| SSDEEP: | 98304:mrq3BdwqpzUmCkOG664nMLi05gOxMPy24nPkviUL/MYjOgHLRd+pybbm/ohniaqC:HTCB2ibhokUNwIaJ/VqcMI |
MALICIOUS
Registers / Runs the DLL via REGSVR32.EXE
- cprepair.tmp (PID: 1052)
SUSPICIOUS
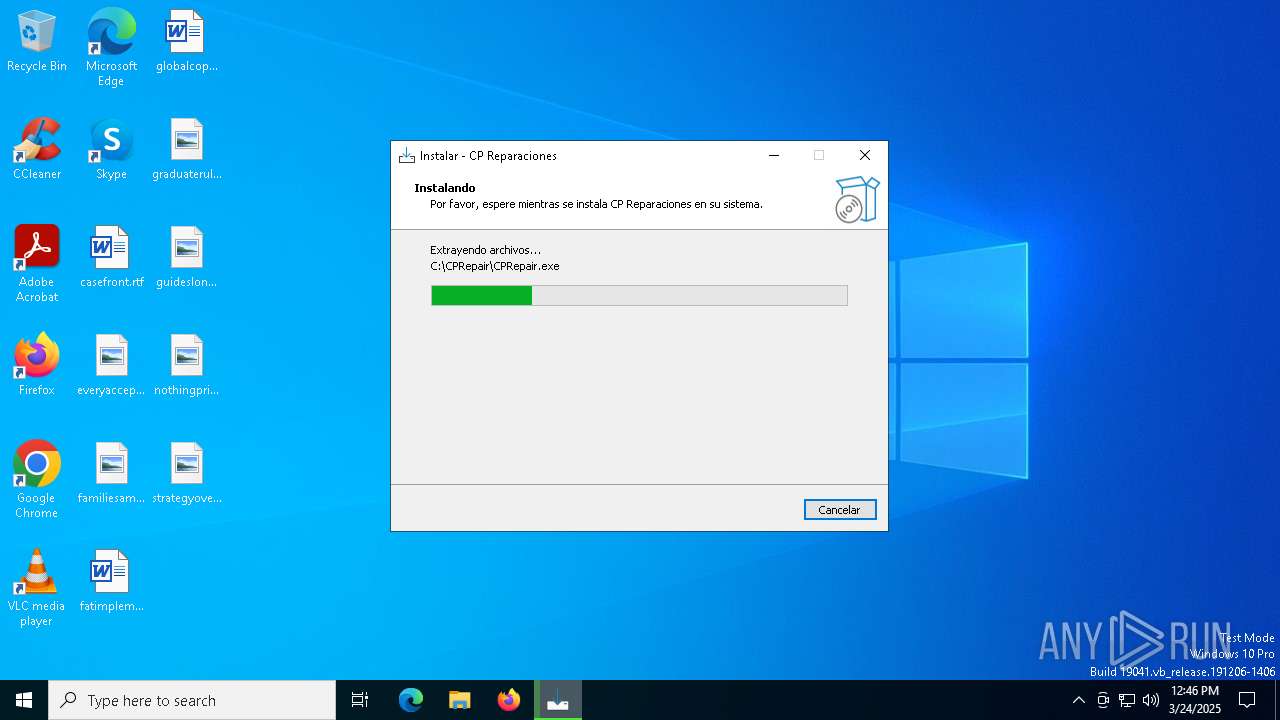
Executable content was dropped or overwritten
- cprepair.exe (PID: 4756)
- cprepair.exe (PID: 5024)
- cprepair.tmp (PID: 1052)
Reads security settings of Internet Explorer
- cprepair.tmp (PID: 4776)
Reads the Windows owner or organization settings
- cprepair.tmp (PID: 1052)
Process drops legitimate windows executable
- cprepair.tmp (PID: 1052)
Creates/Modifies COM task schedule object
- regsvr32.exe (PID: 7560)
- regsvr32.exe (PID: 7616)
- regsvr32.exe (PID: 7656)
- regsvr32.exe (PID: 7636)
- regsvr32.exe (PID: 7680)
- regsvr32.exe (PID: 7800)
INFO
Checks supported languages
- cprepair.exe (PID: 4756)
- cprepair.tmp (PID: 4776)
- cprepair.exe (PID: 5024)
- cprepair.tmp (PID: 1052)
Create files in a temporary directory
- cprepair.exe (PID: 4756)
- cprepair.exe (PID: 5024)
- cprepair.tmp (PID: 1052)
Reads the computer name
- cprepair.tmp (PID: 4776)
- cprepair.exe (PID: 5024)
- cprepair.tmp (PID: 1052)
Process checks computer location settings
- cprepair.tmp (PID: 4776)
The sample compiled with spanish language support
- cprepair.tmp (PID: 1052)
The sample compiled with english language support
- cprepair.tmp (PID: 1052)
Creates files or folders in the user directory
- cprepair.tmp (PID: 1052)
- BackgroundTransferHost.exe (PID: 7308)
Reads mouse settings
- regsvr32.exe (PID: 7680)
Manual execution by a user
- CPRepair.exe (PID: 7736)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Inno Setup installer (53.5) |
|---|---|---|
| .exe | | | InstallShield setup (21) |
| .exe | | | Win32 EXE PECompact compressed (generic) (20.2) |
| .exe | | | Win32 Executable (generic) (2.1) |
| .exe | | | Win16/32 Executable Delphi generic (1) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2024:07:12 07:26:53+00:00 |
| ImageFileCharacteristics: | Executable, 32-bit |
| PEType: | PE32 |
| LinkerVersion: | 2.25 |
| CodeSize: | 685056 |
| InitializedDataSize: | 159744 |
| UninitializedDataSize: | - |
| EntryPoint: | 0xa83bc |
| OSVersion: | 6.1 |
| ImageVersion: | - |
| SubsystemVersion: | 6.1 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 4.9.0.0 |
| ProductVersionNumber: | 4.9.0.0 |
| FileFlagsMask: | 0x003f |
| FileFlags: | (none) |
| FileOS: | Win32 |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | Neutral |
| CharacterSet: | Unicode |
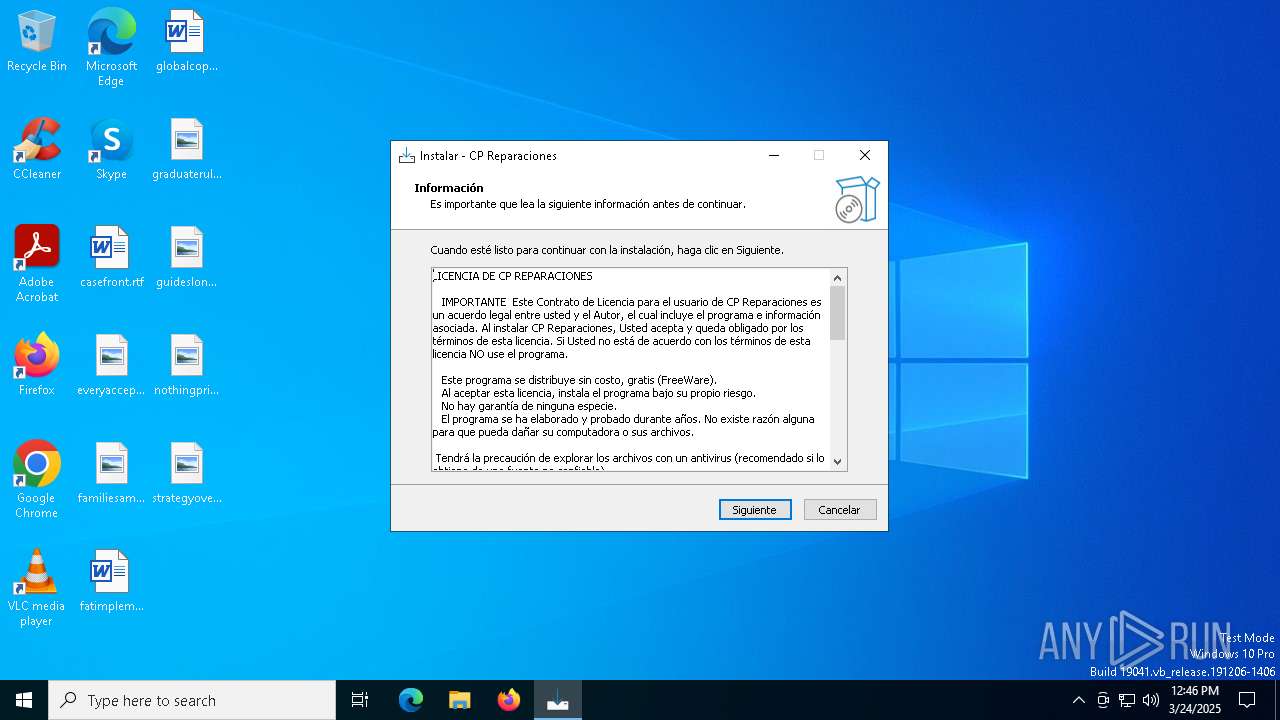
| Comments: | This installation was built with Inno Setup. |
| CompanyName: | Consulta Práctica ® |
| FileDescription: | CP Reparaciones Setup |
| FileVersion: | 4.9.0.0 |
| LegalCopyright: | Dr. Ignacio Mario Morales Flores |
| OriginalFileName: | |
| ProductName: | CP Reparaciones |
| ProductVersion: | 4.9.0.0 |
Total processes
166
Monitored processes
28
Malicious processes
4
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 672 | "C:\WINDOWS\System32\SLUI.exe" RuleId=3482d82e-ca2c-4e1f-8864-da0267b484b2;Action=AutoActivate;AppId=55c92734-d682-4d71-983e-d6ec3f16059f;SkuId=4de7cb65-cdf1-4de9-8ae8-e3cce27b9f2c;NotificationInterval=1440;Trigger=TimerEvent | C:\Windows\System32\slui.exe | — | SppExtComObj.Exe | |||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows Activation Client Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 728 | "BackgroundTransferHost.exe" -ServerName:BackgroundTransferHost.1 | C:\Windows\System32\BackgroundTransferHost.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Download/Upload Host Exit code: 1 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
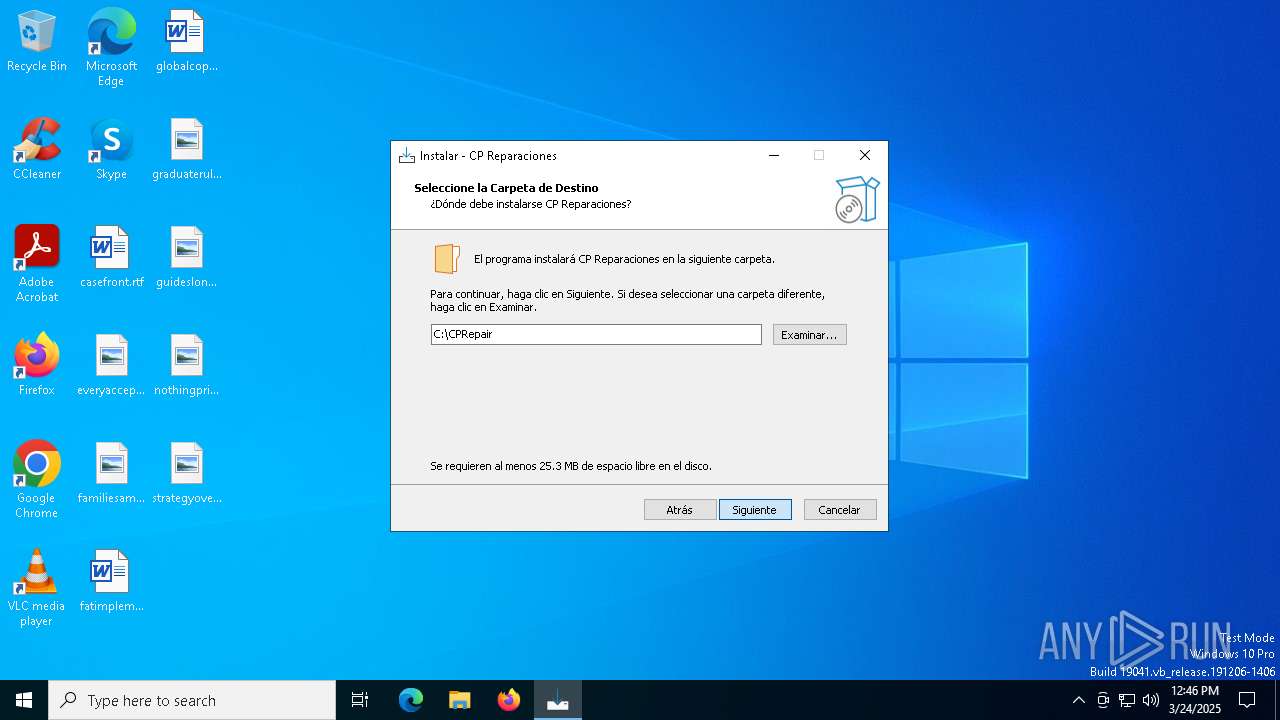
| 1052 | "C:\Users\admin\AppData\Local\Temp\is-11K1H.tmp\cprepair.tmp" /SL5="$1602D4,7577705,845824,C:\Users\admin\AppData\Local\Temp\cprepair.exe" /SPAWNWND=$602B0 /NOTIFYWND=$30300 | C:\Users\admin\AppData\Local\Temp\is-11K1H.tmp\cprepair.tmp | cprepair.exe | ||||||||||||
User: admin Company: Consulta Práctica ® Integrity Level: HIGH Description: Setup/Uninstall Exit code: 0 Version: 51.1052.0.0 Modules
| |||||||||||||||
| 1240 | "BackgroundTransferHost.exe" -ServerName:BackgroundTransferHost.1 | C:\Windows\System32\BackgroundTransferHost.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Download/Upload Host Exit code: 1 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1324 | C:\WINDOWS\system32\SppExtComObj.exe -Embedding | C:\Windows\System32\SppExtComObj.Exe | — | svchost.exe | |||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: KMS Connection Broker Version: 10.0.19041.3996 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4756 | "C:\Users\admin\AppData\Local\Temp\cprepair.exe" | C:\Users\admin\AppData\Local\Temp\cprepair.exe | explorer.exe | ||||||||||||
User: admin Company: Consulta Práctica ® Integrity Level: MEDIUM Description: CP Reparaciones Setup Exit code: 0 Version: 4.9.0.0 Modules
| |||||||||||||||
| 4776 | "C:\Users\admin\AppData\Local\Temp\is-AE5TK.tmp\cprepair.tmp" /SL5="$30300,7577705,845824,C:\Users\admin\AppData\Local\Temp\cprepair.exe" | C:\Users\admin\AppData\Local\Temp\is-AE5TK.tmp\cprepair.tmp | — | cprepair.exe | |||||||||||
User: admin Company: Consulta Práctica ® Integrity Level: MEDIUM Description: Setup/Uninstall Exit code: 0 Version: 51.1052.0.0 Modules
| |||||||||||||||
| 5024 | "C:\Users\admin\AppData\Local\Temp\cprepair.exe" /SPAWNWND=$602B0 /NOTIFYWND=$30300 | C:\Users\admin\AppData\Local\Temp\cprepair.exe | cprepair.tmp | ||||||||||||
User: admin Company: Consulta Práctica ® Integrity Level: HIGH Description: CP Reparaciones Setup Exit code: 0 Version: 4.9.0.0 Modules
| |||||||||||||||
| 7308 | "BackgroundTransferHost.exe" -ServerName:BackgroundTransferHost.1 | C:\Windows\System32\BackgroundTransferHost.exe | svchost.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Download/Upload Host Exit code: 1 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 7532 | "C:\WINDOWS\system32\regsvr32.exe" /s "C:\WINDOWS\system32\msvbvm60.dll" | C:\Windows\SysWOW64\regsvr32.exe | — | cprepair.tmp | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Microsoft(C) Register Server Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
3 295
Read events
2 747
Write events
401
Delete events
147
Modification events
| (PID) Process: | (1052) cprepair.tmp | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Windows\CurrentVersion\SharedDlls |
| Operation: | write | Name: | C:\WINDOWS\system32\msvbvm60.dll |
Value: 2 | |||
| (PID) Process: | (1052) cprepair.tmp | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Windows\CurrentVersion\SharedDlls |
| Operation: | write | Name: | C:\WINDOWS\system32\vb6es.dll |
Value: 1 | |||
| (PID) Process: | (1052) cprepair.tmp | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Windows\CurrentVersion\SharedDlls |
| Operation: | write | Name: | C:\WINDOWS\system32\CMDLGES.DLL |
Value: 1 | |||
| (PID) Process: | (1052) cprepair.tmp | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Windows\CurrentVersion\SharedDlls |
| Operation: | write | Name: | C:\WINDOWS\system32\Comdlg32.ocx |
Value: 1 | |||
| (PID) Process: | (1052) cprepair.tmp | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Windows\CurrentVersion\SharedDlls |
| Operation: | write | Name: | C:\WINDOWS\system32\SSCALA32.OCX |
Value: 1 | |||
| (PID) Process: | (1052) cprepair.tmp | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Windows\CurrentVersion\SharedDlls |
| Operation: | write | Name: | C:\WINDOWS\system32\mscomctl.ocx |
Value: 1 | |||
| (PID) Process: | (1052) cprepair.tmp | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Windows\CurrentVersion\SharedDlls |
| Operation: | write | Name: | C:\WINDOWS\system32\FLXGDES.DLL |
Value: 1 | |||
| (PID) Process: | (1052) cprepair.tmp | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Windows\CurrentVersion\SharedDlls |
| Operation: | write | Name: | C:\WINDOWS\system32\THREED32.OCX |
Value: 1 | |||
| (PID) Process: | (1052) cprepair.tmp | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Windows\CurrentVersion\SharedDlls |
| Operation: | write | Name: | C:\WINDOWS\system32\CPTools.dll |
Value: 1 | |||
| (PID) Process: | (1052) cprepair.tmp | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Windows\CurrentVersion\SharedDlls |
| Operation: | write | Name: | C:\WINDOWS\system32\VBPrnDlg.dll |
Value: 1 | |||
Executable files
117
Suspicious files
32
Text files
10
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 1052 | cprepair.tmp | C:\CPRepair\CPRepair.chm | binary | |
MD5:E261772F6C1E4AD0298DCC8C5BB331B1 | SHA256:4FC890966F16F4998965A37CCA696FE6502196B5AA417A2EC2C19D3316CA0DA6 | |||
| 1052 | cprepair.tmp | C:\CPRepair\is-KA3HJ.tmp | binary | |
MD5:25EBAF03C1DAA8565891BFA2D81FA007 | SHA256:69CC57FD063E4639E2E5227DF3DF17FF15546A7AB1D0863F96D3FE96A0A0E9CC | |||
| 1052 | cprepair.tmp | C:\Users\admin\AppData\Local\Temp\is-LGNOQ.tmp\_isetup\_setup64.tmp | executable | |
MD5:E4211D6D009757C078A9FAC7FF4F03D4 | SHA256:388A796580234EFC95F3B1C70AD4CB44BFDDC7BA0F9203BF4902B9929B136F95 | |||
| 1052 | cprepair.tmp | C:\CPRepair\is-R4L8I.tmp | executable | |
MD5:59B2587D5B8EF627C462D4EB4E719614 | SHA256:2FAC965585E404AE8340425FB5C7F77920B55DE76F5EF50B946118D391608804 | |||
| 1052 | cprepair.tmp | C:\CPRepair\unins000.exe | executable | |
MD5:59B2587D5B8EF627C462D4EB4E719614 | SHA256:2FAC965585E404AE8340425FB5C7F77920B55DE76F5EF50B946118D391608804 | |||
| 5024 | cprepair.exe | C:\Users\admin\AppData\Local\Temp\is-11K1H.tmp\cprepair.tmp | executable | |
MD5:DCB9361FC1E4AED8DD1539C61658762F | SHA256:DF834164D7CCEEED296128A451656E9819D6F8F338AA7F9D627D7515EC3EF557 | |||
| 1052 | cprepair.tmp | C:\CPRepair\is-OTL17.tmp | binary | |
MD5:E261772F6C1E4AD0298DCC8C5BB331B1 | SHA256:4FC890966F16F4998965A37CCA696FE6502196B5AA417A2EC2C19D3316CA0DA6 | |||
| 1052 | cprepair.tmp | C:\Windows\SysWOW64\vb6es.dll | executable | |
MD5:5920F5A17A7BB807EF3F1F7CB5558728 | SHA256:B9C2FA6DECF3C7027C6AC7D363A1714B732E0B75AD17327F3E31C6B88FA9E92A | |||
| 1052 | cprepair.tmp | C:\CPRepair\is-7E5H2.tmp | binary | |
MD5:2CF989E35F6D0682C251DDBB1326271B | SHA256:A8FCC01B90741611C16CAC2083EDF01BF6C9E40C2EAAEFCEDCD1413855B0BF08 | |||
| 1052 | cprepair.tmp | C:\CPRepair\Entrada.rpt | binary | |
MD5:25EBAF03C1DAA8565891BFA2D81FA007 | SHA256:69CC57FD063E4639E2E5227DF3DF17FF15546A7AB1D0863F96D3FE96A0A0E9CC | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
6
TCP/UDP connections
24
DNS requests
13
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
5496 | MoUsoCoreWorker.exe | GET | 200 | 23.48.23.159:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
6544 | svchost.exe | GET | 200 | 184.30.131.245:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
5892 | backgroundTaskHost.exe | GET | 200 | 184.30.131.245:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAUZZSZEml49Gjh0j13P68w%3D | unknown | — | — | whitelisted |
7308 | BackgroundTransferHost.exe | GET | 200 | 184.30.131.245:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
8096 | SIHClient.exe | GET | 200 | 23.219.150.101:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
8096 | SIHClient.exe | GET | 200 | 23.219.150.101:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
— | — | 40.127.240.158:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | IE | unknown |
5496 | MoUsoCoreWorker.exe | 23.48.23.159:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
2104 | svchost.exe | 40.127.240.158:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | IE | unknown |
3216 | svchost.exe | 40.113.103.199:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
6544 | svchost.exe | 40.126.31.69:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
6544 | svchost.exe | 184.30.131.245:80 | ocsp.digicert.com | AKAMAI-AS | US | whitelisted |
1196 | RUXIMICS.exe | 40.127.240.158:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | IE | unknown |
2112 | svchost.exe | 40.127.240.158:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | IE | unknown |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
google.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
arc.msn.com |
| whitelisted |
www.bing.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |