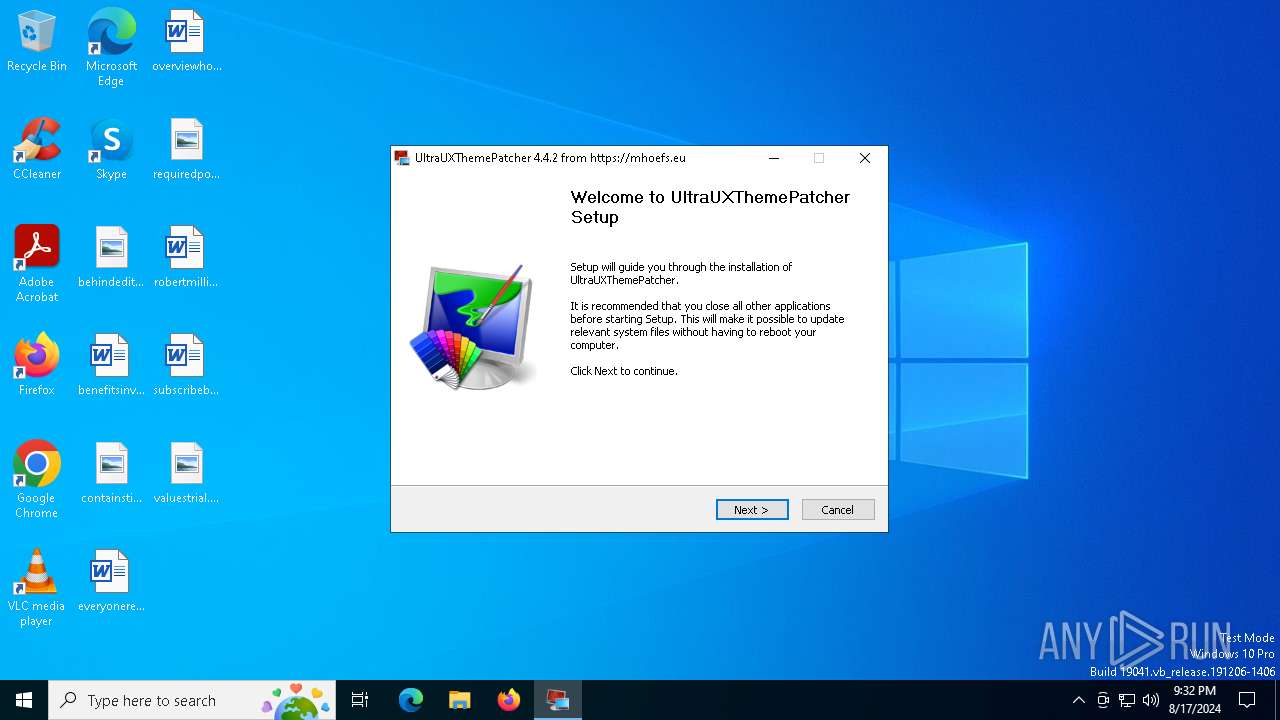
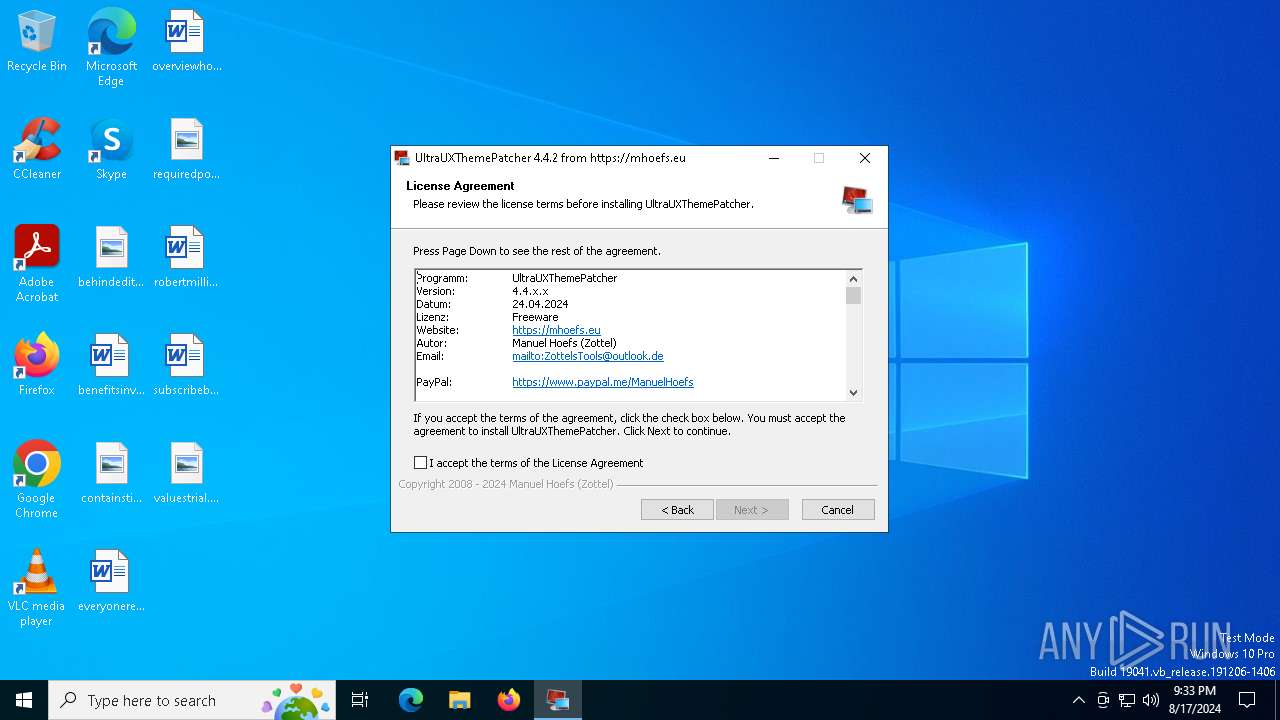
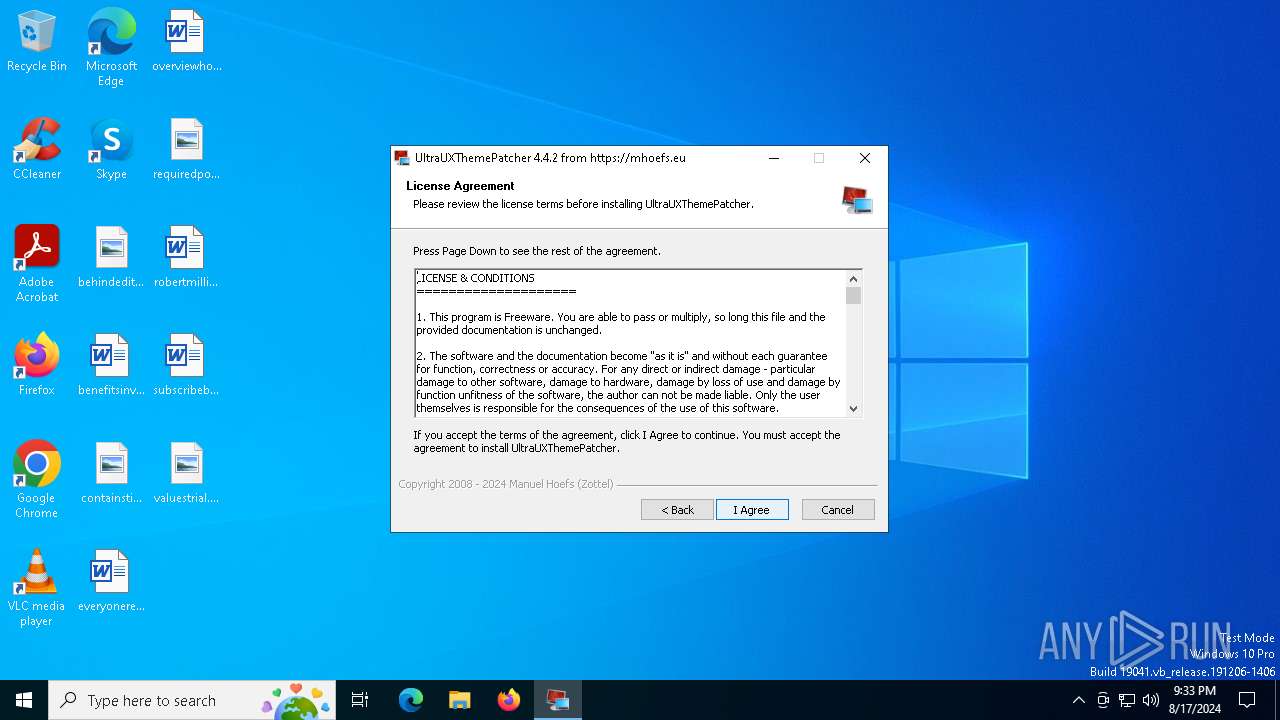
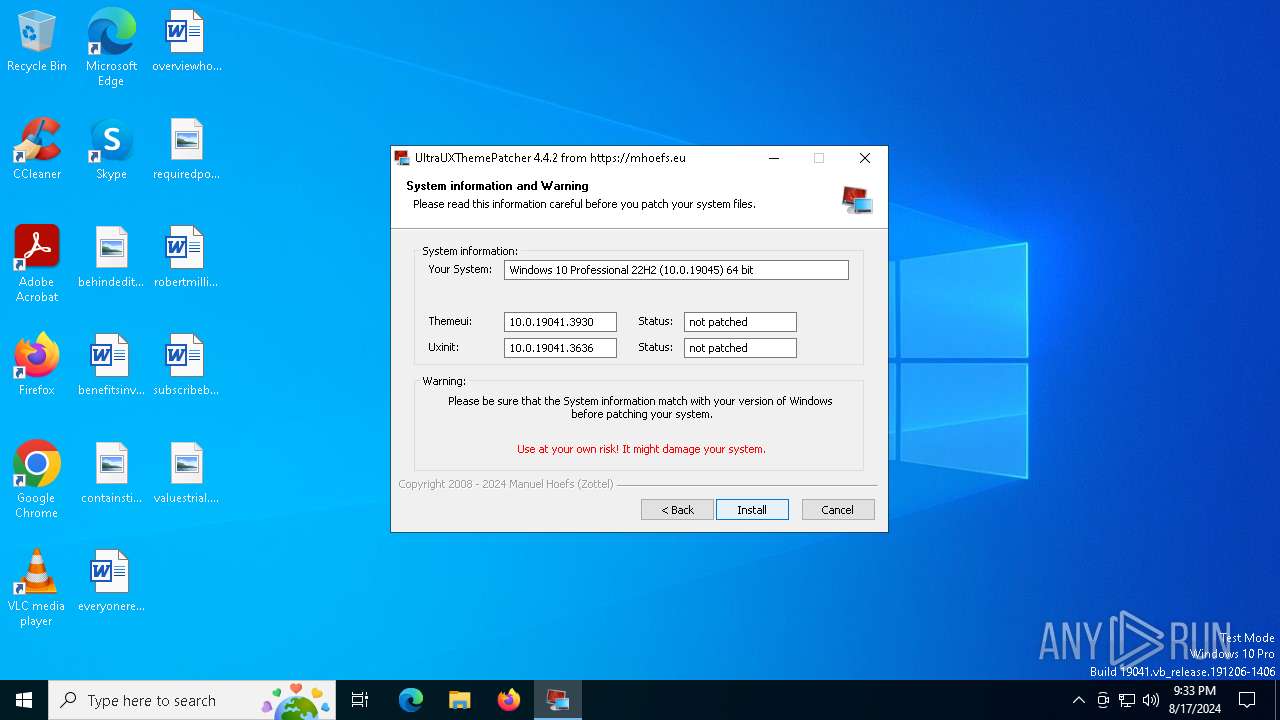
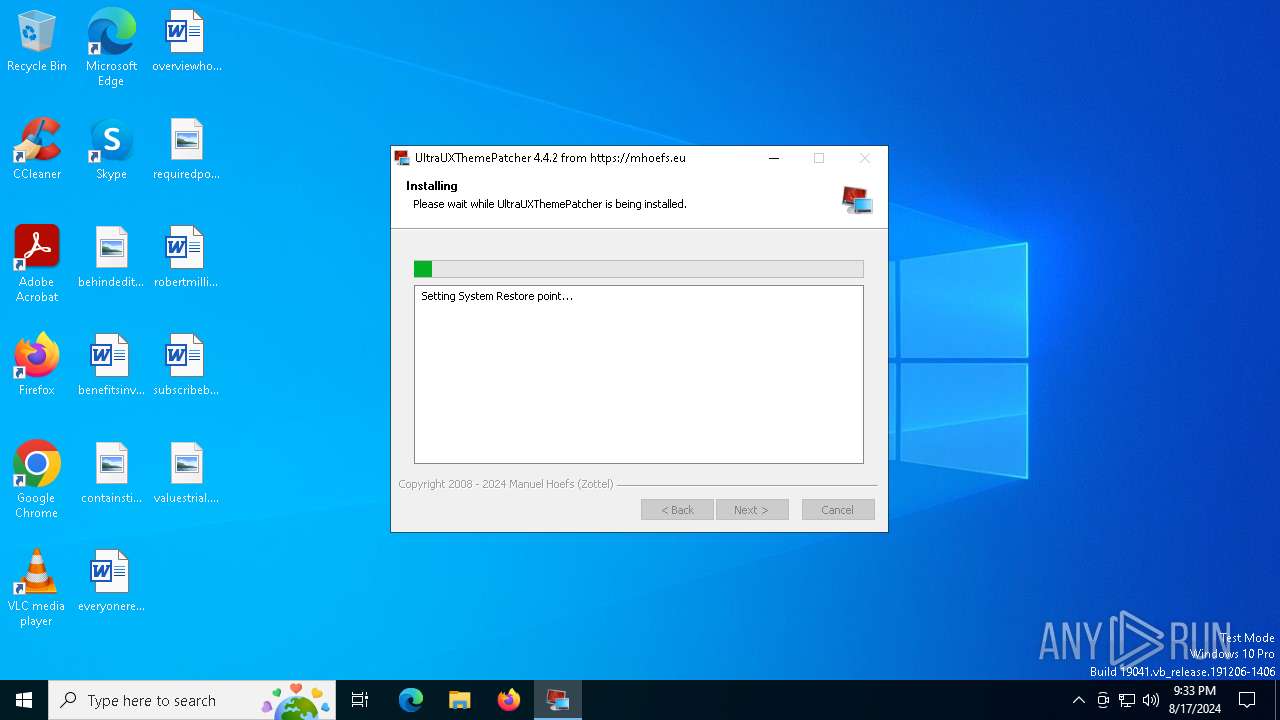
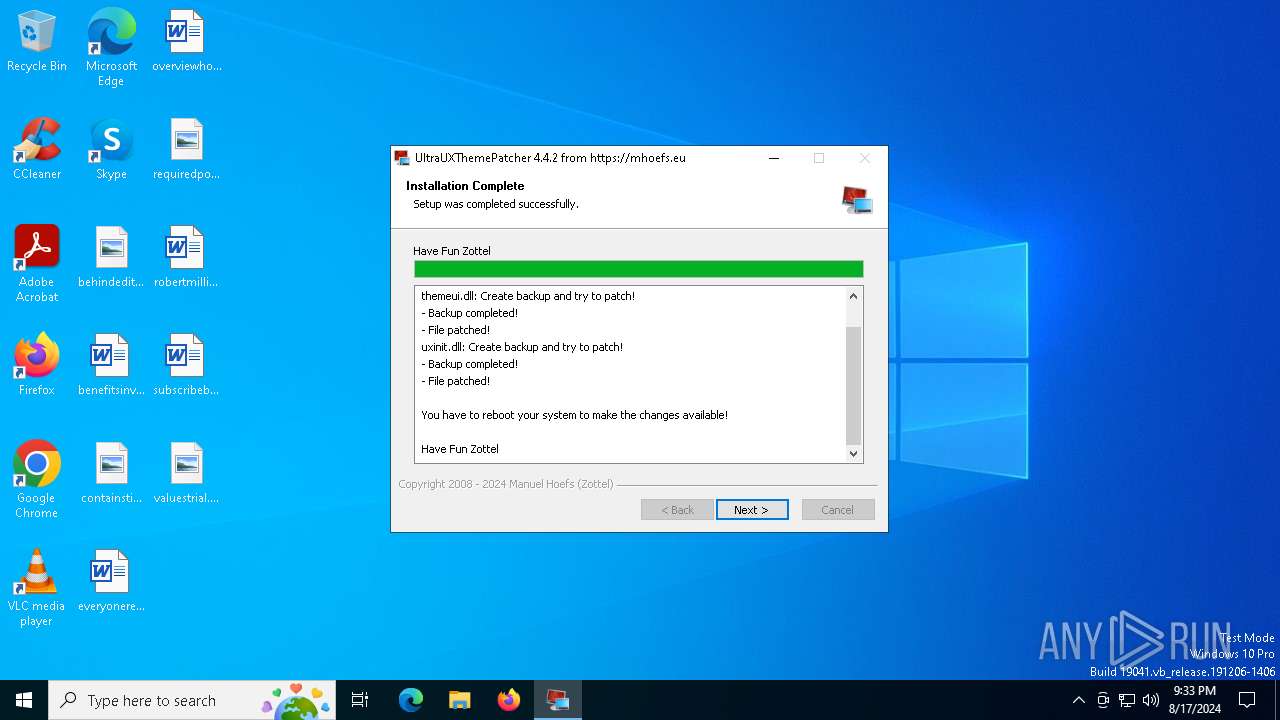
| File name: | UltraUXThemePatcher_4.4.2.exe |
| Full analysis: | https://app.any.run/tasks/683e8bc0-7175-4efc-bf27-84bc24336ba9 |
| Verdict: | Malicious activity |
| Analysis date: | August 17, 2024, 21:32:49 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows, Nullsoft Installer self-extracting archive |
| MD5: | 446DB12350E471737925DC25E82EB21C |
| SHA1: | 5082BA44DCCC26F278ADACAF5E8BF5D4424666AA |
| SHA256: | 48FB5C4C2A2E6AB49BB10C599D69AB614D2C69F91854E00ADAF5508D9EE14F7A |
| SSDEEP: | 3072:0iIRsGru9d9kqDCu0JL913ZjtRxzQjW3BqAouw/AEpT18+8:XGsHwIC5Jp1Nx5BqA/G5pi+8 |
MALICIOUS
No malicious indicators.SUSPICIOUS
Drops the executable file immediately after the start
- UltraUXThemePatcher_4.4.2.exe (PID: 6484)
Malware-specific behavior (creating "System.dll" in Temp)
- UltraUXThemePatcher_4.4.2.exe (PID: 6484)
Executable content was dropped or overwritten
- UltraUXThemePatcher_4.4.2.exe (PID: 6484)
Executes as Windows Service
- VSSVC.exe (PID: 2436)
Reads security settings of Internet Explorer
- UltraUXThemePatcher_4.4.2.exe (PID: 6484)
Searches for installed software
- dllhost.exe (PID: 5484)
Process drops legitimate windows executable
- UltraUXThemePatcher_4.4.2.exe (PID: 6484)
Reads the date of Windows installation
- UltraUXThemePatcher_4.4.2.exe (PID: 6484)
Takes ownership (TAKEOWN.EXE)
- UltraUXThemePatcher_4.4.2.exe (PID: 6484)
Uses ICACLS.EXE to modify access control lists
- UltraUXThemePatcher_4.4.2.exe (PID: 6484)
Creates a software uninstall entry
- UltraUXThemePatcher_4.4.2.exe (PID: 6484)
INFO
Reads Environment values
- UltraUXThemePatcher_4.4.2.exe (PID: 6484)
Create files in a temporary directory
- UltraUXThemePatcher_4.4.2.exe (PID: 6484)
Process checks computer location settings
- UltraUXThemePatcher_4.4.2.exe (PID: 6484)
Checks supported languages
- UltraUXThemePatcher_4.4.2.exe (PID: 6484)
Creates files in the program directory
- UltraUXThemePatcher_4.4.2.exe (PID: 6484)
Creates files or folders in the user directory
- UltraUXThemePatcher_4.4.2.exe (PID: 6484)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win32 Executable MS Visual C++ (generic) (67.4) |
|---|---|---|
| .dll | | | Win32 Dynamic Link Library (generic) (14.2) |
| .exe | | | Win32 Executable (generic) (9.7) |
| .exe | | | Generic Win/DOS Executable (4.3) |
| .exe | | | DOS Executable Generic (4.3) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2024:03:30 16:55:19+00:00 |
| ImageFileCharacteristics: | No relocs, Executable, No line numbers, No symbols, 32-bit |
| PEType: | PE32 |
| LinkerVersion: | 6 |
| CodeSize: | 26624 |
| InitializedDataSize: | 139776 |
| UninitializedDataSize: | 2048 |
| EntryPoint: | 0x3665 |
| OSVersion: | 4 |
| ImageVersion: | 6 |
| SubsystemVersion: | 4 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 4.4.2.0 |
| ProductVersionNumber: | 4.4.2.0 |
| FileFlagsMask: | 0x0000 |
| FileFlags: | (none) |
| FileOS: | Win32 |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | English (U.S.) |
| CharacterSet: | Unicode |
| Comments: | UltraUXThemePatcher modifies your system file(s) to use 3rd party themes |
| CompanyName: | Manuel Hoefs (Zottel) |
| FileDescription: | Windows UltraUXThemePatcher |
| FileVersion: | 4.4.2.0 |
| InternalName: | UltraUXThemePatcher_4.4.2 |
| LegalCopyright: | 2008 - 2024 Manuel Hoefs (Zottel) |
| LegalTrademarks: | UltraUXThemePatcher created by Manuel Hoefs (Zottel) |
| OriginalFileName: | UltraUXThemePatcher_4.4.2.exe |
| ProductName: | UltraUXThemePatcher |
| ProductVersion: | 4.4.2.0 |
| Website: | https://mhoefs.eu |
Total processes
148
Monitored processes
18
Malicious processes
2
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1184 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | takeown.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1700 | "C:\WINDOWS\system32\icacls.exe" "C:\WINDOWS\system32\uxinit.dll" /grant admin:F | C:\Windows\System32\icacls.exe | — | UltraUXThemePatcher_4.4.2.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2436 | C:\WINDOWS\system32\vssvc.exe | C:\Windows\System32\VSSVC.exe | — | services.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Microsoft® Volume Shadow Copy Service Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4292 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | icacls.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5064 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | takeown.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5084 | "C:\WINDOWS\system32\icacls.exe" "C:\WINDOWS\system32\themeui.dll" /grant admin:F | C:\Windows\System32\icacls.exe | — | UltraUXThemePatcher_4.4.2.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5400 | "C:\WINDOWS\system32\takeown.exe" /f "C:\WINDOWS\system32\uxinit.dll" | C:\Windows\System32\takeown.exe | — | UltraUXThemePatcher_4.4.2.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Takes ownership of a file Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5468 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | takeown.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5484 | C:\WINDOWS\system32\DllHost.exe /Processid:{F32D97DF-E3E5-4CB9-9E3E-0EB5B4E49801} | C:\Windows\System32\dllhost.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: COM Surrogate Exit code: 0 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5940 | "C:\WINDOWS\system32\takeown.exe" /f "C:\WINDOWS\system32\uxinit.dll" | C:\Windows\System32\takeown.exe | — | UltraUXThemePatcher_4.4.2.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Takes ownership of a file Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
3 429
Read events
3 192
Write events
217
Delete events
20
Modification events
| (PID) Process: | (5484) dllhost.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\SPP |
| Operation: | write | Name: | SppGetSnapshots (Enter) |
Value: 4800000000000000976FBA0DEDF0DA016C15000078180000D20700000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (6484) UltraUXThemePatcher_4.4.2.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\SystemRestore |
| Operation: | write | Name: | SrCreateRp (Enter) |
Value: 4000000000000000976FBA0DEDF0DA0154190000FC1B0000D5070000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (5484) dllhost.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\SPP |
| Operation: | write | Name: | SppGetSnapshots (Leave) |
Value: 48000000000000003E54040EEDF0DA016C15000078180000D20700000100000000000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (5484) dllhost.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\SPP |
| Operation: | write | Name: | SppEnumGroups (Enter) |
Value: 48000000000000003E54040EEDF0DA016C15000078180000D10700000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (5484) dllhost.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\SPP |
| Operation: | write | Name: | SppEnumGroups (Leave) |
Value: 4800000000000000551C090EEDF0DA016C15000078180000D10700000100000000000000010000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (5484) dllhost.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\SPP |
| Operation: | write | Name: | SppCreate (Enter) |
Value: 48000000000000006DE30D0EEDF0DA016C15000078180000D00700000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (5484) dllhost.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\SPP |
| Operation: | write | Name: | LastIndex |
Value: 11 | |||
| (PID) Process: | (5484) dllhost.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\SPP |
| Operation: | write | Name: | SppGatherWriterMetadata (Enter) |
Value: 48000000000000007DDD890EEDF0DA016C15000078180000D30700000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (5484) dllhost.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\VssapiPublisher |
| Operation: | write | Name: | IDENTIFY (Enter) |
Value: 480000000000000097418C0EEDF0DA016C150000C0180000E8030000010000000000000000000000C27753AA888FD947AC24D575D899672800000000000000000000000000000000 | |||
| (PID) Process: | (2436) VSSVC.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\ASR Writer |
| Operation: | write | Name: | IDENTIFY (Enter) |
Value: 4800000000000000DED1950EEDF0DA018409000010190000E80300000100000001000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
Executable files
13
Suspicious files
4
Text files
3
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 5484 | dllhost.exe | C:\System Volume Information\SPP\metadata-2 | — | |
MD5:— | SHA256:— | |||
| 6484 | UltraUXThemePatcher_4.4.2.exe | C:\Users\admin\AppData\Local\Temp\nsz54A5.tmp\System.dll | executable | |
MD5:192639861E3DC2DC5C08BB8F8C7260D5 | SHA256:23D618A0293C78CE00F7C6E6DD8B8923621DA7DD1F63A070163EF4C0EC3033D6 | |||
| 6484 | UltraUXThemePatcher_4.4.2.exe | C:\Users\admin\AppData\Local\Temp\nsz54A5.tmp\nsisFile.dll | executable | |
MD5:B7D0D765C151D235165823B48554E442 | SHA256:A820A32E5CE89E3E336AFC71AA1BF42A357EC542C2BC6E50C6255C1333812587 | |||
| 6484 | UltraUXThemePatcher_4.4.2.exe | C:\Users\admin\AppData\Local\Temp\nsz54A5.tmp\nsDialogs.dll | executable | |
MD5:B7D61F3F56ABF7B7FF0D4E7DA3AD783D | SHA256:89A82C4849C21DFE765052681E1FAD02D2D7B13C8B5075880C52423DCA72A912 | |||
| 5484 | dllhost.exe | C:\System Volume Information\SPP\snapshot-2 | binary | |
MD5:1AE0EF4C14EC01AEF62D5BDAACB2F183 | SHA256:C0599D52A9C86C8E00F7167D64AC5D33B4F08B3EEF2E5F1671D895215D4ED92A | |||
| 6484 | UltraUXThemePatcher_4.4.2.exe | C:\Windows\System32\themeui.dll.new | executable | |
MD5:DD04F37E7E19F9BCBCCE3119D2B30D2F | SHA256:69B401FF2CF6762E18B5665B40CFE2DDC143DCF7DA1C635036844A745918E67D | |||
| 6484 | UltraUXThemePatcher_4.4.2.exe | C:\Windows\System32\themeui.dll.backup | executable | |
MD5:DD04F37E7E19F9BCBCCE3119D2B30D2F | SHA256:69B401FF2CF6762E18B5665B40CFE2DDC143DCF7DA1C635036844A745918E67D | |||
| 6484 | UltraUXThemePatcher_4.4.2.exe | C:\Users\admin\AppData\Local\Temp\nsz54A5.tmp\modern-wizard.bmp | image | |
MD5:5F728E4E6B970DB76C64BE8CA3CAFC87 | SHA256:AEA40659BDB08337064640EA8B4F171881D37456B37B3E2899349AC04F0889C5 | |||
| 5484 | dllhost.exe | C:\System Volume Information\SPP\OnlineMetadataCache\{aa5377c2-8f88-47d9-ac24-d575d8996728}_OnDiskSnapshotProp | binary | |
MD5:1AE0EF4C14EC01AEF62D5BDAACB2F183 | SHA256:C0599D52A9C86C8E00F7167D64AC5D33B4F08B3EEF2E5F1671D895215D4ED92A | |||
| 6484 | UltraUXThemePatcher_4.4.2.exe | C:\Windows\System32\themeui.dll | executable | |
MD5:4F35DDBD4DC36620C3EA7D06E72E03A8 | SHA256:11BD7A8181475226BBB5F094E5B8D5B84501FEA74500CC04D05959DA1D689F94 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
3
TCP/UDP connections
36
DNS requests
15
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
— | — | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
2384 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
6444 | backgroundTaskHost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
2120 | MoUsoCoreWorker.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | unknown |
876 | svchost.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | unknown |
— | — | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | unknown |
— | — | 239.255.255.250:1900 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
3260 | svchost.exe | 40.113.110.67:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
— | — | 40.126.32.74:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
— | — | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
1884 | svchost.exe | 40.126.32.74:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
876 | svchost.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
arc.msn.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
go.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |