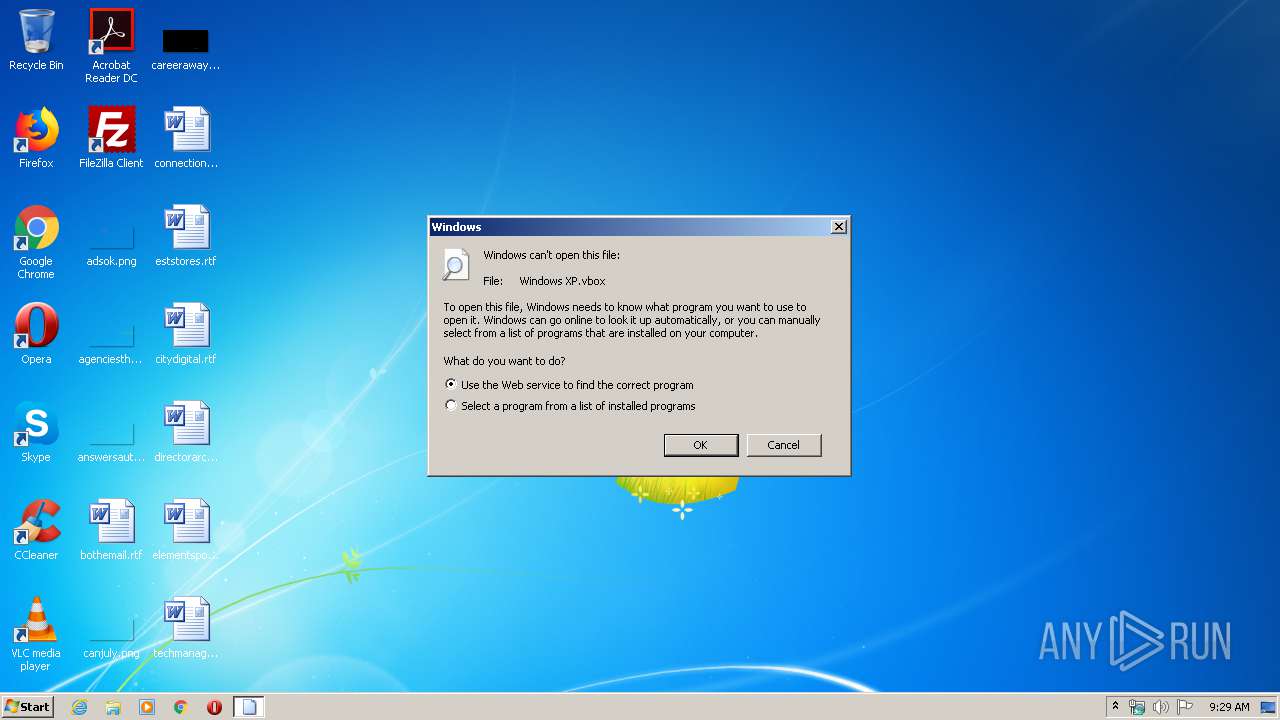
| File name: | Windows XP.vbox |
| Full analysis: | https://app.any.run/tasks/f441a2a5-a79f-44c6-b448-bbf29182154e |
| Verdict: | Malicious activity |
| Analysis date: | April 15, 2020, 08:29:40 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | text/xml |
| File info: | XML 1.0 document, ASCII text |
| MD5: | 01135BC0EBD0E127953C1B7D8598A013 |
| SHA1: | 1AE6B871457C138DCBF7E066CDC125E83FE09DD7 |
| SHA256: | 48FB32E2D58C818B348D7AF8815ED4622D20C1AA8D93DFF1CFD394600C5059E5 |
| SSDEEP: | 192:e2+5FYlCbrrXyKiZGkdsuxOZXg5qCUrd7MmC/kVBsz:e2EF/DuxOi5C7MmC/b |
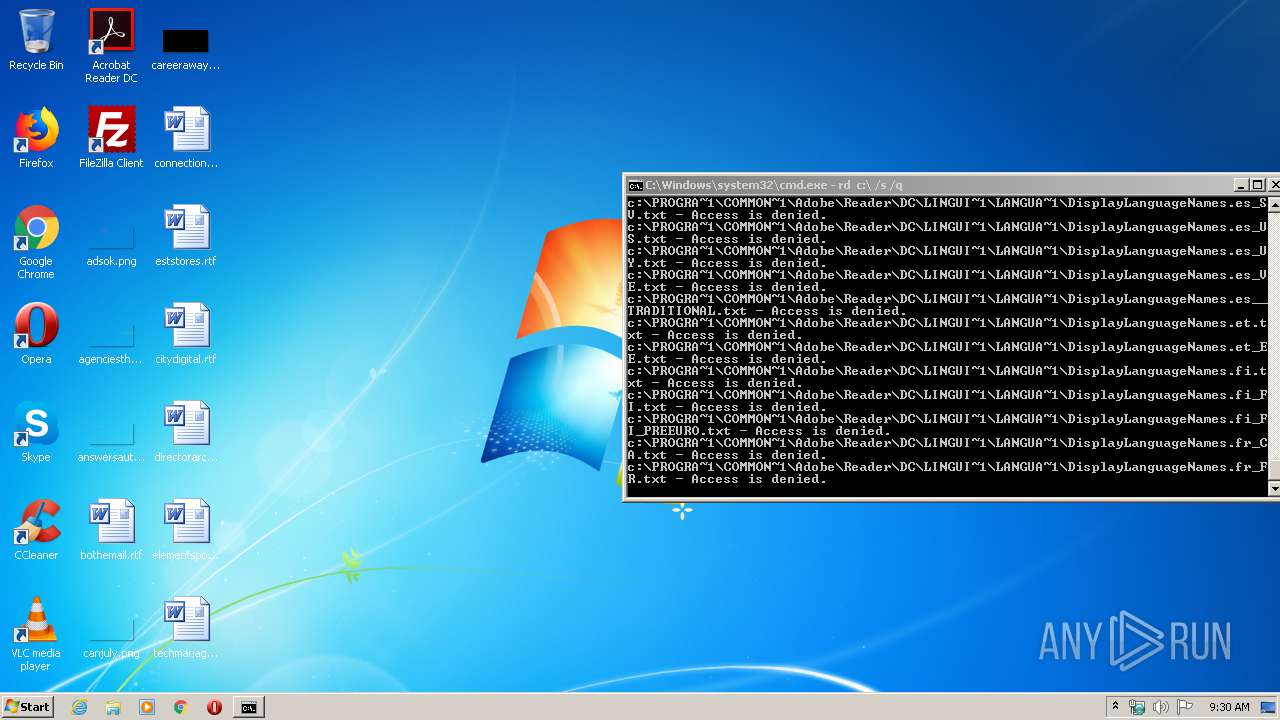
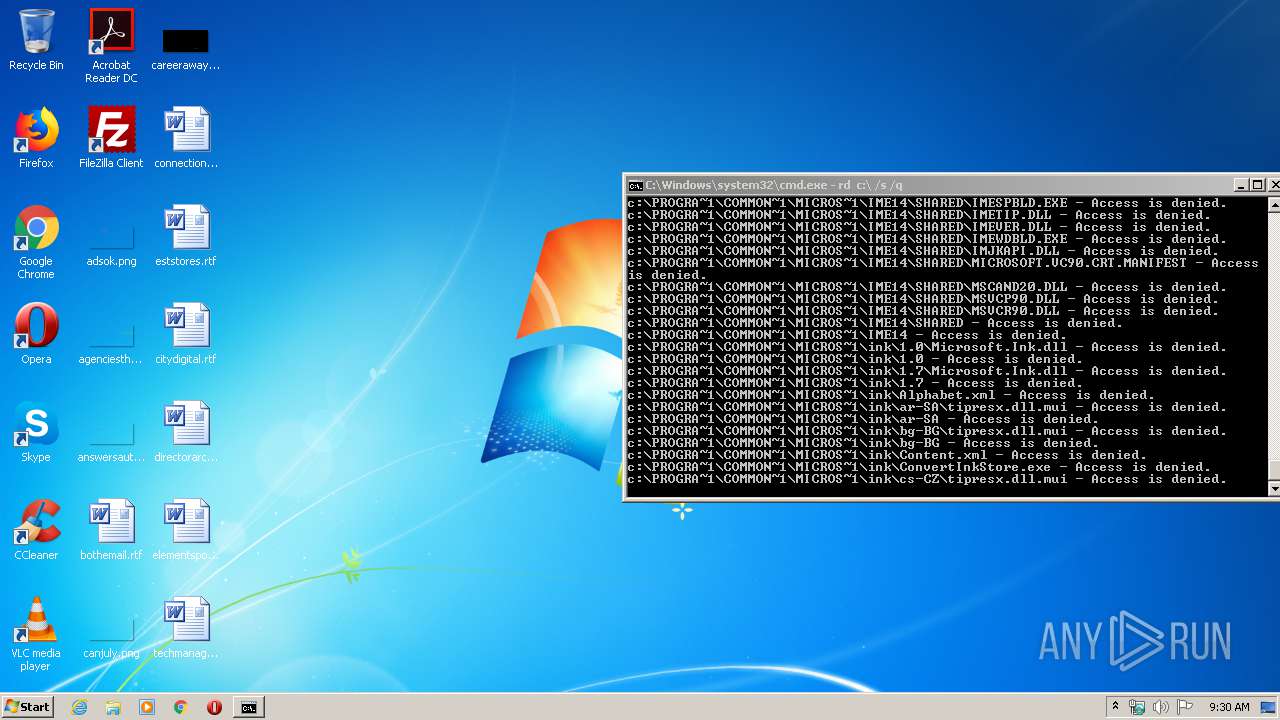
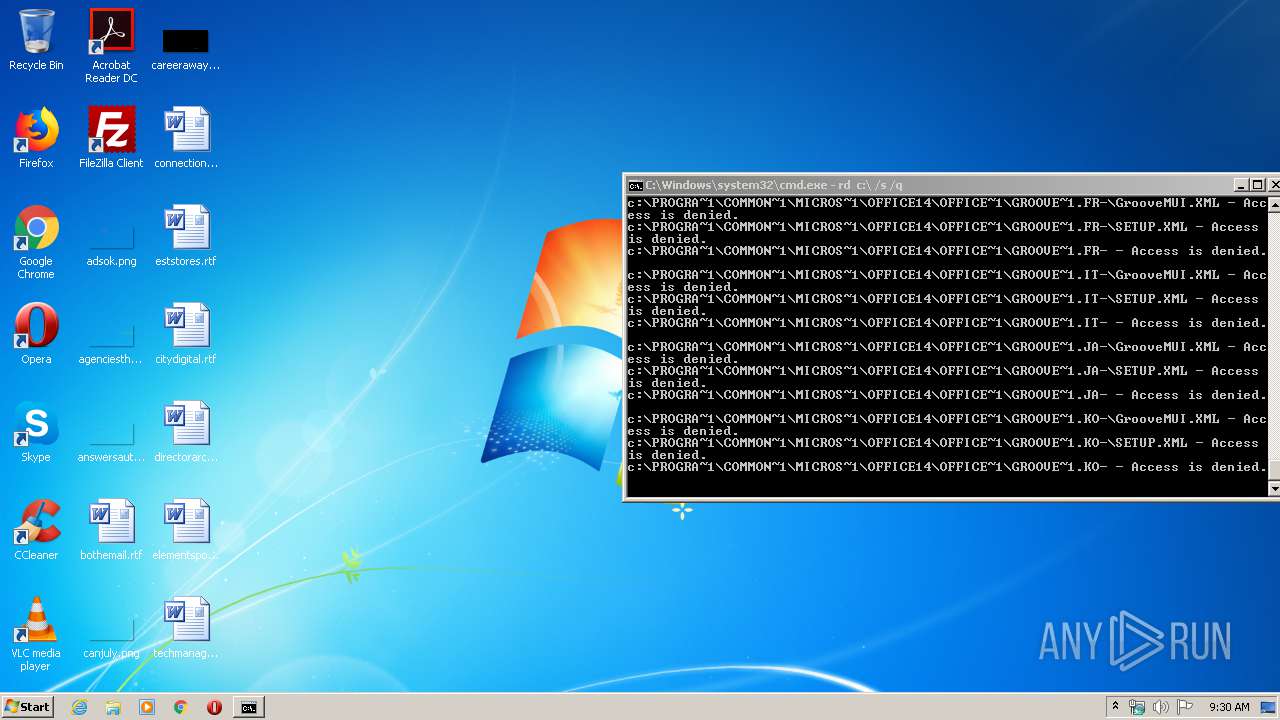
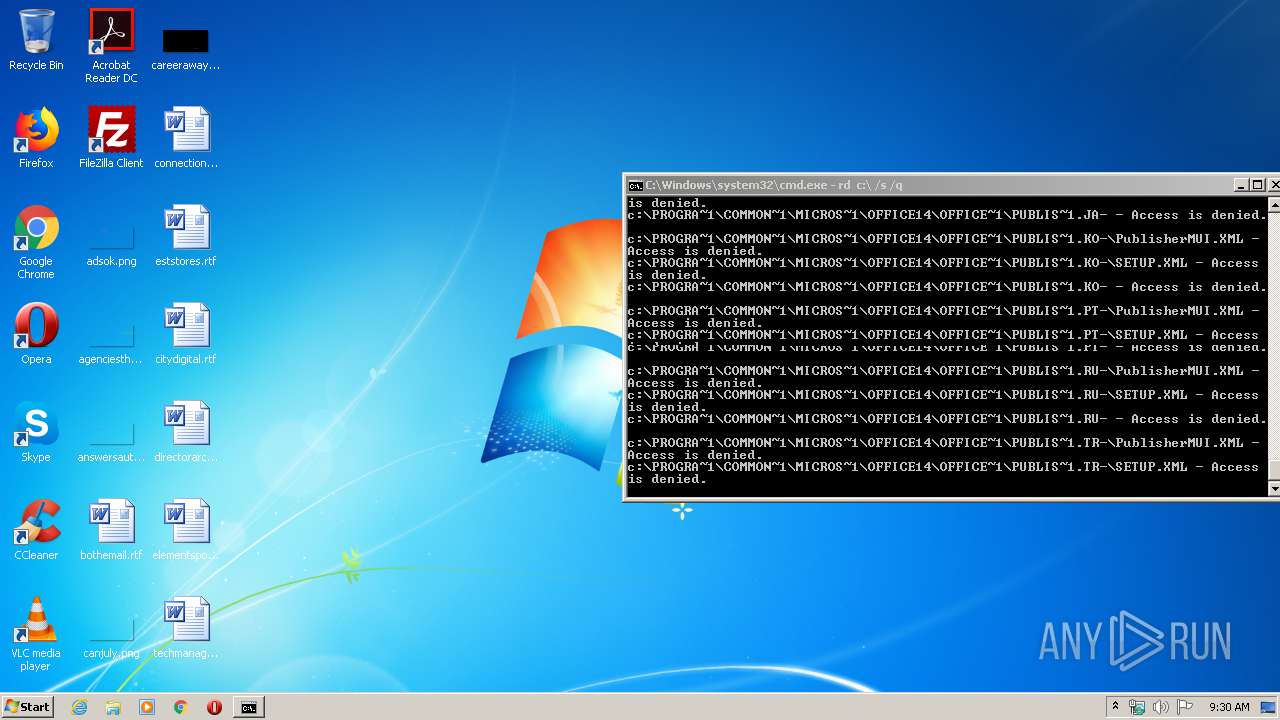
MALICIOUS
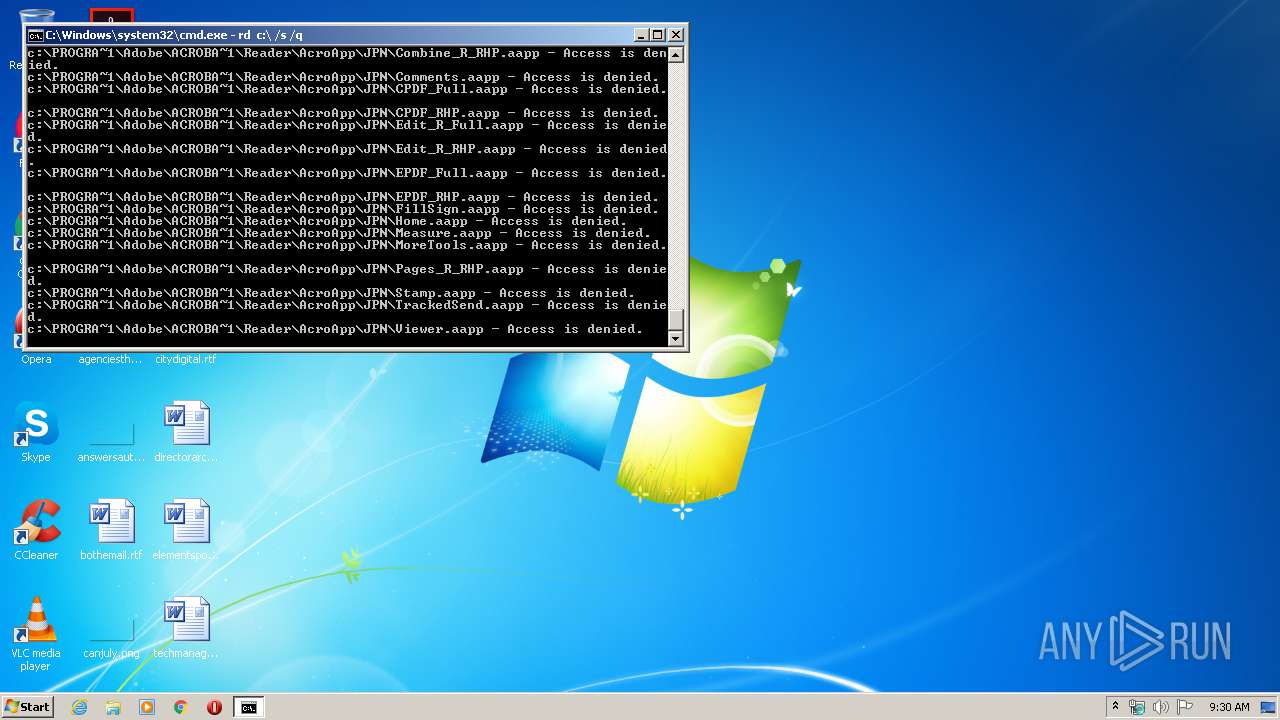
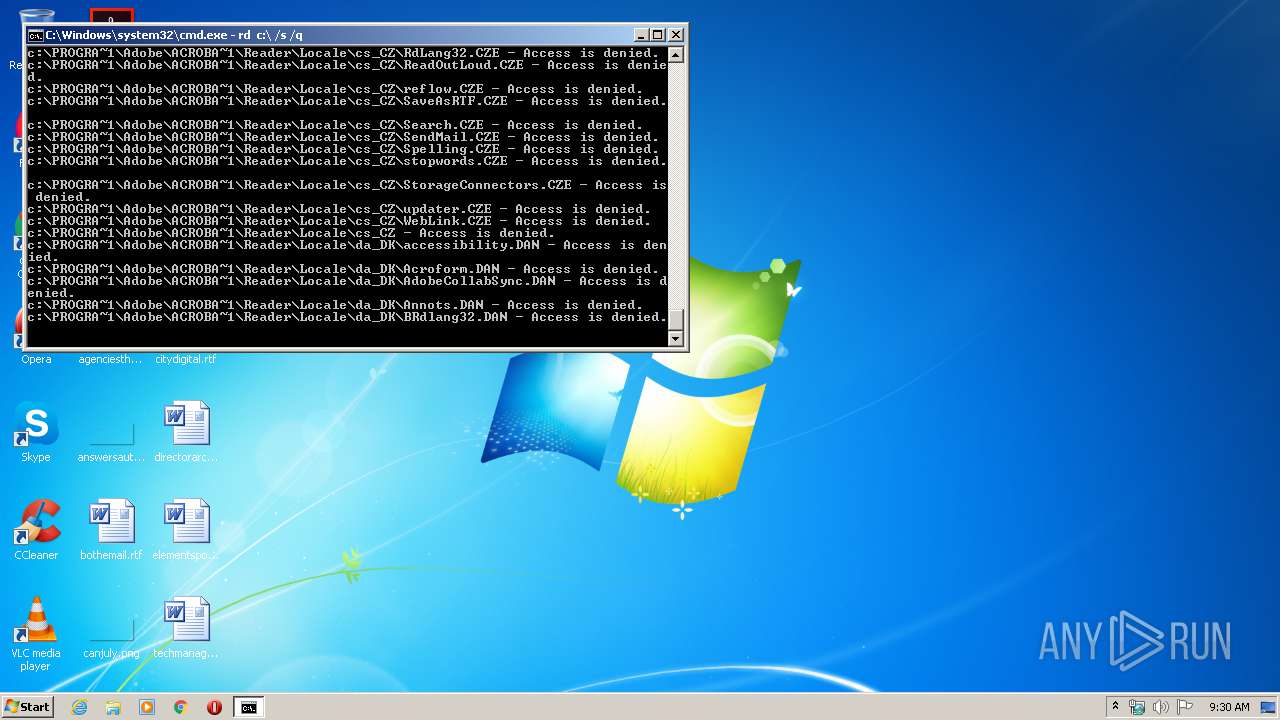
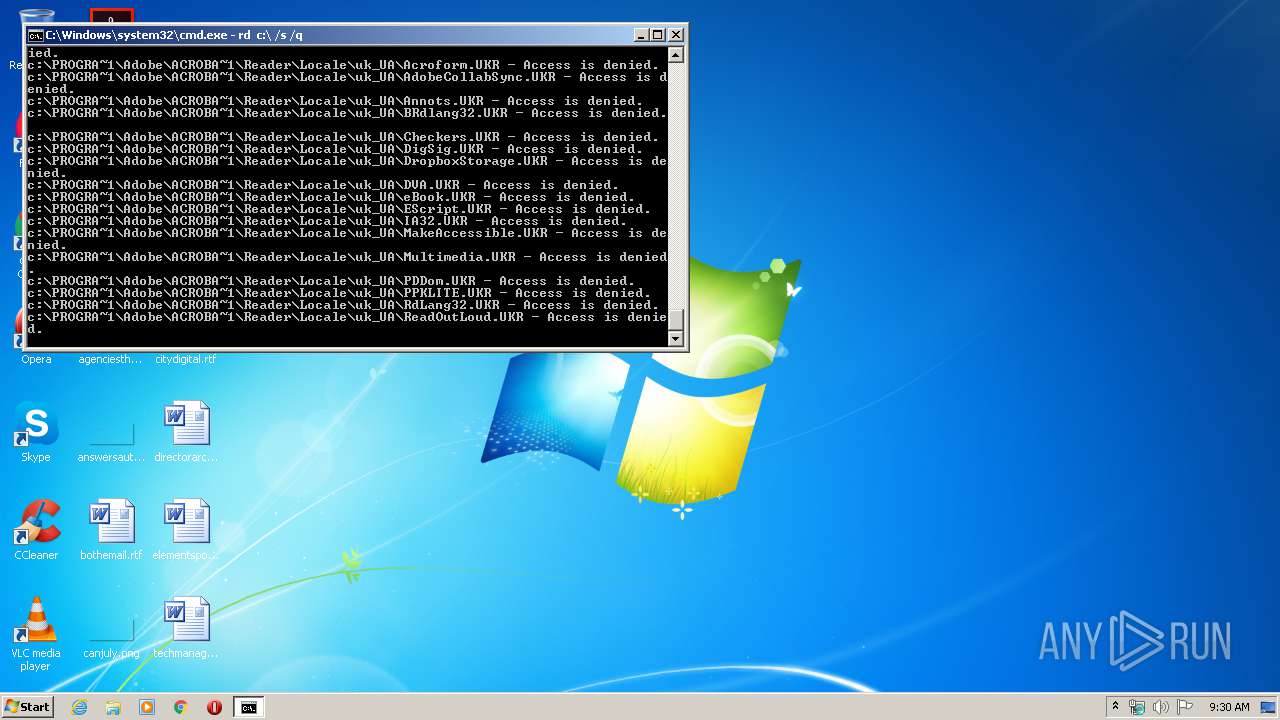
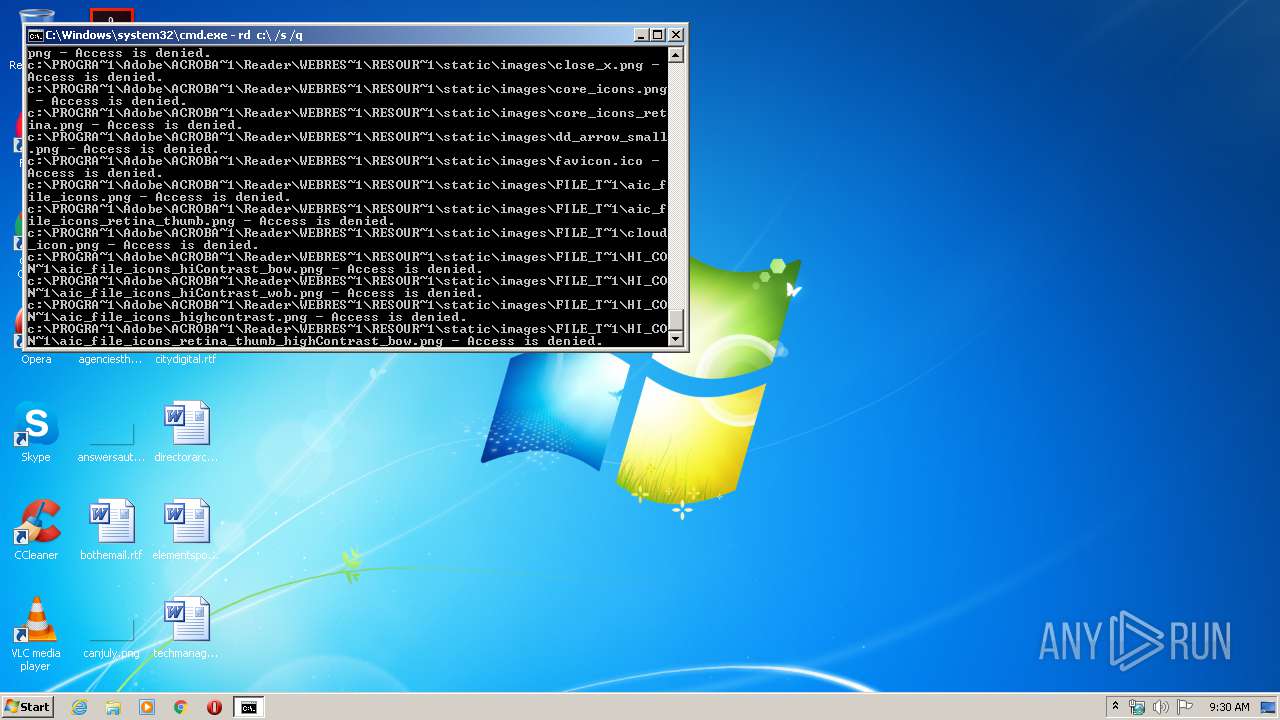
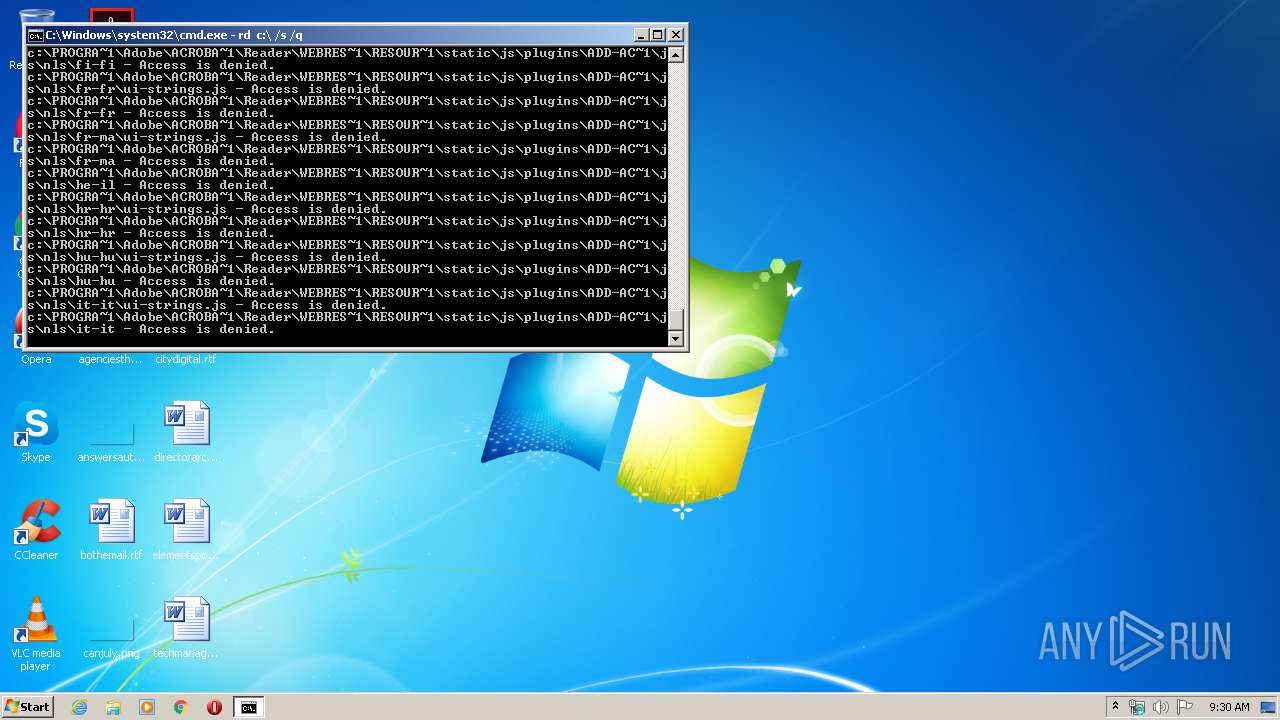
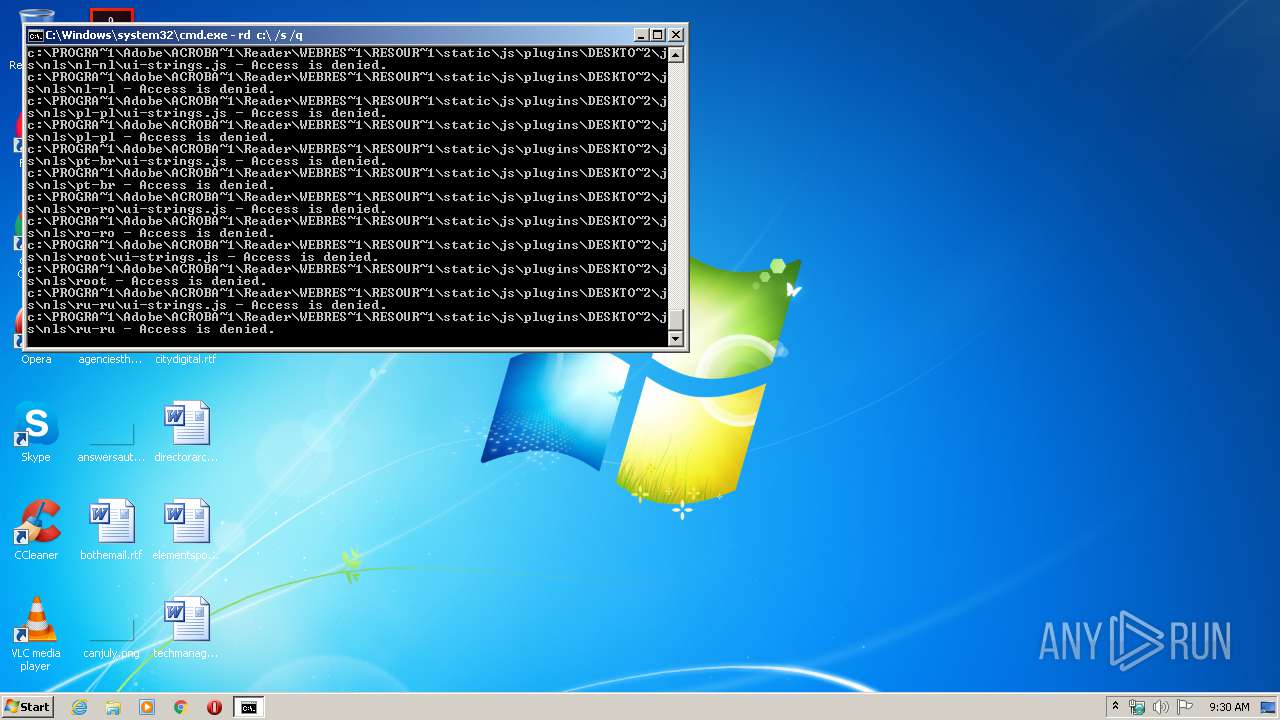
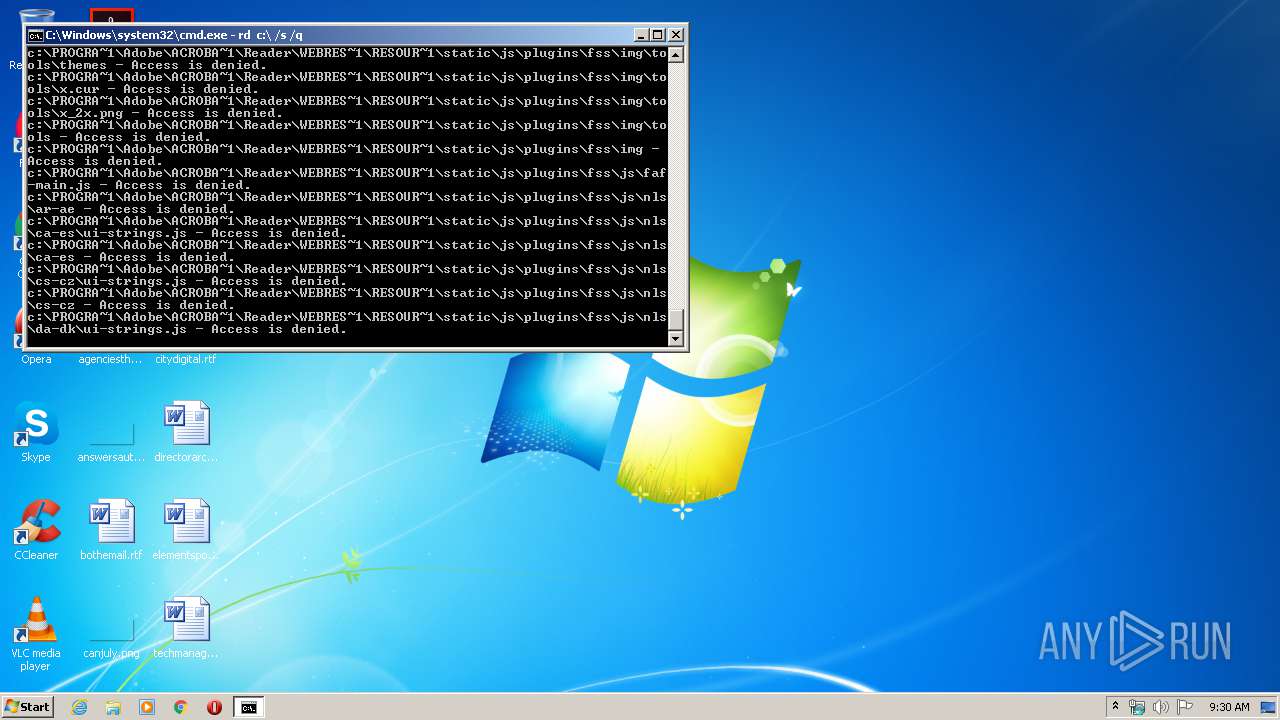
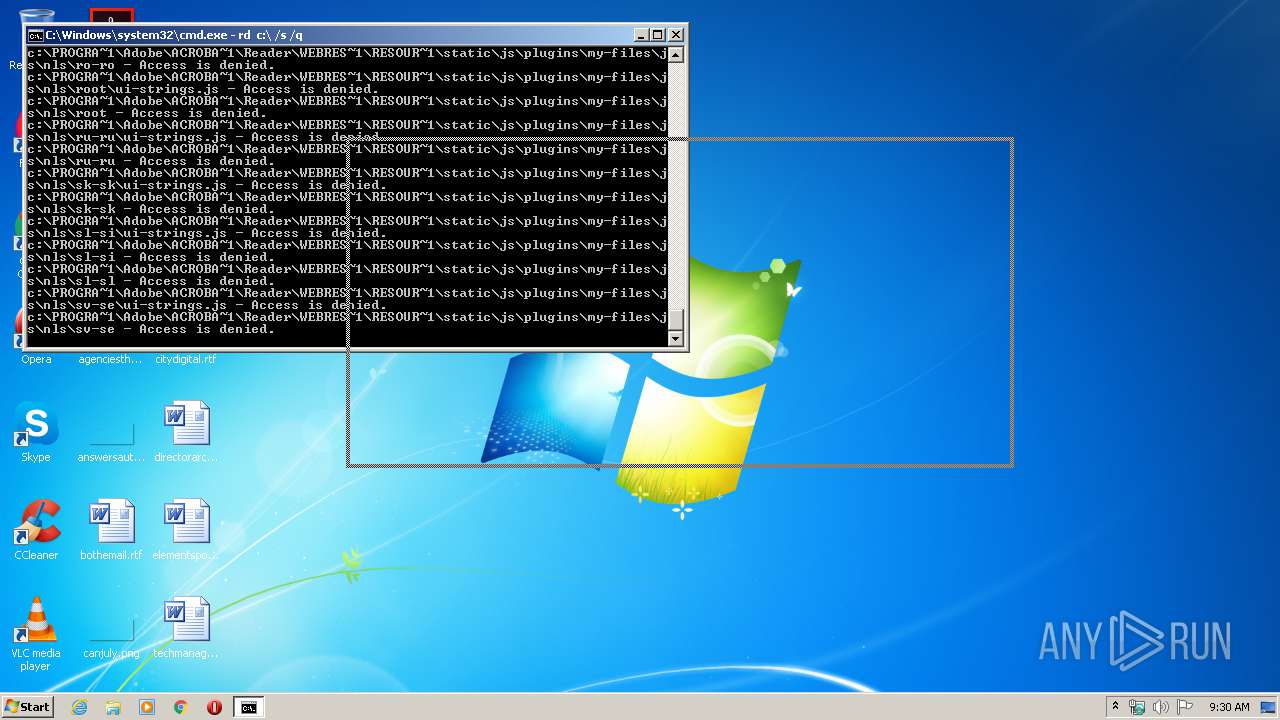
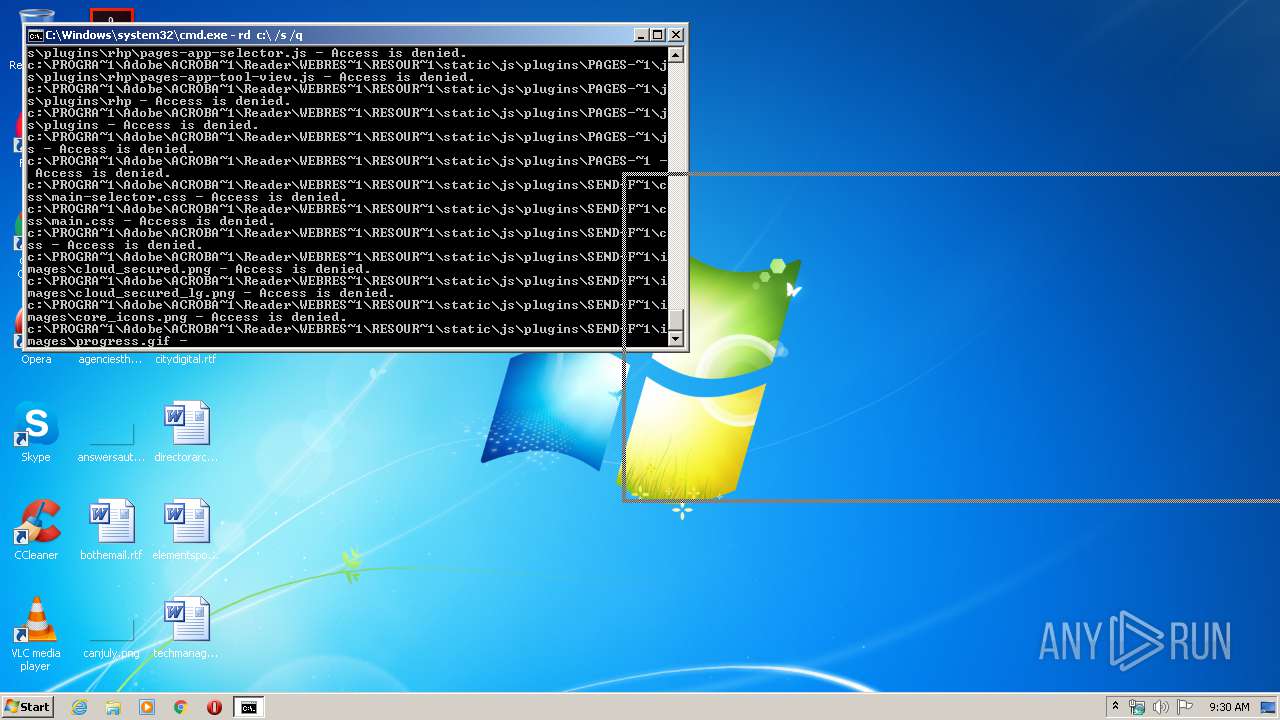
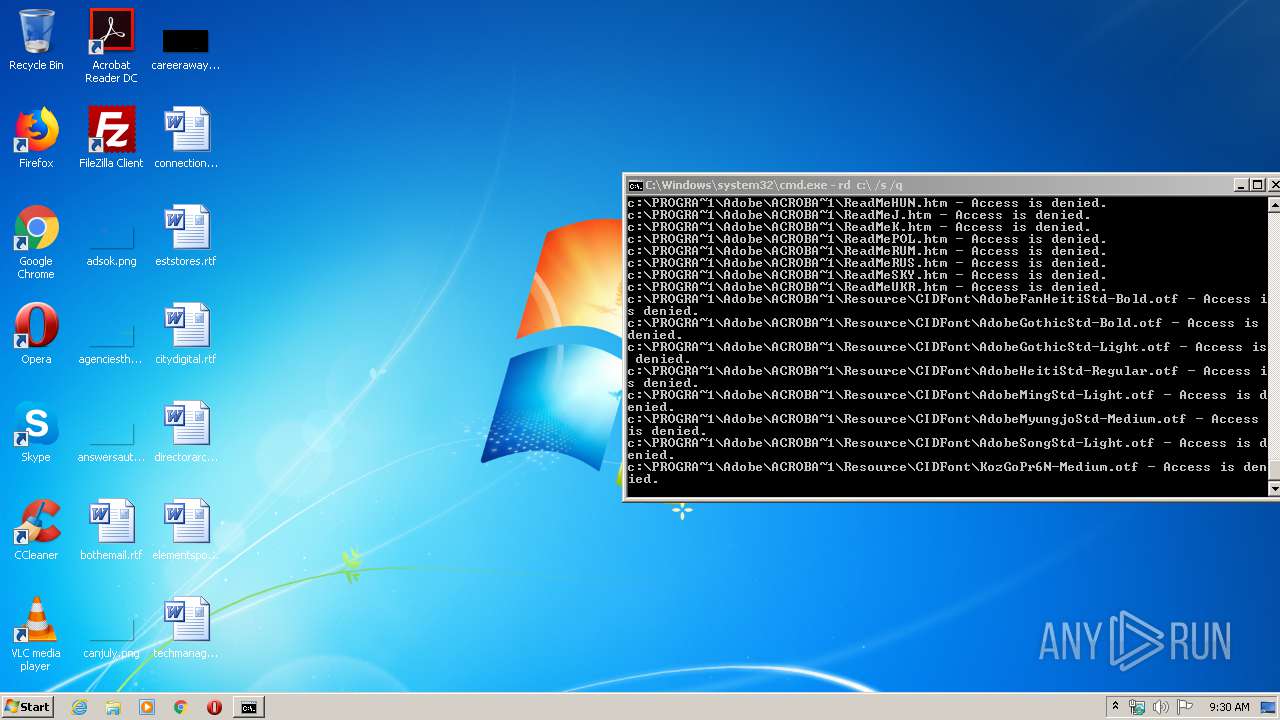
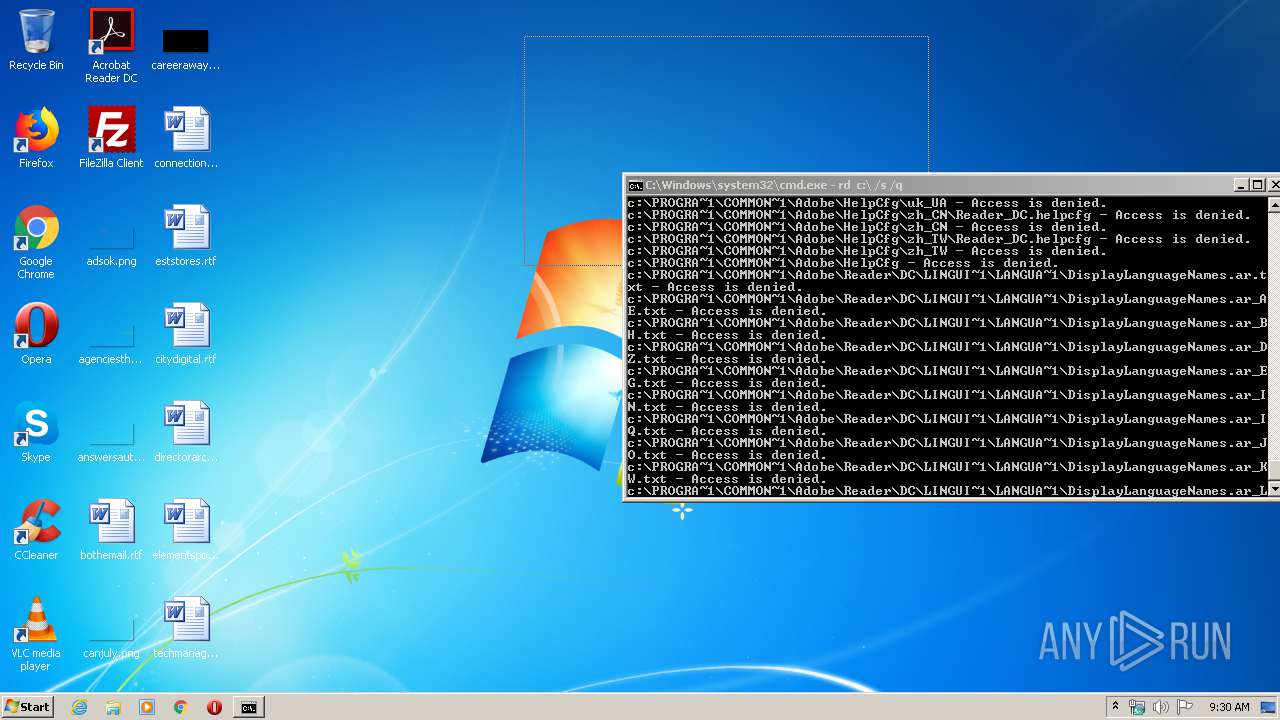
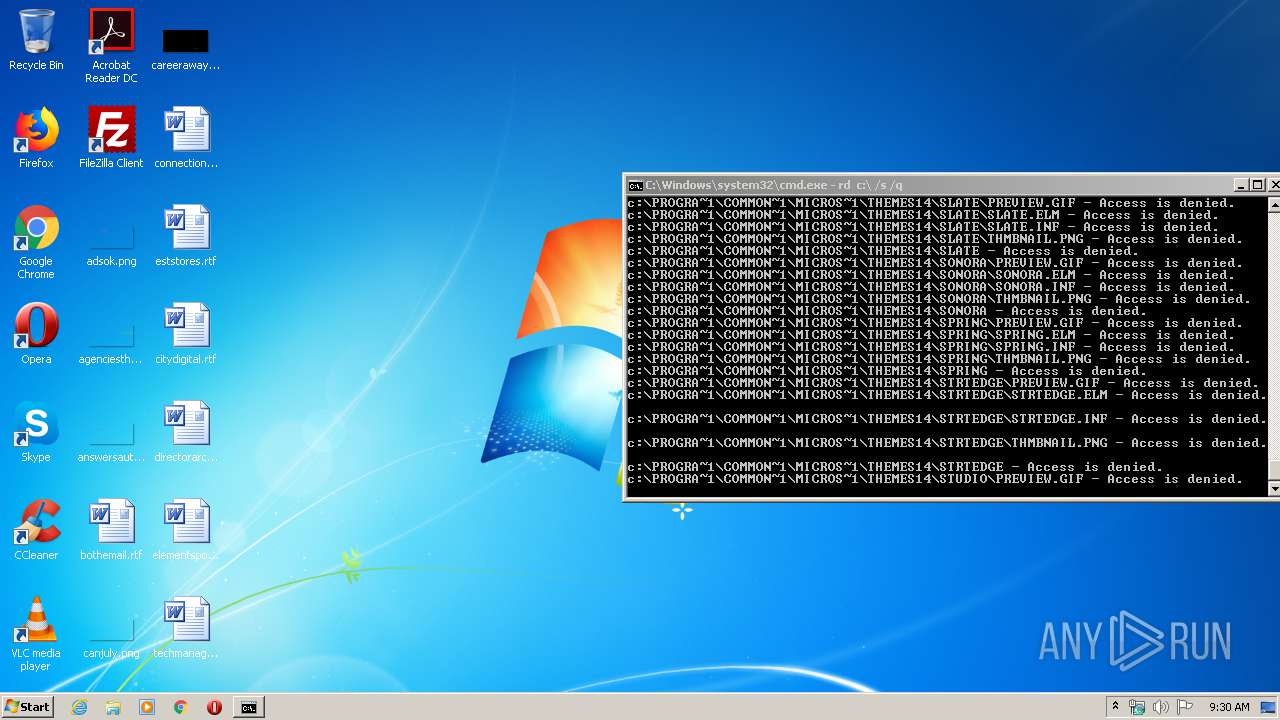
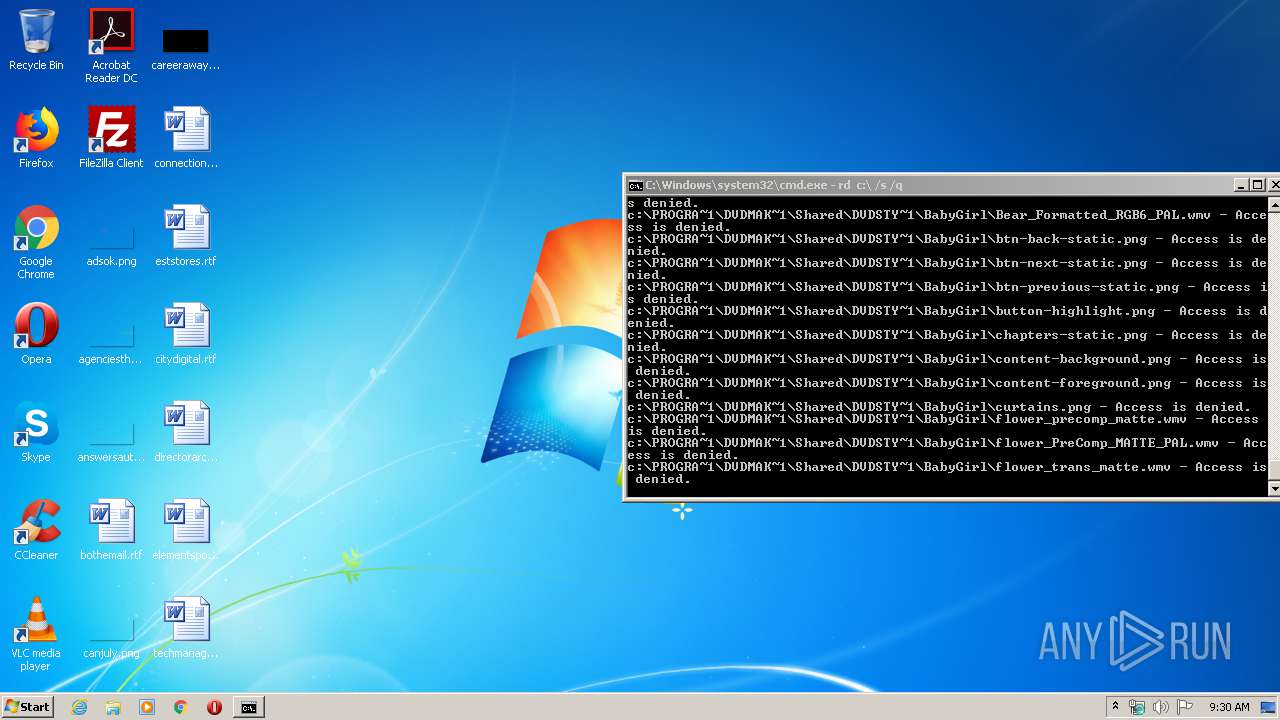
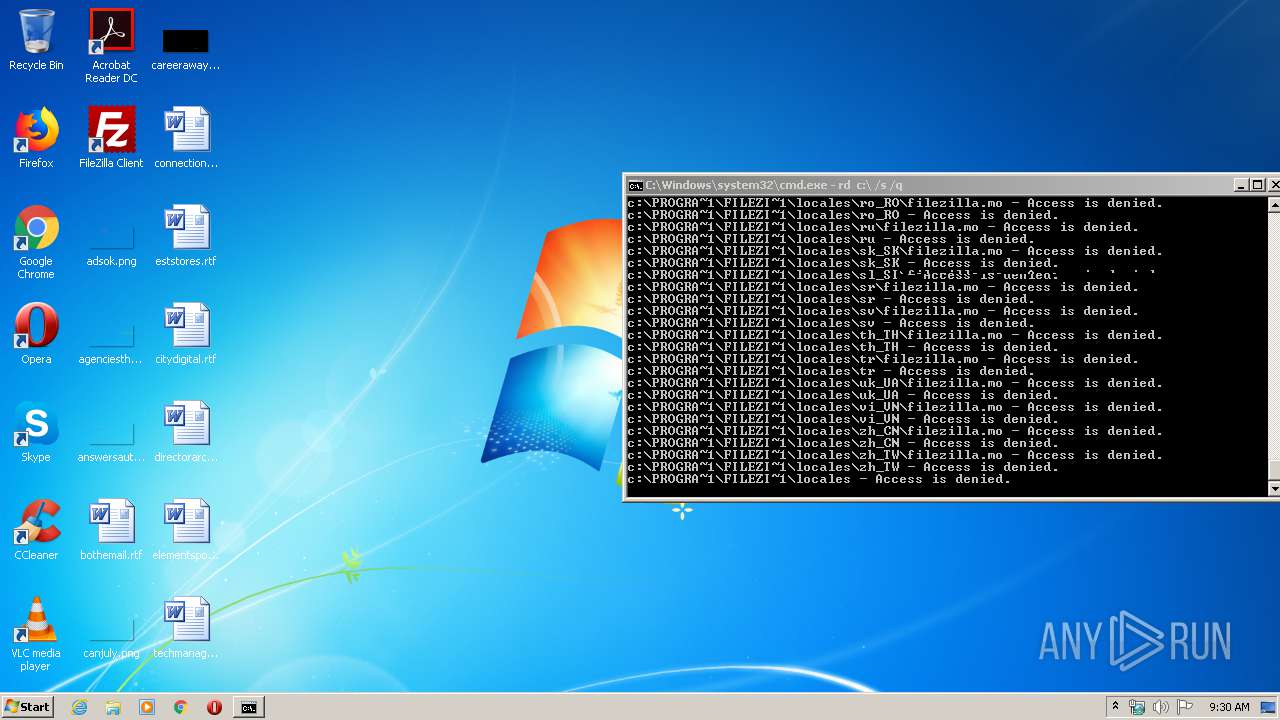
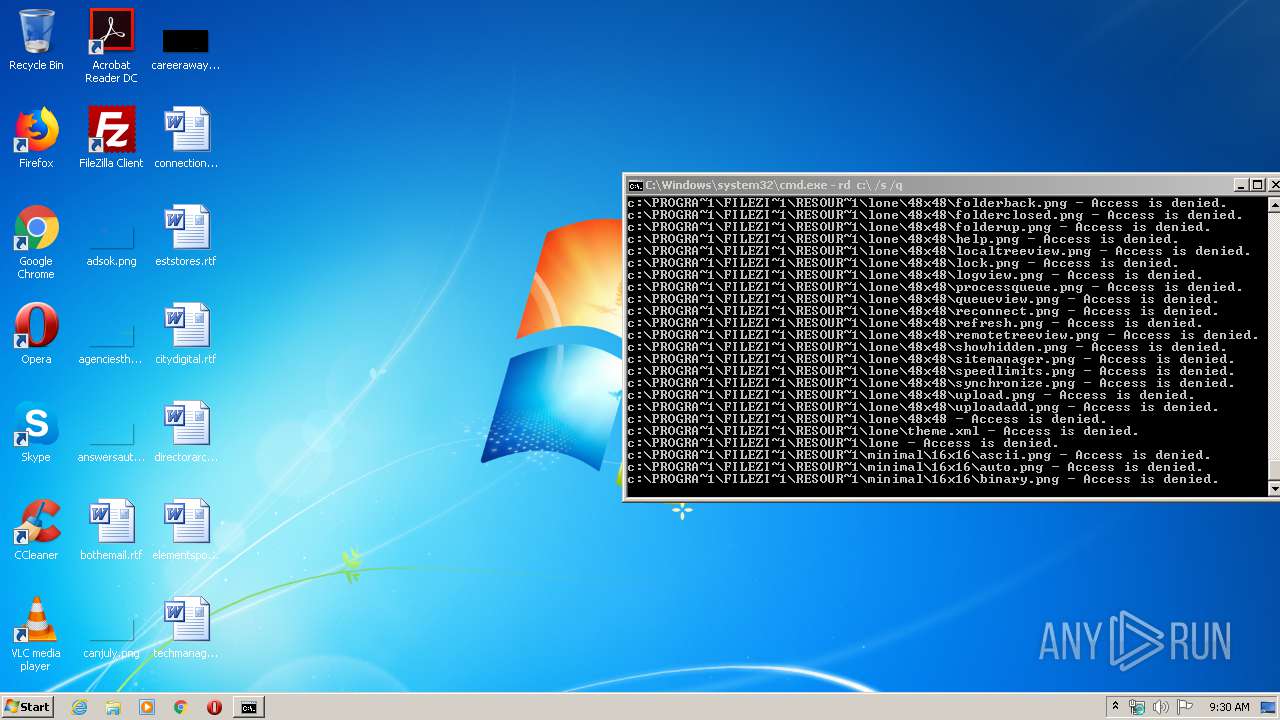
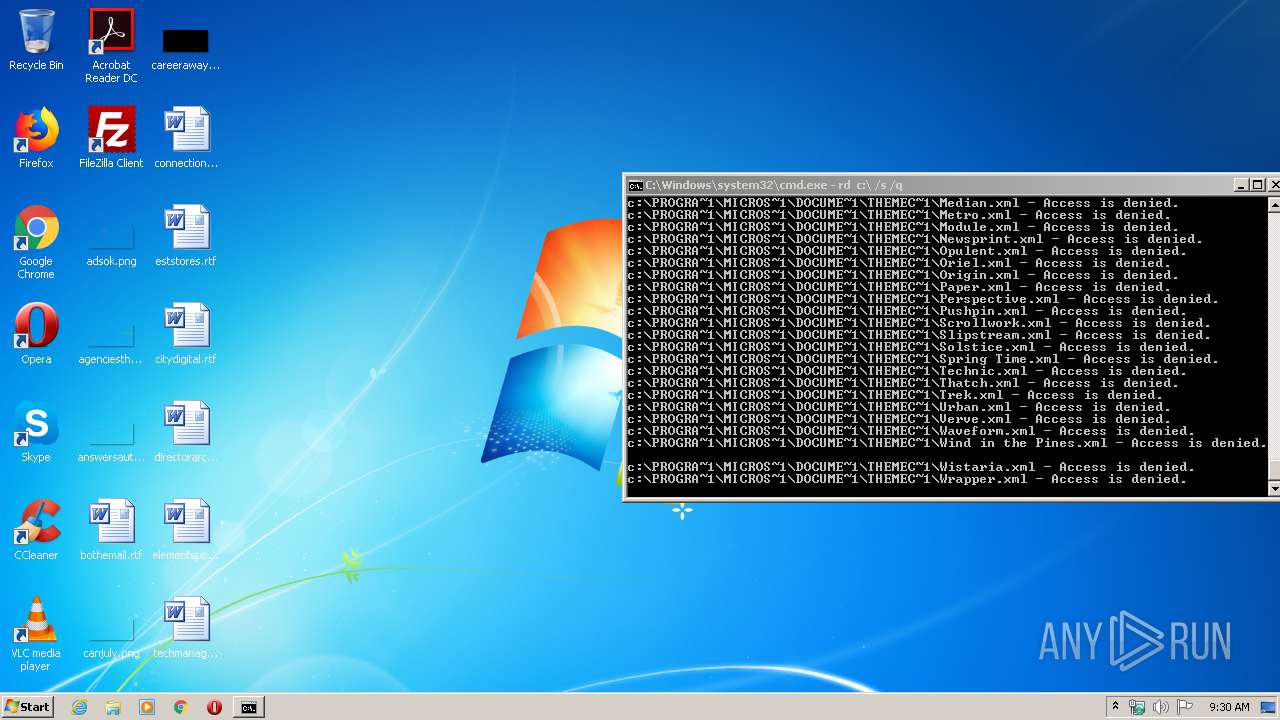
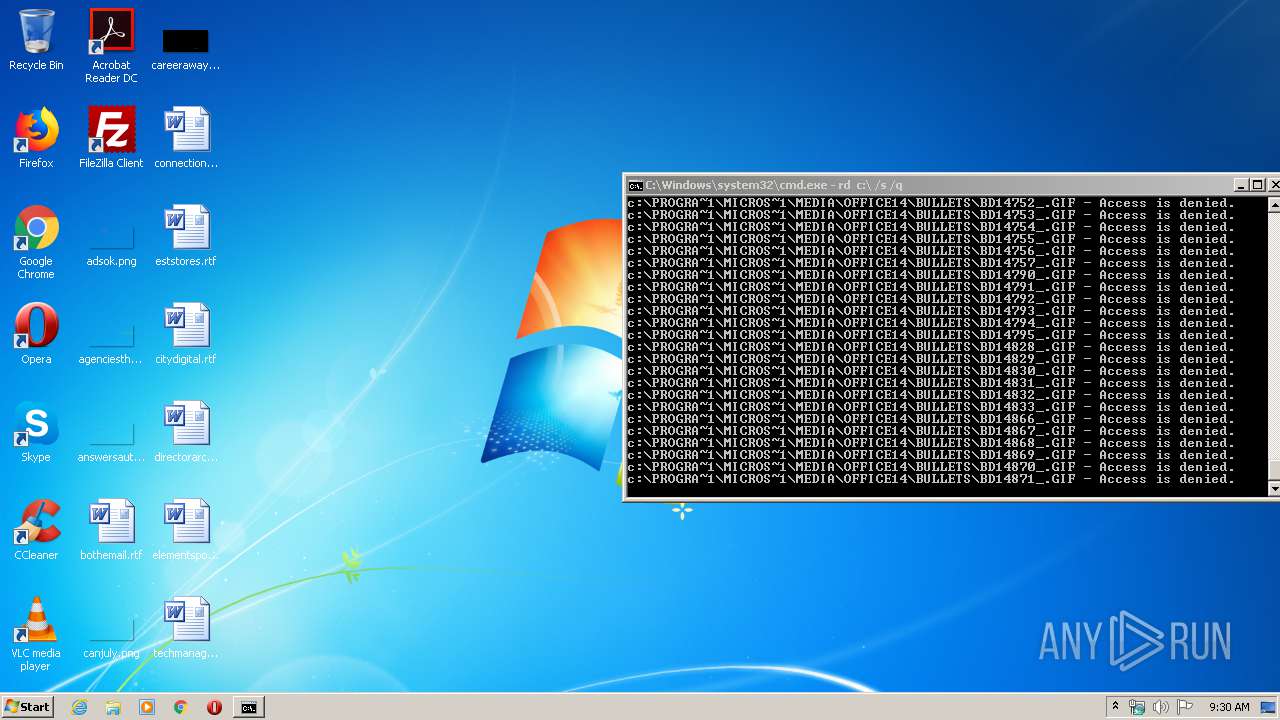
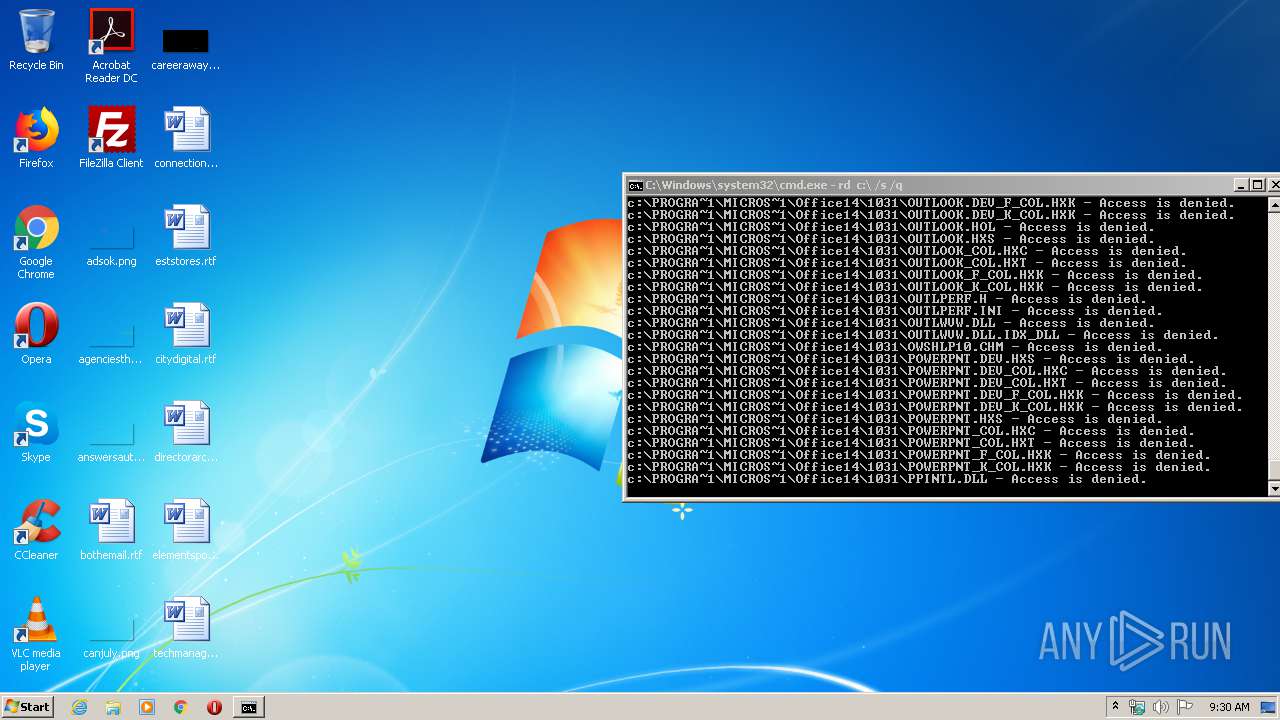
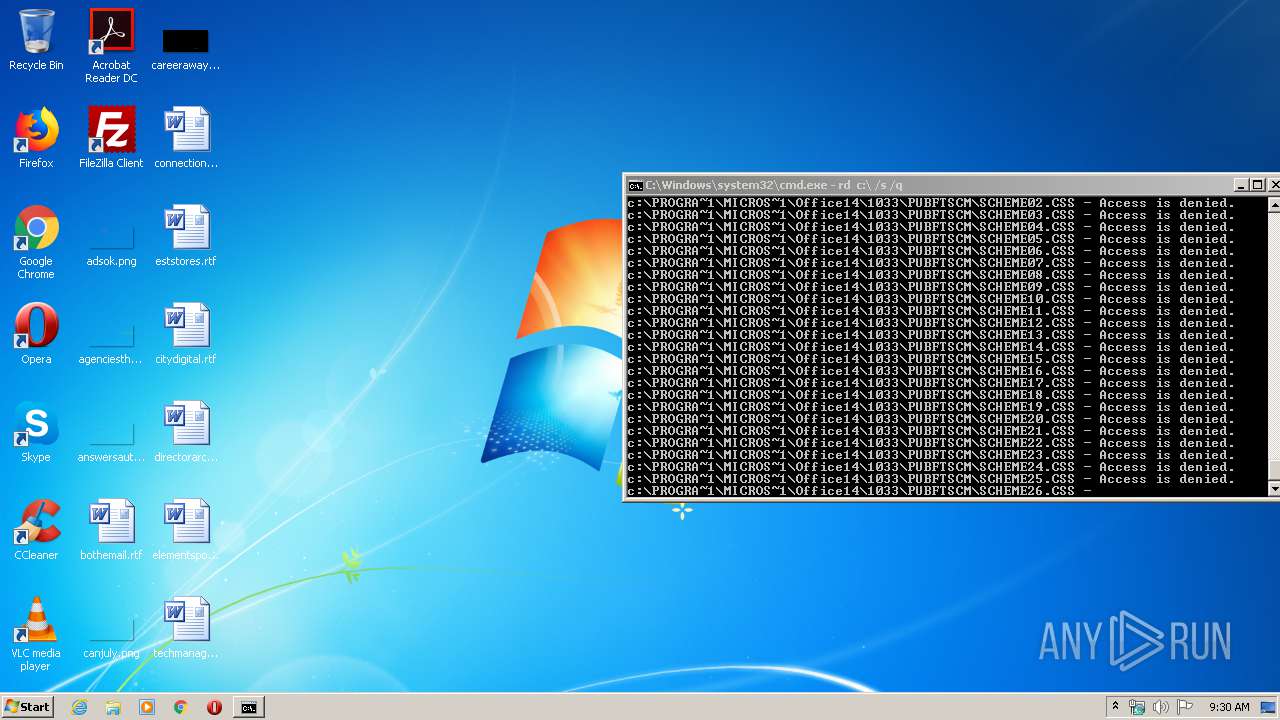
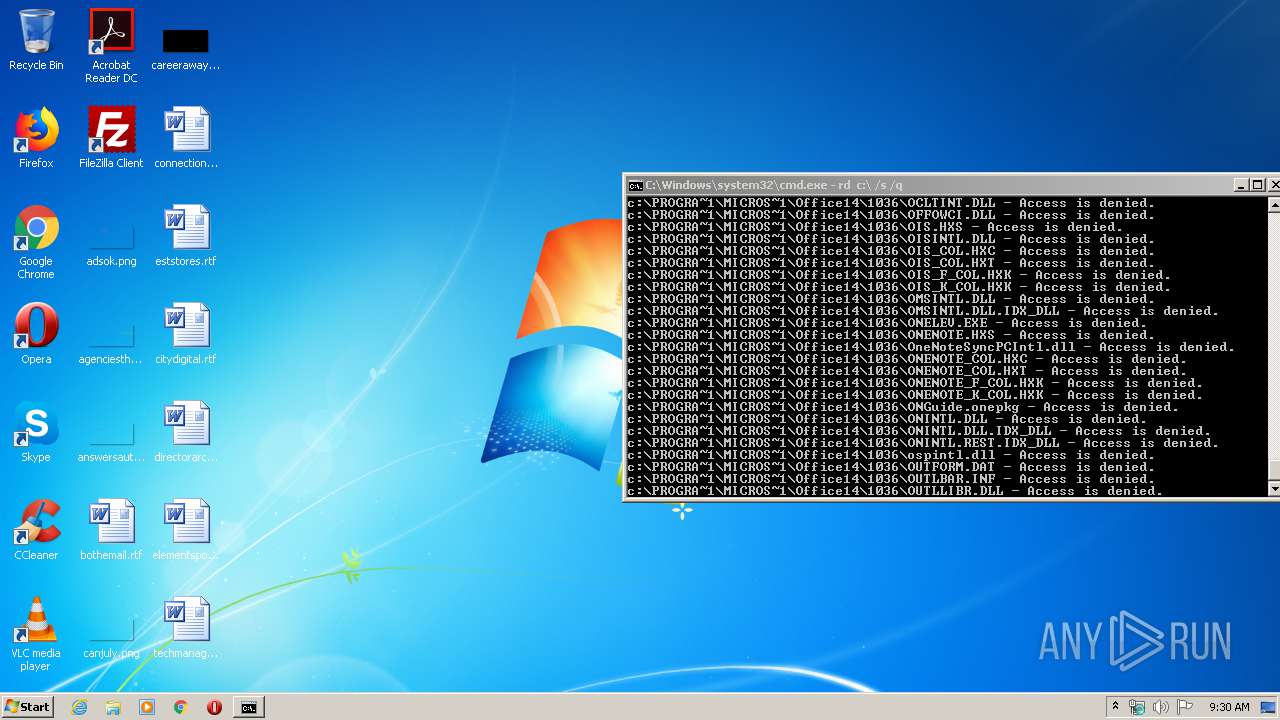
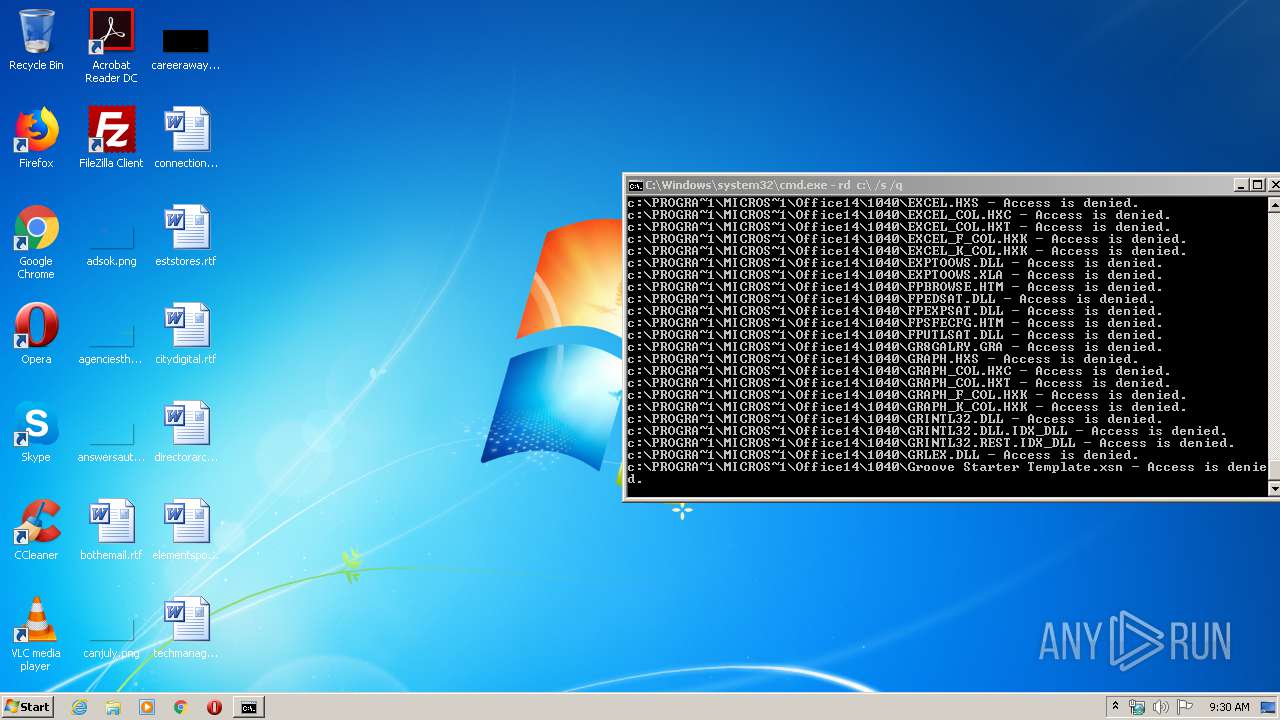
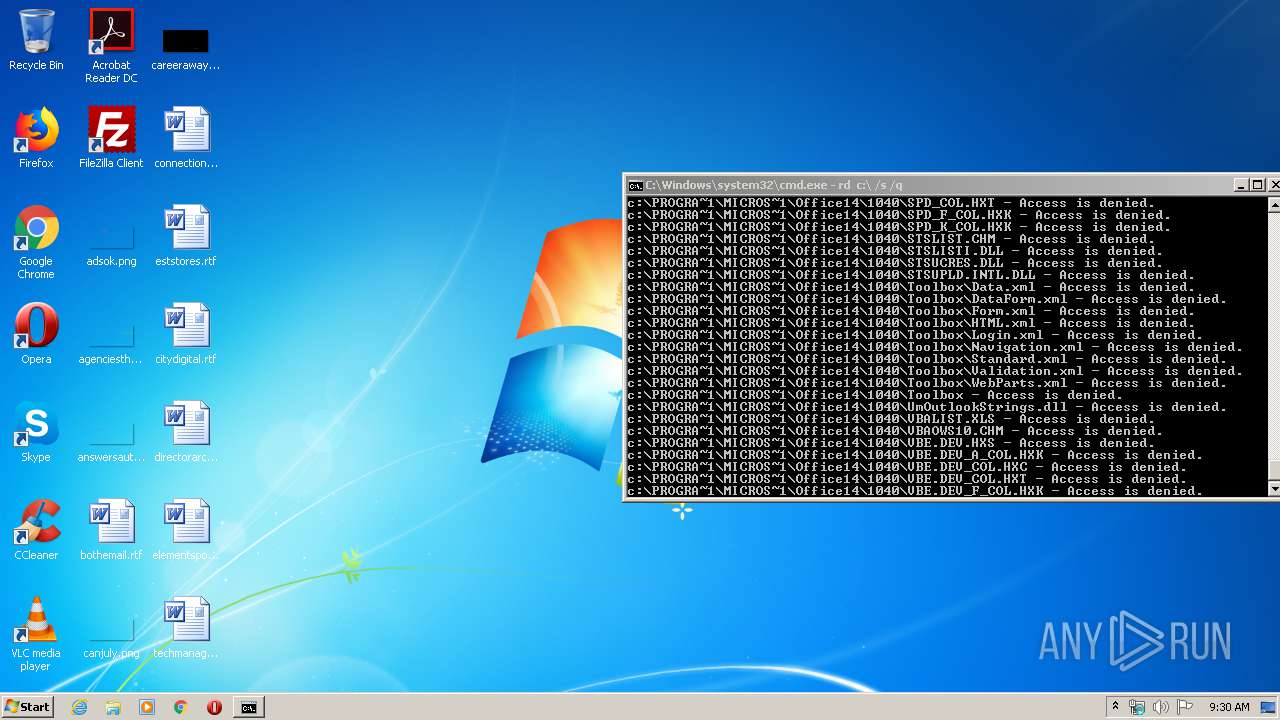
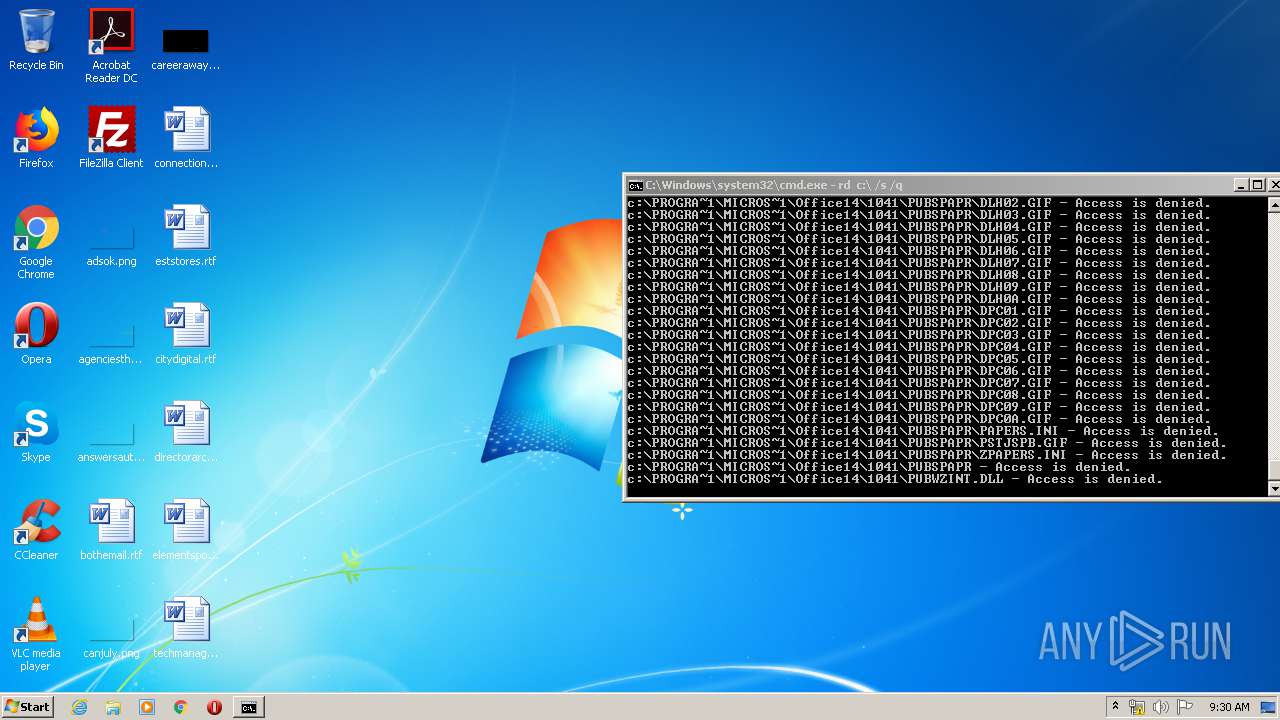
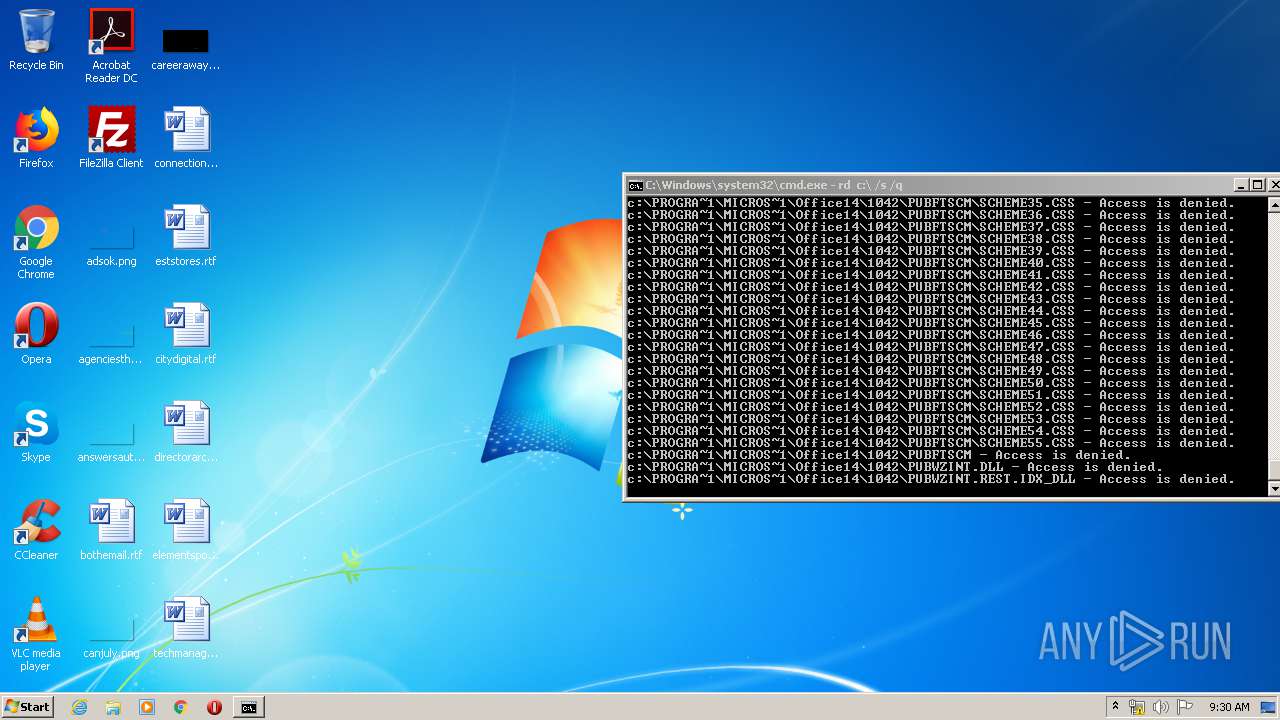
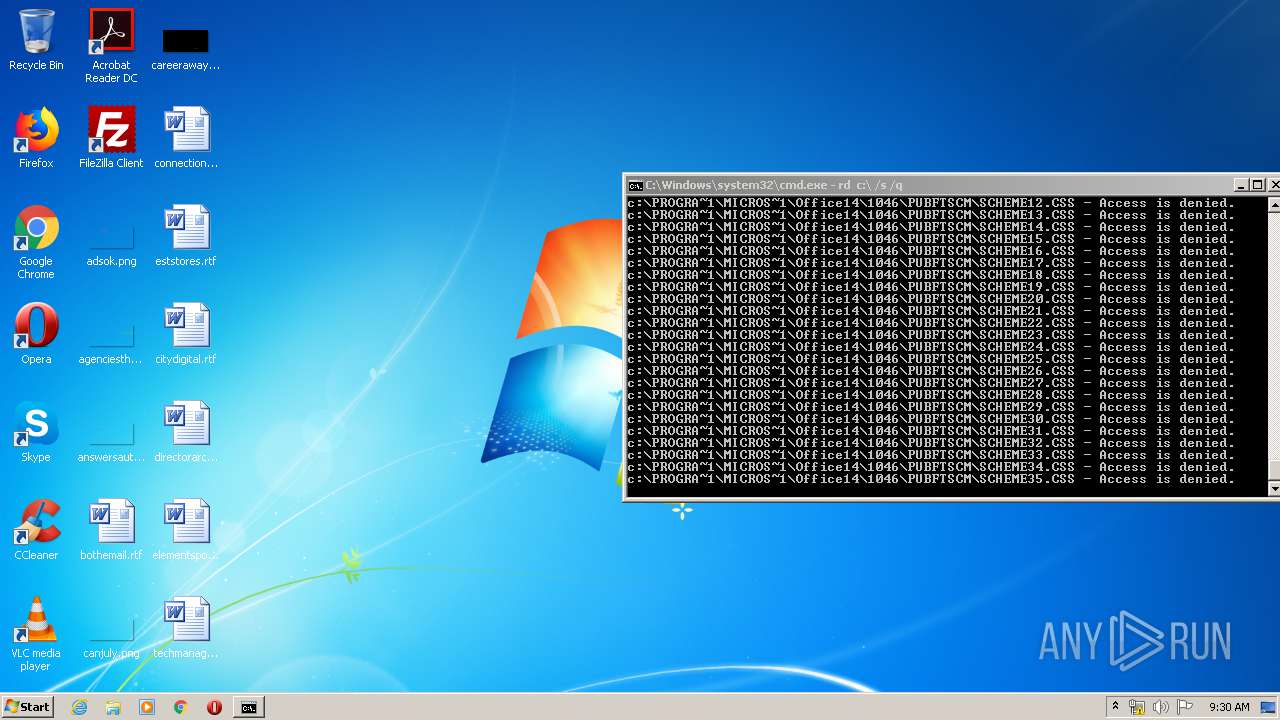
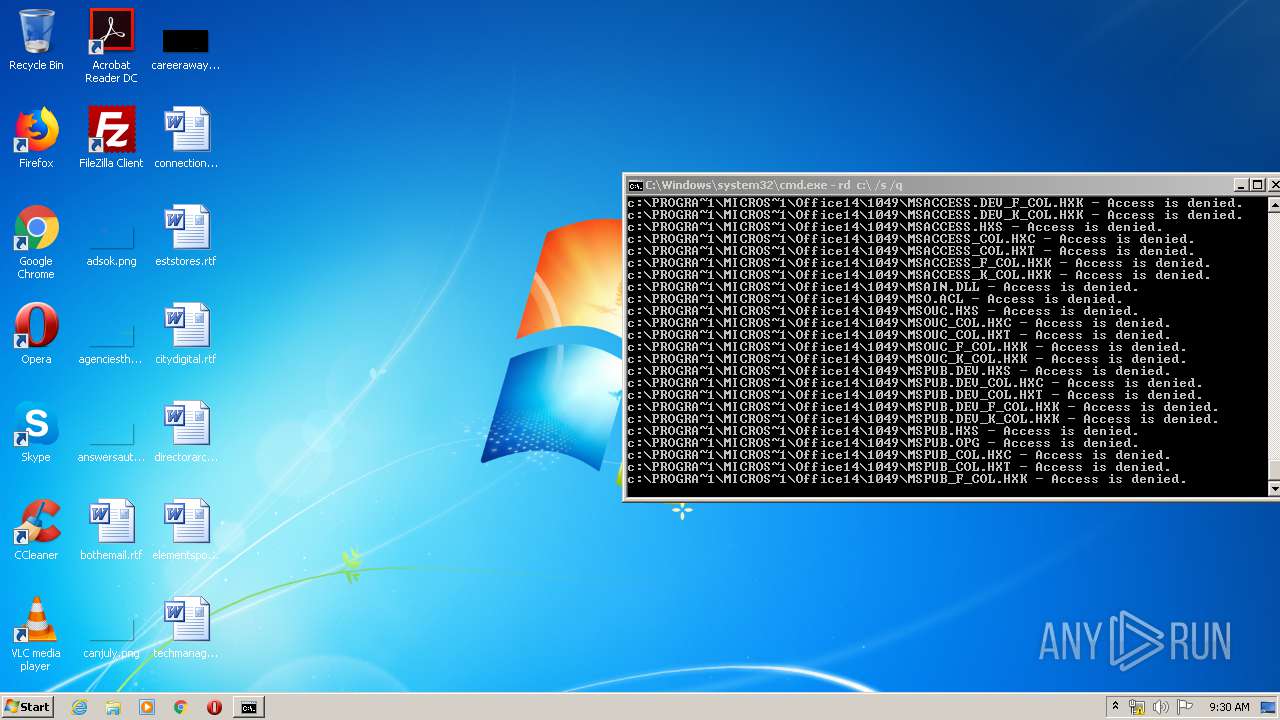
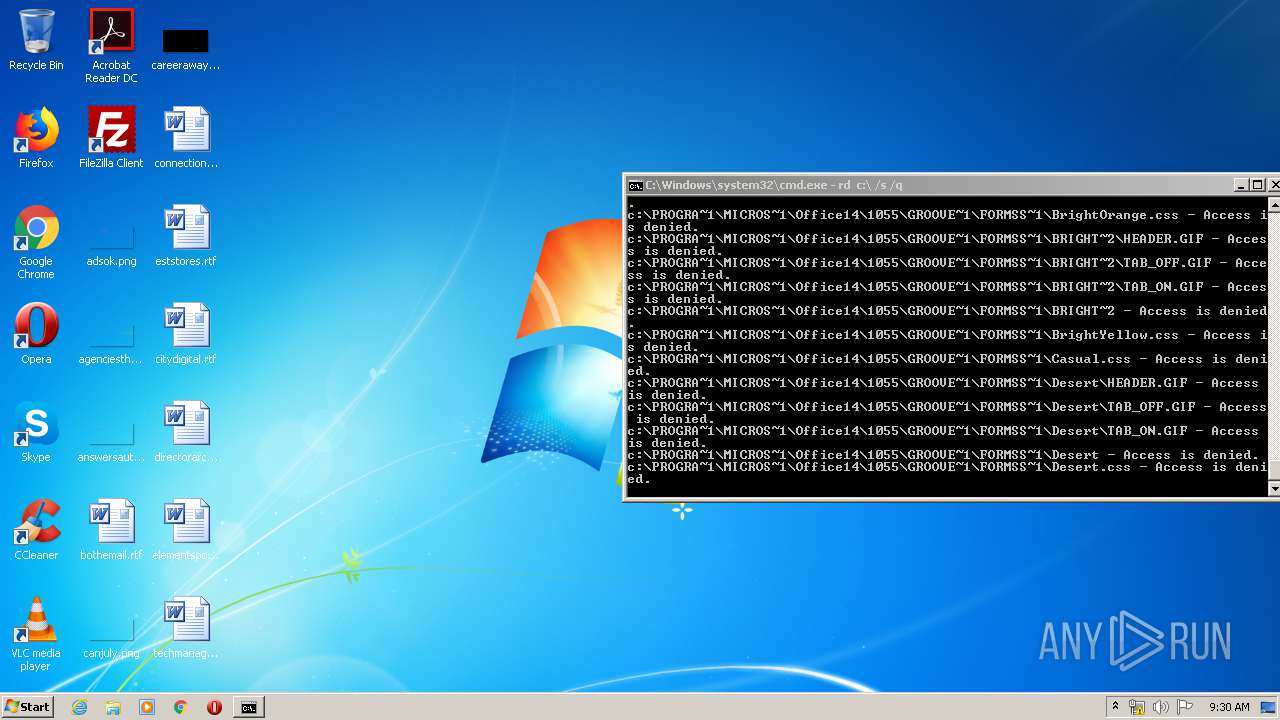
Actions looks like stealing of personal data
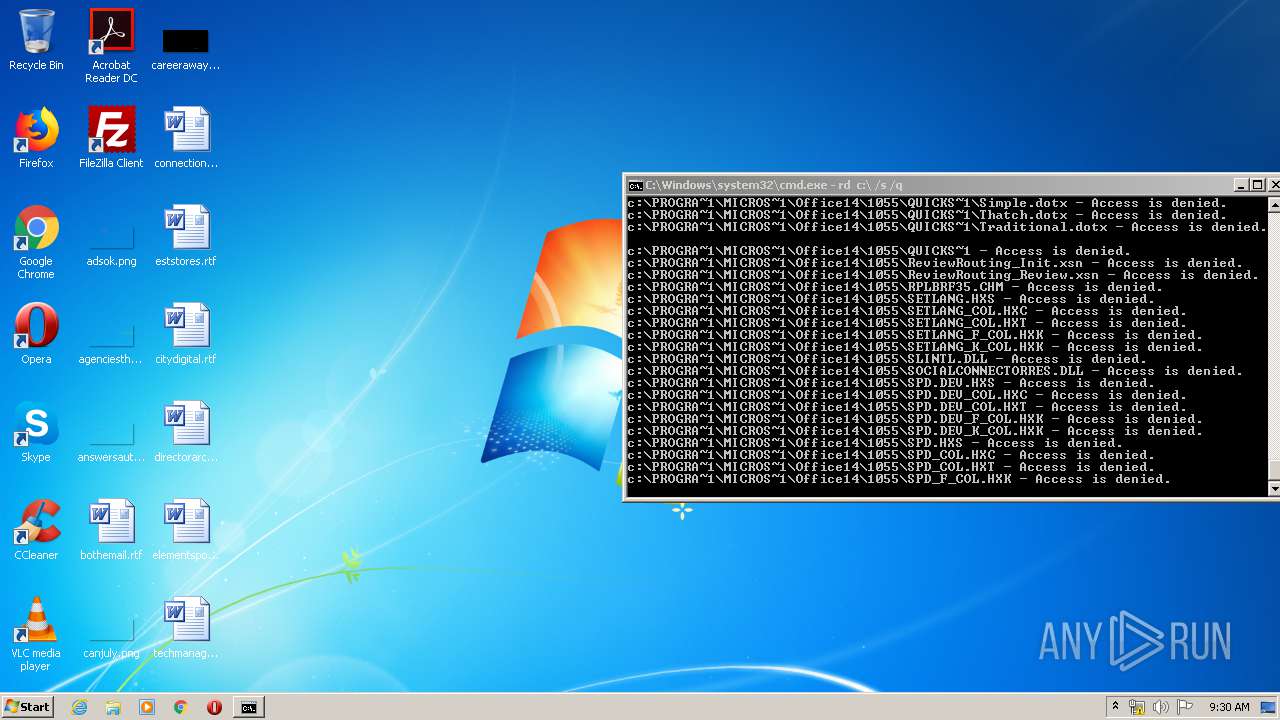
- cmd.exe (PID: 3456)
SUSPICIOUS
No suspicious indicators.INFO
Manual execution by user
- cmd.exe (PID: 3456)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .vbox | | | VirtualBox machine definition (99.1) |
|---|---|---|
| .xml | | | Generic XML (ASCII) (0.8) |
EXIF
XMP
| VirtualBoxXmlns: | http://www.innotek.de/VirtualBox-settings |
|---|---|
| VirtualBoxVersion: | 1.12-windows |
| VirtualBoxMachineUuid: | {7827244e-0cd9-4a0e-876e-a0e29ff5528e} |
| VirtualBoxMachineName: | Windows XP |
| VirtualBoxMachineOSType: | WindowsXP |
| VirtualBoxMachineSnapshotFolder: | Snapshots |
| VirtualBoxMachineLastStateChange: | 2020:02:21 04:54:39Z |
| VirtualBoxMachineMediaRegistryHardDisksHardDiskUuid: | {943224f7-2b59-4355-bf64-eb8fa7f946b6} |
| VirtualBoxMachineMediaRegistryHardDisksHardDiskLocation: | Windows XP.vhd |
| VirtualBoxMachineMediaRegistryHardDisksHardDiskFormat: | VHD |
| VirtualBoxMachineMediaRegistryHardDisksHardDiskType: | Normal |
| VirtualBoxMachineMediaRegistryDVDImagesImageUuid: | {ac707d1e-50b7-429c-8fb6-e3113e9c429d} |
| VirtualBoxMachineMediaRegistryDVDImagesImageLocation: | E:/isos/Windows XP/(GetMyOS)Windows_XP_Pro_x86_With_SP3_English.iso |
| VirtualBoxMachineMediaRegistryFloppyImages: | - |
| VirtualBoxMachineExtraDataExtraDataItemName: | GUI/LastCloseAction |
| VirtualBoxMachineExtraDataExtraDataItemValue: | shutdown |
| VirtualBoxMachineHardwareVersion: | 2 |
| VirtualBoxMachineHardwareCpuCount: | 1 |
| VirtualBoxMachineHardwareCpuHotplug: | - |
| VirtualBoxMachineHardwareCpuHardwareVirtExEnabled: | |
| VirtualBoxMachineHardwareCpuHardwareVirtExExclusive: | - |
| VirtualBoxMachineHardwareCpuHardwareVirtExNestedPagingEnabled: | |
| VirtualBoxMachineHardwareCpuHardwareVirtExVPIDEnabled: | |
| VirtualBoxMachineHardwareCpuPaeEnabled: | |
| VirtualBoxMachineHardwareCpuHardwareVirtExLargePagesEnabled: | |
| VirtualBoxMachineHardwareCpuHardwareVirtForceEnabled: | - |
| VirtualBoxMachineHardwareMemoryRAMSize: | 1100 |
| VirtualBoxMachineHardwareMemoryPageFusion: | - |
| VirtualBoxMachineHardwareHidPointing: | USBTablet |
| VirtualBoxMachineHardwareHidKeyboard: | PS2Keyboard |
| VirtualBoxMachineHardwareHpetEnabled: | - |
| VirtualBoxMachineHardwareChipsetType: | PIIX3 |
| VirtualBoxMachineHardwareBootOrderPosition: | 1 |
| VirtualBoxMachineHardwareBootOrderDevice: | Floppy |
| VirtualBoxMachineHardwareDisplayVRAMSize: | 18 |
| VirtualBoxMachineHardwareDisplayMonitorCount: | 1 |
| VirtualBoxMachineHardwareDisplayAccelerate3D: | - |
| VirtualBoxMachineHardwareDisplayAccelerate2DVideo: | - |
| VirtualBoxMachineHardwareRemoteDisplayEnabled: | - |
| VirtualBoxMachineHardwareRemoteDisplayAuthType: | Null |
| VirtualBoxMachineHardwareRemoteDisplayAuthTimeout: | 5000 |
| VirtualBoxMachineHardwareBiosAcpiEnabled: | |
| VirtualBoxMachineHardwareBiosIoapicEnabled: | - |
| VirtualBoxMachineHardwareBiosLogoFadeIn: | |
| VirtualBoxMachineHardwareBiosLogoFadeOut: | |
| VirtualBoxMachineHardwareBiosLogoDisplayTime: | - |
| VirtualBoxMachineHardwareBiosBootMenuMode: | MessageAndMenu |
| VirtualBoxMachineHardwareBiosTimeOffsetValue: | - |
| VirtualBoxMachineHardwareBiosPXEDebugEnabled: | - |
| VirtualBoxMachineHardwareUSBControllerEnabled: | |
| VirtualBoxMachineHardwareUSBControllerEnabledEhci: | - |
| VirtualBoxMachineHardwareNetworkAdapterSlot: | - |
| VirtualBoxMachineHardwareNetworkAdapterEnabled: | |
| VirtualBoxMachineHardwareNetworkAdapterMACAddress: | 080027607938 |
| VirtualBoxMachineHardwareNetworkAdapterCable: | |
| VirtualBoxMachineHardwareNetworkAdapterSpeed: | - |
| VirtualBoxMachineHardwareNetworkAdapterType: | Am79C973 |
| VirtualBoxMachineHardwareNetworkAdapterDisabledModes: | - |
| VirtualBoxMachineHardwareNetworkAdapterNatDnsPass-domain: | |
| VirtualBoxMachineHardwareNetworkAdapterNatDnsUse-proxy: | - |
| VirtualBoxMachineHardwareNetworkAdapterNatDnsUse-host-resolver: | - |
| VirtualBoxMachineHardwareNetworkAdapterNatAliasLogging: | - |
| VirtualBoxMachineHardwareNetworkAdapterNatAliasProxy-only: | - |
| VirtualBoxMachineHardwareNetworkAdapterNatAliasUse-same-ports: | - |
| VirtualBoxMachineHardwareNetworkAdapterDisabledModesNatDnsPass-domain: | |
| VirtualBoxMachineHardwareNetworkAdapterDisabledModesNatDnsUse-proxy: | - |
| VirtualBoxMachineHardwareNetworkAdapterDisabledModesNatDnsUse-host-resolver: | - |
| VirtualBoxMachineHardwareNetworkAdapterDisabledModesNatAliasLogging: | - |
| VirtualBoxMachineHardwareNetworkAdapterDisabledModesNatAliasProxy-only: | - |
| VirtualBoxMachineHardwareNetworkAdapterDisabledModesNatAliasUse-same-ports: | - |
| VirtualBoxMachineHardwareUartPortSlot: | - |
| VirtualBoxMachineHardwareUartPortEnabled: | - |
| VirtualBoxMachineHardwareUartPortIOBase: | 0x3f8 |
| VirtualBoxMachineHardwareUartPortIrq: | 4 |
| VirtualBoxMachineHardwareUartPortHostMode: | Disconnected |
| VirtualBoxMachineHardwareLptPortSlot: | - |
| VirtualBoxMachineHardwareLptPortEnabled: | - |
| VirtualBoxMachineHardwareLptPortIOBase: | 0x378 |
| VirtualBoxMachineHardwareLptPortIrq: | 4 |
| VirtualBoxMachineHardwareAudioAdapterController: | AC97 |
| VirtualBoxMachineHardwareAudioAdapterDriver: | DirectSound |
| VirtualBoxMachineHardwareAudioAdapterEnabled: | |
| VirtualBoxMachineHardwareRtcLocalOrUTC: | local |
| VirtualBoxMachineHardwareSharedFoldersSharedFolderName: | winxp_programs |
| VirtualBoxMachineHardwareSharedFoldersSharedFolderHostPath: | C:\Users\noobnoob1\Desktop\winxp programs |
| VirtualBoxMachineHardwareSharedFoldersSharedFolderWritable: | - |
| VirtualBoxMachineHardwareSharedFoldersSharedFolderAutoMount: | |
| VirtualBoxMachineHardwareClipboardMode: | Bidirectional |
| VirtualBoxMachineHardwareIoIoCacheEnabled: | |
| VirtualBoxMachineHardwareIoIoCacheSize: | 5 |
| VirtualBoxMachineHardwareIoBandwidthGroups: | - |
| VirtualBoxMachineHardwareHostPciDevices: | - |
| VirtualBoxMachineHardwareGuestMemoryBalloonSize: | - |
| VirtualBoxMachineHardwareGuestPropertiesGuestPropertyName: | /VirtualBox/HostInfo/GUI/LanguageID |
| VirtualBoxMachineHardwareGuestPropertiesGuestPropertyValue: | en_US |
| VirtualBoxMachineHardwareGuestPropertiesGuestPropertyTimestamp: | 1582120355239257100 |
| VirtualBoxMachineHardwareGuestPropertiesGuestPropertyFlags: | - |
| VirtualBoxMachineStorageControllersStorageControllerName: | IDE Controller |
| VirtualBoxMachineStorageControllersStorageControllerType: | PIIX4 |
| VirtualBoxMachineStorageControllersStorageControllerPortCount: | 2 |
| VirtualBoxMachineStorageControllersStorageControllerUseHostIOCache: | |
| VirtualBoxMachineStorageControllersStorageControllerBootable: | |
| VirtualBoxMachineStorageControllersStorageControllerAttachedDeviceType: | HardDisk |
| VirtualBoxMachineStorageControllersStorageControllerAttachedDevicePort: | - |
| VirtualBoxMachineStorageControllersStorageControllerAttachedDeviceDevice: | - |
| VirtualBoxMachineStorageControllersStorageControllerAttachedDeviceImageUuid: | {943224f7-2b59-4355-bf64-eb8fa7f946b6} |
| VirtualBoxMachineStorageControllersStorageControllerAttachedDevicePassthrough: | - |
Total processes
36
Monitored processes
2
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 3456 | "C:\Windows\system32\cmd.exe" | C:\Windows\system32\cmd.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 3840 | "C:\Windows\system32\rundll32.exe" C:\Windows\system32\shell32.dll,OpenAs_RunDLL C:\Users\admin\AppData\Local\Temp\Windows XP.vbox | C:\Windows\system32\rundll32.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows host process (Rundll32) Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
Total events
6
Read events
6
Write events
0
Delete events
0
Modification events
Executable files
0
Suspicious files
0
Text files
0
Unknown types
0
Dropped files
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
0
DNS requests
0
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report