| File name: | Sigmanly_48ebd0e60eed1e5cc38195aa33694afd2a387be44a34270890f7fa756833d9c8 |
| Full analysis: | https://app.any.run/tasks/64e07329-3b96-4934-a5f4-05116c50d871 |
| Verdict: | Malicious activity |
| Analysis date: | May 16, 2025, 12:13:35 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/vnd.microsoft.portable-executable |
| File info: | PE32 executable (GUI) Intel 80386 Mono/.Net assembly, for MS Windows, 3 sections |
| MD5: | 81DAACD7018A10EF90057C993545BB0B |
| SHA1: | E966C8FAF9EC0C445C3D0AA483B4CC770EE24D19 |
| SHA256: | 48EBD0E60EED1E5CC38195AA33694AFD2A387BE44A34270890F7FA756833D9C8 |
| SSDEEP: | 196608:p7Oze8wD8n5oJ+UEwzOA4z7ctzkplPcH0Sxo2Do35d1:1Oy8PuJxEJA/zkpvSG2Do35 |
MALICIOUS
Run PowerShell with an invisible window
- powershell.exe (PID: 644)
- powershell.exe (PID: 5352)
Changes Windows Defender settings
- Update.exe (PID: 2284)
- WinService.exe (PID: 300)
Adds path to the Windows Defender exclusion list
- Update.exe (PID: 2284)
- WinService.exe (PID: 300)
Changes the autorun value in the registry
- Update.exe (PID: 2284)
- WinService.exe (PID: 300)
SUSPICIOUS
Reads security settings of Internet Explorer
- Sigmanly_48ebd0e60eed1e5cc38195aa33694afd2a387be44a34270890f7fa756833d9c8.exe (PID: 5548)
- Update.exe (PID: 2284)
- WinService.exe (PID: 300)
Executable content was dropped or overwritten
- Sigmanly_48ebd0e60eed1e5cc38195aa33694afd2a387be44a34270890f7fa756833d9c8.exe (PID: 5548)
- Update.exe (PID: 2284)
Starts POWERSHELL.EXE for commands execution
- Update.exe (PID: 2284)
- WinService.exe (PID: 300)
Uses REG/REGEDIT.EXE to modify registry
- Update.exe (PID: 2284)
- WinService.exe (PID: 300)
Script adds exclusion path to Windows Defender
- Update.exe (PID: 2284)
- WinService.exe (PID: 300)
Checks for external IP
- Update.exe (PID: 2284)
- WinService.exe (PID: 300)
Connects to unusual port
- Update.exe (PID: 2284)
- WinService.exe (PID: 300)
INFO
Creates files or folders in the user directory
- Sigmanly_48ebd0e60eed1e5cc38195aa33694afd2a387be44a34270890f7fa756833d9c8.exe (PID: 5548)
- Update.exe (PID: 2284)
Checks supported languages
- Sigmanly_48ebd0e60eed1e5cc38195aa33694afd2a387be44a34270890f7fa756833d9c8.exe (PID: 5548)
- Update.exe (PID: 2284)
- WinService.exe (PID: 300)
The sample compiled with english language support
- Sigmanly_48ebd0e60eed1e5cc38195aa33694afd2a387be44a34270890f7fa756833d9c8.exe (PID: 5548)
- Update.exe (PID: 2284)
Reads the computer name
- Sigmanly_48ebd0e60eed1e5cc38195aa33694afd2a387be44a34270890f7fa756833d9c8.exe (PID: 5548)
- Update.exe (PID: 2284)
- WinService.exe (PID: 300)
Process checks computer location settings
- Sigmanly_48ebd0e60eed1e5cc38195aa33694afd2a387be44a34270890f7fa756833d9c8.exe (PID: 5548)
- Update.exe (PID: 2284)
- WinService.exe (PID: 300)
Reads the machine GUID from the registry
- Sigmanly_48ebd0e60eed1e5cc38195aa33694afd2a387be44a34270890f7fa756833d9c8.exe (PID: 5548)
Auto-launch of the file from Registry key
- Update.exe (PID: 2284)
- WinService.exe (PID: 300)
Script raised an exception (POWERSHELL)
- powershell.exe (PID: 644)
- powershell.exe (PID: 5352)
Checks if a key exists in the options dictionary (POWERSHELL)
- powershell.exe (PID: 644)
- powershell.exe (PID: 5352)
Compiled with Borland Delphi (YARA)
- Sigmanly_48ebd0e60eed1e5cc38195aa33694afd2a387be44a34270890f7fa756833d9c8.exe (PID: 5548)
- WinService.exe (PID: 300)
- slui.exe (PID: 5400)
- Update.exe (PID: 2284)
Manual execution by a user
- WinService.exe (PID: 300)
Checks proxy server information
- slui.exe (PID: 5400)
Reads the software policy settings
- slui.exe (PID: 5400)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win32 EXE PECompact compressed (generic) (83) |
|---|---|---|
| .exe | | | Win32 Executable (generic) (9) |
| .exe | | | Generic Win/DOS Executable (3.9) |
| .exe | | | DOS Executable Generic (3.9) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2059:06:18 22:24:49+00:00 |
| ImageFileCharacteristics: | Executable, Large address aware |
| PEType: | PE32 |
| LinkerVersion: | 48 |
| CodeSize: | 28903424 |
| InitializedDataSize: | 2048 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x1b927e2 |
| OSVersion: | 4 |
| ImageVersion: | - |
| SubsystemVersion: | 6 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 1.0.0.0 |
| ProductVersionNumber: | 1.0.0.0 |
| FileFlagsMask: | 0x003f |
| FileFlags: | (none) |
| FileOS: | Win32 |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | Neutral |
| CharacterSet: | Unicode |
| Comments: | - |
| CompanyName: | - |
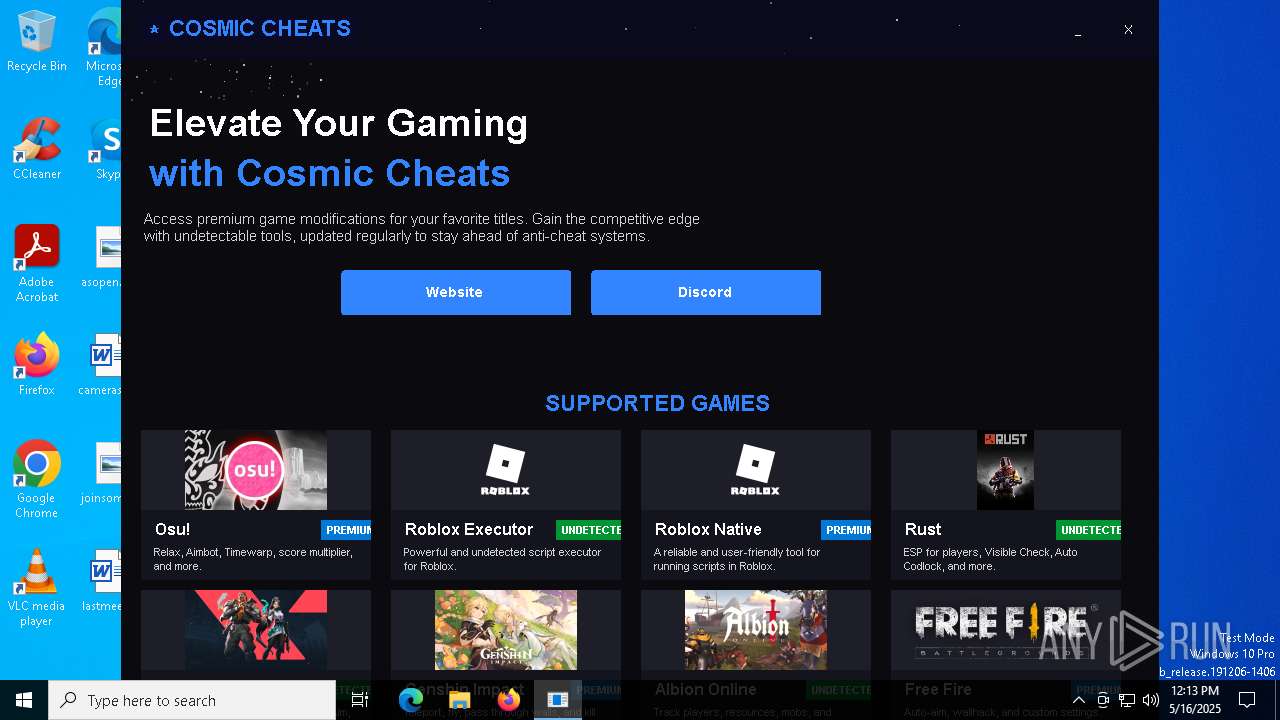
| FileDescription: | CosmicCheats |
| FileVersion: | 1.0.0.0 |
| InternalName: | CosmicCheats.exe |
| LegalCopyright: | Copyright © 2025 |
| LegalTrademarks: | - |
| OriginalFileName: | CosmicCheats.exe |
| ProductName: | CosmicCheats |
| ProductVersion: | 1.0.0.0 |
| AssemblyVersion: | 1.0.0.0 |
Total processes
135
Monitored processes
12
Malicious processes
3
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 300 | C:\Users\admin\AppData\Roaming\WindowsService\WinService.exe | C:\Users\admin\AppData\Roaming\WindowsService\WinService.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Description: RavenOriginalStub Version: 1.0.0.0 Modules
| |||||||||||||||
| 644 | "C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe" -WindowStyle Hidden -Command "Add-MpPreference -ExclusionPath 'C:\'" | C:\Windows\SysWOW64\WindowsPowerShell\v1.0\powershell.exe | — | Update.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2268 | "C:\Windows\System32\reg.exe" add "HKLM\SOFTWARE\Policies\Microsoft\Windows Defender\Exclusions\Paths" /v C:\ /d 0 /f | C:\Windows\SysWOW64\reg.exe | — | WinService.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Registry Console Tool Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2284 | "C:\Users\admin\AppData\Roaming\Update.exe" | C:\Users\admin\AppData\Roaming\Update.exe | Sigmanly_48ebd0e60eed1e5cc38195aa33694afd2a387be44a34270890f7fa756833d9c8.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Description: RavenOriginalStub Version: 1.0.0.0 Modules
| |||||||||||||||
| 2420 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | reg.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4228 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | powershell.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4976 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | reg.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5352 | "C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe" -WindowStyle Hidden -Command "Add-MpPreference -ExclusionPath 'C:\'" | C:\Windows\SysWOW64\WindowsPowerShell\v1.0\powershell.exe | — | WinService.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5384 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | powershell.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5400 | C:\WINDOWS\System32\slui.exe -Embedding | C:\Windows\System32\slui.exe | svchost.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Activation Client Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
15 543
Read events
15 541
Write events
2
Delete events
0
Modification events
| (PID) Process: | (2284) Update.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Run |
| Operation: | write | Name: | WindowsService |
Value: C:\Users\admin\AppData\Roaming\WindowsService\WinService.exe | |||
| (PID) Process: | (300) WinService.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Run |
| Operation: | write | Name: | WindowsService |
Value: C:\Users\admin\AppData\Roaming\WindowsService\WinService.exe | |||
Executable files
2
Suspicious files
1
Text files
8
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2284 | Update.exe | C:\Users\admin\AppData\Roaming\WindowsService\WinService.exe | executable | |
MD5:F040303D85C56F3B40066FD4B535D277 | SHA256:CBF4E04802D850CBC223D439C336703AABA205EEBD6E8D300048DAE293B47722 | |||
| 644 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_mkpslubx.hab.psm1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 5352 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_tqcycr0j.spa.ps1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 5352 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_q40csnwf.de4.psm1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 644 | powershell.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\PowerShell\StartupProfileData-NonInteractive | binary | |
MD5:895A9C35142D9B25C5E3F5B9597B3CEF | SHA256:847951ED1F4AC9303EC66985CB36AABFA04F6086189EF2F88F88F6F03AF8158C | |||
| 5352 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_opg0wtju.odr.ps1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 644 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_qoousaih.uut.ps1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 644 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_1mqpvvpc.ixi.psm1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 5352 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_nyo4cvqo.v4j.psm1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 5548 | Sigmanly_48ebd0e60eed1e5cc38195aa33694afd2a387be44a34270890f7fa756833d9c8.exe | C:\Users\admin\AppData\Roaming\Update.exe | executable | |
MD5:F040303D85C56F3B40066FD4B535D277 | SHA256:CBF4E04802D850CBC223D439C336703AABA205EEBD6E8D300048DAE293B47722 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
13
TCP/UDP connections
183
DNS requests
18
Threats
13
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
— | — | GET | 200 | 23.216.77.13:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
2284 | Update.exe | GET | 200 | 104.26.12.205:80 | http://api.ipify.org/ | unknown | — | — | malicious |
2284 | Update.exe | GET | 200 | 104.26.12.205:80 | http://api.ipify.org/ | unknown | — | — | malicious |
300 | WinService.exe | GET | 200 | 104.26.12.205:80 | http://api.ipify.org/ | unknown | — | — | malicious |
300 | WinService.exe | GET | 200 | 104.26.12.205:80 | http://api.ipify.org/ | unknown | — | — | malicious |
6228 | SIHClient.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20Update%20Signing%20CA%202.1.crl | unknown | — | — | whitelisted |
6228 | SIHClient.exe | GET | 200 | 2.19.11.105:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut_2010-06-23.crl | unknown | — | — | whitelisted |
6228 | SIHClient.exe | GET | 200 | 2.19.11.105:80 | http://crl.microsoft.com/pki/crl/products/MicTimStaPCA_2010-07-01.crl | unknown | — | — | whitelisted |
6228 | SIHClient.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
— | — | 192.168.100.255:137 | — | — | — | whitelisted |
— | — | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
— | — | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
— | — | 23.216.77.13:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
— | — | 23.35.229.160:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
— | — | 172.211.123.250:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | FR | whitelisted |
2284 | Update.exe | 104.26.12.205:80 | api.ipify.org | CLOUDFLARENET | US | shared |
2284 | Update.exe | 51.38.196.118:7777 | yaptikanladin.mentality.cloud | OVH SAS | FR | malicious |
3216 | svchost.exe | 172.211.123.250:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | FR | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
api.ipify.org |
| shared |
yaptikanladin.mentality.cloud |
| malicious |
slscr.update.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |
activation-v2.sls.microsoft.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2284 | Update.exe | Device Retrieving External IP Address Detected | SUSPICIOUS [ANY.RUN] An IP address was received from the server as a result of an HTTP request |
2284 | Update.exe | Device Retrieving External IP Address Detected | ET INFO External IP Lookup api.ipify.org |
2284 | Update.exe | Device Retrieving External IP Address Detected | POLICY [ANY.RUN] External IP Lookup by HTTP (api .ipify .org) |
2196 | svchost.exe | Misc activity | ET INFO External IP Lookup Domain (ipify .org) in DNS Lookup |
2284 | Update.exe | Device Retrieving External IP Address Detected | ET INFO External IP Lookup api.ipify.org |
2284 | Update.exe | Device Retrieving External IP Address Detected | POLICY [ANY.RUN] External IP Lookup by HTTP (api .ipify .org) |
2284 | Update.exe | Device Retrieving External IP Address Detected | SUSPICIOUS [ANY.RUN] An IP address was received from the server as a result of an HTTP request |
300 | WinService.exe | Device Retrieving External IP Address Detected | ET INFO External IP Lookup api.ipify.org |
300 | WinService.exe | Device Retrieving External IP Address Detected | POLICY [ANY.RUN] External IP Lookup by HTTP (api .ipify .org) |
300 | WinService.exe | Device Retrieving External IP Address Detected | SUSPICIOUS [ANY.RUN] An IP address was received from the server as a result of an HTTP request |