| File name: | W95ws2setup.exe |
| Full analysis: | https://app.any.run/tasks/ab4786f2-b7ce-42fc-979c-912220a5b366 |
| Verdict: | Malicious activity |
| Analysis date: | January 29, 2025, 19:37:45 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Indicators: | |
| MIME: | application/vnd.microsoft.portable-executable |
| File info: | PE32 executable (GUI) Intel 80386 (stripped to external PDB), for MS Windows, 5 sections |
| MD5: | FC1D00A94F95A88662229604F68F2669 |
| SHA1: | 79912F041DC43D0918452A00019646CCD466F956 |
| SHA256: | 48C82825328EF63BCE1D471D505F0E243CAE94B5B05C66CF2E51B75C6D4D4922 |
| SSDEEP: | 49152:OIqvmgTS46FKdMd5uyMl3IdYlffcLGHEz+ipAF5NVguRqMw1GPWMNzKYcNSJYTxd:ovmdbd56lCYlffcLGHVipAv3guRqMw1j |
MALICIOUS
Executing a file with an untrusted certificate
- W95ws2setup.exe (PID: 6604)
Changes the autorun value in the registry
- W95ws2setup.exe (PID: 6768)
SUSPICIOUS
Starts a Microsoft application from unusual location
- W95ws2setup.exe (PID: 6604)
- W95ws2setup.exe (PID: 6768)
- setup.exe (PID: 6824)
Executable content was dropped or overwritten
- W95ws2setup.exe (PID: 6768)
Process drops legitimate windows executable
- W95ws2setup.exe (PID: 6768)
The process creates files with name similar to system file names
- W95ws2setup.exe (PID: 6768)
INFO
The sample compiled with english language support
- W95ws2setup.exe (PID: 6768)
Create files in a temporary directory
- W95ws2setup.exe (PID: 6768)
Checks supported languages
- W95ws2setup.exe (PID: 6768)
- setup.exe (PID: 6824)
Reads the computer name
- setup.exe (PID: 6824)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win32 MS Cabinet Self-Extractor (WExtract stub) (58) |
|---|---|---|
| .exe | | | Win32 Executable MS Visual C++ 4.x (25.7) |
| .exe | | | InstallShield setup (8.2) |
| .exe | | | Win32 Executable MS Visual C++ (generic) (5.9) |
| .exe | | | Win32 Executable (generic) (0.8) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 1996:09:30 17:14:31+00:00 |
| ImageFileCharacteristics: | Executable, 32-bit, No debug |
| PEType: | PE32 |
| LinkerVersion: | 3.1 |
| CodeSize: | 60416 |
| InitializedDataSize: | 910336 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x5cab |
| OSVersion: | 4 |
| ImageVersion: | 4 |
| SubsystemVersion: | 4 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 4.71.30.1 |
| ProductVersionNumber: | 4.71.30.1 |
| FileFlagsMask: | 0x003f |
| FileFlags: | (none) |
| FileOS: | Windows NT 32-bit |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | English (U.S.) |
| CharacterSet: | Unicode |
| CompanyName: | Microsoft Corporation |
| FileDescription: | Win32 Cabinet Self-Extractor |
| FileVersion: | 4.71.0030.1 |
| InternalName: | Wextract |
| LegalCopyright: | Copyright (C) Microsoft Corp. 1995 |
| OriginalFileName: | WEXTRACT.EXE |
| ProductName: | Microsoft(R) Windows NT(TM) Operating System |
| ProductVersion: | 4.71.0030.1 |
Total processes
132
Monitored processes
4
Malicious processes
1
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 6604 | "C:\Users\admin\AppData\Local\Temp\W95ws2setup.exe" | C:\Users\admin\AppData\Local\Temp\W95ws2setup.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Win32 Cabinet Self-Extractor Exit code: 3221226540 Version: 4.71.0030.1 Modules
| |||||||||||||||
| 6768 | "C:\Users\admin\AppData\Local\Temp\W95ws2setup.exe" | C:\Users\admin\AppData\Local\Temp\W95ws2setup.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Win32 Cabinet Self-Extractor Version: 4.71.0030.1 Modules
| |||||||||||||||
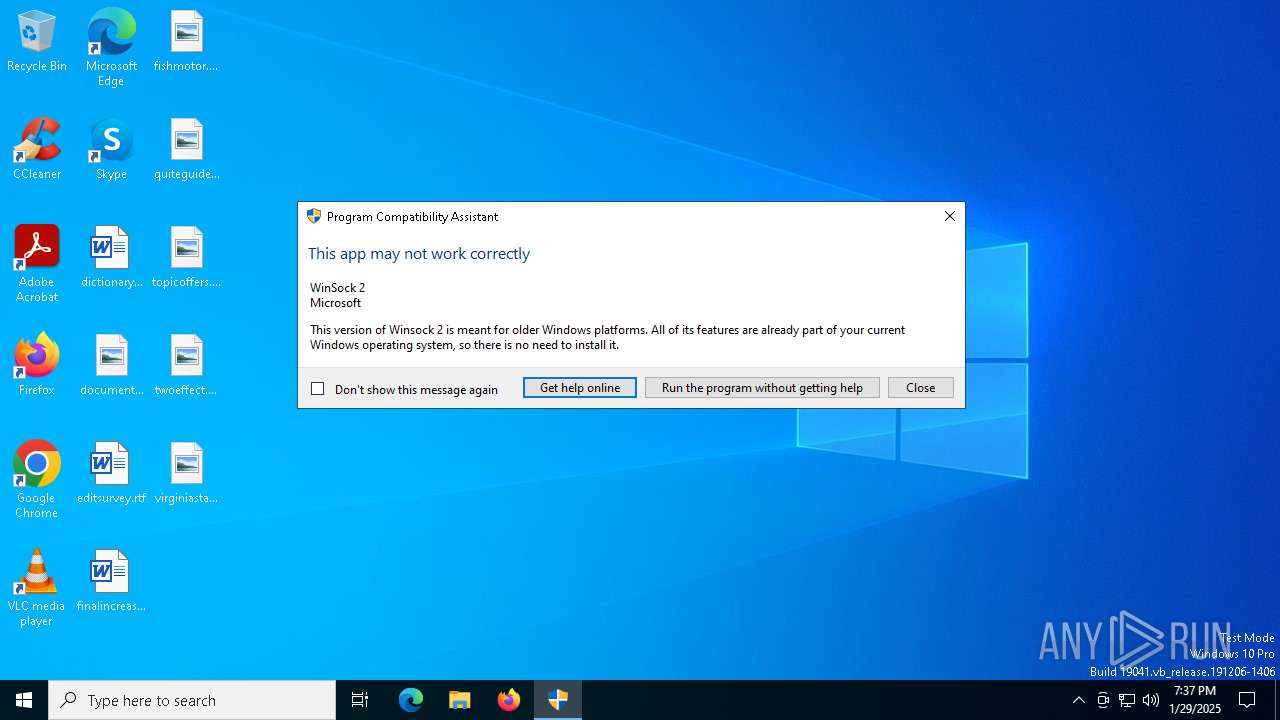
| 6784 | "C:\WINDOWS\system32\pcaui.exe" -g {11111111-1111-1111-1111-111111111111} -x {5eaf2c05-cc3d-4667-93a8-36dad7233794} -a "WinSock 2" -v "Microsoft" -s "This version of Winsock 2 is meant for older Windows platforms. All of its features are already part of your current Windows operating system, so there is no need to install it." -n 1 -f 0 -k 0 -e "C:\Users\admin\AppData\Local\Temp\W95ws2setup.exe" | C:\Windows\System32\pcaui.exe | — | W95ws2setup.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Program Compatibility Assistant User Interface Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
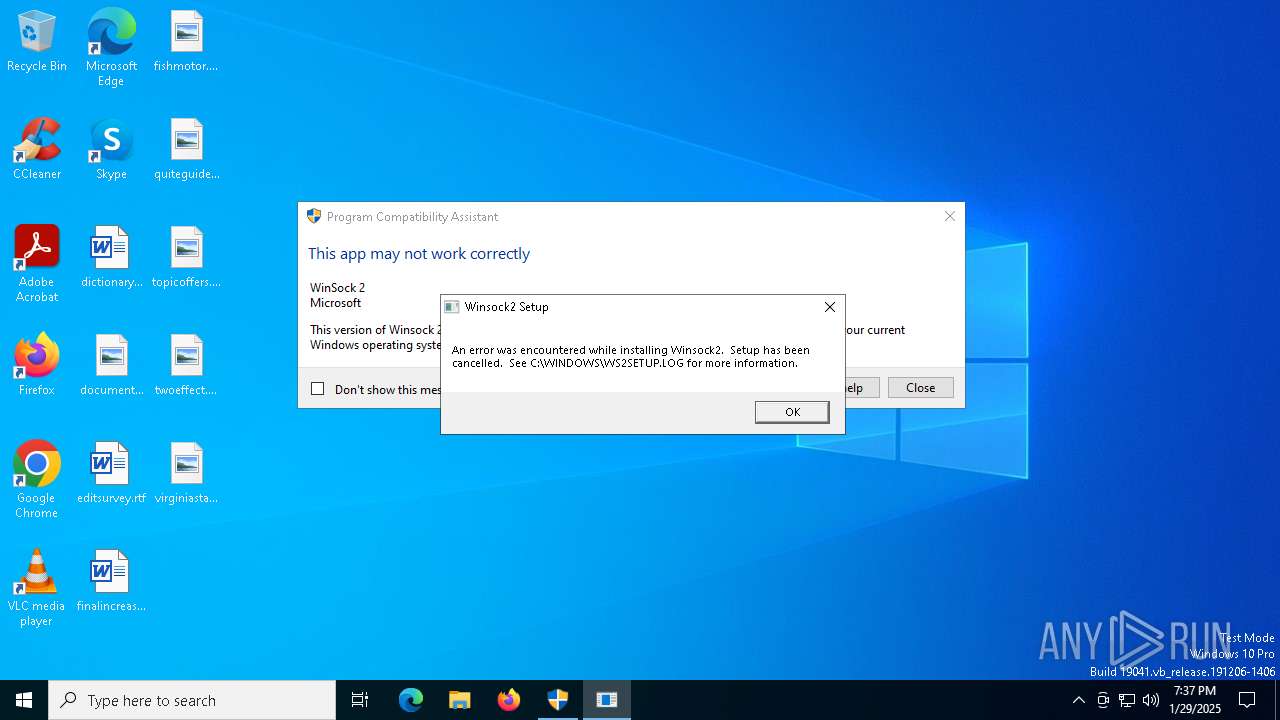
| 6824 | C:\Users\admin\AppData\Local\Temp\MSE000\setup.exe | C:\Users\admin\AppData\Local\Temp\MSE000\setup.exe | — | W95ws2setup.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Winsock2 Setup Version: 4.10.1658 Modules
| |||||||||||||||
Total events
59
Read events
58
Write events
1
Delete events
0
Modification events
| (PID) Process: | (6768) W95ws2setup.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Windows\CurrentVersion\RunOnce |
| Operation: | write | Name: | wextract_cleanup0 |
Value: C:\Users\admin\AppData\Local\Temp\W95ws2setup.exe /D:C:\Users\admin\AppData\Local\Temp\MSE000\ | |||
Executable files
41
Suspicious files
1
Text files
1
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 6768 | W95ws2setup.exe | C:\Users\admin\AppData\Local\Temp\MSE000\setupapi.dll | executable | |
MD5:B36B666D14A52513D7654812A861E925 | SHA256:381114A1E28732FE011CCF9E53EF5D291B977CF6C57AC24F2798905CF410E61A | |||
| 6768 | W95ws2setup.exe | C:\Users\admin\AppData\Local\Temp\MSE000\setup.exe | executable | |
MD5:43605C7BC2986DF52F793452C0D77451 | SHA256:D39799960C41AF7308AB4EFA6A0EB984EC8ECBFFFA537B2B45C09E1E4E77A21C | |||
| 6768 | W95ws2setup.exe | C:\Users\admin\AppData\Local\Temp\MSE000\WS2_32.DLX | executable | |
MD5:EB9E109970C64A44F99D5B103457C9F2 | SHA256:A3F2A139587F8F1F69028EBC30AB3FD3A833BB87C6FC3E2A133B3E917953ADD0 | |||
| 6768 | W95ws2setup.exe | C:\Users\admin\AppData\Local\Temp\MSE000\WINSOCK.DLL | executable | |
MD5:692E3A1168520EF2FC91653EB405D74D | SHA256:8382FD797A9E6A9C6EDED398601DAF91C8E55E9B3CC1F3E837DCA75FE5B9B415 | |||
| 6768 | W95ws2setup.exe | C:\Users\admin\AppData\Local\Temp\MSE000\wsock32.dlx | executable | |
MD5:9569DF48091D5B2085DAF44A36E738C6 | SHA256:A9E0246213DBA79D6CA3C2B00C2691903149700510EADA68E7FF1FE9AF75BCA0 | |||
| 6768 | W95ws2setup.exe | C:\Users\admin\AppData\Local\Temp\MSE000\wsock.vxd | executable | |
MD5:17793DB2732E24CDDFB8EB8BDDBC64C9 | SHA256:6A34A9195F68EDCF9B248A0F9A8E219F2D655D00A47F96E113F746065608347F | |||
| 6768 | W95ws2setup.exe | C:\Users\admin\AppData\Local\Temp\MSE000\WSASRV.exe | executable | |
MD5:6515E4A2E6D10B36395721747D2C9D02 | SHA256:BD30C987EDDEBFE7160182F7922686CC51550D25A9B05967A3A9E0A5CAF21B34 | |||
| 6768 | W95ws2setup.exe | C:\Users\admin\AppData\Local\Temp\MSE000\msafd.dll | executable | |
MD5:59AC0E3167C58D227F54354ADA2D61FE | SHA256:2E0DA87D1A8DD09F899EF316B1DA5AD6A3E15F6EEBF6046D454A18927C6FDE73 | |||
| 6768 | W95ws2setup.exe | C:\Users\admin\AppData\Local\Temp\MSE000\vudp.386 | executable | |
MD5:F0A896FD38A1432CAFC4339876318C83 | SHA256:B94ABEA943223B5CAB482F5A9303A8E80D49613E644EE159579A2B25E70E5E7B | |||
| 6768 | W95ws2setup.exe | C:\Users\admin\AppData\Local\Temp\MSE000\rnr20.dll | executable | |
MD5:9E97AEA459E2D592F30DD09D33EC5279 | SHA256:876FCBEBFA527BC07004AD3D405400490A18F46BB6B7C838AFD3CBE4B42EE1CA | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
9
TCP/UDP connections
33
DNS requests
17
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
— | — | GET | 200 | 2.16.164.42:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
1752 | SIHClient.exe | GET | 200 | 23.52.120.96:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
4712 | MoUsoCoreWorker.exe | GET | 200 | 2.16.164.42:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
4712 | MoUsoCoreWorker.exe | GET | 200 | 23.52.120.96:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
6284 | backgroundTaskHost.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAUZZSZEml49Gjh0j13P68w%3D | unknown | — | — | whitelisted |
1752 | SIHClient.exe | GET | 200 | 23.52.120.96:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 2.23.77.188:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
— | — | GET | 200 | 23.52.120.96:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 2.23.77.188:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
— | — | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
— | — | 2.16.164.42:80 | crl.microsoft.com | Akamai International B.V. | NL | whitelisted |
4712 | MoUsoCoreWorker.exe | 2.16.164.42:80 | crl.microsoft.com | Akamai International B.V. | NL | whitelisted |
4712 | MoUsoCoreWorker.exe | 23.52.120.96:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
— | — | 23.52.120.96:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
— | — | 2.21.65.154:443 | www.bing.com | Akamai International B.V. | NL | whitelisted |
— | — | 2.23.77.188:80 | ocsp.digicert.com | AKAMAI-AS | DE | whitelisted |
1176 | svchost.exe | 40.126.31.73:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
google.com |
| whitelisted |
settings-win.data.microsoft.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
www.bing.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
login.live.com |
| whitelisted |
go.microsoft.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |