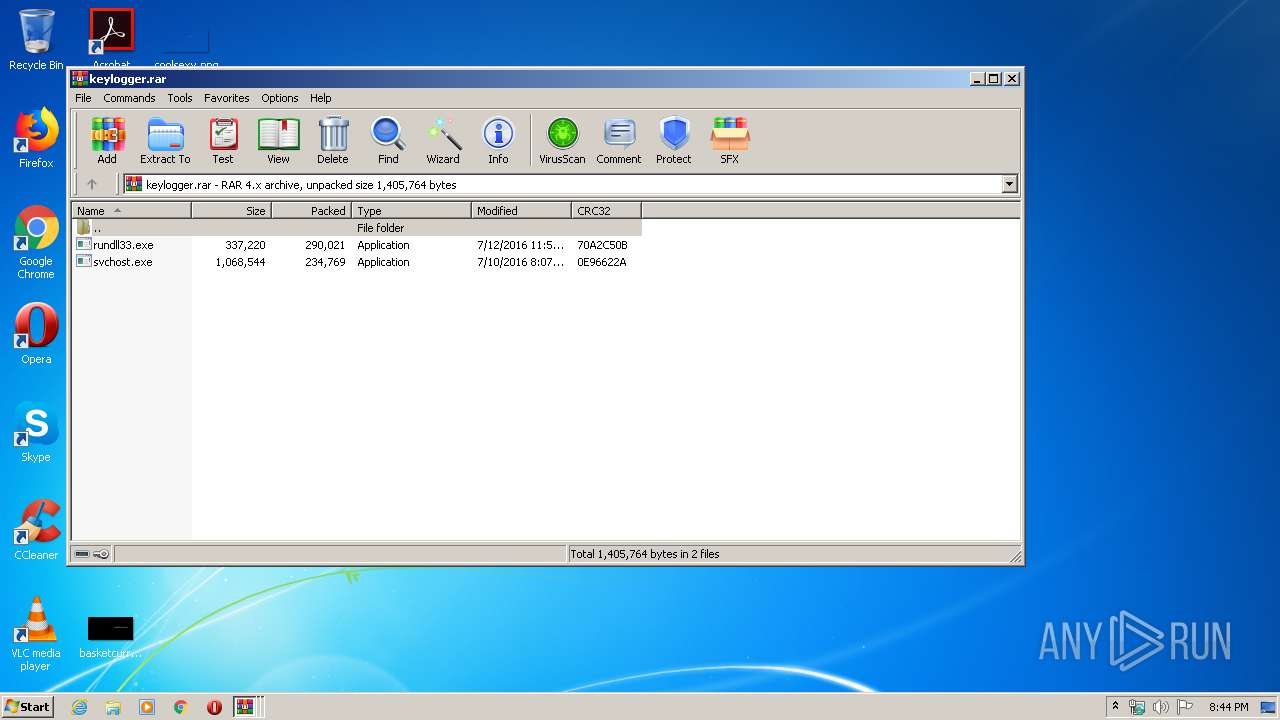
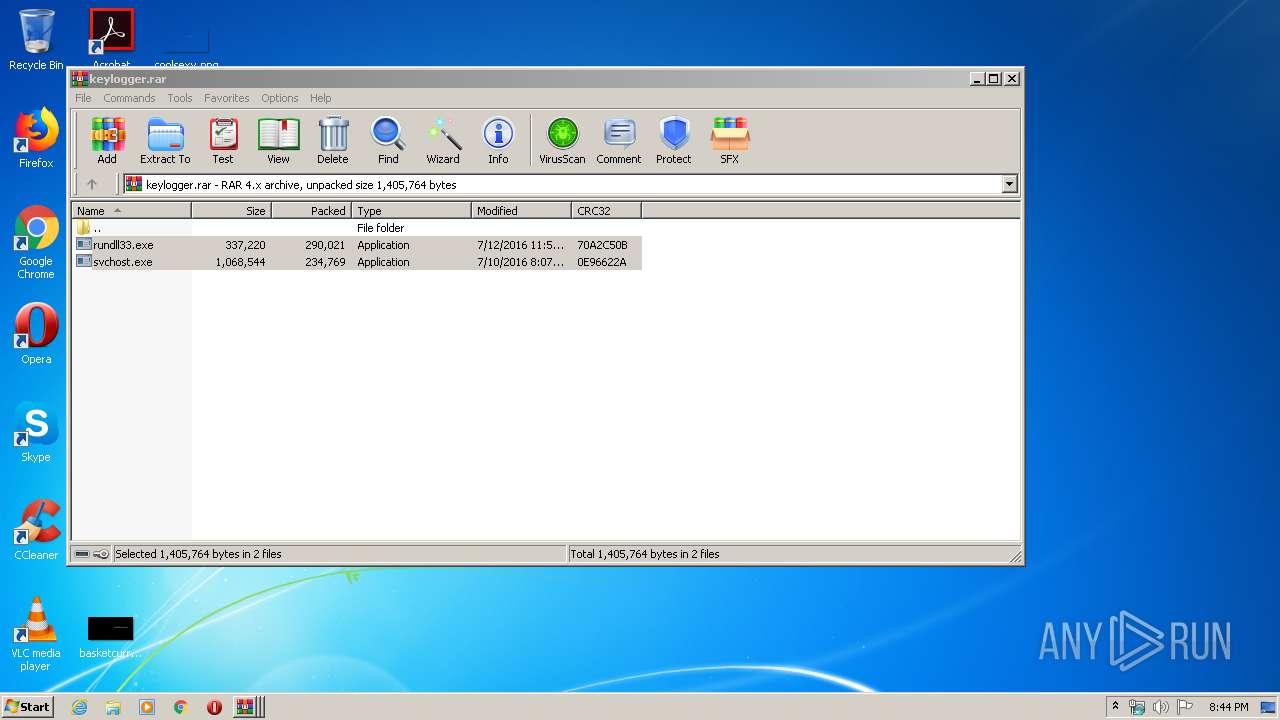
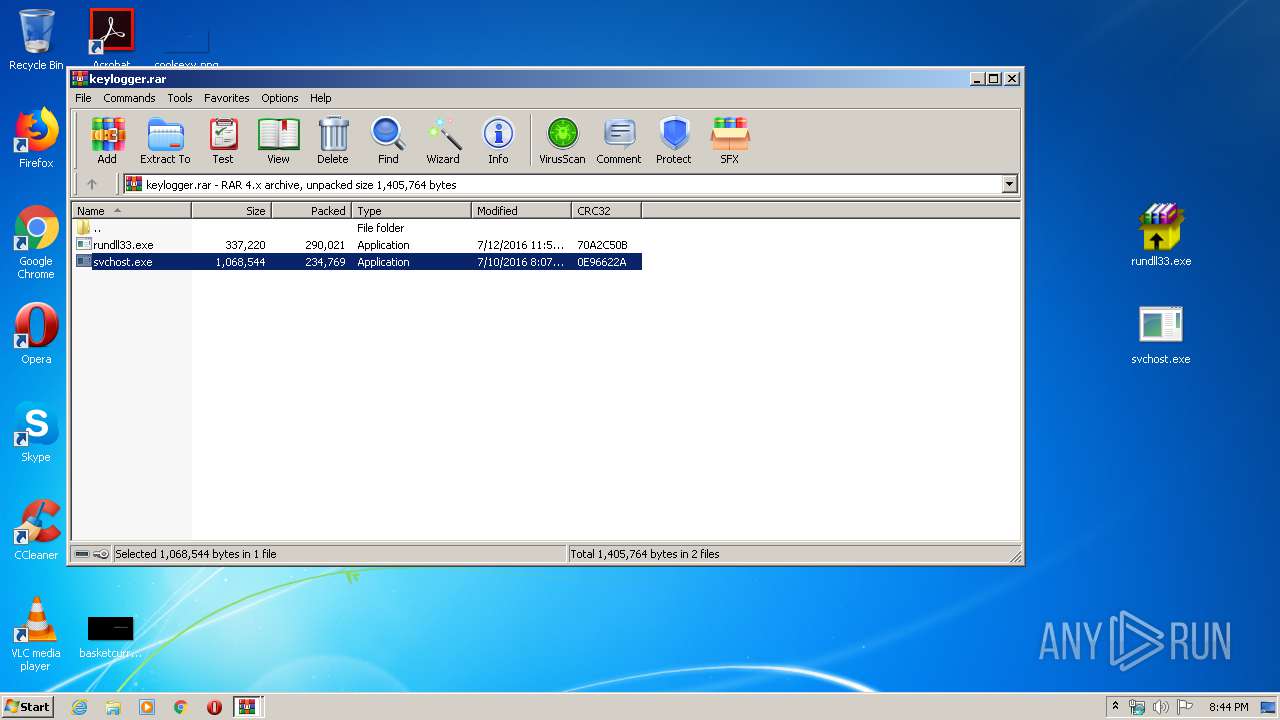
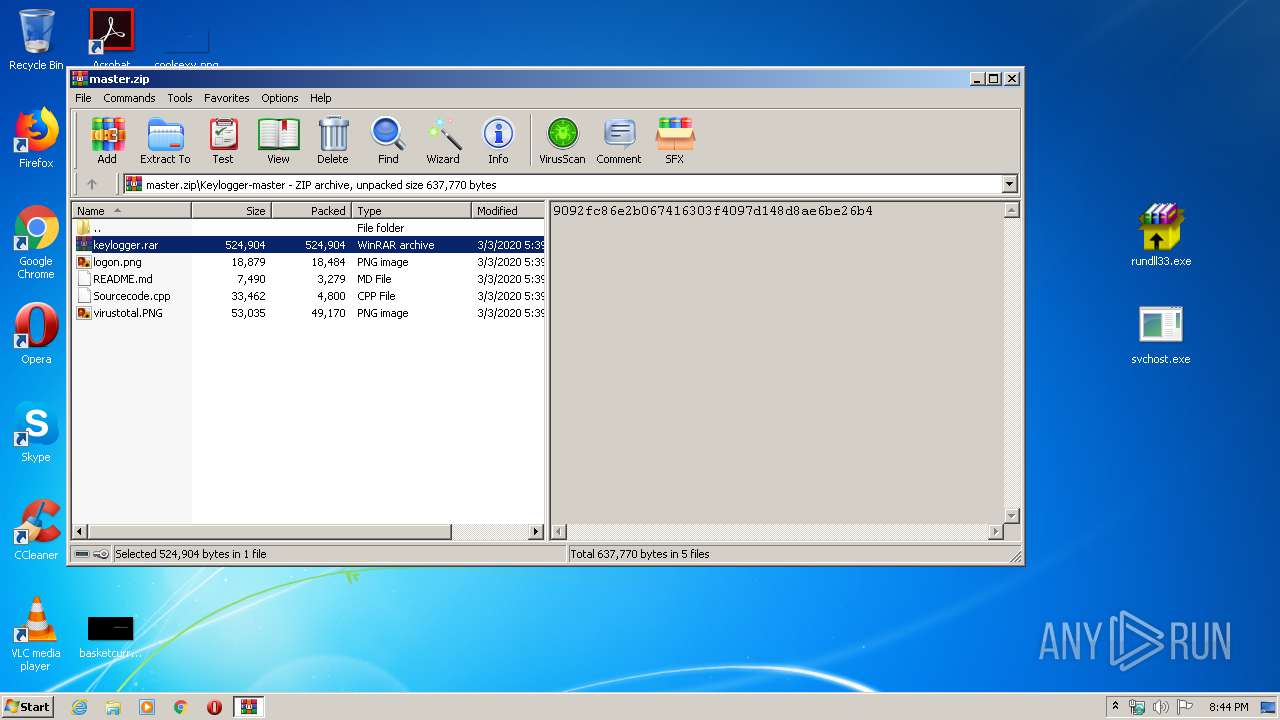
| download: | master.zip |
| Full analysis: | https://app.any.run/tasks/ddce69e5-333b-4a5b-b7fd-a097fc099201 |
| Verdict: | Malicious activity |
| Analysis date: | May 23, 2020, 19:43:42 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v1.0 to extract |
| MD5: | C9FE2C663309A60378C971F92535CD07 |
| SHA1: | 4C50379A80709B8DDEBB93EB2AA462E815215399 |
| SHA256: | 48B467A51548356DB520724B3B7A905822B2DBE9CB53FEA61E93A1DA40C6EB4D |
| SSDEEP: | 12288:y8jORpZLPrrdh6ix6yBQUSAOBU0xsRrU6kKMnKflJYXh87PDdhOW:y8jIrrrdh6is+fSlU0gY6kWsWPDfOW |
MALICIOUS
Application was dropped or rewritten from another process
- svchost.exe (PID: 2056)
- rundll33.exe (PID: 2620)
- rundll33.exe (PID: 3576)
- svchost.exe (PID: 984)
Actions looks like stealing of personal data
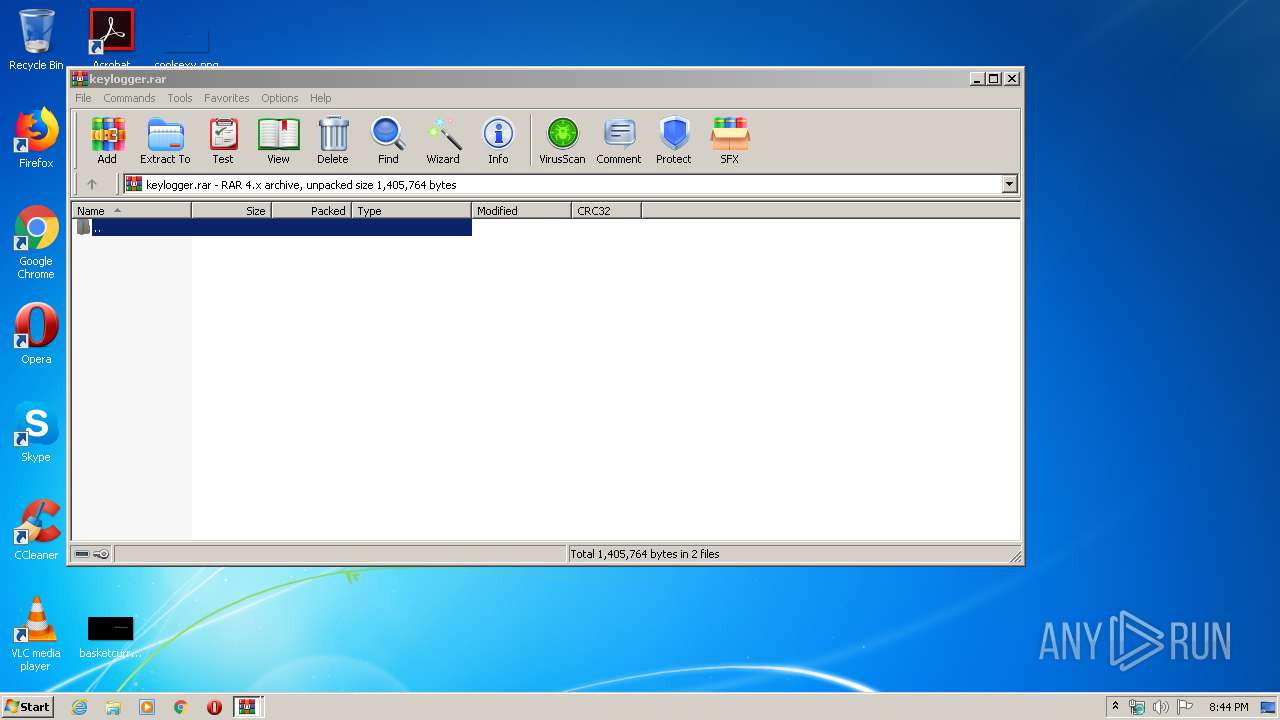
- WinRAR.exe (PID: 1248)
Changes the autorun value in the registry
- svchost.exe (PID: 2056)
- rundll33.exe (PID: 3576)
- svchost.exe (PID: 984)
SUSPICIOUS
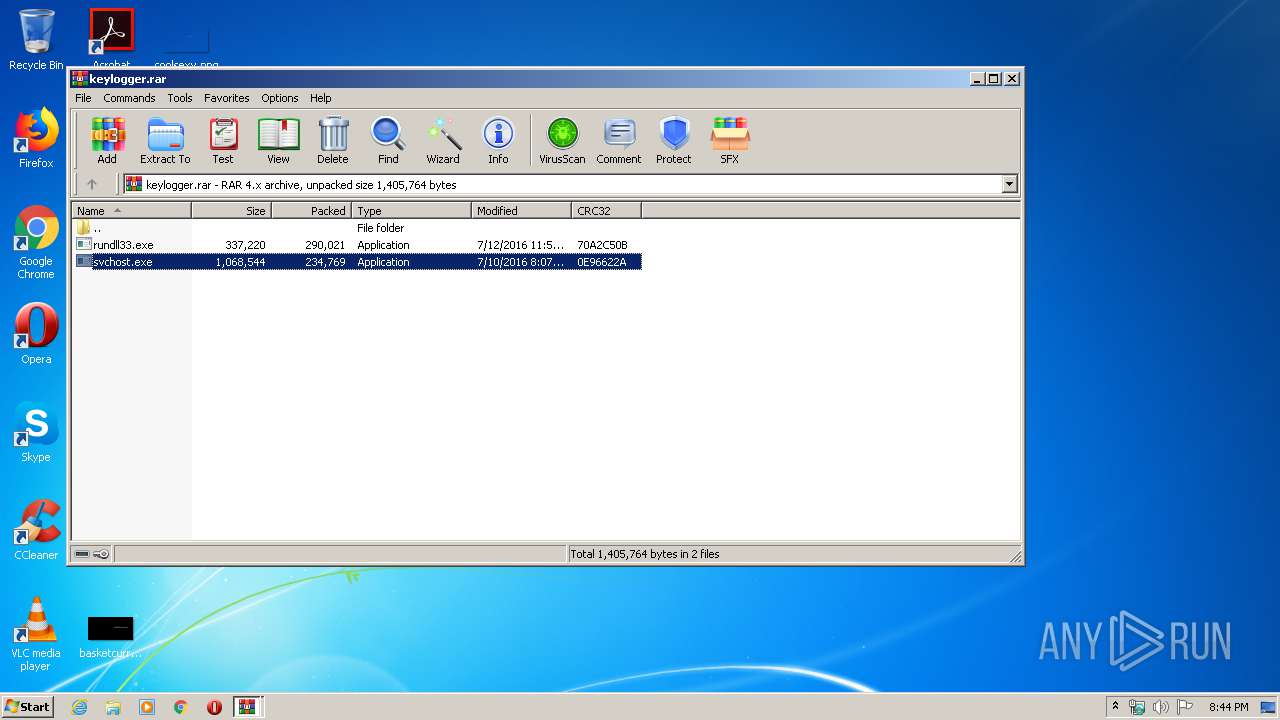
Creates executable files which already exist in Windows
- WinRAR.exe (PID: 3352)
- svchost.exe (PID: 2056)
- WinRAR.exe (PID: 1732)
Executable content was dropped or overwritten
- svchost.exe (PID: 2056)
- WinRAR.exe (PID: 3352)
- svchost.exe (PID: 984)
- rundll33.exe (PID: 2620)
Application launched itself
- WinRAR.exe (PID: 1248)
Creates files in the user directory
- svchost.exe (PID: 2056)
- rundll33.exe (PID: 2620)
- rundll33.exe (PID: 3576)
Reads Internet Cache Settings
- rundll33.exe (PID: 3576)
INFO
Manual execution by user
- svchost.exe (PID: 2056)
- rundll33.exe (PID: 2620)
- svchost.exe (PID: 984)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 10 |
|---|---|
| ZipBitFlag: | - |
| ZipCompression: | None |
| ZipModifyDate: | 2020:03:03 09:39:02 |
| ZipCRC: | 0x00000000 |
| ZipCompressedSize: | - |
| ZipUncompressedSize: | - |
| ZipFileName: | Keylogger-master/ |
Total processes
48
Monitored processes
7
Malicious processes
3
Suspicious processes
2
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 984 | "C:\Users\admin\Desktop\svchost.exe" | C:\Users\admin\Desktop\svchost.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 1248 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\AppData\Local\Temp\master.zip" | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.60.0 Modules
| |||||||||||||||
| 1732 | "C:\Program Files\WinRAR\WinRAR.exe" C:\Users\admin\AppData\Local\Temp\Rar$DIa1248.38838\keylogger.rar | C:\Program Files\WinRAR\WinRAR.exe | — | WinRAR.exe | |||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.60.0 Modules
| |||||||||||||||
| 2056 | "C:\Users\admin\Desktop\svchost.exe" | C:\Users\admin\Desktop\svchost.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 2620 | "C:\Users\admin\Desktop\rundll33.exe" | C:\Users\admin\Desktop\rundll33.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 3352 | "C:\Program Files\WinRAR\WinRAR.exe" C:\Users\admin\AppData\Local\Temp\Rar$DIa1248.38290\keylogger.rar | C:\Program Files\WinRAR\WinRAR.exe | WinRAR.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.60.0 Modules
| |||||||||||||||
| 3576 | "C:\Users\admin\AppData\Roaming\WPDNSE\rundll33.exe" | C:\Users\admin\AppData\Roaming\WPDNSE\rundll33.exe | rundll33.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
Total events
1 803
Read events
1 728
Write events
75
Delete events
0
Modification events
| (PID) Process: | (1248) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (1248) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (1248) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\12D\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (1248) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\12D\52C64B7E |
| Operation: | write | Name: | @C:\Windows\system32\NetworkExplorer.dll,-1 |
Value: Network | |||
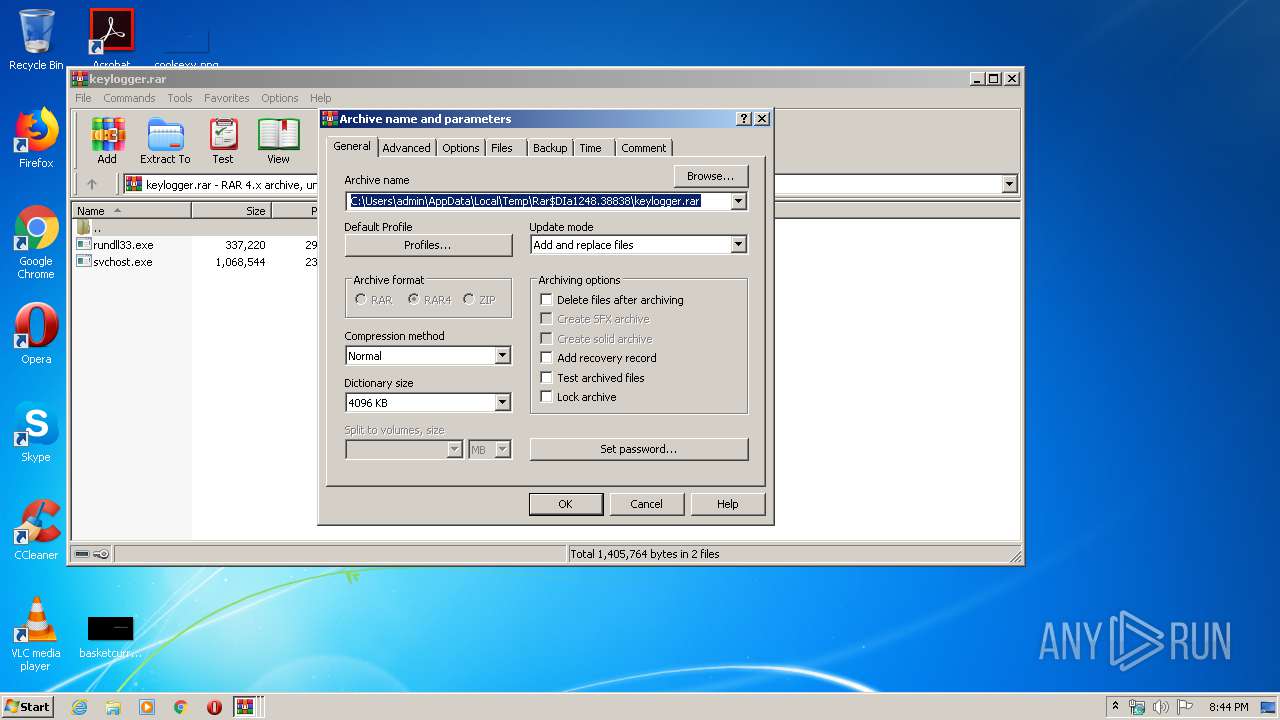
| (PID) Process: | (1248) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\master.zip | |||
| (PID) Process: | (1248) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (1248) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (1248) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (1248) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (3352) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
Executable files
4
Suspicious files
2
Text files
6
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 1732 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa1732.40177\rundll33.exe | — | |
MD5:— | SHA256:— | |||
| 1732 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa1732.40177\svchost.exe | — | |
MD5:— | SHA256:— | |||
| 2056 | svchost.exe | C:\Users\admin\AppData\Roaming\WPDNSE\atapi.sys | text | |
MD5:— | SHA256:— | |||
| 3576 | rundll33.exe | C:\Users\admin\AppData\Roaming\WPDNSE\core32.mni | image | |
MD5:— | SHA256:— | |||
| 984 | svchost.exe | C:\Users\admin\Desktop\log_error.txt | text | |
MD5:— | SHA256:— | |||
| 984 | svchost.exe | C:\Users\admin\AppData\Roaming\WPDNSE\atapi.sys | text | |
MD5:— | SHA256:— | |||
| 3576 | rundll33.exe | C:\Users\admin\AppData\Roaming\WPDNSE\log_error.txt | text | |
MD5:0ED9B635F8AABC919EF0DEE6B49D158F | SHA256:1498CA5FB4FAE3224F05117675208A86856E4ADFDD073501D8D02C6163B43B00 | |||
| 2056 | svchost.exe | C:\Users\admin\Desktop\log_error.txt | text | |
MD5:0ED9B635F8AABC919EF0DEE6B49D158F | SHA256:1498CA5FB4FAE3224F05117675208A86856E4ADFDD073501D8D02C6163B43B00 | |||
| 2056 | svchost.exe | C:\Users\admin\AppData\Roaming\WPDNSE\svchost.exe | executable | |
MD5:80460DB2C846A4115B7F0509A63FB0BD | SHA256:53E57C196CC3C46937947309C9B0988E2C3A7DDB2D19BE9CBA9390AC6D65C069 | |||
| 3352 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa3352.39593\svchost.exe | executable | |
MD5:80460DB2C846A4115B7F0509A63FB0BD | SHA256:53E57C196CC3C46937947309C9B0988E2C3A7DDB2D19BE9CBA9390AC6D65C069 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
0
DNS requests
0
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report