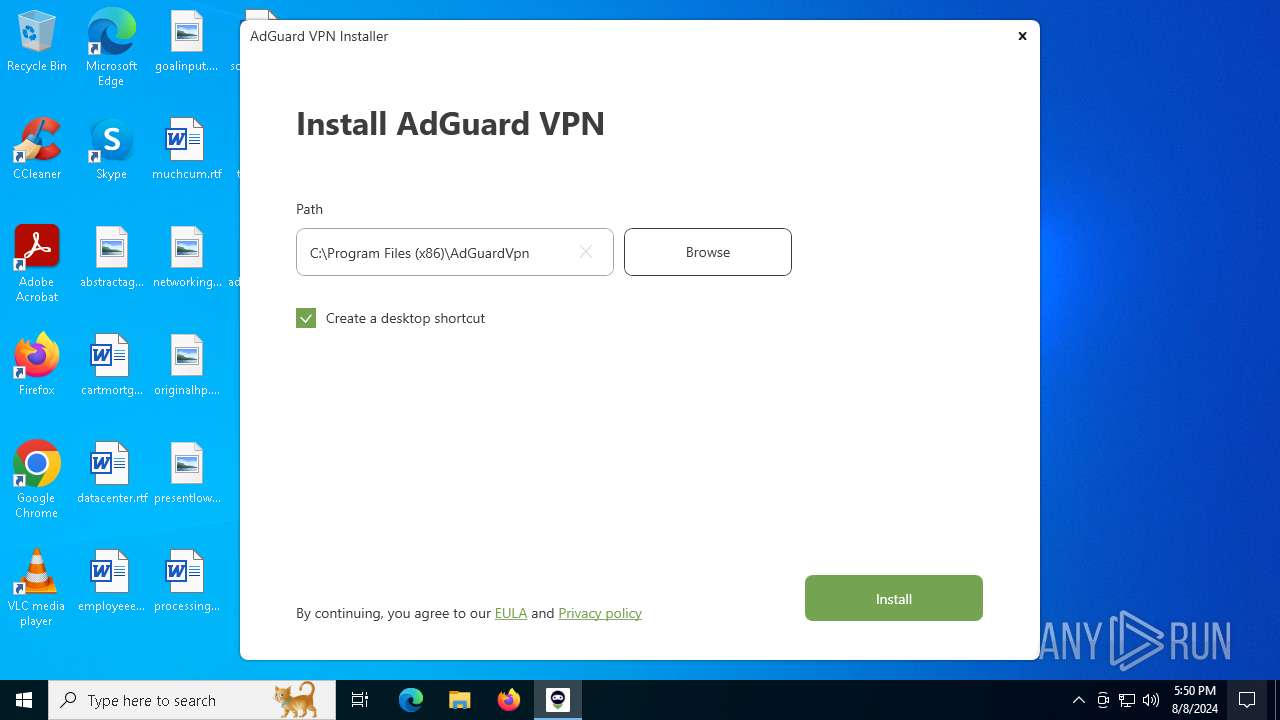
| File name: | adguardVPNInstaller.exe |
| Full analysis: | https://app.any.run/tasks/0a6b0103-0db2-4b60-a53e-2732ba2a9654 |
| Verdict: | Malicious activity |
| Analysis date: | August 08, 2024, 17:50:16 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (GUI) Intel 80386 (stripped to external PDB), for MS Windows |
| MD5: | DEB11446EE45533A7D4CB0513D9FC5CE |
| SHA1: | 31D039AF4D05F23D1A2A4F5A15833ADDD9298979 |
| SHA256: | 48AAC3F78071780B00E9DFBBFC2760B701DD42992F00AD3E6B505E6C88BEEF02 |
| SSDEEP: | 3072:vchRVv3/O4bLrFGJn/xRSPB61FsYqcmPQVkt:vK//O4HmQYqhL |
MALICIOUS
Changes the autorun value in the registry
- installer.exe (PID: 3068)
- ie4uinit.exe (PID: 7896)
- setup.exe (PID: 3188)
Starts NET.EXE for service management
- net.exe (PID: 7600)
- cmd.exe (PID: 8188)
Uses Task Scheduler to run other applications
- cmd.exe (PID: 7312)
SUSPICIOUS
Drops the executable file immediately after the start
- adguardVPNInstaller.exe (PID: 6388)
- setup.exe (PID: 6704)
- setup.exe (PID: 3188)
- installer.exe (PID: 3068)
- msiexec.exe (PID: 4056)
- AdGuardVpnSvc.exe (PID: 1236)
Reads security settings of Internet Explorer
- adguardVPNInstaller.exe (PID: 6388)
- setup.exe (PID: 3188)
- AdGuardVpn.exe (PID: 7824)
Checks Windows Trust Settings
- adguardVPNInstaller.exe (PID: 6388)
- msiexec.exe (PID: 4056)
- AdGuardVpnSvc.exe (PID: 1236)
The process creates files with name similar to system file names
- setup.exe (PID: 3188)
Executable content was dropped or overwritten
- setup.exe (PID: 6704)
- setup.exe (PID: 3188)
- installer.exe (PID: 3068)
- rundll32.exe (PID: 1116)
- rundll32.exe (PID: 6640)
- rundll32.exe (PID: 252)
- rundll32.exe (PID: 7848)
- rundll32.exe (PID: 6212)
- AdGuardVpnSvc.exe (PID: 1236)
- rundll32.exe (PID: 7228)
Process drops legitimate windows executable
- setup.exe (PID: 3188)
- rundll32.exe (PID: 1116)
- rundll32.exe (PID: 6640)
- rundll32.exe (PID: 252)
- rundll32.exe (PID: 7848)
- rundll32.exe (PID: 6212)
- msiexec.exe (PID: 4056)
- rundll32.exe (PID: 7228)
Searches for installed software
- setup.exe (PID: 3188)
- installer.exe (PID: 3068)
Adds/modifies Windows certificates
- msiexec.exe (PID: 4056)
- rundll32.exe (PID: 7848)
Reads the date of Windows installation
- setup.exe (PID: 3188)
Starts itself from another location
- setup.exe (PID: 3188)
Creates a software uninstall entry
- installer.exe (PID: 3068)
Reads the Windows owner or organization settings
- msiexec.exe (PID: 4056)
Executes as Windows Service
- WmiApSrv.exe (PID: 904)
- AdGuardVpnSvc.exe (PID: 1236)
The process checks if it is being run in the virtual environment
- rundll32.exe (PID: 1116)
Starts CMD.EXE for commands execution
- rundll32.exe (PID: 7848)
- AdGuardVpnSvc.exe (PID: 1236)
Drops a system driver (possible attempt to evade defenses)
- AdGuardVpnSvc.exe (PID: 1236)
The process executes via Task Scheduler
- AdGuardVpn.exe (PID: 7824)
Process uses IPCONFIG to clear DNS cache
- cmd.exe (PID: 6712)
Deletes scheduled task without confirmation
- schtasks.exe (PID: 5244)
INFO
Checks proxy server information
- adguardVPNInstaller.exe (PID: 6388)
- setup.exe (PID: 3188)
Creates files or folders in the user directory
- adguardVPNInstaller.exe (PID: 6388)
- msiexec.exe (PID: 4056)
- ie4uinit.exe (PID: 7896)
- AdGuardVpn.exe (PID: 7824)
Reads the computer name
- adguardVPNInstaller.exe (PID: 6388)
- setup.exe (PID: 3188)
- installer.exe (PID: 3068)
- msiexec.exe (PID: 4056)
- msiexec.exe (PID: 7056)
- msiexec.exe (PID: 7316)
- TextInputHost.exe (PID: 7476)
- AdGuardVpnSvc.exe (PID: 1236)
- identity_helper.exe (PID: 2044)
- AdGuardVpn.exe (PID: 7824)
Reads the machine GUID from the registry
- adguardVPNInstaller.exe (PID: 6388)
- setup.exe (PID: 3188)
- msiexec.exe (PID: 4056)
- installer.exe (PID: 3068)
- AdGuardVpnSvc.exe (PID: 1236)
- AdGuardVpn.exe (PID: 7824)
Checks supported languages
- adguardVPNInstaller.exe (PID: 6388)
- setup.exe (PID: 6704)
- setup.exe (PID: 3188)
- installer.exe (PID: 3068)
- msiexec.exe (PID: 4056)
- msiexec.exe (PID: 7056)
- TextInputHost.exe (PID: 7476)
- msiexec.exe (PID: 7316)
- AdGuardVpnSvc.exe (PID: 1236)
- identity_helper.exe (PID: 2044)
- AdGuardVpn.exe (PID: 7824)
Create files in a temporary directory
- adguardVPNInstaller.exe (PID: 6388)
- setup.exe (PID: 3188)
- installer.exe (PID: 3068)
Reads the software policy settings
- adguardVPNInstaller.exe (PID: 6388)
- setup.exe (PID: 3188)
- msiexec.exe (PID: 4056)
- rundll32.exe (PID: 7848)
- AdGuardVpnSvc.exe (PID: 1236)
Reads Environment values
- setup.exe (PID: 3188)
- identity_helper.exe (PID: 2044)
- AdGuardVpnSvc.exe (PID: 1236)
- AdGuardVpn.exe (PID: 7824)
Disables trace logs
- setup.exe (PID: 3188)
Creates files in the program directory
- setup.exe (PID: 3188)
- installer.exe (PID: 3068)
- rundll32.exe (PID: 7848)
- AdGuardVpnSvc.exe (PID: 1236)
- AdGuardVpn.exe (PID: 7824)
Process checks computer location settings
- setup.exe (PID: 3188)
Executable content was dropped or overwritten
- msiexec.exe (PID: 4056)
Reads the time zone
- rundll32.exe (PID: 1116)
Creates a software uninstall entry
- msiexec.exe (PID: 4056)
Reads security settings of Internet Explorer
- ie4uinit.exe (PID: 7896)
Manual execution by a user
- msedge.exe (PID: 3372)
Application launched itself
- msedge.exe (PID: 3372)
- msedge.exe (PID: 8156)
Reads Microsoft Office registry keys
- msedge.exe (PID: 3372)
- msedge.exe (PID: 8156)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win32 Executable MS Visual C++ (generic) (67.4) |
|---|---|---|
| .dll | | | Win32 Dynamic Link Library (generic) (14.2) |
| .exe | | | Win32 Executable (generic) (9.7) |
| .exe | | | Generic Win/DOS Executable (4.3) |
| .exe | | | DOS Executable Generic (4.3) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2022:12:07 14:17:23+00:00 |
| ImageFileCharacteristics: | Executable, No line numbers, No symbols, 32-bit, No debug |
| PEType: | PE32 |
| LinkerVersion: | 2.39 |
| CodeSize: | 45568 |
| InitializedDataSize: | 102912 |
| UninitializedDataSize: | 3072 |
| EntryPoint: | 0x14b0 |
| OSVersion: | 4 |
| ImageVersion: | 1 |
| SubsystemVersion: | 4 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 1.0.0.0 |
| ProductVersionNumber: | 1.0.0.0 |
| FileFlagsMask: | 0x0000 |
| FileFlags: | (none) |
| FileOS: | Unknown (0) |
| ObjectFileType: | Unknown |
| FileSubtype: | - |
| LanguageCode: | English (U.S.) |
| CharacterSet: | Unicode |
| FileDescription: | AdGuard Web Installer |
| LegalCopyright: | (C) 2009-2018 Adguard Software Ltd |
| ProductName: | AdGuard Web Installer |
| ProductVersion: | 1 |
| CompanyName: | Adguard Software Ltd |
Total processes
208
Monitored processes
69
Malicious processes
10
Suspicious processes
5
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 252 | rundll32.exe "C:\WINDOWS\Installer\MSIE9E1.tmp",zzzzInvokeManagedCustomActionOutOfProc SfxCA_978046 35 AdGuardVpn.CustomActions!AdGuardVpn.CustomActions.CustomActions.OnInstallInitialize | C:\Windows\SysWOW64\rundll32.exe | msiexec.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows host process (Rundll32) Exit code: 0 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 460 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=renderer --no-appcompat-clear --lang=en-US --js-flags=--ms-user-locale= --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=18 --mojo-platform-channel-handle=5528 --field-trial-handle=2284,i,722886293829977384,13066205816754884088,262144 --variations-seed-version /prefetch:1 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Version: 122.0.2365.59 Modules
| |||||||||||||||
| 872 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | sc.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 904 | C:\WINDOWS\system32\wbem\WmiApSrv.exe | C:\Windows\System32\wbem\WmiApSrv.exe | — | services.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: WMI Performance Reverse Adapter Exit code: 0 Version: 10.0.19041.3758 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1116 | rundll32.exe "C:\WINDOWS\Installer\MSID424.tmp",zzzzInvokeManagedCustomActionOutOfProc SfxCA_972437 2 AdGuardVpn.CustomActions!AdGuardVpn.CustomActions.CustomActions.OnFirstInstall | C:\Windows\SysWOW64\rundll32.exe | msiexec.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows host process (Rundll32) Exit code: 0 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1236 | "C:\Program Files (x86)\AdGuardVpn\AdGuardVpnSvc.exe" | C:\Program Files (x86)\AdGuardVpn\AdGuardVpnSvc.exe | services.exe | ||||||||||||
User: SYSTEM Company: Adguard Software Limited Integrity Level: SYSTEM Description: AdGuard VPN for Windows Version: 2.3.1464.0 Modules
| |||||||||||||||
| 1528 | "sc" sdset "Adguard VPN Service" D:(A;;CCLCSWRPWPDTLOCRRC;;;SY)(A;;CCDCLCSWRPWPDTLOCRSDRCWDWO;;;BA)(A;;CCRPLCSWLOCRRC;;;IU)(A;;CCLCSWLOCRRC;;;SU)S:(AU;FA;CCDCLCSWRPWPDTLOCRSDRCWDWO;;;WD) | C:\Windows\SysWOW64\sc.exe | — | AdGuardVpnSvc.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Service Control Manager Configuration Tool Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1692 | "sc" query adgvpnnetworktdidrv | C:\Windows\SysWOW64\sc.exe | — | setup.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Service Control Manager Configuration Tool Exit code: 1060 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1884 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=crashpad-handler "--user-data-dir=C:\Users\admin\AppData\Local\Microsoft\Edge\User Data" /prefetch:4 --monitor-self-annotation=ptype=crashpad-handler "--database=C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Crashpad" --annotation=IsOfficialBuild=1 --annotation=channel= --annotation=chromium-version=122.0.6261.70 "--annotation=exe=C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --annotation=plat=Win64 "--annotation=prod=Microsoft Edge" --annotation=ver=122.0.2365.59 --initial-client-data=0x1e8,0x1c0,0x1e0,0x168,0x2a0,0x7fffd35a5fd8,0x7fffd35a5fe4,0x7fffd35a5ff0 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Edge Version: 122.0.2365.59 Modules
| |||||||||||||||
| 2044 | "C:\Program Files (x86)\Microsoft\Edge\Application\122.0.2365.59\identity_helper.exe" --type=utility --utility-sub-type=winrt_app_id.mojom.WinrtAppIdService --lang=en-US --service-sandbox-type=none --no-appcompat-clear --mojo-platform-channel-handle=4980 --field-trial-handle=2284,i,722886293829977384,13066205816754884088,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\122.0.2365.59\identity_helper.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: PWA Identity Proxy Host Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
Total events
40 403
Read events
40 046
Write events
331
Delete events
26
Modification events
| (PID) Process: | (6388) adguardVPNInstaller.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Content |
| Operation: | write | Name: | CachePrefix |
Value: | |||
| (PID) Process: | (6388) adguardVPNInstaller.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (6388) adguardVPNInstaller.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
| (PID) Process: | (6388) adguardVPNInstaller.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (6388) adguardVPNInstaller.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
| (PID) Process: | (6388) adguardVPNInstaller.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 1 | |||
| (PID) Process: | (6388) adguardVPNInstaller.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 0 | |||
| (PID) Process: | (3188) setup.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Tracing |
| Operation: | write | Name: | EnableConsoleTracing |
Value: 0 | |||
| (PID) Process: | (3188) setup.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Tracing\setup_RASAPI32 |
| Operation: | write | Name: | EnableFileTracing |
Value: 0 | |||
| (PID) Process: | (3188) setup.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Tracing\setup_RASAPI32 |
| Operation: | write | Name: | EnableAutoFileTracing |
Value: 0 | |||
Executable files
319
Suspicious files
462
Text files
152
Unknown types
4
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 6388 | adguardVPNInstaller.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\INetCache\IE\KCV3KQBA\installer[1].exe | — | |
MD5:— | SHA256:— | |||
| 6388 | adguardVPNInstaller.exe | C:\Users\admin\AppData\Local\Temp\adguard\setup.exe | — | |
MD5:— | SHA256:— | |||
| 3188 | setup.exe | C:\Windows\Temp\{0CD3A895-DAD9-4384-910A-399D1CDFE7DB}\.ba\BootstrapperCore.dll | executable | |
MD5:B0D10A2A622A322788780E7A3CBB85F3 | SHA256:F2C2B3CE2DF70A3206F3111391FFC7B791B32505FA97AEF22C0C2DBF6F3B0426 | |||
| 3188 | setup.exe | C:\Windows\Temp\{0CD3A895-DAD9-4384-910A-399D1CDFE7DB}\.ba\mbahost.dll | executable | |
MD5:C59832217903CE88793A6C40888E3CAE | SHA256:9DFA1BC5D2AB4C652304976978749141B8C312784B05CB577F338A0AA91330DB | |||
| 6704 | setup.exe | C:\Windows\Temp\{87C86B7E-EAF7-4870-9CB7-87A2929DCAE8}\.cr\setup.exe | executable | |
MD5:BDD2706A63B0A996731D1398182E02AE | SHA256:6A7D13333E576B8A07AF161EDAEF4F4AB728026C57A32881359C1FCD0C7881FE | |||
| 3188 | setup.exe | C:\Windows\Temp\{0CD3A895-DAD9-4384-910A-399D1CDFE7DB}\.ba\1032\mbapreq.wxl | xml | |
MD5:074D5921AF07E6126049CB45814246ED | SHA256:B8E90E20EDF110AAAAEA54FBC8533872831777BE5589E380CFDD17E1F93147B5 | |||
| 3188 | setup.exe | C:\Windows\Temp\{0CD3A895-DAD9-4384-910A-399D1CDFE7DB}\.ba\1030\mbapreq.wxl | xml | |
MD5:7C6E4CE87870B3B5E71D3EF4555500F8 | SHA256:CAC263E0E90A4087446A290055257B1C39F17E11F065598CB2286DF4332C7696 | |||
| 3188 | setup.exe | C:\Windows\Temp\{0CD3A895-DAD9-4384-910A-399D1CDFE7DB}\.ba\1038\mbapreq.wxl | xml | |
MD5:17FB605A2F02DA203DF06F714D1CC6DE | SHA256:55CF62D54EFB79801A9D94B24B3C9BA221C2465417A068950D40A67C52BA66EF | |||
| 3188 | setup.exe | C:\Windows\Temp\{0CD3A895-DAD9-4384-910A-399D1CDFE7DB}\.ba\mbapreq.wxl | xml | |
MD5:4D2C8D10C5DCCA6B938B71C8F02CA8A8 | SHA256:C63DE5F309502F9272402587A6BE22624D1BC2FEACD1BD33FB11E44CD6614B96 | |||
| 3188 | setup.exe | C:\Windows\Temp\{0CD3A895-DAD9-4384-910A-399D1CDFE7DB}\.ba\AdGuardVpn.Burn.dll | executable | |
MD5:0CFD8FAF4A9303F57D64A615519F5DAE | SHA256:586557532484F320308B76E1849EFE54456F367B1F22BB5707AD319B75CCF2F2 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
11
TCP/UDP connections
109
DNS requests
98
Threats
4
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
6388 | adguardVPNInstaller.exe | GET | 301 | 212.102.56.178:80 | http://static.adtidy.net/windows/installer.exe | unknown | — | — | whitelisted |
4772 | svchost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
4772 | svchost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
6948 | backgroundTaskHost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | whitelisted |
5336 | SearchApp.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
6988 | backgroundTaskHost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | whitelisted |
3188 | setup.exe | GET | 301 | 212.102.56.179:80 | http://static.adguard.com/installer.v1.0.json | unknown | — | — | whitelisted |
4056 | msiexec.exe | GET | 200 | 172.64.149.23:80 | http://ocsp.sectigo.com/MFIwUDBOMEwwSjAJBgUrDgMCGgUABBQVD%2BnGf79Hpedv3mhy6uKMVZkPCQQUDyrLIIcouOxvSK4rVKYpqhekzQwCEQCxOOZmDcp8w3fLL29gJ%2FYW | unknown | — | — | whitelisted |
4056 | msiexec.exe | GET | 200 | 172.64.149.23:80 | http://ocsp.sectigo.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSdE3gf41WAic8Uh9lF92%2BIJqh5qwQUMuuSmv81lkgvKEBCcCA2kVwXheYCEGIdbQxSAZ47kHkVIIkhHAo%3D | unknown | — | — | whitelisted |
4056 | msiexec.exe | GET | 200 | 172.64.149.23:80 | http://ocsp.comodoca.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBRTtU9uFqgVGHhJwXZyWCNXmVR5ngQUoBEKIz6W8Qfs4q8p74Klf9AwpLQCEEj8k7RgVZSNNqfJionWlBY%3D | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
5240 | svchost.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
3888 | svchost.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
1120 | RUXIMICS.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
2120 | MoUsoCoreWorker.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
6388 | adguardVPNInstaller.exe | 212.102.56.178:80 | static.adtidy.net | Datacamp Limited | DE | unknown |
6388 | adguardVPNInstaller.exe | 212.102.56.178:443 | static.adtidy.net | Datacamp Limited | DE | unknown |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
5240 | svchost.exe | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
5336 | SearchApp.exe | 184.86.251.19:443 | www.bing.com | Akamai International B.V. | DE | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
static.adtidy.net |
| unknown |
www.bing.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
login.live.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
th.bing.com |
| whitelisted |
fd.api.iris.microsoft.com |
| whitelisted |
arc.msn.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
6388 | adguardVPNInstaller.exe | A Network Trojan was detected | ET MALWARE Potential Dridex.Maldoc Minimal Executable Request |
7848 | rundll32.exe | Misc activity | ET INFO Observed Cloudflare DNS over HTTPS Domain (cloudflare-dns .com in TLS SNI) |
7848 | rundll32.exe | Misc activity | ET INFO Observed DNS Over HTTPS Domain (dns .alidns .com in TLS SNI) |
7848 | rundll32.exe | Misc activity | ET INFO Observed Google DNS over HTTPS Domain (dns .google in TLS SNI) |
Process | Message |
|---|---|
AdGuardVpnSvc.exe | Native library pre-loader is trying to load native SQLite library "C:\Program Files (x86)\AdGuardVpn\x86\SQLite.Interop.dll"...
|