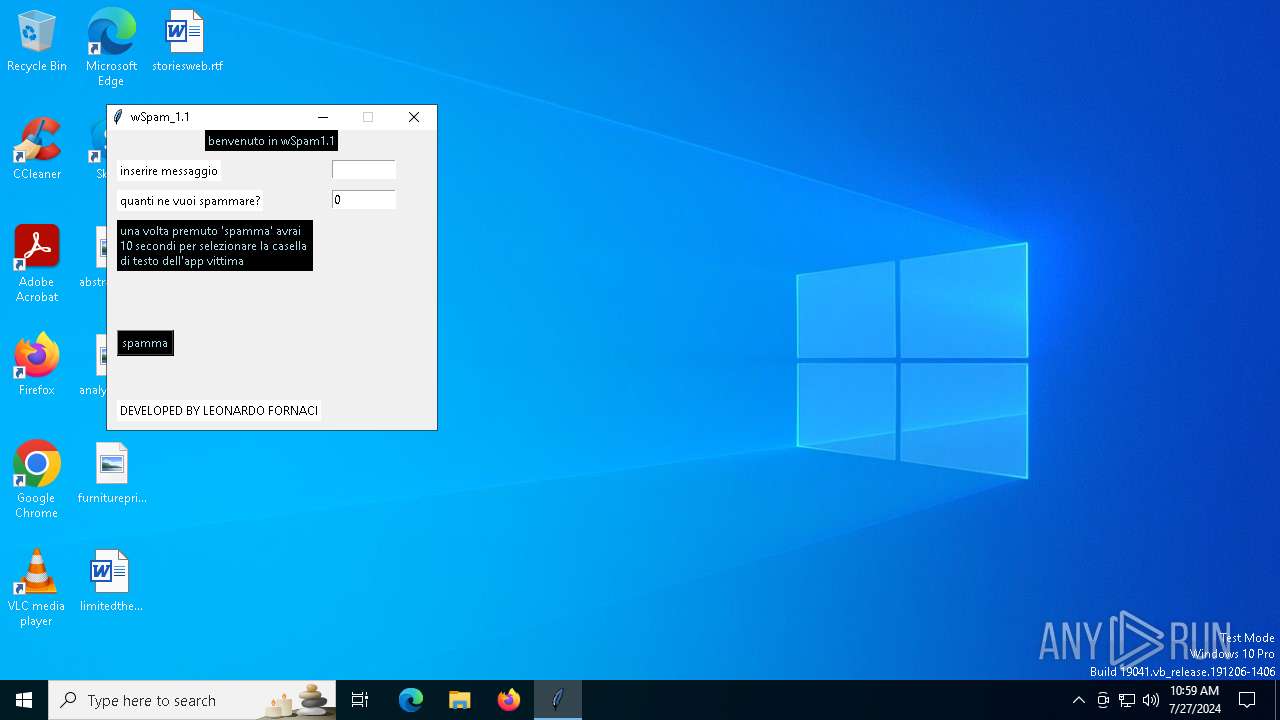
| File name: | wSpam1.1.exe |
| Full analysis: | https://app.any.run/tasks/fdc219af-9bd9-4a03-92e0-f14e23bdd791 |
| Verdict: | Malicious activity |
| Analysis date: | July 27, 2024, 10:58:59 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32+ executable (GUI) x86-64, for MS Windows |
| MD5: | 0A6CFC7C55A66793DD61734E855948AB |
| SHA1: | 88FBA9035DCD422B12610F12D6DBE2C3B0164A5C |
| SHA256: | 48A1672EEF39C1F4D3330BEB8737C13C0630066B7E7F6C803CFB6E5CDD903645 |
| SSDEEP: | 196608:qMc6x6mQTqvueYgB6R7yUPS0G3lCMCBcMKzHgrjTQeq7PM:bpx6mQTguXgOPiL1HgrjTQeq7 |
MALICIOUS
Drops the executable file immediately after the start
- wSpam1.1.exe (PID: 6872)
SUSPICIOUS
Process drops python dynamic module
- wSpam1.1.exe (PID: 6872)
Executable content was dropped or overwritten
- wSpam1.1.exe (PID: 6872)
There is functionality for taking screenshot (YARA)
- wSpam1.1.exe (PID: 4468)
Loads Python modules
- wSpam1.1.exe (PID: 4468)
The process drops C-runtime libraries
- wSpam1.1.exe (PID: 6872)
Application launched itself
- wSpam1.1.exe (PID: 6872)
Process drops legitimate windows executable
- wSpam1.1.exe (PID: 6872)
INFO
Reads the machine GUID from the registry
- wSpam1.1.exe (PID: 4468)
Reads the software policy settings
- slui.exe (PID: 5696)
Checks supported languages
- wSpam1.1.exe (PID: 6872)
- wSpam1.1.exe (PID: 4468)
Checks proxy server information
- slui.exe (PID: 5696)
Reads the computer name
- wSpam1.1.exe (PID: 4468)
- wSpam1.1.exe (PID: 6872)
Create files in a temporary directory
- wSpam1.1.exe (PID: 6872)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win64 Executable (generic) (87.3) |
|---|---|---|
| .exe | | | Generic Win/DOS Executable (6.3) |
| .exe | | | DOS Executable Generic (6.3) |
EXIF
EXE
| MachineType: | AMD AMD64 |
|---|---|
| TimeStamp: | 2020:08:08 12:28:52+00:00 |
| ImageFileCharacteristics: | Executable, Large address aware |
| PEType: | PE32+ |
| LinkerVersion: | 14 |
| CodeSize: | 133120 |
| InitializedDataSize: | 180224 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x8808 |
| OSVersion: | 5.2 |
| ImageVersion: | - |
| SubsystemVersion: | 5.2 |
| Subsystem: | Windows GUI |
Total processes
135
Monitored processes
3
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 4468 | "C:\Users\admin\Desktop\wSpam1.1.exe" | C:\Users\admin\Desktop\wSpam1.1.exe | wSpam1.1.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Modules
| |||||||||||||||
| 5696 | C:\WINDOWS\System32\slui.exe -Embedding | C:\Windows\System32\slui.exe | svchost.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Activation Client Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6872 | "C:\Users\admin\Desktop\wSpam1.1.exe" | C:\Users\admin\Desktop\wSpam1.1.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Modules
| |||||||||||||||
Total events
3 811
Read events
3 811
Write events
0
Delete events
0
Modification events
Executable files
43
Suspicious files
5
Text files
915
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 6872 | wSpam1.1.exe | C:\Users\admin\AppData\Local\Temp\_MEI68722\_asyncio.pyd | executable | |
MD5:05F37B6BE4CD6B5DC8F165128913CF89 | SHA256:0ED512E410A8604821F74C84396DD61E71756DBE8E36E8A96261C707B659721A | |||
| 6872 | wSpam1.1.exe | C:\Users\admin\AppData\Local\Temp\_MEI68722\_decimal.pyd | executable | |
MD5:CE4DF4DFE65AB8DC7AE6FCDEBAE46112 | SHA256:FFBE84F0A1EAB363CA9CF73EFB7518F2ABD52C0893C7CC63266613C930855E96 | |||
| 6872 | wSpam1.1.exe | C:\Users\admin\AppData\Local\Temp\_MEI68722\_lzma.pyd | executable | |
MD5:B5355DD319FB3C122BB7BF4598AD7570 | SHA256:B9BC7F1D8AA8498CB8B5DC75BB0DBB6E721B48953A3F295870938B27267FB5F5 | |||
| 6872 | wSpam1.1.exe | C:\Users\admin\AppData\Local\Temp\_MEI68722\libopenblas.QVLO2T66WEPI7JZ63PS3HMOHFEY472BC.gfortran-win_amd64.dll | — | |
MD5:— | SHA256:— | |||
| 6872 | wSpam1.1.exe | C:\Users\admin\AppData\Local\Temp\_MEI68722\_ssl.pyd | executable | |
MD5:EF4755195CC9B2FF134EA61ACDE20637 | SHA256:8A86957B3496C8B679FCF22C287006108BFE0BB0AAFFEA17121C761A0744B470 | |||
| 6872 | wSpam1.1.exe | C:\Users\admin\AppData\Local\Temp\_MEI68722\_overlapped.pyd | executable | |
MD5:BF495600C3D758141BED531FAABF2A4F | SHA256:AF74C3FC4BC87E1ED70E11A700A073DF77C4C891B6FAD17A9F019DF0D32C18FC | |||
| 6872 | wSpam1.1.exe | C:\Users\admin\AppData\Local\Temp\_MEI68722\PIL\_imagingft.cp39-win_amd64.pyd | executable | |
MD5:23237B7491F4C8C45C5665C0977AFB23 | SHA256:01EB05EB596BC0A740DCF8493EF3B07C8395ACE457E543299A150F4852D293E4 | |||
| 6872 | wSpam1.1.exe | C:\Users\admin\AppData\Local\Temp\_MEI68722\_socket.pyd | executable | |
MD5:F5DD9C5922A362321978C197D3713046 | SHA256:4494992665305FC9401ED327398EE40064FE26342FE44DF11D89D2AC1CC6F626 | |||
| 6872 | wSpam1.1.exe | C:\Users\admin\AppData\Local\Temp\_MEI68722\_testcapi.pyd | executable | |
MD5:302EB737314834FC2C0F33C26D18BFB5 | SHA256:7A3F795EA5663E42BD46315D7F334739DA9C108C436B403DE1CF3FD190986311 | |||
| 6872 | wSpam1.1.exe | C:\Users\admin\AppData\Local\Temp\_MEI68722\_bz2.pyd | executable | |
MD5:6C7565C1EFFFE44CB0616F5B34FAA628 | SHA256:FE63361F6C439C6AA26FD795AF3FD805FF5B60B3B14F9B8C60C50A8F3449060A | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
3
TCP/UDP connections
22
DNS requests
9
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
— | — | POST | 500 | 40.91.76.224:443 | https://activation-v2.sls.microsoft.com/SLActivateProduct/SLActivateProduct.asmx?configextension=Retail | unknown | xml | 512 b | unknown |
— | — | POST | 200 | 13.89.178.26:443 | https://self.events.data.microsoft.com/OneCollector/1.0/ | unknown | binary | 9 b | unknown |
— | — | POST | — | 40.91.76.224:443 | https://activation-v2.sls.microsoft.com/SLActivateProduct/SLActivateProduct.asmx?configextension=Retail | unknown | — | — | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
3392 | svchost.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
6012 | MoUsoCoreWorker.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
— | — | 131.253.33.254:443 | a-ring-fallback.msedge.net | MICROSOFT-CORP-MSN-AS-BLOCK | US | unknown |
— | — | 184.86.251.4:443 | www.bing.com | Akamai International B.V. | DE | unknown |
6716 | slui.exe | 40.91.76.224:443 | activation-v2.sls.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
1340 | RUXIMICS.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
— | — | 40.91.76.224:443 | activation-v2.sls.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
3952 | svchost.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
t-ring-fdv2.msedge.net |
| unknown |
a-ring-fallback.msedge.net |
| unknown |
www.bing.com |
| whitelisted |
google.com |
| whitelisted |
self.events.data.microsoft.com |
| whitelisted |
activation-v2.sls.microsoft.com |
| whitelisted |