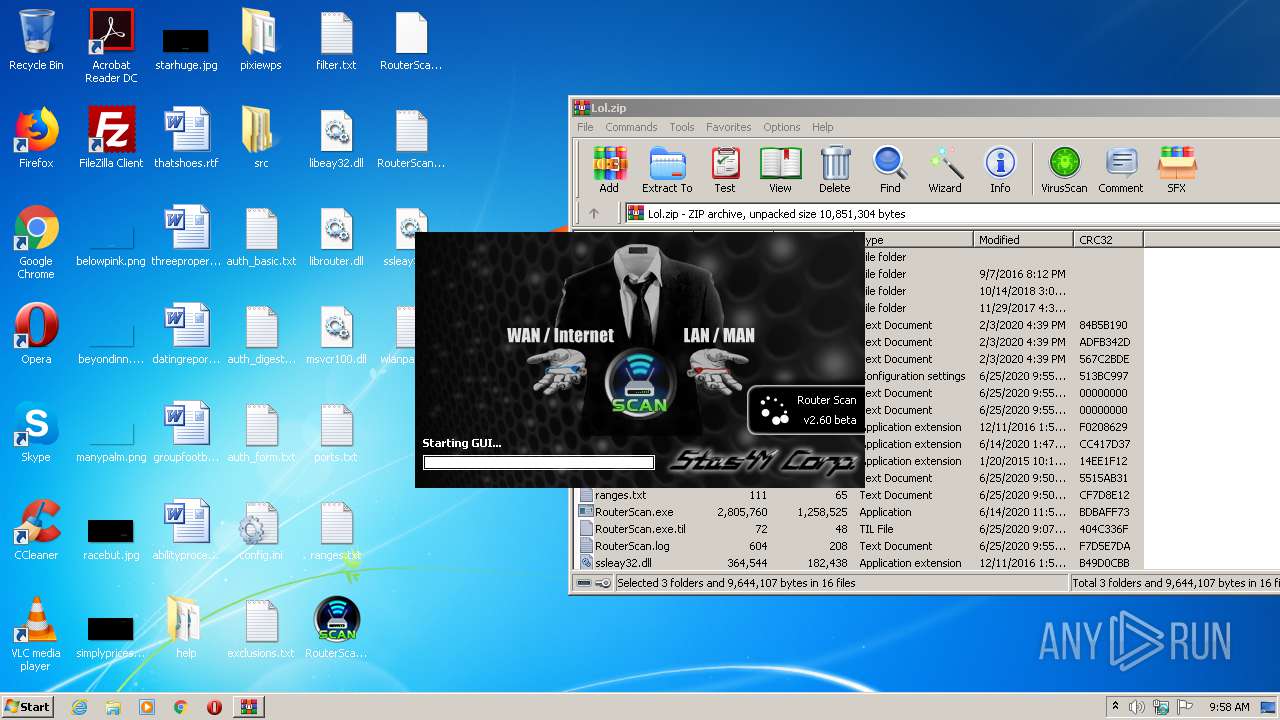
| File name: | Lol.zip |
| Full analysis: | https://app.any.run/tasks/6df87567-922e-4108-b4fa-152017bbaba1 |
| Verdict: | Malicious activity |
| Analysis date: | June 25, 2020, 08:58:26 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v1.0 to extract |
| MD5: | 7FE72729060A4246D85113E44CA9C867 |
| SHA1: | 3F4CD1976CCC2E9CE4B5E7A0BAF8964224384266 |
| SHA256: | 489BD45FABDDE41E75496EDB2071DAE617F3ED5B5E775BCBC36F0377886391C3 |
| SSDEEP: | 98304:iBEBG3/t7CN1VoZQ6I04z7gRqKV/RQ07wKHka0C81qd3hRr:iBEUAfyTNM7gRqUJQ0UJJqRr |
MALICIOUS
Application was dropped or rewritten from another process
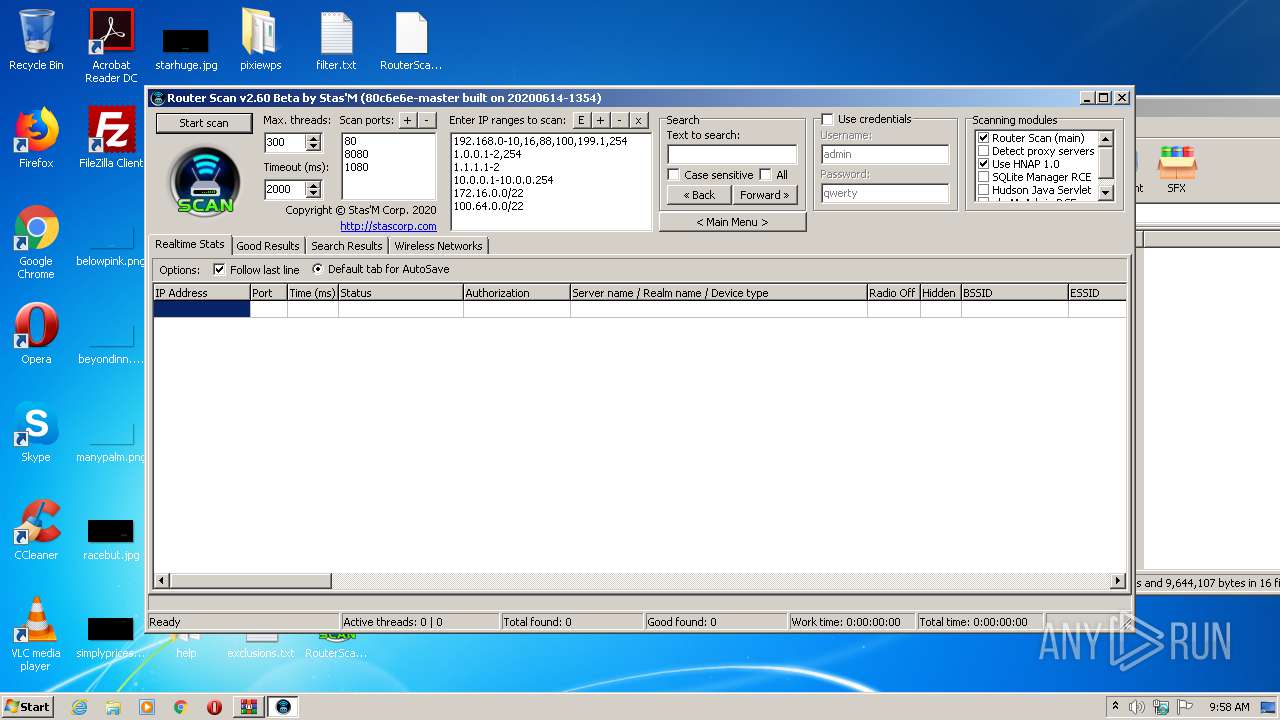
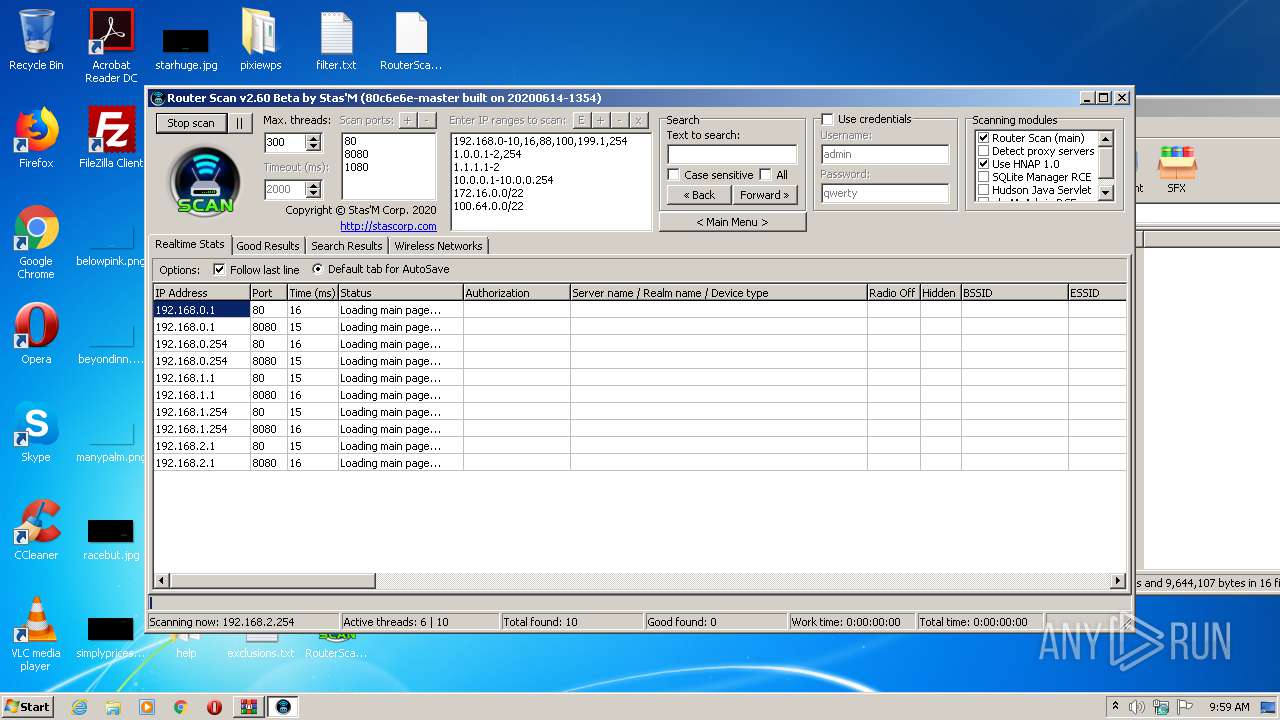
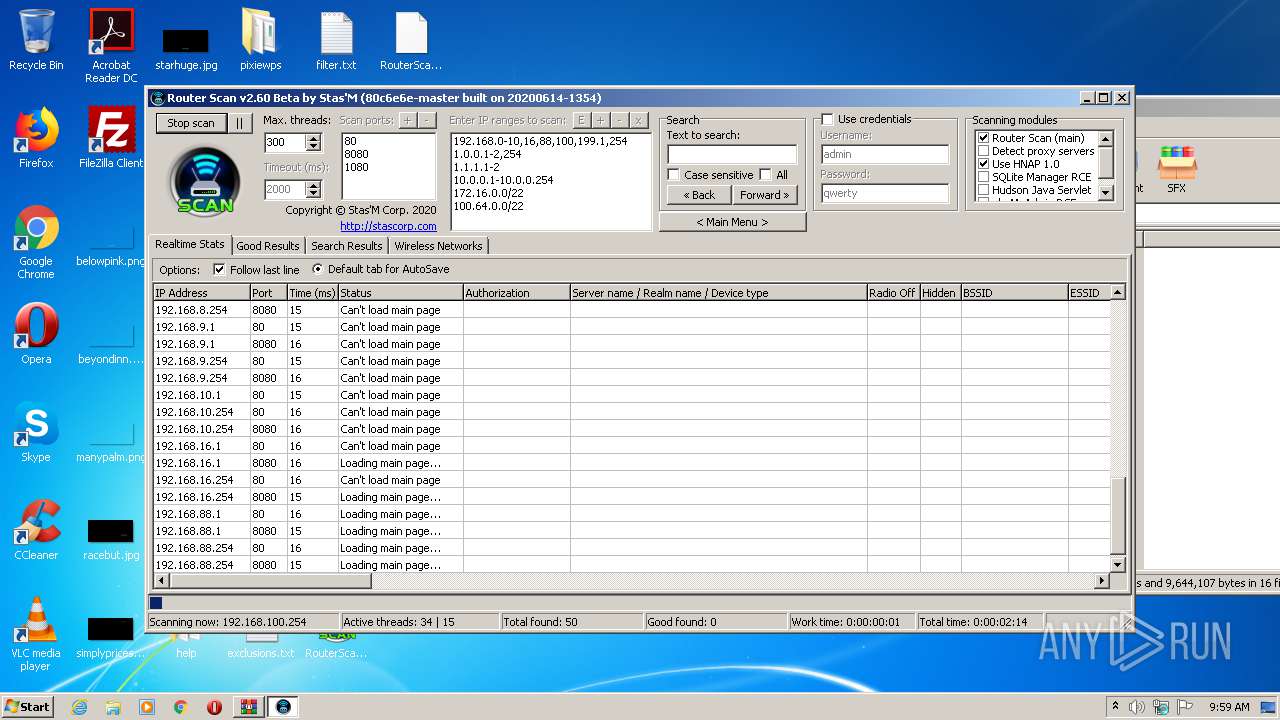
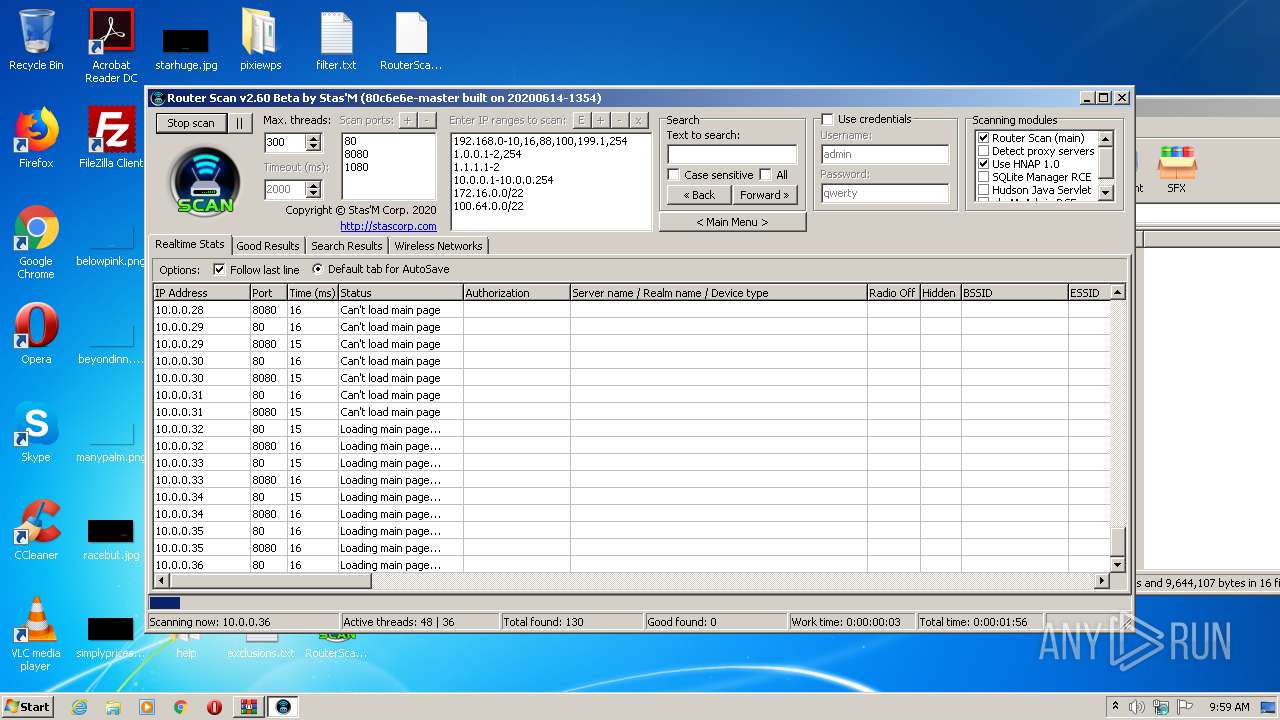
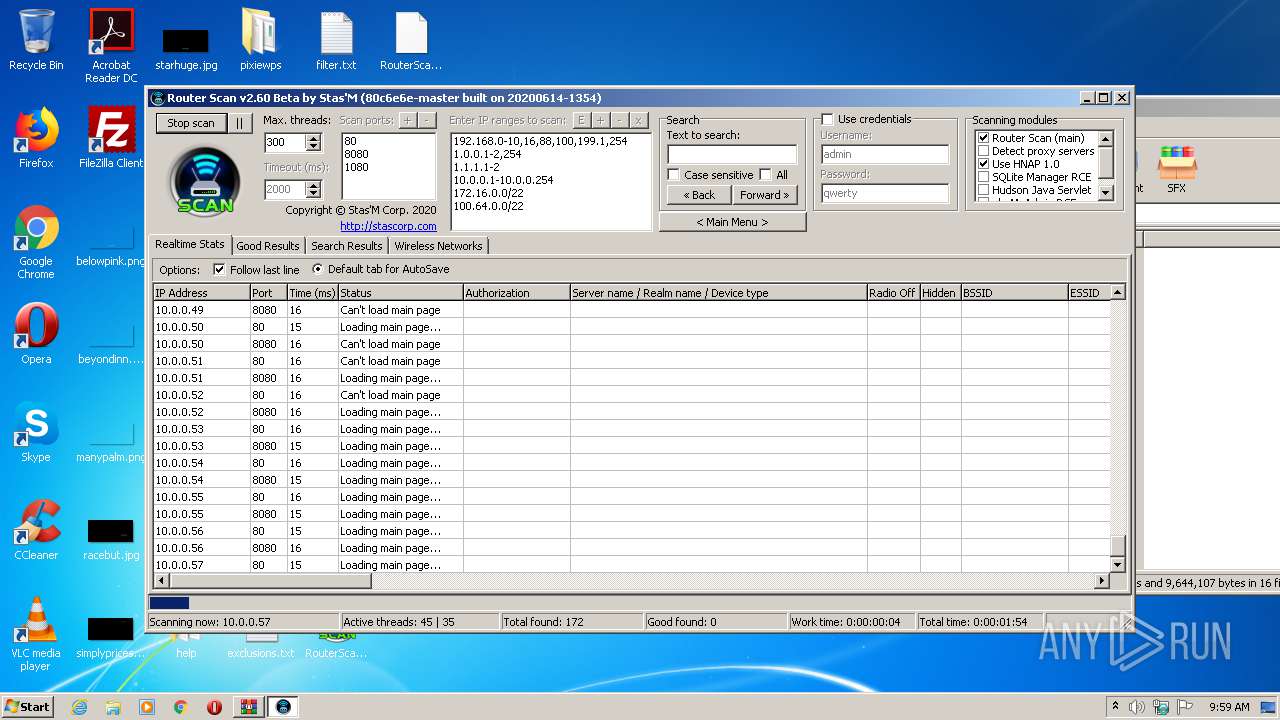
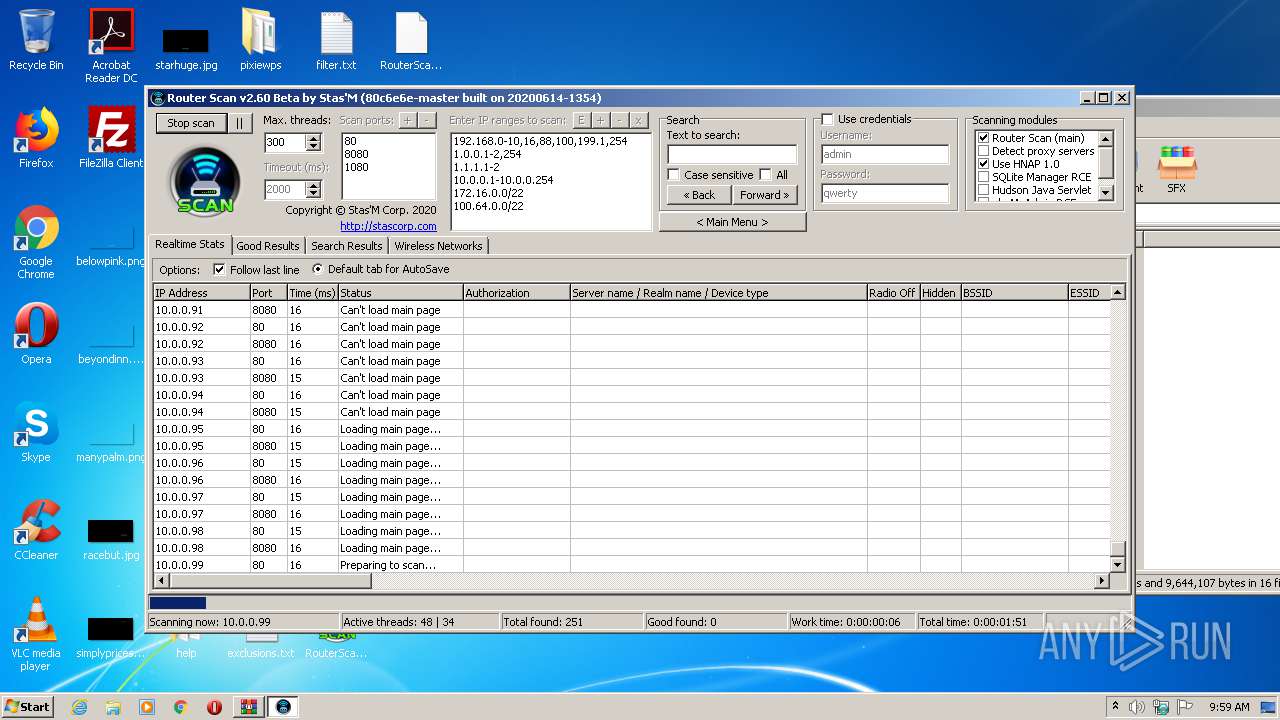
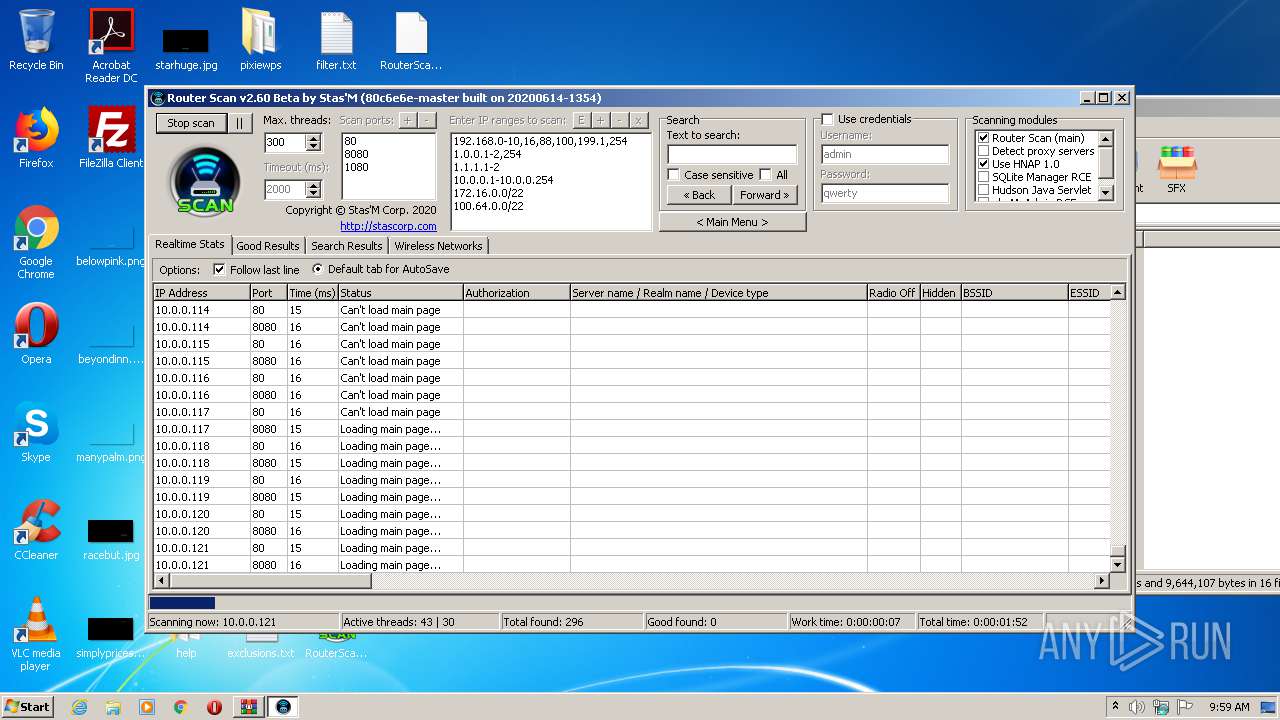
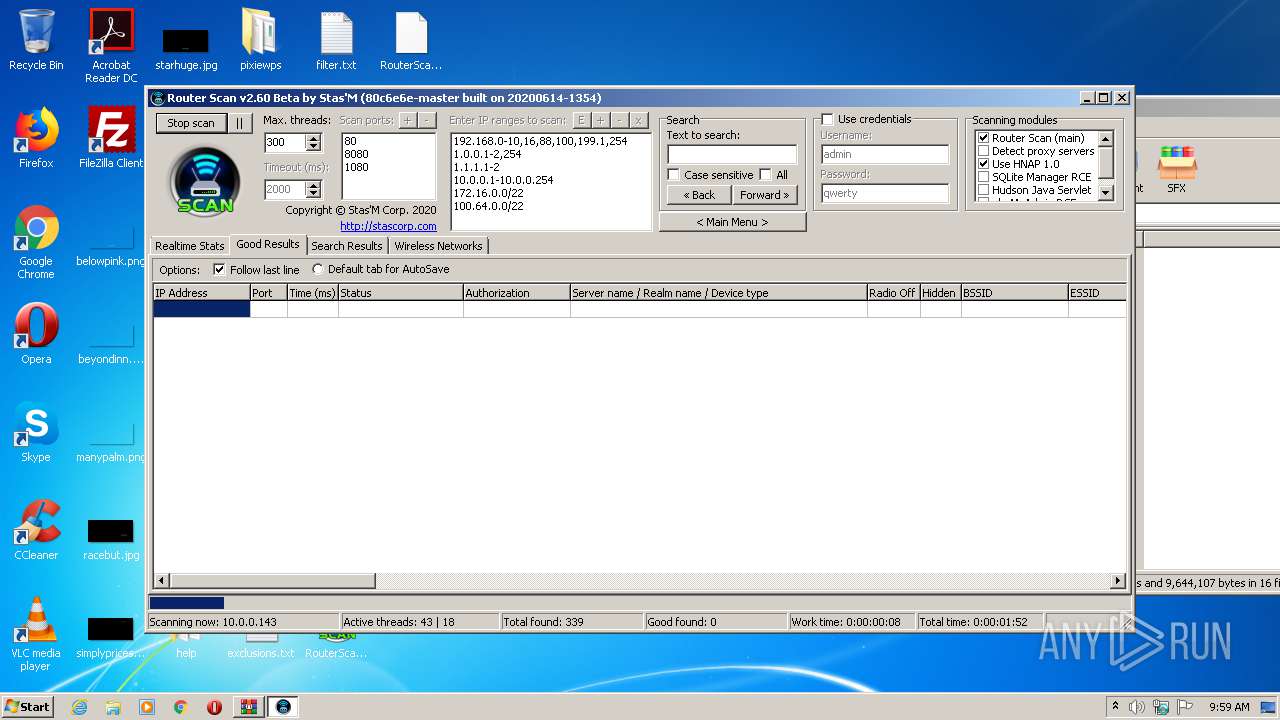
- RouterScan.exe (PID: 1888)
Loads dropped or rewritten executable
- RouterScan.exe (PID: 1888)
- SearchProtocolHost.exe (PID: 3576)
SUSPICIOUS
Executable content was dropped or overwritten
- WinRAR.exe (PID: 2132)
INFO
Manual execution by user
- RouterScan.exe (PID: 1888)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (36.3) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 10 |
|---|---|
| ZipBitFlag: | - |
| ZipCompression: | None |
| ZipModifyDate: | 2020:06:25 11:55:11 |
| ZipCRC: | 0x00000000 |
| ZipCompressedSize: | - |
| ZipUncompressedSize: | - |
| ZipFileName: | filter.txt |
Total processes
37
Monitored processes
3
Malicious processes
1
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1888 | "C:\Users\admin\Desktop\RouterScan.exe" | C:\Users\admin\Desktop\RouterScan.exe | explorer.exe | ||||||||||||
User: admin Company: Stas'M Corp. Integrity Level: MEDIUM Description: Router Scan by Stas'M Exit code: 0 Version: 2.6.0.0 Modules
| |||||||||||||||
| 2132 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\AppData\Local\Temp\Lol.zip" | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.60.0 Modules
| |||||||||||||||
| 3576 | "C:\Windows\system32\SearchProtocolHost.exe" Global\UsGthrFltPipeMssGthrPipe3_ Global\UsGthrCtrlFltPipeMssGthrPipe3 1 -2147483646 "Software\Microsoft\Windows Search" "Mozilla/4.0 (compatible; MSIE 6.0; Windows NT; MS Search 4.0 Robot)" "C:\ProgramData\Microsoft\Search\Data\Temp\usgthrsvc" "DownLevelDaemon" | C:\Windows\System32\SearchProtocolHost.exe | — | SearchIndexer.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Microsoft Windows Search Protocol Host Exit code: 0 Version: 7.00.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
Total events
785
Read events
764
Write events
21
Delete events
0
Modification events
| (PID) Process: | (2132) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (2132) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (2132) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\12F\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (2132) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\12F\52C64B7E |
| Operation: | write | Name: | @C:\Windows\system32\NetworkExplorer.dll,-1 |
Value: Network | |||
| (PID) Process: | (2132) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\Lol.zip | |||
| (PID) Process: | (2132) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (2132) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (2132) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (2132) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (2132) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\12F\52C64B7E |
| Operation: | write | Name: | @C:\Windows\system32\notepad.exe,-469 |
Value: Text Document | |||
Executable files
8
Suspicious files
0
Text files
176
Unknown types
1
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2132 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa2132.36022\RouterScan.exe | executable | |
MD5:— | SHA256:— | |||
| 2132 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa2132.36022\help\data\manual\menu_main.png | image | |
MD5:6EA94AA073E42F7E79885831DA173462 | SHA256:25FE2D89C8D99B9D8B6D3FFA9CA095A49283CA4A9E23FA9FAC34C755CAA66819 | |||
| 2132 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa2132.36022\librouter.dll | executable | |
MD5:— | SHA256:— | |||
| 2132 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa2132.36022\help\data\code.css | text | |
MD5:EB21D6145A7B341CA198228B2C9930A8 | SHA256:FAB0FD6EEDFD3F618BC3C9522F259F51BF1FF09181A1D482FB965829F2387018 | |||
| 2132 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa2132.36022\ranges.txt | text | |
MD5:A46D6BD36988F9F45FF4C6C0B1C567DE | SHA256:91679EDAA5D933F5332C94EB0C666E2DF2A0D0F9551F26A51E09FF2AE10A9BE6 | |||
| 2132 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa2132.36022\msvcr100.dll | executable | |
MD5:BF38660A9125935658CFA3E53FDC7D65 | SHA256:60C06E0FA4449314DA3A0A87C1A9D9577DF99226F943637E06F61188E5862EFA | |||
| 2132 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa2132.36022\RouterScan.exe.til | til | |
MD5:6D4048F29EAE0AB078A797F723C5B563 | SHA256:513E9D059AB03CFC3088999D32EB2FB26A8A3F338A7F95720E81075256443D4B | |||
| 2132 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa2132.36022\RouterScan.log | text | |
MD5:— | SHA256:— | |||
| 2132 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa2132.36022\help\data\manual\window_exclusions.png | image | |
MD5:445458767080CAFFE78E3485FBE073D0 | SHA256:017130EE877058E66FE5488E624B46A96516DF248F8A34CE3BB5B437EC2C2F7D | |||
| 2132 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa2132.36022\help\data\manual\menu_table.png | image | |
MD5:8764457F339A125AC67BB57D98961D4A | SHA256:79CBBB622DC431B03D00089BF5D74B290F7A97F8DF3BE504A42CF7C81FC0DC94 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
1 236
TCP/UDP connections
3 123
DNS requests
0
Threats
2
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
1888 | RouterScan.exe | GET | — | 1.1.1.2:8080 | http://1.1.1.2:8080/ | AU | — | — | unknown |
1888 | RouterScan.exe | GET | — | 10.0.0.1:80 | http://10.0.0.1/ | unknown | — | — | whitelisted |
1888 | RouterScan.exe | GET | — | 10.0.0.2:80 | http://10.0.0.2/ | unknown | — | — | malicious |
1888 | RouterScan.exe | GET | — | 10.0.0.1:80 | http://10.0.0.1/ | unknown | — | — | whitelisted |
1888 | RouterScan.exe | GET | — | 10.0.0.1:8080 | http://10.0.0.1:8080/ | unknown | — | — | whitelisted |
1888 | RouterScan.exe | GET | — | 10.0.0.2:80 | http://10.0.0.2/ | unknown | — | — | malicious |
1888 | RouterScan.exe | GET | — | 10.0.0.3:8080 | http://10.0.0.3:8080/ | unknown | — | — | suspicious |
1888 | RouterScan.exe | GET | — | 10.0.0.1:8080 | http://10.0.0.1:8080/ | unknown | — | — | whitelisted |
1888 | RouterScan.exe | GET | — | 10.0.0.2:8080 | http://10.0.0.2:8080/ | unknown | — | — | malicious |
1888 | RouterScan.exe | GET | — | 10.0.0.1:80 | http://10.0.0.1/ | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
1888 | RouterScan.exe | 1.0.0.2:80 | — | — | AU | unknown |
1888 | RouterScan.exe | 1.0.0.1:80 | — | — | AU | unknown |
1888 | RouterScan.exe | 1.0.0.2:1080 | — | — | AU | unknown |
1888 | RouterScan.exe | 1.0.0.1:1080 | — | — | AU | unknown |
1888 | RouterScan.exe | 1.0.0.2:8080 | — | — | AU | unknown |
1888 | RouterScan.exe | 1.0.0.254:1080 | — | — | AU | unknown |
1888 | RouterScan.exe | 1.0.0.1:443 | — | — | AU | unknown |
1888 | RouterScan.exe | 1.0.0.254:80 | — | — | AU | unknown |
1888 | RouterScan.exe | 1.0.0.254:8080 | — | — | AU | unknown |
1888 | RouterScan.exe | 1.1.1.2:80 | — | — | AU | unknown |
DNS requests
Threats
PID | Process | Class | Message |
|---|---|---|---|
1888 | RouterScan.exe | Potential Corporate Privacy Violation | ET POLICY Cloudflare DNS Over HTTPS Certificate Inbound |
1888 | RouterScan.exe | Potential Corporate Privacy Violation | ET POLICY Cloudflare DNS Over HTTPS Certificate Inbound |