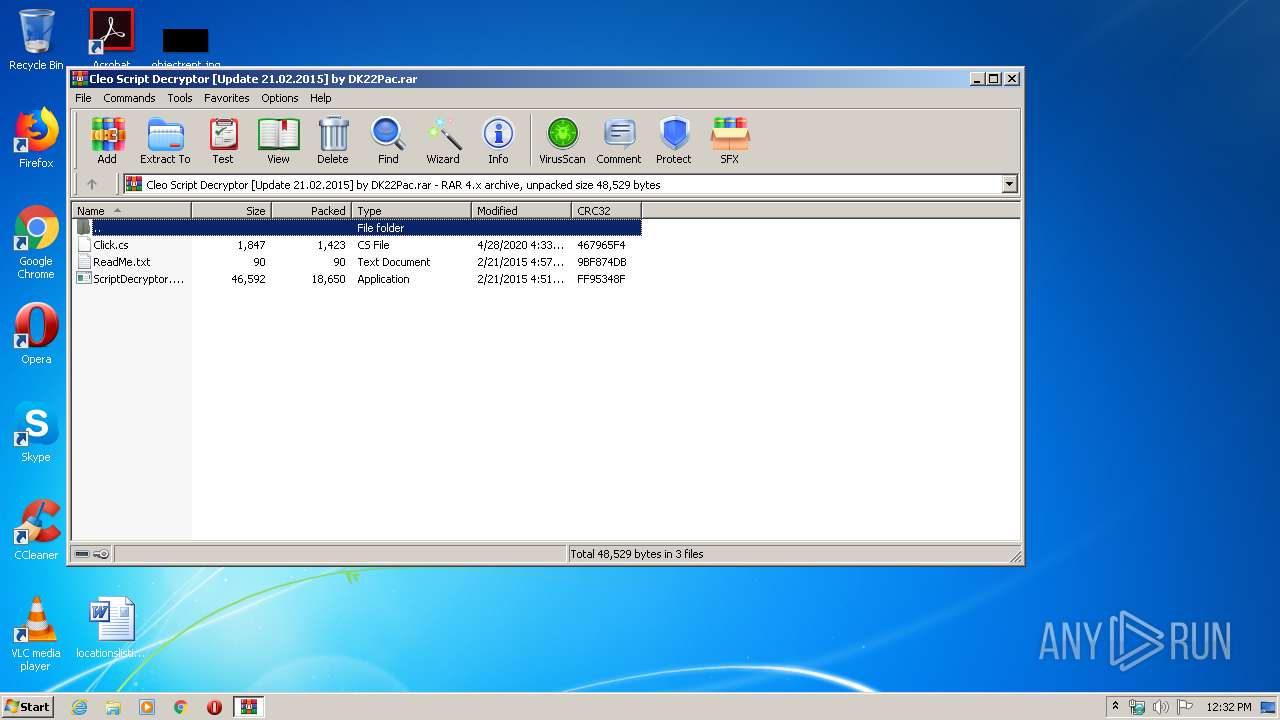
| File name: | Cleo Script Decryptor [Update 21.02.2015] by DK22Pac.rar |
| Full analysis: | https://app.any.run/tasks/b4d87da4-33f8-4ef7-a75d-766a249b1a58 |
| Verdict: | Malicious activity |
| Analysis date: | April 28, 2020, 11:32:06 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/x-rar |
| File info: | RAR archive data, v4, os: Win32 |
| MD5: | E59E62B972B539FFB4E4E9B6A747C583 |
| SHA1: | 57CE3ED0863169EC1FAFB039A777112069DEE2B9 |
| SHA256: | 488580934C4B088498AE5FB43571F54187D9B6C1AF383D039D65B2834385E4F9 |
| SSDEEP: | 384:oUdCCiwXMCJs/++CPeostJA8N9UiUDR+23daLPIjz+DiyweIIVHnL:fdXMC+/vKXstJp9+30PInClImHL |
MALICIOUS
Application was dropped or rewritten from another process
- ScriptDecryptor.exe (PID: 2888)
Actions looks like stealing of personal data
- ScriptDecryptor.exe (PID: 2888)
SUSPICIOUS
No suspicious indicators.INFO
Manual execution by user
- ScriptDecryptor.exe (PID: 2888)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .rar | | | RAR compressed archive (v-4.x) (58.3) |
|---|---|---|
| .rar | | | RAR compressed archive (gen) (41.6) |
EXIF
ZIP
| CompressedSize: | 126 |
|---|---|
| UncompressedSize: | 90 |
| OperatingSystem: | Win32 |
| ModifyDate: | 2015:02:21 16:57:00 |
| PackingMethod: | Stored |
| ArchivedFileName: | ReadMe.txt |
Total processes
38
Monitored processes
2
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
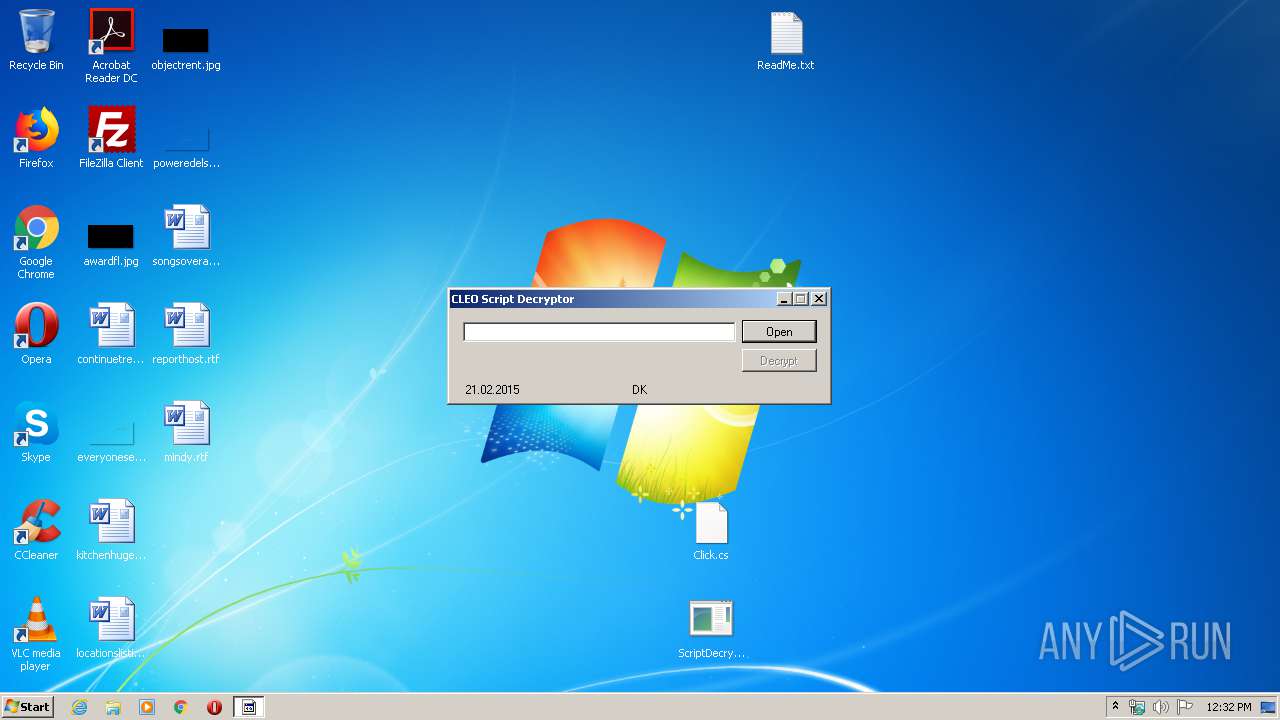
| 2888 | "C:\Users\admin\Desktop\ScriptDecryptor.exe" | C:\Users\admin\Desktop\ScriptDecryptor.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 3996 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\AppData\Local\Temp\Cleo Script Decryptor [Update 21.02.2015] by DK22Pac.rar" | C:\Program Files\WinRAR\WinRAR.exe | — | explorer.exe | |||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.60.0 Modules
| |||||||||||||||
Total events
982
Read events
897
Write events
81
Delete events
4
Modification events
| (PID) Process: | (3996) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (3996) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (3996) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\12B\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (3996) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\Cleo Script Decryptor [Update 21.02.2015] by DK22Pac.rar | |||
| (PID) Process: | (3996) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (3996) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (3996) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (3996) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (3996) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\MainWin |
| Operation: | write | Name: | Placement |
Value: 2C0000000000000001000000FFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFF42000000420000000204000037020000 | |||
| (PID) Process: | (3996) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\General |
| Operation: | write | Name: | LastFolder |
Value: C:\Users\admin\AppData\Local\Temp | |||
Executable files
0
Suspicious files
0
Text files
0
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3996 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa3996.37890\ReadMe.txt | — | |
MD5:— | SHA256:— | |||
| 3996 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa3996.37890\ScriptDecryptor.exe | — | |
MD5:— | SHA256:— | |||
| 3996 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa3996.37890\Click.cs | — | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
0
DNS requests
0
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report