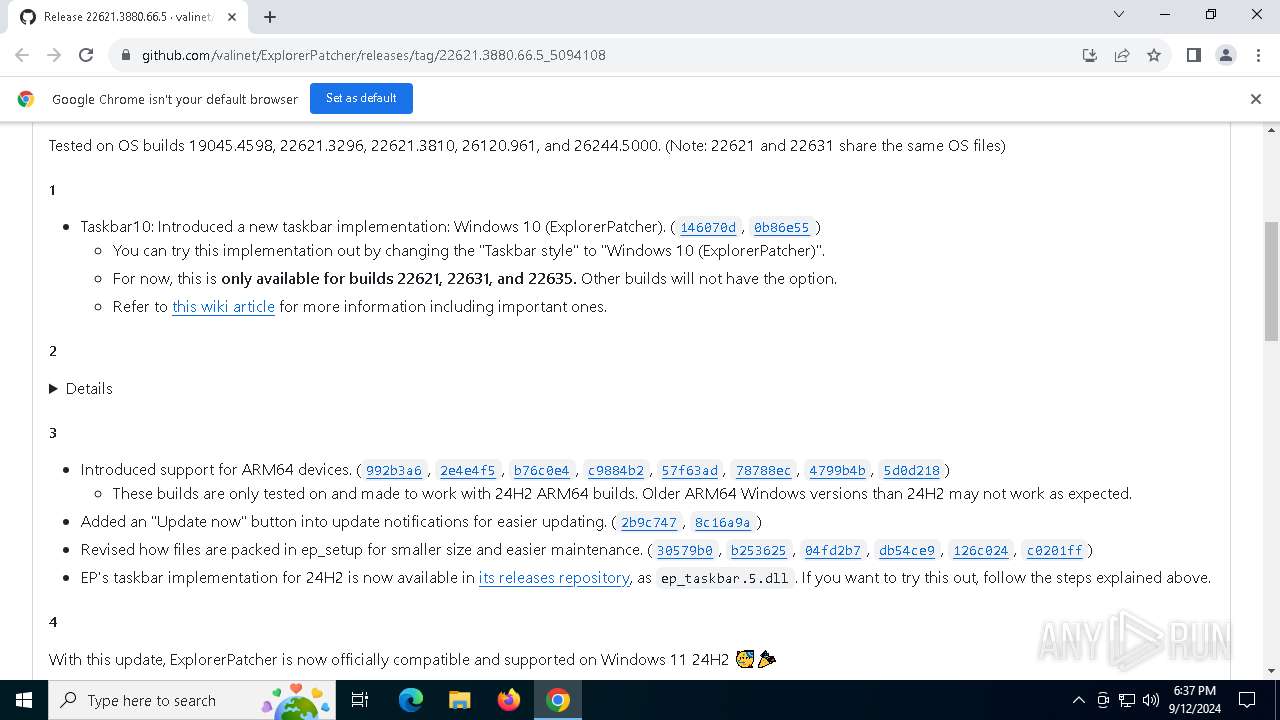
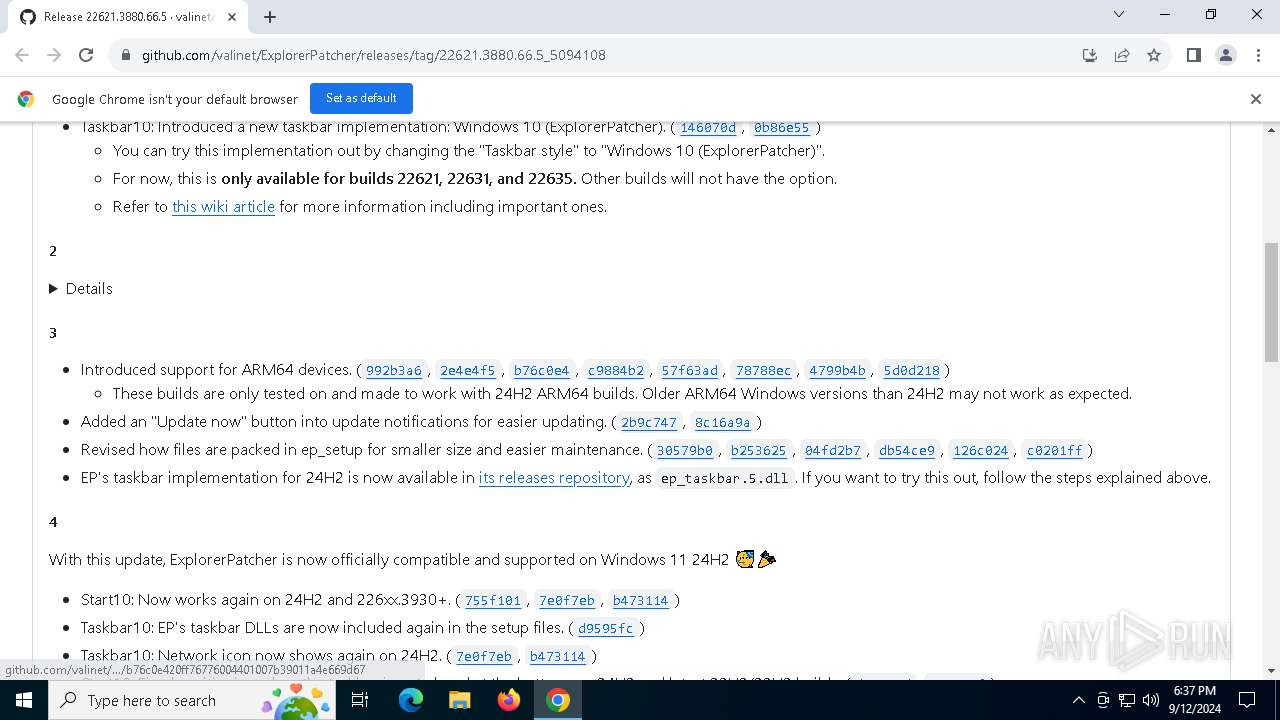
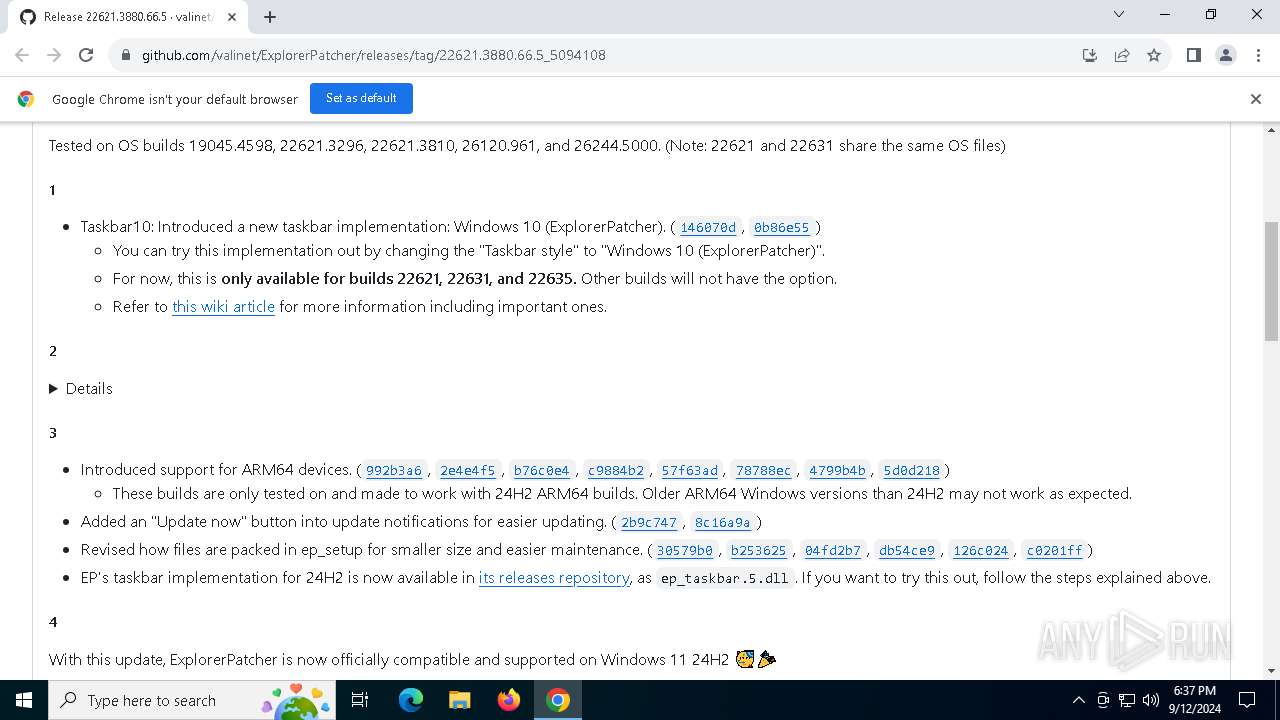
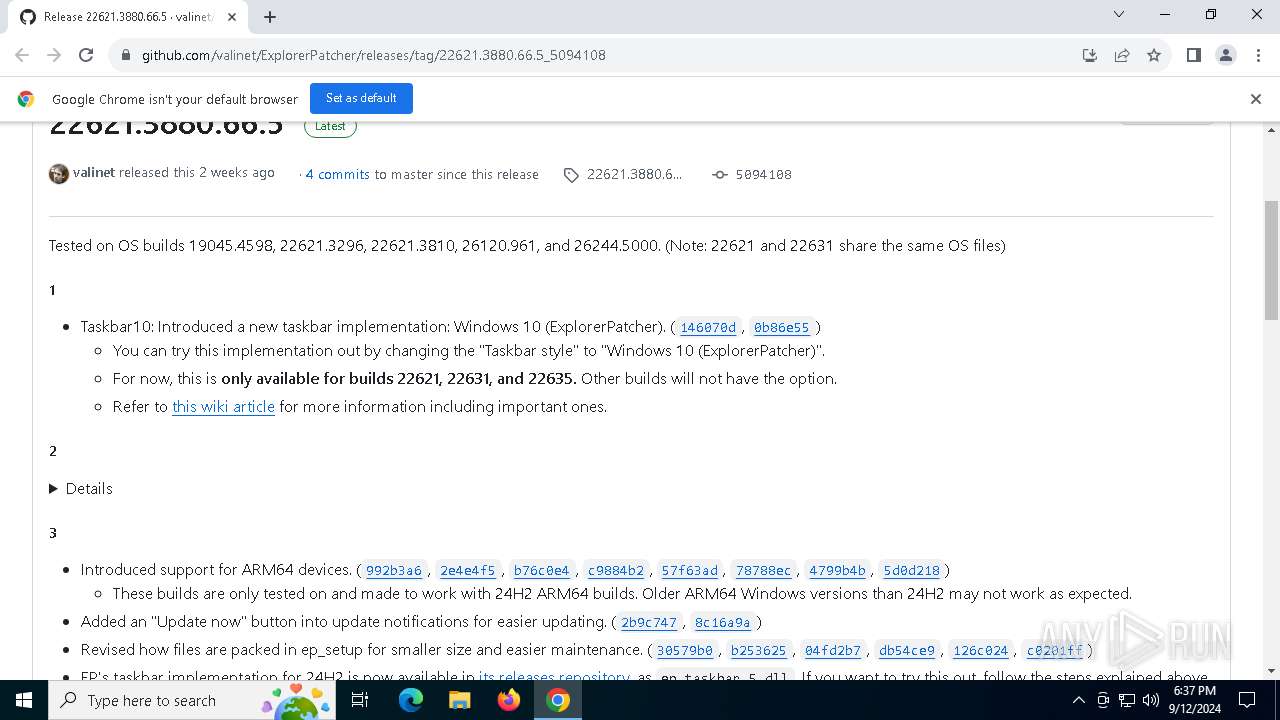
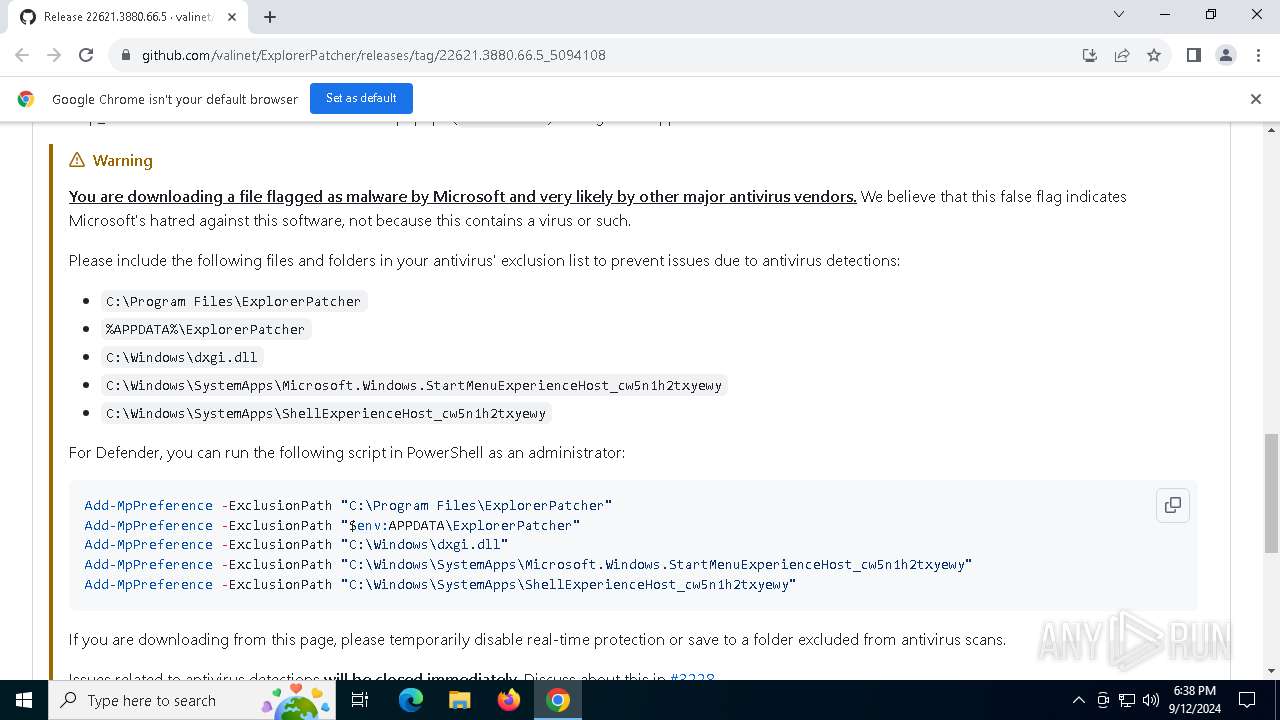
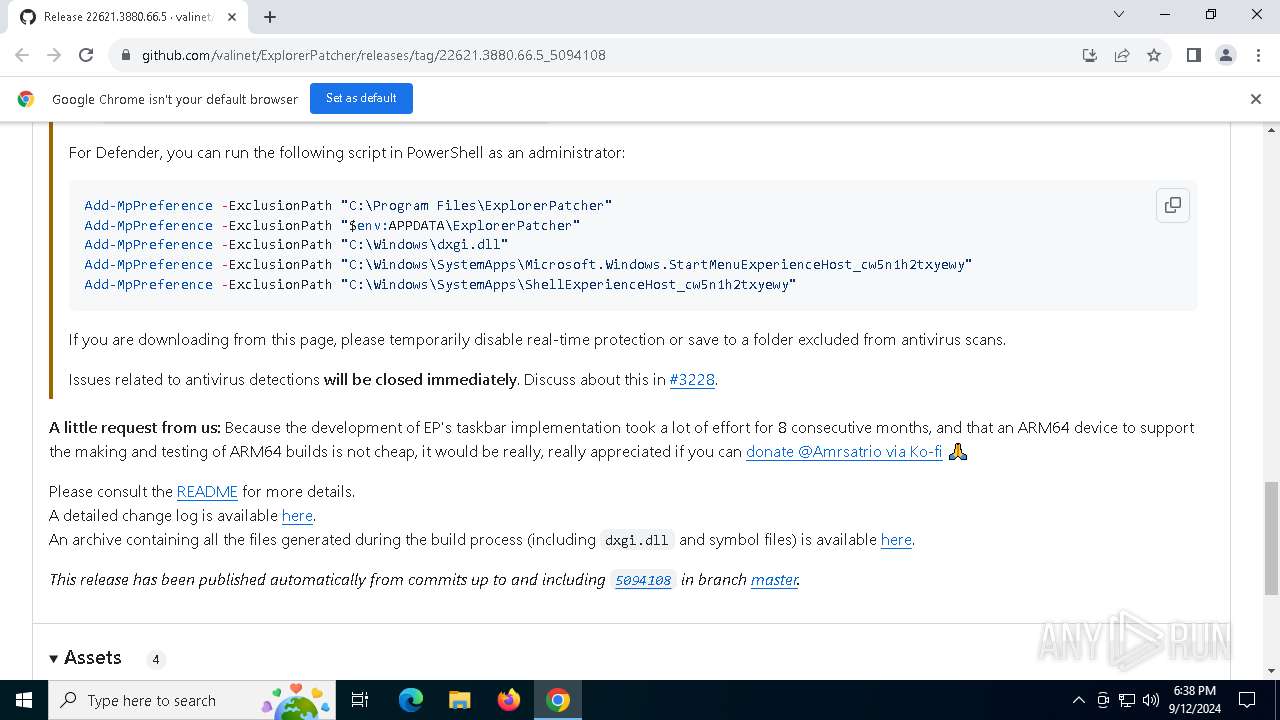
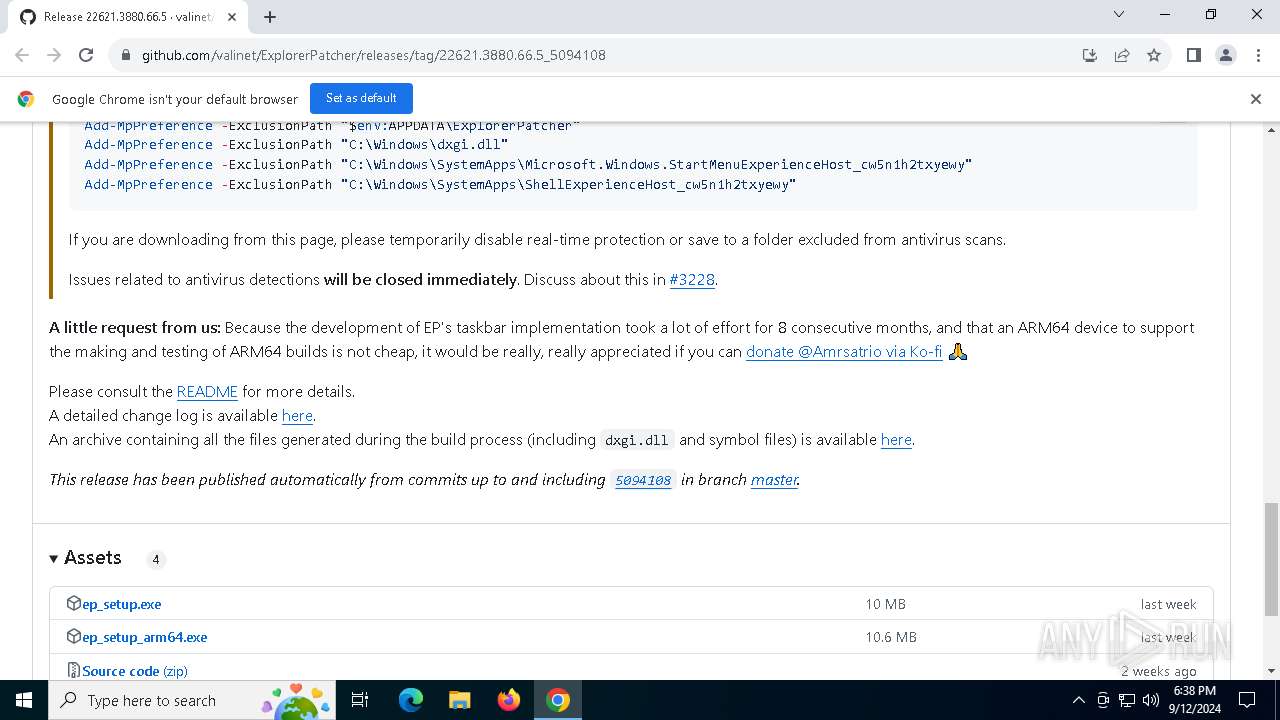
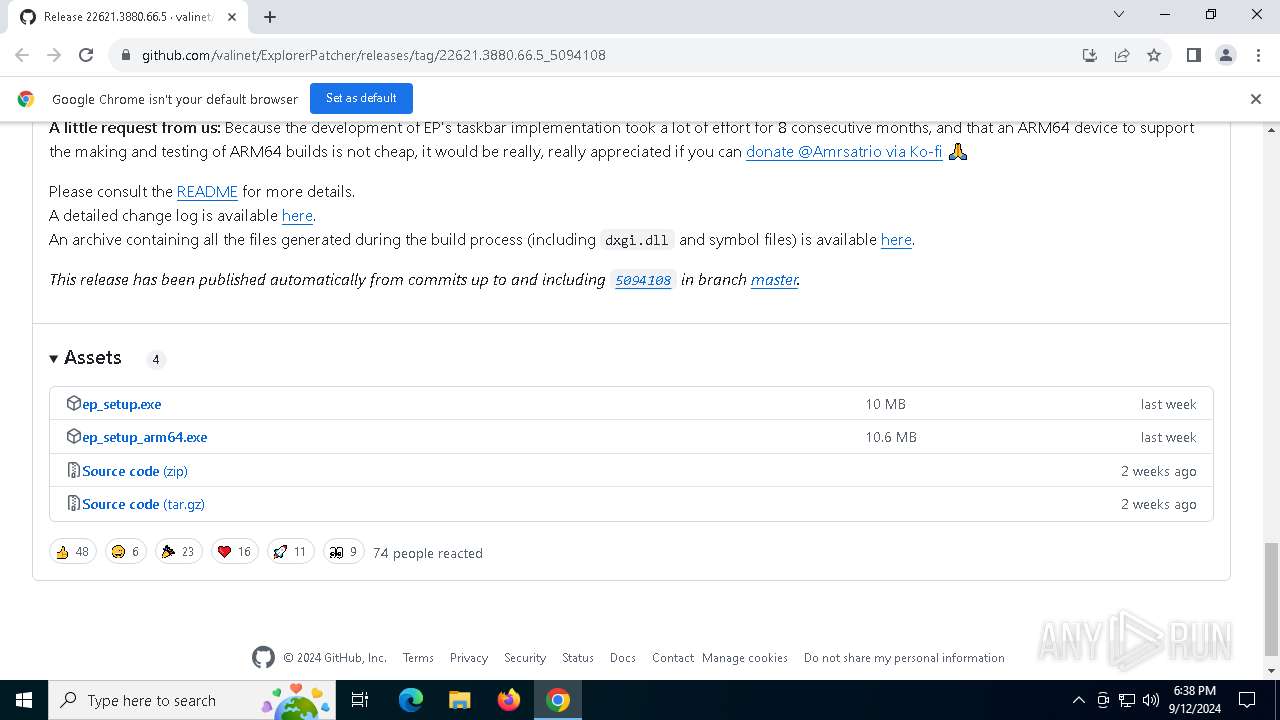
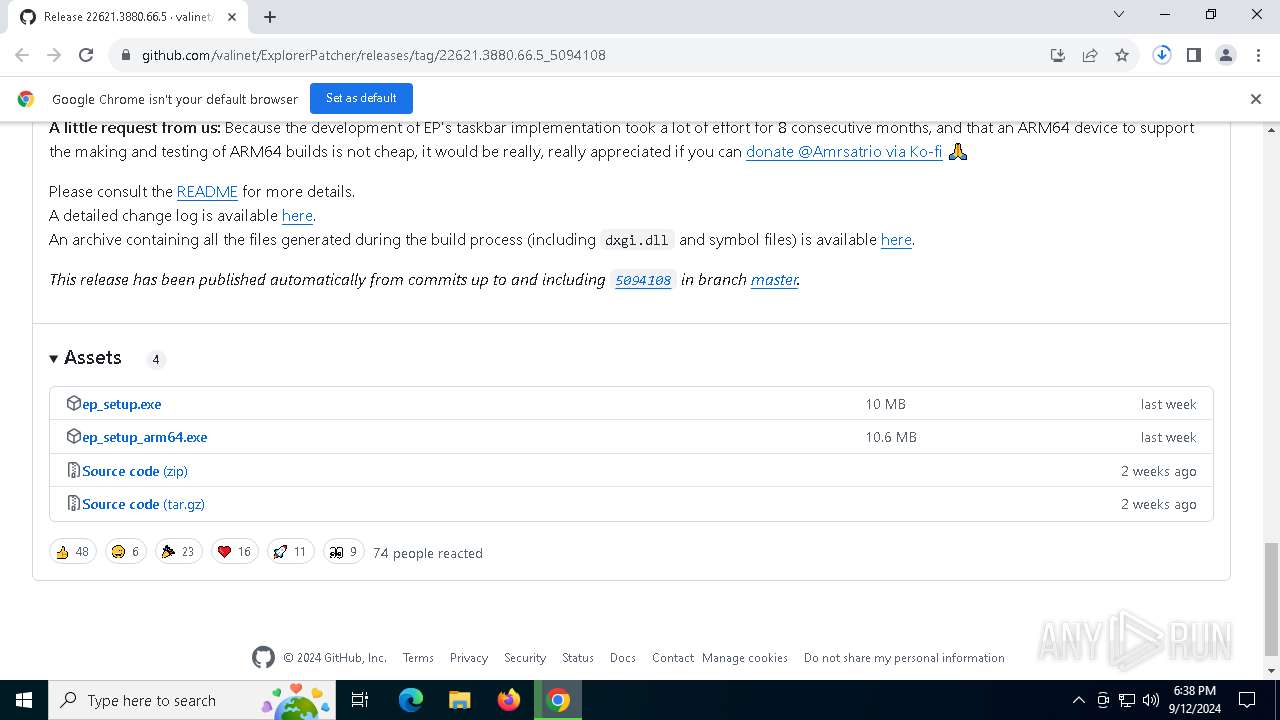
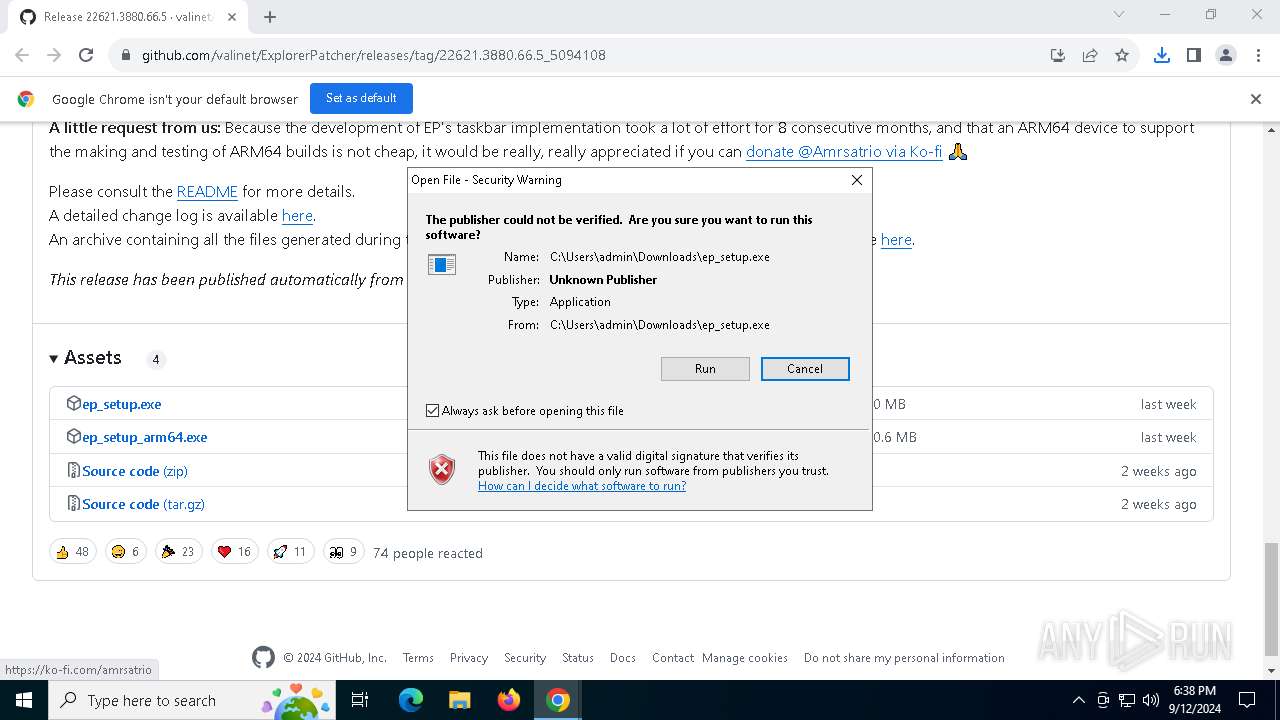
| URL: | https://github.com/valinet/ExplorerPatcher/releases/latest |
| Full analysis: | https://app.any.run/tasks/d1afb790-ef5d-4a47-a297-3e5223adaa09 |
| Verdict: | Malicious activity |
| Analysis date: | September 12, 2024, 18:37:33 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Indicators: | |
| MD5: | 76488722909C117C75F74CD4BF64563E |
| SHA1: | BE2BBB8837C41B85807188C7691C12A56831930B |
| SHA256: | 484D820BB0436F728D059ED4DD0824A5A543015CBB7D536EAD958D870E773266 |
| SSDEEP: | 3:N8tEdjFzY2QeRcE2RR:2uPzY1eRcr3 |
MALICIOUS
Registers / Runs the DLL via REGSVR32.EXE
- ep_setup.exe (PID: 6040)
SUSPICIOUS
Reads security settings of Internet Explorer
- ep_setup.exe (PID: 6816)
- ep_setup.exe (PID: 6040)
- StartMenuExperienceHost.exe (PID: 6640)
- StartMenuExperienceHost.exe (PID: 2708)
Reads the date of Windows installation
- ep_setup.exe (PID: 6816)
- ep_setup.exe (PID: 6040)
- StartMenuExperienceHost.exe (PID: 6640)
- SearchApp.exe (PID: 5020)
- StartMenuExperienceHost.exe (PID: 2708)
Application launched itself
- ep_setup.exe (PID: 6816)
Uses TASKKILL.EXE to kill process
- ep_setup.exe (PID: 6040)
Starts SC.EXE for service management
- ep_setup.exe (PID: 6040)
The process creates files with name similar to system file names
- ep_setup.exe (PID: 6040)
Process drops legitimate windows executable
- ep_setup.exe (PID: 6040)
Executable content was dropped or overwritten
- ep_setup.exe (PID: 6040)
Creates/Modifies COM task schedule object
- regsvr32.exe (PID: 6320)
- regsvr32.exe (PID: 4068)
The process executes via Task Scheduler
- explorer.exe (PID: 5552)
Creates a software uninstall entry
- ep_setup.exe (PID: 6040)
Uses RUNDLL32.EXE to load library
- explorer.exe (PID: 5552)
Uses REG/REGEDIT.EXE to modify registry
- rundll32.exe (PID: 5148)
INFO
The process uses the downloaded file
- chrome.exe (PID: 752)
- chrome.exe (PID: 5552)
- ep_setup.exe (PID: 6816)
- ep_setup.exe (PID: 6040)
- rundll32.exe (PID: 5148)
Executable content was dropped or overwritten
- chrome.exe (PID: 752)
Reads the computer name
- ep_setup.exe (PID: 6816)
- ep_setup.exe (PID: 6040)
- SearchApp.exe (PID: 5020)
- StartMenuExperienceHost.exe (PID: 6640)
- TextInputHost.exe (PID: 1860)
- SystemSettings.exe (PID: 2028)
- StartMenuExperienceHost.exe (PID: 2708)
Checks supported languages
- ep_setup.exe (PID: 6816)
- ep_setup.exe (PID: 6040)
- StartMenuExperienceHost.exe (PID: 6640)
- SearchApp.exe (PID: 5020)
- TextInputHost.exe (PID: 1860)
- SystemSettings.exe (PID: 2028)
- StartMenuExperienceHost.exe (PID: 2708)
Process checks computer location settings
- ep_setup.exe (PID: 6816)
- ep_setup.exe (PID: 6040)
- StartMenuExperienceHost.exe (PID: 6640)
- SearchApp.exe (PID: 5020)
- StartMenuExperienceHost.exe (PID: 2708)
Creates files in the program directory
- ep_setup.exe (PID: 6040)
Application launched itself
- chrome.exe (PID: 752)
Sends debugging messages
- StartMenuExperienceHost.exe (PID: 6640)
- StartMenuExperienceHost.exe (PID: 2708)
Checks proxy server information
- SearchApp.exe (PID: 5020)
- explorer.exe (PID: 5552)
- slui.exe (PID: 5464)
Reads the machine GUID from the registry
- SearchApp.exe (PID: 5020)
- SystemSettings.exe (PID: 2028)
Reads the software policy settings
- explorer.exe (PID: 5552)
- SearchApp.exe (PID: 5020)
- slui.exe (PID: 2572)
- slui.exe (PID: 5464)
- SystemSettings.exe (PID: 2028)
Reads security settings of Internet Explorer
- explorer.exe (PID: 5552)
- rundll32.exe (PID: 5148)
Creates files or folders in the user directory
- explorer.exe (PID: 5552)
Reads Environment values
- SearchApp.exe (PID: 5020)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
190
Monitored processes
46
Malicious processes
1
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 752 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --disk-cache-dir=null --disk-cache-size=1 --media-cache-size=1 --disable-gpu-shader-disk-cache --disable-background-networking --disable-features=OptimizationGuideModelDownloading,OptimizationHintsFetching,OptimizationTargetPrediction,OptimizationHints "https://github.com/valinet/ExplorerPatcher/releases/latest" | C:\Program Files\Google\Chrome\Application\chrome.exe | explorer.exe | ||||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Version: 122.0.6261.70 Modules
| |||||||||||||||
| 1228 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | reg.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1300 | "C:\WINDOWS\system32\reg.exe" ADD "HKCU\SOFTWARE\Policies\Microsoft\Windows\Explorer" /V ForceStartSize /T REG_DWORD /D 2 /F | C:\Windows\System32\reg.exe | rundll32.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Registry Console Tool Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1616 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=gpu-process --no-appcompat-clear --gpu-preferences=WAAAAAAAAADgABAMAAAAAAAAAAAAAAAAAABgAAAAAAA4AAAAAAAAAAAAAAAEAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAGAAAAAAAAAAYAAAAAAAAAAgAAAAAAAAACAAAAAAAAAAIAAAAAAAAAA== --mojo-platform-channel-handle=1800 --field-trial-handle=1888,i,3046162429543370476,15155300190211111157,262144 --disable-features=OptimizationGuideModelDownloading,OptimizationHints,OptimizationHintsFetching,OptimizationTargetPrediction --variations-seed-version /prefetch:2 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Version: 122.0.6261.70 Modules
| |||||||||||||||
| 1636 | "C:\WINDOWS\system32\sc.exe" start ep_dwm_D17F1E1A-5919-4427-8F89-A1A8503CA3EB | C:\Windows\System32\sc.exe | — | ep_setup.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Service Control Manager Configuration Tool Exit code: 1060 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1860 | "C:\WINDOWS\SystemApps\MicrosoftWindows.Client.CBS_cw5n1h2txyewy\TextInputHost.exe" -ServerName:InputApp.AppXjd5de1g66v206tj52m9d0dtpppx4cgpn.mca | C:\Windows\SystemApps\MicrosoftWindows.Client.CBS_cw5n1h2txyewy\TextInputHost.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Version: 123.26505.0.0 Modules
| |||||||||||||||
| 2028 | "C:\Windows\ImmersiveControlPanel\SystemSettings.exe" -ServerName:microsoft.windows.immersivecontrolpanel | C:\Windows\ImmersiveControlPanel\SystemSettings.exe | svchost.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Settings Exit code: 1 Version: 10.0.19041.3996 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2324 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=unzip.mojom.Unzipper --lang=en-US --service-sandbox-type=service --disable-quic --no-appcompat-clear --mojo-platform-channel-handle=5392 --field-trial-handle=1888,i,3046162429543370476,15155300190211111157,262144 --disable-features=OptimizationGuideModelDownloading,OptimizationHints,OptimizationHintsFetching,OptimizationTargetPrediction --variations-seed-version /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 122.0.6261.70 Modules
| |||||||||||||||
| 2572 | "C:\WINDOWS\System32\SLUI.exe" RuleId=3482d82e-ca2c-4e1f-8864-da0267b484b2;Action=AutoActivate;AppId=55c92734-d682-4d71-983e-d6ec3f16059f;SkuId=4de7cb65-cdf1-4de9-8ae8-e3cce27b9f2c;NotificationInterval=1440;Trigger=TimerEvent | C:\Windows\System32\slui.exe | SppExtComObj.Exe | ||||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows Activation Client Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2708 | "C:\WINDOWS\SystemApps\Microsoft.Windows.StartMenuExperienceHost_cw5n1h2txyewy\StartMenuExperienceHost.exe" -ServerName:App.AppXywbrabmsek0gm3tkwpr5kwzbs55tkqay.mca | C:\Windows\SystemApps\Microsoft.Windows.StartMenuExperienceHost_cw5n1h2txyewy\StartMenuExperienceHost.exe | — | svchost.exe | |||||||||||
User: admin Integrity Level: MEDIUM Modules
| |||||||||||||||
Total events
54 397
Read events
53 870
Write events
473
Delete events
54
Modification events
| (PID) Process: | (752) chrome.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Google\Chrome\BLBeacon |
| Operation: | write | Name: | failed_count |
Value: 0 | |||
| (PID) Process: | (752) chrome.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Google\Chrome\BLBeacon |
| Operation: | write | Name: | state |
Value: 2 | |||
| (PID) Process: | (752) chrome.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Google\Chrome\BLBeacon |
| Operation: | write | Name: | state |
Value: 1 | |||
| (PID) Process: | (752) chrome.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Google\Chrome\StabilityMetrics |
| Operation: | write | Name: | user_experience_metrics.stability.exited_cleanly |
Value: 0 | |||
| (PID) Process: | (752) chrome.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Google\Update\ClientStateMedium\{8A69D345-D564-463C-AFF1-A69D9E530F96} |
| Operation: | write | Name: | usagestats |
Value: 0 | |||
| (PID) Process: | (5552) chrome.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Shell Extensions\Cached |
| Operation: | write | Name: | {2781761E-28E0-4109-99FE-B9D127C57AFE} {56FFCC30-D398-11D0-B2AE-00A0C908FA49} 0xFFFF |
Value: 0100000000000000AAAC7AEF4205DB01 | |||
| (PID) Process: | (6040) ep_setup.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall\{D17F1E1A-5919-4427-8F89-A1A8503CA3EB}_ExplorerPatcher |
| Operation: | write | Name: | UninstallString |
Value: "C:\Program Files\ExplorerPatcher\ep_setup.exe" /uninstall | |||
| (PID) Process: | (6040) ep_setup.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall\{D17F1E1A-5919-4427-8F89-A1A8503CA3EB}_ExplorerPatcher |
| Operation: | write | Name: | DisplayName |
Value: ExplorerPatcher | |||
| (PID) Process: | (6040) ep_setup.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall\{D17F1E1A-5919-4427-8F89-A1A8503CA3EB}_ExplorerPatcher |
| Operation: | write | Name: | Publisher |
Value: VALINET Solutions SRL | |||
| (PID) Process: | (6040) ep_setup.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall\{D17F1E1A-5919-4427-8F89-A1A8503CA3EB}_ExplorerPatcher |
| Operation: | write | Name: | NoModify |
Value: 1 | |||
Executable files
16
Suspicious files
236
Text files
349
Unknown types
26
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 752 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\discounts_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 752 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\parcel_tracking_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 752 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\commerce_subscription_db\LOG.old~RF12b0d9.TMP | — | |
MD5:— | SHA256:— | |||
| 752 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\commerce_subscription_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 752 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\chrome_cart_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 752 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\coupon_db\LOG.old~RF12b0e9.TMP | — | |
MD5:— | SHA256:— | |||
| 752 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\PersistentOriginTrials\LOG.old | — | |
MD5:— | SHA256:— | |||
| 752 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\coupon_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 752 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Crashpad\settings.dat | binary | |
MD5:FC81892AC822DCBB09441D3B58B47125 | SHA256:FB077C966296D02D50CCBF7F761D2A3311A206A784A7496F331C2B0D6AD205C8 | |||
| 752 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\Site Characteristics Database\LOG.old | text | |
MD5:19D1A06251A8678F85D8DE5BFAB83807 | SHA256:AA6E55DCF84CDAF0BD3F913E7B837F65500E9B71A5A7AA773D02FFBC18C7FF01 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
39
TCP/UDP connections
95
DNS requests
63
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
5552 | explorer.exe | GET | 302 | 204.79.197.219:80 | http://msdl.microsoft.com/download/symbols/twinui.pcshell.pdb/3F0945AE4BC25ECE16353588B05D30B61/twinui.pcshell.pdb | unknown | — | — | whitelisted |
5552 | explorer.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAz1vQYrVgL0erhQLCPM8GY%3D | unknown | — | — | whitelisted |
5552 | explorer.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | whitelisted |
5372 | svchost.exe | GET | 206 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/j2hxfei2occ5siitujtlwgp6xi_3/ojhpjlocmbogdgmfpkhlaaeamibhnphh_3_all_gplutbkdljxxbjolk3siq7kive.crx3 | unknown | — | — | whitelisted |
5372 | svchost.exe | HEAD | 200 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/j2hxfei2occ5siitujtlwgp6xi_3/ojhpjlocmbogdgmfpkhlaaeamibhnphh_3_all_gplutbkdljxxbjolk3siq7kive.crx3 | unknown | — | — | whitelisted |
5372 | svchost.exe | GET | 206 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/j2hxfei2occ5siitujtlwgp6xi_3/ojhpjlocmbogdgmfpkhlaaeamibhnphh_3_all_gplutbkdljxxbjolk3siq7kive.crx3 | unknown | — | — | whitelisted |
5372 | svchost.exe | GET | 206 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/j2hxfei2occ5siitujtlwgp6xi_3/ojhpjlocmbogdgmfpkhlaaeamibhnphh_3_all_gplutbkdljxxbjolk3siq7kive.crx3 | unknown | — | — | whitelisted |
5372 | svchost.exe | GET | 206 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/j2hxfei2occ5siitujtlwgp6xi_3/ojhpjlocmbogdgmfpkhlaaeamibhnphh_3_all_gplutbkdljxxbjolk3siq7kive.crx3 | unknown | — | — | whitelisted |
5372 | svchost.exe | GET | 206 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/j2hxfei2occ5siitujtlwgp6xi_3/ojhpjlocmbogdgmfpkhlaaeamibhnphh_3_all_gplutbkdljxxbjolk3siq7kive.crx3 | unknown | — | — | whitelisted |
5372 | svchost.exe | GET | 206 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/j2hxfei2occ5siitujtlwgp6xi_3/ojhpjlocmbogdgmfpkhlaaeamibhnphh_3_all_gplutbkdljxxbjolk3siq7kive.crx3 | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
6012 | svchost.exe | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
6408 | RUXIMICS.exe | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
— | — | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
2120 | MoUsoCoreWorker.exe | 23.35.229.160:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
3888 | svchost.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
6648 | chrome.exe | 140.82.121.4:443 | github.com | GITHUB | US | shared |
752 | chrome.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
3260 | svchost.exe | 40.115.3.253:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
6648 | chrome.exe | 74.125.143.84:443 | accounts.google.com | GOOGLE | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
github.com |
| shared |
accounts.google.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
github.githubassets.com |
| whitelisted |
avatars.githubusercontent.com |
| whitelisted |
github-cloud.s3.amazonaws.com |
| shared |
user-images.githubusercontent.com |
| whitelisted |