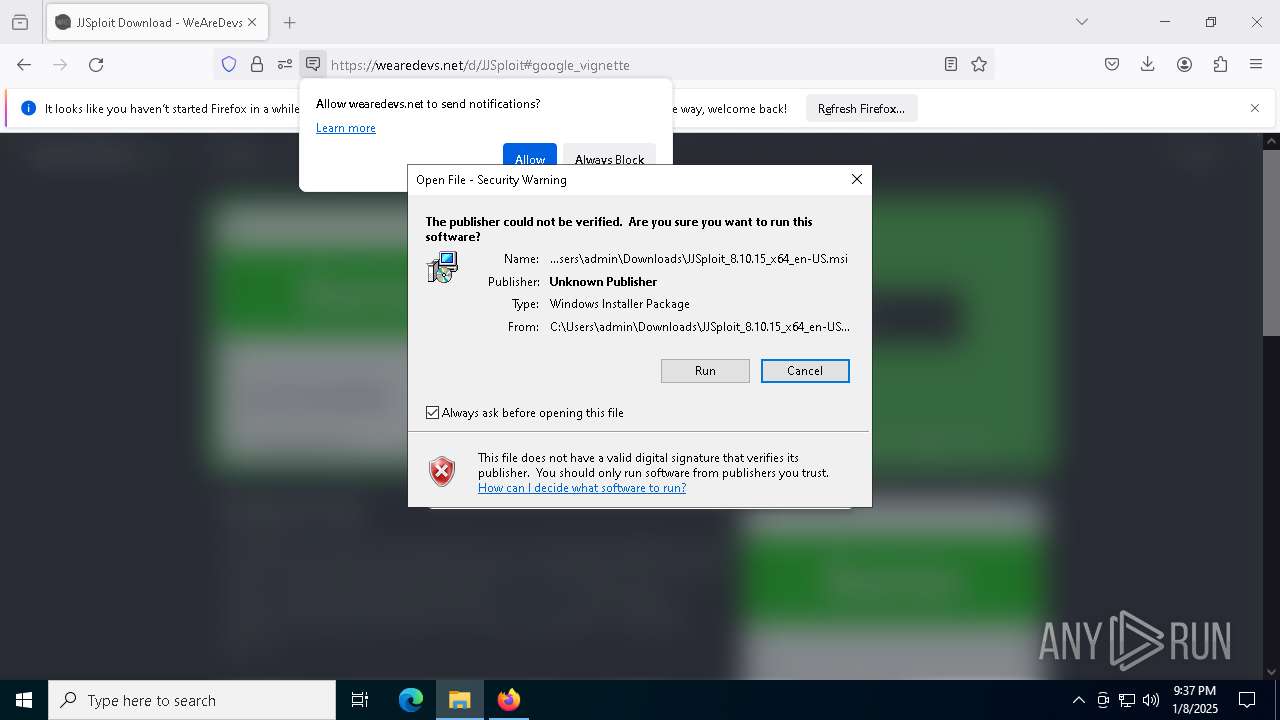
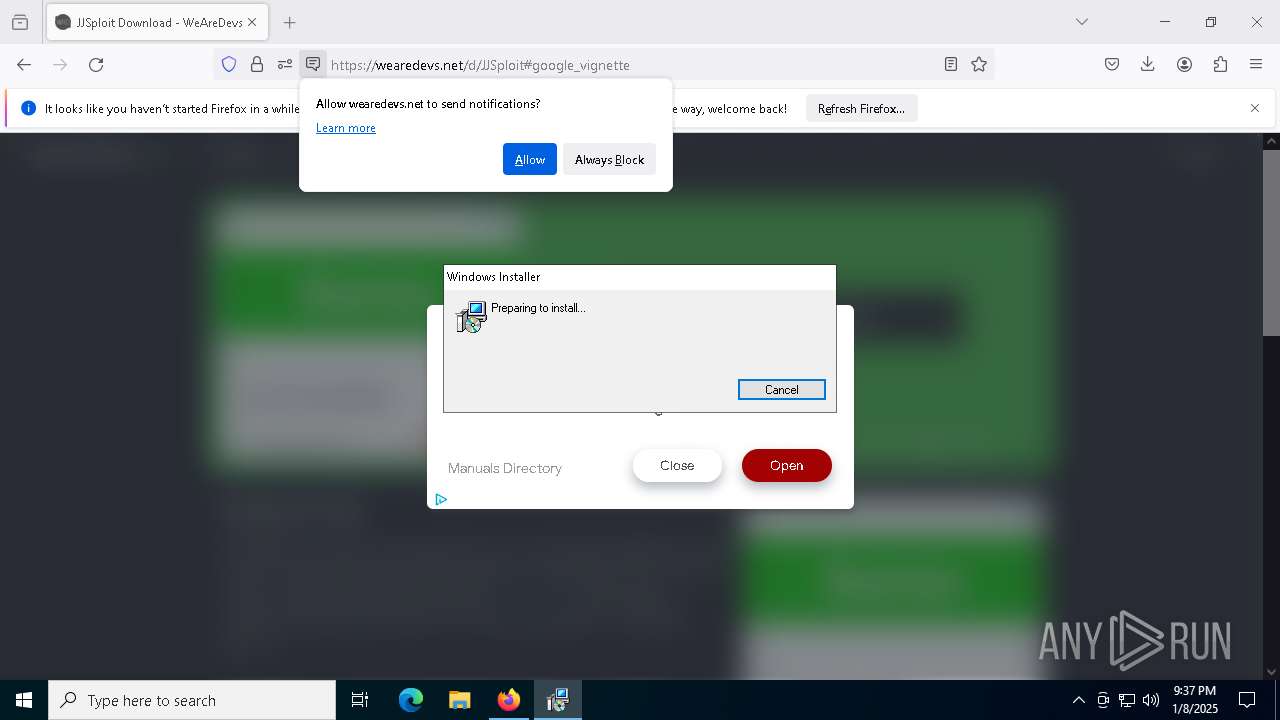
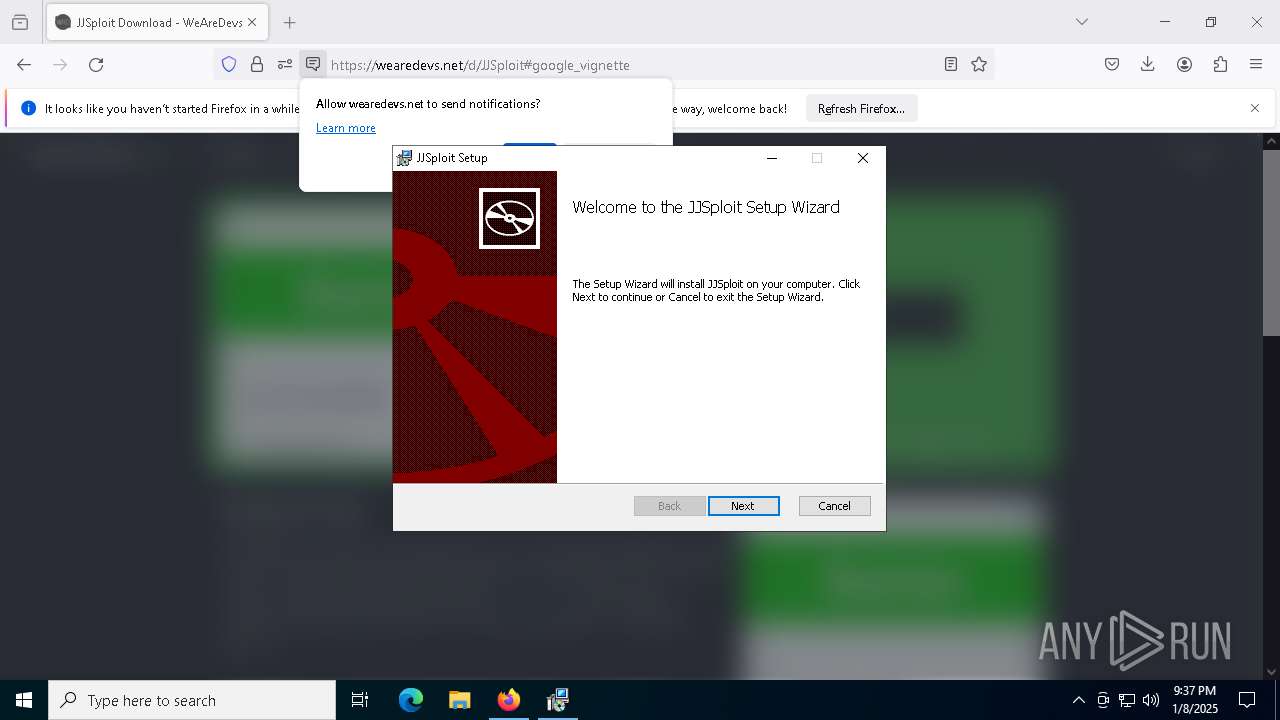
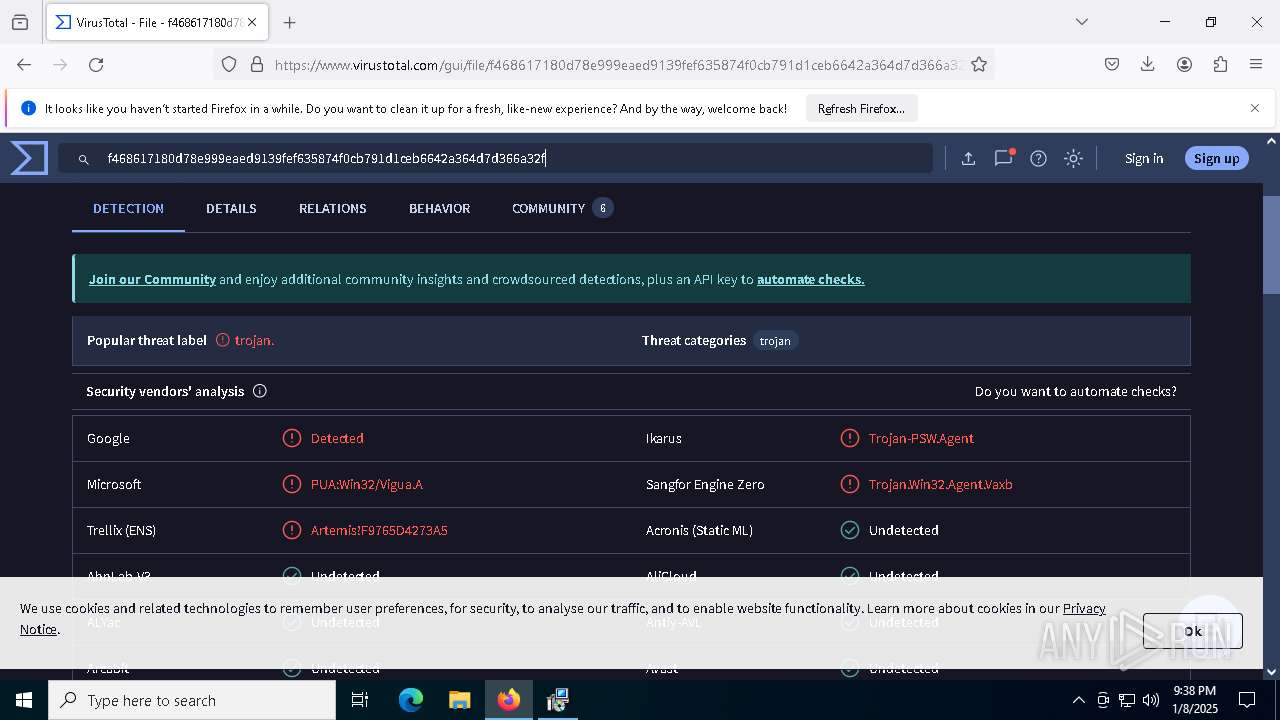
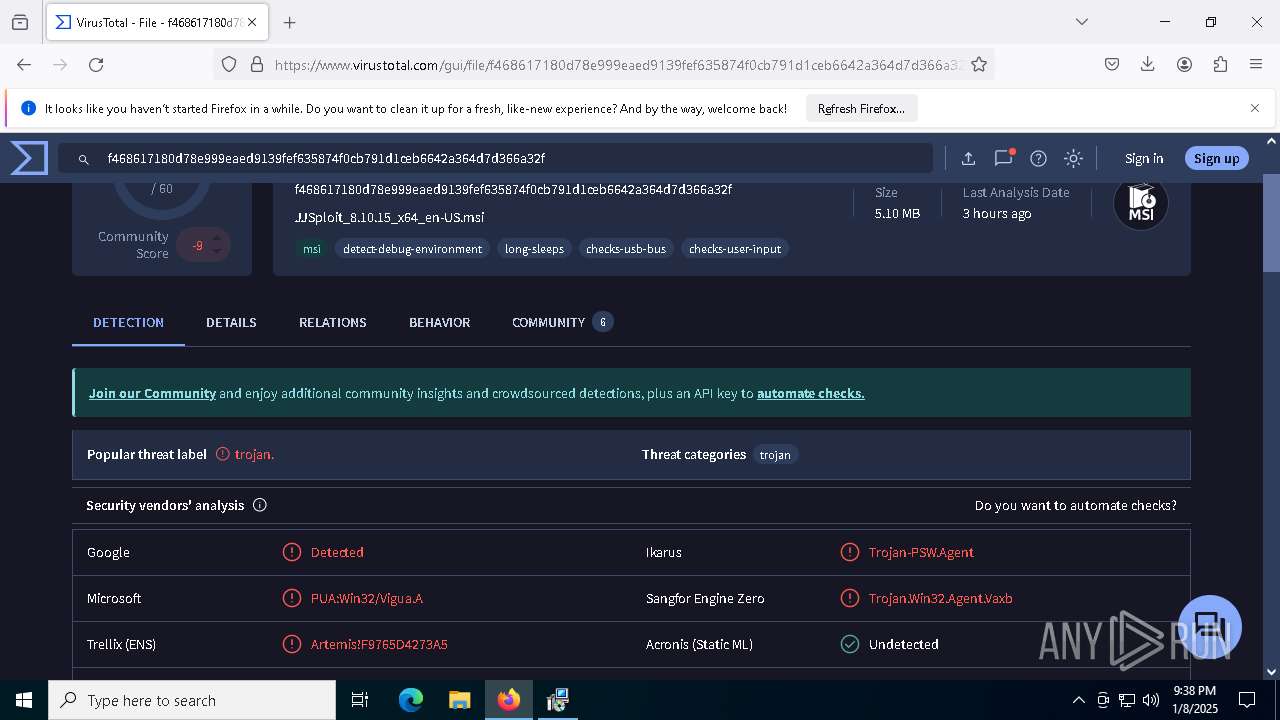
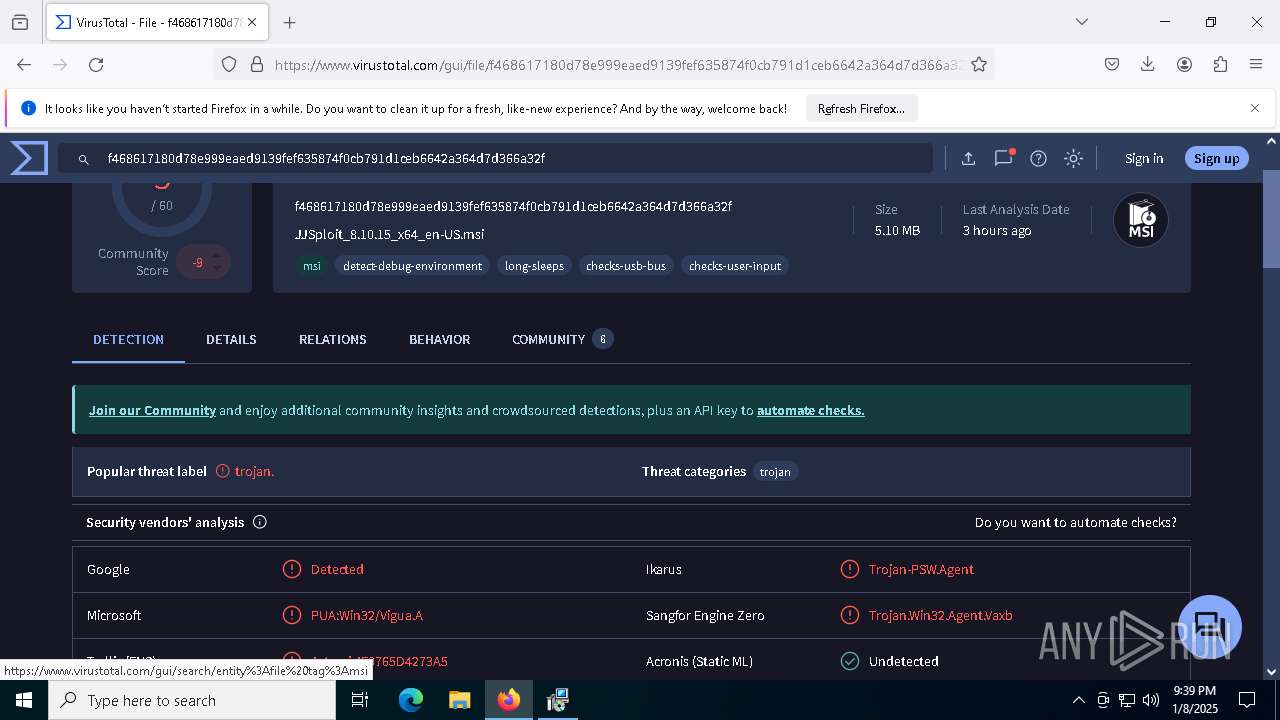
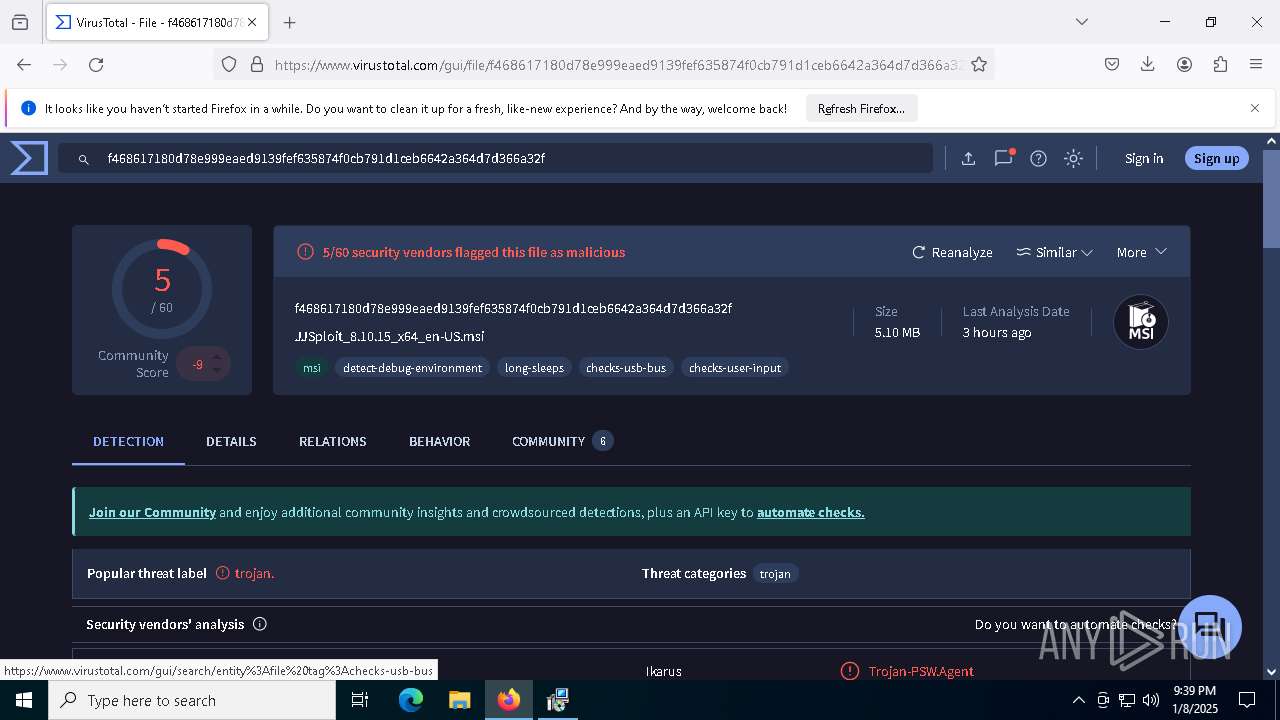
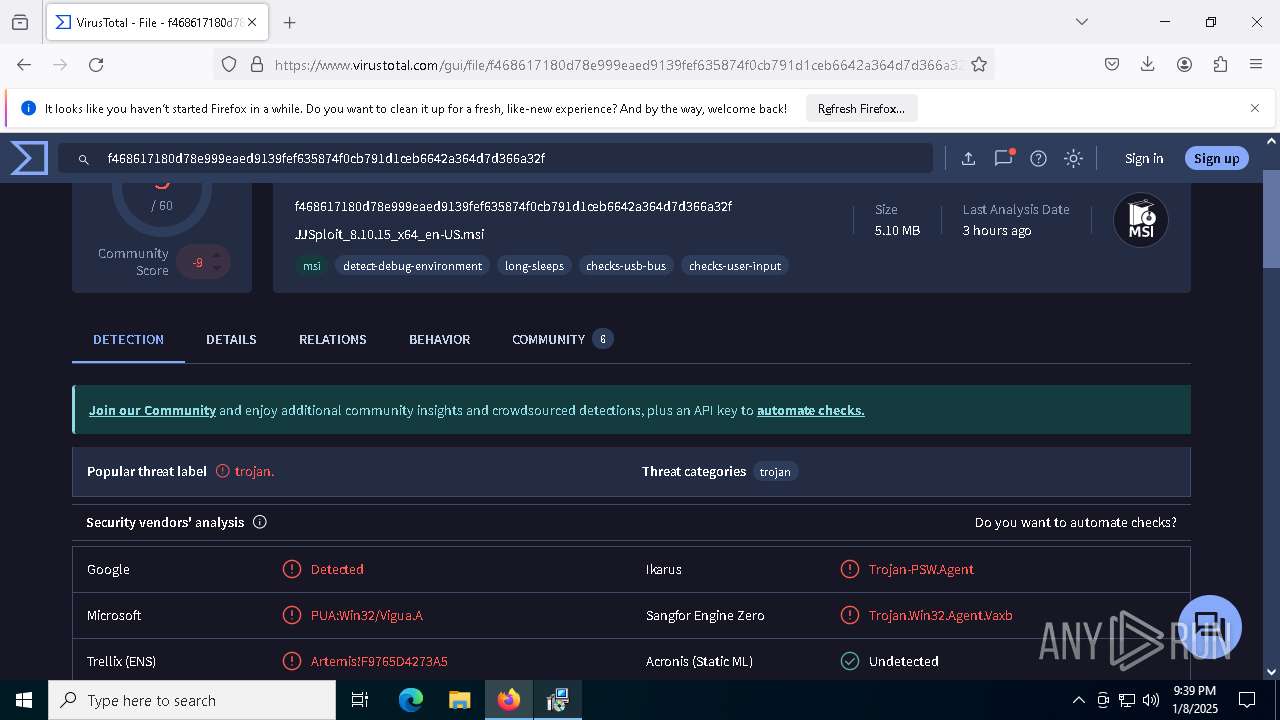
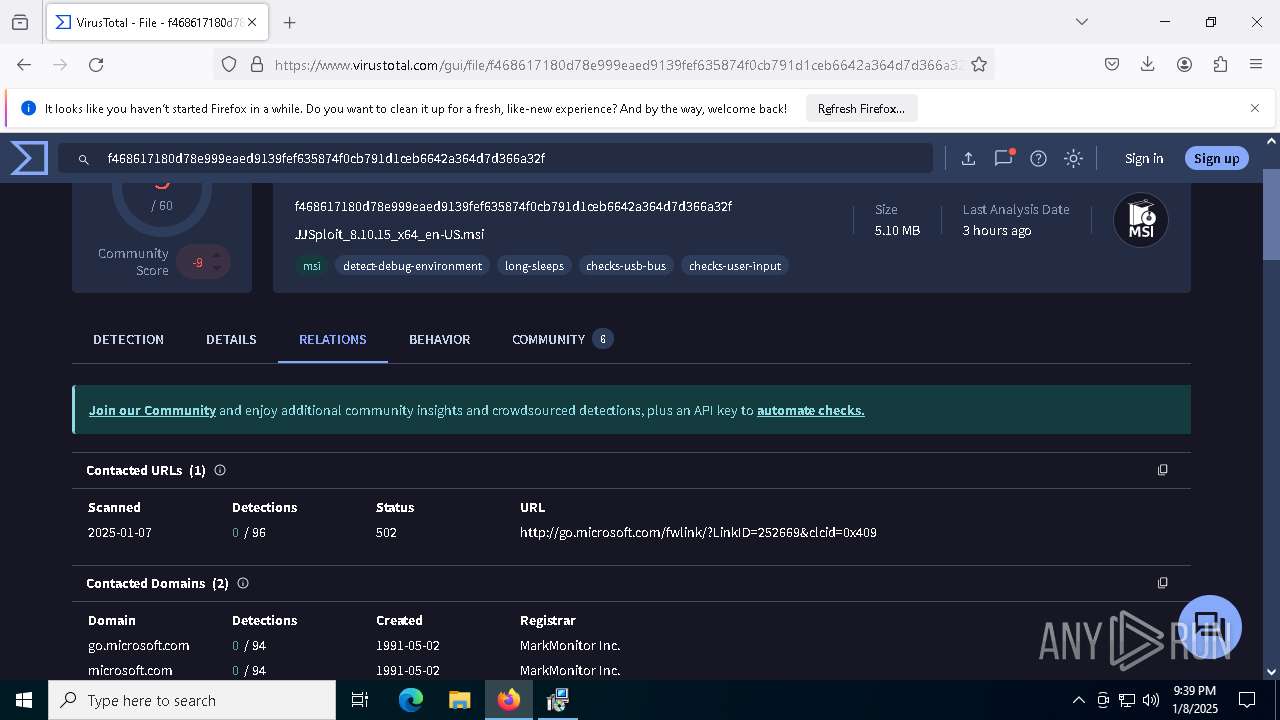
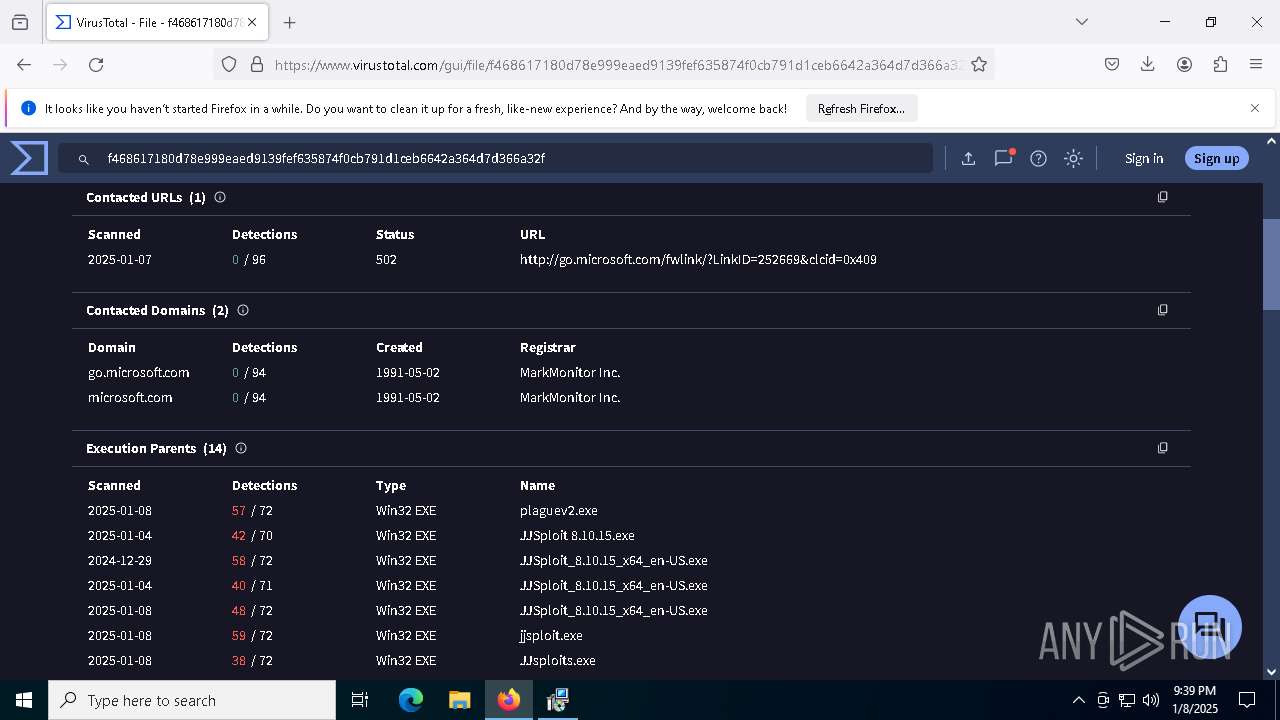
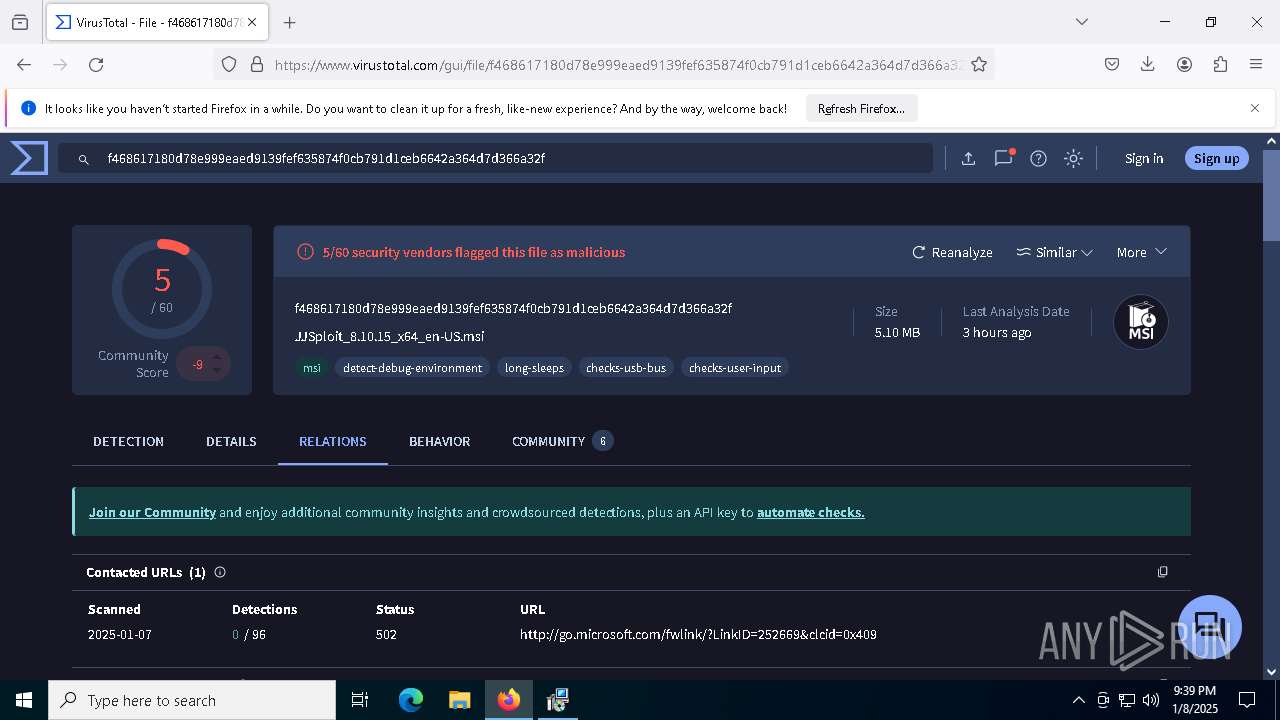
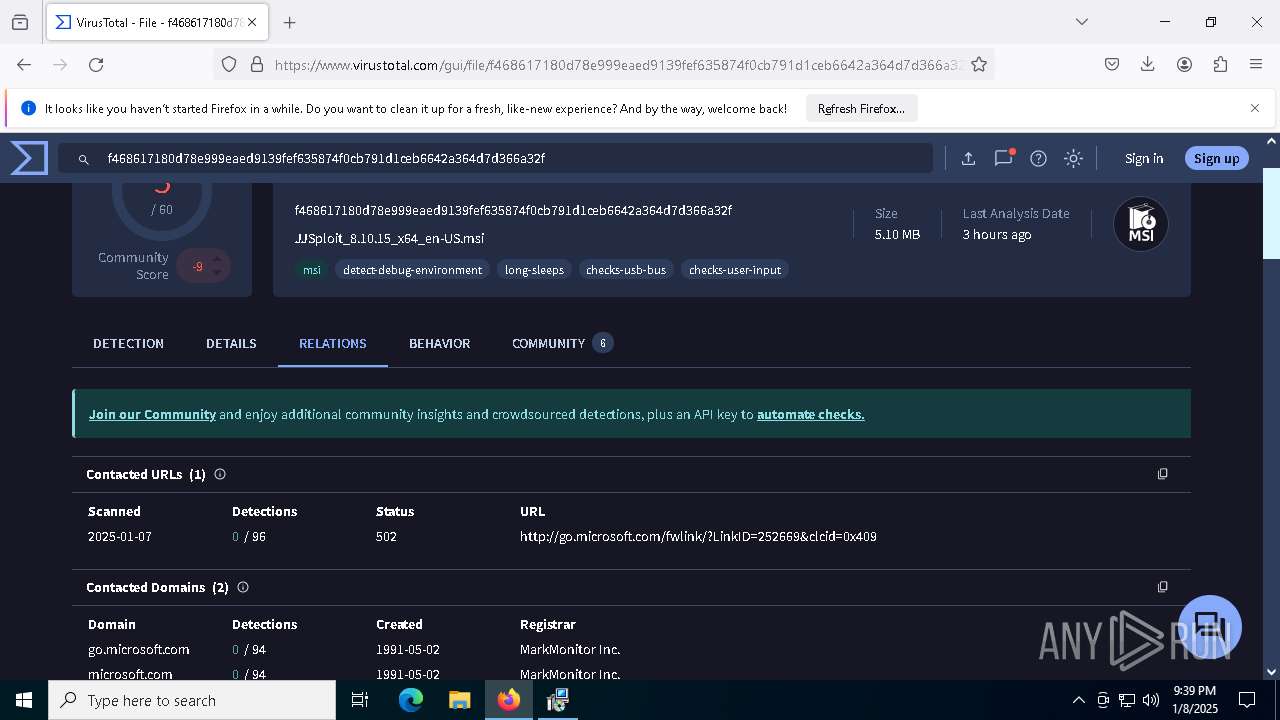
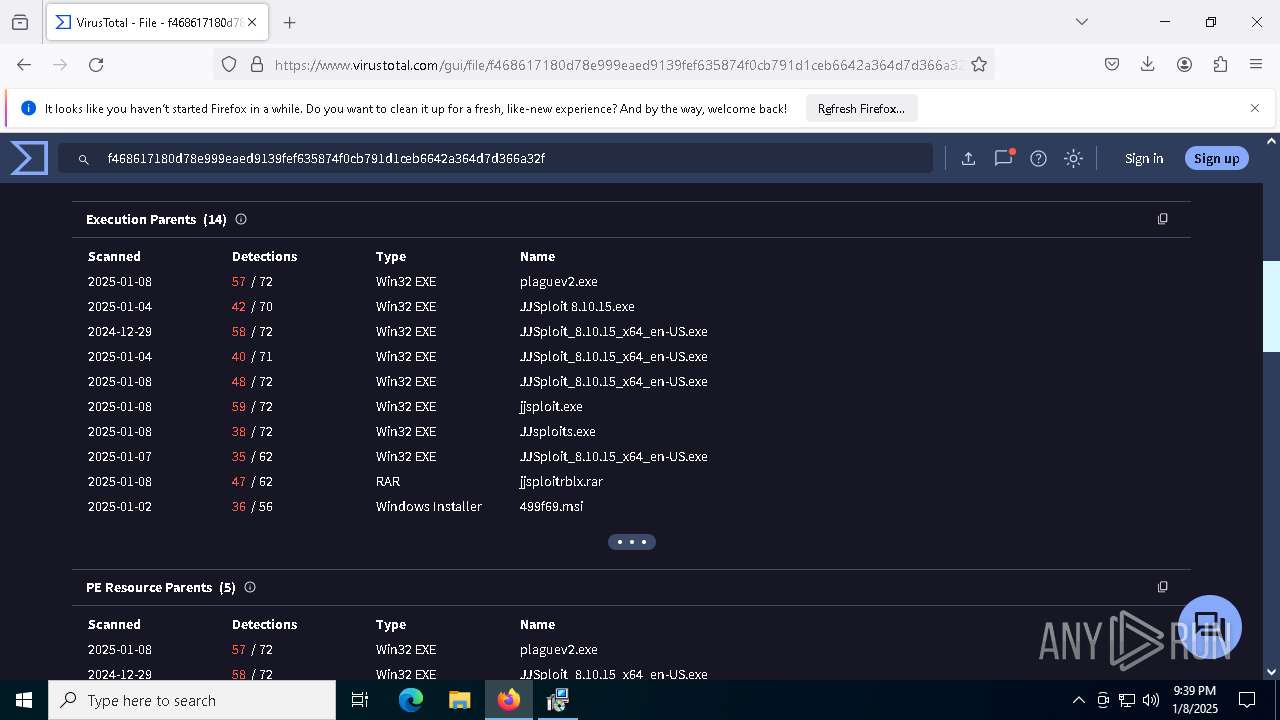
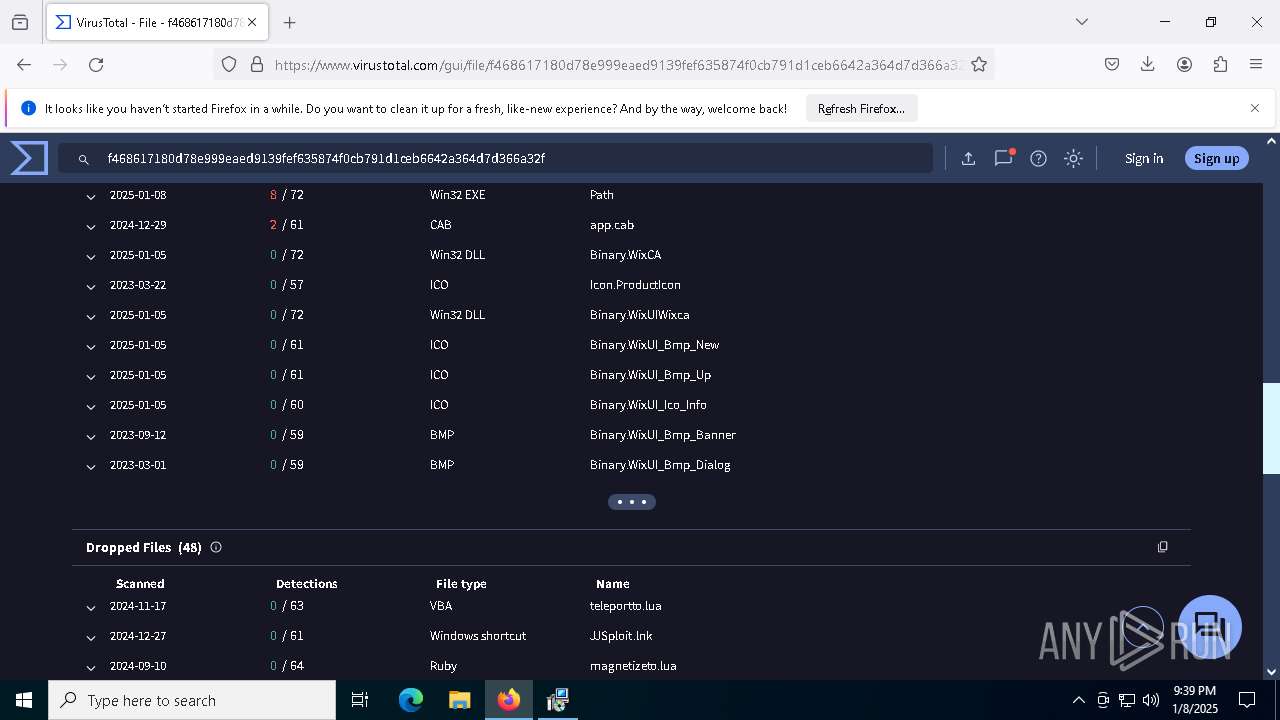
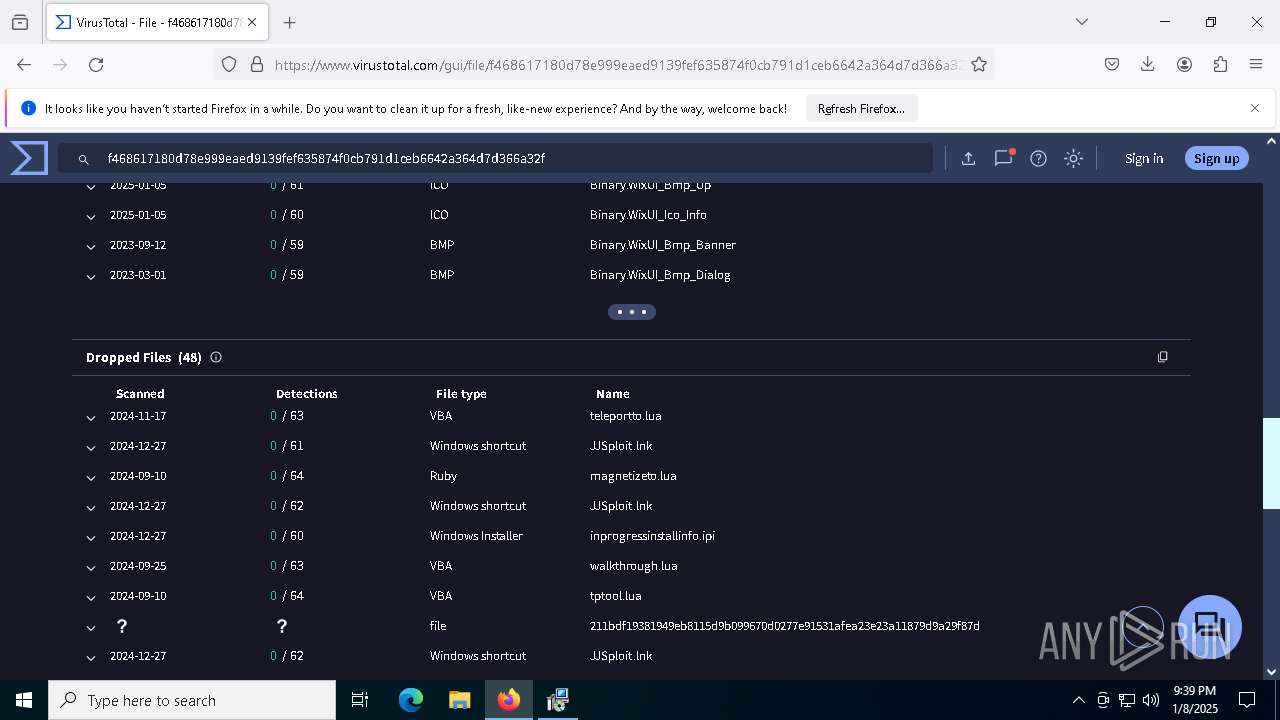
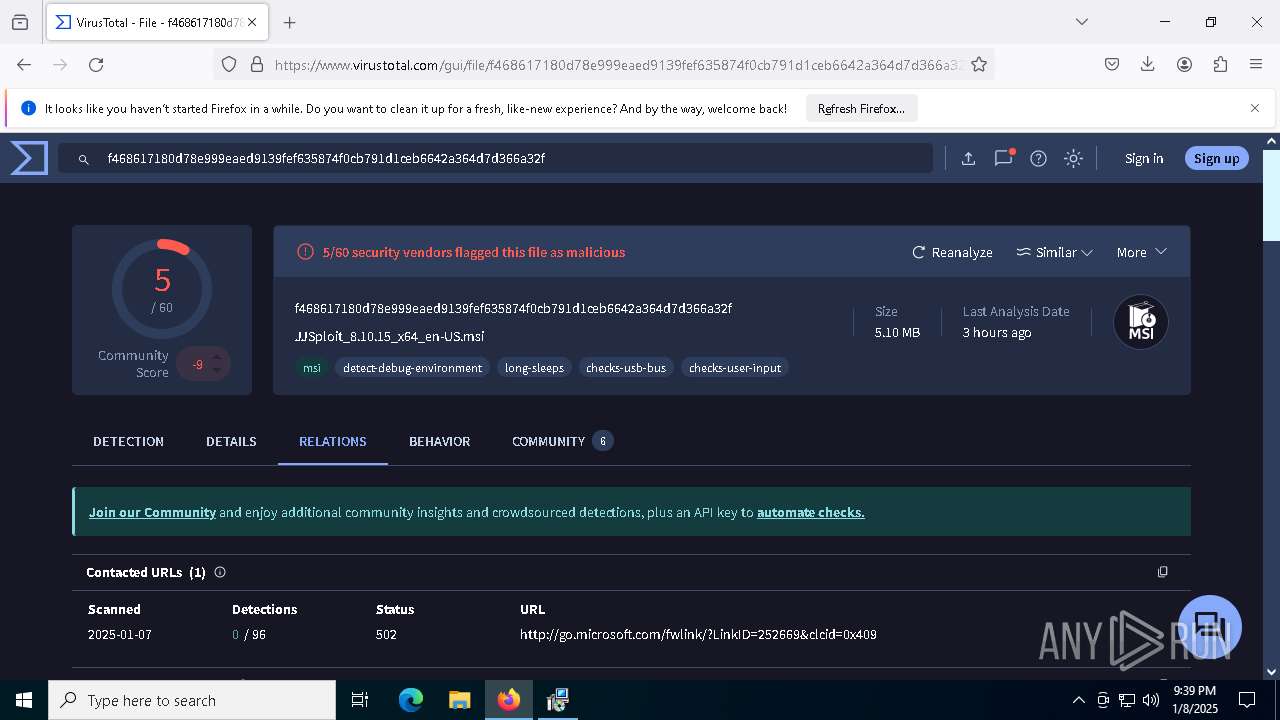
| URL: | https://wearedevs.net/d/JJSploit |
| Full analysis: | https://app.any.run/tasks/6b4e02f4-43ff-40e4-adf7-7791263735a1 |
| Verdict: | Malicious activity |
| Analysis date: | January 08, 2025, 21:36:49 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MD5: | AF4F0F3F58AF746C6F1F8983436ACBD9 |
| SHA1: | 09E980C8D1D92C3DF8498BD3A725CB83F4314AAB |
| SHA256: | 484ABDB18866BC82426BE62FDF91D5C82FB9C951B25C22B00E1AA3EFC95E4B95 |
| SSDEEP: | 3:N8R/BApK83BQ:25BuBq |
MALICIOUS
Run PowerShell with an invisible window
- powershell.exe (PID: 6236)
Changes the autorun value in the registry
- MicrosoftEdgeUpdate.exe (PID: 4996)
SUSPICIOUS
Executes as Windows Service
- VSSVC.exe (PID: 1448)
Reads the Windows owner or organization settings
- msiexec.exe (PID: 5836)
Manipulates environment variables
- powershell.exe (PID: 6236)
Starts process via Powershell
- powershell.exe (PID: 6236)
Starts POWERSHELL.EXE for commands execution
- msiexec.exe (PID: 5836)
The process bypasses the loading of PowerShell profile settings
- msiexec.exe (PID: 5836)
Downloads file from URI via Powershell
- powershell.exe (PID: 6236)
Executable content was dropped or overwritten
- powershell.exe (PID: 6236)
- MicrosoftEdgeWebview2Setup.exe (PID: 6420)
- MicrosoftEdgeUpdate.exe (PID: 4996)
- MicrosoftEdge_X64_131.0.2903.112.exe (PID: 7852)
Process drops legitimate windows executable
- powershell.exe (PID: 6236)
- MicrosoftEdgeWebview2Setup.exe (PID: 6420)
- MicrosoftEdgeUpdate.exe (PID: 4996)
- MicrosoftEdge_X64_131.0.2903.112.exe (PID: 7852)
Starts a Microsoft application from unusual location
- MicrosoftEdgeWebview2Setup.exe (PID: 6420)
- MicrosoftEdgeUpdate.exe (PID: 4996)
Gets or sets the security protocol (POWERSHELL)
- powershell.exe (PID: 6236)
Starts itself from another location
- MicrosoftEdgeUpdate.exe (PID: 4996)
Creates/Modifies COM task schedule object
- MicrosoftEdgeUpdateComRegisterShell64.exe (PID: 7888)
- MicrosoftEdgeUpdate.exe (PID: 8104)
- MicrosoftEdgeUpdateComRegisterShell64.exe (PID: 6352)
- MicrosoftEdgeUpdateComRegisterShell64.exe (PID: 7324)
Reads security settings of Internet Explorer
- MicrosoftEdgeUpdate.exe (PID: 4996)
- MicrosoftEdgeUpdate.exe (PID: 8136)
Potential Corporate Privacy Violation
- svchost.exe (PID: 6328)
Checks Windows Trust Settings
- MicrosoftEdgeUpdate.exe (PID: 8136)
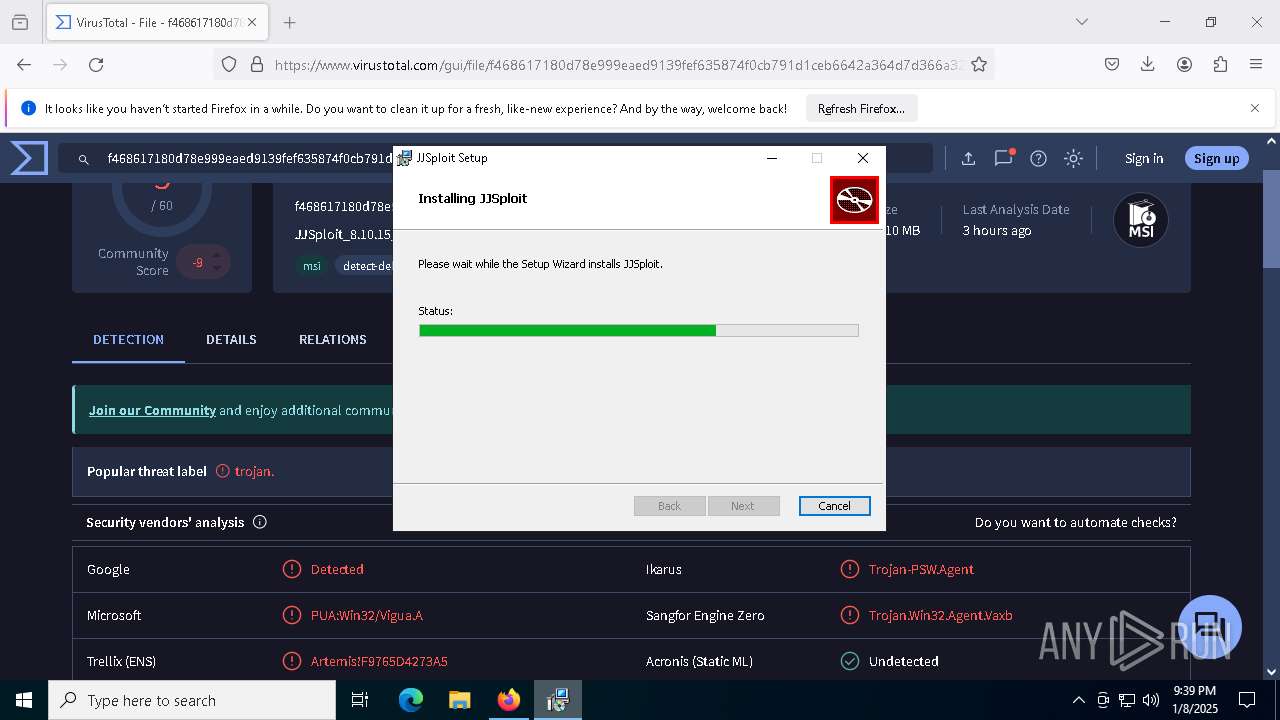
Application launched itself
- setup.exe (PID: 6280)
INFO
Application launched itself
- firefox.exe (PID: 6284)
- firefox.exe (PID: 6388)
Executable content was dropped or overwritten
- firefox.exe (PID: 6388)
- msiexec.exe (PID: 628)
- msiexec.exe (PID: 5836)
Manual execution by a user
- msiexec.exe (PID: 628)
Checks supported languages
- msiexec.exe (PID: 5836)
- msiexec.exe (PID: 3060)
- MicrosoftEdgeWebview2Setup.exe (PID: 6420)
- MicrosoftEdgeUpdate.exe (PID: 8104)
- MicrosoftEdgeUpdateComRegisterShell64.exe (PID: 7888)
- MicrosoftEdgeUpdateComRegisterShell64.exe (PID: 6352)
- MicrosoftEdgeUpdateComRegisterShell64.exe (PID: 7324)
- MicrosoftEdgeUpdate.exe (PID: 4996)
- MicrosoftEdgeUpdate.exe (PID: 2212)
- MicrosoftEdgeUpdate.exe (PID: 8136)
- MicrosoftEdge_X64_131.0.2903.112.exe (PID: 7852)
- MicrosoftEdgeUpdate.exe (PID: 2136)
- setup.exe (PID: 6280)
- setup.exe (PID: 4308)
The process uses the downloaded file
- firefox.exe (PID: 6388)
- powershell.exe (PID: 6236)
Reads the computer name
- msiexec.exe (PID: 3060)
- msiexec.exe (PID: 5836)
- MicrosoftEdgeUpdate.exe (PID: 4996)
- MicrosoftEdgeUpdateComRegisterShell64.exe (PID: 7324)
- MicrosoftEdgeUpdate.exe (PID: 8104)
- MicrosoftEdgeUpdateComRegisterShell64.exe (PID: 7888)
- MicrosoftEdgeUpdateComRegisterShell64.exe (PID: 6352)
- MicrosoftEdgeUpdate.exe (PID: 2212)
- MicrosoftEdgeUpdate.exe (PID: 8136)
- MicrosoftEdgeUpdate.exe (PID: 2136)
- MicrosoftEdge_X64_131.0.2903.112.exe (PID: 7852)
- setup.exe (PID: 6280)
Manages system restore points
- SrTasks.exe (PID: 2976)
Creates a software uninstall entry
- msiexec.exe (PID: 5836)
Disables trace logs
- powershell.exe (PID: 6236)
Checks proxy server information
- powershell.exe (PID: 6236)
- MicrosoftEdgeUpdate.exe (PID: 2136)
- MicrosoftEdgeUpdate.exe (PID: 8136)
The sample compiled with english language support
- powershell.exe (PID: 6236)
- MicrosoftEdgeWebview2Setup.exe (PID: 6420)
- MicrosoftEdgeUpdate.exe (PID: 4996)
- MicrosoftEdge_X64_131.0.2903.112.exe (PID: 7852)
The executable file from the user directory is run by the Powershell process
- MicrosoftEdgeWebview2Setup.exe (PID: 6420)
Create files in a temporary directory
- MicrosoftEdgeWebview2Setup.exe (PID: 6420)
- MicrosoftEdgeUpdate.exe (PID: 4996)
- svchost.exe (PID: 6328)
Creates files or folders in the user directory
- MicrosoftEdgeUpdate.exe (PID: 4996)
- MicrosoftEdgeUpdate.exe (PID: 8136)
- setup.exe (PID: 4308)
- setup.exe (PID: 6280)
- MicrosoftEdge_X64_131.0.2903.112.exe (PID: 7852)
Reads the software policy settings
- MicrosoftEdgeUpdate.exe (PID: 8136)
- MicrosoftEdgeUpdate.exe (PID: 2136)
Process checks computer location settings
- MicrosoftEdgeUpdate.exe (PID: 4996)
Reads the machine GUID from the registry
- MicrosoftEdgeUpdate.exe (PID: 8136)
Reads Environment values
- MicrosoftEdgeUpdate.exe (PID: 2136)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
172
Monitored processes
39
Malicious processes
5
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 236 | "C:\Program Files\Mozilla Firefox\firefox.exe" -contentproc --channel=5200 -childID 6 -isForBrowser -prefsHandle 5192 -prefMapHandle 5052 -prefsLen 36588 -prefMapSize 244583 -jsInitHandle 1348 -jsInitLen 235124 -parentBuildID 20240213221259 -win32kLockedDown -appDir "C:\Program Files\Mozilla Firefox\browser" - {30ba613d-c286-4c75-8c10-a3844bf8c0ab} 6388 "\\.\pipe\gecko-crash-server-pipe.6388" 227b1ccbbd0 tab | C:\Program Files\Mozilla Firefox\firefox.exe | — | firefox.exe | |||||||||||
User: admin Company: Mozilla Corporation Integrity Level: MEDIUM Description: Firefox Version: 123.0 Modules
| |||||||||||||||
| 628 | "C:\WINDOWS\System32\msiexec.exe" /i "C:\Users\admin\Downloads\JJSploit_8.10.15_x64_en-US.msi" | C:\Windows\System32\msiexec.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows® installer Version: 5.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1448 | C:\WINDOWS\system32\vssvc.exe | C:\Windows\System32\VSSVC.exe | — | services.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Microsoft® Volume Shadow Copy Service Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2136 | "C:\Users\admin\AppData\Local\Microsoft\EdgeUpdate\MicrosoftEdgeUpdate.exe" /ping PD94bWwgdmVyc2lvbj0iMS4wIiBlbmNvZGluZz0iVVRGLTgiPz48cmVxdWVzdCBwcm90b2NvbD0iMy4wIiB1cGRhdGVyPSJPbWFoYSIgdXBkYXRlcnZlcnNpb249IjEuMy4xOTUuNDMiIHNoZWxsX3ZlcnNpb249IjEuMy4xOTUuNDMiIGlzbWFjaGluZT0iMCIgc2Vzc2lvbmlkPSJ7MTNFMjk0QkUtRUI2MC00RTI3LUFDQzItRjcyNzg0RjVGNjU5fSIgdXNlcmlkPSJ7MjQ0Q0FFQzAtMzBDQi00QzA2LTgyREQtQjNDMTZEMjIwMjQ3fSIgaW5zdGFsbHNvdXJjZT0ib3RoZXJpbnN0YWxsY21kIiByZXF1ZXN0aWQ9Ins1Q0YwM0UyRS0wMkM2LTQ5ODUtQTVCNS1CNDIzM0FEQzI5NEJ9IiBkZWR1cD0iY3IiIGRvbWFpbmpvaW5lZD0iMCI-PGh3IGxvZ2ljYWxfY3B1cz0iNCIgcGh5c21lbW9yeT0iNCIgZGlza190eXBlPSIyIiBzc2U9IjEiIHNzZTI9IjEiIHNzZTM9IjEiIHNzc2UzPSIxIiBzc2U0MT0iMSIgc3NlNDI9IjEiIGF2eD0iMSIvPjxvcyBwbGF0Zm9ybT0id2luIiB2ZXJzaW9uPSIxMC4wLjE5MDQ1LjQwNDYiIHNwPSIiIGFyY2g9Ing2NCIgcHJvZHVjdF90eXBlPSI0OCIgaXNfd2lwPSIwIiBpc19pbl9sb2NrZG93bl9tb2RlPSIwIi8-PG9lbSBwcm9kdWN0X21hbnVmYWN0dXJlcj0iREVMTCIgcHJvZHVjdF9uYW1lPSJERUxMIi8-PGV4cCBldGFnPSIiLz48YXBwIGFwcGlkPSJ7RjNDNEZFMDAtRUZENS00MDNCLTk1NjktMzk4QTIwRjFCQTRBfSIgdmVyc2lvbj0iIiBuZXh0dmVyc2lvbj0iMS4zLjE5NS40MyIgbGFuZz0iIiBicmFuZD0iIiBjbGllbnQ9IiI-PGV2ZW50IGV2ZW50dHlwZT0iMiIgZXZlbnRyZXN1bHQ9IjEiIGVycm9yY29kZT0iMCIgZXh0cmFjb2RlMT0iMCIgc3lzdGVtX3VwdGltZV90aWNrcz0iMTM4NjAzMTU2NTQiIGluc3RhbGxfdGltZV9tcz0iMjAwNCIvPjwvYXBwPjwvcmVxdWVzdD4 | C:\Users\admin\AppData\Local\Microsoft\EdgeUpdate\MicrosoftEdgeUpdate.exe | MicrosoftEdgeUpdate.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Edge Update Exit code: 0 Version: 1.3.195.43 Modules
| |||||||||||||||
| 2212 | "C:\Users\admin\AppData\Local\Microsoft\EdgeUpdate\MicrosoftEdgeUpdate.exe" /handoff "appguid={F3017226-FE2A-4295-8BDF-00C3A9A7E4C5}&appname=Microsoft%20Edge%20Webview2%20Runtime&needsadmin=false" /installsource otherinstallcmd /sessionid "{13E294BE-EB60-4E27-ACC2-F72784F5F659}" /silent | C:\Users\admin\AppData\Local\Microsoft\EdgeUpdate\MicrosoftEdgeUpdate.exe | — | MicrosoftEdgeUpdate.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Edge Update Version: 1.3.195.43 Modules
| |||||||||||||||
| 2976 | C:\WINDOWS\system32\srtasks.exe ExecuteScopeRestorePoint /WaitForRestorePoint:11 | C:\Windows\System32\SrTasks.exe | — | msiexec.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Microsoft® Windows System Protection background tasks. Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3060 | C:\Windows\syswow64\MsiExec.exe -Embedding 3085D035FE71F74E0938D037119BD1E7 C | C:\Windows\SysWOW64\msiexec.exe | — | msiexec.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows® installer Version: 5.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3836 | "C:\Program Files\Mozilla Firefox\firefox.exe" -contentproc --channel=5180 -childID 11 -isForBrowser -prefsHandle 6696 -prefMapHandle 6692 -prefsLen 32214 -prefMapSize 244583 -jsInitHandle 1348 -jsInitLen 235124 -parentBuildID 20240213221259 -win32kLockedDown -appDir "C:\Program Files\Mozilla Firefox\browser" - {353a45ed-f945-46e1-b5a0-a246f7d87888} 6388 "\\.\pipe\gecko-crash-server-pipe.6388" 227b1bf3bd0 tab | C:\Program Files\Mozilla Firefox\firefox.exe | — | firefox.exe | |||||||||||
User: admin Company: Mozilla Corporation Integrity Level: MEDIUM Description: Firefox Version: 123.0 Modules
| |||||||||||||||
| 4012 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | SrTasks.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4308 | C:\Users\admin\AppData\Local\Microsoft\EdgeUpdate\Install\{6486C2C7-AD72-462D-870B-F39A3A1F80DC}\EDGEMITMP_2AA67.tmp\setup.exe --type=crashpad-handler /prefetch:4 --monitor-self-annotation=ptype=crashpad-handler "--database=C:\Users\admin\AppData\Local\Microsoft\EdgeWebView\User Data\Crashpad" --annotation=IsOfficialBuild=1 --annotation=channel= --annotation=chromium-version=131.0.6778.205 --annotation=exe=C:\Users\admin\AppData\Local\Microsoft\EdgeUpdate\Install\{6486C2C7-AD72-462D-870B-F39A3A1F80DC}\EDGEMITMP_2AA67.tmp\setup.exe --annotation=plat=Win64 --annotation=prod=Edge --annotation=ver=131.0.2903.112 --initial-client-data=0x240,0x244,0x248,0x21c,0x24c,0x7ff7c6902918,0x7ff7c6902924,0x7ff7c6902930 | C:\Users\admin\AppData\Local\Microsoft\EdgeUpdate\Install\{6486C2C7-AD72-462D-870B-F39A3A1F80DC}\EDGEMITMP_2AA67.tmp\setup.exe | — | setup.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Edge Installer Version: 131.0.2903.112 Modules
| |||||||||||||||
Total events
42 679
Read events
40 415
Write events
2 205
Delete events
59
Modification events
| (PID) Process: | (6388) firefox.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Mozilla\Firefox\DllPrefetchExperiment |
| Operation: | write | Name: | C:\Program Files\Mozilla Firefox\firefox.exe |
Value: 0 | |||
| (PID) Process: | (5836) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\SystemRestore |
| Operation: | write | Name: | SrCreateRp (Enter) |
Value: 4800000000000000B0C3CE951562DB01CC160000E00C0000D50700000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (5836) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\SPP |
| Operation: | write | Name: | SppGetSnapshots (Enter) |
Value: 48000000000000001416CF951562DB01CC160000E00C0000D20700000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (5836) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\SPP |
| Operation: | write | Name: | SppGetSnapshots (Leave) |
Value: 4800000000000000546F6C961562DB01CC160000E00C0000D20700000100000000000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (5836) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\SPP |
| Operation: | write | Name: | SppEnumGroups (Enter) |
Value: 4800000000000000EE966C961562DB01CC160000E00C0000D10700000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (5836) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\SPP |
| Operation: | write | Name: | SppEnumGroups (Leave) |
Value: 4800000000000000BA9977961562DB01CC160000E00C0000D10700000100000000000000010000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (5836) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\SPP |
| Operation: | write | Name: | SppCreate (Enter) |
Value: 48000000000000008ABC7A961562DB01CC160000E00C0000D00700000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (5836) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\SPP |
| Operation: | write | Name: | LastIndex |
Value: 11 | |||
| (PID) Process: | (5836) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\SPP |
| Operation: | write | Name: | SppGatherWriterMetadata (Enter) |
Value: 480000000000000039E4DC971562DB01CC160000E00C0000D30700000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (5836) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\VssapiPublisher |
| Operation: | write | Name: | IDENTIFY (Enter) |
Value: 48000000000000008530E4971562DB01CC16000030170000E8030000010000000000000000000000244E94AA9FE3974796925C82A5685E6F00000000000000000000000000000000 | |||
Executable files
207
Suspicious files
260
Text files
83
Unknown types
7
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 6388 | firefox.exe | C:\Users\admin\AppData\Local\Mozilla\Firefox\Profiles\9kie7cg6.default-release\startupCache\scriptCache-current.bin | — | |
MD5:— | SHA256:— | |||
| 6388 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\9kie7cg6.default-release\SiteSecurityServiceState.bin | binary | |
MD5:BDADFF9AFE3783A5EB7BE5493B6D3B2F | SHA256:6EF0776C8AD1FBFB93320D7AAE99A0B6DECA9A6DD5422C7CE624B634A4397946 | |||
| 6388 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\9kie7cg6.default-release\storage\permanent\chrome\idb\3870112724rsegmnoittet-es.sqlite | — | |
MD5:— | SHA256:— | |||
| 6388 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\9kie7cg6.default-release\sessionCheckpoints.json.tmp | binary | |
MD5:EA8B62857DFDBD3D0BE7D7E4A954EC9A | SHA256:792955295AE9C382986222C6731C5870BD0E921E7F7E34CC4615F5CD67F225DA | |||
| 6388 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\9kie7cg6.default-release\sessionCheckpoints.json | binary | |
MD5:EA8B62857DFDBD3D0BE7D7E4A954EC9A | SHA256:792955295AE9C382986222C6731C5870BD0E921E7F7E34CC4615F5CD67F225DA | |||
| 6388 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\9kie7cg6.default-release\prefs.js | text | |
MD5:2C99A16AED3906D92FFE3EF1808E2753 | SHA256:08412578CC3BB4922388F8FF8C23962F616B69A1588DA720ADE429129C73C452 | |||
| 6388 | firefox.exe | C:\Users\admin\AppData\Local\Mozilla\Firefox\Profiles\9kie7cg6.default-release\startupCache\urlCache-current.bin | binary | |
MD5:297E88D7CEB26E549254EC875649F4EB | SHA256:8B75D4FB1845BAA06122888D11F6B65E6A36B140C54A72CC13DF390FD7C95702 | |||
| 6388 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\9kie7cg6.default-release\storage\permanent\chrome\idb\3870112724rsegmnoittet-es.sqlite-shm | binary | |
MD5:B7C14EC6110FA820CA6B65F5AEC85911 | SHA256:FD4C9FDA9CD3F9AE7C962B0DDF37232294D55580E1AA165AA06129B8549389EB | |||
| 6388 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\9kie7cg6.default-release\prefs-1.js | text | |
MD5:2C99A16AED3906D92FFE3EF1808E2753 | SHA256:08412578CC3BB4922388F8FF8C23962F616B69A1588DA720ADE429129C73C452 | |||
| 6388 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\9kie7cg6.default-release\storage\permanent\chrome\idb\1657114595AmcateirvtiSty.sqlite-shm | binary | |
MD5:B7C14EC6110FA820CA6B65F5AEC85911 | SHA256:FD4C9FDA9CD3F9AE7C962B0DDF37232294D55580E1AA165AA06129B8549389EB | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
67
TCP/UDP connections
240
DNS requests
229
Threats
4
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
6388 | firefox.exe | GET | 200 | 34.107.221.82:80 | http://detectportal.firefox.com/success.txt?ipv4 | unknown | — | — | whitelisted |
6388 | firefox.exe | GET | 200 | 34.107.221.82:80 | http://detectportal.firefox.com/canonical.html | unknown | — | — | whitelisted |
6388 | firefox.exe | POST | 200 | 184.24.77.54:80 | http://r11.o.lencr.org/ | unknown | — | — | whitelisted |
6388 | firefox.exe | POST | 200 | 184.24.77.79:80 | http://r10.o.lencr.org/ | unknown | — | — | whitelisted |
— | — | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
5064 | SearchApp.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
— | — | GET | 200 | 23.32.238.112:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
6388 | firefox.exe | POST | 200 | 142.250.181.227:80 | http://o.pki.goog/s/wr3/jLM | unknown | — | — | whitelisted |
6388 | firefox.exe | POST | — | 184.24.77.79:80 | http://r10.o.lencr.org/ | unknown | — | — | whitelisted |
6388 | firefox.exe | POST | 200 | 184.24.77.79:80 | http://r10.o.lencr.org/ | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4712 | MoUsoCoreWorker.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
5064 | SearchApp.exe | 104.126.37.145:443 | www.bing.com | Akamai International B.V. | DE | whitelisted |
— | — | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
5064 | SearchApp.exe | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
— | — | 23.32.238.112:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
— | — | 184.30.21.171:80 | www.microsoft.com | AKAMAI-AS | DE | unknown |
5732 | svchost.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
1076 | svchost.exe | 23.35.238.131:443 | go.microsoft.com | AKAMAI-AS | DE | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
www.bing.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
go.microsoft.com |
| whitelisted |
wearedevs.net |
| whitelisted |
detectportal.firefox.com |
| whitelisted |
prod.detectportal.prod.cloudops.mozgcp.net |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2192 | svchost.exe | Not Suspicious Traffic | INFO [ANY.RUN] Attempting to access raw user content on GitHub |
2192 | svchost.exe | Not Suspicious Traffic | INFO [ANY.RUN] Attempting to access raw user content on GitHub |
2192 | svchost.exe | Not Suspicious Traffic | INFO [ANY.RUN] Attempting to access raw user content on GitHub |
6328 | svchost.exe | Potential Corporate Privacy Violation | ET POLICY PE EXE or DLL Windows file download HTTP |