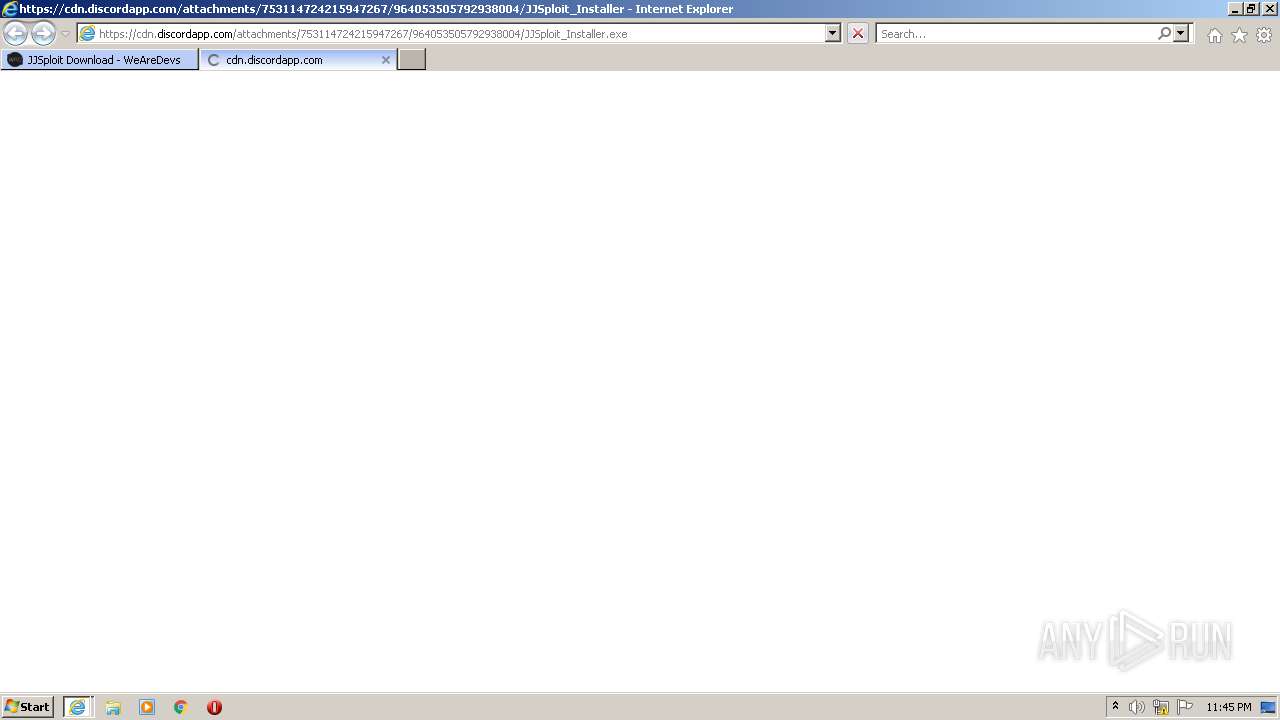
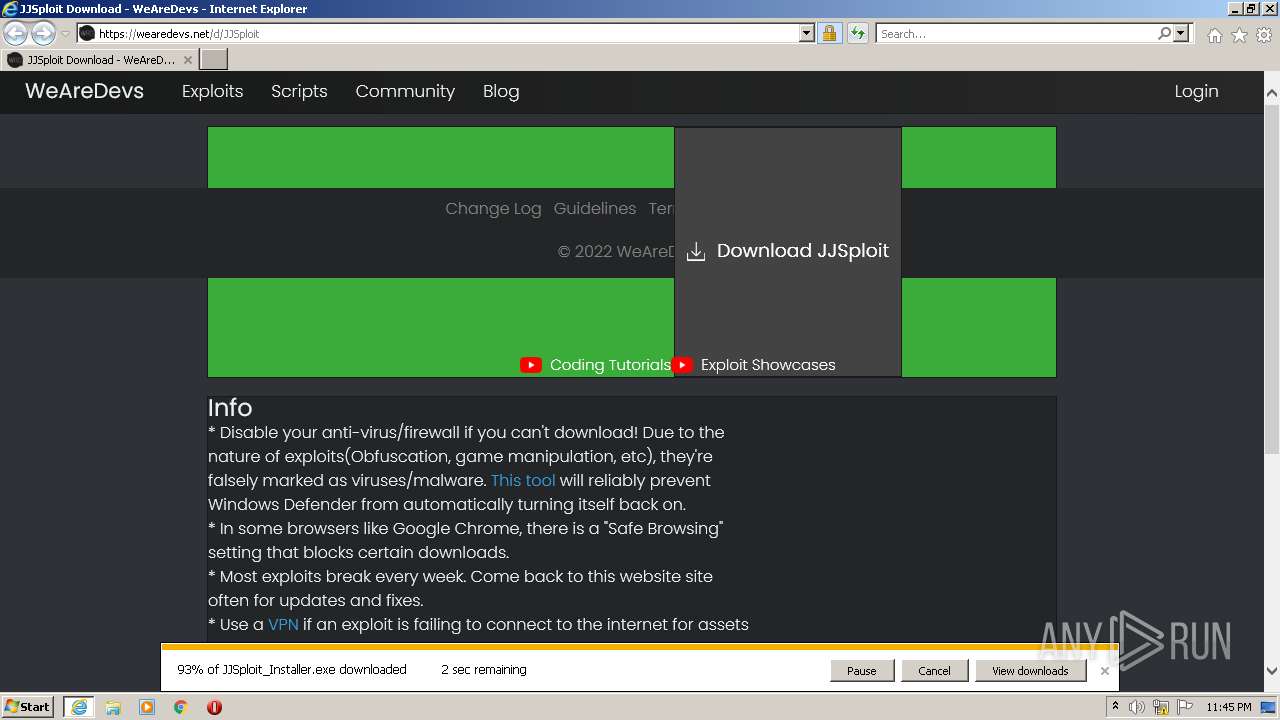
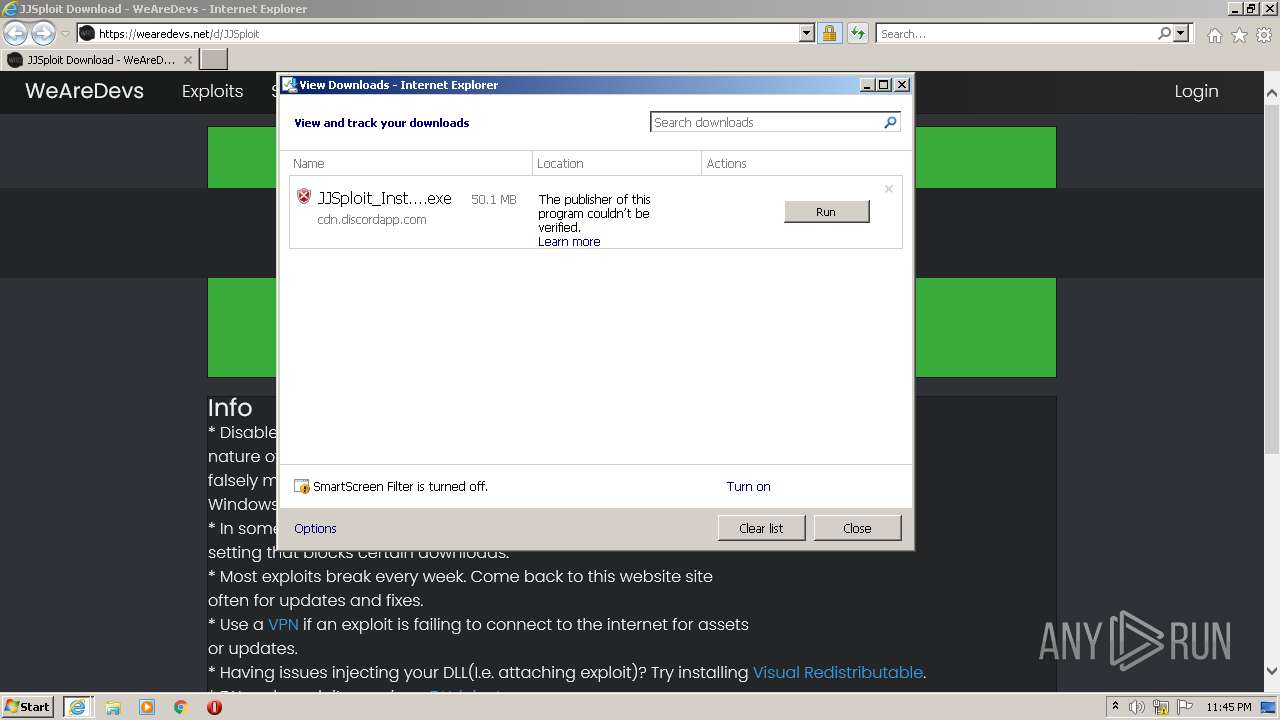
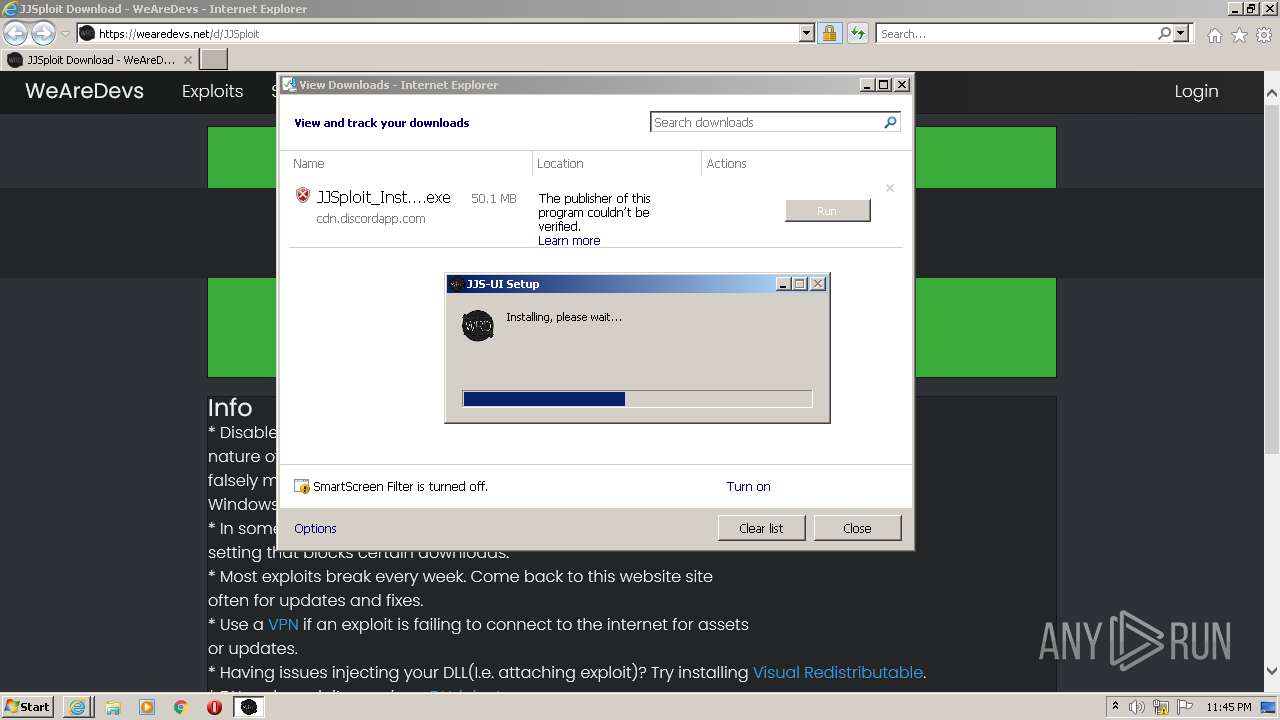
| URL: | https://wearedevs.net/d/JJSploit |
| Full analysis: | https://app.any.run/tasks/3a5b901c-6c2e-425d-848e-49d9330c5872 |
| Verdict: | Malicious activity |
| Analysis date: | May 03, 2022, 22:44:49 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MD5: | AF4F0F3F58AF746C6F1F8983436ACBD9 |
| SHA1: | 09E980C8D1D92C3DF8498BD3A725CB83F4314AAB |
| SHA256: | 484ABDB18866BC82426BE62FDF91D5C82FB9C951B25C22B00E1AA3EFC95E4B95 |
| SSDEEP: | 3:N8R/BApK83BQ:25BuBq |
MALICIOUS
Application was dropped or rewritten from another process
- JJSploit_Installer.exe (PID: 2700)
Drops executable file immediately after starts
- JJSploit_Installer.exe (PID: 2700)
- JJS-UI.exe (PID: 3268)
- iexplore.exe (PID: 3860)
Loads dropped or rewritten executable
- JJSploit_Installer.exe (PID: 2700)
- JJS-UI.exe (PID: 3268)
- JJS-UI.exe (PID: 2492)
- JJS-UI.exe (PID: 3904)
- JJS-UI.exe (PID: 2796)
- JJS-UI.exe (PID: 2432)
SUSPICIOUS
Reads Microsoft Outlook installation path
- iexplore.exe (PID: 3804)
- iexplore.exe (PID: 3860)
- iexplore.exe (PID: 3836)
Executable content was dropped or overwritten
- iexplore.exe (PID: 3860)
- JJSploit_Installer.exe (PID: 2700)
- JJS-UI.exe (PID: 3268)
Checks supported languages
- JJSploit_Installer.exe (PID: 2700)
- JJS-UI.exe (PID: 3268)
- JJS-UI.exe (PID: 3904)
- JJS-UI.exe (PID: 2796)
- JJS-UI.exe (PID: 2432)
- JJS-UI.exe (PID: 2492)
Reads the computer name
- JJSploit_Installer.exe (PID: 2700)
- JJS-UI.exe (PID: 3268)
- JJS-UI.exe (PID: 2492)
- JJS-UI.exe (PID: 3904)
- JJS-UI.exe (PID: 2432)
Drops a file with a compile date too recent
- JJSploit_Installer.exe (PID: 2700)
- iexplore.exe (PID: 3860)
- JJS-UI.exe (PID: 3268)
Creates a software uninstall entry
- JJSploit_Installer.exe (PID: 2700)
Creates files in the user directory
- JJS-UI.exe (PID: 3268)
- JJSploit_Installer.exe (PID: 2700)
- JJS-UI.exe (PID: 3904)
Application launched itself
- JJS-UI.exe (PID: 3268)
INFO
Application launched itself
- iexplore.exe (PID: 2932)
Checks supported languages
- iexplore.exe (PID: 2932)
- iexplore.exe (PID: 3804)
- iexplore.exe (PID: 3860)
- iexplore.exe (PID: 3836)
Changes internet zones settings
- iexplore.exe (PID: 2932)
Reads settings of System Certificates
- iexplore.exe (PID: 3804)
- iexplore.exe (PID: 2932)
- iexplore.exe (PID: 3860)
- JJS-UI.exe (PID: 3904)
- iexplore.exe (PID: 3836)
Reads internet explorer settings
- iexplore.exe (PID: 3804)
- iexplore.exe (PID: 3860)
- iexplore.exe (PID: 3836)
Reads the computer name
- iexplore.exe (PID: 3804)
- iexplore.exe (PID: 2932)
- iexplore.exe (PID: 3860)
- iexplore.exe (PID: 3836)
Checks Windows Trust Settings
- iexplore.exe (PID: 3804)
- iexplore.exe (PID: 2932)
- iexplore.exe (PID: 3860)
- iexplore.exe (PID: 3836)
Creates files in the user directory
- iexplore.exe (PID: 3804)
- iexplore.exe (PID: 3860)
- iexplore.exe (PID: 3836)
Modifies the phishing filter of IE
- iexplore.exe (PID: 2932)
Manual execution by user
- JJS-UI.exe (PID: 3268)
Reads the hosts file
- JJS-UI.exe (PID: 3268)
- JJS-UI.exe (PID: 3904)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
44
Monitored processes
10
Malicious processes
3
Suspicious processes
3
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 2432 | "C:\Users\admin\AppData\Local\Programs\JJS-UI\JJS-UI.exe" --type=gpu-process --field-trial-handle=1076,7099226105656174887,4755176932233472920,131072 --enable-features=WebComponentsV0Enabled --disable-features=SpareRendererForSitePerProcess --gpu-preferences=KAAAAAAAAADgAAAwAAAAAAAAYAAAAAAAEAAAAAAAAAAAAAAAAAAAACgAAAAEAAAAIAAAAAAAAAAoAAAAAAAAADAAAAAAAAAAOAAAAAAAAAAQAAAAAAAAAAAAAAAFAAAAEAAAAAAAAAAAAAAABgAAABAAAAAAAAAAAQAAAAUAAAAQAAAAAAAAAAEAAAAGAAAA --use-gl=swiftshader-webgl --mojo-platform-channel-handle=1244 --ignored=" --type=renderer " /prefetch:2 | C:\Users\admin\AppData\Local\Programs\JJS-UI\JJS-UI.exe | — | JJS-UI.exe | |||||||||||
User: admin Company: GitHub, Inc. Integrity Level: LOW Description: JJS-UI Exit code: 0 Version: 6.4.8 Modules
| |||||||||||||||
| 2492 | "C:\Users\admin\AppData\Local\Programs\JJS-UI\JJS-UI.exe" --type=gpu-process --field-trial-handle=1076,7099226105656174887,4755176932233472920,131072 --enable-features=WebComponentsV0Enabled --disable-features=SpareRendererForSitePerProcess --gpu-preferences=KAAAAAAAAADgAAAwAAAAAAAAYAAAAAAAEAAAAAAAAAAAAAAAAAAAACgAAAAEAAAAIAAAAAAAAAAoAAAAAAAAADAAAAAAAAAAOAAAAAAAAAAQAAAAAAAAAAAAAAAFAAAAEAAAAAAAAAAAAAAABgAAABAAAAAAAAAAAQAAAAUAAAAQAAAAAAAAAAEAAAAGAAAA --mojo-platform-channel-handle=1072 --ignored=" --type=renderer " /prefetch:2 | C:\Users\admin\AppData\Local\Programs\JJS-UI\JJS-UI.exe | — | JJS-UI.exe | |||||||||||
User: admin Company: GitHub, Inc. Integrity Level: LOW Description: JJS-UI Exit code: 0 Version: 6.4.8 Modules
| |||||||||||||||
| 2700 | "C:\Users\admin\Downloads\JJSploit_Installer.exe" | C:\Users\admin\Downloads\JJSploit_Installer.exe | iexplore.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Version: 6.4.8 Modules
| |||||||||||||||
| 2796 | "C:\Users\admin\AppData\Local\Programs\JJS-UI\JJS-UI.exe" --type=renderer --field-trial-handle=1076,7099226105656174887,4755176932233472920,131072 --enable-features=WebComponentsV0Enabled --disable-features=SpareRendererForSitePerProcess --lang=en-US --app-path="C:\Users\admin\AppData\Local\Programs\JJS-UI\resources\app.asar" --no-sandbox --no-zygote --preload="C:\Users\admin\AppData\Local\Programs\JJS-UI\resources\app.asar\build\preload.js" --enable-remote-module --background-color=#fff --enable-websql --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=5 --no-v8-untrusted-code-mitigations --mojo-platform-channel-handle=1516 /prefetch:1 | C:\Users\admin\AppData\Local\Programs\JJS-UI\JJS-UI.exe | — | JJS-UI.exe | |||||||||||
User: admin Company: GitHub, Inc. Integrity Level: MEDIUM Description: JJS-UI Exit code: 0 Version: 6.4.8 Modules
| |||||||||||||||
| 2932 | "C:\Program Files\Internet Explorer\iexplore.exe" "https://wearedevs.net/d/JJSploit" | C:\Program Files\Internet Explorer\iexplore.exe | Explorer.EXE | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Internet Explorer Exit code: 0 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
| 3268 | "C:\Users\admin\AppData\Local\Programs\JJS-UI\JJS-UI.exe" | C:\Users\admin\AppData\Local\Programs\JJS-UI\JJS-UI.exe | Explorer.EXE | ||||||||||||
User: admin Company: GitHub, Inc. Integrity Level: MEDIUM Description: JJS-UI Exit code: 0 Version: 6.4.8 Modules
| |||||||||||||||
| 3804 | "C:\Program Files\Internet Explorer\iexplore.exe" SCODEF:2932 CREDAT:267521 /prefetch:2 | C:\Program Files\Internet Explorer\iexplore.exe | iexplore.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Internet Explorer Exit code: 0 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
| 3836 | "C:\Program Files\Internet Explorer\iexplore.exe" SCODEF:2932 CREDAT:2102562 /prefetch:2 | C:\Program Files\Internet Explorer\iexplore.exe | iexplore.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Internet Explorer Exit code: 0 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
| 3860 | "C:\Program Files\Internet Explorer\iexplore.exe" SCODEF:2932 CREDAT:988435 /prefetch:2 | C:\Program Files\Internet Explorer\iexplore.exe | iexplore.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Internet Explorer Exit code: 0 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
| 3904 | "C:\Users\admin\AppData\Local\Programs\JJS-UI\JJS-UI.exe" --type=utility --field-trial-handle=1076,7099226105656174887,4755176932233472920,131072 --enable-features=WebComponentsV0Enabled --disable-features=SpareRendererForSitePerProcess --lang=en-US --service-sandbox-type=network --mojo-platform-channel-handle=1304 /prefetch:8 | C:\Users\admin\AppData\Local\Programs\JJS-UI\JJS-UI.exe | JJS-UI.exe | ||||||||||||
User: admin Company: GitHub, Inc. Integrity Level: MEDIUM Description: JJS-UI Exit code: 0 Version: 6.4.8 Modules
| |||||||||||||||
Total events
32 868
Read events
32 624
Write events
244
Delete events
0
Modification events
| (PID) Process: | (2932) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPDaysSinceLastAutoMigration |
Value: 1 | |||
| (PID) Process: | (2932) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPLastLaunchLowDateTime |
Value: | |||
| (PID) Process: | (2932) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPLastLaunchHighDateTime |
Value: 30957375 | |||
| (PID) Process: | (2932) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\UrlBlockManager |
| Operation: | write | Name: | NextCheckForUpdateLowDateTime |
Value: | |||
| (PID) Process: | (2932) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\UrlBlockManager |
| Operation: | write | Name: | NextCheckForUpdateHighDateTime |
Value: 30957375 | |||
| (PID) Process: | (2932) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Content |
| Operation: | write | Name: | CachePrefix |
Value: | |||
| (PID) Process: | (2932) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (2932) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
| (PID) Process: | (2932) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\Main |
| Operation: | write | Name: | CompatibilityFlags |
Value: 0 | |||
| (PID) Process: | (2932) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
Executable files
20
Suspicious files
32
Text files
61
Unknown types
97
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3804 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\57C8EDB95DF3F0AD4EE2DC2B8CFD4157 | binary | |
MD5:— | SHA256:— | |||
| 3804 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\6BADA8974A10C4BD62CC921D13E43B18_28DEA62A0AE77228DD387E155AD0BA27 | der | |
MD5:— | SHA256:— | |||
| 3804 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\6BADA8974A10C4BD62CC921D13E43B18_28DEA62A0AE77228DD387E155AD0BA27 | binary | |
MD5:— | SHA256:— | |||
| 3804 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\DY534W2X\download[1].css | text | |
MD5:— | SHA256:— | |||
| 3804 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\DY534W2X\JJSploit[1].htm | html | |
MD5:— | SHA256:— | |||
| 3804 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\24BD96D5497F70B3F510A6B53CD43F3E_3A89246FB90C5EE6620004F1AE0EB0EA | der | |
MD5:— | SHA256:— | |||
| 3804 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\CAF4703619713E3F18D8A9D5D88D6288_A7725538C46DE2D0088EE44974E2CEBA | binary | |
MD5:— | SHA256:— | |||
| 3804 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\CAF4703619713E3F18D8A9D5D88D6288_A7725538C46DE2D0088EE44974E2CEBA | der | |
MD5:— | SHA256:— | |||
| 3804 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\E87CE99F124623F95572A696C80EFCAF_3517CB42B5B938EC6C02EDBEE239D982 | der | |
MD5:— | SHA256:— | |||
| 3804 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\24BD96D5497F70B3F510A6B53CD43F3E_3A89246FB90C5EE6620004F1AE0EB0EA | binary | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
19
TCP/UDP connections
93
DNS requests
36
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
3804 | iexplore.exe | GET | 200 | 142.250.185.163:80 | http://ocsp.pki.goog/gts1c3/MFIwUDBOMEwwSjAJBgUrDgMCGgUABBTHLnmK3f9hNLO67UdCuLvGwCQHYwQUinR%2Fr4XN7pXNPZzQ4kYU83E1HScCEQCCPD%2BmI1IjpApTbalFlJFC | US | der | 472 b | whitelisted |
3804 | iexplore.exe | GET | 200 | 142.250.185.163:80 | http://ocsp.pki.goog/gts1c3/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTHLnmK3f9hNLO67UdCuLvGwCQHYwQUinR%2Fr4XN7pXNPZzQ4kYU83E1HScCEFBpiRkWWQcXClTQVPWVHTs%3D | US | der | 471 b | whitelisted |
3804 | iexplore.exe | GET | 200 | 142.250.185.163:80 | http://ocsp.pki.goog/gts1c3/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTHLnmK3f9hNLO67UdCuLvGwCQHYwQUinR%2Fr4XN7pXNPZzQ4kYU83E1HScCEHLcgbtYah9CCmuI0rVkaoY%3D | US | der | 471 b | whitelisted |
3804 | iexplore.exe | GET | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTBL0V27RVZ7LBduom%2FnYB45SPUEwQU5Z1ZMIJHWMys%2BghUNoZ7OrUETfACEAo3h2ReX7SMIk79G%2B0UDDw%3D | US | der | 1.47 Kb | whitelisted |
2932 | iexplore.exe | GET | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTBL0V27RVZ7LBduom%2FnYB45SPUEwQU5Z1ZMIJHWMys%2BghUNoZ7OrUETfACEA8Ull8gIGmZT9XHrHiJQeI%3D | US | der | 1.47 Kb | whitelisted |
3804 | iexplore.exe | GET | 200 | 142.250.185.163:80 | http://ocsp.pki.goog/gts1c3/MFIwUDBOMEwwSjAJBgUrDgMCGgUABBTHLnmK3f9hNLO67UdCuLvGwCQHYwQUinR%2Fr4XN7pXNPZzQ4kYU83E1HScCEQD75t1%2F7WSOdBIZOUv88I5W | US | der | 472 b | whitelisted |
2932 | iexplore.exe | GET | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | US | der | 471 b | whitelisted |
3804 | iexplore.exe | GET | 200 | 142.250.185.163:80 | http://ocsp.pki.goog/gts1c3/MFIwUDBOMEwwSjAJBgUrDgMCGgUABBTHLnmK3f9hNLO67UdCuLvGwCQHYwQUinR%2Fr4XN7pXNPZzQ4kYU83E1HScCEQDPHOYdSk1KPwrBCsCAw3KJ | US | der | 472 b | whitelisted |
3804 | iexplore.exe | GET | 200 | 142.250.185.163:80 | http://ocsp.pki.goog/gts1c3/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTHLnmK3f9hNLO67UdCuLvGwCQHYwQUinR%2Fr4XN7pXNPZzQ4kYU83E1HScCEHquXS%2BaUA73EnirQKFr398%3D | US | der | 471 b | whitelisted |
3804 | iexplore.exe | GET | 200 | 142.250.185.163:80 | http://ocsp.pki.goog/gtsr1/ME4wTDBKMEgwRjAJBgUrDgMCGgUABBQwkcLWD4LqGJ7bE7B1XZsEbmfwUAQU5K8rJnEaK0gnhS9SZizv8IkTcT4CDQIDvFNZazTHGPUBUGY%3D | US | der | 724 b | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
3804 | iexplore.exe | 142.250.186.98:443 | pagead2.googlesyndication.com | Google Inc. | US | suspicious |
3804 | iexplore.exe | 93.184.221.240:80 | ctldl.windowsupdate.com | MCI Communications Services, Inc. d/b/a Verizon Business | US | whitelisted |
3804 | iexplore.exe | 172.217.16.138:443 | fonts.googleapis.com | Google Inc. | US | whitelisted |
3804 | iexplore.exe | 104.26.7.147:443 | wearedevs.net | Cloudflare Inc | US | suspicious |
3804 | iexplore.exe | 142.250.185.200:443 | www.googletagmanager.com | Google Inc. | US | suspicious |
3804 | iexplore.exe | 104.26.6.147:443 | wearedevs.net | Cloudflare Inc | US | suspicious |
3804 | iexplore.exe | 142.250.186.142:443 | www.google-analytics.com | Google Inc. | US | whitelisted |
3804 | iexplore.exe | 142.250.185.163:80 | ocsp.pki.goog | Google Inc. | US | whitelisted |
3804 | iexplore.exe | 142.250.185.162:443 | googleads.g.doubleclick.net | Google Inc. | US | whitelisted |
3804 | iexplore.exe | 93.184.220.29:80 | ocsp.digicert.com | MCI Communications Services, Inc. d/b/a Verizon Business | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
wearedevs.net |
| whitelisted |
ctldl.windowsupdate.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
pagead2.googlesyndication.com |
| whitelisted |
cdn.wearedevs.net |
| whitelisted |
fonts.googleapis.com |
| whitelisted |
ocsp.pki.goog |
| whitelisted |
www.googletagmanager.com |
| whitelisted |
www.google-analytics.com |
| whitelisted |
fonts.gstatic.com |
| whitelisted |