| download: | /download/wicreset.exe |
| Full analysis: | https://app.any.run/tasks/d0708c58-af18-4751-94d4-8b29d0c4fd90 |
| Verdict: | Malicious activity |
| Analysis date: | May 19, 2024, 17:48:51 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows |
| MD5: | A3BF50D833F10E1F976FA5E72997F45F |
| SHA1: | 9C3CA9415074EB1BE0BEE075FE914DEA110A5B0F |
| SHA256: | 483F2613F51E072FD645B047AE9311C6B6605A466EF81E05FFC0C04CB6E9F191 |
| SSDEEP: | 98304:o0MP1iC4bbdXTpzoE3j+K/0iCi4d/pMJaOcAg4carPAgavo1L0QblluLZw3uHFua:dJ8+vf4 |
MALICIOUS
Drops the executable file immediately after the start
- wicreset.exe (PID: 6484)
- wicreset.exe (PID: 6580)
- wicreset.tmp (PID: 6612)
Antivirus name has been found in the command line (generic signature)
- wicreset.tmp (PID: 6504)
- wicreset.exe (PID: 6580)
- wicreset.exe (PID: 6484)
- wicreset.tmp (PID: 6612)
- wicreset.exe (PID: 1172)
SUSPICIOUS
Reads the date of Windows installation
- wicreset.tmp (PID: 6504)
Reads security settings of Internet Explorer
- wicreset.tmp (PID: 6504)
Executable content was dropped or overwritten
- wicreset.exe (PID: 6484)
- wicreset.exe (PID: 6580)
- wicreset.tmp (PID: 6612)
Reads the Windows owner or organization settings
- wicreset.tmp (PID: 6612)
Connects to unusual port
- wicreset.exe (PID: 1172)
INFO
Checks supported languages
- wicreset.exe (PID: 6484)
- wicreset.tmp (PID: 6504)
- wicreset.exe (PID: 6580)
- wicreset.tmp (PID: 6612)
- wicreset.exe (PID: 1172)
Reads the computer name
- wicreset.tmp (PID: 6504)
- wicreset.tmp (PID: 6612)
- wicreset.exe (PID: 1172)
Create files in a temporary directory
- wicreset.exe (PID: 6484)
- wicreset.exe (PID: 6580)
- wicreset.tmp (PID: 6612)
Process checks computer location settings
- wicreset.tmp (PID: 6504)
Creates a software uninstall entry
- wicreset.tmp (PID: 6612)
Creates files in the program directory
- wicreset.tmp (PID: 6612)
Creates files or folders in the user directory
- wicreset.exe (PID: 1172)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win32 Executable Delphi generic (45.2) |
|---|---|---|
| .dll | | | Win32 Dynamic Link Library (generic) (20.9) |
| .exe | | | Win32 Executable (generic) (14.3) |
| .exe | | | Win16/32 Executable Delphi generic (6.6) |
| .exe | | | Generic Win/DOS Executable (6.3) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2018:06:14 13:27:46+00:00 |
| ImageFileCharacteristics: | No relocs, Executable, No line numbers, No symbols, Bytes reversed lo, 32-bit, Bytes reversed hi |
| PEType: | PE32 |
| LinkerVersion: | 2.25 |
| CodeSize: | 66560 |
| InitializedDataSize: | 53760 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x1181c |
| OSVersion: | 5 |
| ImageVersion: | 6 |
| SubsystemVersion: | 5 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 5.90.0.0 |
| ProductVersionNumber: | 5.90.0.0 |
| FileFlagsMask: | 0x003f |
| FileFlags: | (none) |
| FileOS: | Win32 |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | Neutral |
| CharacterSet: | Unicode |
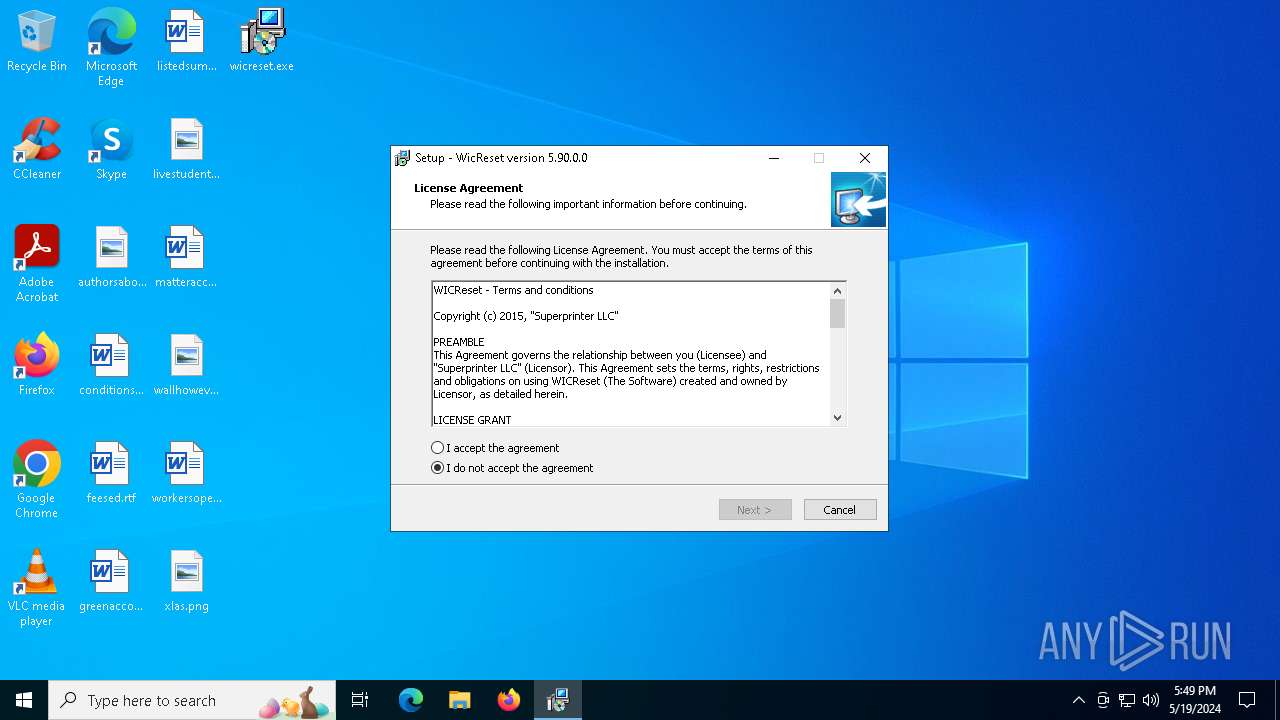
| Comments: | This installation was built with Inno Setup. |
| CompanyName: | WWW.WIC.SUPPORT |
| FileDescription: | WicReset Setup |
| FileVersion: | 5.90.0.0 |
| LegalCopyright: | |
| ProductName: | WicReset |
| ProductVersion: | 5.90.0.0 |
Total processes
122
Monitored processes
6
Malicious processes
4
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1172 | "C:\Program Files (x86)\WicReset\wicreset.exe" | C:\Program Files (x86)\WicReset\wicreset.exe | wicreset.tmp | ||||||||||||
User: admin Integrity Level: MEDIUM Modules
| |||||||||||||||
| 6484 | "C:\Users\admin\Desktop\wicreset.exe" | C:\Users\admin\Desktop\wicreset.exe | explorer.exe | ||||||||||||
User: admin Company: WWW.WIC.SUPPORT Integrity Level: MEDIUM Description: WicReset Setup Exit code: 0 Version: 5.90.0.0 Modules
| |||||||||||||||
| 6504 | "C:\Users\admin\AppData\Local\Temp\is-37N9A.tmp\wicreset.tmp" /SL5="$401DE,2664001,121344,C:\Users\admin\Desktop\wicreset.exe" | C:\Users\admin\AppData\Local\Temp\is-37N9A.tmp\wicreset.tmp | — | wicreset.exe | |||||||||||
User: admin Integrity Level: MEDIUM Description: Setup/Uninstall Exit code: 0 Version: 51.1052.0.0 Modules
| |||||||||||||||
| 6580 | "C:\Users\admin\Desktop\wicreset.exe" /SPAWNWND=$302B2 /NOTIFYWND=$401DE | C:\Users\admin\Desktop\wicreset.exe | wicreset.tmp | ||||||||||||
User: admin Company: WWW.WIC.SUPPORT Integrity Level: HIGH Description: WicReset Setup Exit code: 0 Version: 5.90.0.0 Modules
| |||||||||||||||
| 6612 | "C:\Users\admin\AppData\Local\Temp\is-5HV5P.tmp\wicreset.tmp" /SL5="$502B8,2664001,121344,C:\Users\admin\Desktop\wicreset.exe" /SPAWNWND=$302B2 /NOTIFYWND=$401DE | C:\Users\admin\AppData\Local\Temp\is-5HV5P.tmp\wicreset.tmp | wicreset.exe | ||||||||||||
User: admin Integrity Level: HIGH Description: Setup/Uninstall Exit code: 0 Version: 51.1052.0.0 Modules
| |||||||||||||||
| 7156 | C:\Users\admin\AppData\Local\Microsoft\OneDrive\19.043.0304.0013\FileCoAuth.exe -Embedding | C:\Users\admin\AppData\Local\Microsoft\OneDrive\19.043.0304.0013\FileCoAuth.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft OneDriveFile Co-Authoring Executable Exit code: 0 Version: 19.043.0304.0013 Modules
| |||||||||||||||
Total events
4 447
Read events
4 409
Write events
32
Delete events
6
Modification events
| (PID) Process: | (6612) wicreset.tmp | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\RestartManager\Session0000 |
| Operation: | write | Name: | Owner |
Value: D4190000F73617D714AADA01 | |||
| (PID) Process: | (6612) wicreset.tmp | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\RestartManager\Session0000 |
| Operation: | write | Name: | SessionHash |
Value: 45560BC48659ED1906BAB59F408C85DF2B67F68EF831B90DE262802BCD50160C | |||
| (PID) Process: | (6612) wicreset.tmp | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\RestartManager\Session0000 |
| Operation: | write | Name: | Sequence |
Value: 1 | |||
| (PID) Process: | (6612) wicreset.tmp | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\RestartManager\Session0000 |
| Operation: | write | Name: | RegFiles0000 |
Value: C:\Program Files (x86)\WicReset\wicreset.exe | |||
| (PID) Process: | (6612) wicreset.tmp | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\RestartManager\Session0000 |
| Operation: | write | Name: | RegFilesHash |
Value: C15393A3109F4F5A1B5007B6CF3A8CA1FD8E7F1B4FA8CE6CFD1858F89316228E | |||
| (PID) Process: | (6612) wicreset.tmp | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Windows\CurrentVersion\Uninstall\{20379D3A-321B-4830-96A6-37183B713AE8}_is1 |
| Operation: | write | Name: | Inno Setup: Setup Version |
Value: 5.6.1 (u) | |||
| (PID) Process: | (6612) wicreset.tmp | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Windows\CurrentVersion\Uninstall\{20379D3A-321B-4830-96A6-37183B713AE8}_is1 |
| Operation: | write | Name: | Inno Setup: App Path |
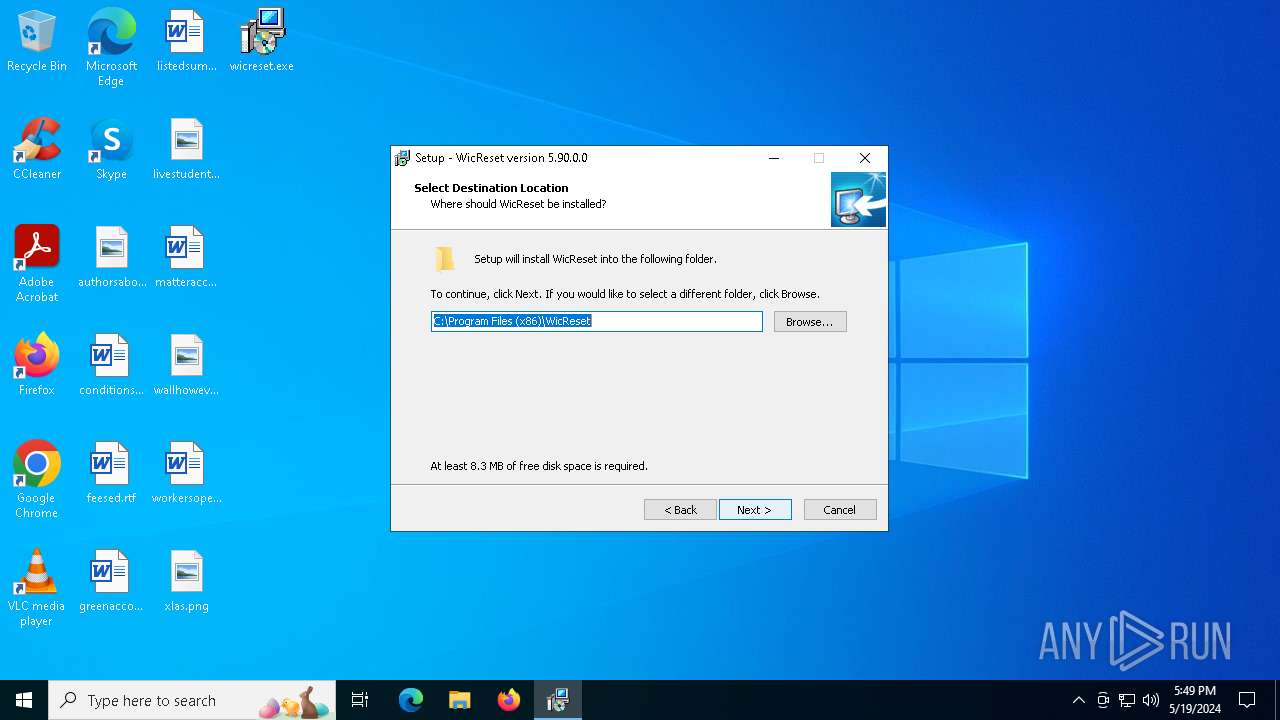
Value: C:\Program Files (x86)\WicReset | |||
| (PID) Process: | (6612) wicreset.tmp | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Windows\CurrentVersion\Uninstall\{20379D3A-321B-4830-96A6-37183B713AE8}_is1 |
| Operation: | write | Name: | InstallLocation |
Value: C:\Program Files (x86)\WicReset\ | |||
| (PID) Process: | (6612) wicreset.tmp | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Windows\CurrentVersion\Uninstall\{20379D3A-321B-4830-96A6-37183B713AE8}_is1 |
| Operation: | write | Name: | Inno Setup: Icon Group |
Value: WicReset | |||
| (PID) Process: | (6612) wicreset.tmp | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Windows\CurrentVersion\Uninstall\{20379D3A-321B-4830-96A6-37183B713AE8}_is1 |
| Operation: | write | Name: | Inno Setup: User |
Value: admin | |||
Executable files
7
Suspicious files
65
Text files
0
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 6484 | wicreset.exe | C:\Users\admin\AppData\Local\Temp\is-37N9A.tmp\wicreset.tmp | executable | |
MD5:34ACC2BDB45A9C436181426828C4CB49 | SHA256:9C81817ACD4982632D8C7F1DF3898FCA1477577738184265D735F49FC5480F07 | |||
| 6580 | wicreset.exe | C:\Users\admin\AppData\Local\Temp\is-5HV5P.tmp\wicreset.tmp | executable | |
MD5:34ACC2BDB45A9C436181426828C4CB49 | SHA256:9C81817ACD4982632D8C7F1DF3898FCA1477577738184265D735F49FC5480F07 | |||
| 6612 | wicreset.tmp | C:\Program Files (x86)\WicReset\wicreset.exe | executable | |
MD5:E0B28C2C8F2DA461107A3F7CE4926DB1 | SHA256:40A3A679821A785F315B7CC954463712DC63DAE2F4A2642F3BD50214B8DC1960 | |||
| 6612 | wicreset.tmp | C:\ProgramData\Microsoft\Windows\Start Menu\Programs\WicReset\WicReset.lnk | binary | |
MD5:9BB4923B7CD879F1DB9C3A28B085AEAB | SHA256:87BFA0A9AB3B248CCC74D92BEC563A67C677D502BCBEEFB445AA8EA03AC8F41B | |||
| 6612 | wicreset.tmp | C:\ProgramData\Microsoft\Windows\Start Menu\Programs\WicReset\Uninstall WicReset.lnk | binary | |
MD5:FD20BB2A8FA421CBD223C8CD7FE73262 | SHA256:88CD8F775364FC28D62CA19C1E8006984735127CE7E68D3AE8ED04FAD05AD1F7 | |||
| 1172 | wicreset.exe | C:\Users\admin\AppData\Roaming\wicreset\patterns\colour-l-xxx-standard.bin | binary | |
MD5:74714DC7052DFCDBD19E8C39EAB4E074 | SHA256:BC1CBB90C8AF62854139124A87CD9A836FE5E450012436A96674164378B93DDE | |||
| 1172 | wicreset.exe | C:\Users\admin\AppData\Roaming\wicreset\patterns\colour-l-800-standard.bin | binary | |
MD5:E2BE218354175BC1EC3F79D2443C261D | SHA256:C05C27F712C7D16FB223AD9B65BCC142551DAB2692549CFC08DBD9AC5071A876 | |||
| 7156 | FileCoAuth.exe | C:\Users\admin\AppData\Local\Microsoft\OneDrive\logs\Common\FileCoAuth-2024-05-19.1750.7156.1.odl | binary | |
MD5:149EB133DBCCB5E6FFD8428B16BE58D6 | SHA256:0942C054ECEAB9A66BDBD28726CA32831722D15E9220EA78BDD83DC4C5C21186 | |||
| 1172 | wicreset.exe | C:\Users\admin\AppData\Roaming\wicreset\patterns\colour-r-270-standard.bin | binary | |
MD5:FAB5A26FEBB3AC2C311C314536DC9498 | SHA256:6826D06E5D38A0DE836ABA75D1497D8309E1DEFBA80D7768461B979789D30B76 | |||
| 6612 | wicreset.tmp | C:\Program Files (x86)\WicReset\unins000.dat | binary | |
MD5:3E88A56290D6FF739B6AD81F8CD48895 | SHA256:202451096F07929B6A01B08AEADC2380C76B28C08E584B9C75179591FCDE9A9F | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
14
TCP/UDP connections
33
DNS requests
20
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
1984 | RUXIMICS.exe | GET | 200 | 2.19.122.206:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | unknown |
1984 | RUXIMICS.exe | GET | 200 | 23.44.252.205:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | unknown |
1172 | wicreset.exe | GET | 200 | 176.9.157.164:80 | http://www.printhelp.info/data/redist/upgrades.xml | unknown | — | — | unknown |
1172 | wicreset.exe | GET | 200 | 176.9.157.164:80 | http://www.2manuals.com/WIC/banners/u-csfwr.png | unknown | — | — | unknown |
1172 | wicreset.exe | GET | 200 | 176.9.157.164:80 | http://www.2manuals.com/WIC/wicreset.rss | unknown | — | — | unknown |
1172 | wicreset.exe | GET | 200 | 176.9.157.164:80 | http://www.2manuals.com/WIC/banners/content.xml | unknown | — | — | unknown |
1172 | wicreset.exe | GET | 200 | 176.9.157.164:80 | http://www.printhelp.info/data/redist/upgrades.zip | unknown | — | — | unknown |
1172 | wicreset.exe | GET | 200 | 176.9.157.164:80 | http://www.2manuals.com/WIC/support_message.php | unknown | — | — | unknown |
1172 | wicreset.exe | GET | 200 | 176.9.157.164:80 | http://www.2manuals.com/WIC/wicfaq.rss | unknown | — | — | unknown |
— | — | POST | 204 | 23.222.16.81:443 | https://www.bing.com/threshold/xls.aspx | unknown | — | — | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
5632 | svchost.exe | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
1984 | RUXIMICS.exe | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
5140 | MoUsoCoreWorker.exe | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
1984 | RUXIMICS.exe | 2.19.122.206:80 | crl.microsoft.com | Akamai International B.V. | DE | unknown |
1984 | RUXIMICS.exe | 23.44.252.205:80 | www.microsoft.com | Cellcom Fixed Line Communication L.P | IL | unknown |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
5456 | svchost.exe | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4680 | SearchApp.exe | 23.222.16.96:443 | — | Akamai International B.V. | US | unknown |
4680 | SearchApp.exe | 23.222.16.97:443 | — | Akamai International B.V. | US | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
settings-win.data.microsoft.com |
| whitelisted |
wasteinkcounter.com |
| unknown |
www.printhelp.info |
| malicious |
www.2manuals.com |
| malicious |
self.events.data.microsoft.com |
| whitelisted |
Threats
Process | Message |
|---|---|
wicreset.exe | d:\development\libraries\wx\src\msw\window.cpp(581): 'SetFocus' failed with error 0x00000057 (the parameter is incorrect.).
|
wicreset.exe | d:\development\libraries\wx\src\msw\window.cpp(581): 'SetFocus' failed with error 0x00000057 (the parameter is incorrect.).
|