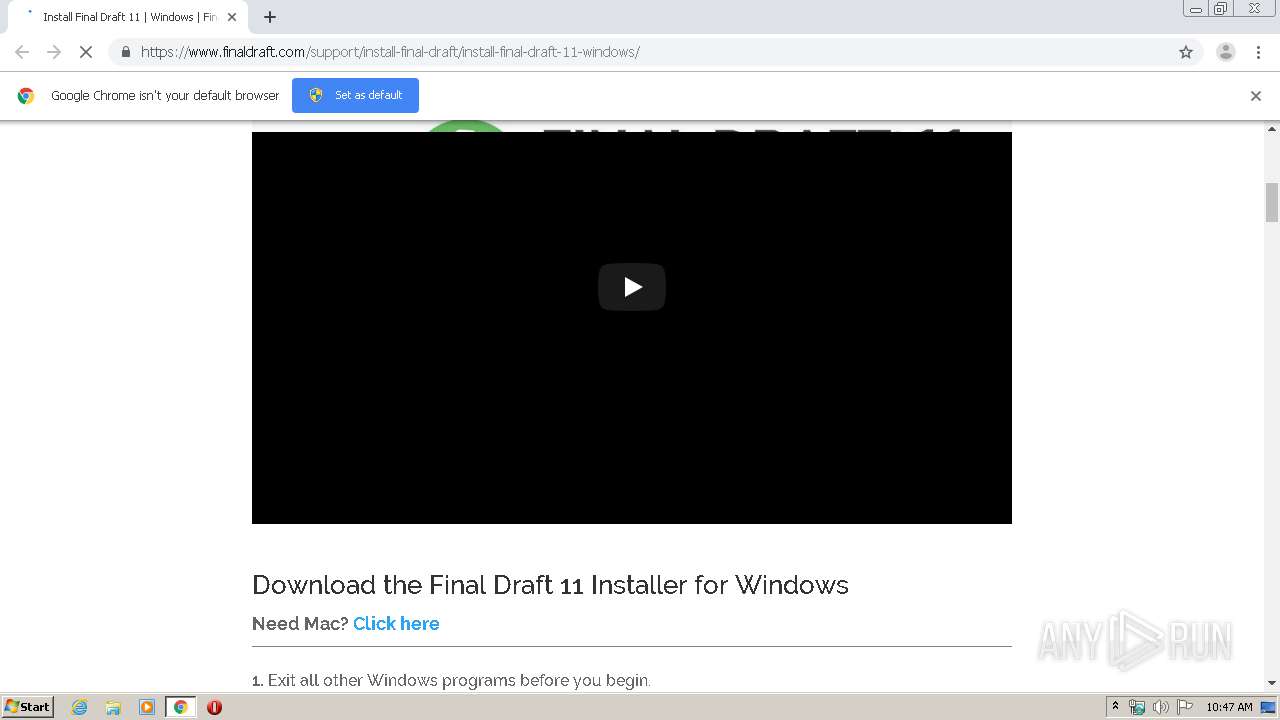
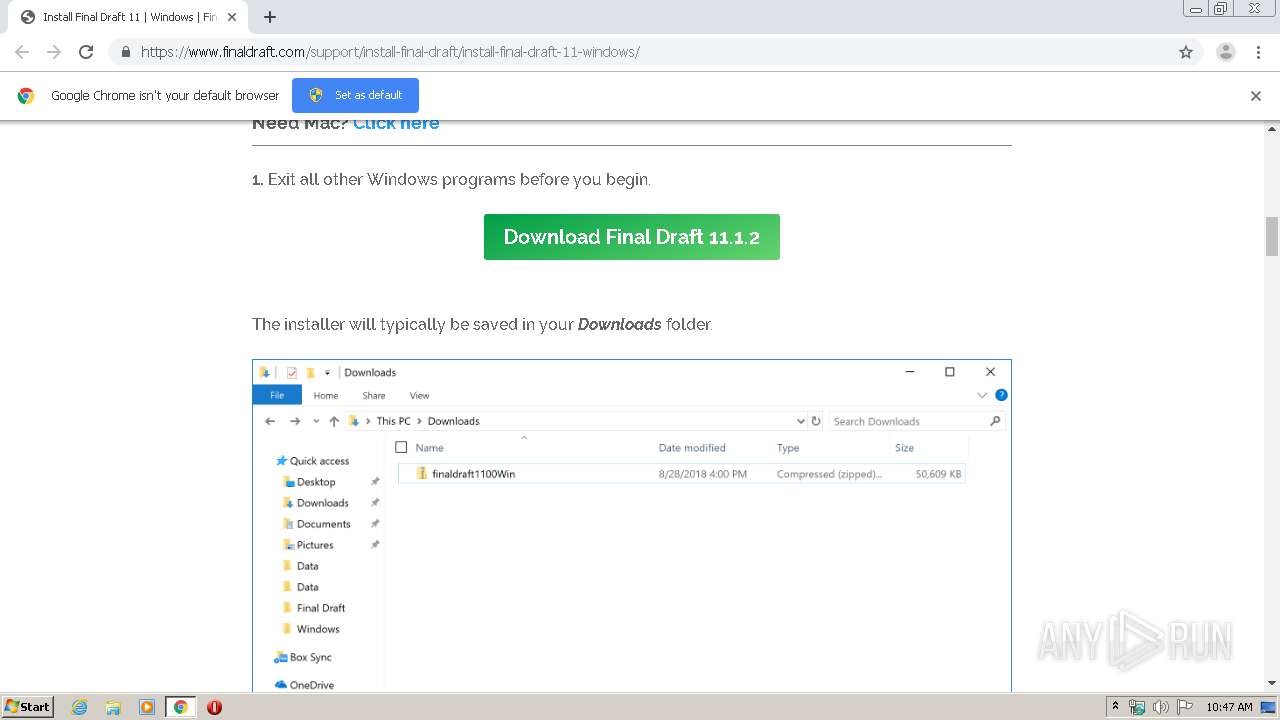
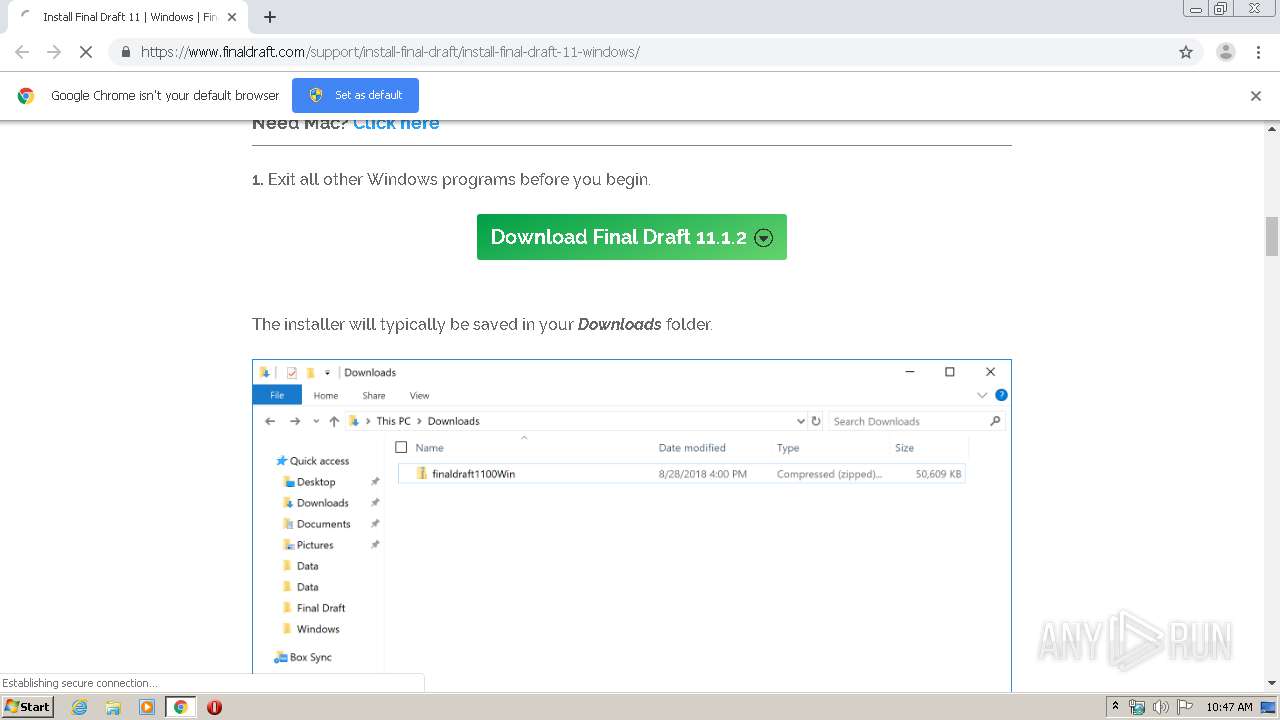
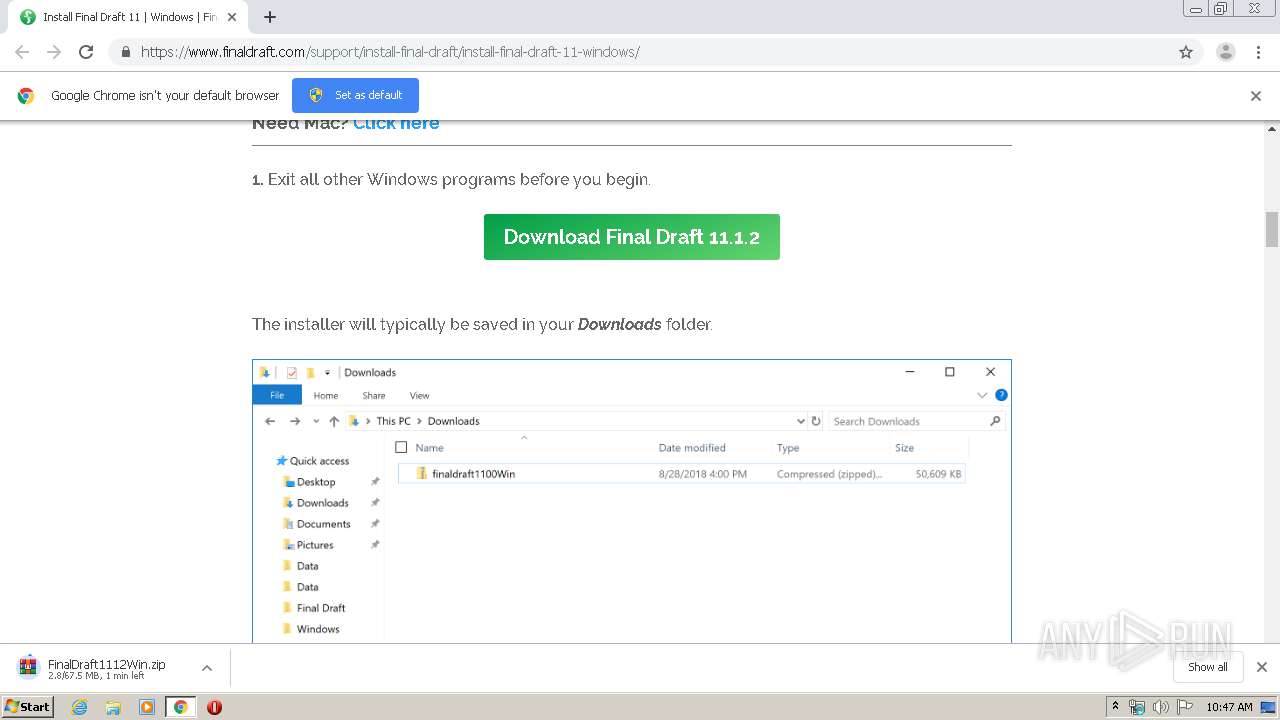
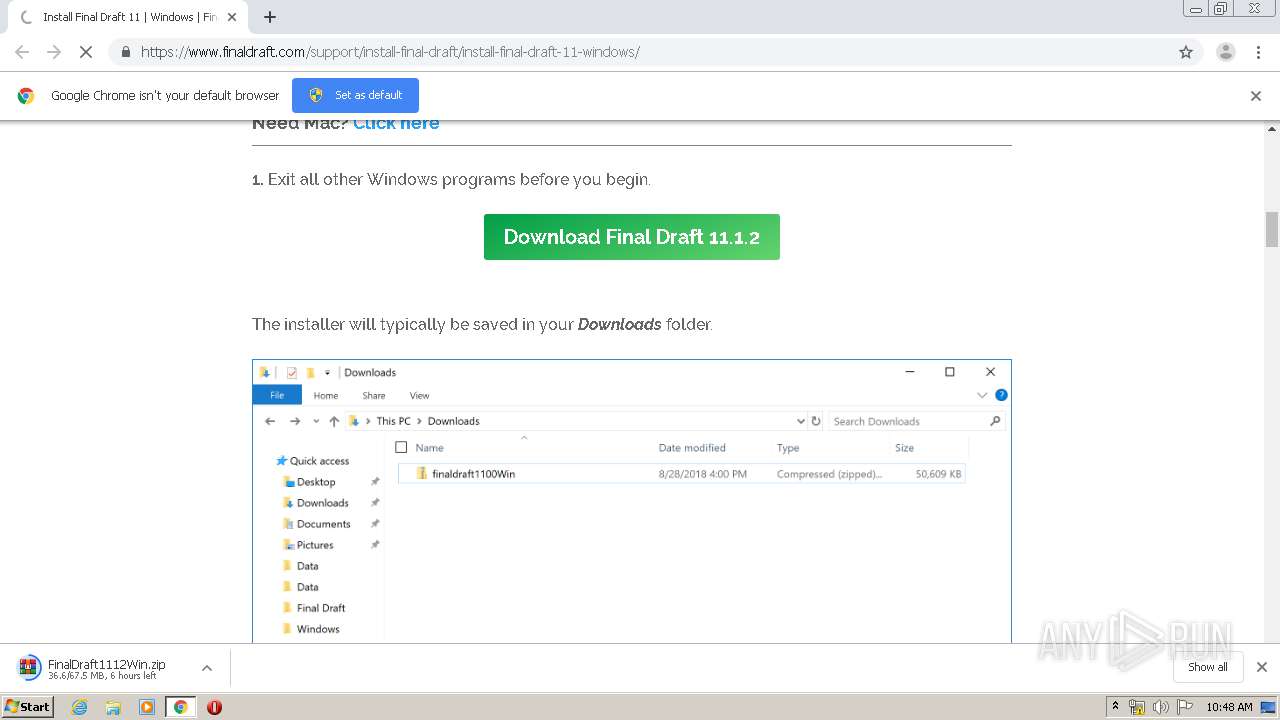
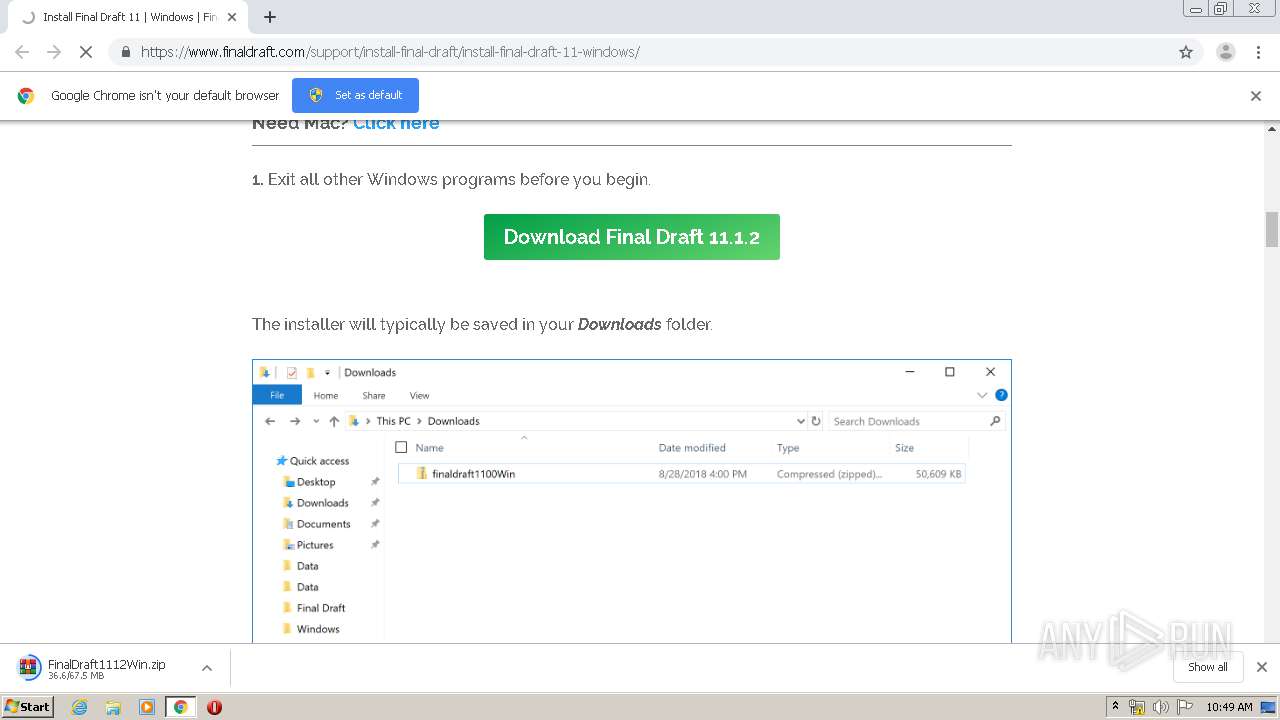
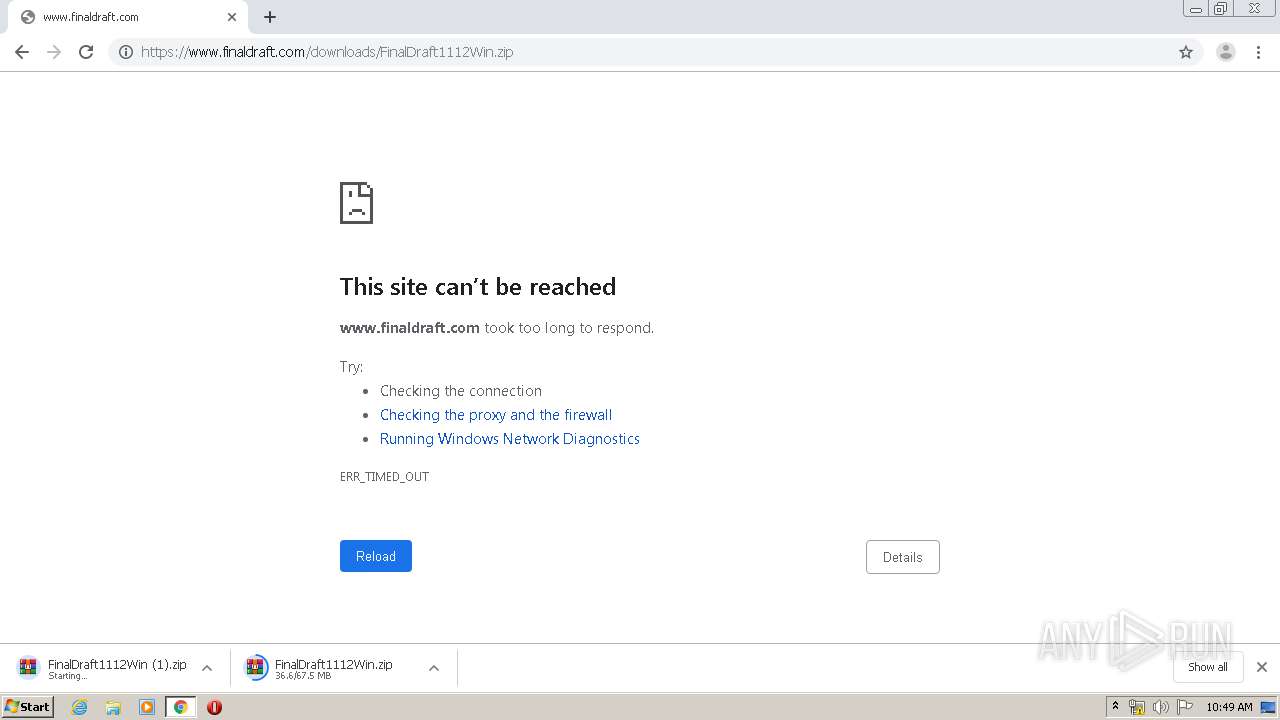
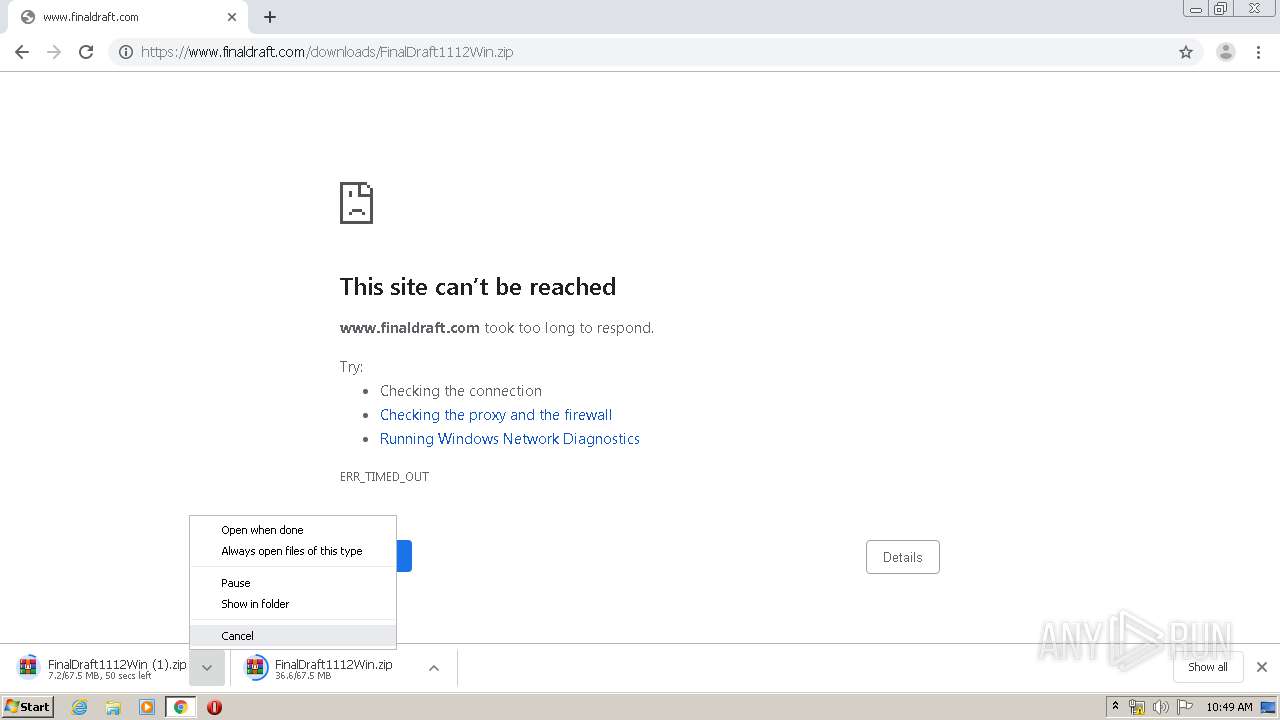
| URL: | https://www.finaldraft.com/support/install-final-draft/install-final-draft-11-windows/ |
| Full analysis: | https://app.any.run/tasks/4450685a-7934-4b97-b922-380f6f910136 |
| Verdict: | Malicious activity |
| Analysis date: | March 02, 2020, 10:47:04 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MD5: | 933C0460D295056B4709D3E719ECEC8B |
| SHA1: | 599B257EF76B4301E8B7CBCAC6CBDB57089D2EA9 |
| SHA256: | 483F0EDEE531A439F840B020CC2D2A56B766D269B27ADC97717A9294D366CD02 |
| SSDEEP: | 3:N8DSLQwykKXViKkGDeXqKkGDeXqIU5N:2OLQ3FipGDeapGDeazN |
MALICIOUS
Loads dropped or rewritten executable
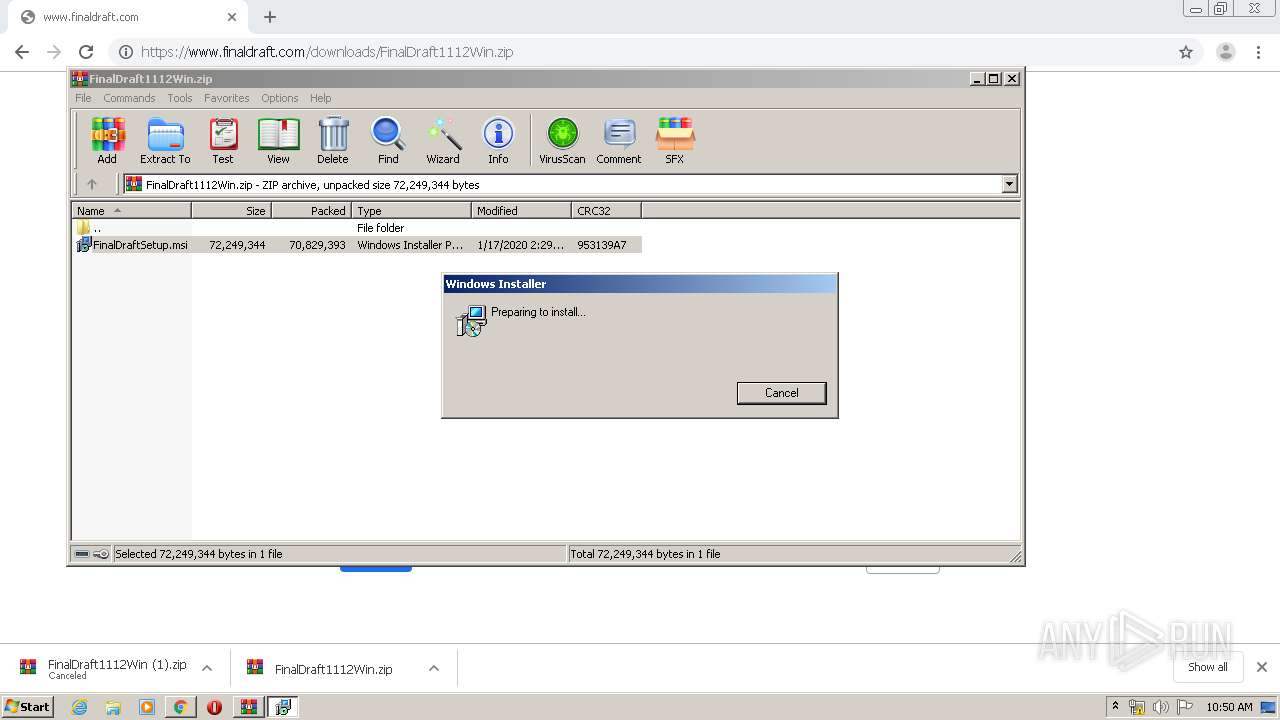
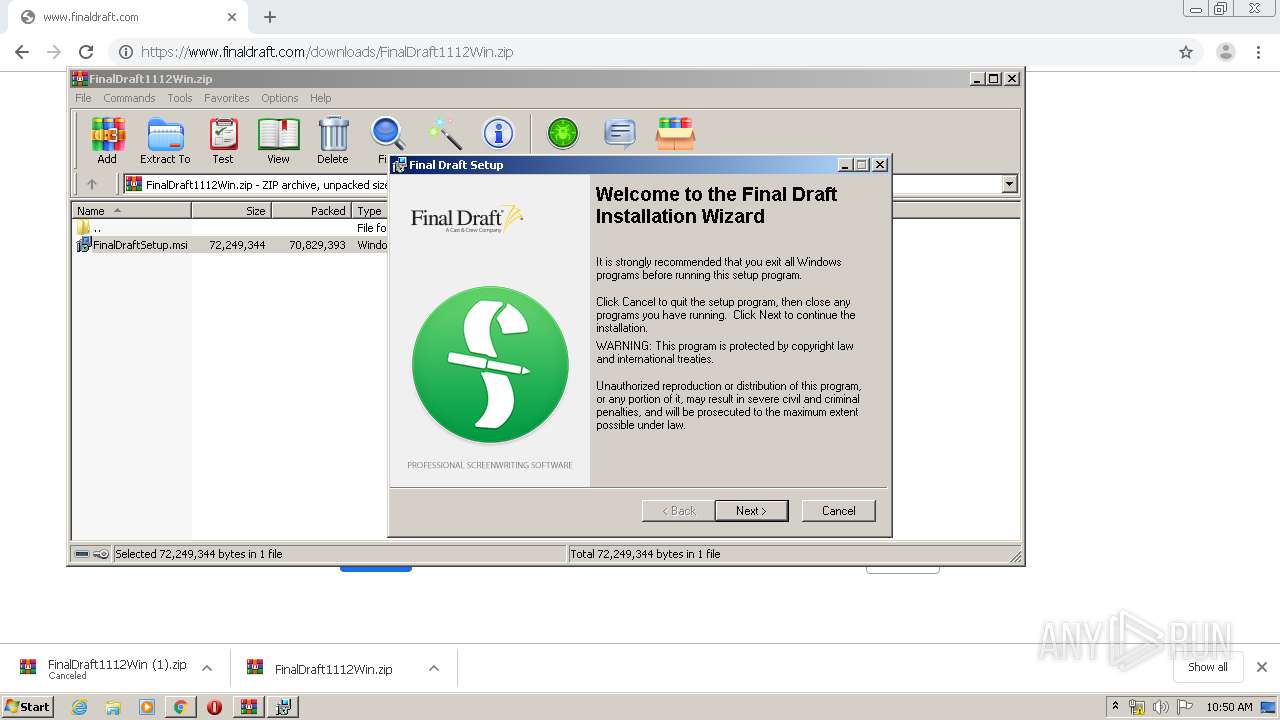
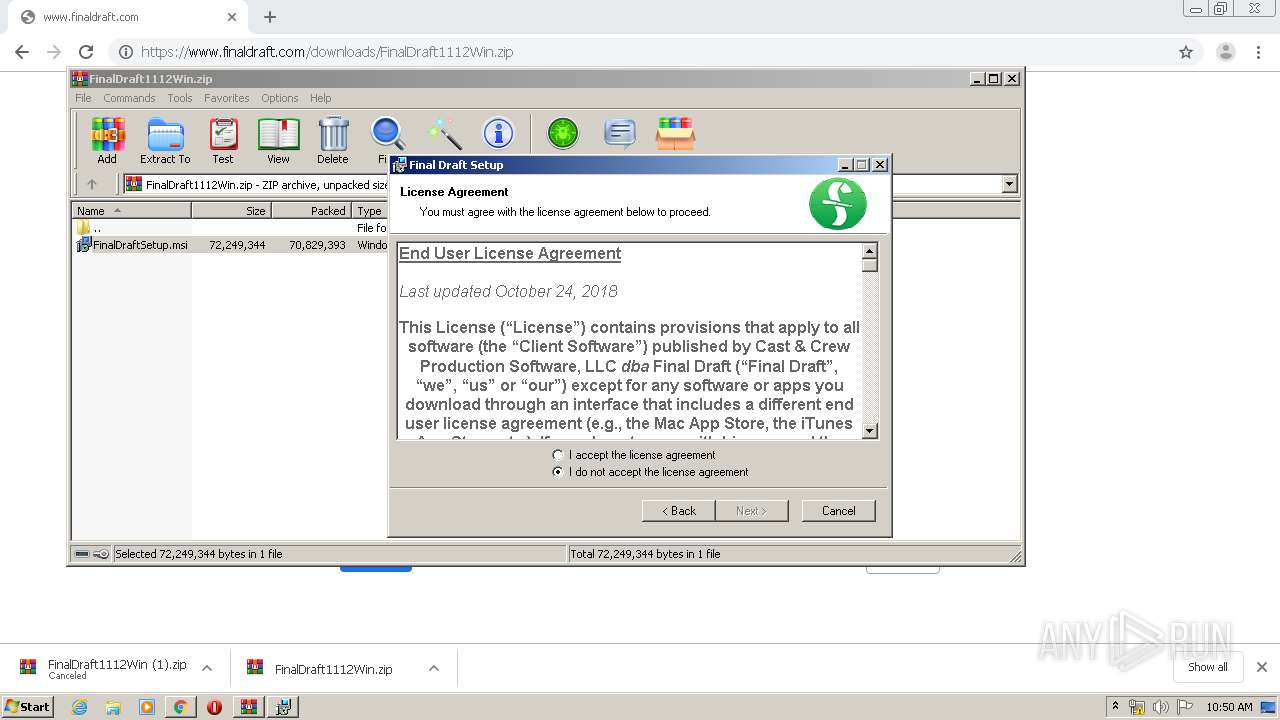
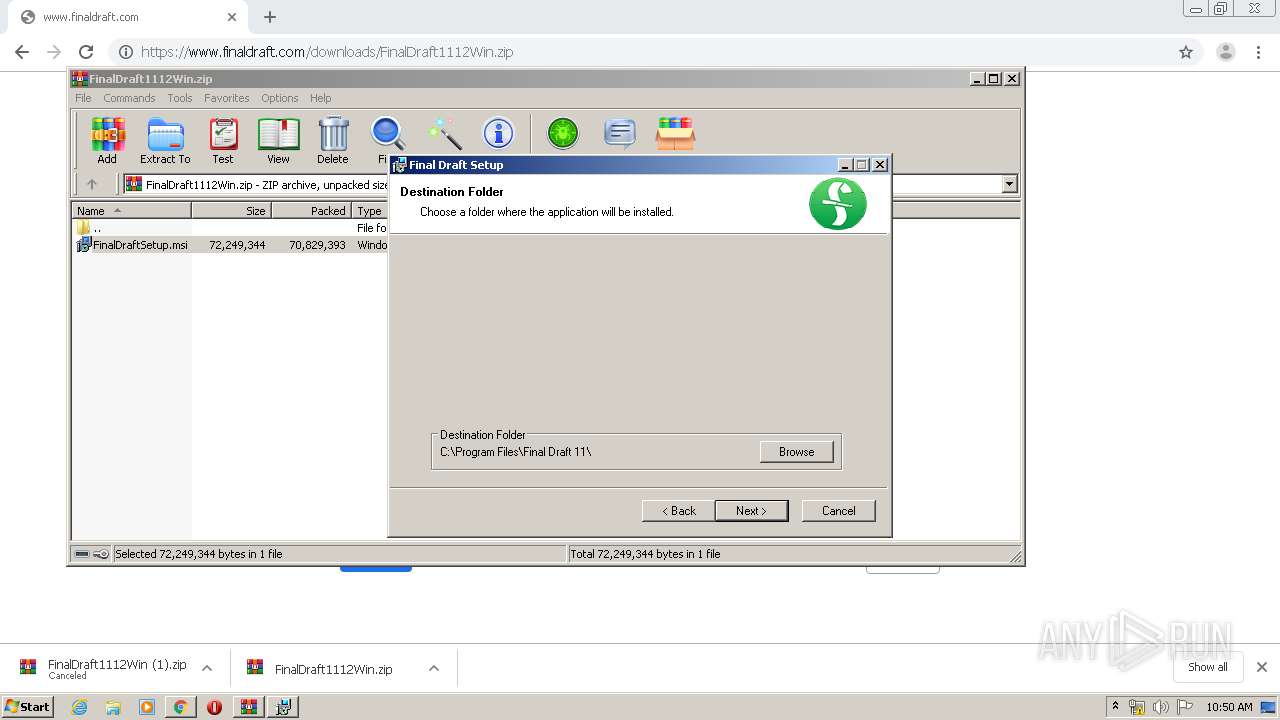
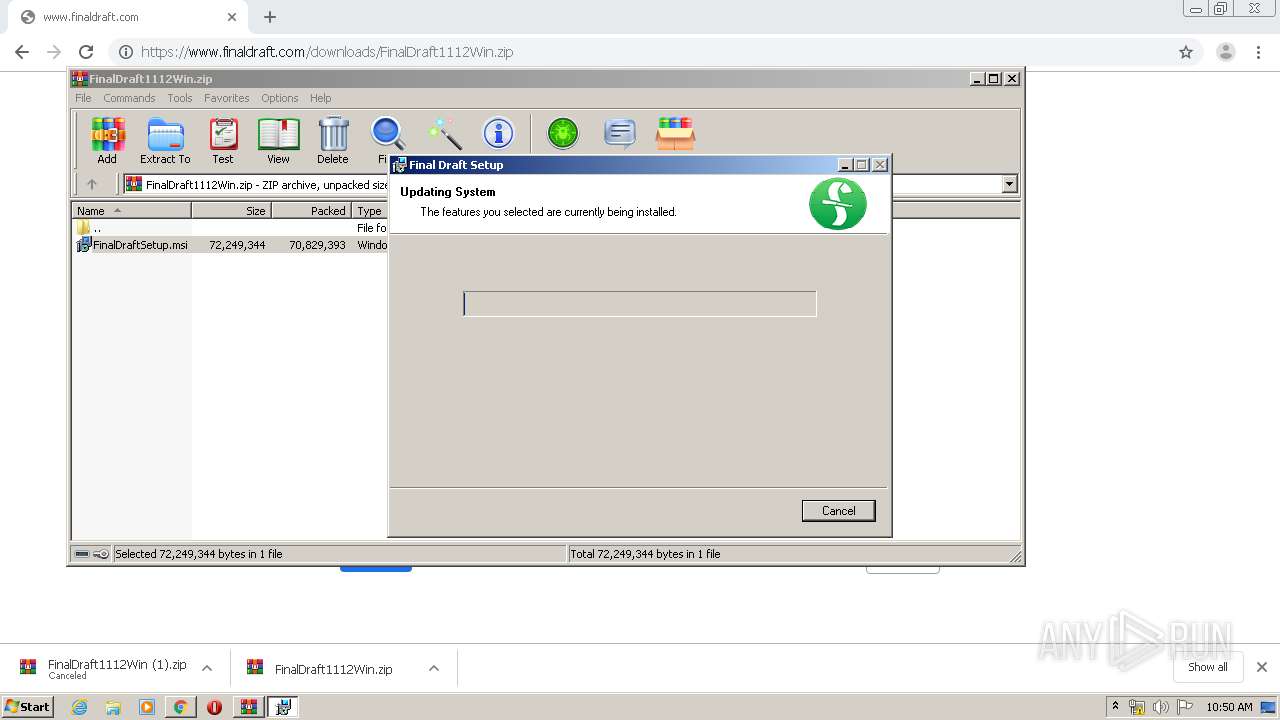
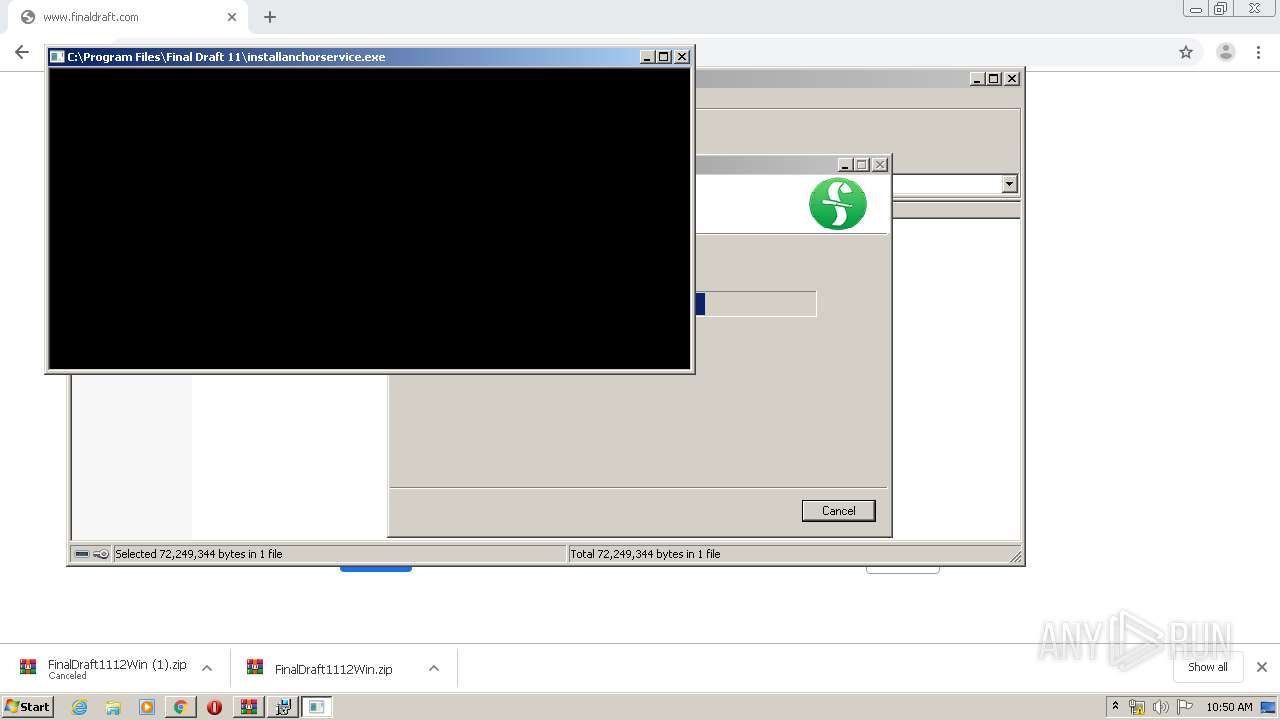
- installanchorservice.exe (PID: 3572)
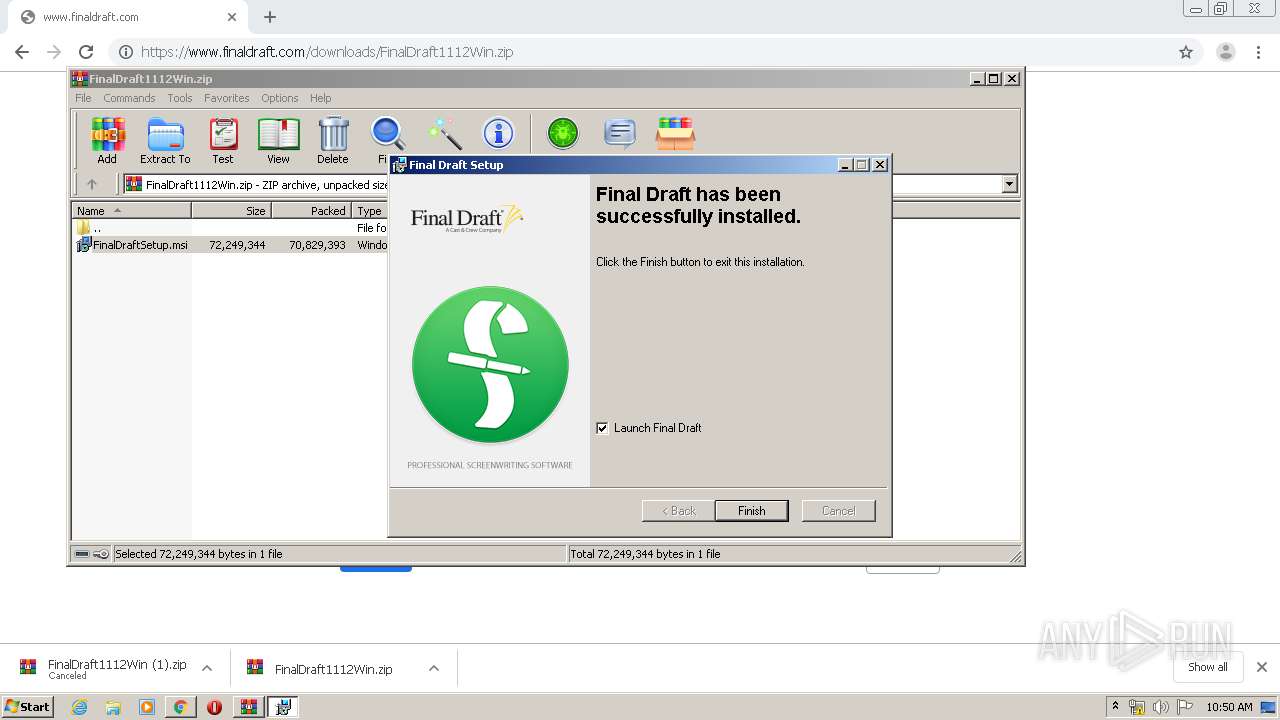
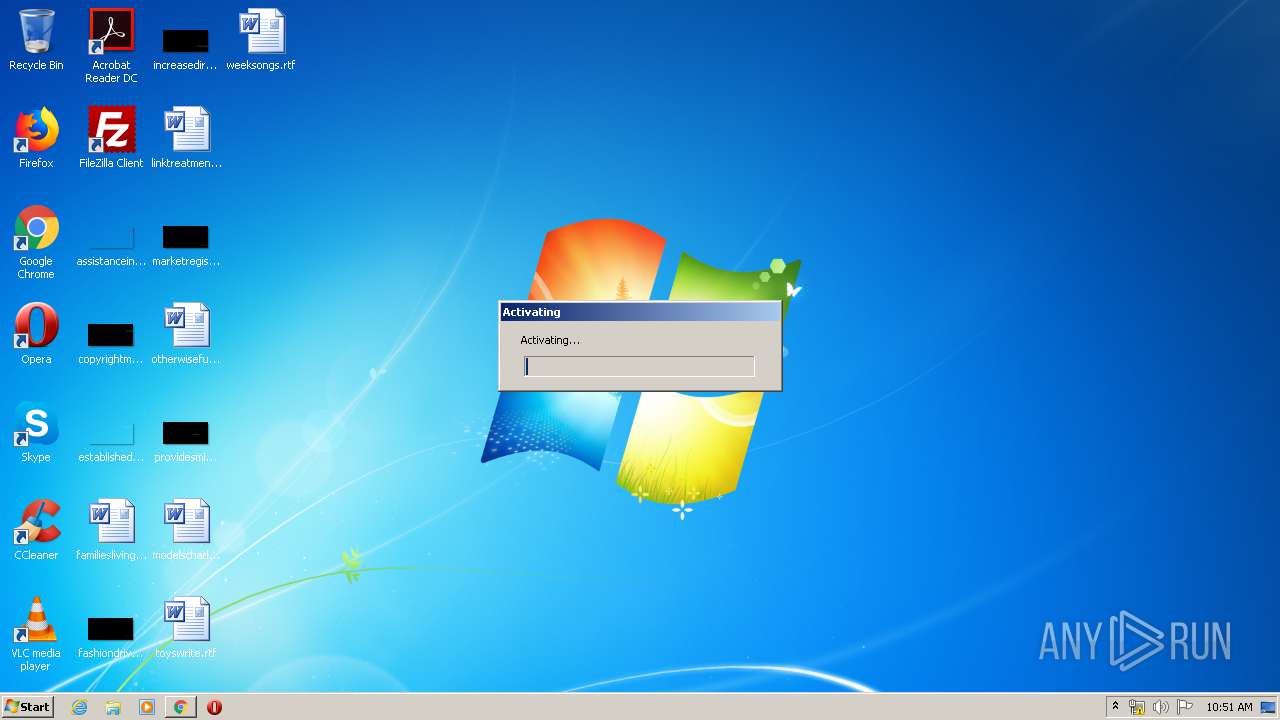
- Final Draft.exe (PID: 3536)
- Final Draft.exe (PID: 2588)
Application was dropped or rewritten from another process
- installanchorservice.exe (PID: 3572)
- FNPLicensingService.exe (PID: 1916)
Low-level write access rights to disk partition
- FNPLicensingService.exe (PID: 1916)
Changes the autorun value in the registry
- FNPLicensingService.exe (PID: 1916)
SUSPICIOUS
Modifies files in Chrome extension folder
- chrome.exe (PID: 304)
Starts Microsoft Installer
- WinRAR.exe (PID: 2632)
Executed as Windows Service
- vssvc.exe (PID: 180)
- FNPLicensingService.exe (PID: 1916)
Modifies the open verb of a shell class
- msiexec.exe (PID: 3316)
Creates files in the program directory
- installanchorservice.exe (PID: 3572)
- FNPLicensingService.exe (PID: 1916)
- Final Draft.exe (PID: 3536)
Executable content was dropped or overwritten
- installanchorservice.exe (PID: 3572)
- msiexec.exe (PID: 3316)
- msiexec.exe (PID: 1748)
Creates COM task schedule object
- FNPLicensingService.exe (PID: 1916)
Low-level read access rights to disk partition
- FNPLicensingService.exe (PID: 1916)
Reads Internet Cache Settings
- Final Draft.exe (PID: 3536)
INFO
Reads the hosts file
- chrome.exe (PID: 304)
- chrome.exe (PID: 2796)
Application launched itself
- chrome.exe (PID: 304)
- msiexec.exe (PID: 3316)
Low-level read access rights to disk partition
- vssvc.exe (PID: 180)
Loads dropped or rewritten executable
- MsiExec.exe (PID: 2672)
- MsiExec.exe (PID: 1392)
Searches for installed software
- msiexec.exe (PID: 3316)
Creates a software uninstall entry
- msiexec.exe (PID: 3316)
Reads Internet Cache Settings
- chrome.exe (PID: 304)
Creates files in the program directory
- msiexec.exe (PID: 3316)
Dropped object may contain Bitcoin addresses
- msiexec.exe (PID: 3316)
Manual execution by user
- Final Draft.exe (PID: 2588)
Reads settings of System Certificates
- chrome.exe (PID: 2796)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
86
Monitored processes
42
Malicious processes
3
Suspicious processes
3
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 180 | C:\Windows\system32\vssvc.exe | C:\Windows\system32\vssvc.exe | — | services.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Microsoft® Volume Shadow Copy Service Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 304 | "C:\Program Files\Google\Chrome\Application\chrome.exe" "https://www.finaldraft.com/support/install-final-draft/install-final-draft-11-windows/" | C:\Program Files\Google\Chrome\Application\chrome.exe | explorer.exe | ||||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 536 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=crashpad-handler "--user-data-dir=C:\Users\admin\AppData\Local\Google\Chrome\User Data" /prefetch:7 --monitor-self-annotation=ptype=crashpad-handler "--database=C:\Users\admin\AppData\Local\Google\Chrome\User Data\Crashpad" "--metrics-dir=C:\Users\admin\AppData\Local\Google\Chrome\User Data" --url=https://clients2.google.com/cr/report --annotation=channel= --annotation=plat=Win32 --annotation=prod=Chrome --annotation=ver=75.0.3770.100 --initial-client-data=0x7c,0x80,0x84,0x78,0x88,0x6fa8a9d0,0x6fa8a9e0,0x6fa8a9ec | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 1008 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=1028,15263198736065265692,5579417641597082632,131072 --enable-features=PasswordImport --disable-gpu-compositing --lang=en-US --enable-offline-auto-reload --enable-offline-auto-reload-visible-only --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --service-request-channel-token=11834154772842154800 --renderer-client-id=8 --no-v8-untrusted-code-mitigations --mojo-platform-channel-handle=2656 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 1168 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=1028,15263198736065265692,5579417641597082632,131072 --enable-features=PasswordImport --lang=en-US --enable-offline-auto-reload --enable-offline-auto-reload-visible-only --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --service-request-channel-token=6871405708506344500 --renderer-client-id=5 --no-v8-untrusted-code-mitigations --mojo-platform-channel-handle=2288 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 1232 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --field-trial-handle=1028,15263198736065265692,5579417641597082632,131072 --enable-features=PasswordImport --lang=en-US --service-sandbox-type=utility --service-request-channel-token=14758647536073866115 --mojo-platform-channel-handle=2948 --ignored=" --type=renderer " /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 1392 | C:\Windows\system32\MsiExec.exe -Embedding BA42B29127F159B7C1E9DCCE7DDC81DE C | C:\Windows\system32\MsiExec.exe | — | msiexec.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows® installer Exit code: 0 Version: 5.0.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1740 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --field-trial-handle=1028,15263198736065265692,5579417641597082632,131072 --enable-features=PasswordImport --lang=en-US --service-sandbox-type=utility --service-request-channel-token=11896376380013676040 --mojo-platform-channel-handle=3604 --ignored=" --type=renderer " /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 1748 | "C:\Windows\System32\msiexec.exe" /i "C:\Users\admin\AppData\Local\Temp\Rar$EXa2632.22199\FinalDraftSetup.msi" | C:\Windows\System32\msiexec.exe | WinRAR.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows® installer Exit code: 0 Version: 5.0.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1836 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=1028,15263198736065265692,5579417641597082632,131072 --enable-features=PasswordImport --disable-gpu-compositing --lang=en-US --extension-process --enable-offline-auto-reload --enable-offline-auto-reload-visible-only --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --service-request-channel-token=6508312093108221059 --renderer-client-id=25 --no-v8-untrusted-code-mitigations --mojo-platform-channel-handle=2952 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
Total events
2 918
Read events
2 370
Write events
516
Delete events
32
Modification events
| (PID) Process: | (304) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\BLBeacon |
| Operation: | write | Name: | failed_count |
Value: 0 | |||
| (PID) Process: | (304) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\BLBeacon |
| Operation: | write | Name: | state |
Value: 2 | |||
| (PID) Process: | (304) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\ThirdParty |
| Operation: | write | Name: | StatusCodes |
Value: | |||
| (PID) Process: | (304) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\ThirdParty |
| Operation: | write | Name: | StatusCodes |
Value: 01000000 | |||
| (PID) Process: | (304) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\BLBeacon |
| Operation: | write | Name: | state |
Value: 1 | |||
| (PID) Process: | (2952) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\BrowserExitCodes |
| Operation: | write | Name: | 304-13227619640247000 |
Value: 259 | |||
| (PID) Process: | (304) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Update\ClientState\{8A69D345-D564-463c-AFF1-A69D9E530F96} |
| Operation: | write | Name: | dr |
Value: 1 | |||
| (PID) Process: | (304) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome |
| Operation: | write | Name: | UsageStatsInSample |
Value: 0 | |||
| (PID) Process: | (304) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\BrowserExitCodes |
| Operation: | delete value | Name: | 3120-13213713943555664 |
Value: 0 | |||
| (PID) Process: | (304) chrome.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Google\Update\ClientStateMedium\{8A69D345-D564-463C-AFF1-A69D9E530F96} |
| Operation: | write | Name: | usagestats |
Value: 0 | |||
Executable files
14
Suspicious files
133
Text files
314
Unknown types
22
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 304 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\BrowserMetrics\BrowserMetrics-5E5CE438-130.pma | — | |
MD5:— | SHA256:— | |||
| 304 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\8259a99c-1a5a-4eb5-bda3-54d95a110a2d.tmp | — | |
MD5:— | SHA256:— | |||
| 304 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\data_reduction_proxy_leveldb\000028.dbtmp | — | |
MD5:— | SHA256:— | |||
| 304 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\Site Characteristics Database\LOG.old~RFa66cdb.TMP | text | |
MD5:— | SHA256:— | |||
| 304 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\Sync Data\LevelDB\LOG.old | text | |
MD5:— | SHA256:— | |||
| 304 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\Site Characteristics Database\LOG.old | text | |
MD5:— | SHA256:— | |||
| 304 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\data_reduction_proxy_leveldb\LOG.old~RFa66d0a.TMP | text | |
MD5:— | SHA256:— | |||
| 304 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\Sync Data\LevelDB\LOG.old~RFa66cfb.TMP | text | |
MD5:— | SHA256:— | |||
| 304 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\shared_proto_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 304 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\shared_proto_db\LOG.old~RFa66f0e.TMP | — | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
5
TCP/UDP connections
67
DNS requests
48
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
2796 | chrome.exe | GET | 204 | 216.58.207.35:80 | http://www.gstatic.com/generate_204 | US | — | — | whitelisted |
2796 | chrome.exe | GET | 302 | 172.217.22.78:80 | http://redirector.gvt1.com/edgedl/chromewebstore/L2Nocm9tZV9leHRlbnNpb24vYmxvYnMvOWVmQUFXS041NV9ZVXlJVWwxbGc5TUM4dw/7519.422.0.3_pkedcjkdefgpdelpbcmbmeomcjbeemfm.crx | US | html | 515 b | whitelisted |
2796 | chrome.exe | GET | 302 | 172.217.22.78:80 | http://redirector.gvt1.com/edgedl/chromewebstore/L2Nocm9tZV9leHRlbnNpb24vYmxvYnMvOTRmQUFXVHlhaGJaUTdMLWtCSkNJUl9ZQQ/1.0.0.5_nmmhkkegccagdldgiimedpiccmgmieda.crx | US | html | 510 b | whitelisted |
2796 | chrome.exe | GET | 200 | 173.194.150.231:80 | http://r1---sn-2gb7sn7s.gvt1.com/edgedl/chromewebstore/L2Nocm9tZV9leHRlbnNpb24vYmxvYnMvOTRmQUFXVHlhaGJaUTdMLWtCSkNJUl9ZQQ/1.0.0.5_nmmhkkegccagdldgiimedpiccmgmieda.crx?cms_redirect=yes&mip=195.181.166.91&mm=28&mn=sn-2gb7sn7s&ms=nvh&mt=1583145973&mv=m&mvi=0&pl=24&shardbypass=yes | US | crx | 293 Kb | whitelisted |
2796 | chrome.exe | GET | 200 | 173.194.150.236:80 | http://r6---sn-2gb7sn7s.gvt1.com/edgedl/chromewebstore/L2Nocm9tZV9leHRlbnNpb24vYmxvYnMvOWVmQUFXS041NV9ZVXlJVWwxbGc5TUM4dw/7519.422.0.3_pkedcjkdefgpdelpbcmbmeomcjbeemfm.crx?cms_redirect=yes&mip=195.181.166.91&mm=28&mn=sn-2gb7sn7s&ms=nvh&mt=1583145973&mv=m&mvi=5&pl=24&shardbypass=yes | US | crx | 862 Kb | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
2796 | chrome.exe | 172.217.23.138:443 | fonts.googleapis.com | Google Inc. | US | whitelisted |
2796 | chrome.exe | 216.58.206.8:443 | www.googletagmanager.com | Google Inc. | US | whitelisted |
2796 | chrome.exe | 3.213.5.196:443 | magento.hubshop.ly | — | US | unknown |
2796 | chrome.exe | 172.217.21.228:443 | www.google.com | Google Inc. | US | whitelisted |
2796 | chrome.exe | 209.197.3.15:443 | netdna.bootstrapcdn.com | Highwinds Network Group, Inc. | US | whitelisted |
2796 | chrome.exe | 216.58.205.227:443 | fonts.gstatic.com | Google Inc. | US | whitelisted |
2796 | chrome.exe | 104.17.67.176:443 | js.hs-analytics.net | Cloudflare Inc | US | shared |
2796 | chrome.exe | 216.58.208.46:443 | www.google-analytics.com | Google Inc. | US | whitelisted |
2796 | chrome.exe | 104.17.235.204:443 | js.usemessages.com | Cloudflare Inc | US | shared |
2796 | chrome.exe | 104.17.131.171:443 | js.hscollectedforms.net | Cloudflare Inc | US | shared |
DNS requests
Domain | IP | Reputation |
|---|---|---|
clientservices.googleapis.com |
| whitelisted |
www.finaldraft.com |
| unknown |
accounts.google.com |
| shared |
fonts.googleapis.com |
| whitelisted |
www.googletagmanager.com |
| whitelisted |
magento.hubshop.ly |
| unknown |
js.hs-scripts.com |
| whitelisted |
js.hsforms.net |
| whitelisted |
www.google.com |
| malicious |
fonts.gstatic.com |
| whitelisted |
Threats
Process | Message |
|---|---|
FNPLicensingService.exe | Getting VMAttrs
|
FNPLicensingService.exe | Getting TPMProps
|