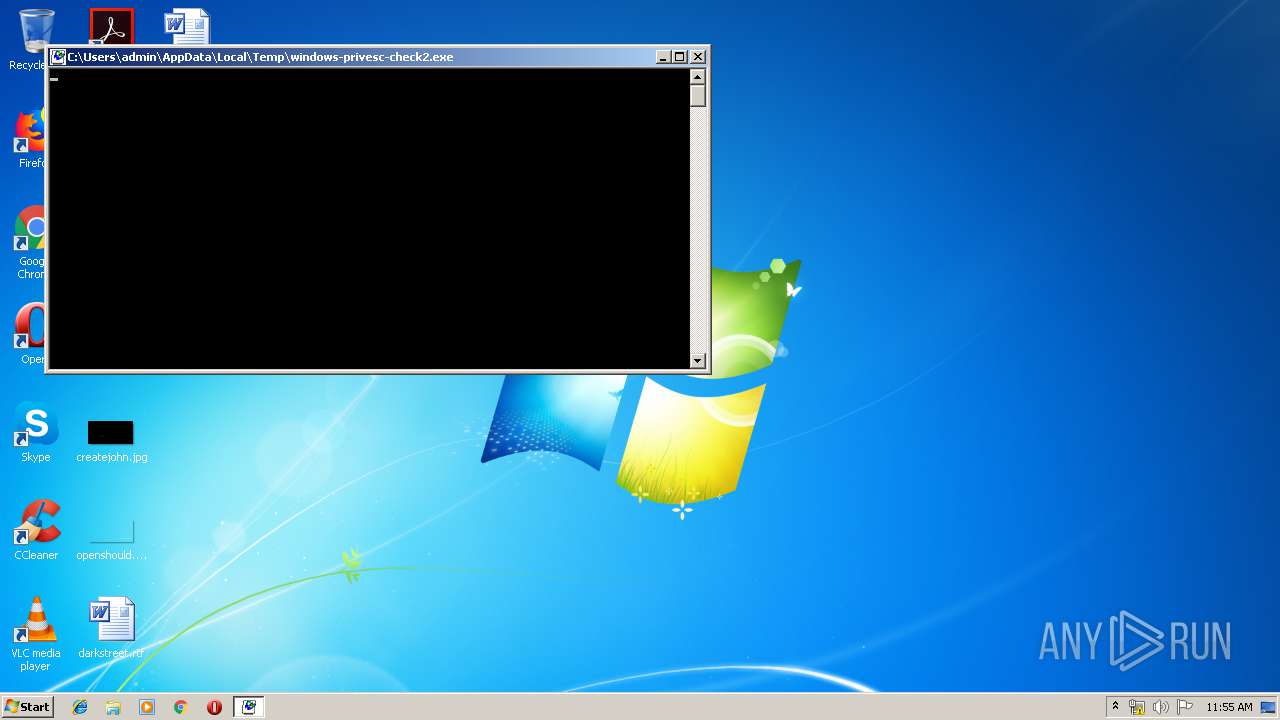
| File name: | windows-privesc-check2.exe |
| Full analysis: | https://app.any.run/tasks/fbac23c3-3802-40e6-84c9-a44f1e8550bd |
| Verdict: | Malicious activity |
| Analysis date: | June 05, 2019, 10:55:16 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (console) Intel 80386, for MS Windows |
| MD5: | 0F4471B3F8B3485268DFA7E825A217B4 |
| SHA1: | 1FBC3F8CF90DCFFEFB8F42436F9DB2EC6F9AE12D |
| SHA256: | 483622FB3A2B1287DBD15C3C73A91025FFACC8A485134054BCDFB9592E7E9718 |
| SSDEEP: | 196608:NvPGP3TjBcWivlGV0Es2OkbtFELnZMEvEQWARzAF:NvOHBvm2Ns2OkpeZMXAOF |
MALICIOUS
Loads dropped or rewritten executable
- windows-privesc-check2.exe (PID: 3324)
- windows-privesc-check2.exe (PID: 584)
- windows-privesc-check2.exe (PID: 2912)
SUSPICIOUS
Application launched itself
- windows-privesc-check2.exe (PID: 3092)
Executable content was dropped or overwritten
- windows-privesc-check2.exe (PID: 3092)
- windows-privesc-check2.exe (PID: 1136)
- windows-privesc-check2.exe (PID: 2736)
Loads Python modules
- windows-privesc-check2.exe (PID: 3324)
- windows-privesc-check2.exe (PID: 584)
- windows-privesc-check2.exe (PID: 2912)
INFO
Manual execution by user
- cmd.exe (PID: 2008)
- explorer.exe (PID: 3608)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win32 Executable MS Visual C++ (generic) (42.2) |
|---|---|---|
| .exe | | | Win64 Executable (generic) (37.3) |
| .dll | | | Win32 Dynamic Link Library (generic) (8.8) |
| .exe | | | Win32 Executable (generic) (6) |
| .exe | | | Generic Win/DOS Executable (2.7) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2010:11:12 17:08:38+01:00 |
| PEType: | PE32 |
| LinkerVersion: | 7.1 |
| CodeSize: | 57344 |
| InitializedDataSize: | 36864 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x6a0b |
| OSVersion: | 4 |
| ImageVersion: | - |
| SubsystemVersion: | 4 |
| Subsystem: | Windows command line |
Summary
| Architecture: | IMAGE_FILE_MACHINE_I386 |
|---|---|
| Subsystem: | IMAGE_SUBSYSTEM_WINDOWS_CUI |
| Compilation Date: | 12-Nov-2010 16:08:38 |
DOS Header
| Magic number: | MZ |
|---|---|
| Bytes on last page of file: | 0x0090 |
| Pages in file: | 0x0003 |
| Relocations: | 0x0000 |
| Size of header: | 0x0004 |
| Min extra paragraphs: | 0x0000 |
| Max extra paragraphs: | 0xFFFF |
| Initial SS value: | 0x0000 |
| Initial SP value: | 0x00B8 |
| Checksum: | 0x0000 |
| Initial IP value: | 0x0000 |
| Initial CS value: | 0x0000 |
| Overlay number: | 0x0000 |
| OEM identifier: | 0x0000 |
| OEM information: | 0x0000 |
| Address of NE header: | 0x000000E8 |
PE Headers
| Signature: | PE |
|---|---|
| Machine: | IMAGE_FILE_MACHINE_I386 |
| Number of sections: | 4 |
| Time date stamp: | 12-Nov-2010 16:08:38 |
| Pointer to Symbol Table: | 0x00000000 |
| Number of symbols: | 0 |
| Size of Optional Header: | 0x00E0 |
| Characteristics: |
|
Sections
Name | Virtual Address | Virtual Size | Raw Size | Charateristics | Entropy |
|---|---|---|---|---|---|
.text | 0x00001000 | 0x0000D18E | 0x0000E000 | IMAGE_SCN_CNT_CODE, IMAGE_SCN_MEM_EXECUTE, IMAGE_SCN_MEM_READ | 6.47947 |
.rdata | 0x0000F000 | 0x00004FD6 | 0x00005000 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ | 6.83391 |
.data | 0x00014000 | 0x000026C4 | 0x00001000 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ, IMAGE_SCN_MEM_WRITE | 1.18751 |
.rsrc | 0x00017000 | 0x000003A0 | 0x00001000 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ | 0.976058 |
Resources
Title | Entropy | Size | Codepage | Language | Type |
|---|---|---|---|---|---|
1 | 2.74586 | 744 | UNKNOWN | UNKNOWN | RT_ICON |
101 | 2.16096 | 20 | UNKNOWN | UNKNOWN | RT_GROUP_ICON |
Imports
COMCTL32.dll |
KERNEL32.dll |
WS2_32.dll |
Total processes
42
Monitored processes
8
Malicious processes
7
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 584 | "C:\Users\admin\AppData\Local\Temp\windows-privesc-check2.exe" | C:\Users\admin\AppData\Local\Temp\windows-privesc-check2.exe | — | windows-privesc-check2.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
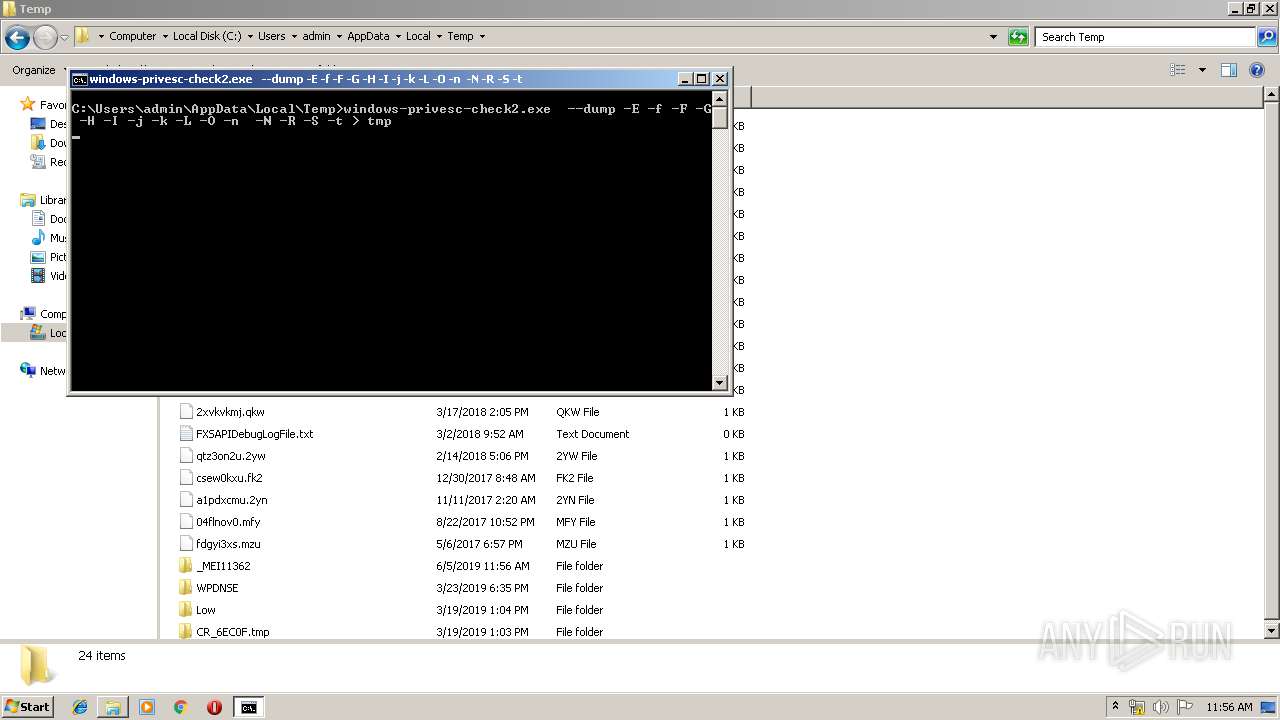
| 1136 | windows-privesc-check2.exe --dump -E -f -F -G -H -I -j -k -L -O -n -N -R -S -t | C:\Users\admin\AppData\Local\Temp\windows-privesc-check2.exe | cmd.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
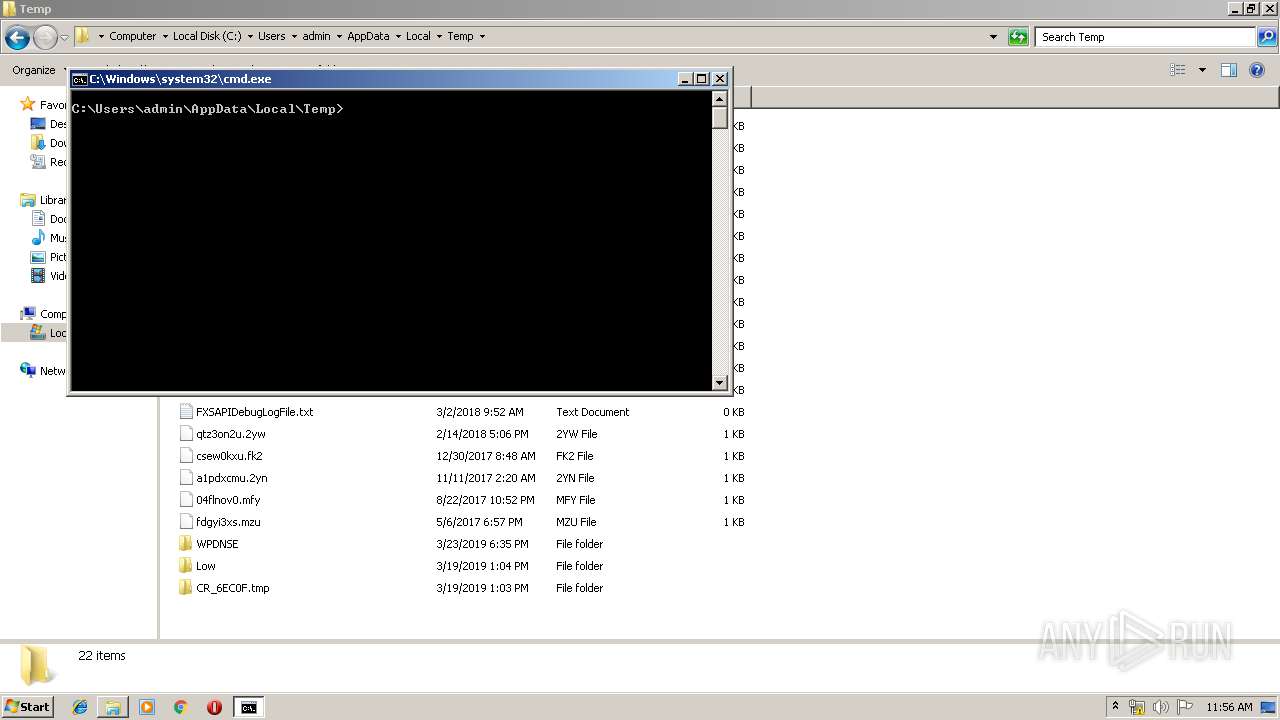
| 2008 | "cmd.exe" /s /k pushd "C:\Users\admin\AppData\Local\Temp" | C:\Windows\system32\cmd.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 2736 | windows-privesc-check2.exe --dump -E -f -F -G -H -I -j -k -L -O -n -N -R -S -t -e -r | C:\Users\admin\AppData\Local\Temp\windows-privesc-check2.exe | cmd.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 2912 | windows-privesc-check2.exe --dump -E -f -F -G -H -I -j -k -L -O -n -N -R -S -t -e -r | C:\Users\admin\AppData\Local\Temp\windows-privesc-check2.exe | — | windows-privesc-check2.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 3092 | "C:\Users\admin\AppData\Local\Temp\windows-privesc-check2.exe" | C:\Users\admin\AppData\Local\Temp\windows-privesc-check2.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 3324 | windows-privesc-check2.exe --dump -E -f -F -G -H -I -j -k -L -O -n -N -R -S -t | C:\Users\admin\AppData\Local\Temp\windows-privesc-check2.exe | — | windows-privesc-check2.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 3608 | "C:\Windows\explorer.exe" | C:\Windows\explorer.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Explorer Exit code: 1 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
Total events
44
Read events
44
Write events
0
Delete events
0
Modification events
Executable files
90
Suspicious files
0
Text files
7
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3092 | windows-privesc-check2.exe | C:\Users\admin\AppData\Local\Temp\_MEI30922\lxml.etree.pyd | executable | |
MD5:6A21F6FBBF3108AD99C84652EA95658B | SHA256:FD6B56D9F66189B7FAC18B5F6C886A088CCE22878A09D241DCDDF3EE72EEEF83 | |||
| 3092 | windows-privesc-check2.exe | C:\Users\admin\AppData\Local\Temp\_MEI30922\_ctypes.pyd | executable | |
MD5:6027866CC7E8A639FE7300B2558112A3 | SHA256:552AA528F998319DD95D95EA13CD37615A725155D171E88BD15ADE707723FFD7 | |||
| 3092 | windows-privesc-check2.exe | C:\Users\admin\AppData\Local\Temp\_MEI30922\unicodedata.pyd | executable | |
MD5:0F0DEB93E54A9F1B88264F7A0361693B | SHA256:929397BBFB0E34DDA5D18B6C4E5D271B4EE6A63A32E5F0C328A53B1C55A9590E | |||
| 3092 | windows-privesc-check2.exe | C:\Users\admin\AppData\Local\Temp\_MEI30922\_ssl.pyd | executable | |
MD5:1984F73F94D11E197EFAEC2DC41232F5 | SHA256:BCAD190AB35F96A8F360131C0B7138DCD826BA8A903679510FFB34CA4F73CC77 | |||
| 3092 | windows-privesc-check2.exe | C:\Users\admin\AppData\Local\Temp\_MEI30922\win32security.pyd | executable | |
MD5:C7B4B4E558119A29E539DBA732C683BE | SHA256:2CAF1331C77E2C2CECC5E10FAD8F5BC71BA8CED1E8BBE1FF89281D8AF4E9D75A | |||
| 3092 | windows-privesc-check2.exe | C:\Users\admin\AppData\Local\Temp\_MEI30922\pyexpat.pyd | executable | |
MD5:BD4D05A721092AF27631432186C9FEB7 | SHA256:4378F7822EA0E05069DB404DB2C1DB0392DF76CD6EB77B6D0FB209D0E4F35CFF | |||
| 3092 | windows-privesc-check2.exe | C:\Users\admin\AppData\Local\Temp\_MEI30922\win32ts.pyd | executable | |
MD5:EC45CC5611C0CF5F4E0430F438DC3486 | SHA256:2B2BF3A3D1A1175A81416686132CD6CE45C6E7DA8969DE03FED2E150264EF5FE | |||
| 3092 | windows-privesc-check2.exe | C:\Users\admin\AppData\Local\Temp\_MEI30922\win32file.pyd | executable | |
MD5:D4F8743311FFF7DACB9D5AE68B49BFE3 | SHA256:9AA650A9117918B9C57F89B573BB597C91C18E77E4EAE0145829A3E283C74B82 | |||
| 3092 | windows-privesc-check2.exe | C:\Users\admin\AppData\Local\Temp\_MEI30922\win32service.pyd | executable | |
MD5:E13134CD2996BAE2E9573EA7568A0648 | SHA256:FBB43981B5DFB0B7392724831855AC7B9AD4980CD625B0A14EE8B90320EA0B34 | |||
| 3092 | windows-privesc-check2.exe | C:\Users\admin\AppData\Local\Temp\_MEI30922\win32process.pyd | executable | |
MD5:25445FAED925F4657043CDEEA487BDEF | SHA256:2DD65A8A8C85C4DAF4C16DD7F1E12ADFBE2E18111A208EF4E01471358CBF4DC3 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
0
DNS requests
0
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report